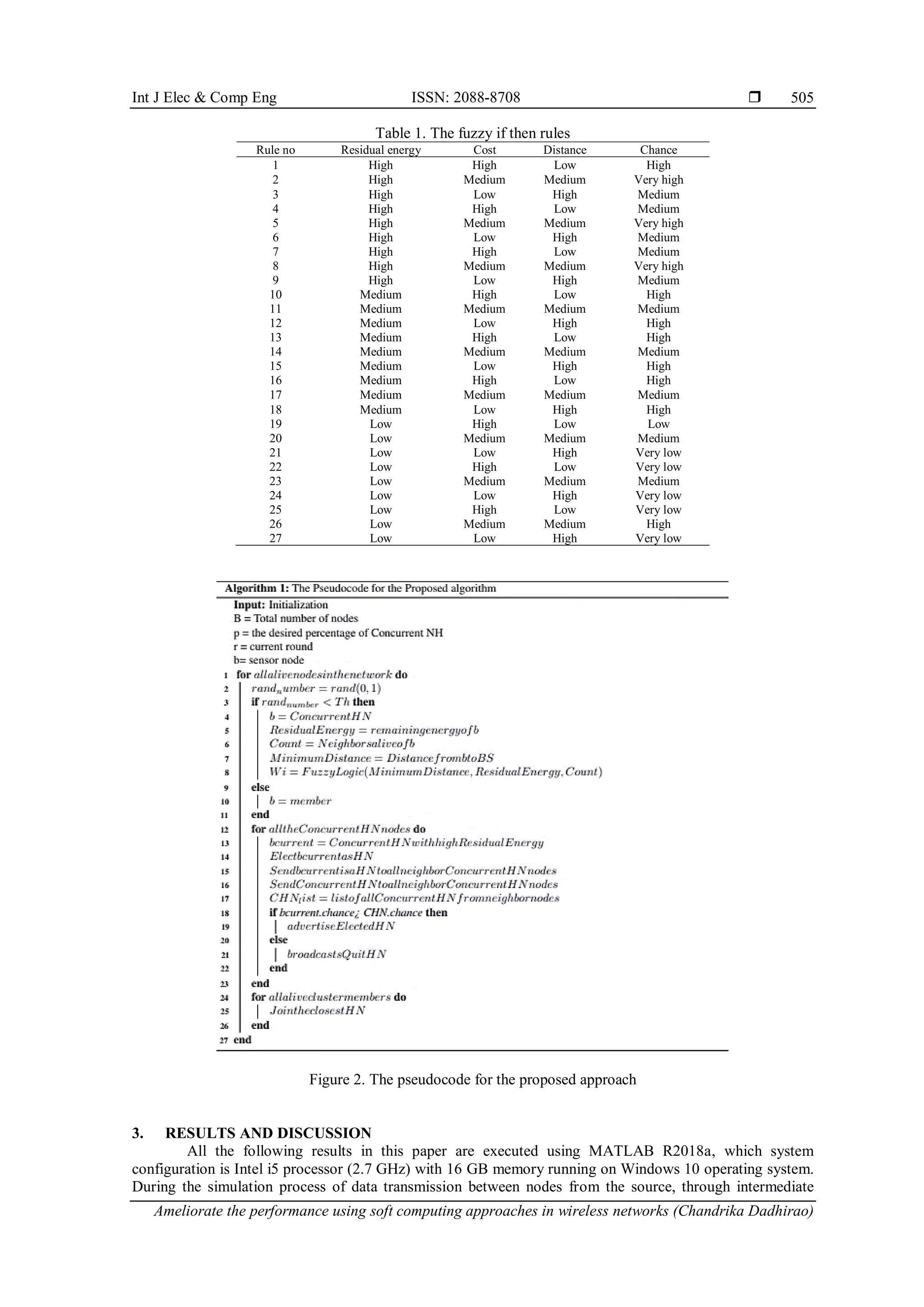
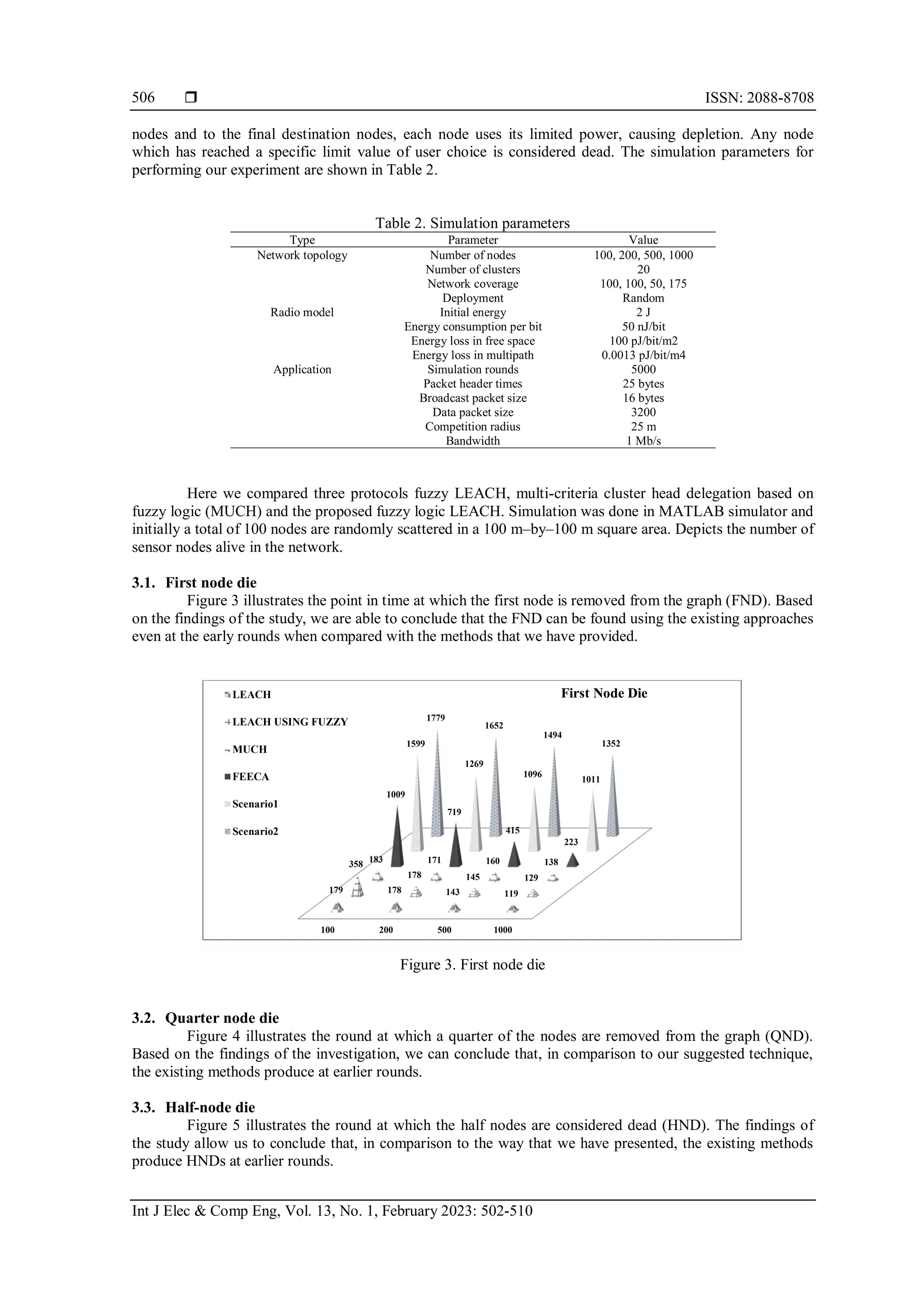
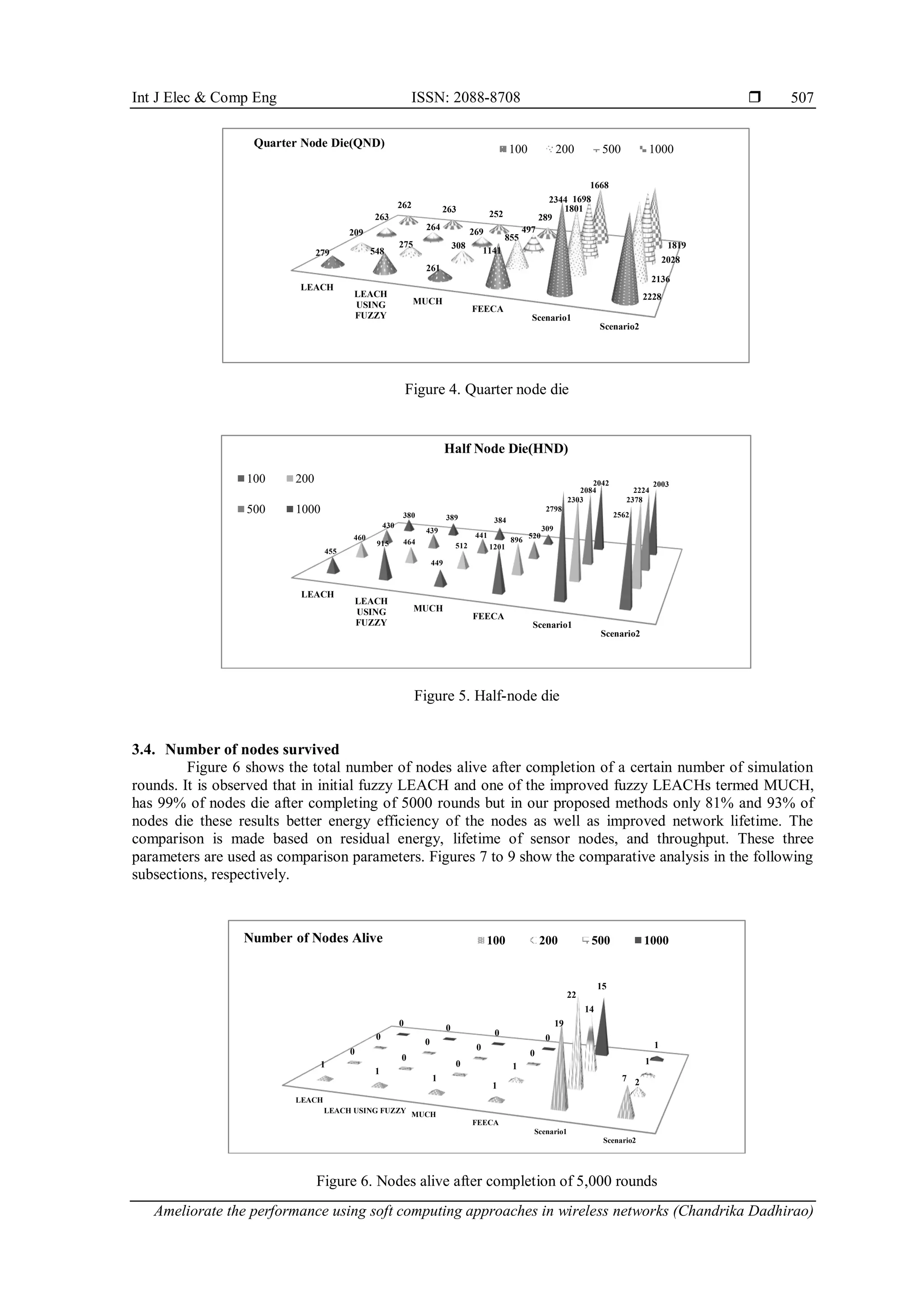
The document discusses an improved version of the Low-Energy Adaptive Clustering Hierarchy (LEACH) protocol for wireless sensor networks using fuzzy logic to optimize head node selection, thereby enhancing energy efficiency and network lifetime. The proposed fuzzy LEACH algorithm outperforms existing protocols in terms of stability, survivability, and energy consumption during simulations. The effectiveness of the method is demonstrated through various simulation scenarios that indicate better performance compared to conventional approaches.

