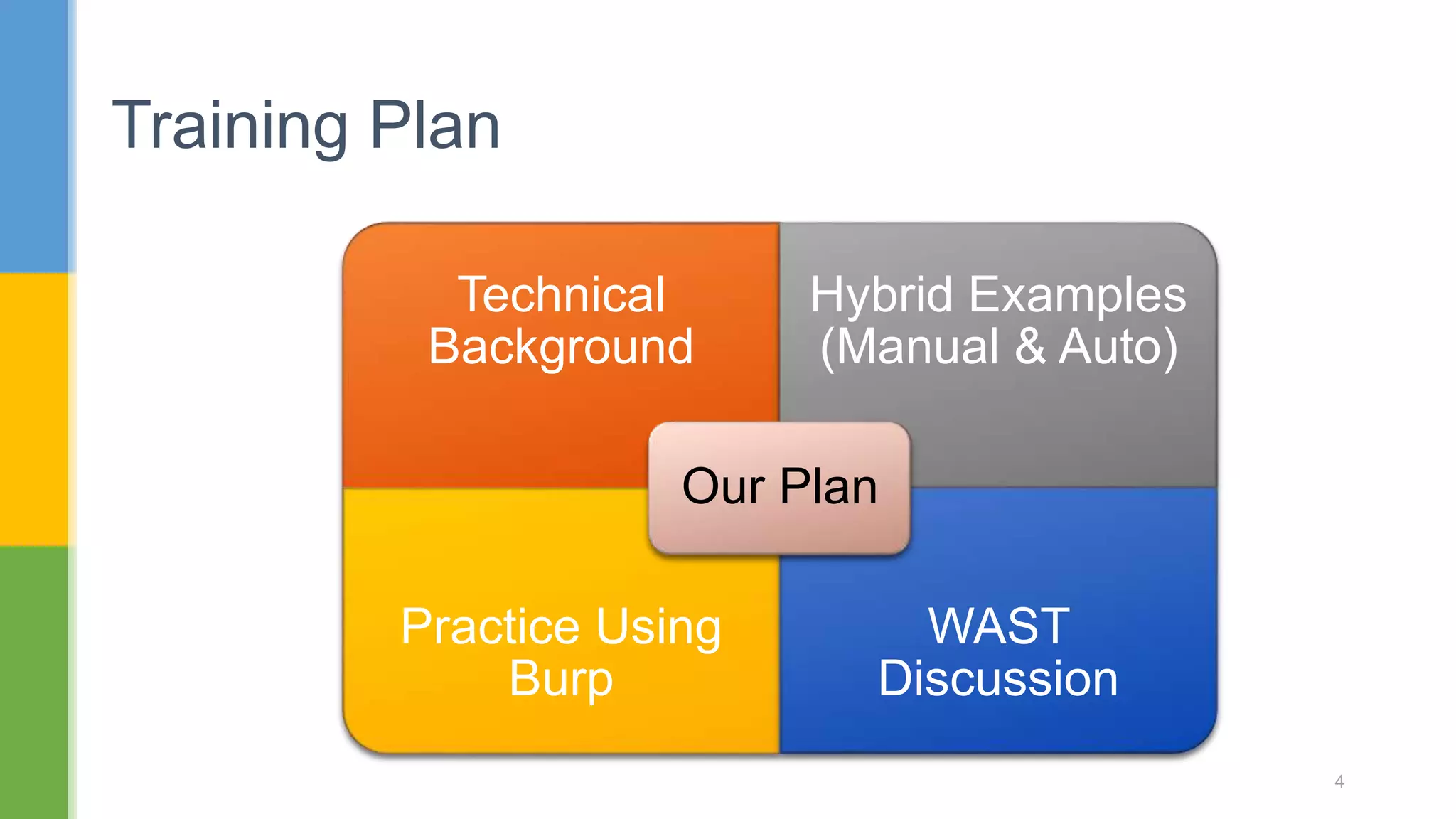
