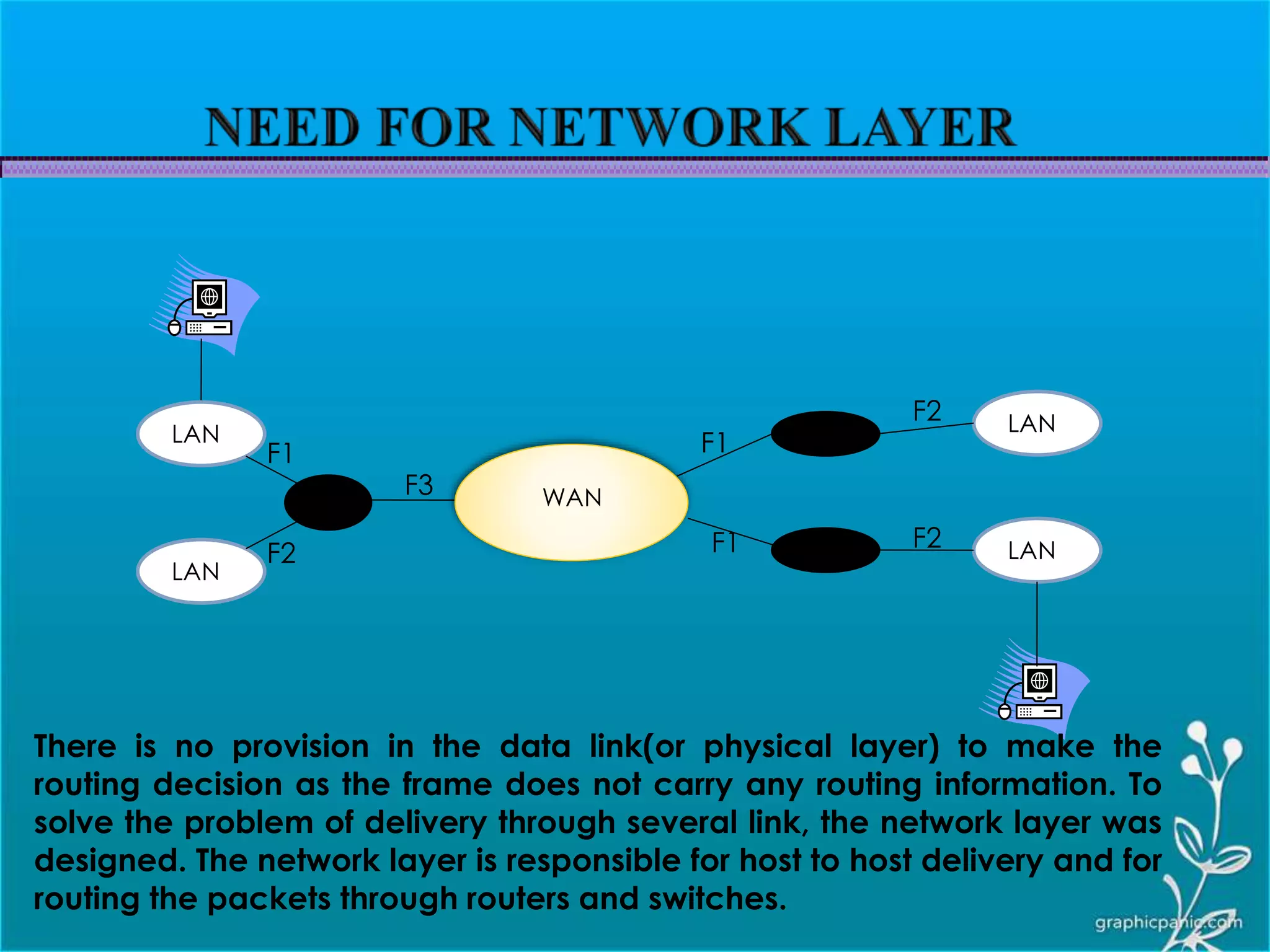
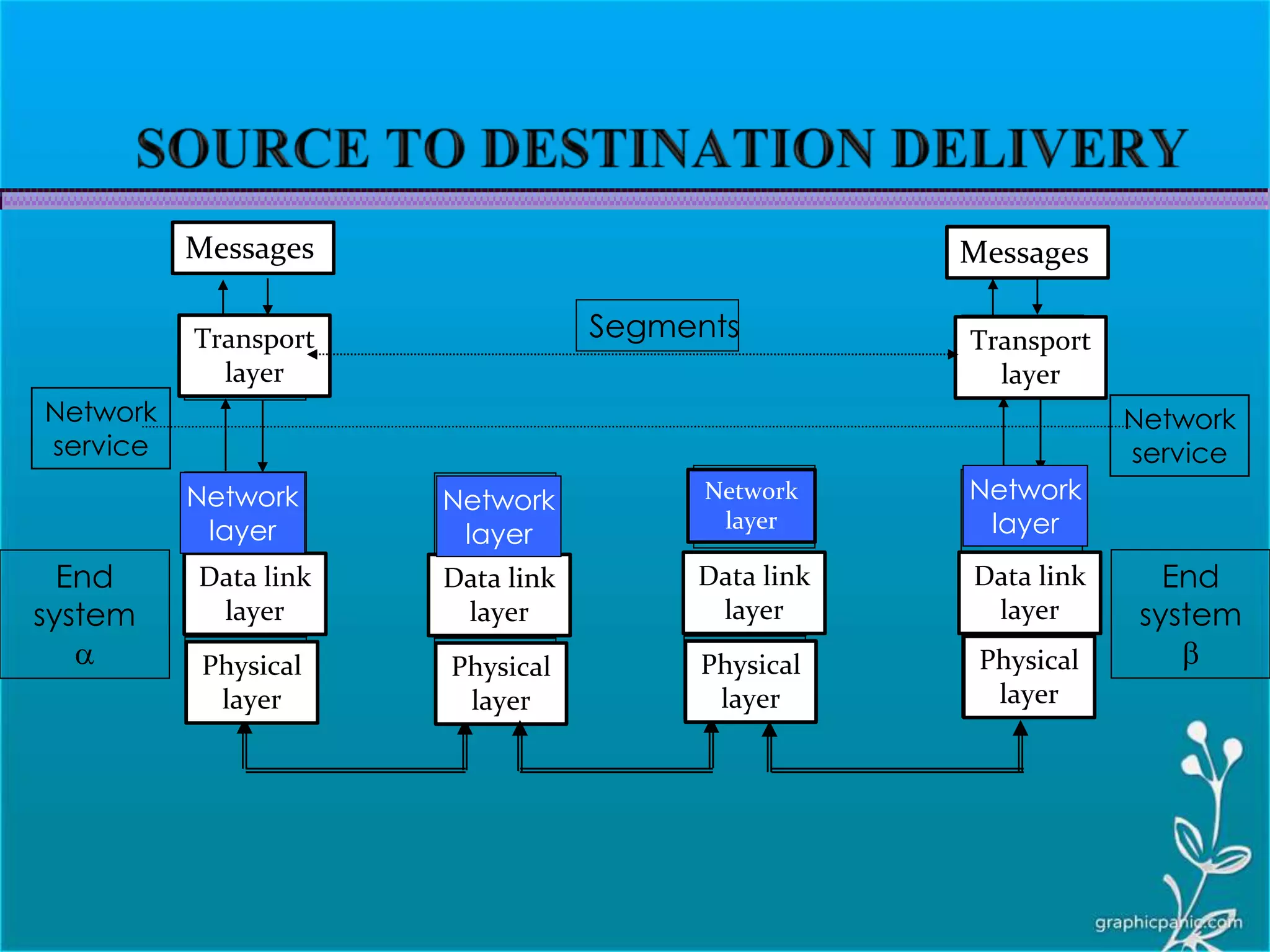
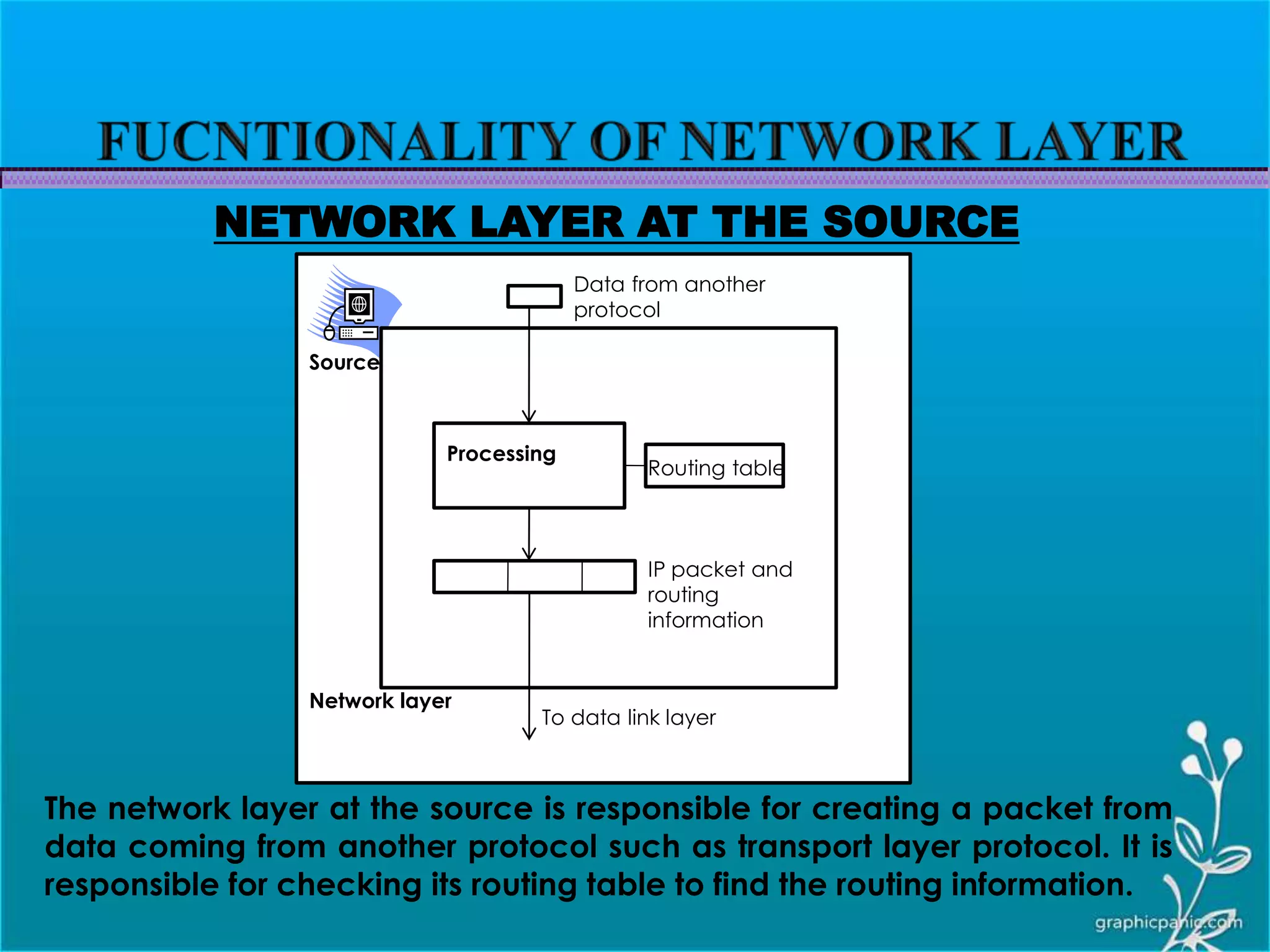
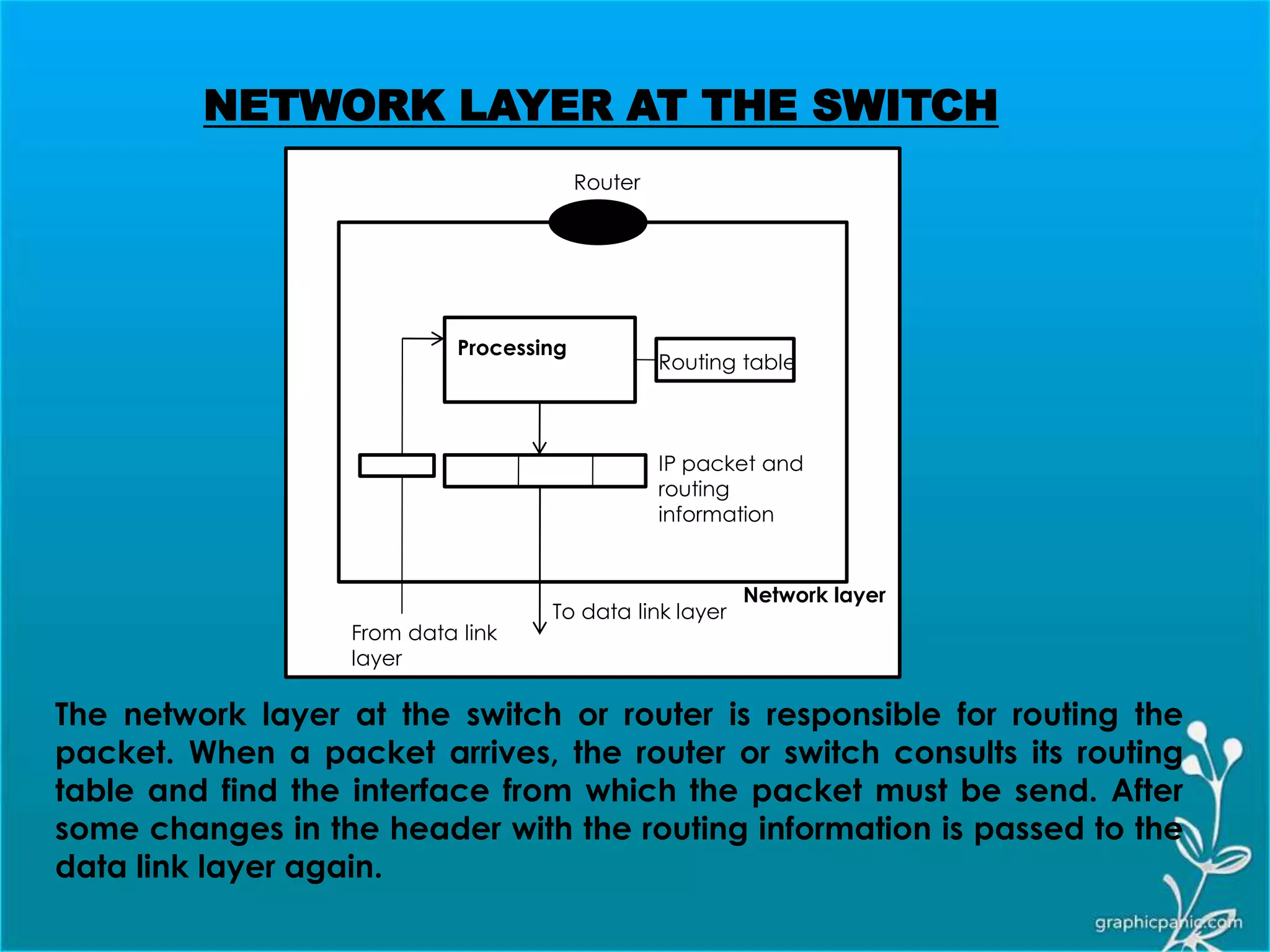
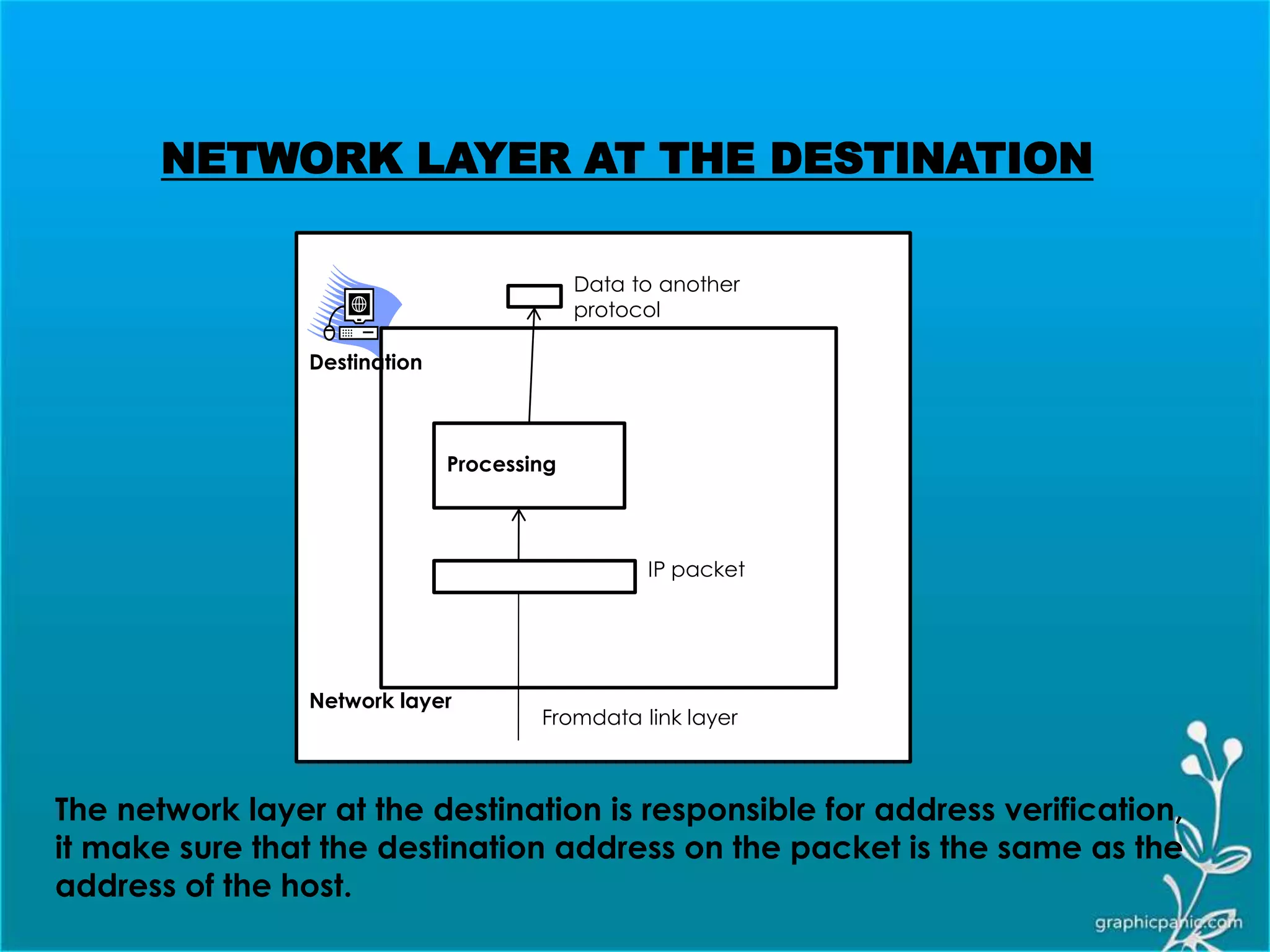
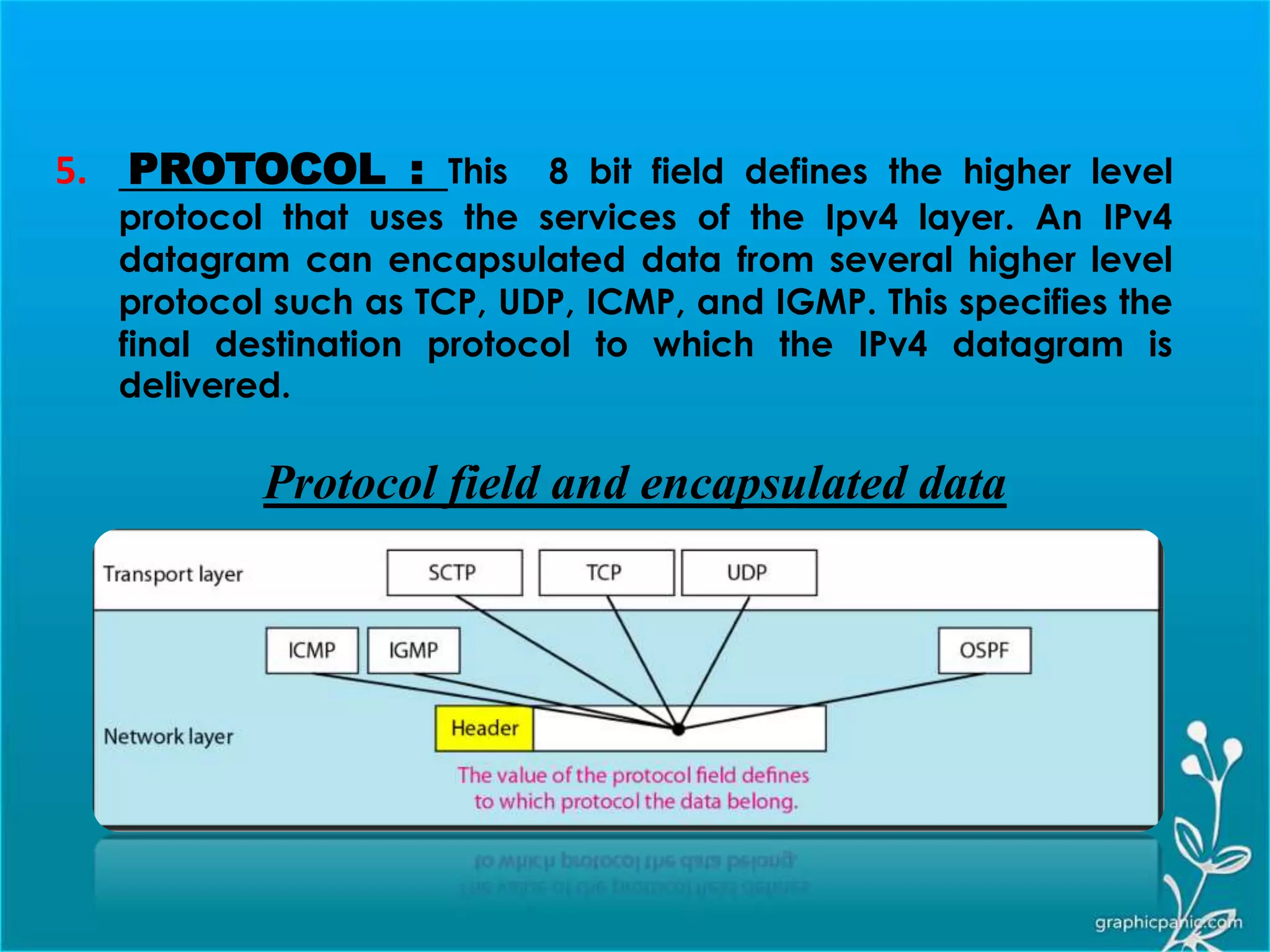