![Int J Elec & Comp Eng ISSN: 2088-8708 Ameliorate the performance using soft computing approaches in wireless networks (Chandrika Dadhirao) 503 In terms of productivity in WSNs, routing protocols [1], [2] play a vital role. Routing is one of the most challenging techniques on WSN. It is necessary to find the best path between the source node and the target node. This method is the mathematical portrayal of human concepts. The main motto of any network is the efficient and effective transmission of information between the source and the final destination. This routing is one of the best solutions to provide an efficient and best path for wireless sensor networks. In routing, in this work the clustering approach is chosen [3]–[9] for selecting the best way for intra-clustering and inter-clustering. The classification of routing protocols [10]–[12] relies upon two critical elements, i.e., first off, primarily based on network structure and secondly based on the protocol operation. The chore of discovering and retaining routes in WSNs is not minor, as energy restrictions and sudden changes in a node. WSN has attracted tremendous attention from academics and industry worldwide in the past, present, and future. The wide range of applications [13] of WSNs is flora and fauna, military, industrial, urban, environmental, health, education, entertainment [14]–[20]. WSN involve millions of nodes that operate together, detecting and transmitting ambient knowledge to the base station [21]. Apart from those have worked on multiple sink nodes in a WSN to increase the scalability and lifetime of the network [22]. Many cluster heads choose a specific sink node and try to send their data to the sink simultaneously. Sujith et al. [23] suggested an energy-efficient zone-based clustering algorithm for WSN. In their approach, they considered zones as clusters and zone monitor as cluster head. Bagga et al. [24] has initiated an fuzzy logic- based clustering routing (FLBCR) protocol as a routing scheme that applies fluctuating logic to determine the likelihood of selecting a node as a cluster head (CH) with a variable setting existence a network. For instance, an improved low-energy adaptive clustering hierarchy–mobile fuzzy (LEACH MF) protocol has been addressed to prolong lifetime of wireless sensor networks and they show in their results that the proposed modified parameter LEACH MF is better in performance and energy consumption [25]. This compared type1 and type2 fuzzy logic approach in choosing cluster head selection to increase the wireless sensor networks. Figure 1. Layout of the wireless sensor network 2. METHOD The main steps of our proposed fuzzy based LEACH approach are discussed in this section. In proposed algorithm, optimum number of head nodes are chosen using Kopt from (1). 