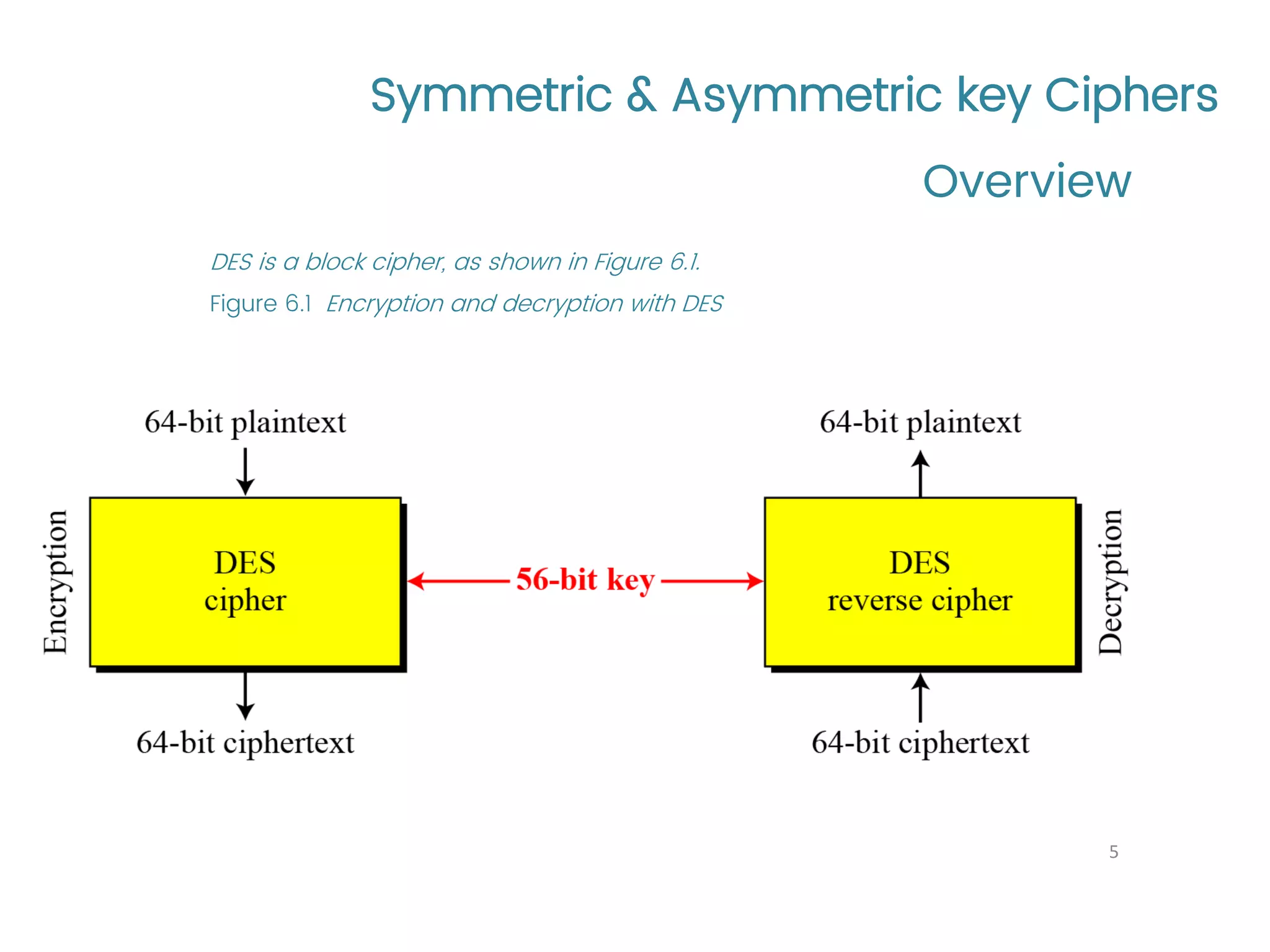
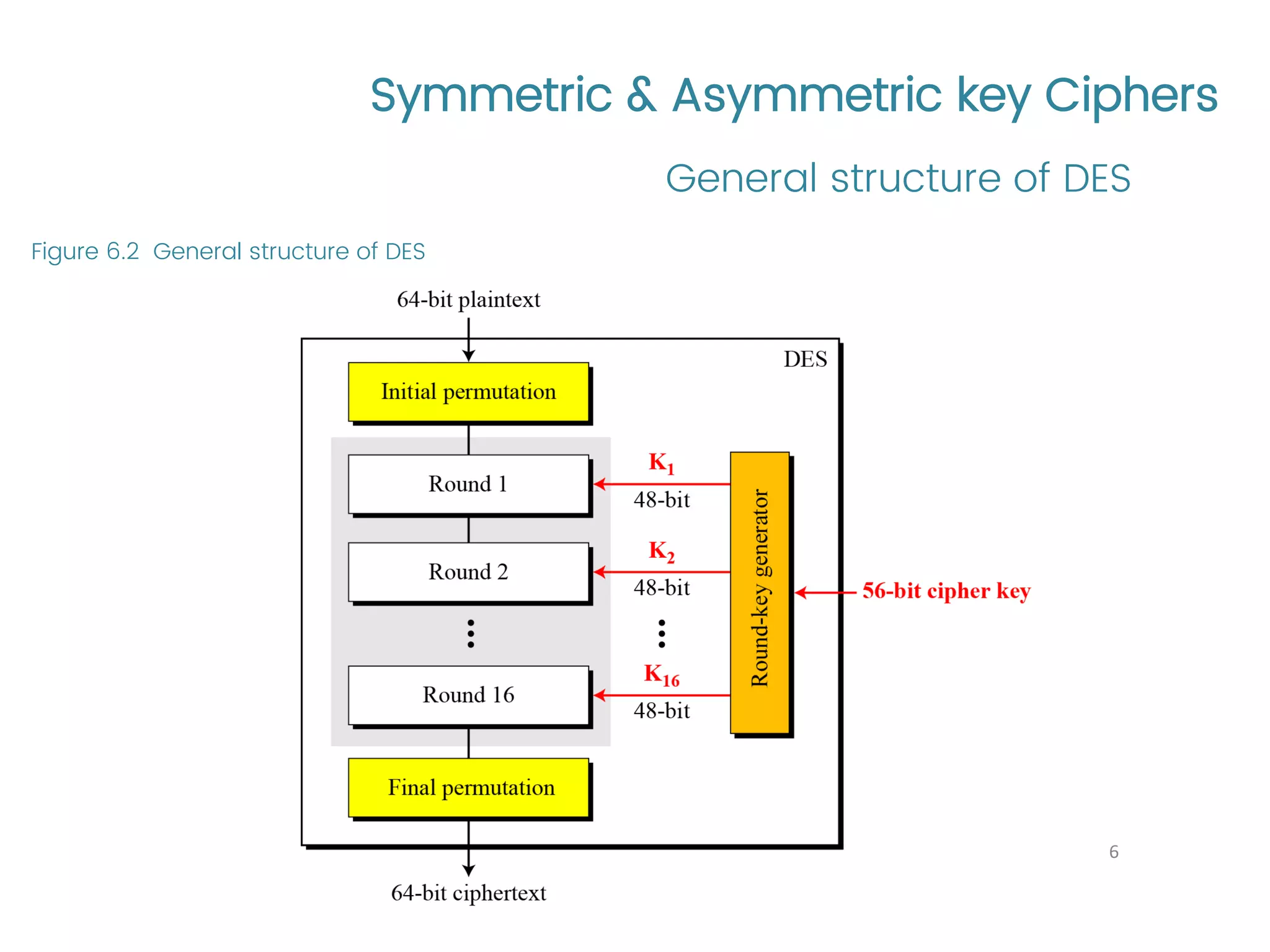
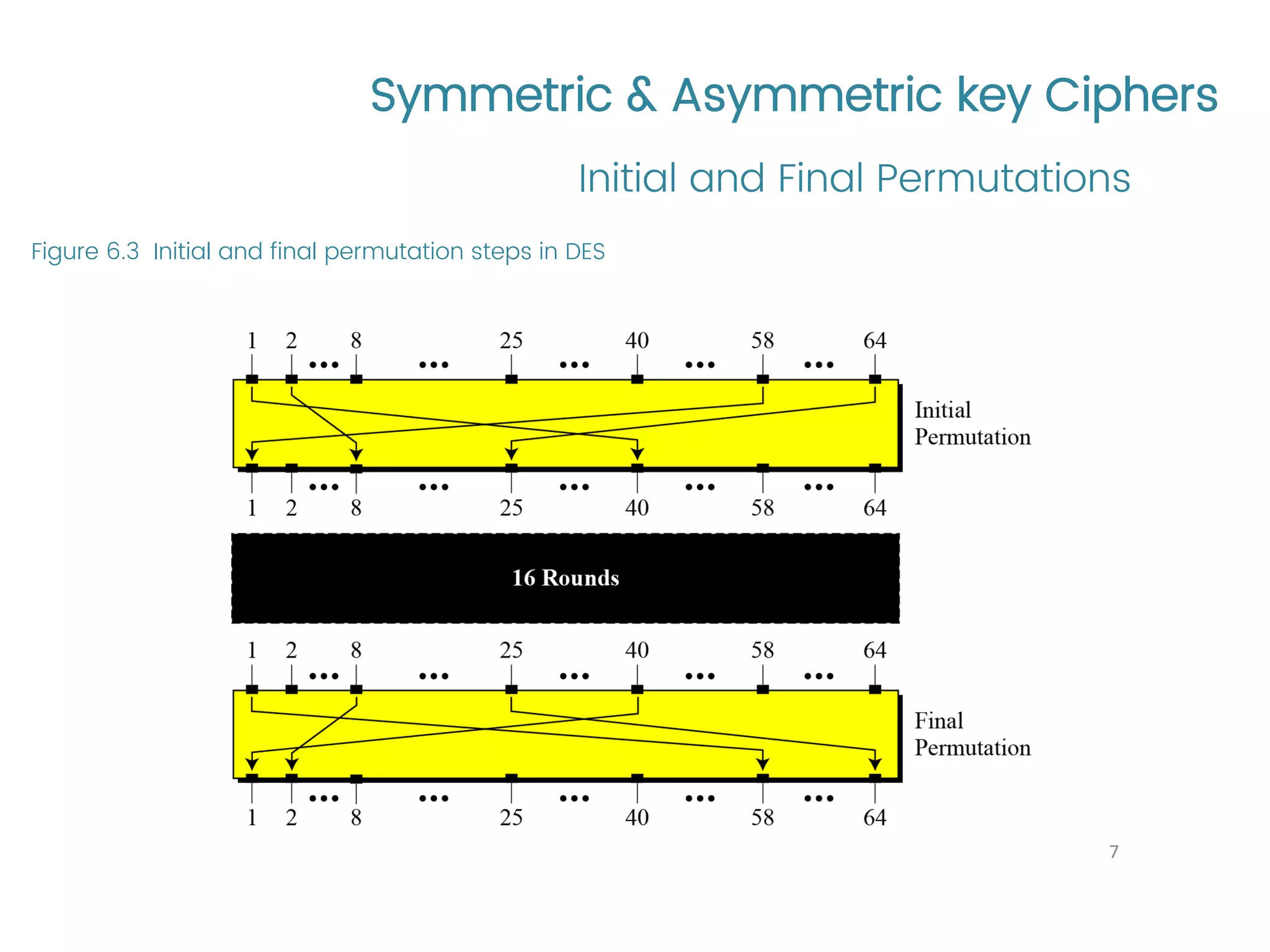
