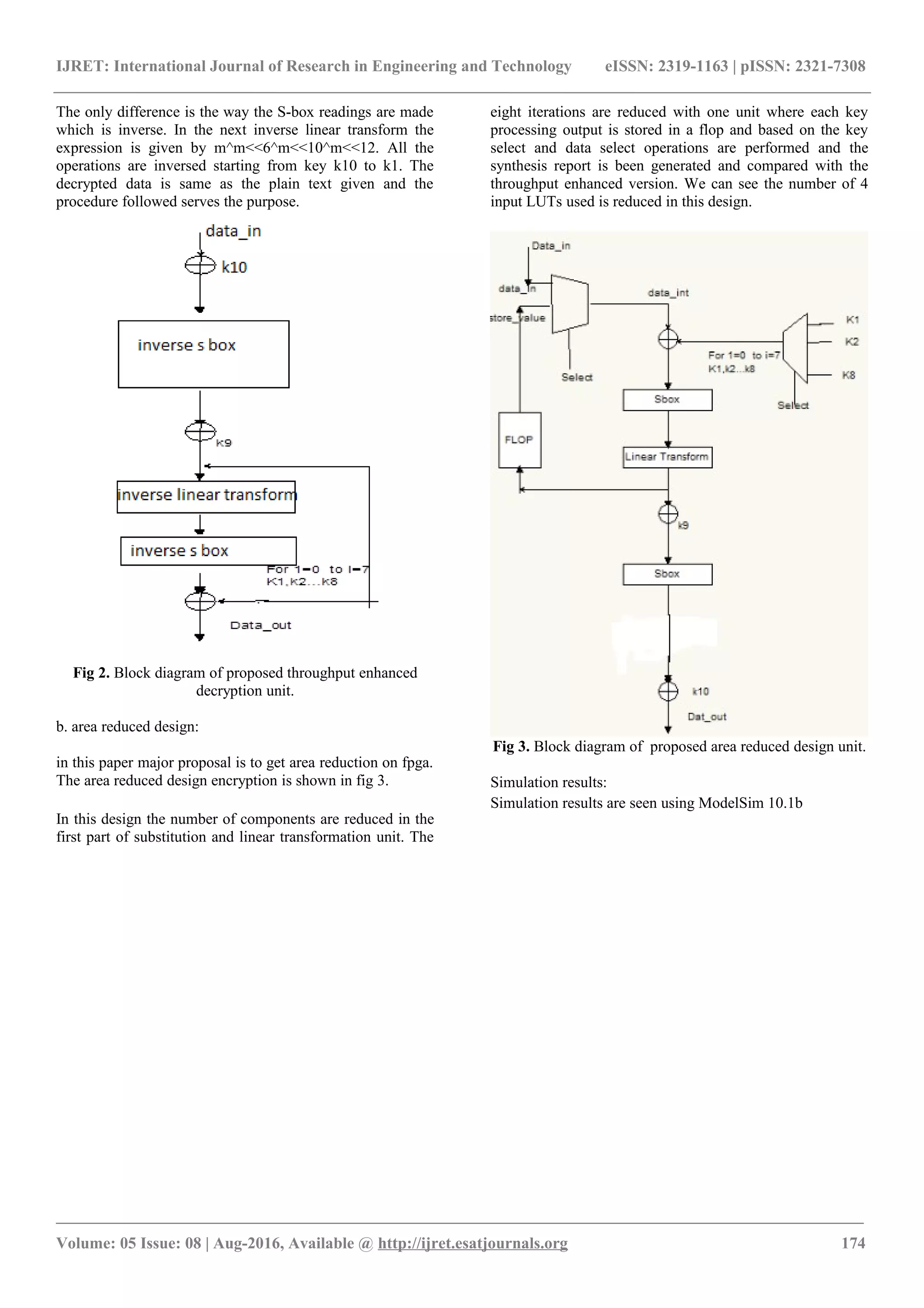
The document discusses the design and implementation of a block cipher architecture using the Hummingbird cryptographic algorithm, focusing on efficiency and security with a 128-bit key. It compares two designs—throughput enhanced and area reduced—evaluating their area utilization and performance through FPGA implementation. The results indicate a significant reduction in area for the area-reduced design, making it suitable for use in lightweight applications such as wireless sensor nodes and smart chips.