𝐾𝑜𝑝𝑡 = √𝑏 √2∗𝑇ℎ ∗ 𝜃0 ∗ 𝑀 𝑑𝐵𝑆2 (1) where b is the number of nodes, Th is the user defined threshold value, θ0 is the computed ratio of energy dissipated in the free space (µ) by the energy dissipated in multi path (ϑ), M is the product of area of the network and sink coordinates, and dBS2 is the first form of Euclidean distance of respective node to the sink node. The current heads of nodes calculate their W i (output fuzzy parameter) value using the fuzzy method and broadcast the current head node (HN) message to all nodes coming under the communication range. The member nodes choose the nearest HN and join it to form clusters, respectively using dBS (2): 𝐷𝑖𝑠𝑡𝑎𝑛𝑐𝑒 = min (√(𝑆𝑝 − 𝑆𝑞) 2 , (𝑆𝑞 − 𝑆𝑏𝑗)2) (2)](https://image.slidesharecdn.com/v5127066emr28jul2213jan2218n-221121063929-9004bf02/75/Ameliorate-the-performance-using-soft-computing-approaches-in-wireless-networks-2-2048.jpg)

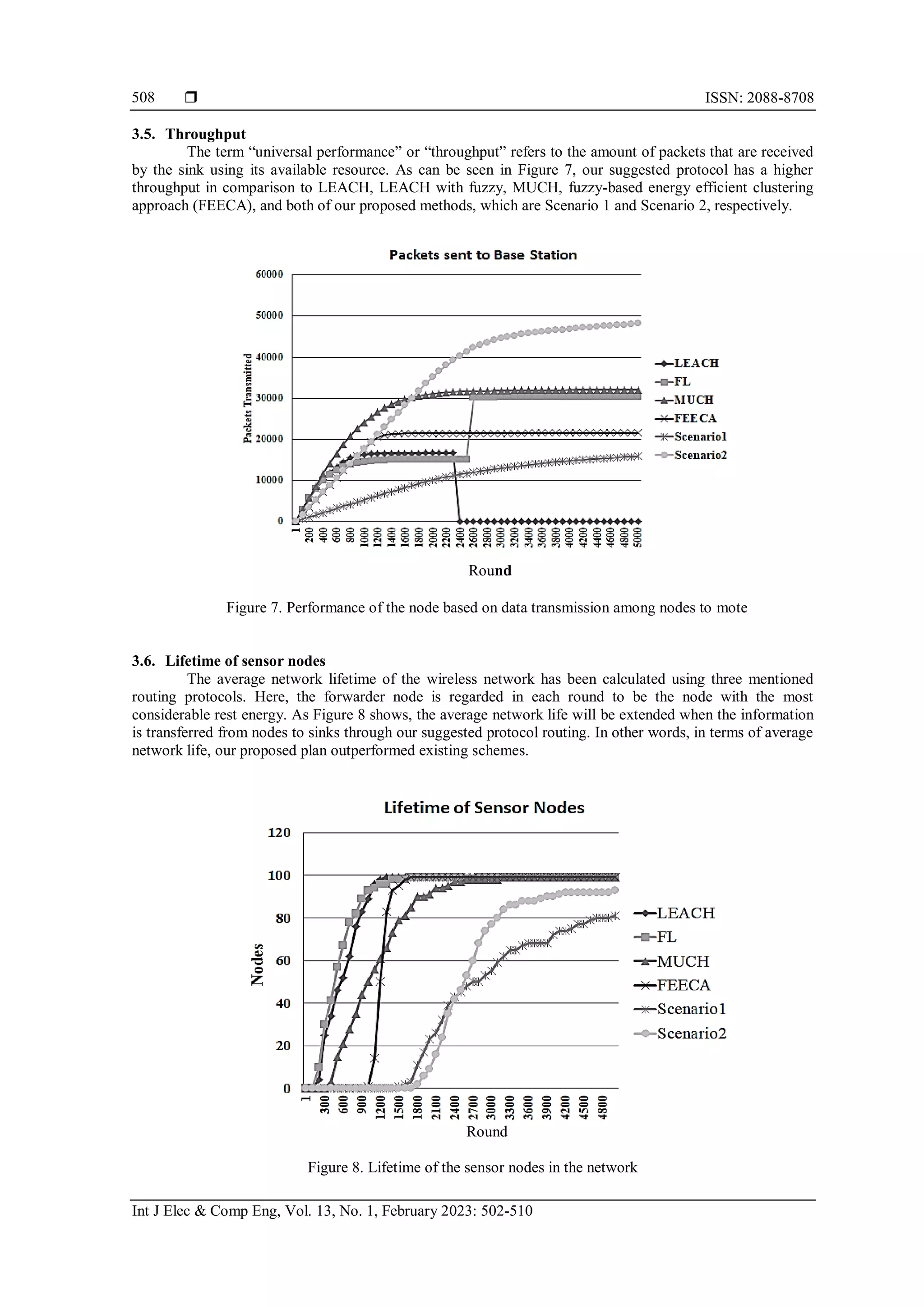
![Int J Elec & Comp Eng ISSN: 2088-8708 Ameliorate the performance using soft computing approaches in wireless networks (Chandrika Dadhirao) 509 3.7. Residual energy In this experiment, we have considered the average residual energy of all the nodes as a measure of performance and compared our protocol to three others. Higher residual energy is essential to extend the network life. From Figure 9, we can see that this residual average power is above the three mentioned protocols. Figure 9. Total energy dissipated among the nodes during each round 4. CONCLUSION Wireless sensor networks are becoming relevant in a broad range of emerging technologies. One of the challenges to WSNs is to reduce the use of resources and increase the networks' existence, for which routing may be a remedy. As the propagation energy is proportional to the distance between the sender and the receiver, the clustering mechanism minimizes energy use in routing. Using fuzzy reasoning, WSN can resist complicated mathematical models and provide considerable stability in the networks life to deal with uncertainty and interpretation. These suggested strategies described in both scenarios are a revision of the option of LEACH to select the optimal number of head node selection and select the best head node selection in any round during each cluster. The simulation findings indicate that our proposed solution delivers more robust results than four other existing state-of-the-art algorithms and proves to be more scalable after completing rounds in FND, QND, HND, and the number of nodes alive. REFERENCES [1] R. T. Ai-Zubi, N. Abedsalam, A. Atieh, and K. A. Darabkh, “Lifetime-improvement routing protocol for wireless sensor networks,” in 2018 15th International Multi-Conference on Systems, Signals & Devices (SSD), Mar. 2018, pp. 683–687, doi: 10.1109/SSD.2018.8570628. [2] J. N. Al-Karaki and A. E. Kamal, “Routing techniques in wireless sensor networks: a survey,” IEEE Wireless Communications, vol. 11, no. 6, pp. 6–28, Dec. 2004, doi: 10.1109/MWC.2004.1368893. [3] J. A. Patel and Y. Patel, “The clustering techniques for wireless sensor networks: a review,” in 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), Apr. 2018, pp. 147–151, doi: 10.1109/ICICCT.2018.8473153. [4] H. Yetgin, K. T. K. Cheung, M. El-Hajjar, and