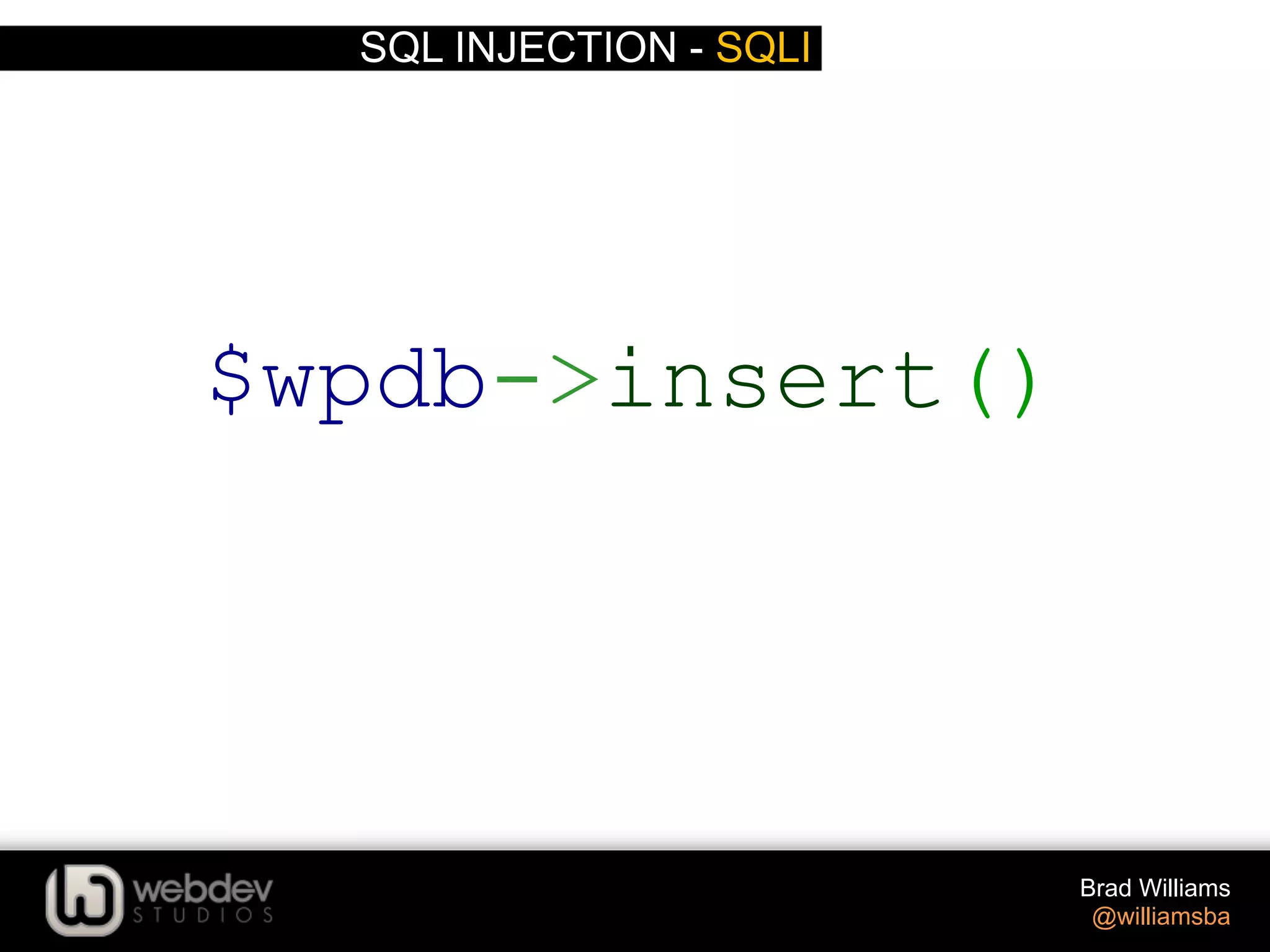
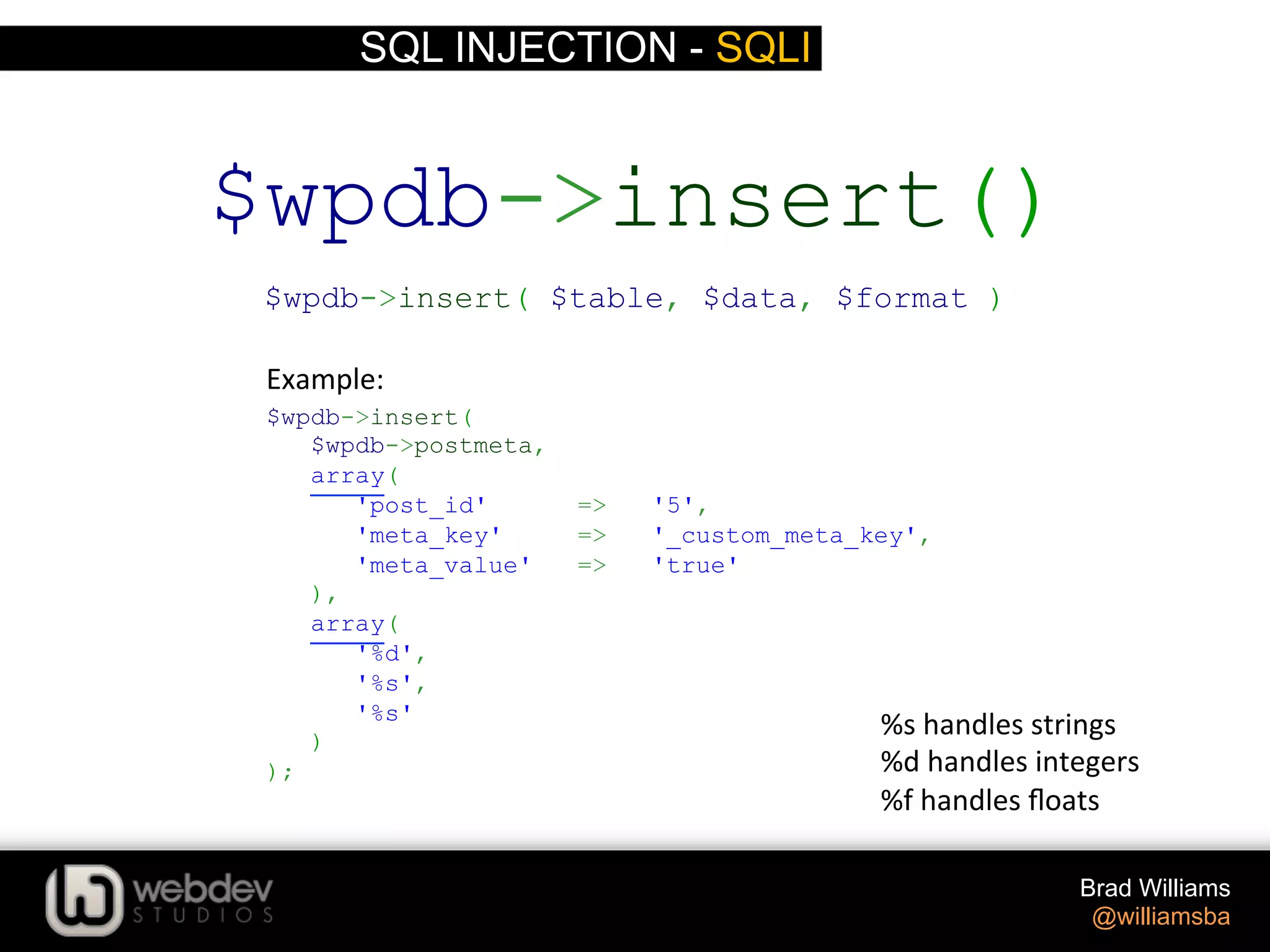
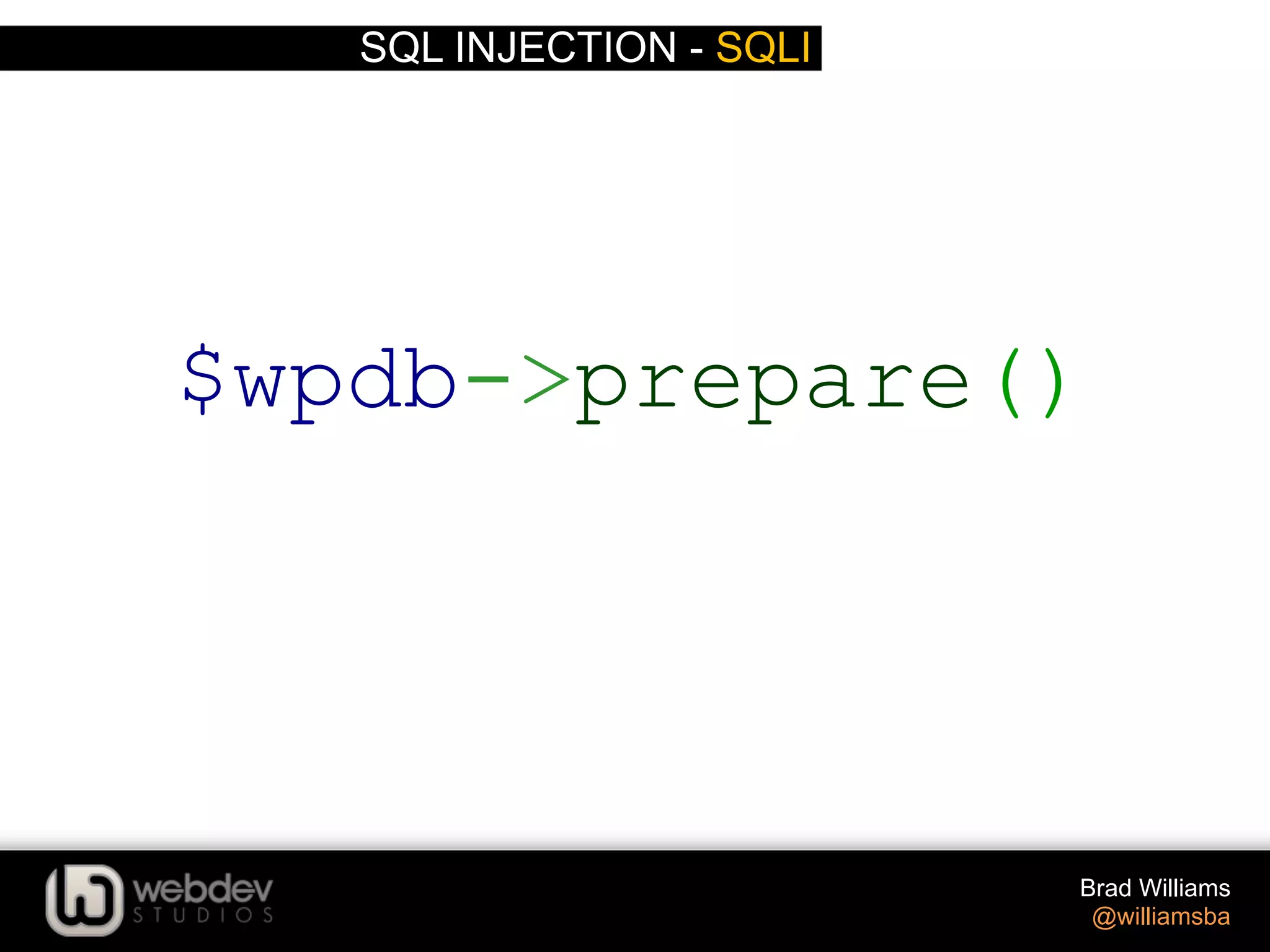
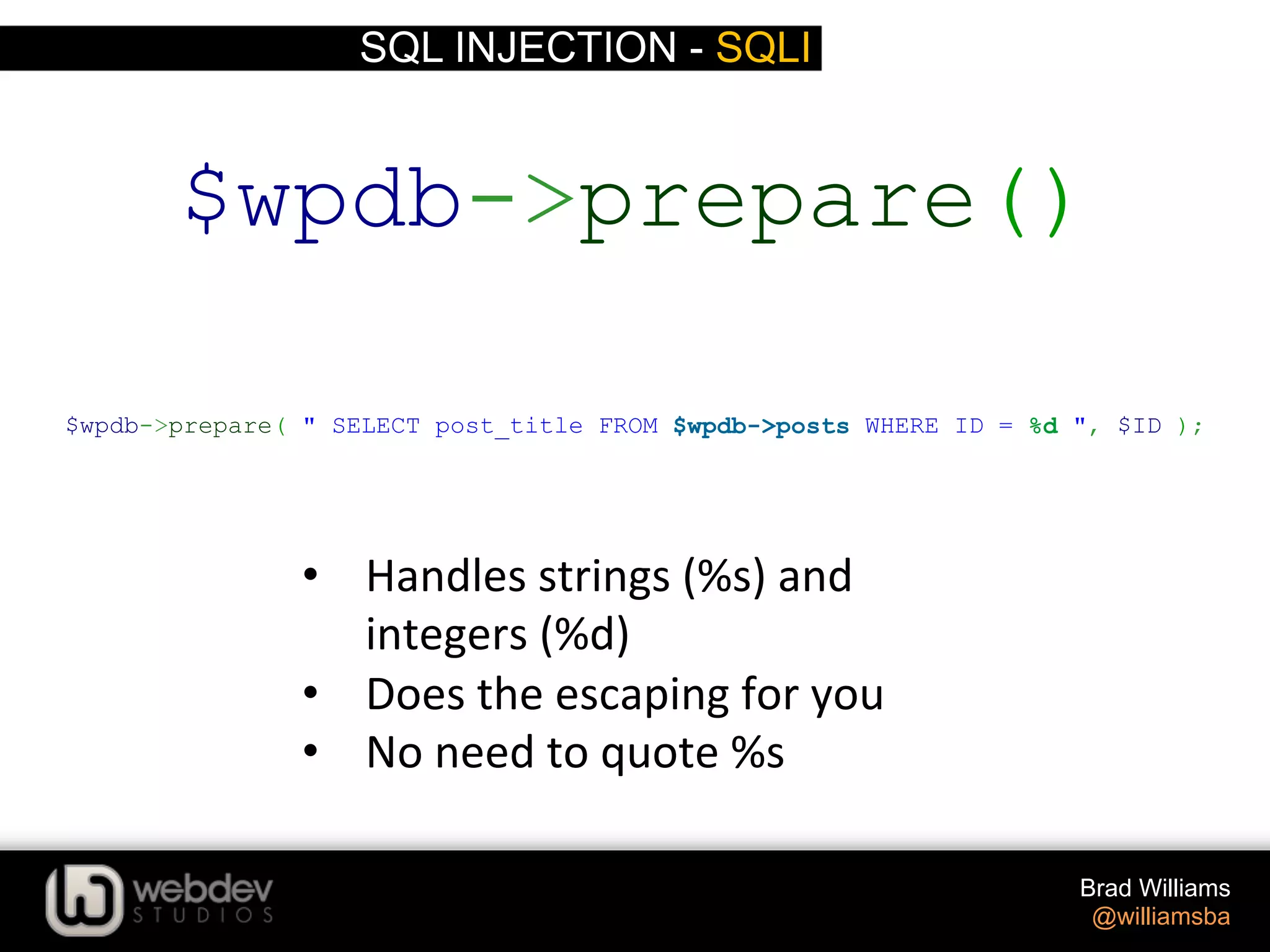
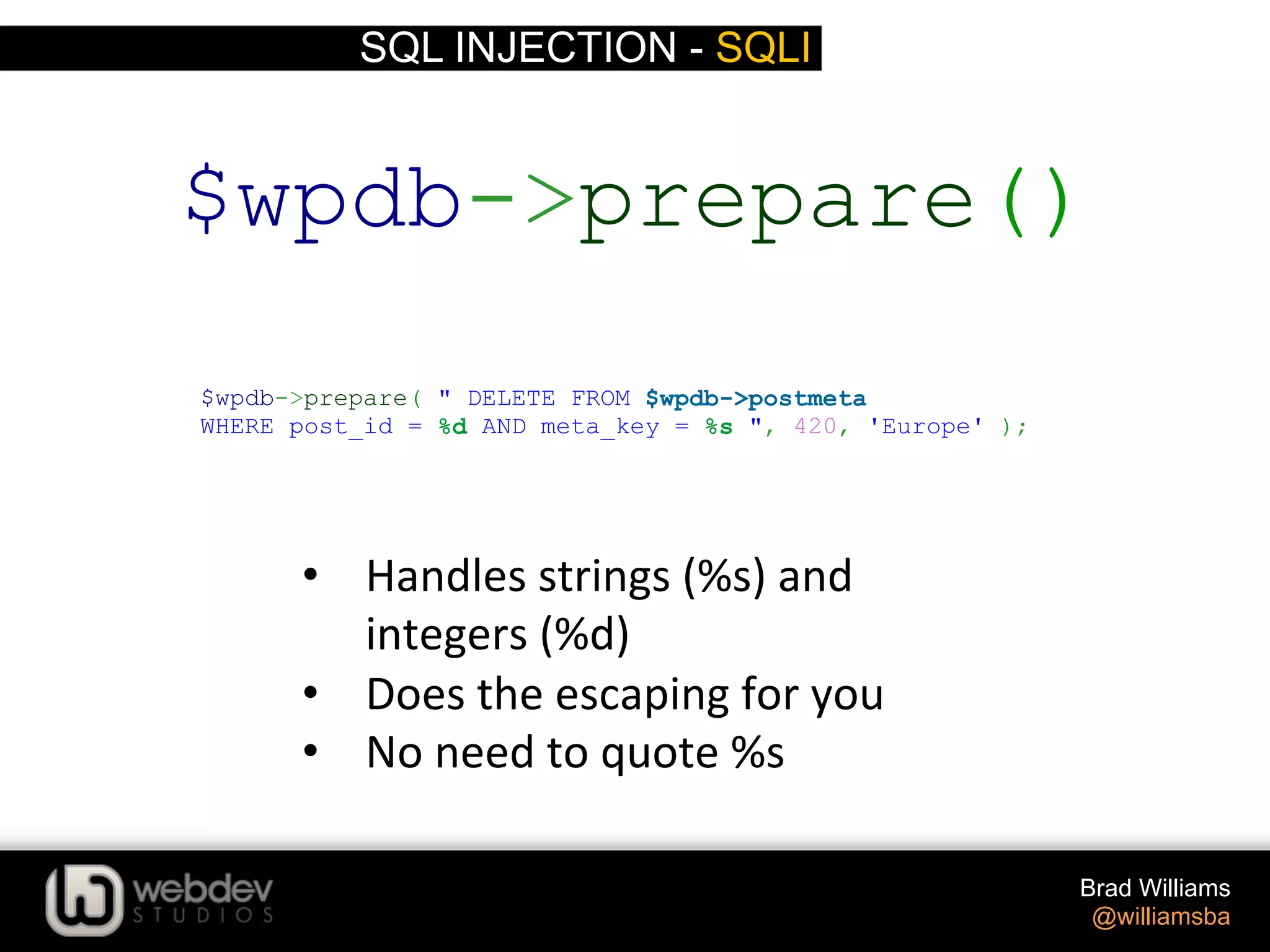
