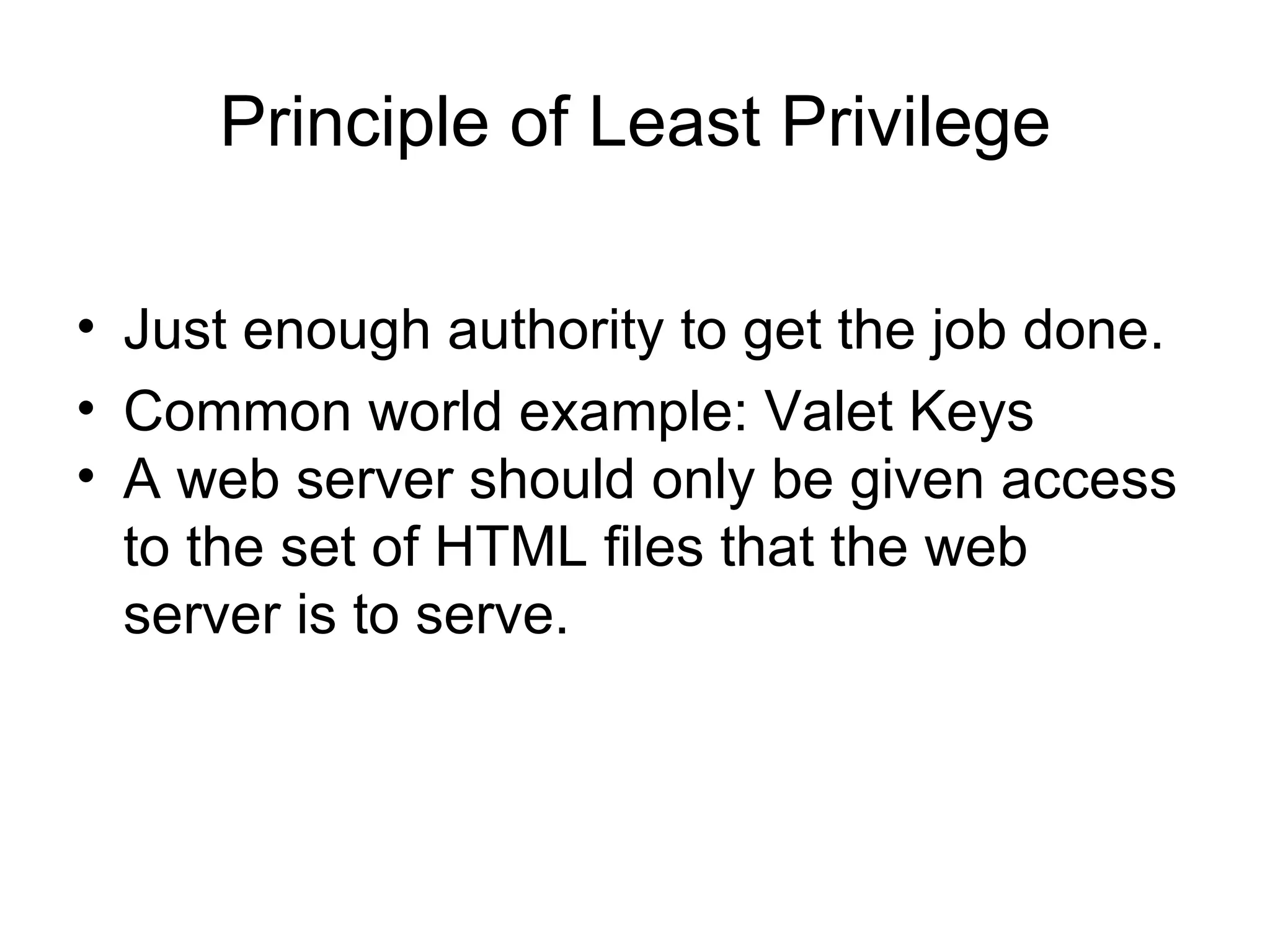
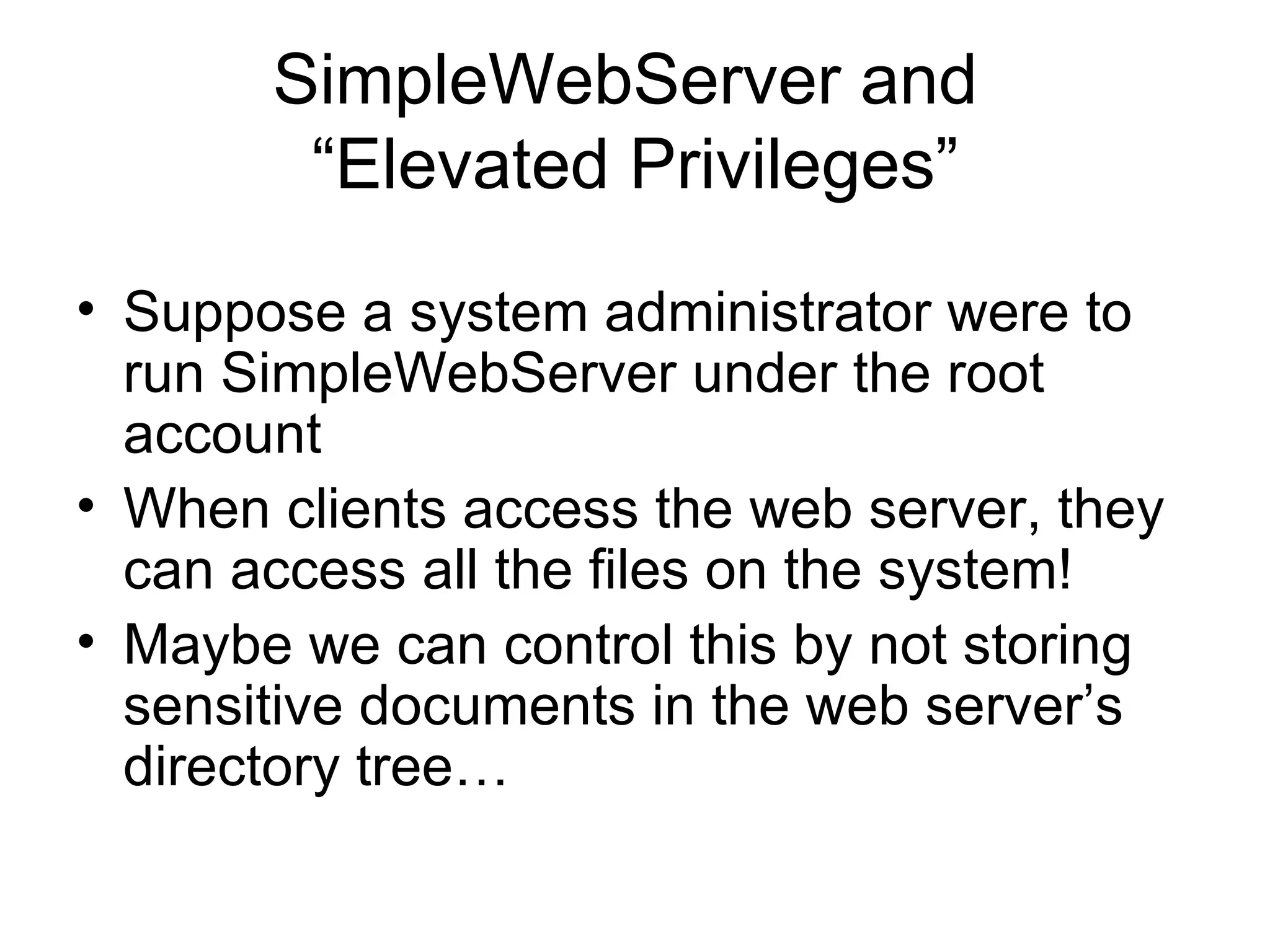
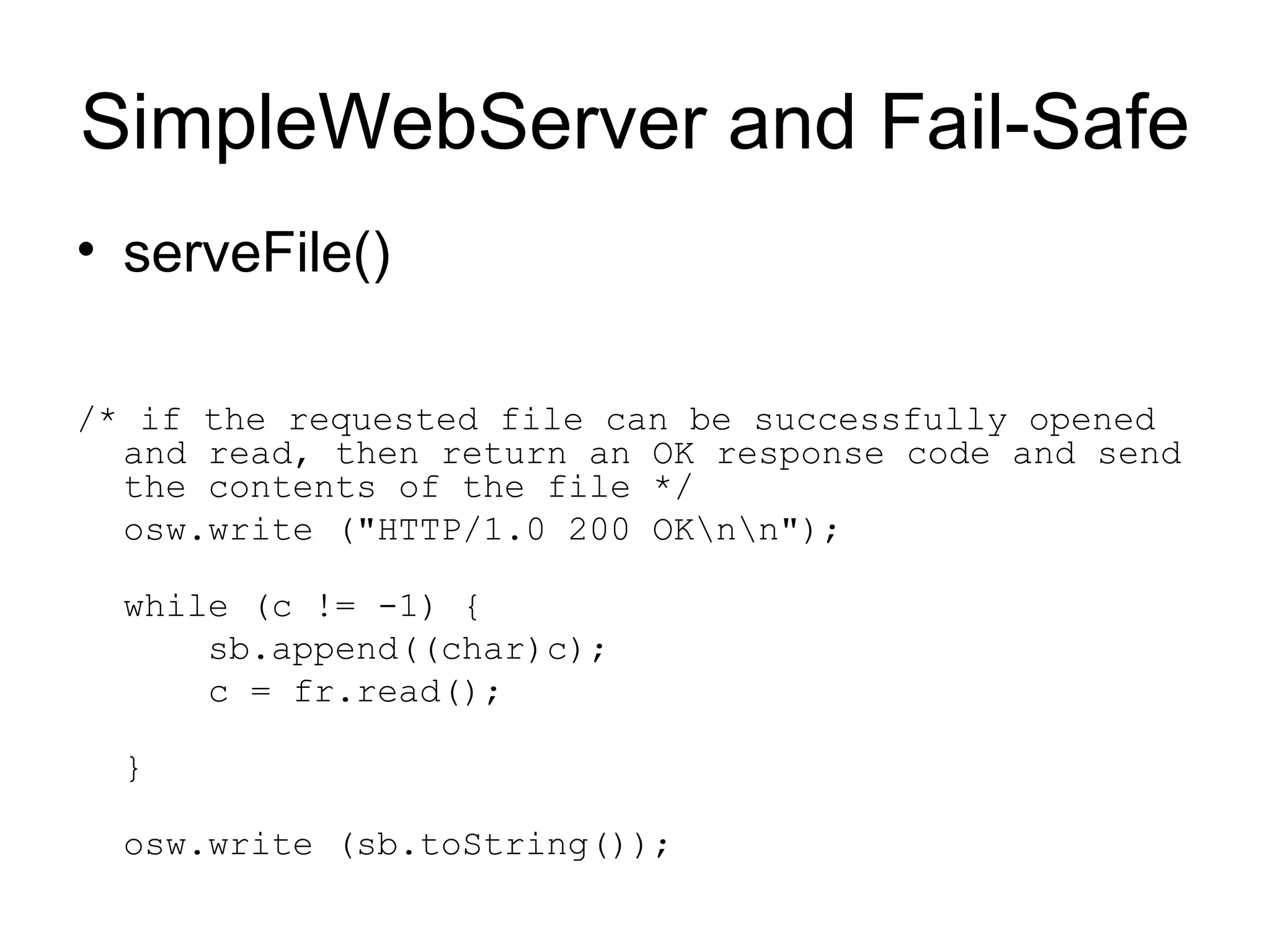
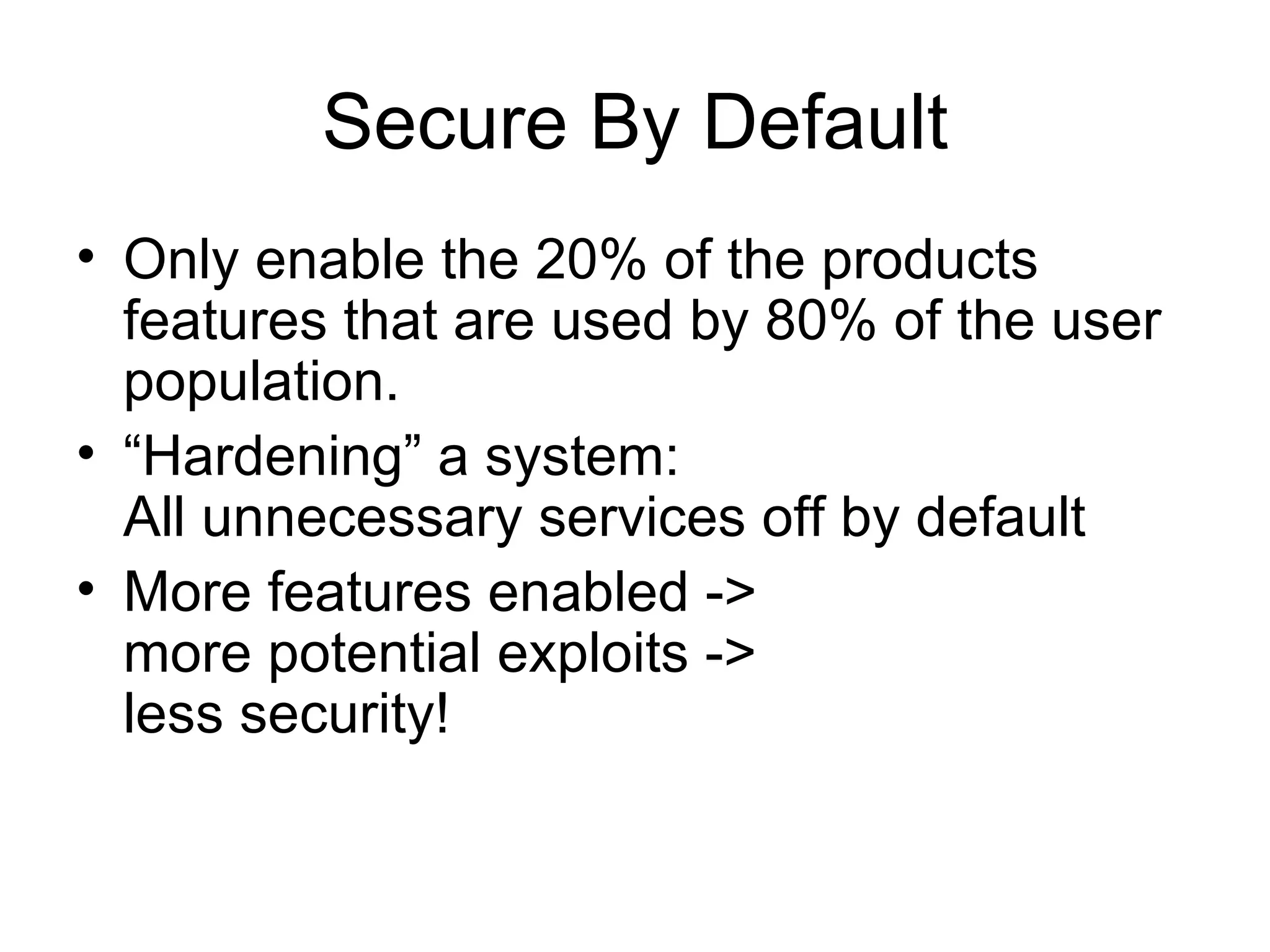
The document discusses several security design principles for software including: - Least privilege - Give users and processes only the minimum permissions needed to perform their tasks - Defense in depth - Use multiple layers of security instead of just one - Secure the weakest link - Focus on common weak points like passwords, firewalls, and buffer overflows - Fail-safe stance - Assume failures will occur and plan for them by denying access by default if something fails - Secure by default - Only enable necessary features and harden the system by disabling unnecessary services - Simplicity - Complex software is more likely to have security holes, so keep it simple - Usability - Design with security in mind by default so users don