L. Hanzo, “A survey of network lifetime maximization techniques in wireless sensor networks,” IEEE Communications Surveys & Tutorials, vol. 19, no. 2, pp. 828–854, 2017, doi: 10.1109/COMST.2017.2650979. [5] K. A. Darabkh, W. S. Al-Rawashdeh, R. T. Al-Zubi, and S. H. Alnabelsi, “C-DTB-CHR: centralized density- and threshold-based cluster head replacement protocols for wireless sensor networks,” The Journal of Supercomputing, vol. 73, no. 12, pp. 5332–5353, Dec. 2017, doi: 10.1007/s11227-017-2089-4. [6] L. XingGuo, W. JunFeng, and B. LinLin, “LEACH protocol and its improved algorithm in wireless sensor network,” in 2016 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Oct. 2016, pp. 418–422, doi: 10.1109/CyberC.2016.87. [7] V. Kadrolli and J. Agarkhed, “Soft computing routing techniques in wireless sensor network,” in 2016 2nd International Conference on Advances in Electrical, Electronics, Information, Communication and Bio-Informatics (AEEICB), Feb. 2016, pp. 748–751, doi: 10.1109/AEEICB.2016.7538395. [8] B. Bhushan and G. Sahoo, “Routing protocols in wireless sensor networks,” in Computational intelligence in sensor networks, 2019, pp. 215–248. Round](https://image.slidesharecdn.com/v5127066emr28jul2213jan2218n-221121063929-9004bf02/75/Ameliorate-the-performance-using-soft-computing-approaches-in-wireless-networks-8-2048.jpg)
![ ISSN: 2088-8708 Int J Elec & Comp Eng, Vol. 13, No. 1, February 2023: 502-510 510 [9] M. F. S. Yagoub, J. J. P. C. Rodrigues, O. O. Khalifa, A. B. Mohammed, and V. Korotaev, “Service redundancy and cluster-based routing protocols for wireless sensor and mobile ad hoc networks: A survey,” International Journal of Communication Systems, vol. 33, no. 16, 2020, doi: 10.1002/dac.4471. [10] H. S. Bazzi, A. M. Haidar, and A. Bilal, “Classification of routing protocols in wireless sensor network,” in International Conference on Computer Vision and Image Analysis Applications, Jan. 2015, pp. 1–5, doi: 10.1109/ICCVIA.2015.7351790. [11] A. Krishnamoorthy and V. Vijayarajan, “Energy aware routing technique based on Markov model in wireless sensor network,” International Journal of Computers and Applications, vol. 42, no. 1, pp. 23–29, 2020, doi: 10.1080/1206212X.2017.1396423. [12] J. Tan et al., “An adaptive collection scheme-based matrix completion for data gathering in energy-harvesting wireless sensor networks,” IEEE Access, vol. 7, pp. 6703–6723, 2019, doi: 10.1109/ACCESS.2019.2890862. [13] D. Kandris, C. Nakas, D. Vomvas, and G. Koulouras, “Applications of wireless sensor networks: An up-to-date survey,” Applied System Innovation, vol. 3, no. 1, Feb. 2020, doi: 10.3390/asi3010014. [14] K. A. Darabkh and J. N. Zomot, “An improved cluster head selection algorithm for wireless sensor networks,” in 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Jun. 2018, pp. 65–70, doi: 10.1109/IWCMC.2018.8450446. [15] I. A. T. Hashem et al., “The role of big data in smart city,” International Journal of Information Management, vol. 36, no. 5, pp. 748–758, Oct. 