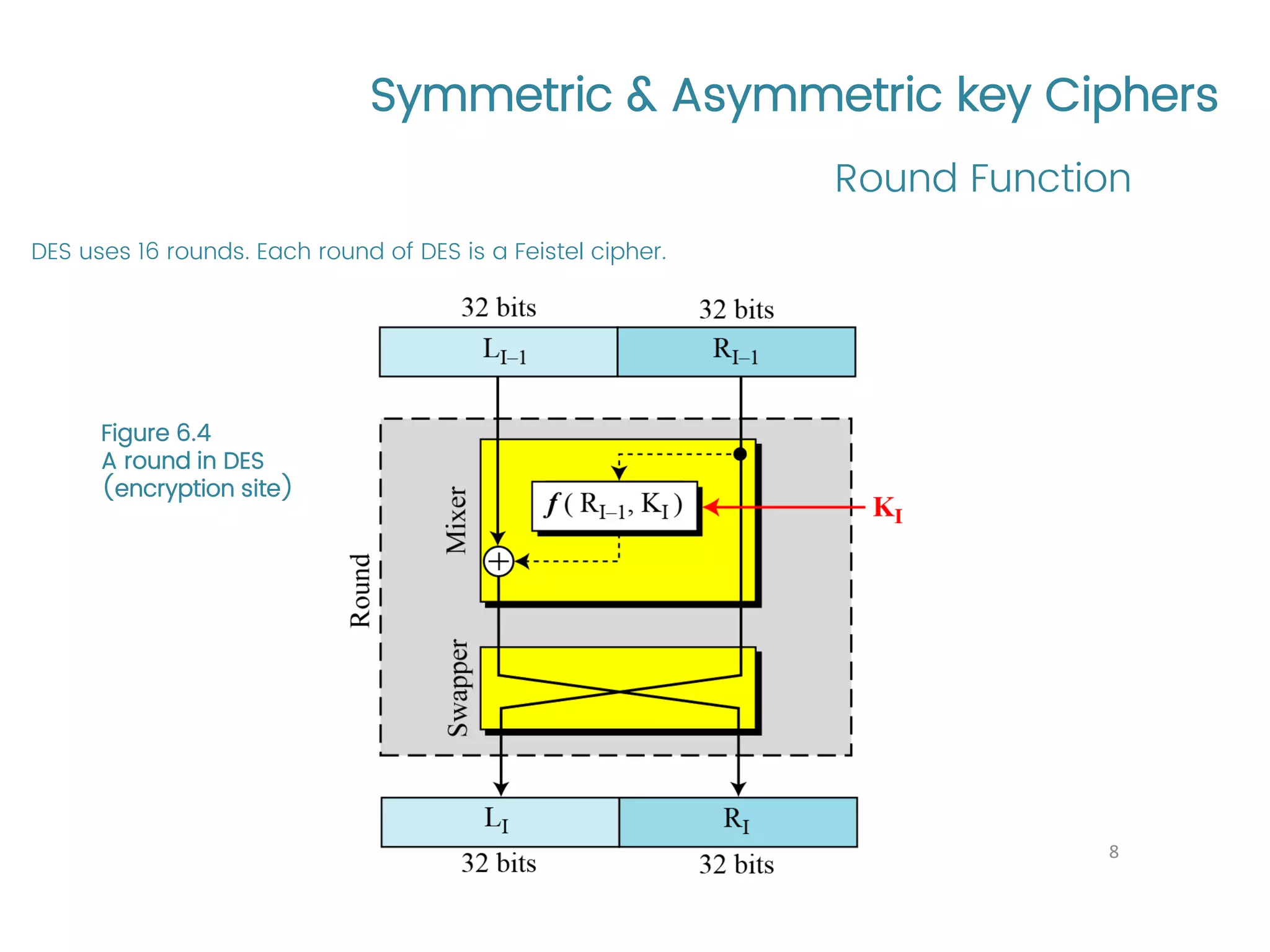
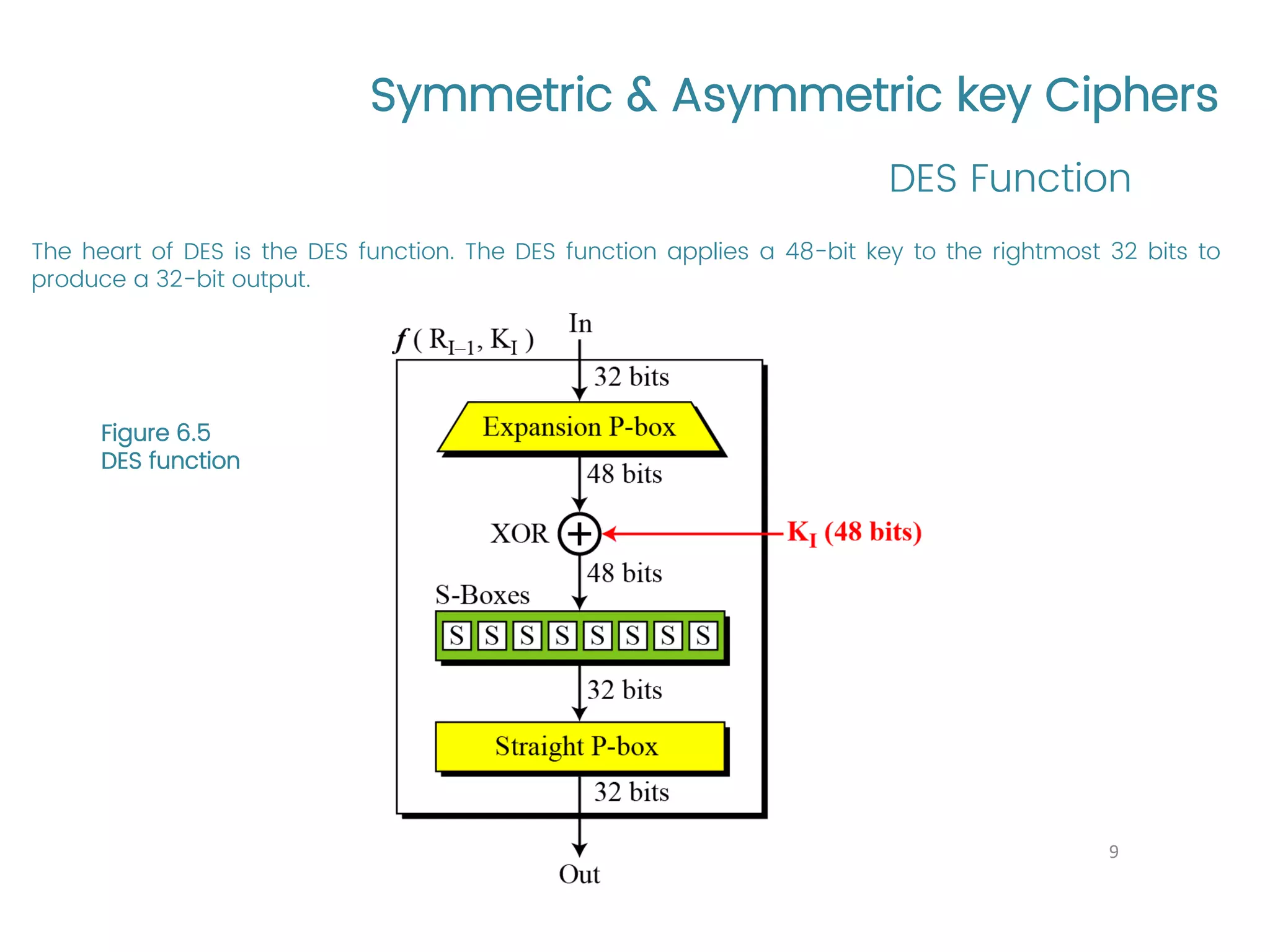
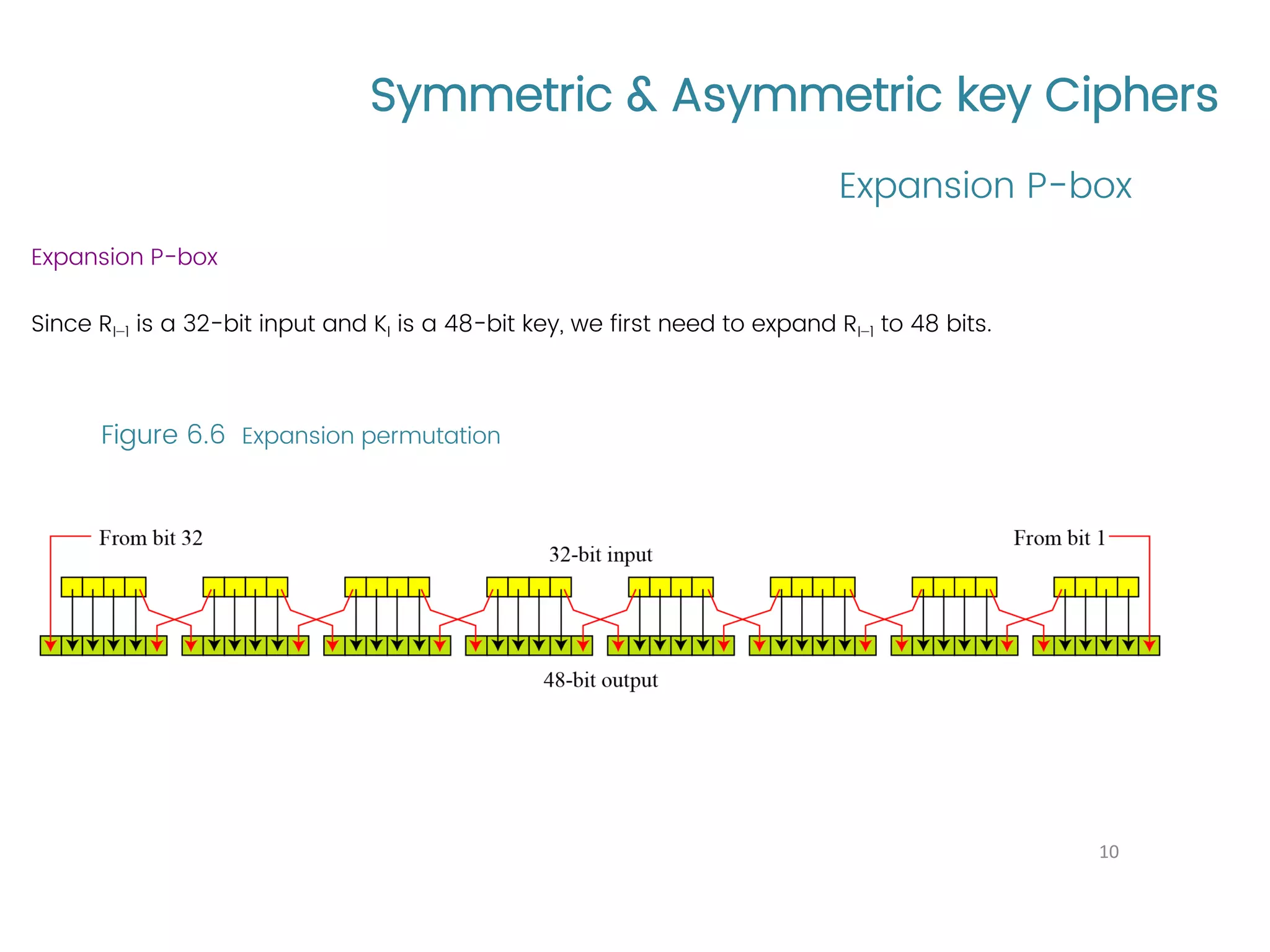