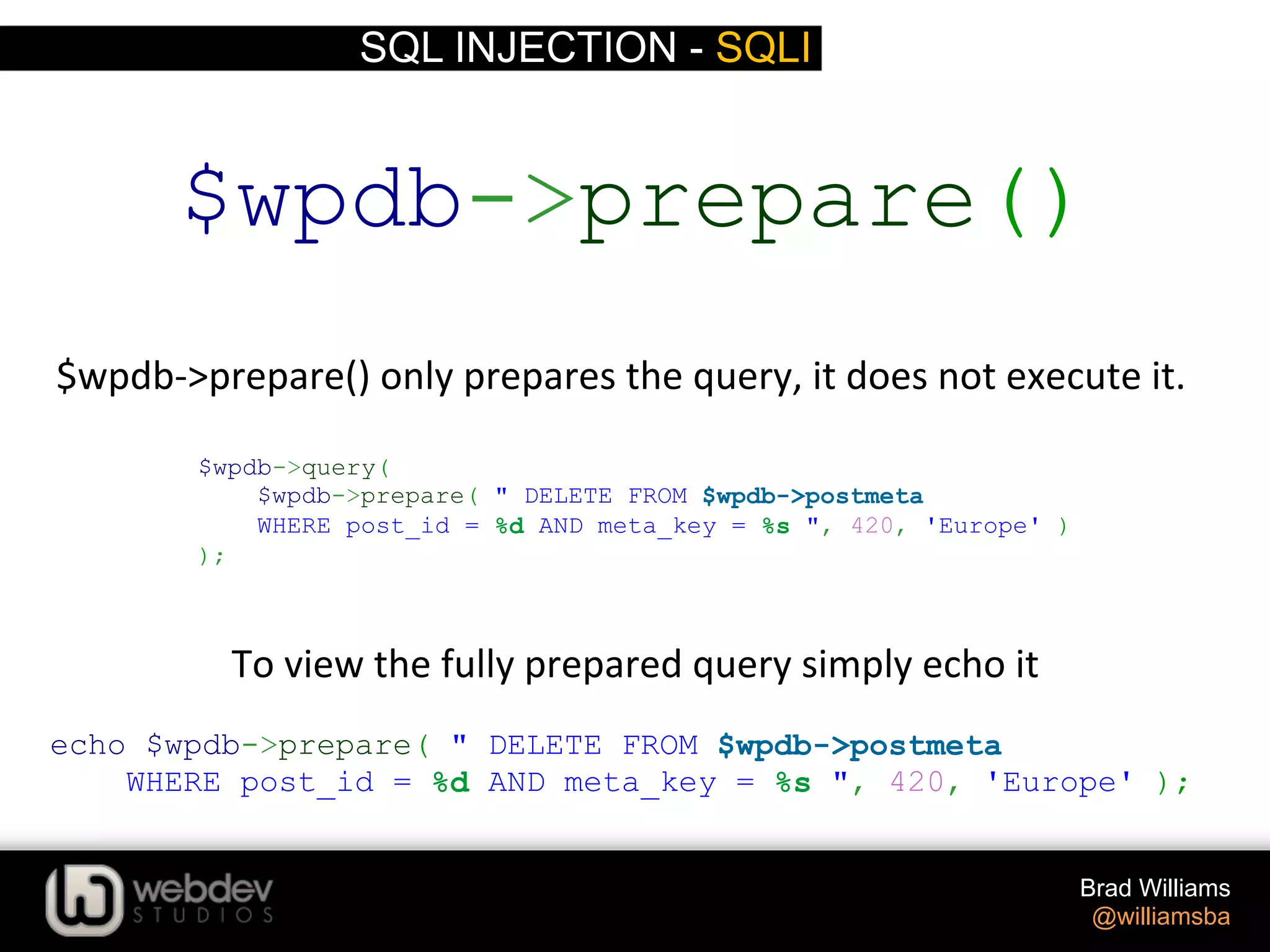
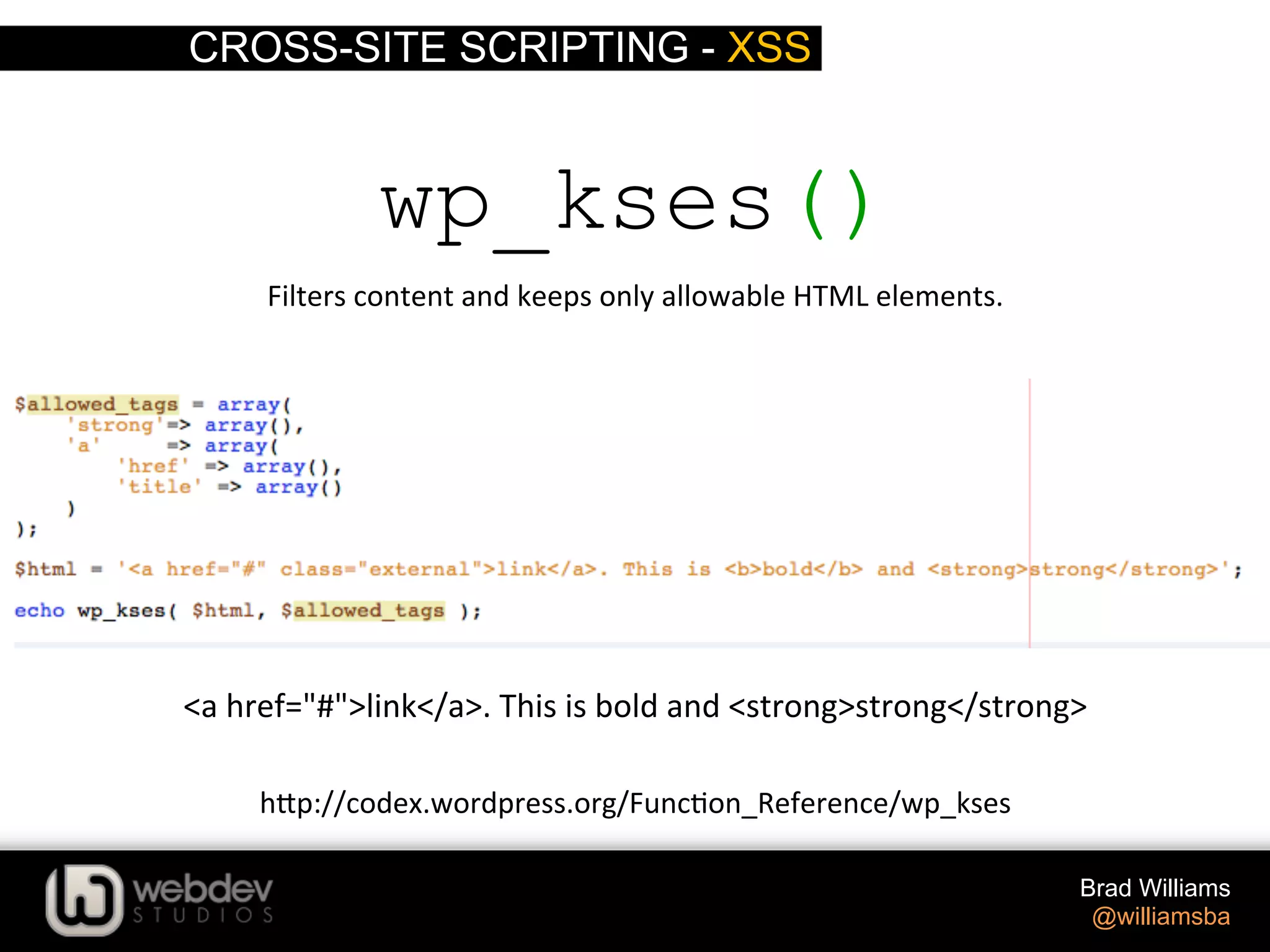
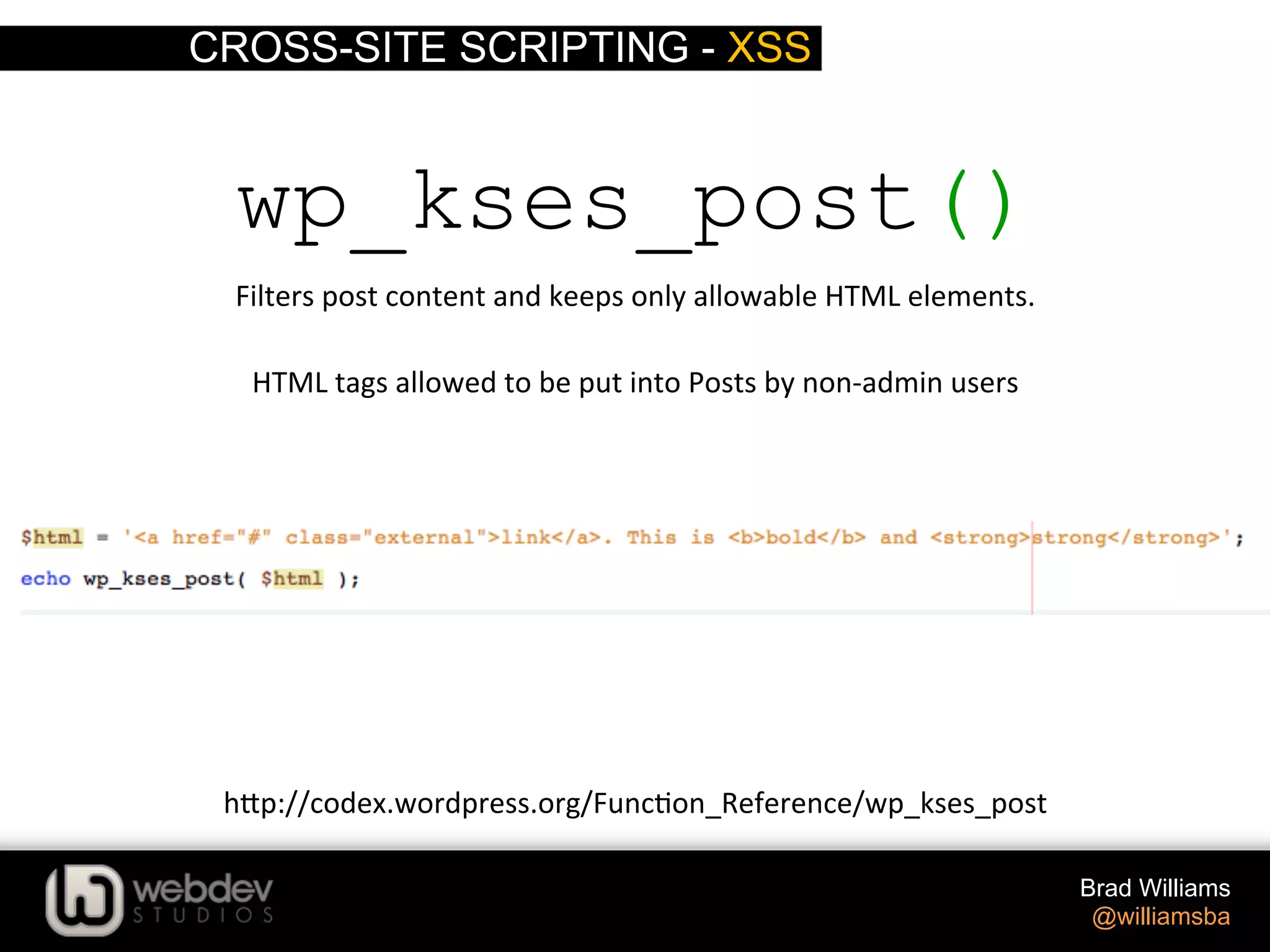
The document discusses various techniques for writing secure WordPress code. It covers the top exploits of SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It provides examples of how these exploits can occur and recommendations for data validation, sanitization, and escaping user input to prevent exploits. These include using functions like $wpdb->prepare(), esc_html(), sanitize_text_field(), and others to properly handle and escape data when outputting or storing it.