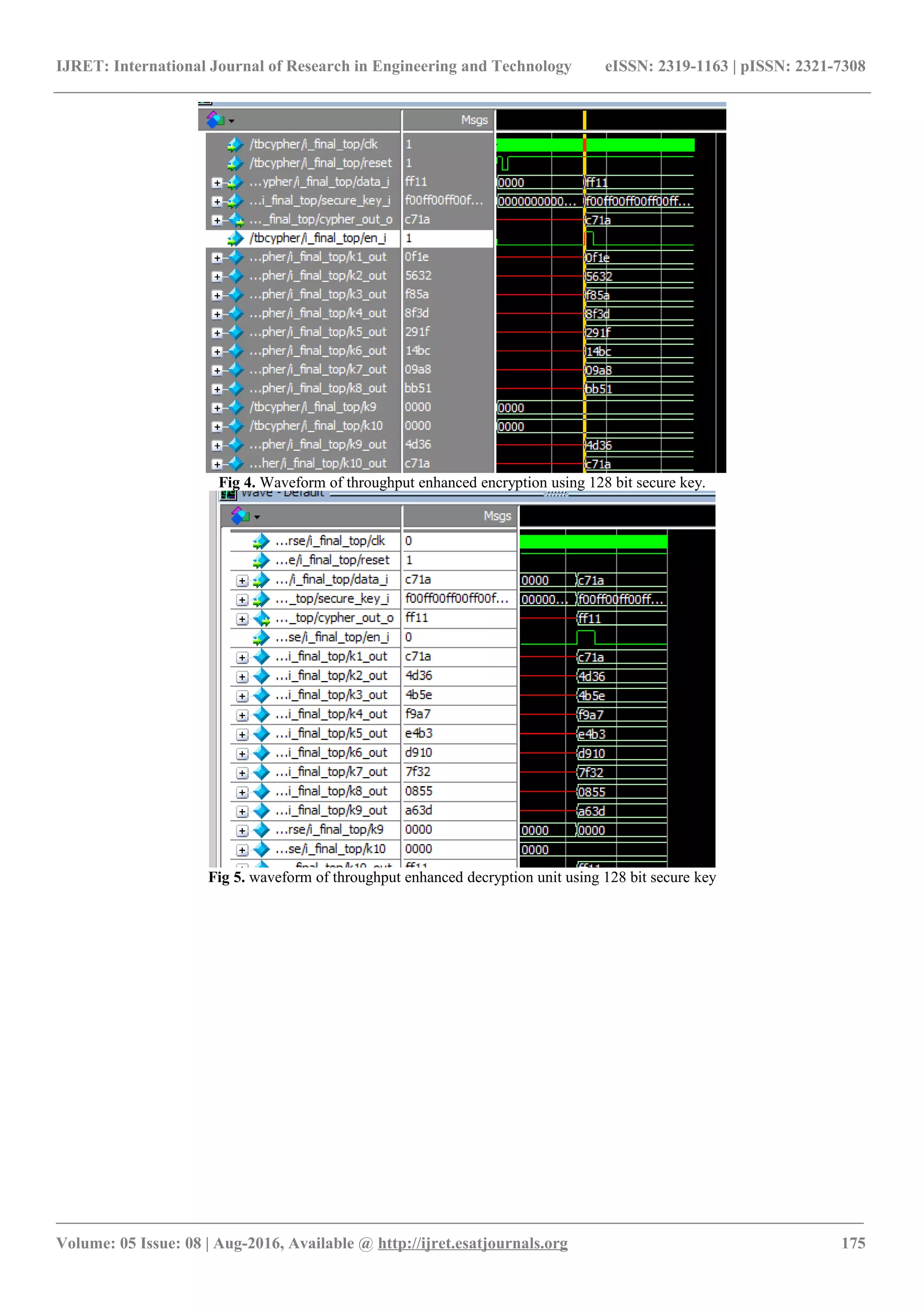
![IJRET: International Journal of Research in Engineering and Technology eISSN: 2319-1163 | pISSN: 2321-7308 Fig 6. waveform of area reduced encryption unit using 128 bit secure key.Synthesis report : Syntesis is done using Xilinx 14.6 version. Table 2: Device utilization summary Module Area in LUT Throughput Oriented 128 252 Area oriented 128 104 Through put base paper 64 132 Area oriented 64 88 CONCLUSION In this paper , the cipher block named throughput enhanced and area reduced block ciphers are implemented. Both encryption and decryption units are developed and implemented. The round keys are generated and registered using 128 bit secure key instead of 64 bit key used in the previous work. The S – box implementation is done using readily available LUTs instead of Boolean expression which is time consuming and more number of slices for implementation. The simulation and synthesis reports are tabulated . as seen from the table 2 area reduced design required lesser number of 4 input LUT compared to throughput enhanced design. This shows that single module chip area optimization is observed in greater manner. This is a well balanced architecture with high performance and low complexity. This cipher block can also be used in wireless sensor nodes and smart chips. REFERENCES [1] R. Anderson, E. Biham, and L. Knudsen, “Serpent: A proposal for the advanced encryption standard,” in Proc. 1st Advanced Encryption Standard (AES) Conf., 1998. [2] B. Singh, L. Alexander, and S. Burman, “On algebraic relations of Serpent S-boxes”, Cryptology ePrint Archive, Report 2009/038, 2009. [3] M. J. O. Saarinen, “Cryptanalysis of Hummingbird-1,” in Proc. the 18th international conference on Fast software encryption, Denmark, Feb. 2011. [4] C. Patterson, “A Dynamic FPGA Implementation of the Serpent Block Cipher,” Lecture Notes in Computer Science, Vol. 1965, pp 141-155, 2000. [5] X. Fan, H. Hu, G. Gong, E. Smith, and D. Engels, “Lightweight Implementation of Hummingbird Cryptographic Algorithm on 4-Bit Microcontrollers,” in Proc. 4th International Conference for Internet Technology and Secured Transactions (ICITST 2009), pp. 838-844, Nov. 2009. [6] X. Fan, G. Gong, K. Lauffenburger, and T. Hicks, “FPGA Implementations of the Hummingbird Cryptographic Algorithm,” in Proc. The 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST 2010), pp.48-51, 2010. [7] X. Chen, Y. Zhu, Z. Gong, and