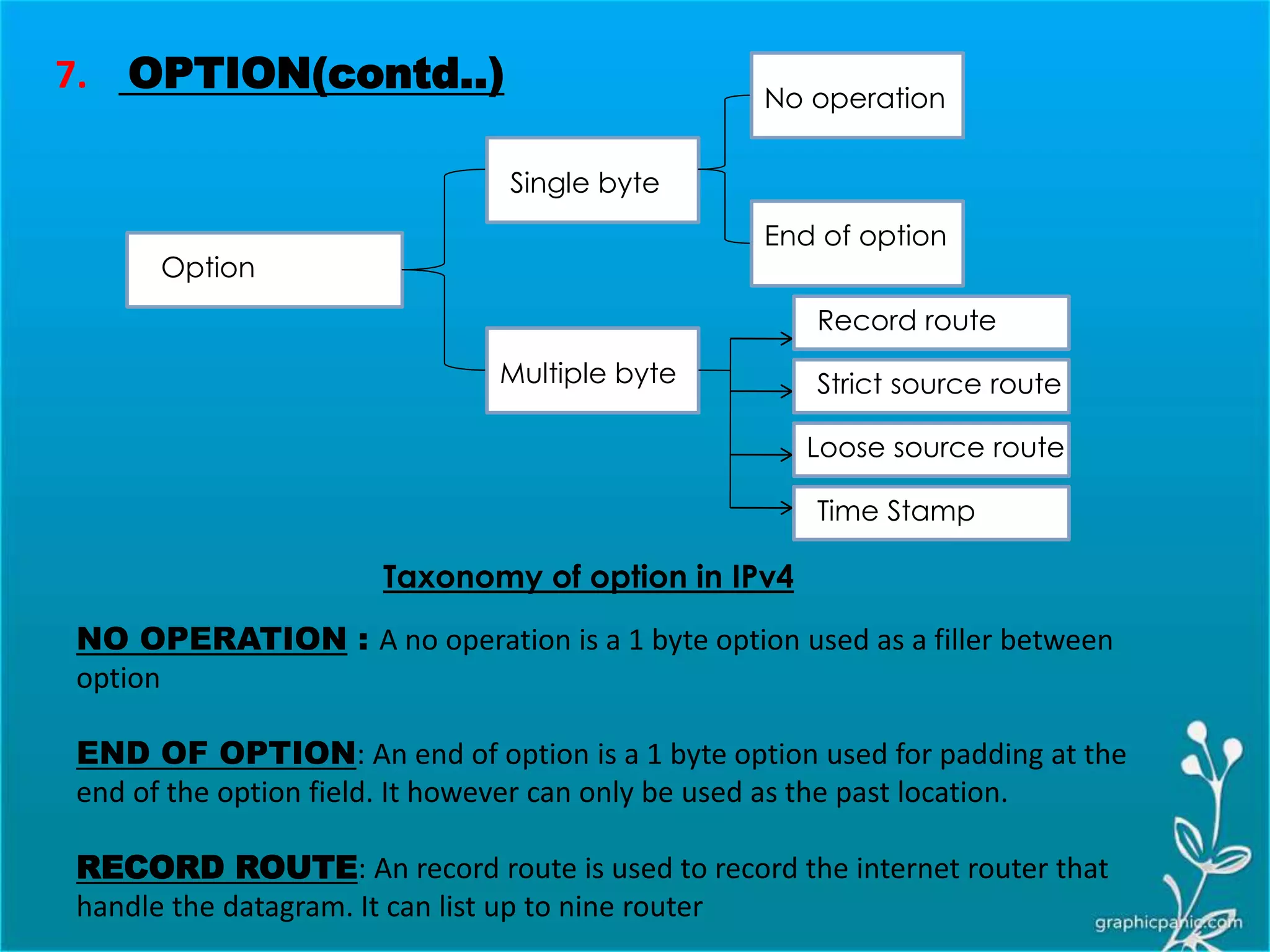
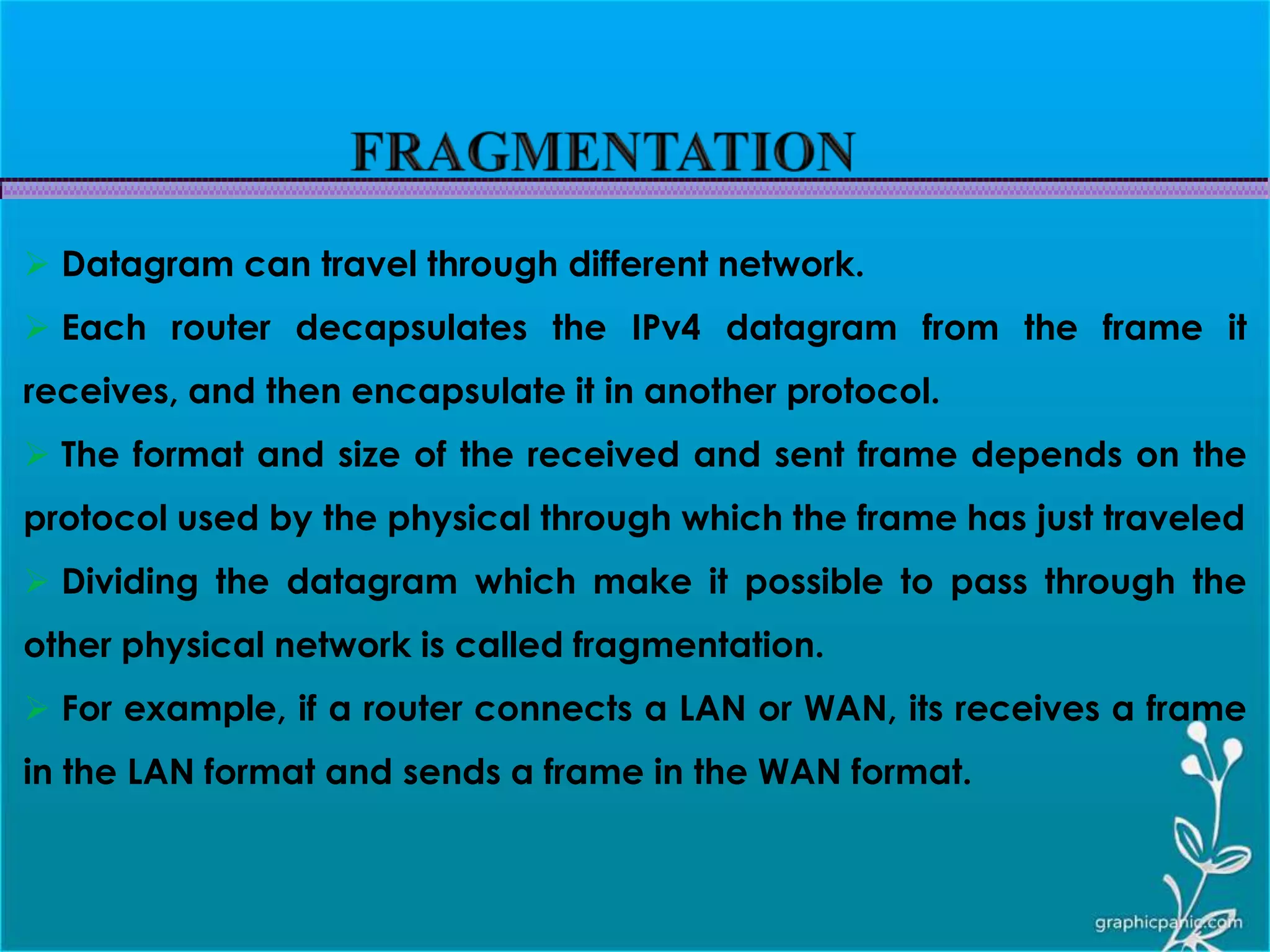
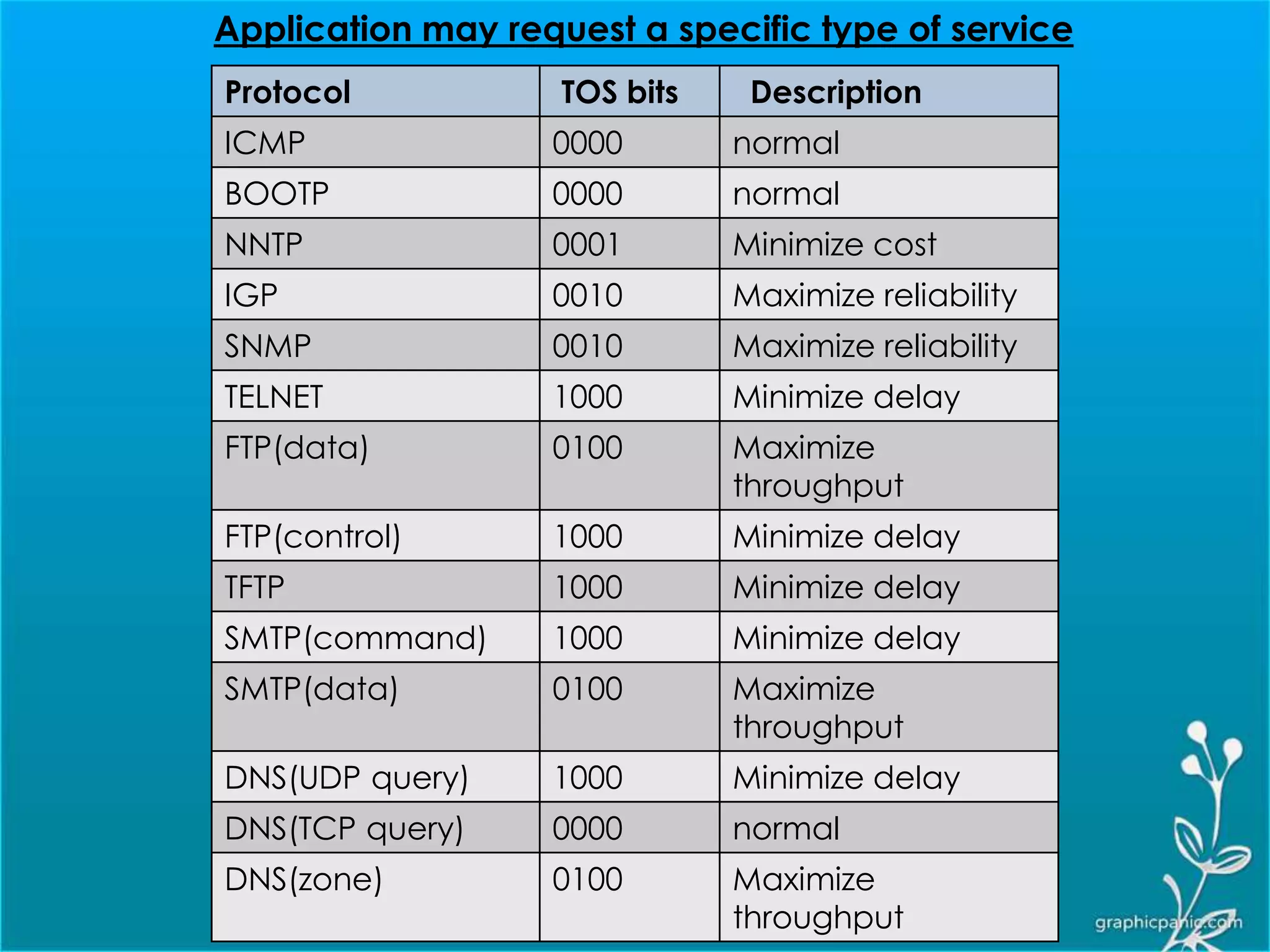
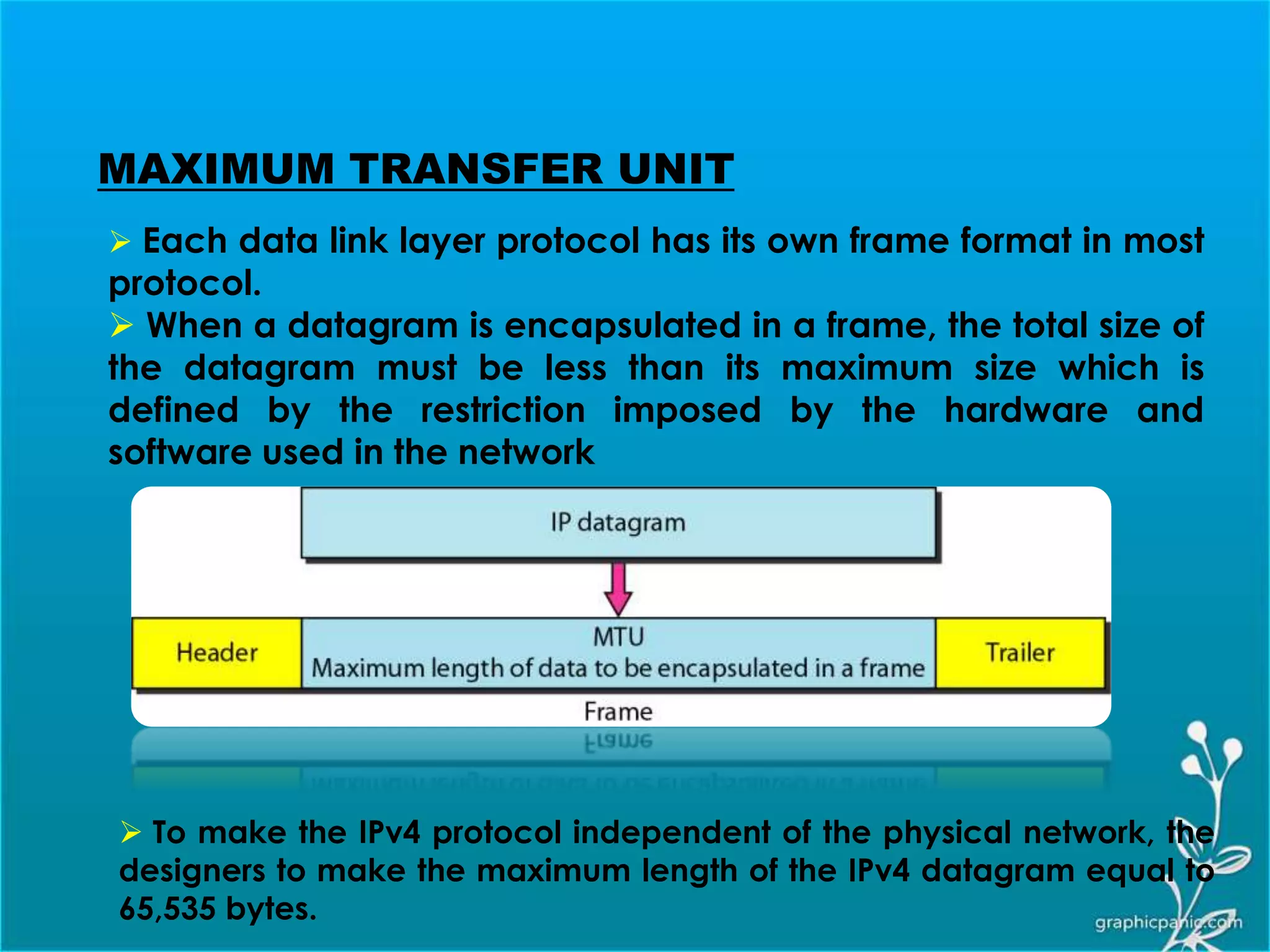
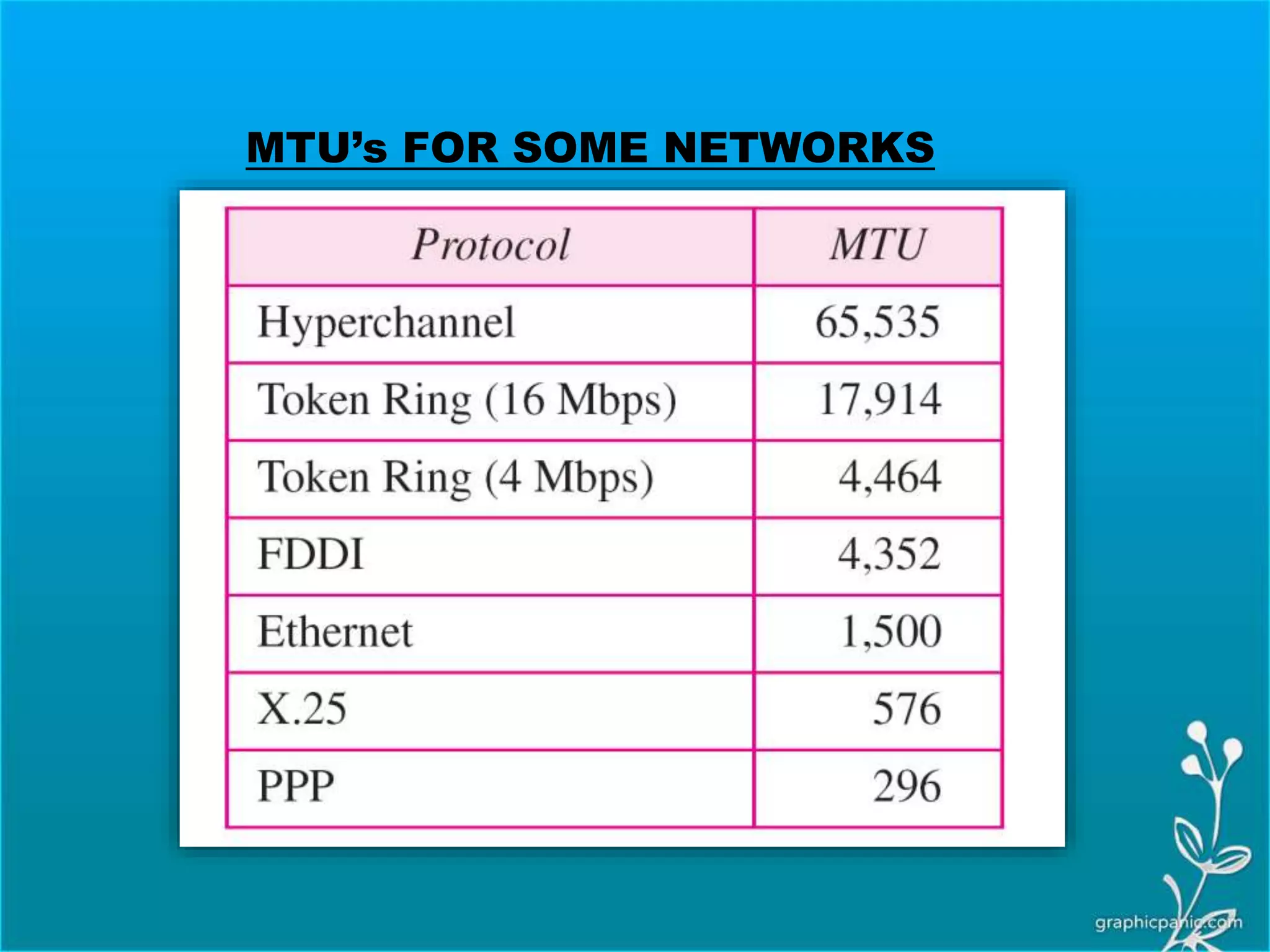
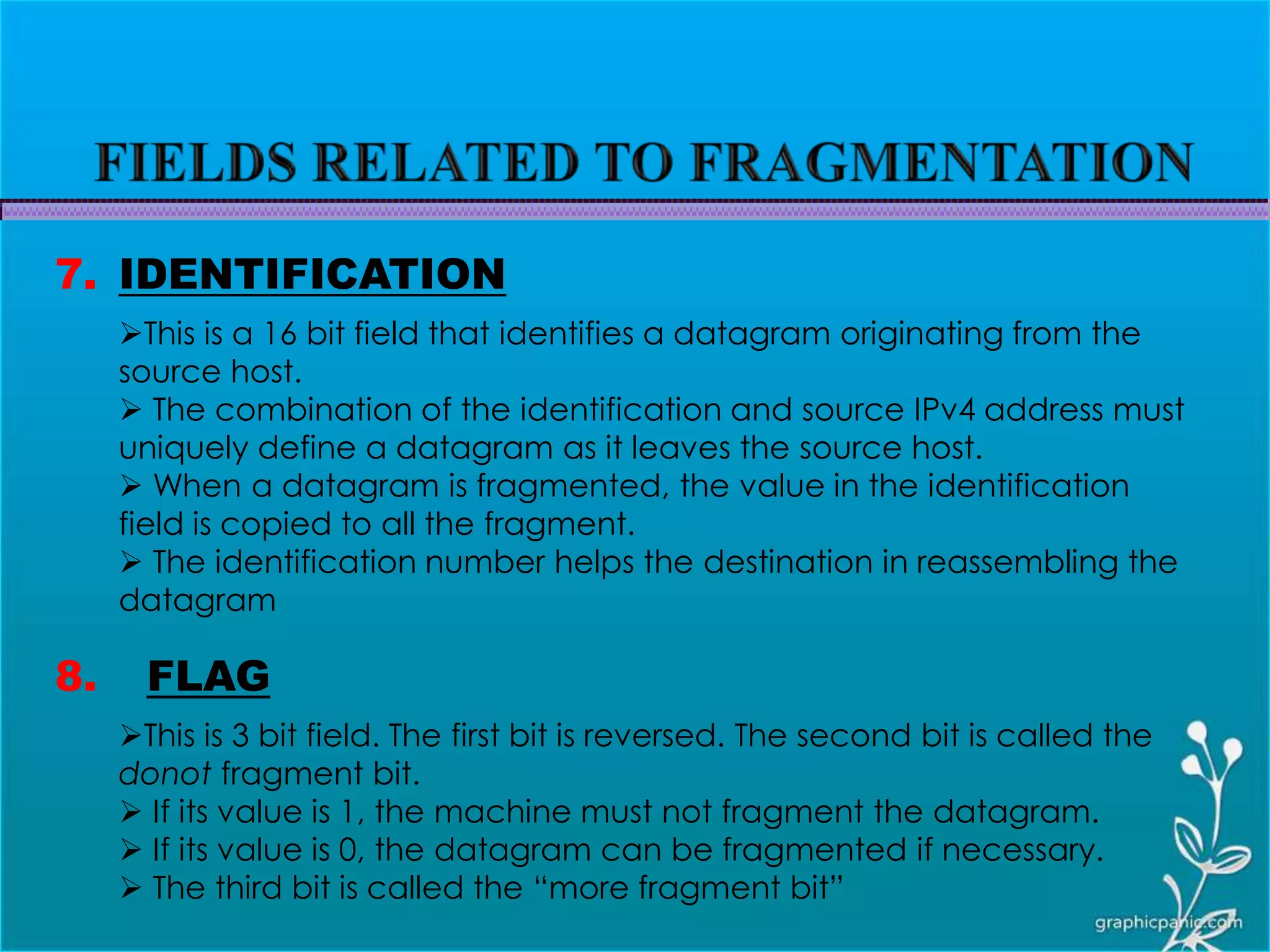