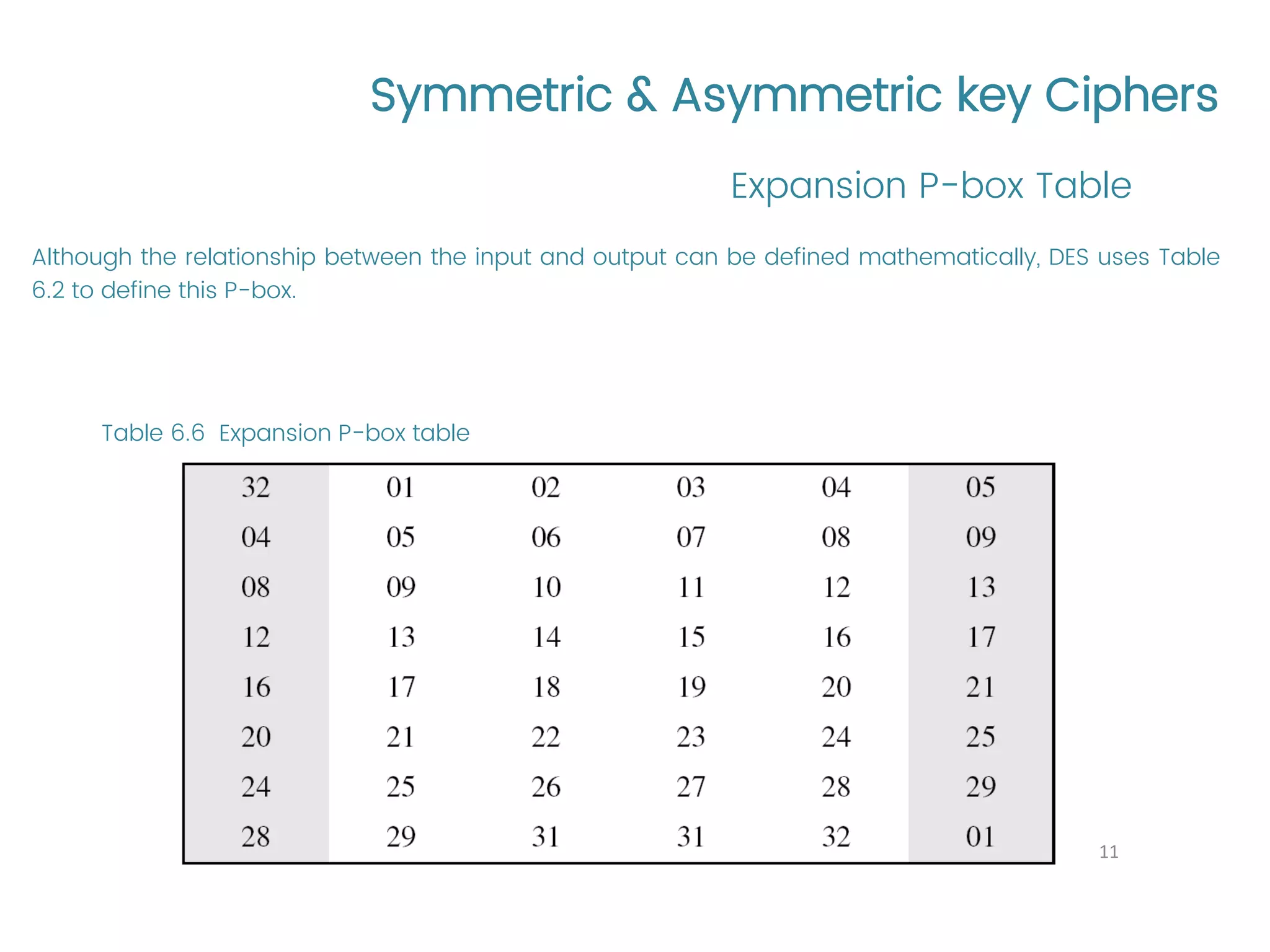
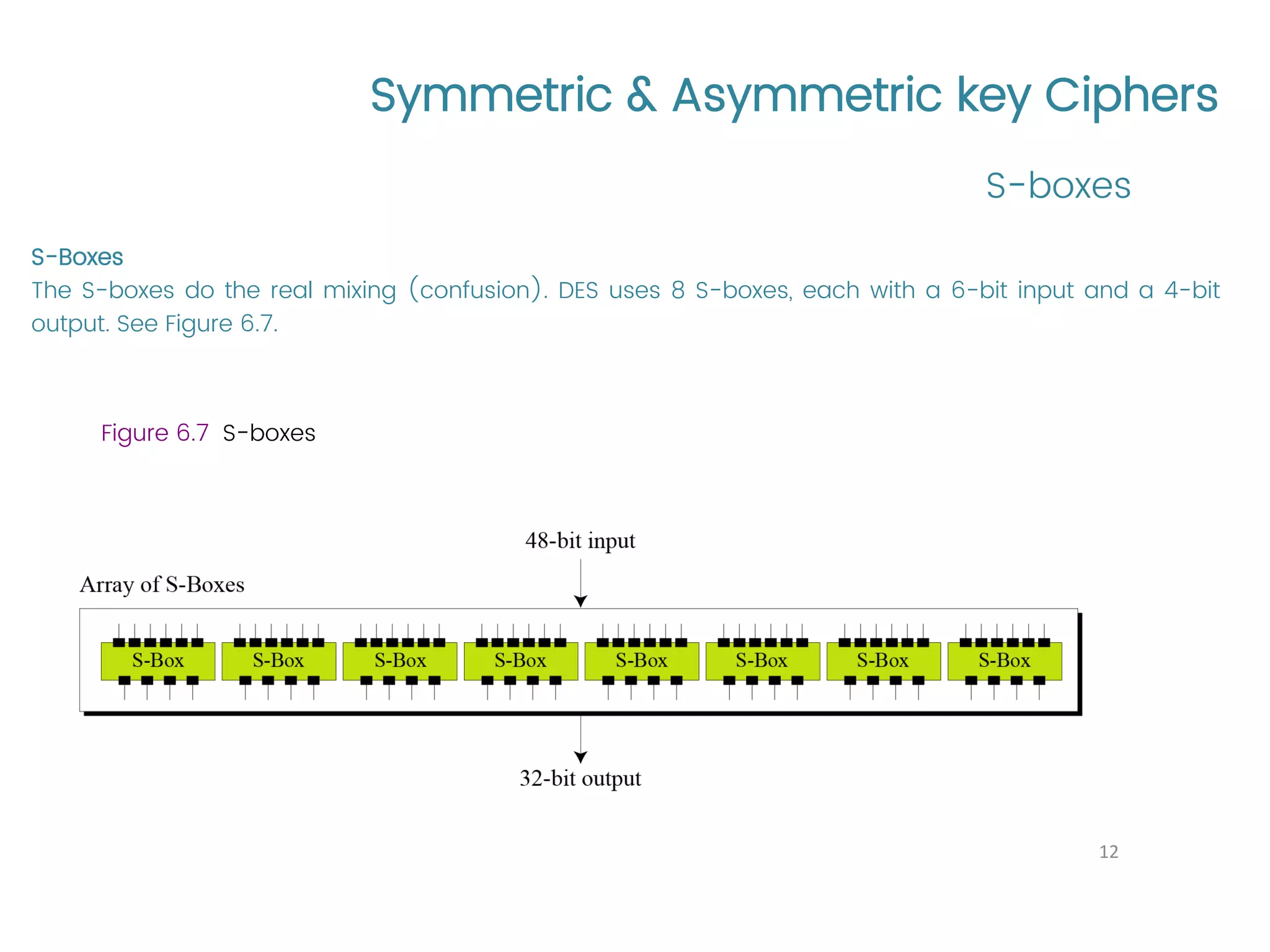
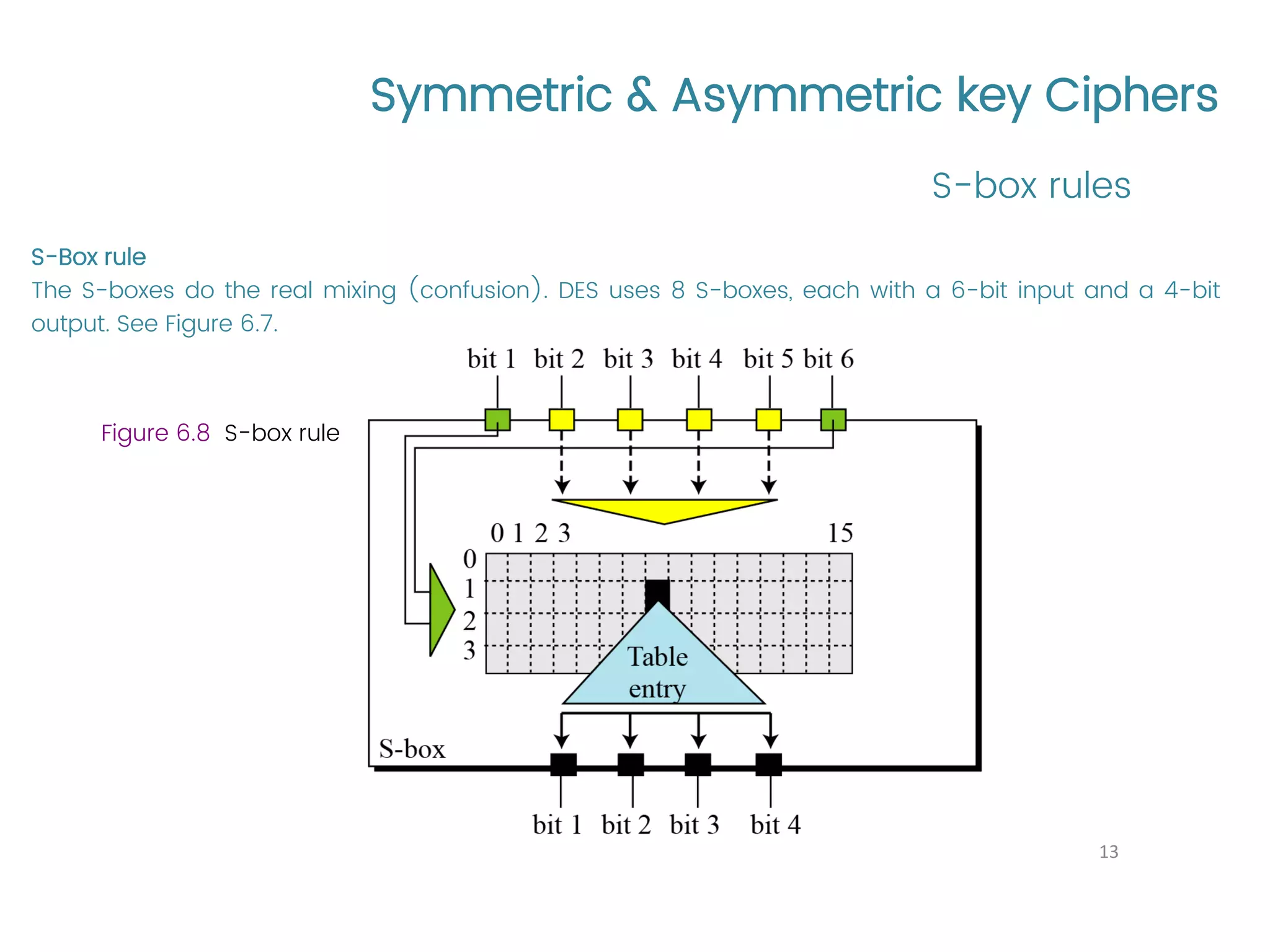