Y. Luo, “Cryptanalysis of the Lightweight Block Cipher Hummingbird-1,” in proc. Fourth International Conference on Emerging Intelligent Data and Web Technologies (EIDWT), pp. 515 - 518, 2013. [8] I. San and N. At, “Compact Hardware Architecture for Hummingbird Cryptographic Algorithm,” in Proc. 2011 International Conference on Field Programmable Logic and Applications (FPL), pp.376- 381, Sept. 2011. ________________________________________________________________________________________________________ Volume: 05 Issue: 08 | Aug-2016, Available @ http://ijret.esatjournals.org 176](https://image.slidesharecdn.com/avlsiimplementationofaresourceefficientandsecurearchitectureofablockcipher-161224105914/75/A-vlsi-implementation-of-a-resource-efficient-and-secure-architecture-of-a-block-cipher-5-2048.jpg)
![IJRET: International Journal of Research in Engineering and Technology eISSN: 2319-1163 | pISSN: 2321-7308 [9] A. Bogdanov, L. R. Knudsen, G. Leander, C. Paar, A. Poschmann, M. Robshaw, Y. Seurin and C. Vikkelsoe, “PRESENT: An Ultra- Lightweight Block Cipher”, Cryptographic Hardware and Embedded Systems, vol. 4727,Springer Heidelber, pp. 450- 466, 2007. [10] G. Xianwei,L. Erhong, X. Liqin, C. Hanlin, “FPGA Implementation of the SMS4 Block Cipher in the Chinese WAPI Standard,” in Proc. International Conference on Embedded Software and Systems Symposia, pp.104-106, July 2008. [11] X. Fan, “Efficient Cryptographic Algorithms and Protocols for Mobile Ad Hoc Networks,” Ph.D. thesis, University of Waterloo, Canada, March 2010. [12] P. Bora and T. Czajka,“Implementation of the Serpent Algorithm Using Altera FPGA Devices,” Public Comments on AES Candidate Algorithms-Round 2, available at : http://www.nist.gov/aes/. [13] A.J. Elbirt and C Paar, “An FPGA implementation and performance evaluation of the Serpent block cipher,” In Proc. ACM Eighth International Symposium on Field Programmable Gate Arrays (FPGA 2000), pp. 33–40, Feb 2000. [14] X. Fan, G. Gong, and H. Hu, “Remedying the Hummingbird Cryptographic Algorithm,” in Proc. The 2011 IEEE International Workshop on Security and Privacy in Internet of Things (SPIoT 2011), China, Nov. 2011. [15]Saha, Shumit, Md. Rashedul Islam, Habibur Rahman, Mehadi Hassan, and A. B. M. Aowlad Hossain. "Design and implementation of block cipher in hummingbird algorithm over FPGA", Fifth International Conference on Computing Communications and Networking Technologies (ICCCNT), 