2016, doi: 10.1016/j.ijinfomgt.2016.05.002. [16] D. P. Agrawal, “Applications of sensor networks,” in Embedded Sensor Systems, vol. 8, no. 9S3, Singapore: Springer Singapore, 2017, pp. 35–63. [17] B. Rashid and M. H. Rehmani, “Applications of wireless sensor networks for urban areas: A survey,” Journal of Network and Computer Applications, vol. 60, pp. 192–219, Jan. 2016, doi: 10.1016/j.jnca.2015.09.008. [18] S. R. Jino Ramson and D. J. Moni, “Applications of wireless sensor networks — A survey,” in 2017 International Conference on Innovations in Electrical, Electronics, Instrumentation and Media Technology (ICEEIMT), Feb. 2017, pp. 325–329, doi: 10.1109/ICIEEIMT.2017.8116858. [19] T. Khan et al., “A novel and comprehensive trust estimation clustering based approach for large scale wireless sensor networks,” IEEE Access, vol. 7, pp. 58221–58240, 2019, doi: 10.1109/ACCESS.2019.2914769. [20] S. S. Desai and M. J. Nene, “Node-level trust evaluation in wireless sensor networks,” IEEE Transactions on Information Forensics and Security, vol. 14, no. 8, pp. 2139–2152, Aug. 2019, doi: 10.1109/TIFS.2019.2894027. [21] D. Agrawal and S. Pandey, “Optimization of the selection of cluster‐head using fuzzy logic and harmony search in wireless sensor networks,” International Journal of Communication Systems, vol. 34, no. 13, Sep. 2021, doi: 10.1002/dac.4391. [22] A. Shahidinejad and S. Barshandeh, “Sink selection and clustering using fuzzy-based controller for wireless sensor networks,” International Journal of Communication Systems, vol. 33, no. 4, Aug. 2020, doi: 10.1002/dac.4557. [23] A. Sujith, D. R. Dorai, and V. N. Kamalesh, “Energy efficient zone‐based clustering algorithm using fuzzy inference system for wireless sensor networks,” Engineering Reports, vol. 3, no. 4, Apr. 2021, doi: 10.1002/eng2.12310. [24] S. Bagga, A. Goyal, G. Gupta, and D. K. Sharma, “FLBCR: Fuzzy logic based clustering routing protocol,” in 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Jul. 2019, pp. 1–7, doi: 10.1109/ICCCNT45670.2019.8944547. [25] S. Sharma and N. Mittal, “An improved LEACH-MF protocol to prolong lifetime of wireless sensor networks,” in 2018 IEEE 8th International Advance Computing Conference (IACC), Dec. 2018, pp. 174–179, doi: 10.1109/IADCC.2018.8692096. BIOGRAPHIES OF AUTHORS Chandrika Dadhirao is a research scholar in the School of Computer Science and Engineering at VIT-AP University, near Vijayawada. Her areas of interest are wireless sensor networks, soft computing, and cloud computing. She can be contacted at email: chandrikad10@gmail.com. Ravi Sankar Sangam is an associate professor in the School of Computer Science and Engineering at VIT-AP University, near Vijayawada. His specialization areas are data clustering and mining, wireless sensor networks. He can be contacted at email: srskar@gmail.com.](https://image.slidesharecdn.com/v5127066emr28jul2213jan2218n-221121063929-9004bf02/75/Ameliorate-the-performance-using-soft-computing-approaches-in-wireless-networks-9-2048.jpg)