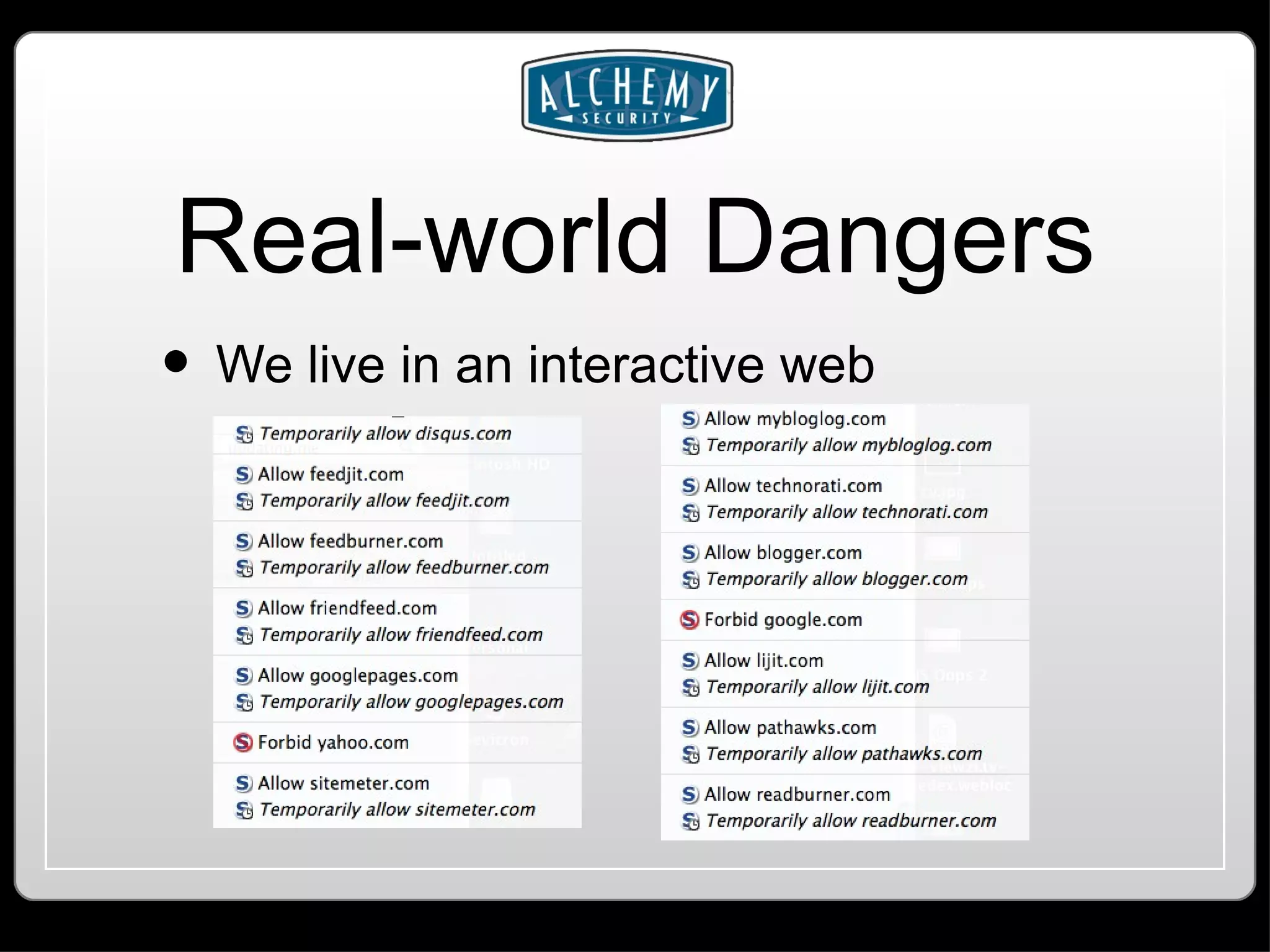
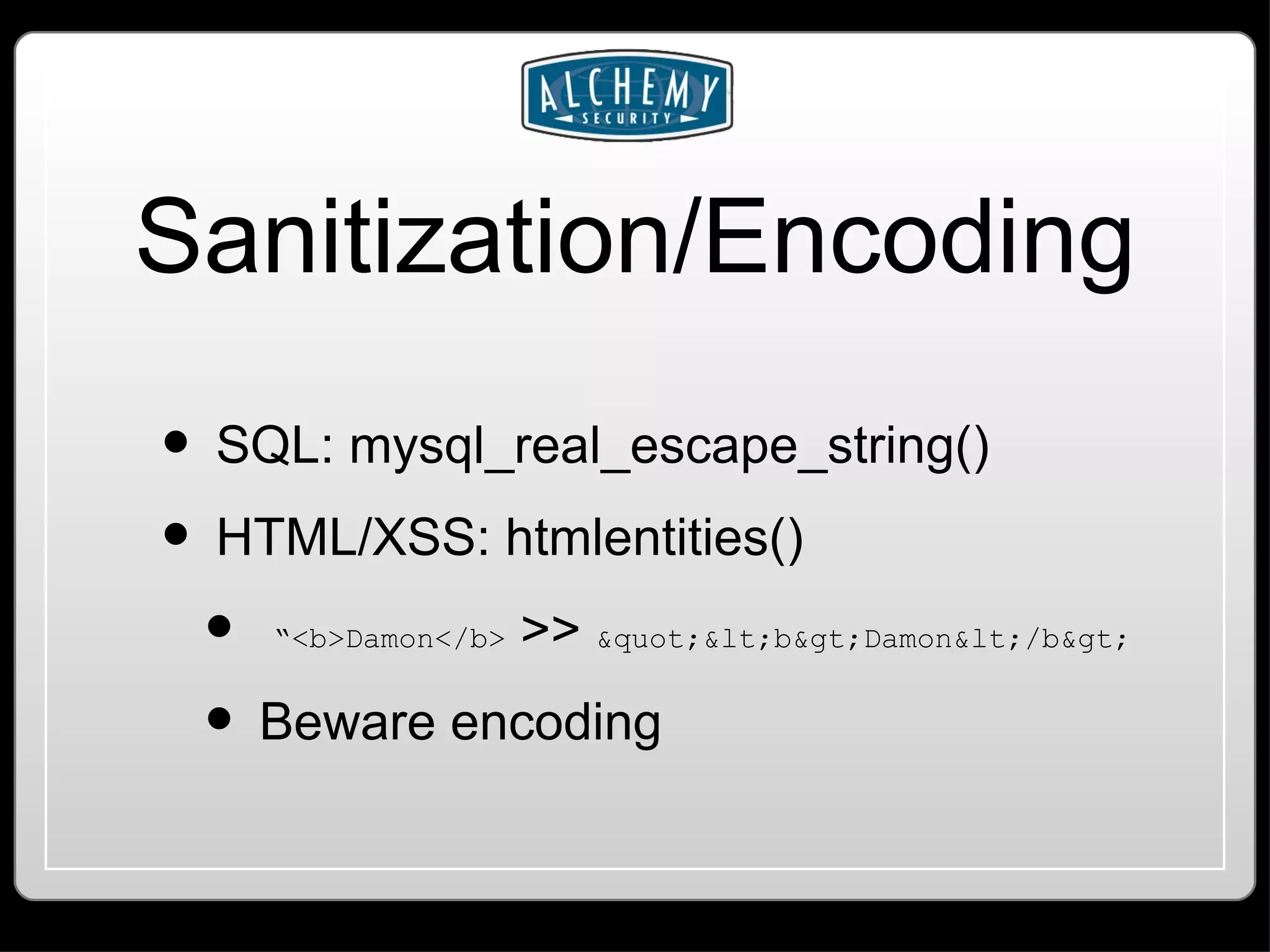
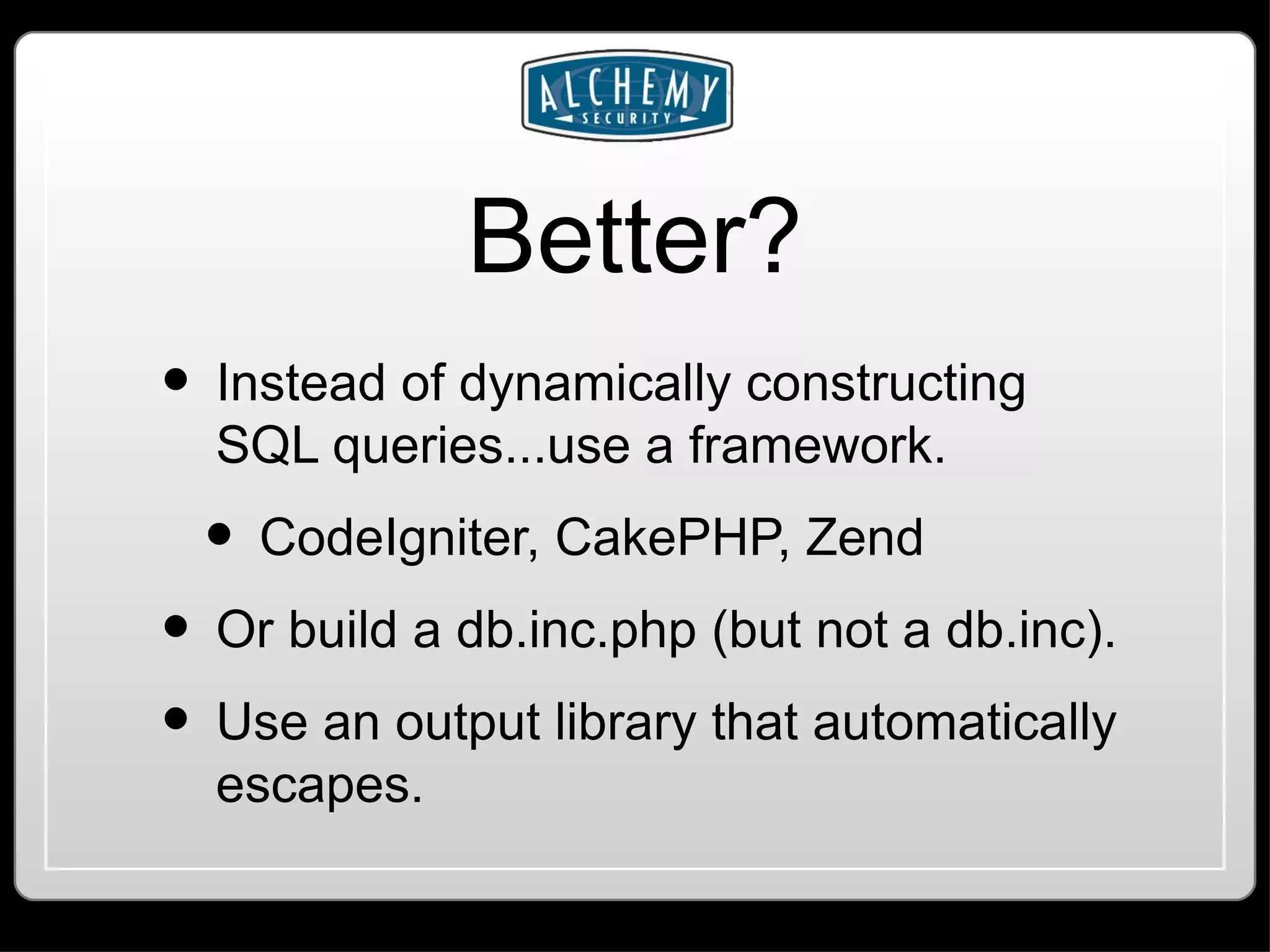
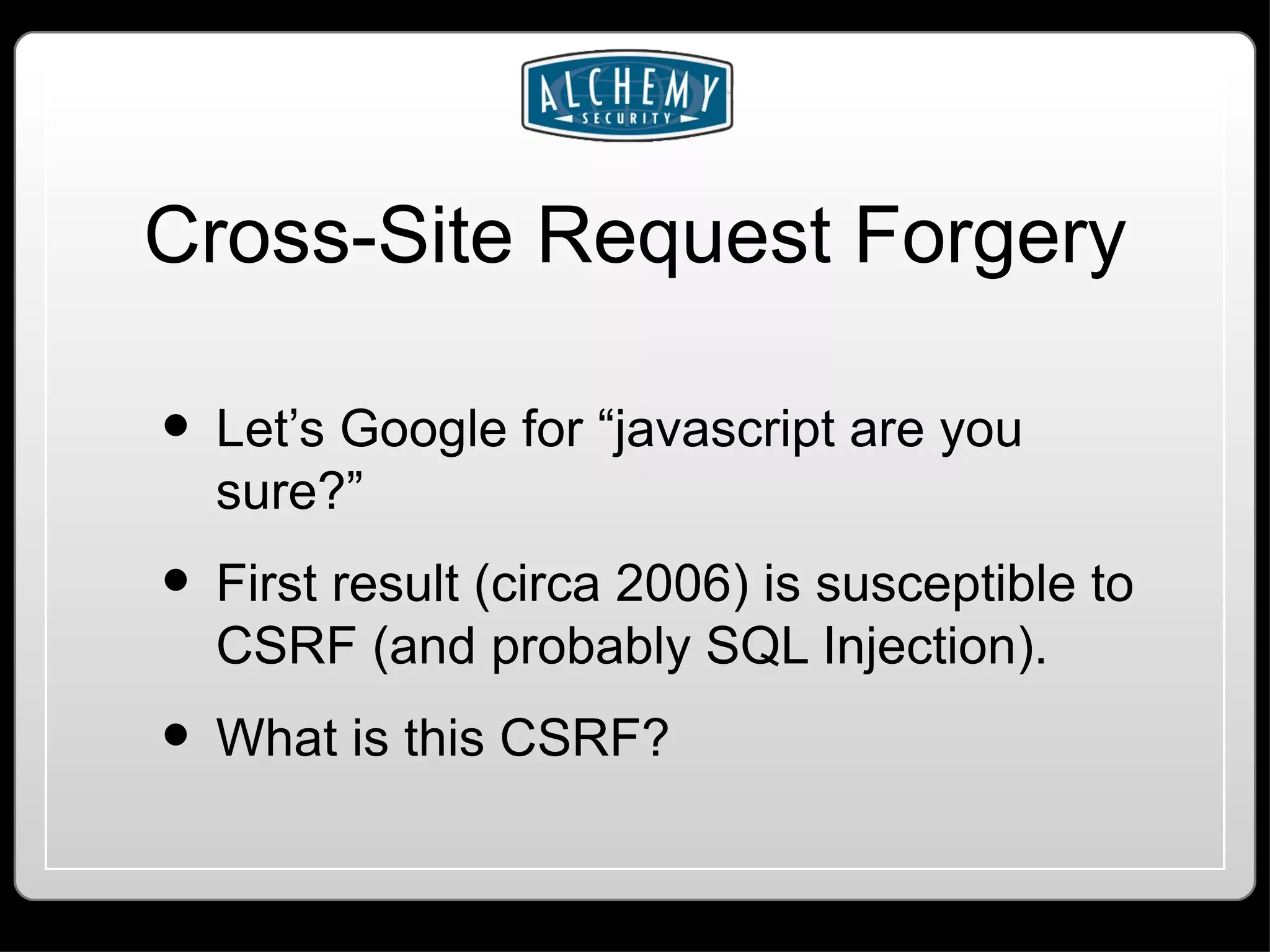
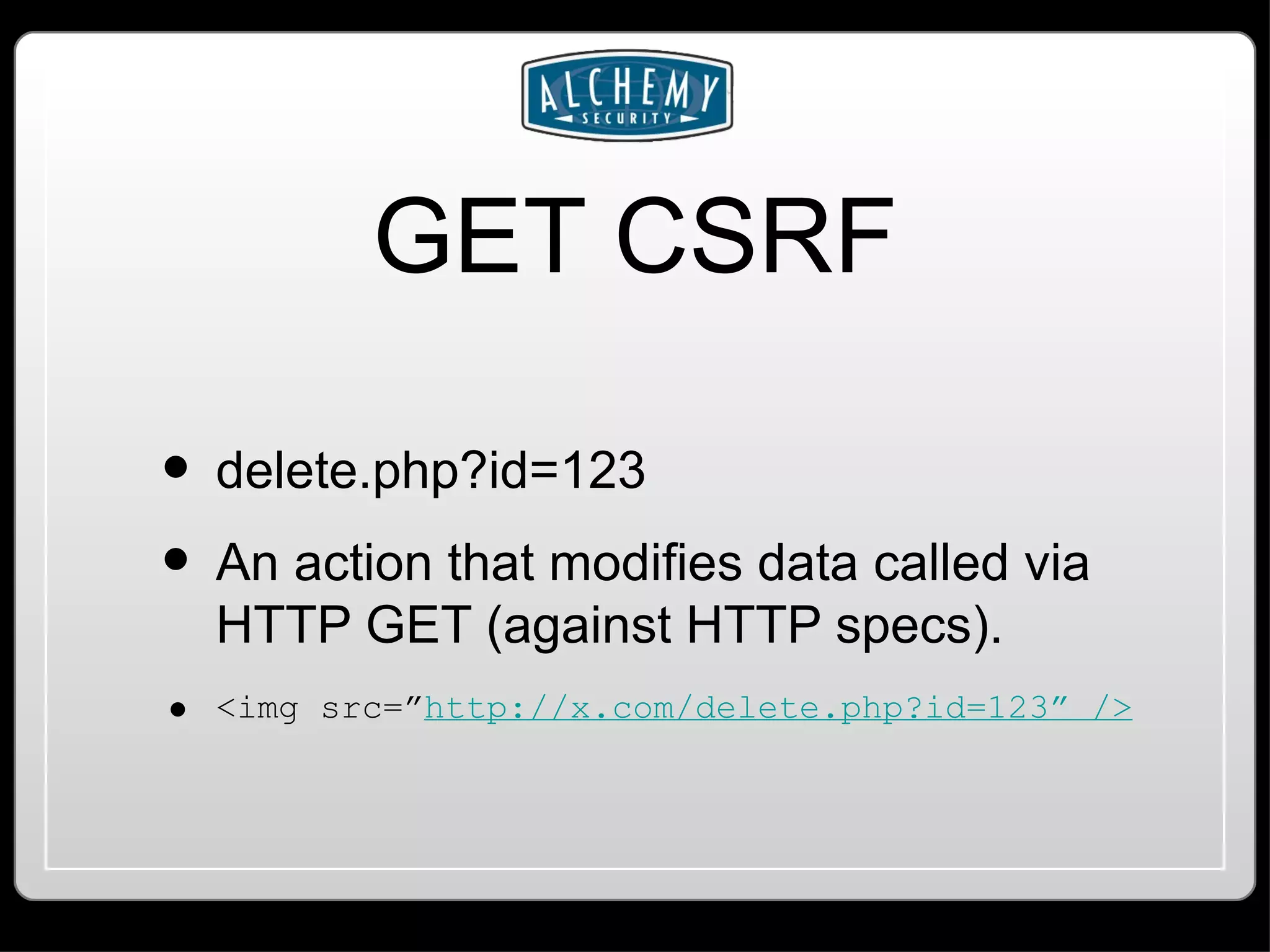
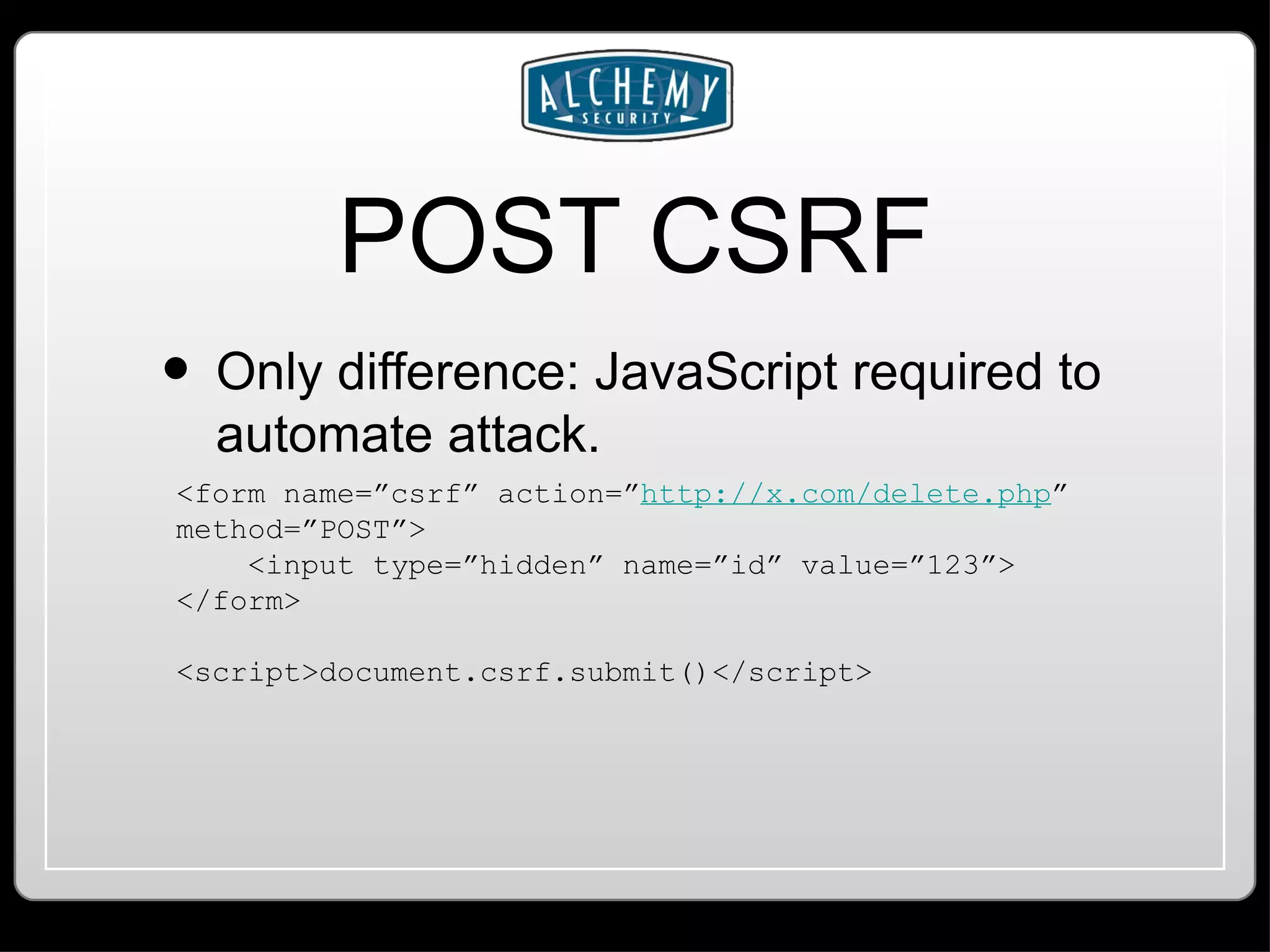