2014. ________________________________________________________________________________________________________ Volume: 05 Issue: 08 | Aug-2016, Available @ http://ijret.esatjournals.org 177](https://image.slidesharecdn.com/avlsiimplementationofaresourceefficientandsecurearchitectureofablockcipher-161224105914/75/A-vlsi-implementation-of-a-resource-efficient-and-secure-architecture-of-a-block-cipher-6-2048.jpg)
![IJRET: International Journal of Research in Engineering and Technology eISSN: 2319-1163 | pISSN: 2321-7308 [9] A. Bogdanov, L. R. Knudsen, G. Leander, C. Paar, A. Poschmann, M. Robshaw, Y. Seurin and C. Vikkelsoe, “PRESENT: An Ultra- Lightweight Block Cipher”, Cryptographic Hardware and Embedded Systems, vol. 4727,Springer Heidelber, pp. 450- 466, 2007. [10] G. Xianwei,L. Erhong, X. Liqin, C. Hanlin, “FPGA Implementation of the SMS4 Block Cipher in the Chinese WAPI Standard,” in Proc. International Conference on Embedded Software and Systems Symposia, pp.104-106, July 2008. [11] X. Fan, “Efficient Cryptographic Algorithms and Protocols for Mobile Ad Hoc Networks,” Ph.D. thesis, University of Waterloo, Canada, March 2010. [12] P. Bora and T. Czajka,“Implementation of the Serpent Algorithm Using Altera FPGA Devices,” Public Comments on AES Candidate Algorithms-Round 2, available at : http://www.nist.gov/aes/. [13] A.J. Elbirt and C Paar, “An FPGA implementation and performance evaluation of the Serpent block cipher,” In Proc. ACM Eighth International Symposium on Field Programmable Gate Arrays (FPGA 2000), pp. 33–40, Feb 2000. [14] X. Fan, G. Gong, and H. Hu, “Remedying the Hummingbird Cryptographic Algorithm,” in Proc. The 2011 IEEE International Workshop on Security and Privacy in Internet of Things (SPIoT 2011), China, Nov. 2011. [15]Saha, Shumit, Md. Rashedul Islam, Habibur Rahman, Mehadi Hassan, and A. B. M. Aowlad Hossain. "Design and implementation of block cipher in hummingbird algorithm over FPGA", Fifth International Conference on Computing Communications and Networking Technologies (ICCCNT), 2014. ________________________________________________________________________________________________________ Volume: 05 Issue: 08 | Aug-2016, Available @ http://ijret.esatjournals.org 177](https://image.slidesharecdn.com/avlsiimplementationofaresourceefficientandsecurearchitectureofablockcipher-161224105914/75/A-vlsi-implementation-of-a-resource-efficient-and-secure-architecture-of-a-block-cipher-7-2048.jpg)