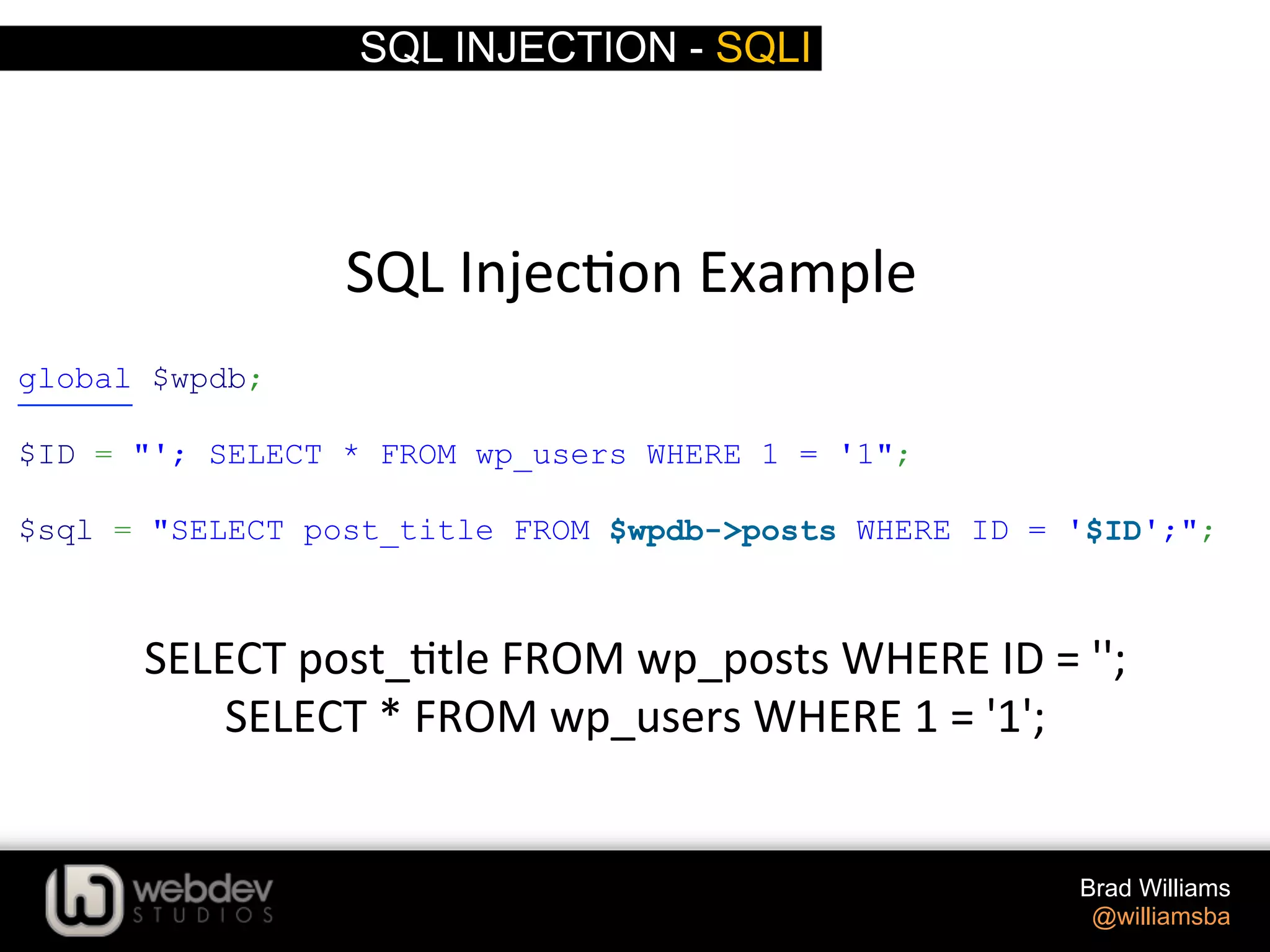
![SQL INJECTION - SQLI Brad Williams @williamsba SQL Injec>on Example global $wpdb; $ID = $_GET['ID']; $sql = "SELECT post_title FROM $wpdb->posts WHERE ID = '$ID';"; SELECT post_>tle FROM wp_posts WHERE ID = '5';](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-9-2048.jpg)


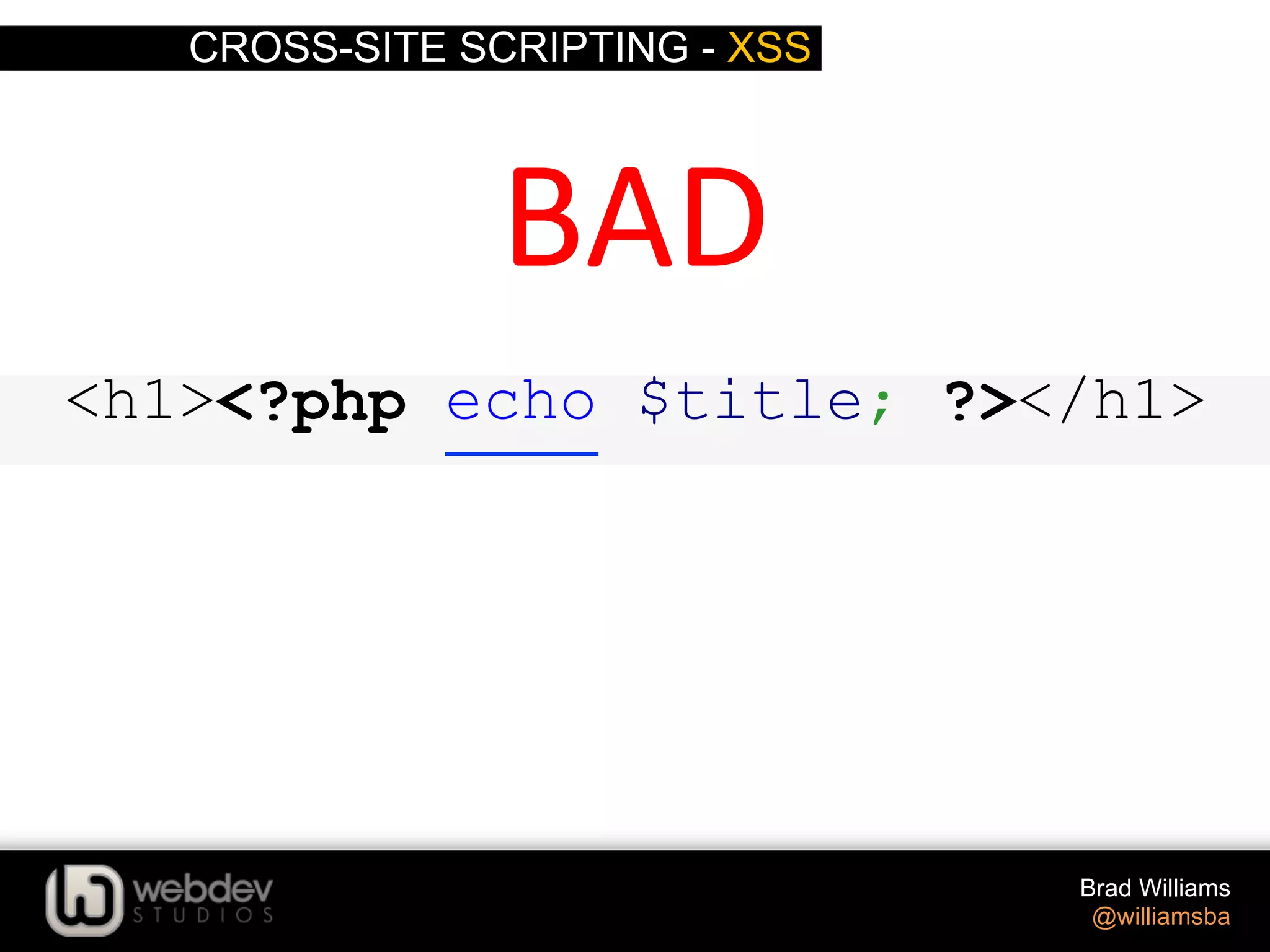
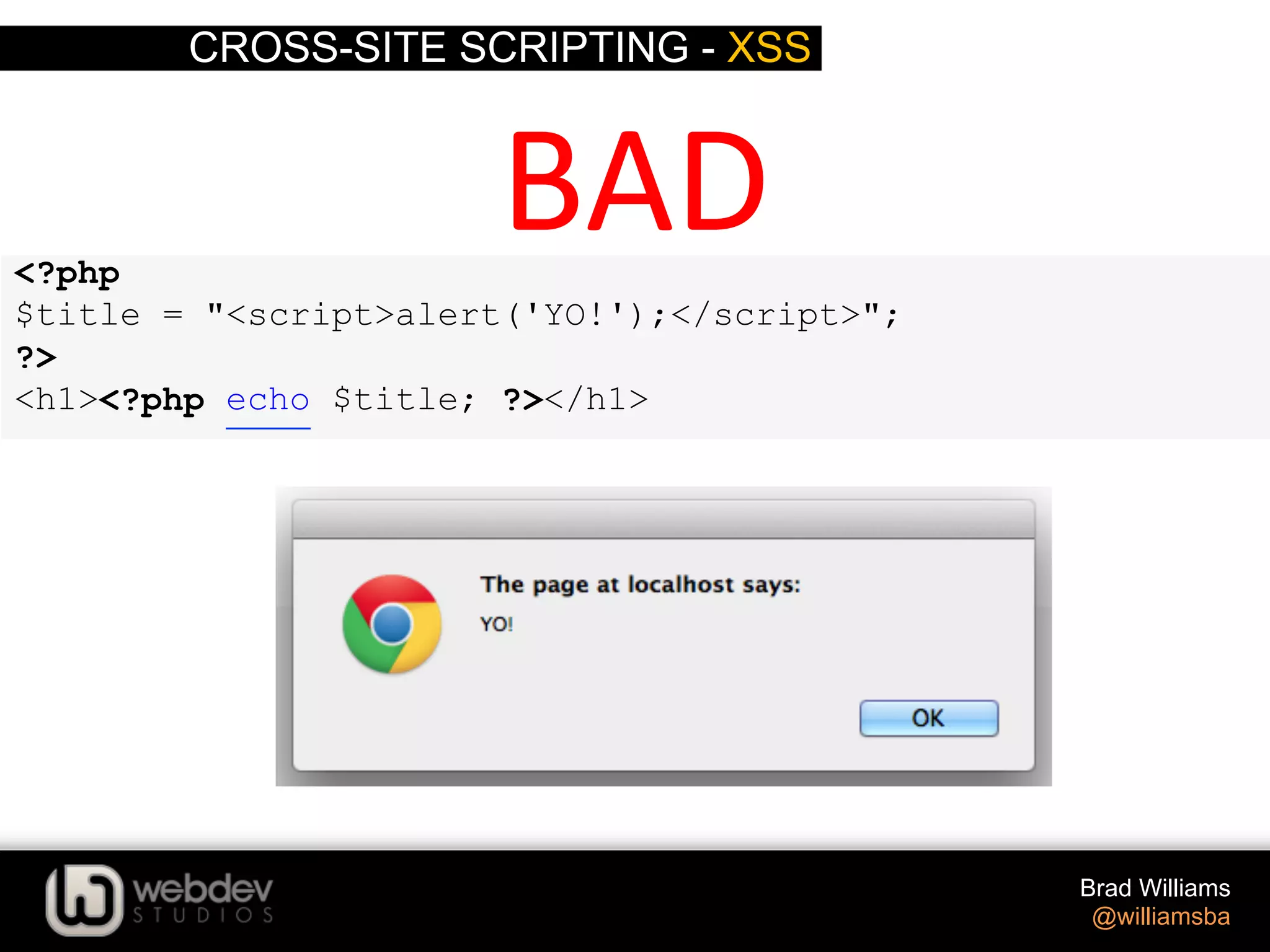
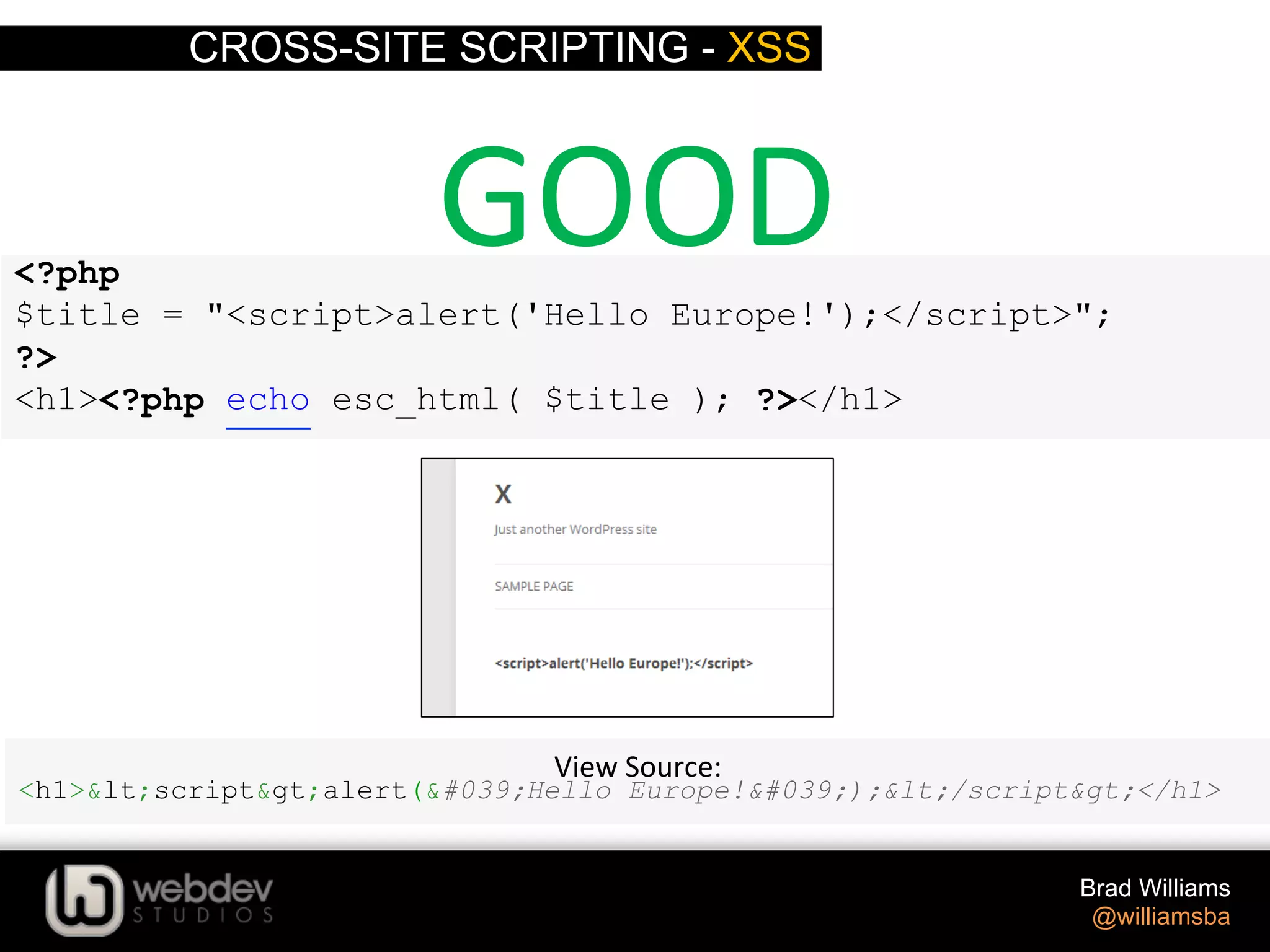
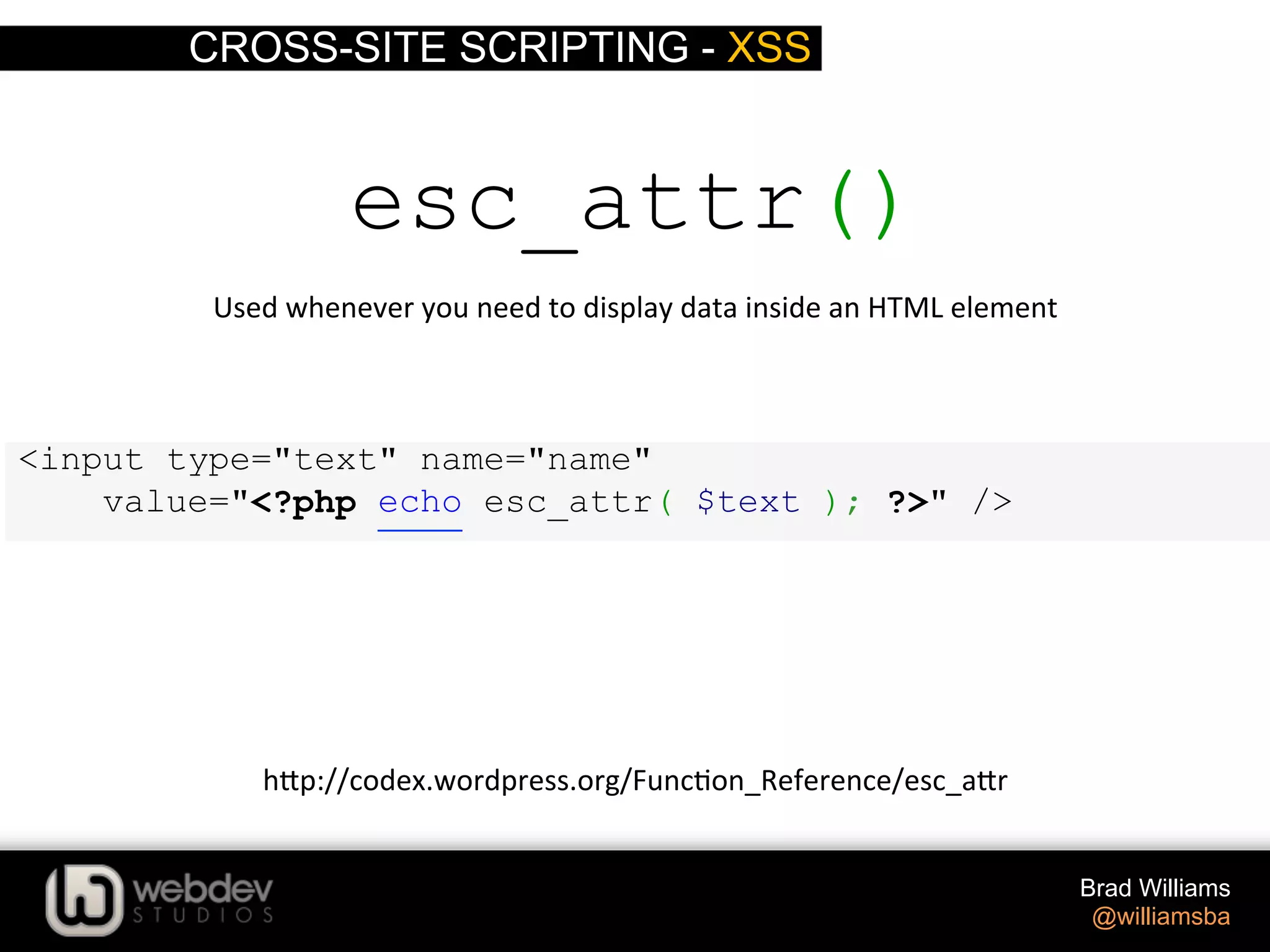
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba $ID = absint( $_GET['ID'] ); absint() Coverts a value to a non-‐nega>ve integer h-p://codex.wordpress.org/Func>on_Reference/absint <input type="text" name="number_posts" value="<?php echo absint( $number ); ?>" />](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-38-2048.jpg)
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba $ID = intval( $_GET['ID'] ); intval() Returns the integer value. Works with nega>ve values h-p://php.net/manual/en/func>on.intval.php <input type="text" name="number_posts" value="<?php echo intval( $number ); ?>" />](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-39-2048.jpg)