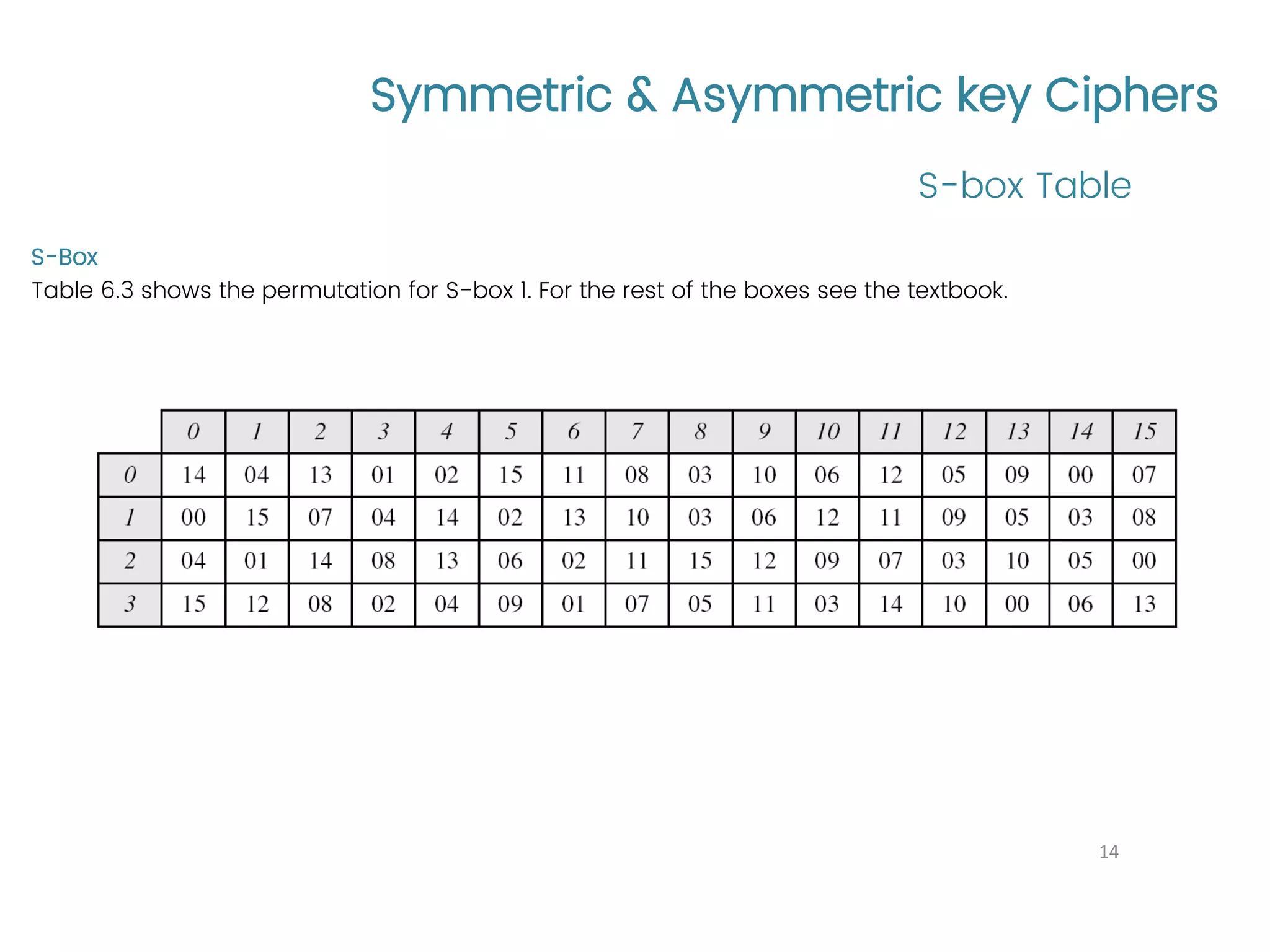
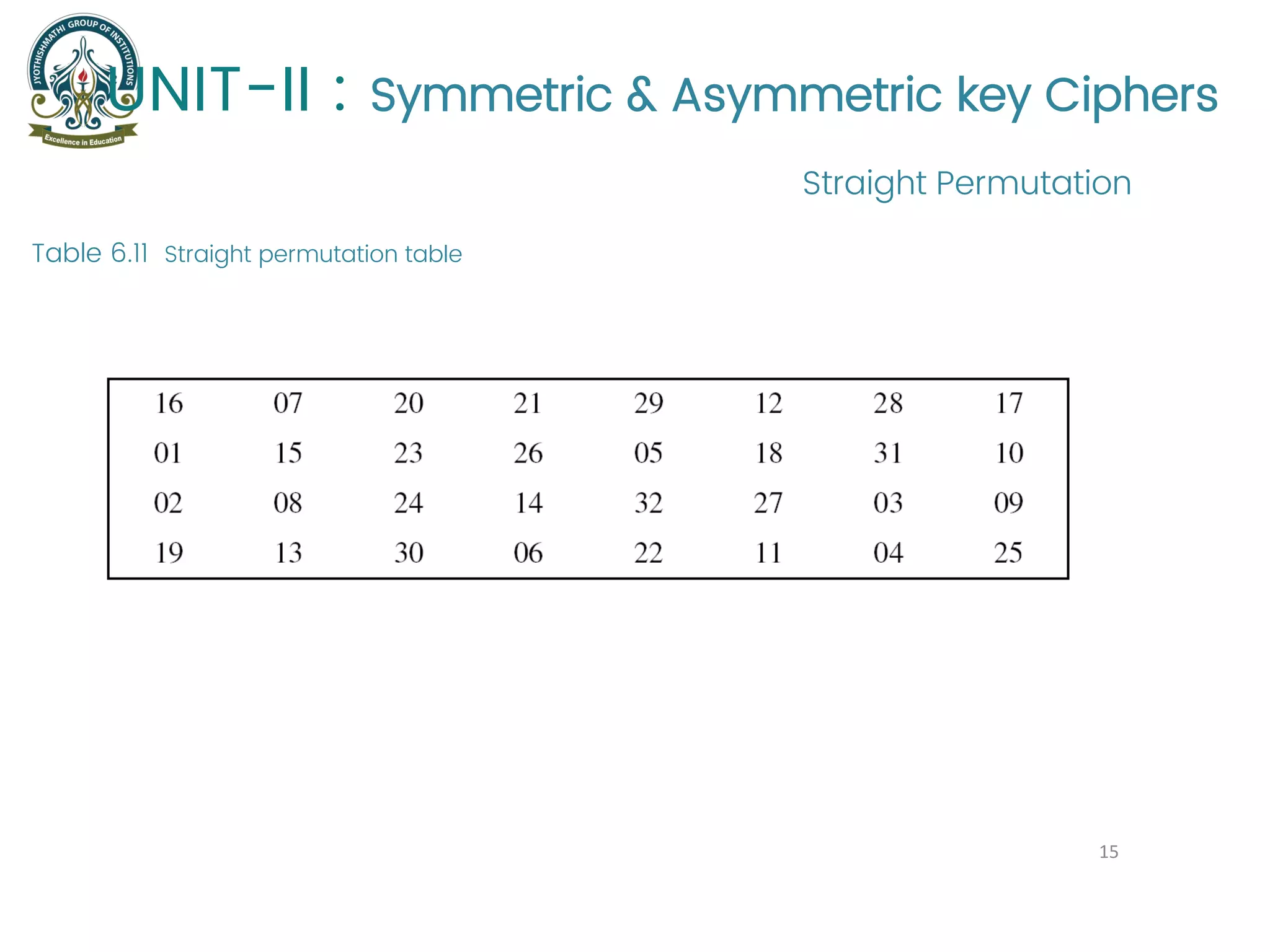
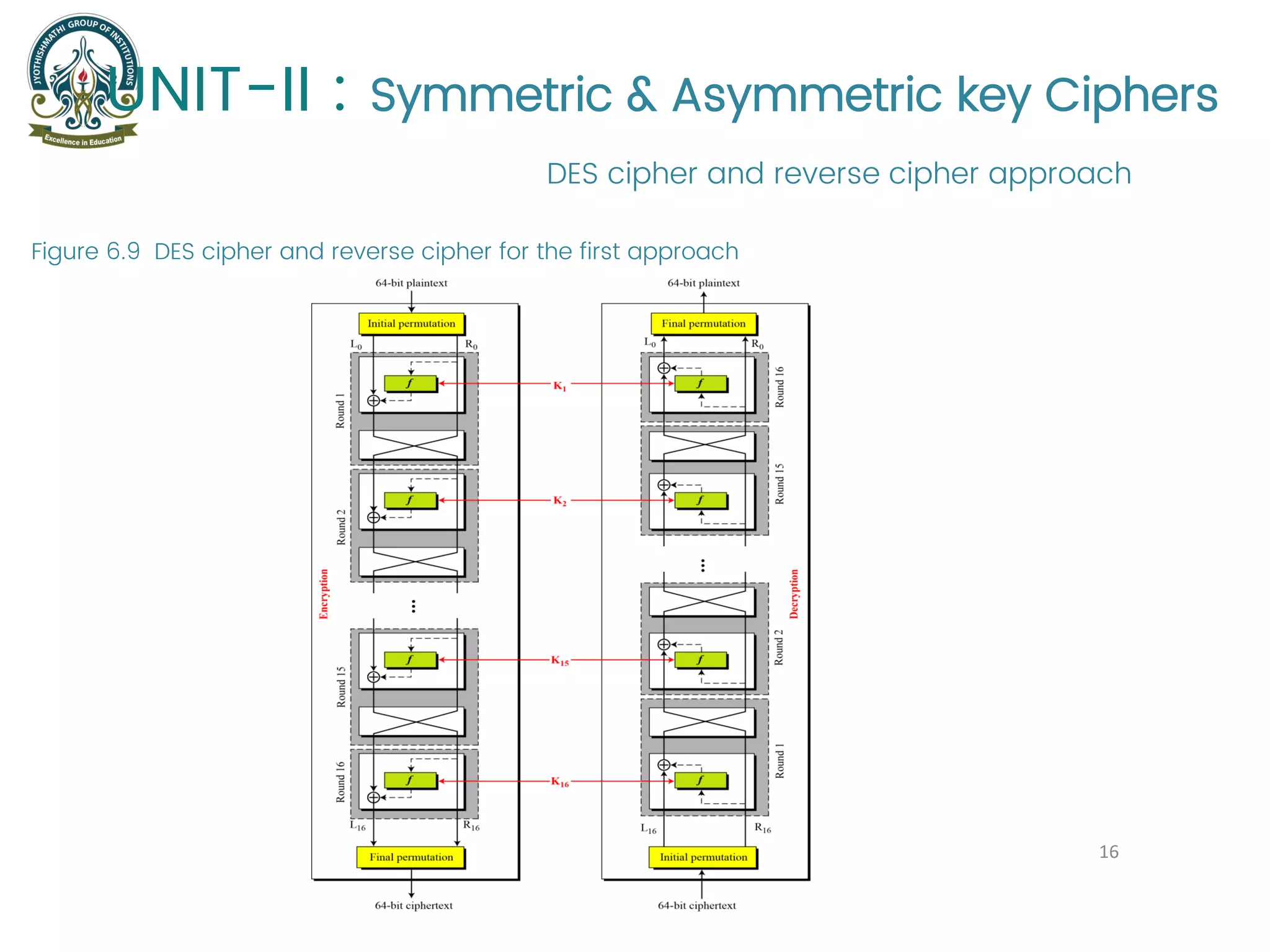