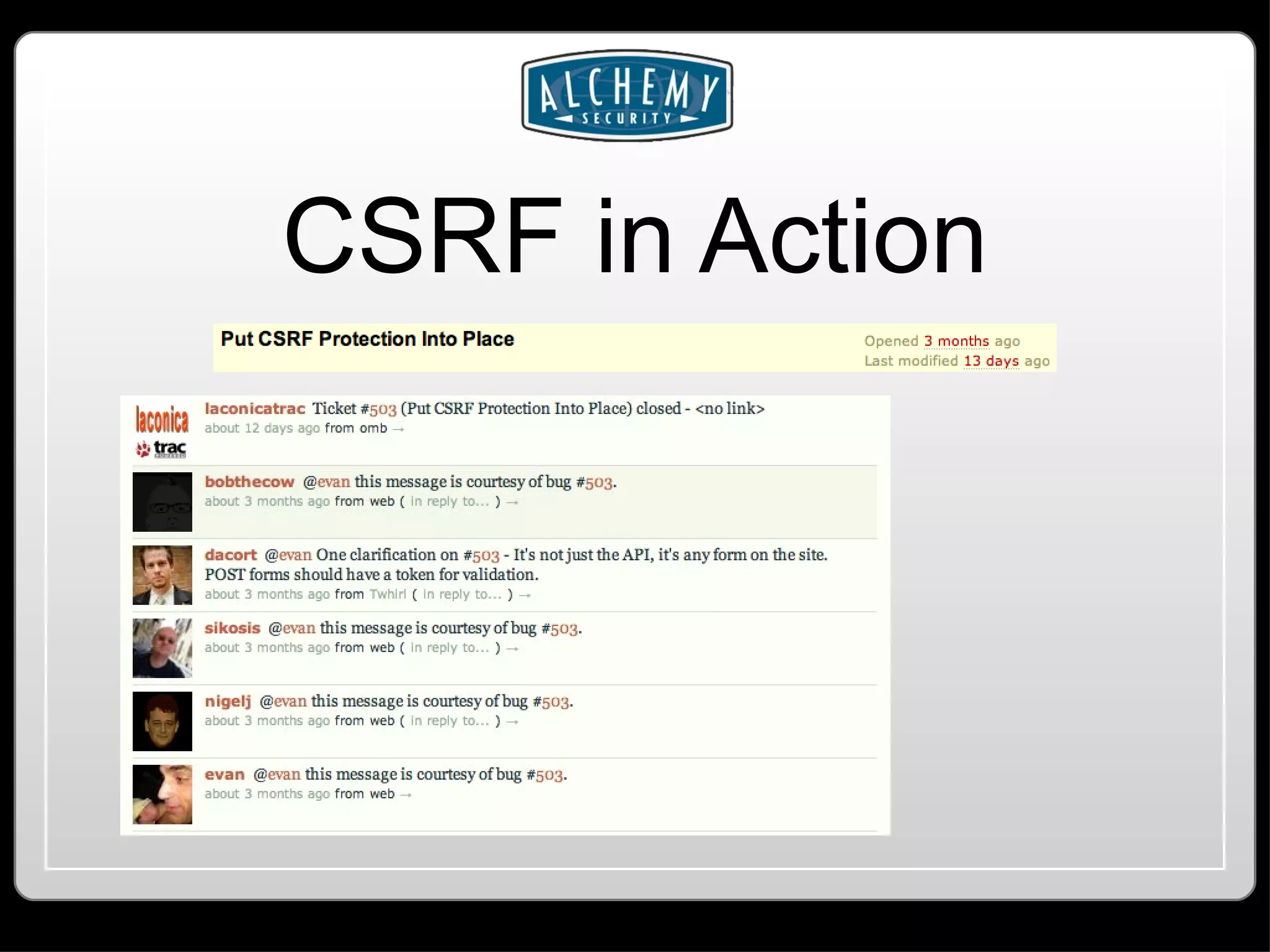
This document summarizes common web application vulnerabilities like SQL injection and cross-site scripting (XSS) for PHP applications. It provides examples of each vulnerability and discusses mitigation strategies like input sanitization, encoding