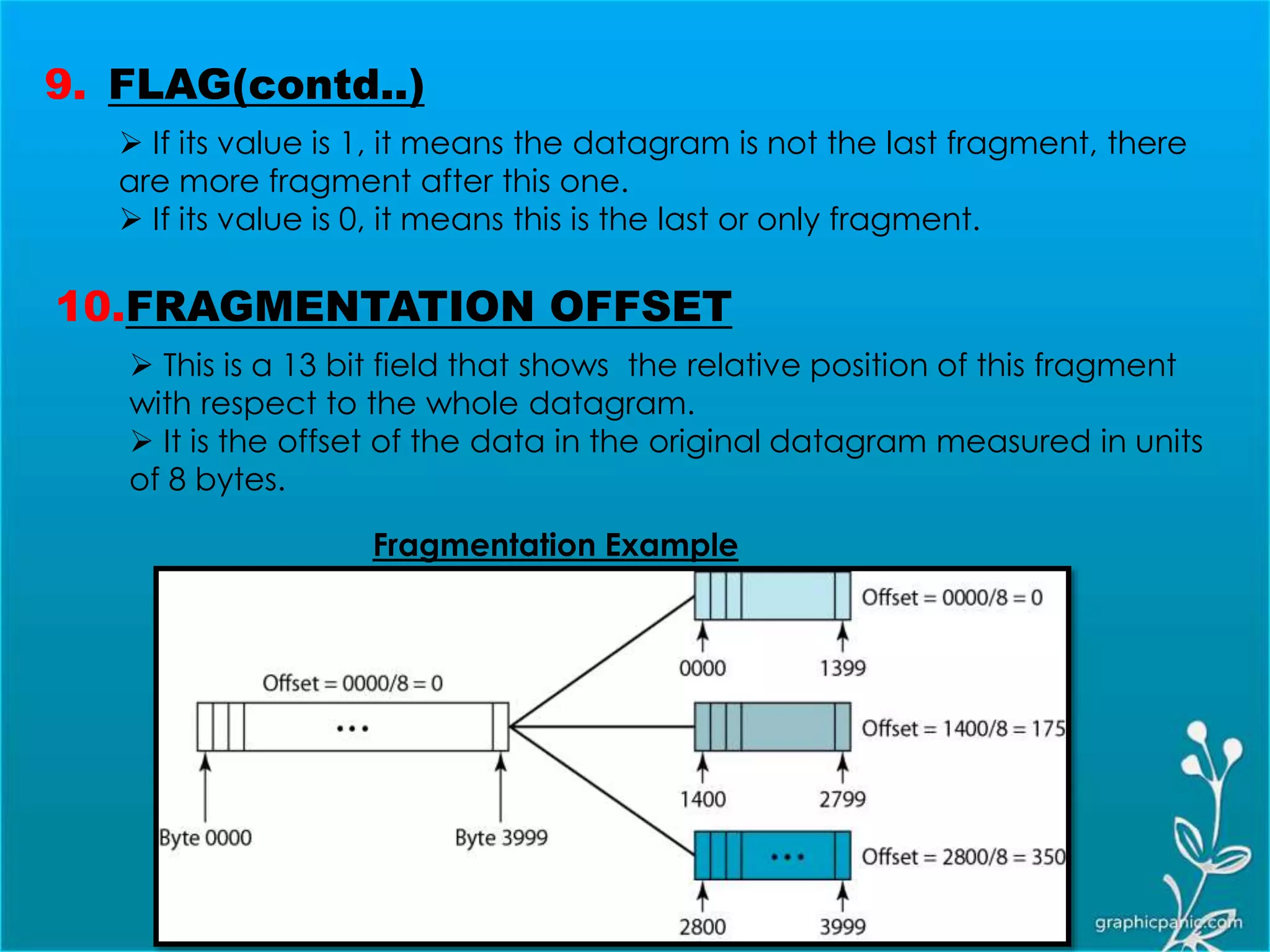
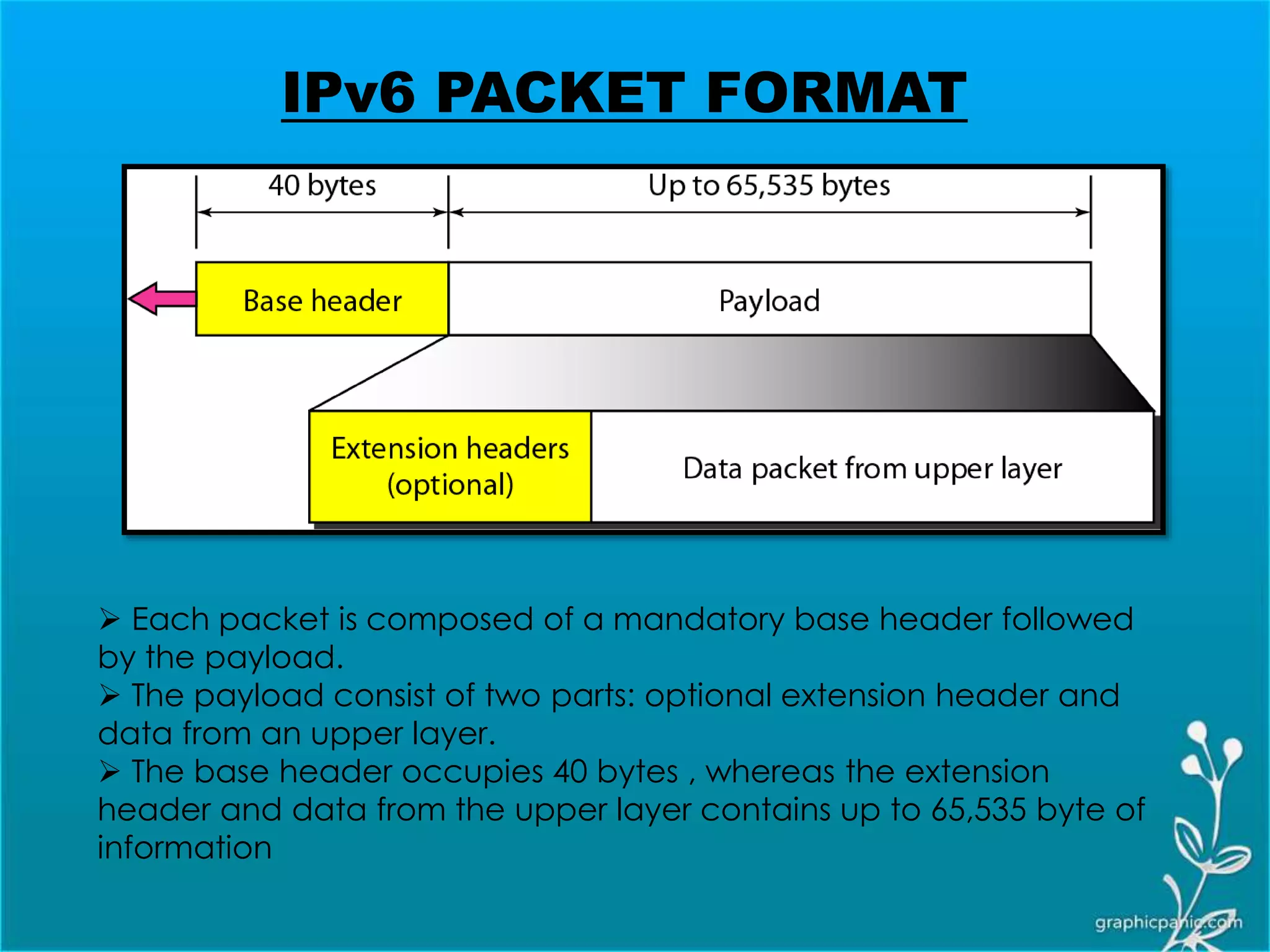
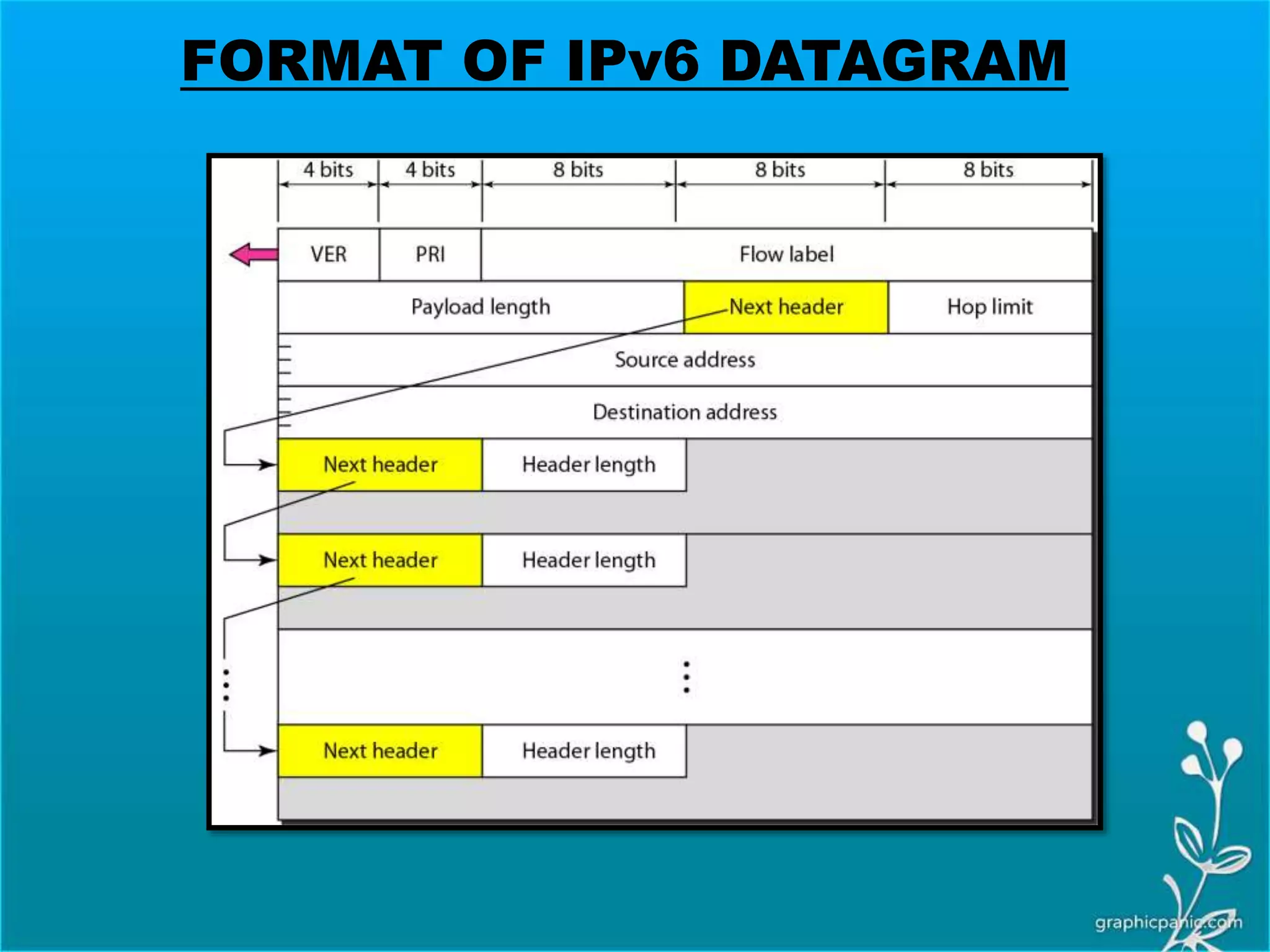
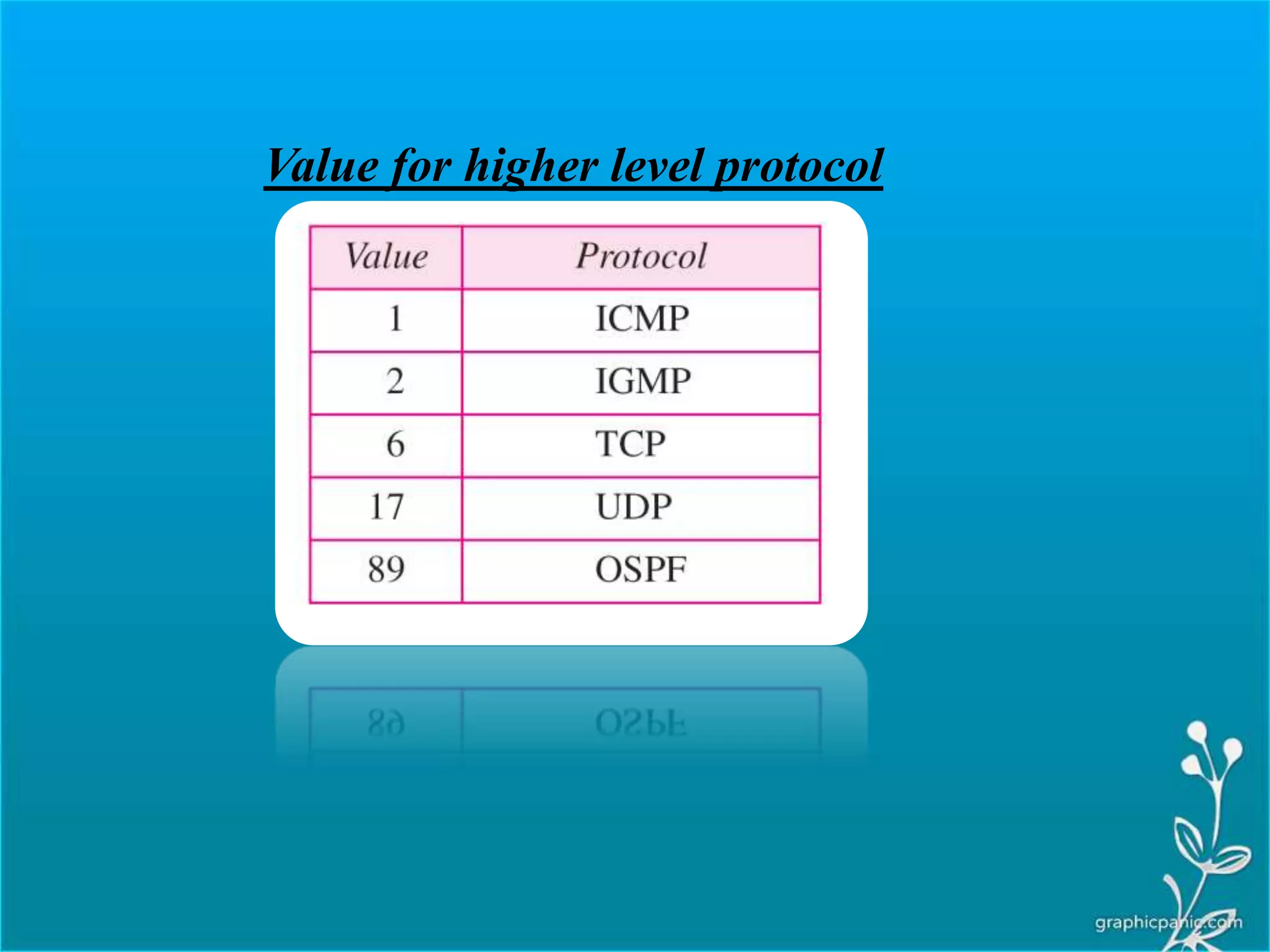
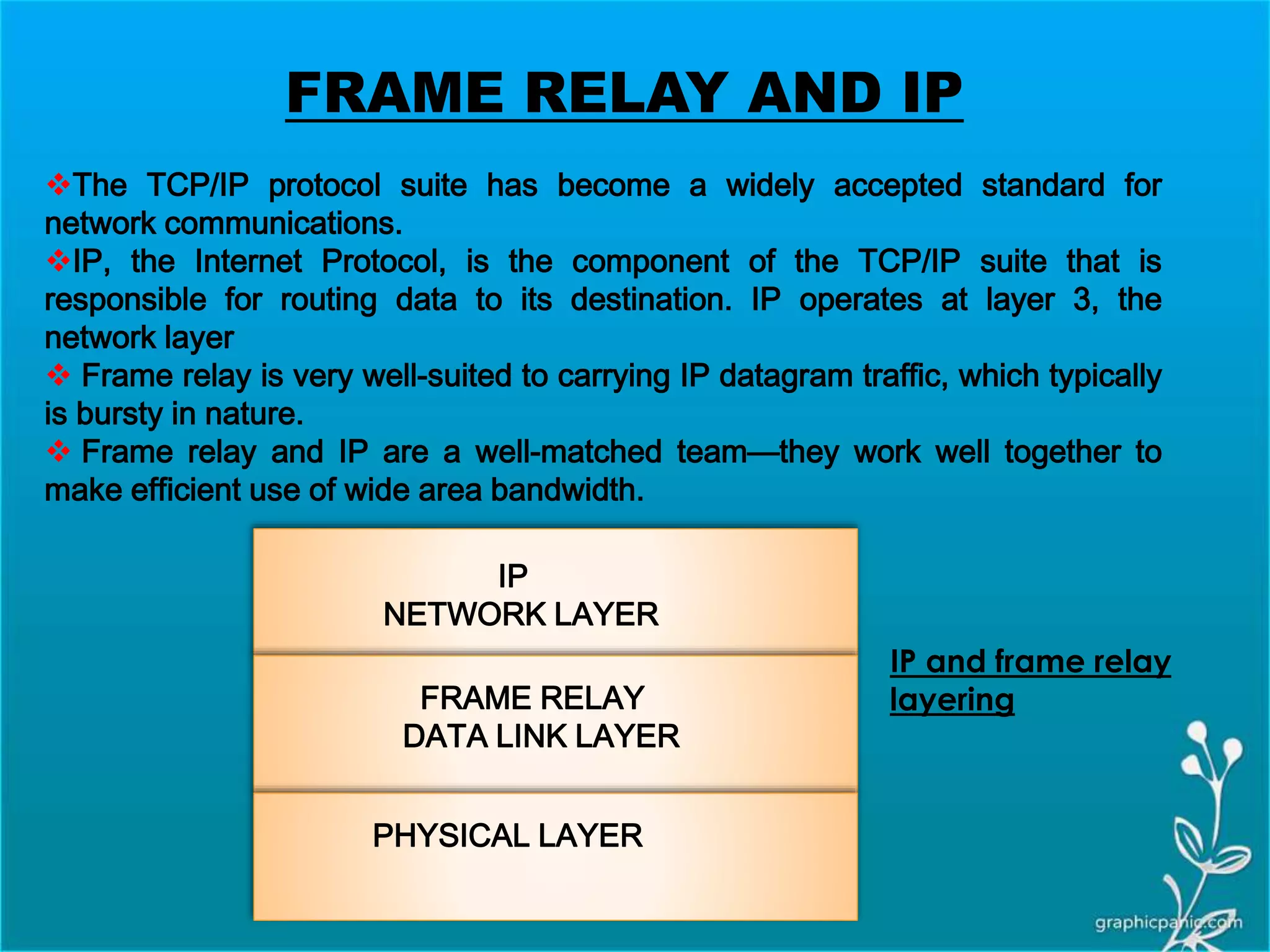
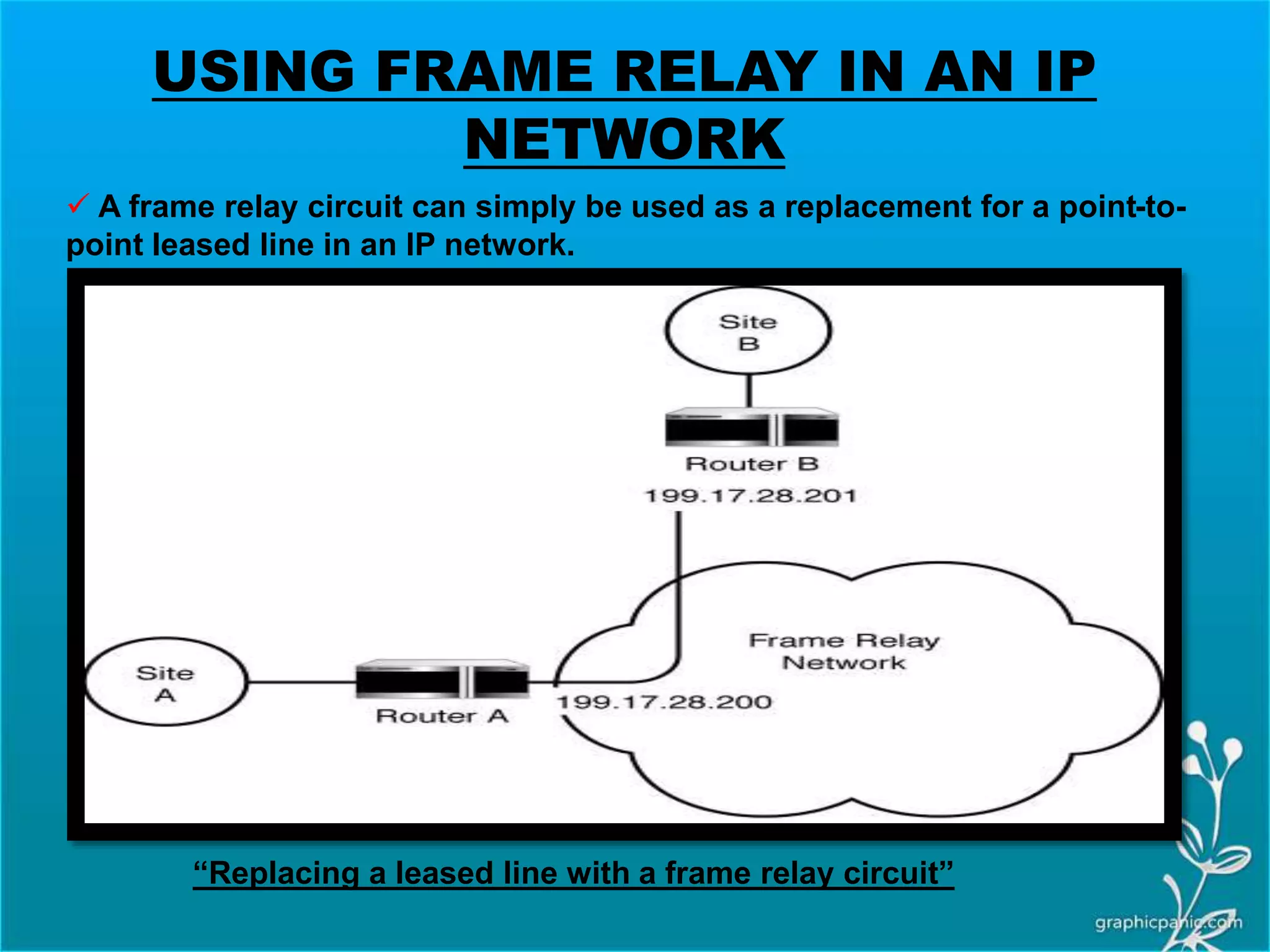
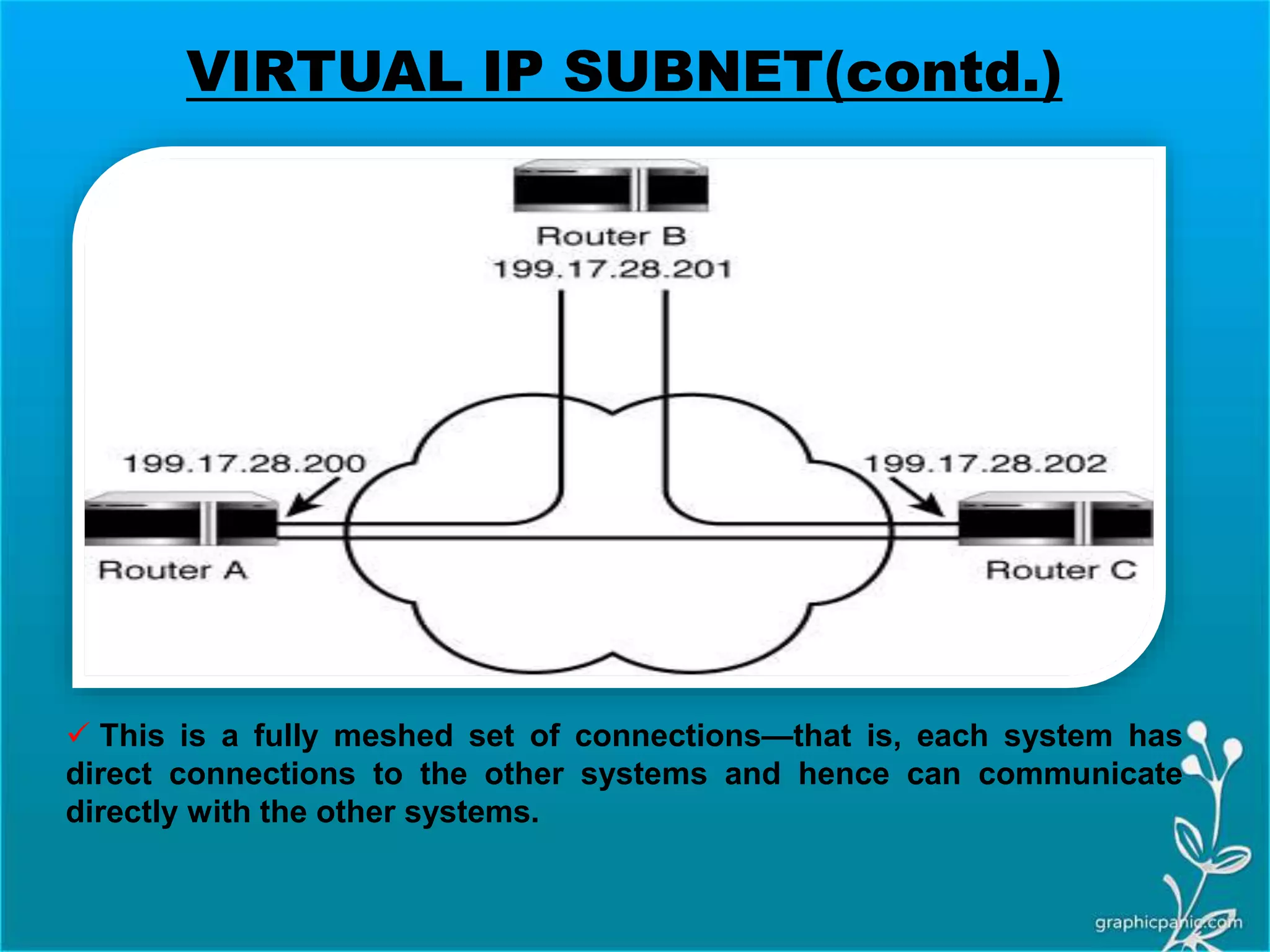