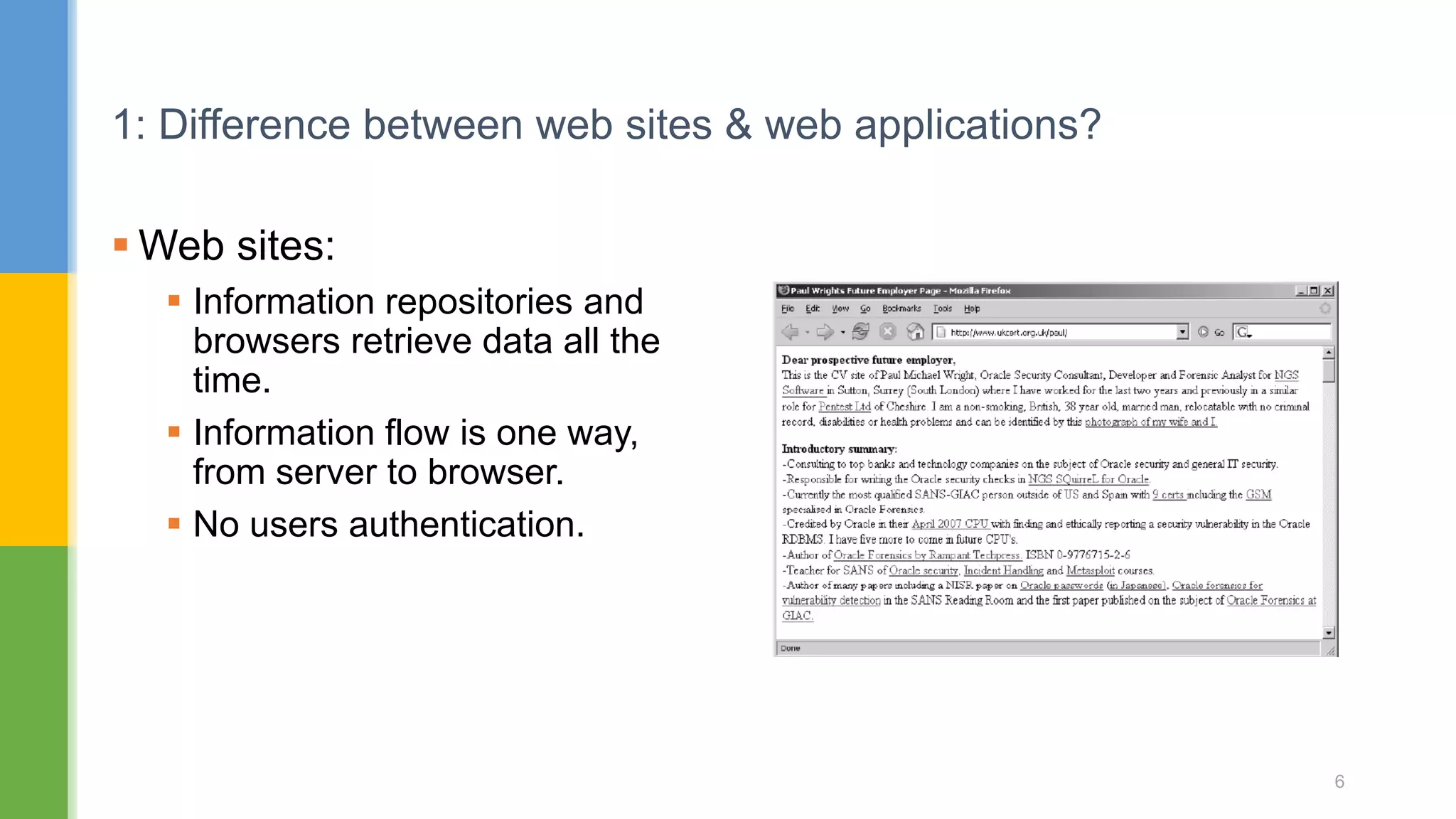