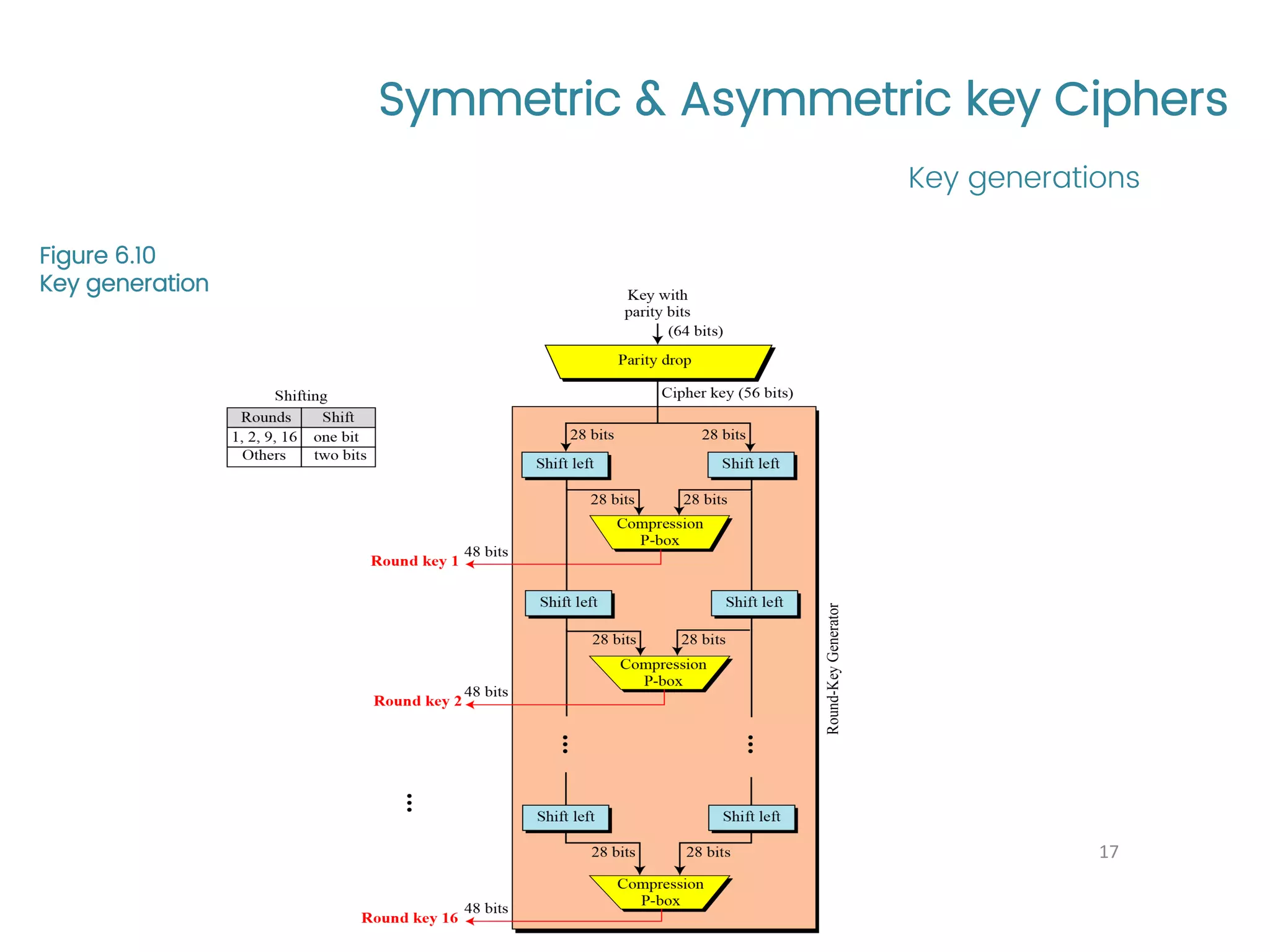
The document provides an overview of symmetric and asymmetric key ciphers, with a focus on the Data Encryption Standard (DES) as a symmetric-key block cipher, detailing its structure, round keys generation, and operational principles. It also covers various cryptographic algorithms and principles such as RSA, ElGamal, and Diffie-Hellman, as well as resources for further study. Additionally, it includes tutorial references and questions related to network security and cryptography.