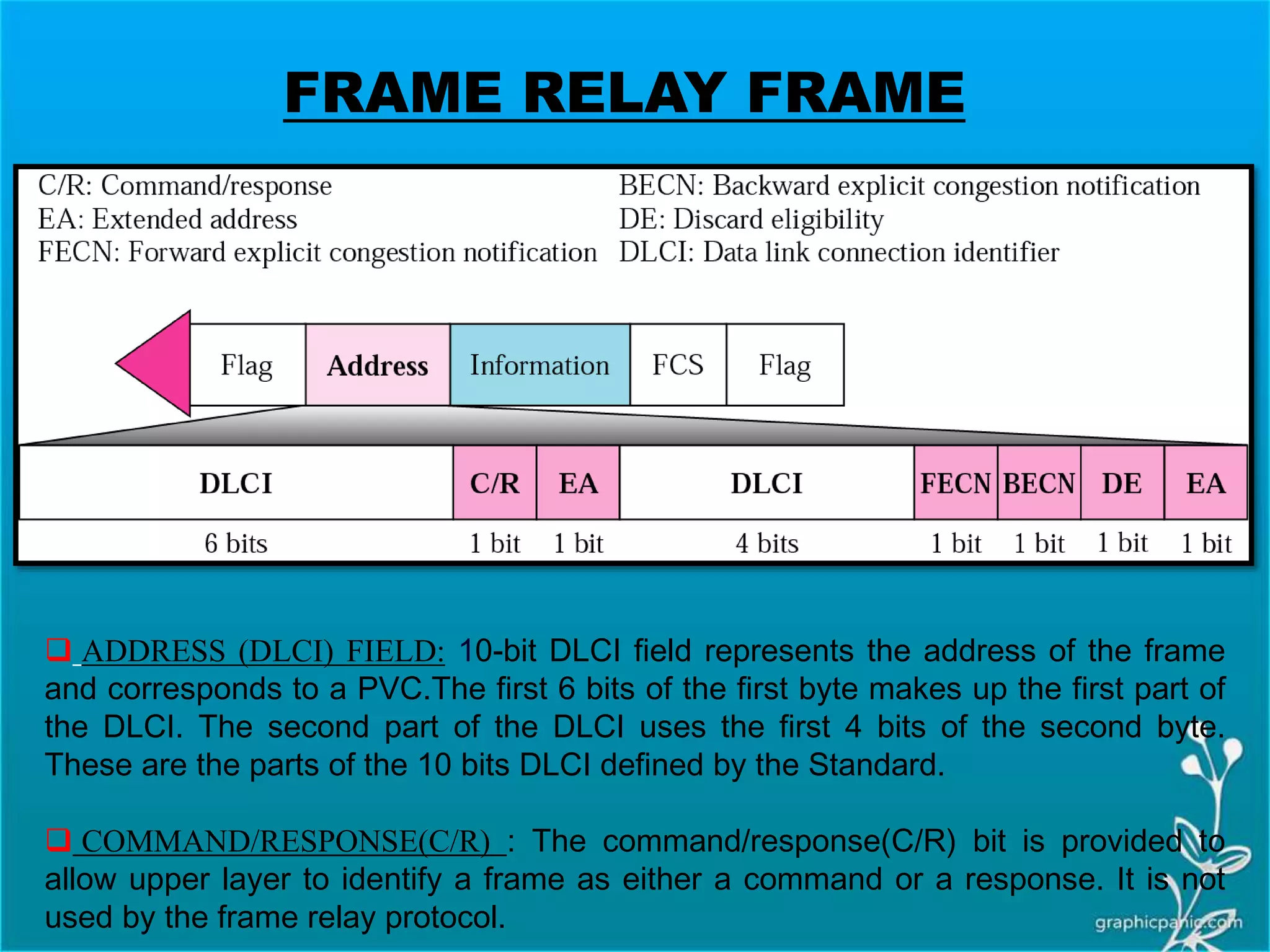
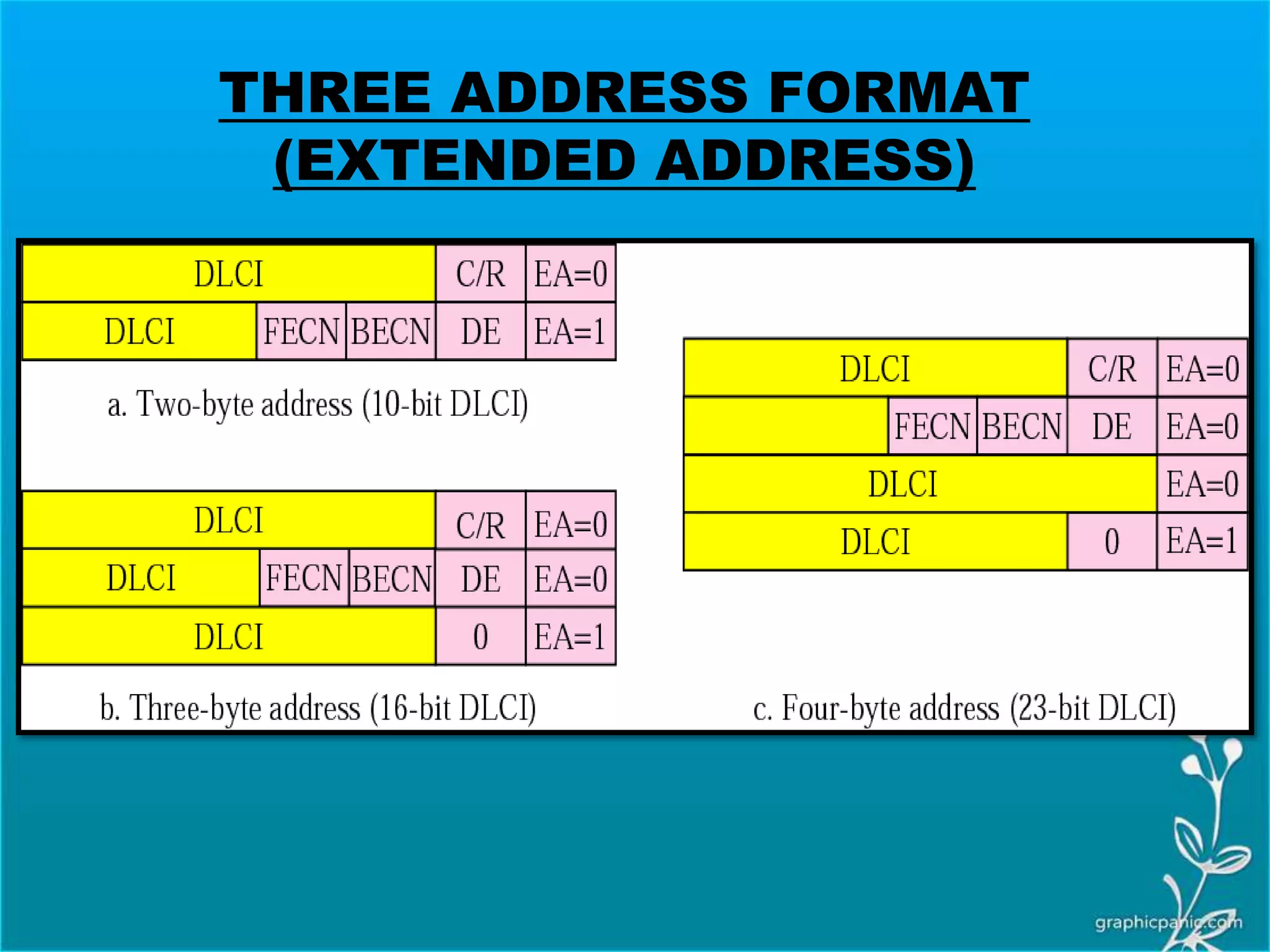
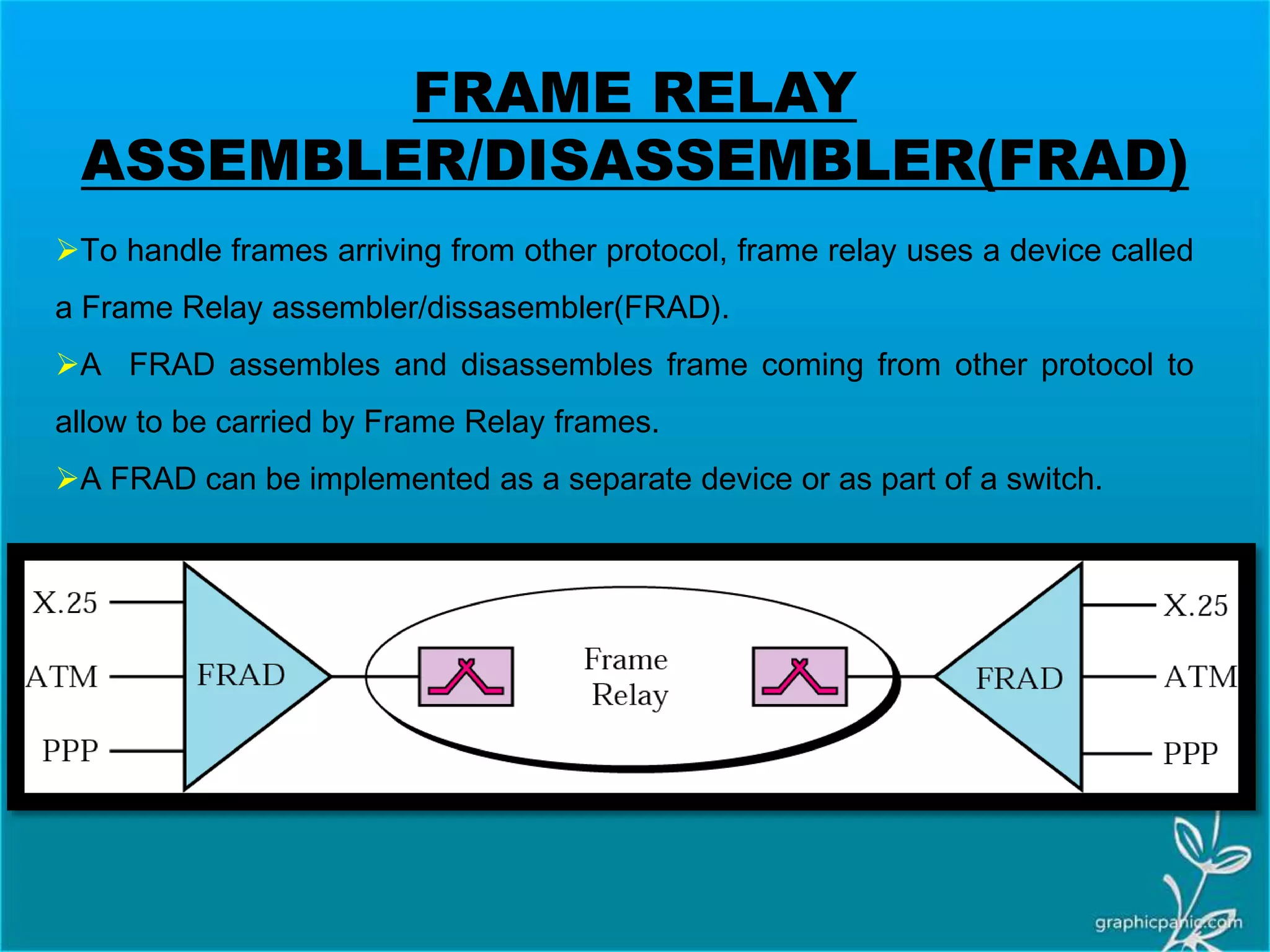
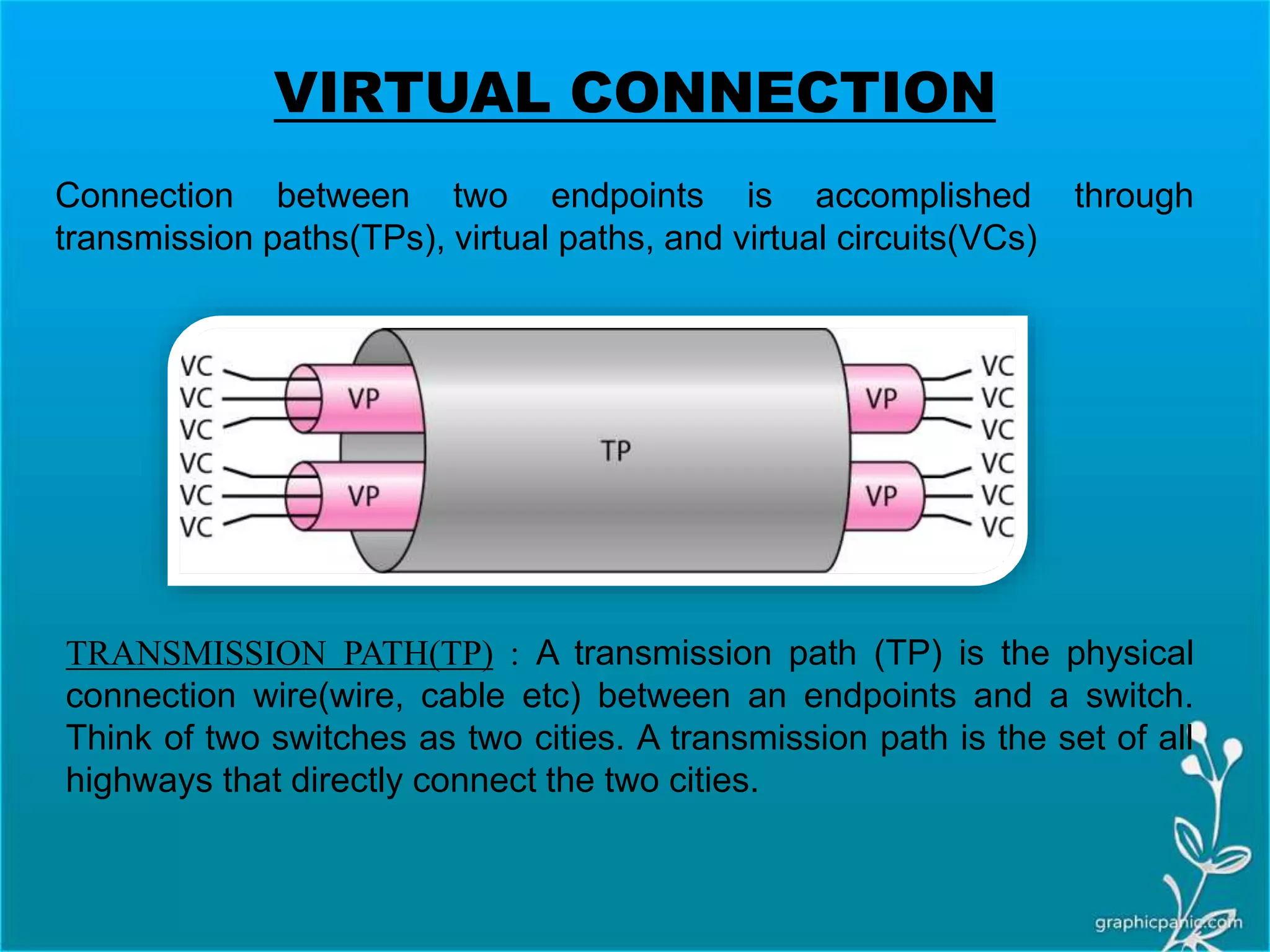
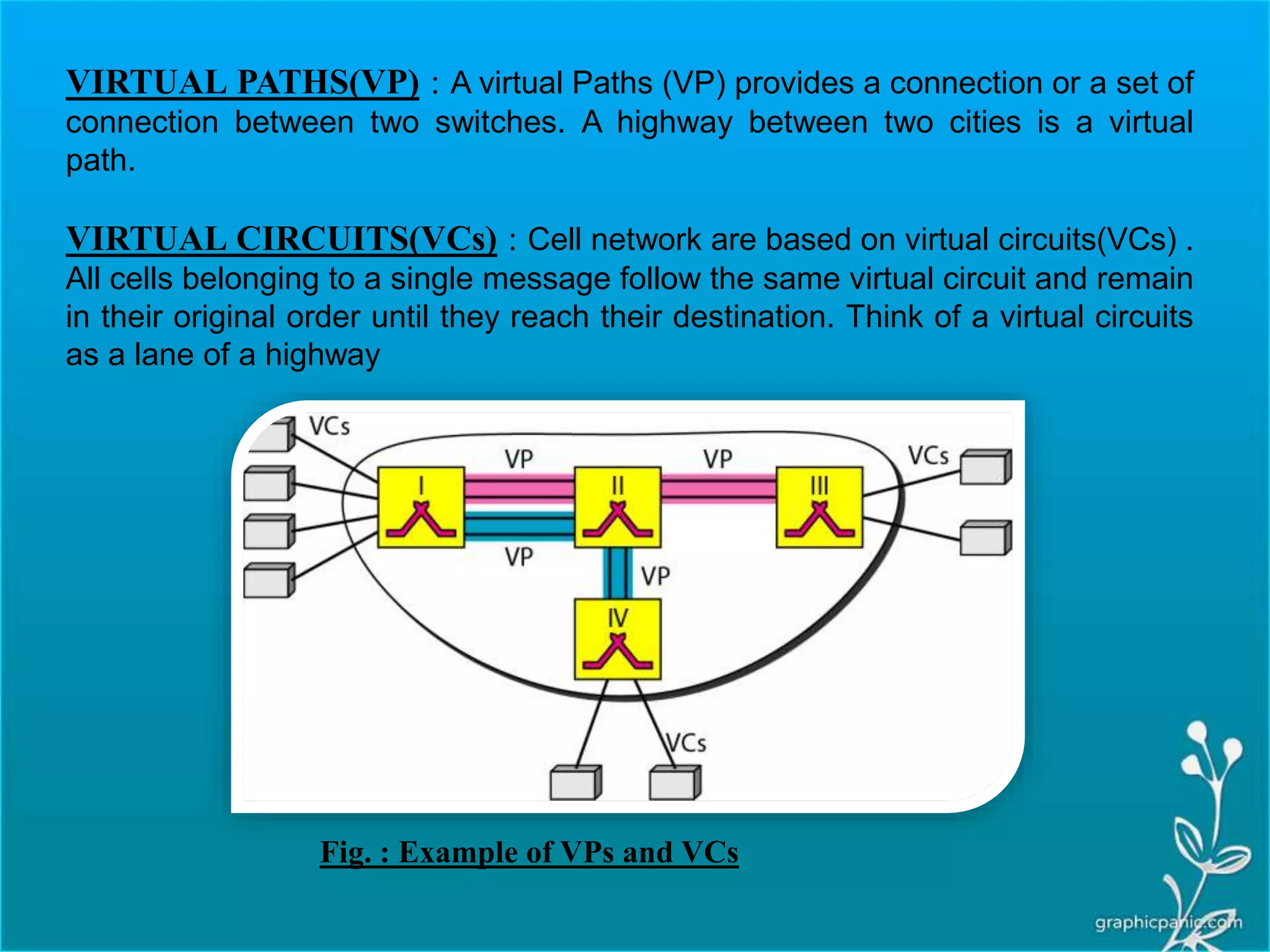
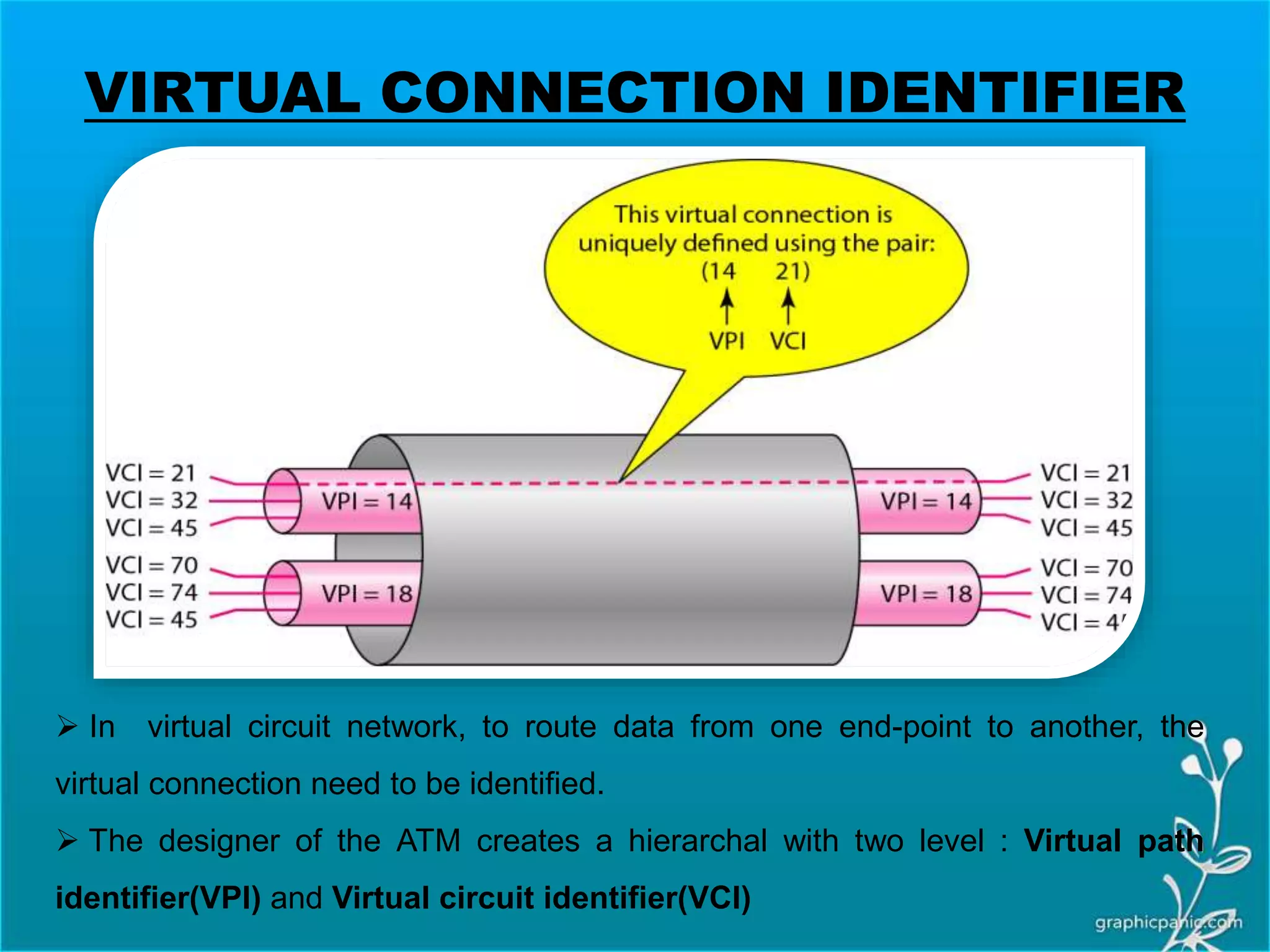