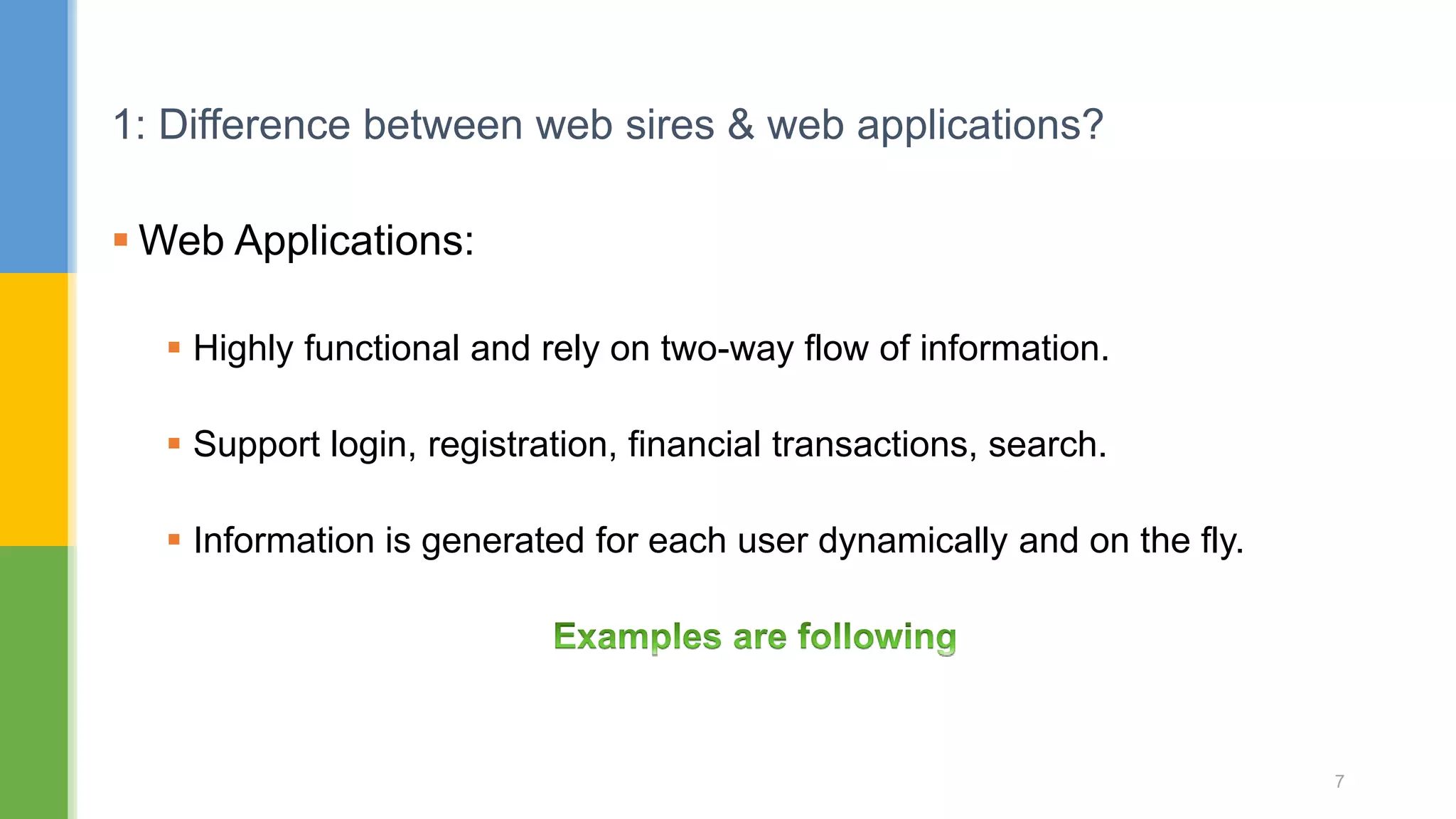