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba <?php update_post_meta( 420, '_post_meta_key', $_POST['new_meta_value'] ); ?> BAD](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-41-2048.jpg)
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba sanitize_text_field() Sani>ze a string h-p://codex.wordpress.org/Func>on_Reference/sani>ze_text_field <?php update_post_meta( 34, '_post_meta_key', sanitize_text_field( $_POST['new_meta_value'] ) ); ?>](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-42-2048.jpg)
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba sanitize_email() Strip out all characters not allowed in an email address h-p://codex.wordpress.org/Func>on_Reference/sani>ze_email <?php update_post_meta( 34, '_email_address', sanitize_email( $_POST['email'] ) ); ?>](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-43-2048.jpg)
![CROSS-SITE SCRIPTING - XSS Brad Williams @williamsba sanitize_user() Sani>ze username stripping out unsafe characters h-p://codex.wordpress.org/Func>on_Reference/sani>ze_user <?php update_post_meta( 34, '_custom_username', sanitize_user( $_POST['username'] ) ); ?>](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-44-2048.jpg)
![CROSS-SITE REQUEST FORGERY - CSRF Brad Williams @williamsba <?php if ( isset( $_POST['email'] ) ) { //process form data } ?> <form method="post"> <input type="text" name="email /><br /> <input type="submit" name="submit" value="Submit" /> </form> Example There is no way to know where $_POST[‘email’] is being posted from](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-50-2048.jpg)
![CROSS-SITE REQUEST FORGERY - CSRF Brad Williams @williamsba if ( isset( $_POST['email'] ) ) { check_admin_referer( 'bw_process_email_action', 'bw_newsletter' ); //process form data } check_admin_referer() Processing Code: check_admin_referer( $action, $query_arg ); h-p://codex.wordpress.org/Func>on_Reference/check_admin_referer](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-52-2048.jpg)