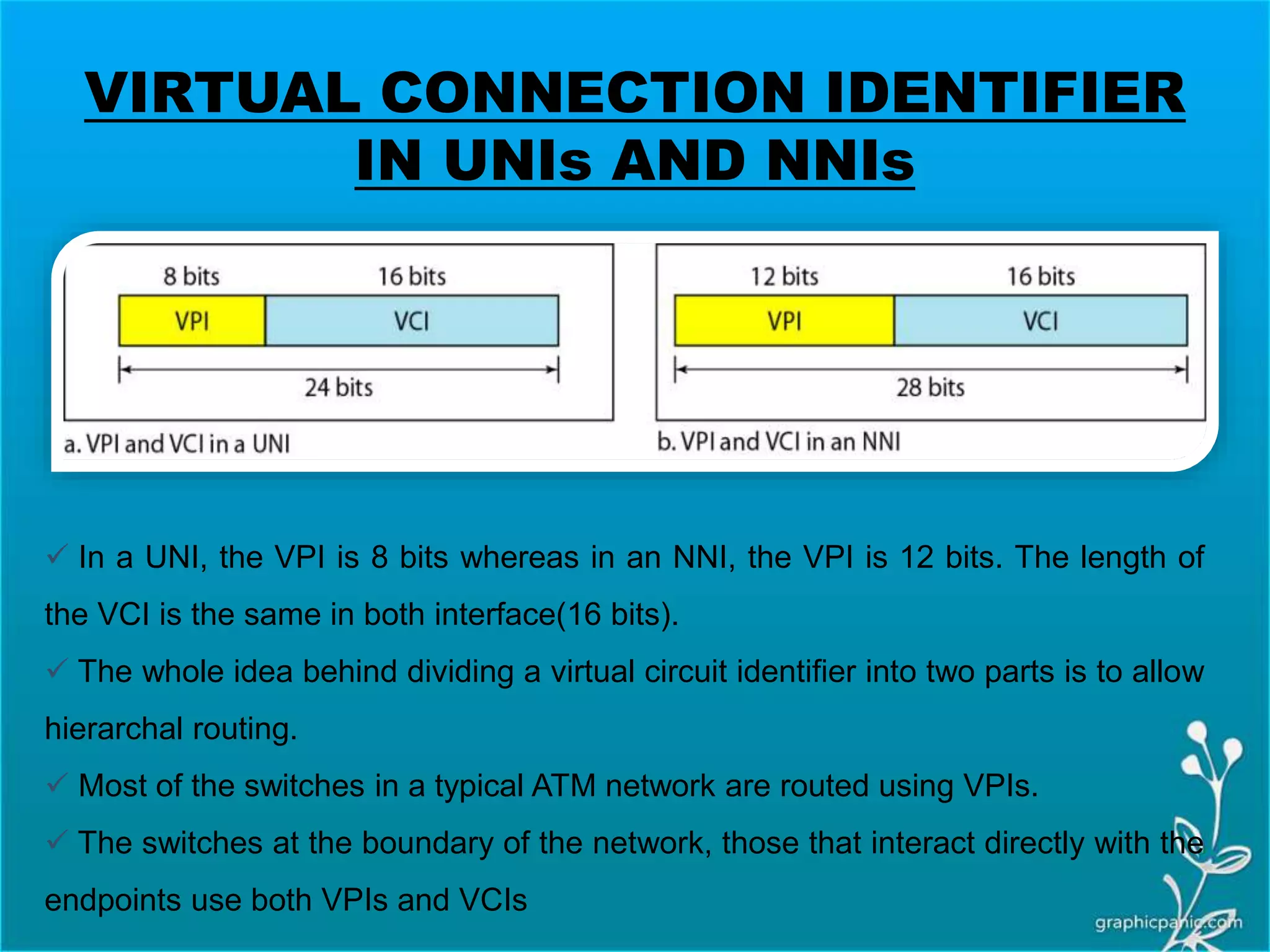
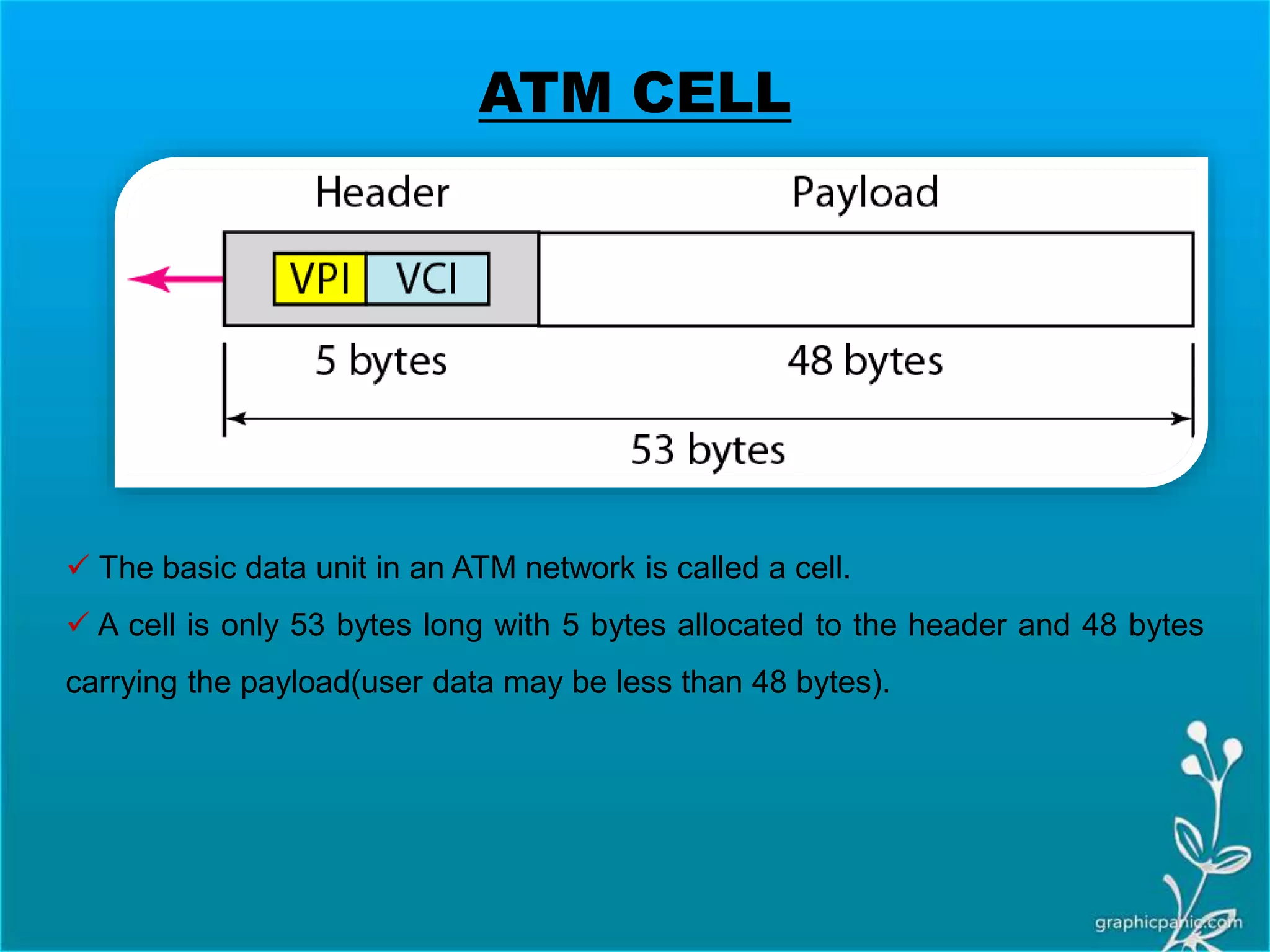
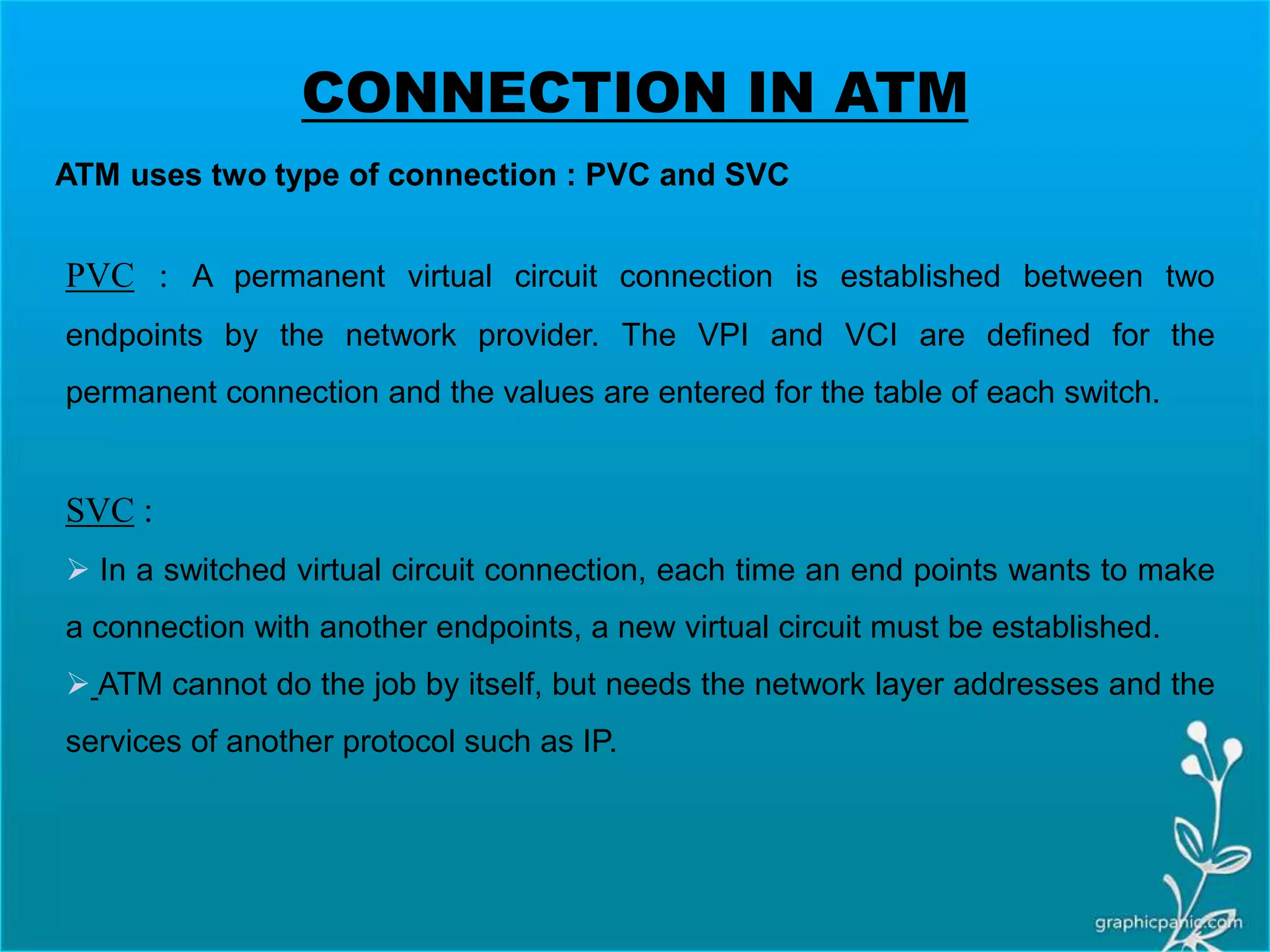
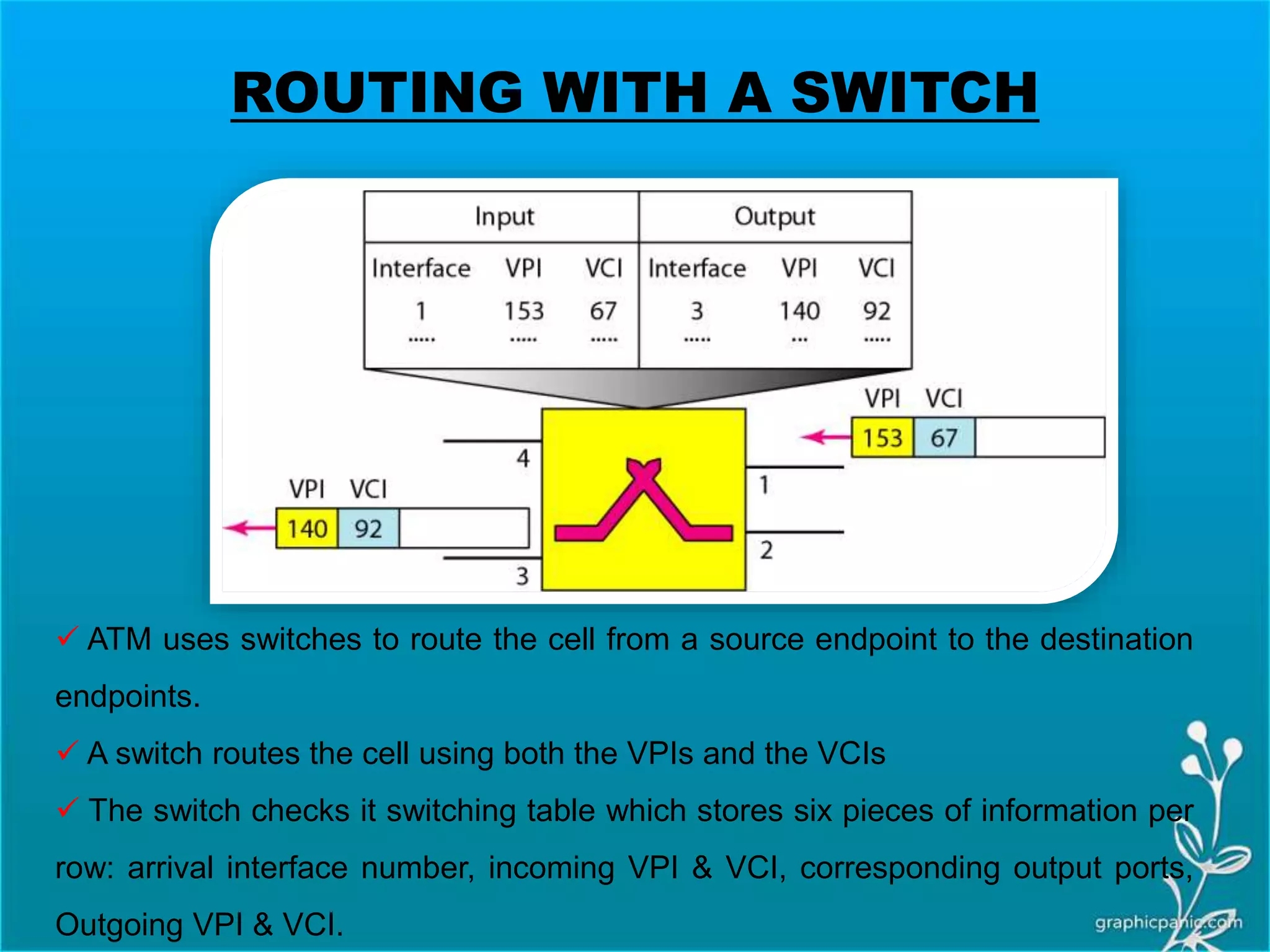
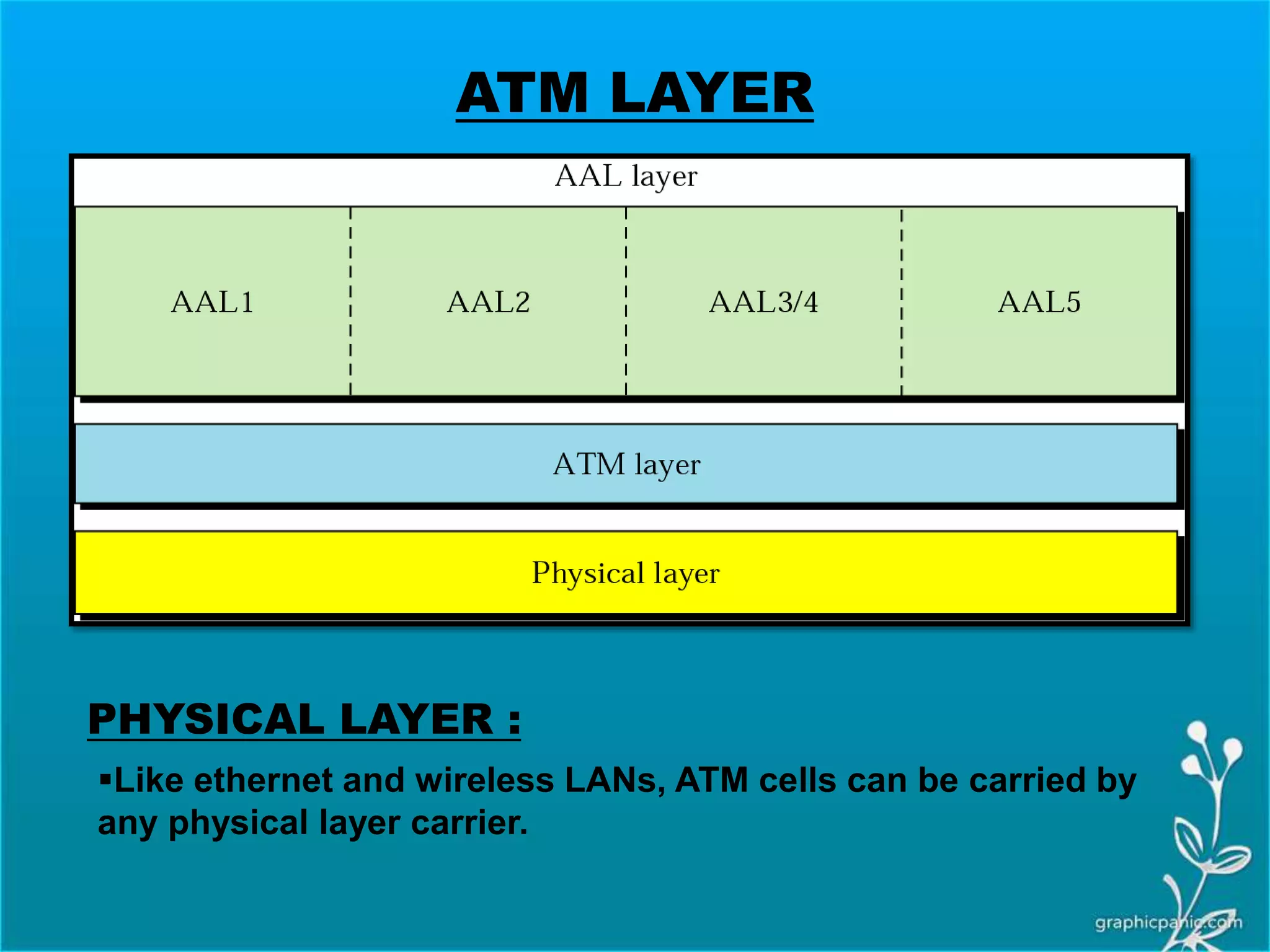
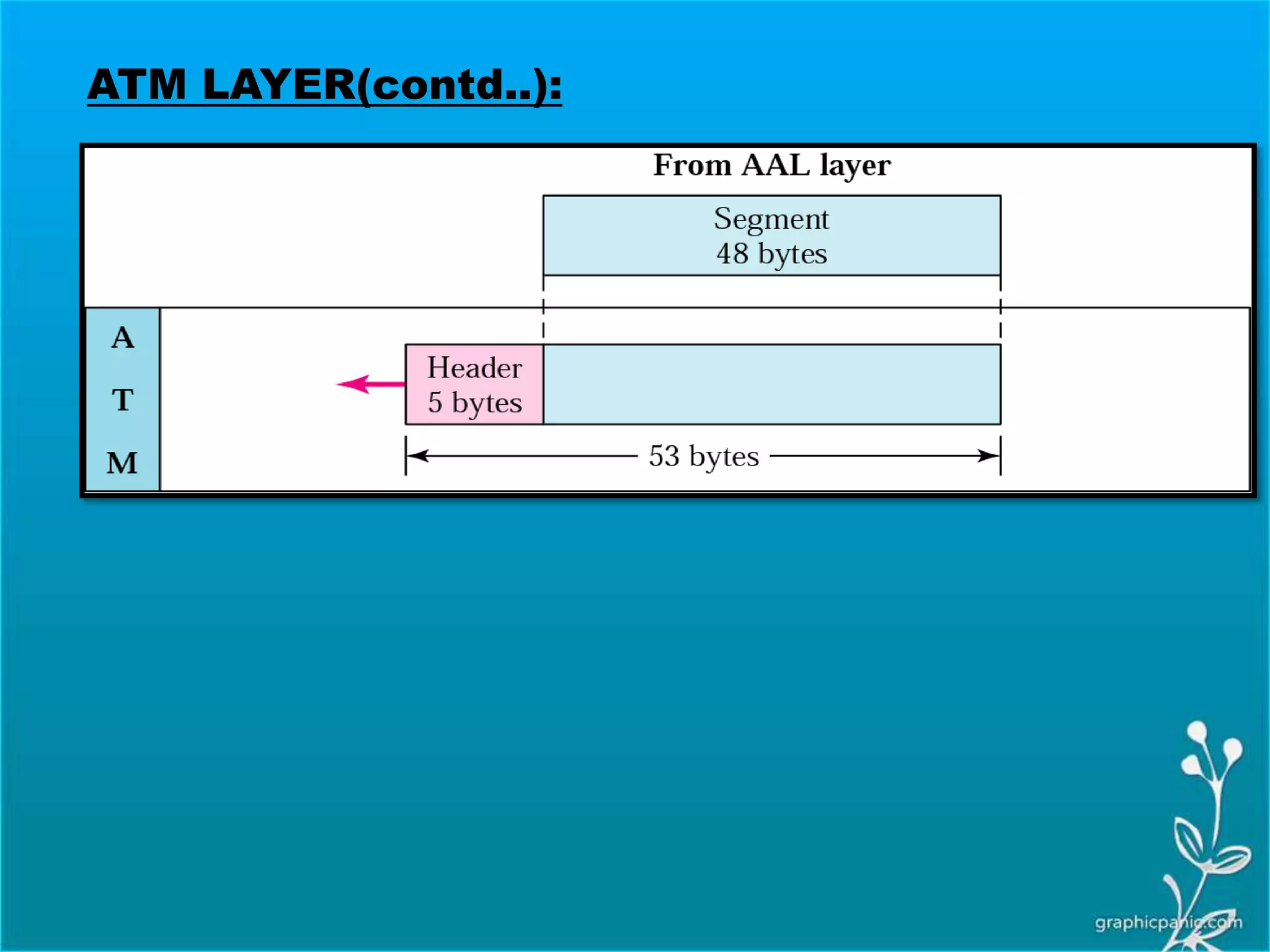