output, and using security frameworks. It also covers other risks like cross-site request forgery (CSRF) and the importance of secure server configurations.


![SQL Injection $sql = “SELECT * FROM users WHERE username = ‘“ . $_POST[‘username’] . “‘ AND password = ‘“ . $_POST[‘password’] . “‘“; What if username is: “dpc’ or ‘a’=’a” ? ... username = ‘ dpc’ or ‘a’=’a ‘ ...](https://image.slidesharecdn.com/phpug-presentation-1228431880253979-8/75/PHPUG-Presentation-4-2048.jpg)




![Input Sanitization Fail exec(mysql_escape_string($_GET[‘var’])) Problem #1: mysql_escape_string is deprecated. Problem #2: MySQL escape does not make it safe for exec(). ?? preg_match("/.jpe?g$/i", $var) exec ( "convert '" . mysql_escape_string ( $path ) . "' /tmp/'" . mysql_escape_string ( basename ( $path )). "'.png" );](https://image.slidesharecdn.com/phpug-presentation-1228431880253979-8/75/PHPUG-Presentation-14-2048.jpg)
![Bug Hunting Data Inputs $_GET, $_POST, $_REQUEST $_SERVER[‘QUERY_STRING’] $_SERVER[‘PHP_SELF’] $_COOKIE Shell commands: exec()](https://image.slidesharecdn.com/phpug-presentation-1228431880253979-8/75/PHPUG-Presentation-17-2048.jpg)



![Thanks [email_address] http://xkcd.com/327/](https://image.slidesharecdn.com/phpug-presentation-1228431880253979-8/75/PHPUG-Presentation-27-2048.jpg)