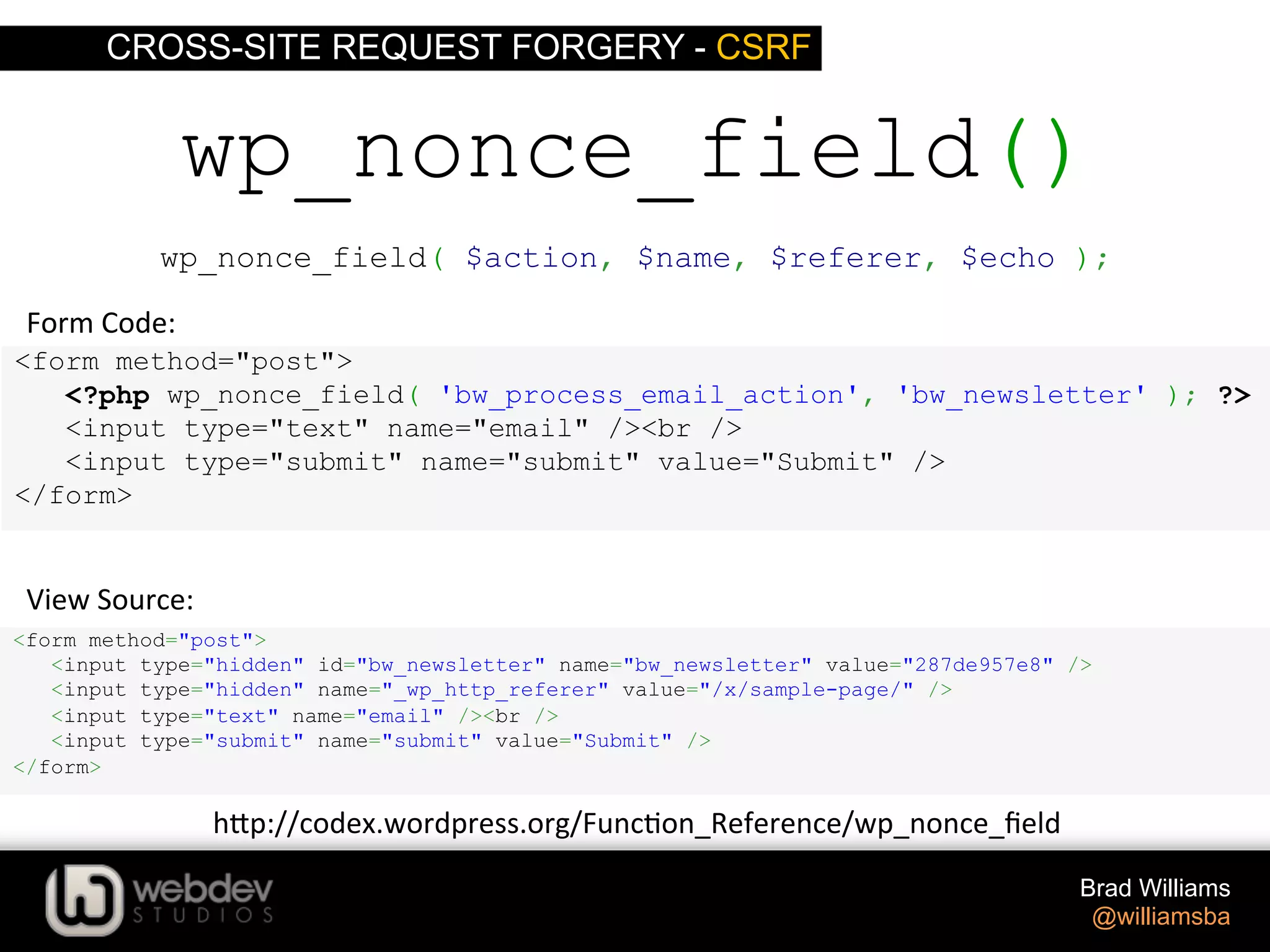
![CROSS-SITE REQUEST FORGERY - CSRF Brad Williams @williamsba <?php if ( isset( $_POST['email'] ) ) { check_admin_referer( 'bw_process_email_action', 'bw_newsletter' ); //process form data } ?> <form method="post"> <?php wp_nonce_field( 'bw_process_email_action', 'bw_newsletter' ); ?> <input type="text" name="email" /><br /> <input type="submit" name="submit" value="Submit" /> </form> Fixed Example](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-53-2048.jpg)
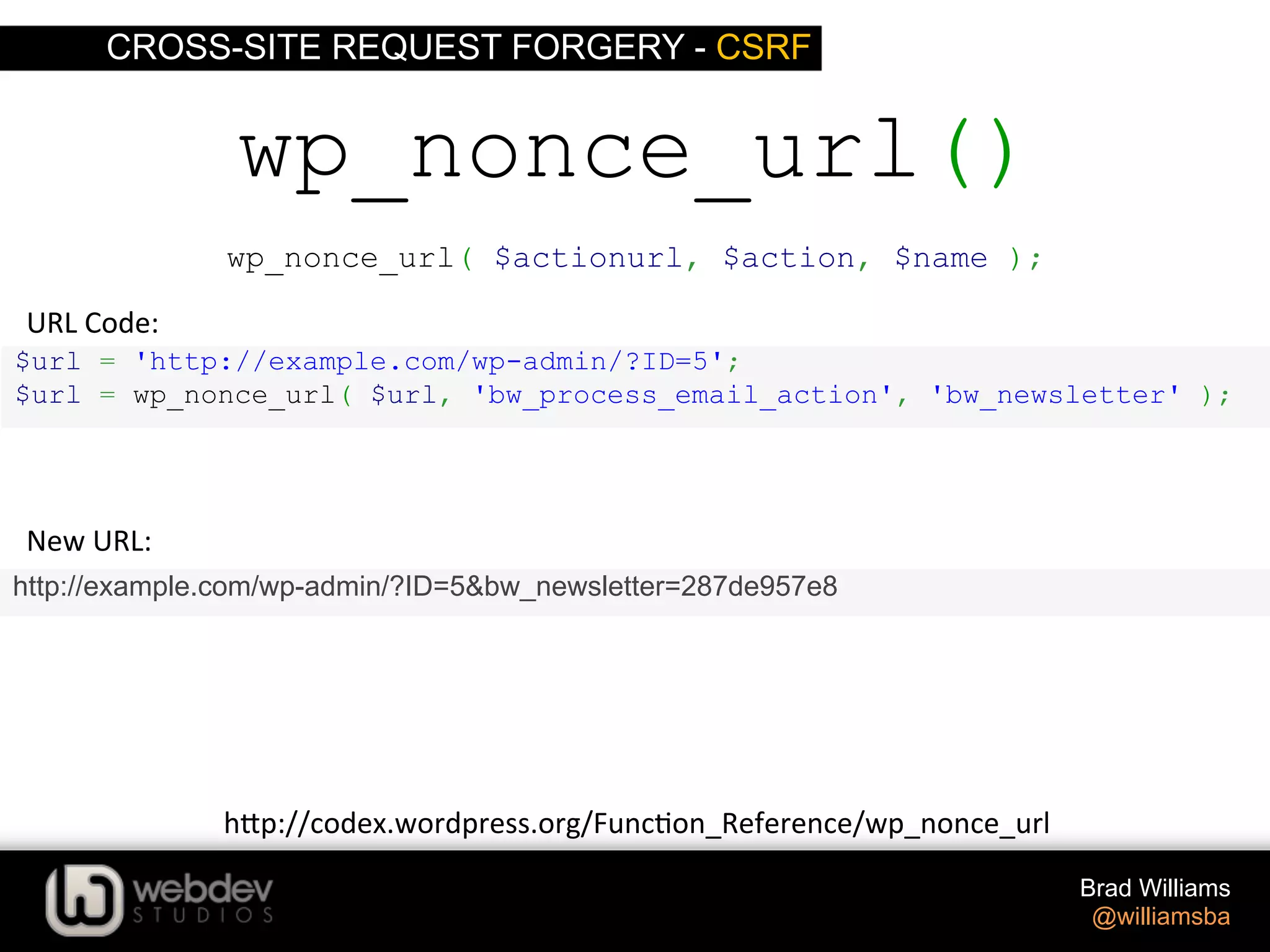
![CROSS-SITE REQUEST FORGERY - CSRF Brad Williams @williamsba if ( isset( $_GET[ID'] ) ) { check_admin_referer( 'bw_process_email_action', 'bw_newsletter' ); //process data } wp_nonce_url() Processing Code: h-p://codex.wordpress.org/Func>on_Reference/check_admin_referer](https://image.slidesharecdn.com/writing-secure-wordpress-code-140803121344-phpapp02/75/Writing-Secure-WordPress-Code-WordCamp-NYC-2014-55-2048.jpg)