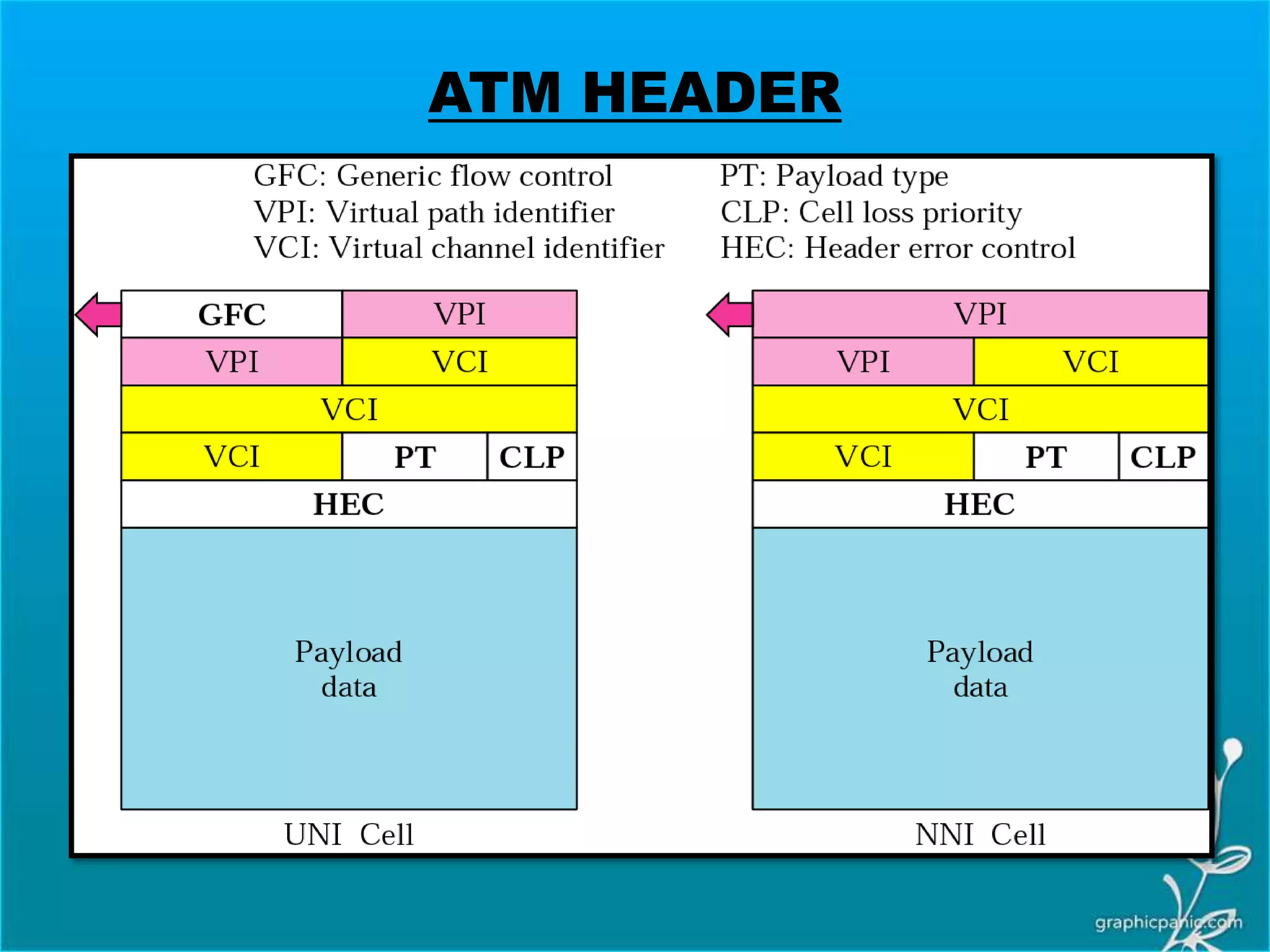
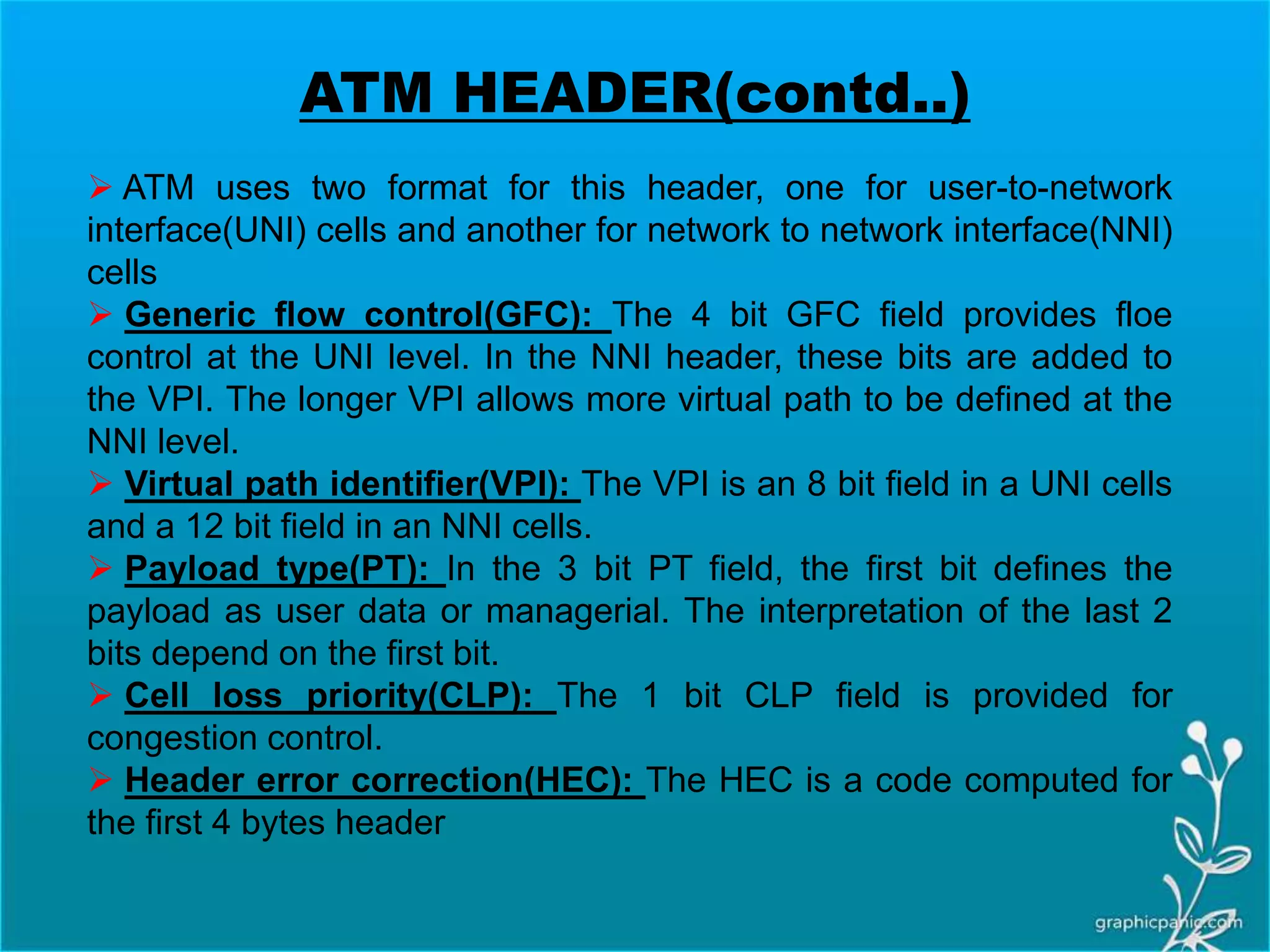
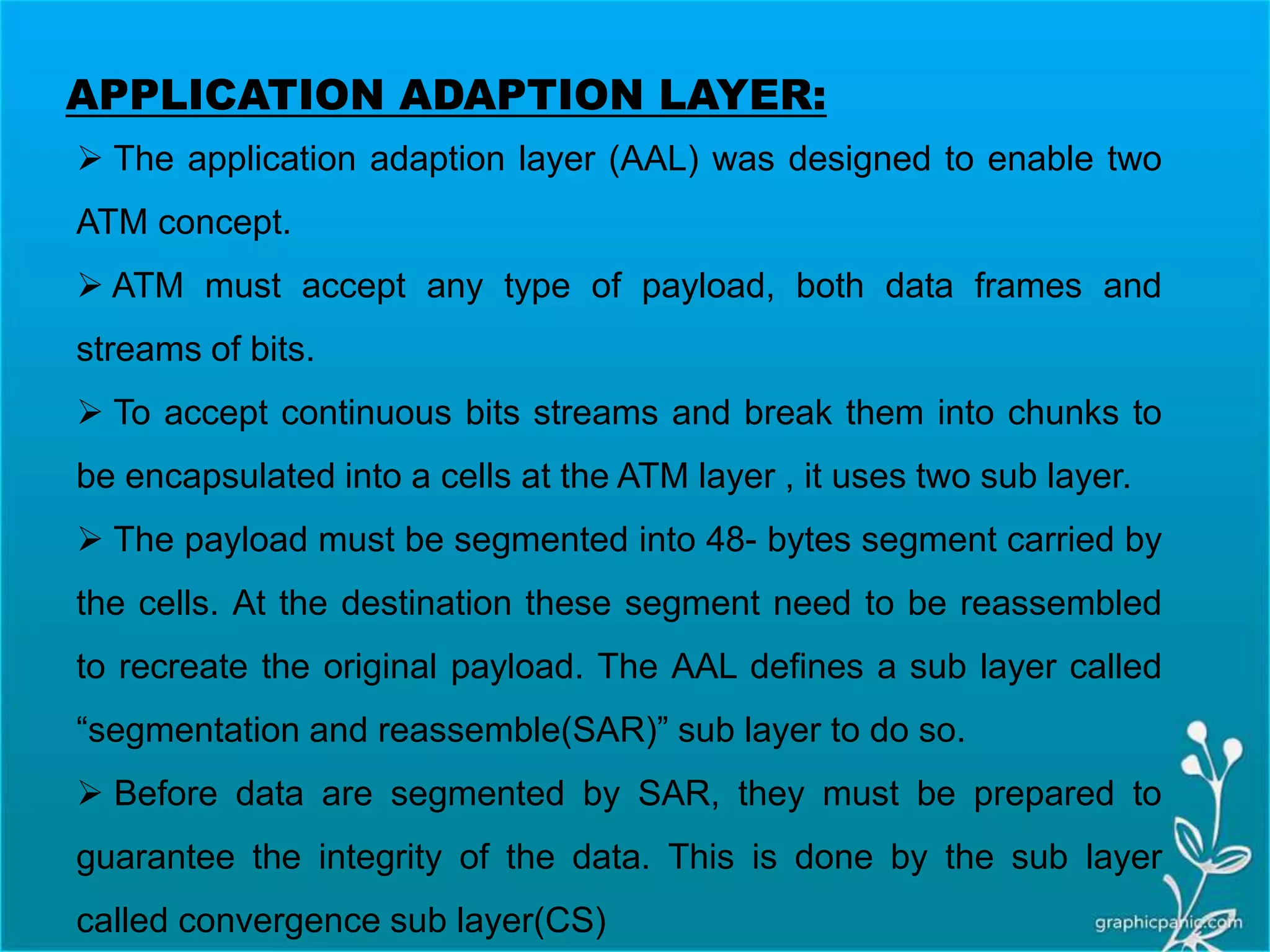
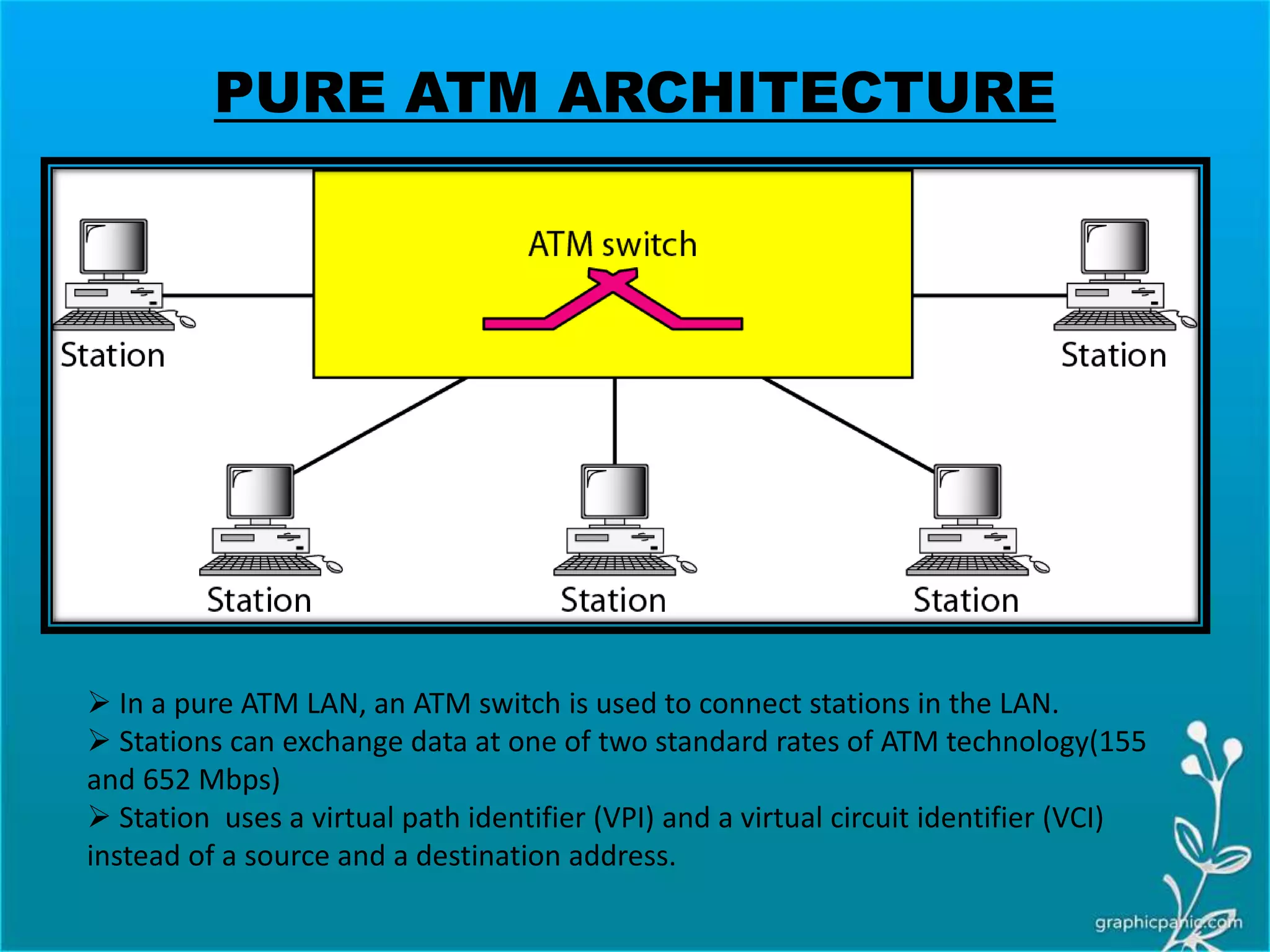
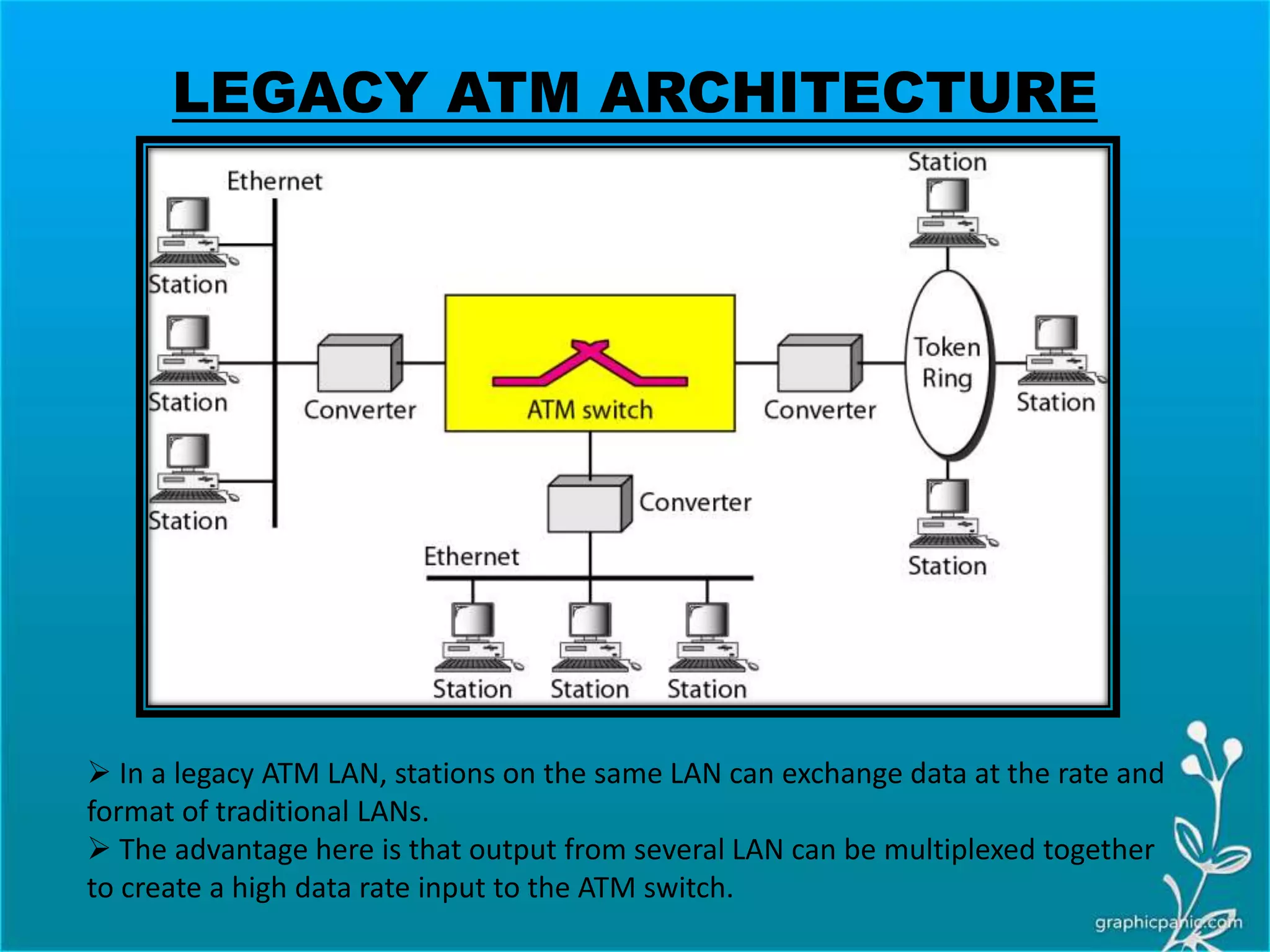
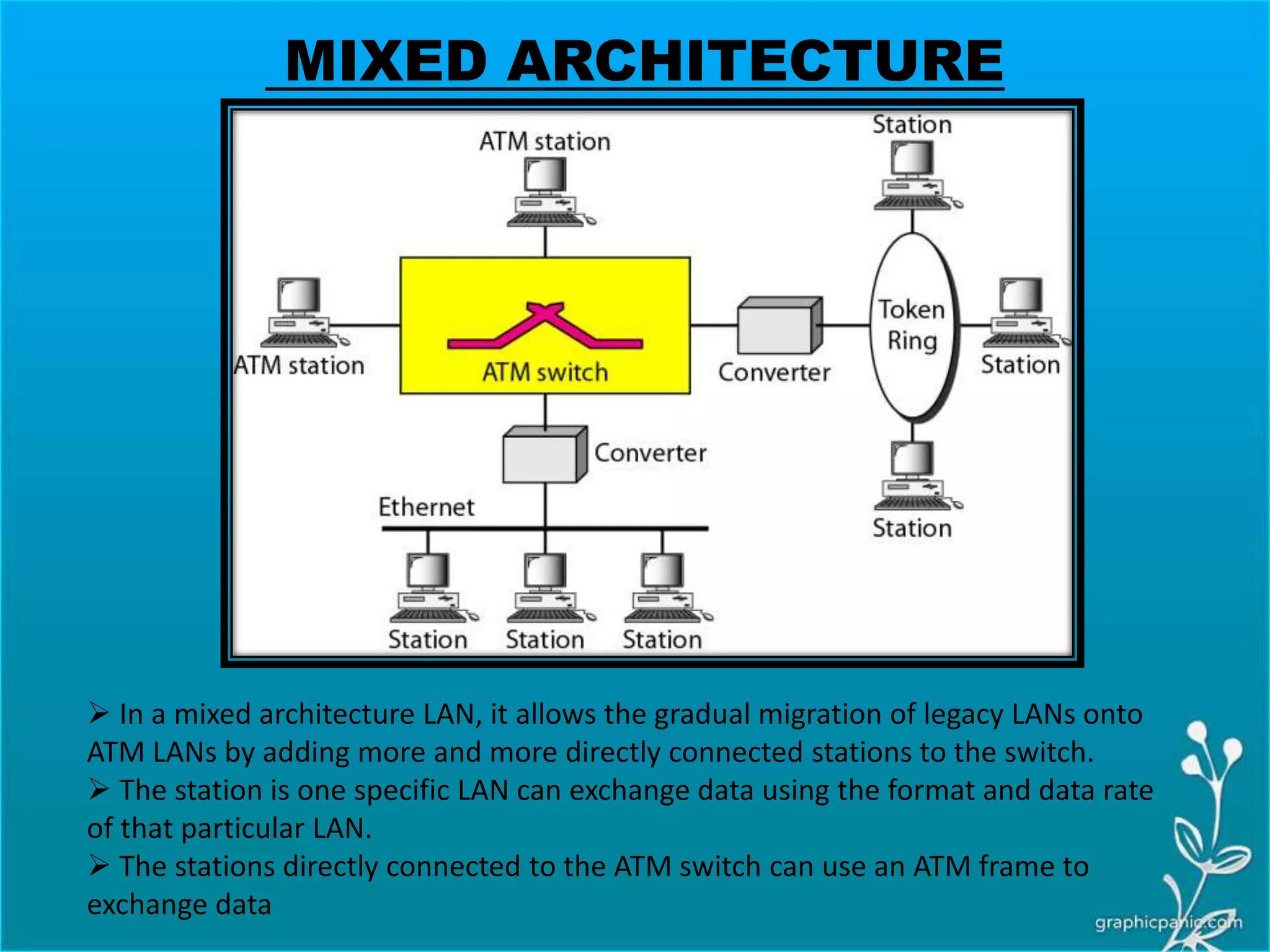
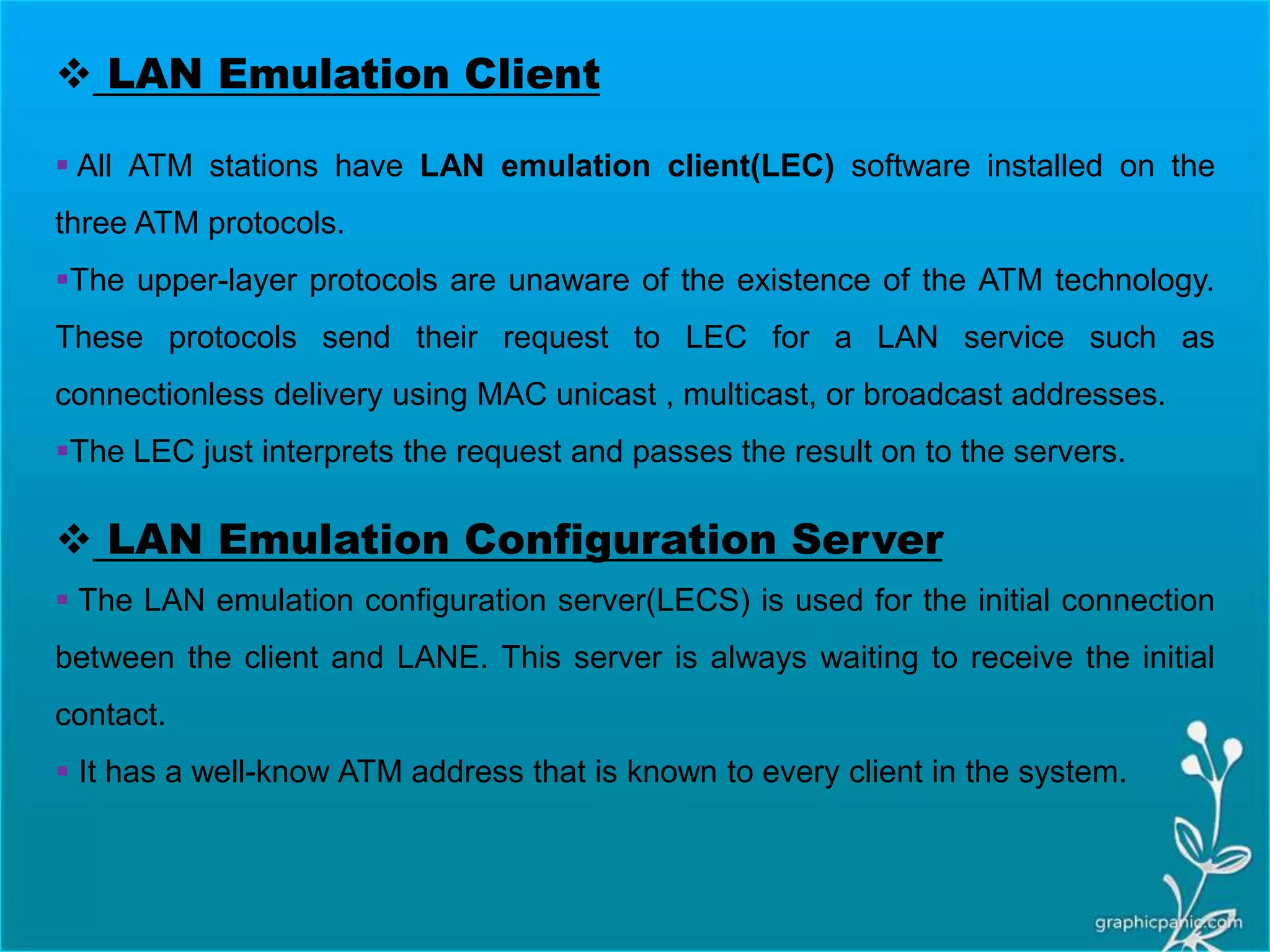
The network layer is responsible for delivering packets from source to destination. It must know the topology of the subnet and choose appropriate paths. When sources and destinations are in different networks, the network layer must deal with these differences. The network layer uses logical addressing that is independent of the underlying physical network. Routing ensures packets are delivered through routers and switches from source to destination across interconnected networks.