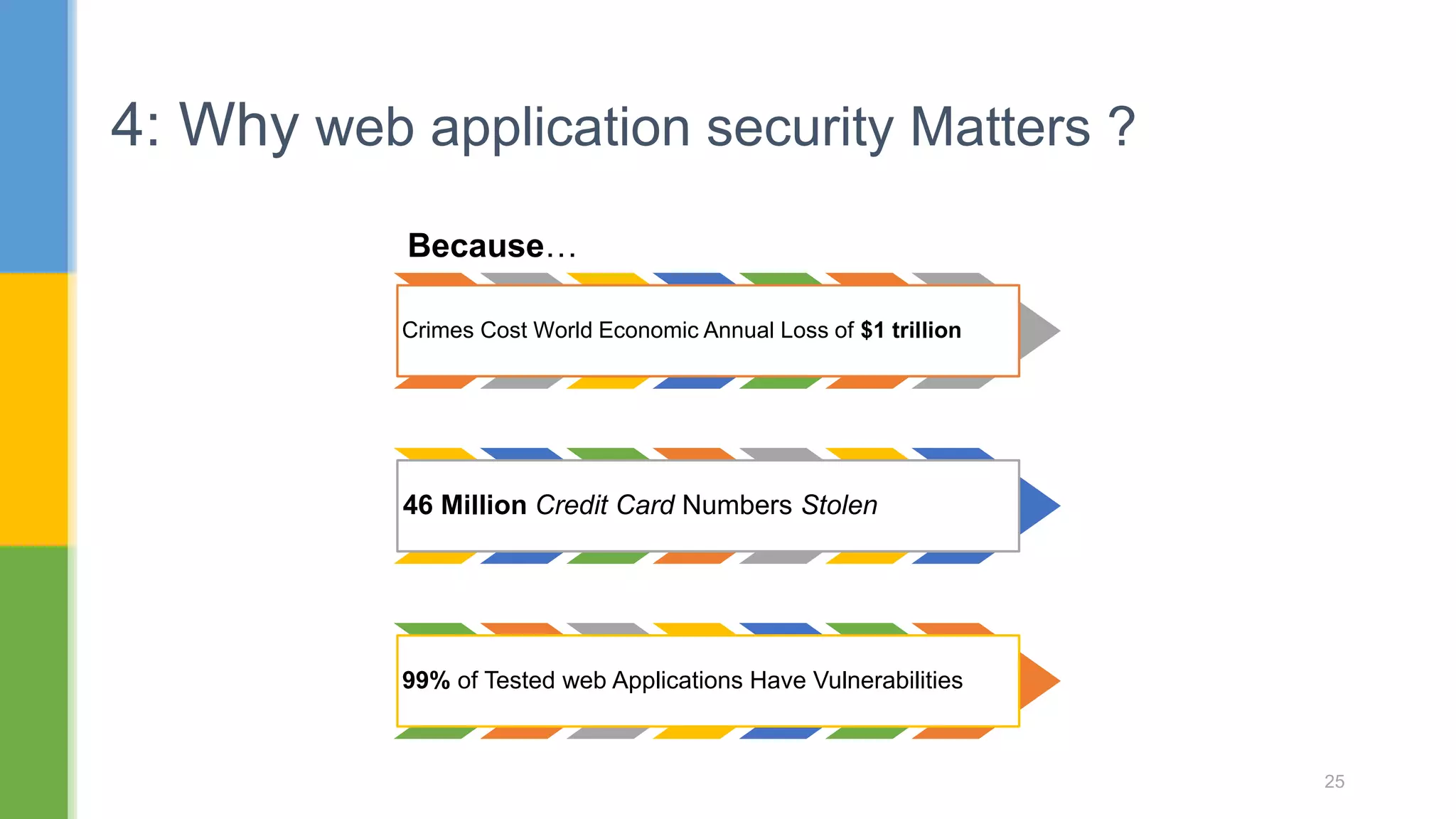
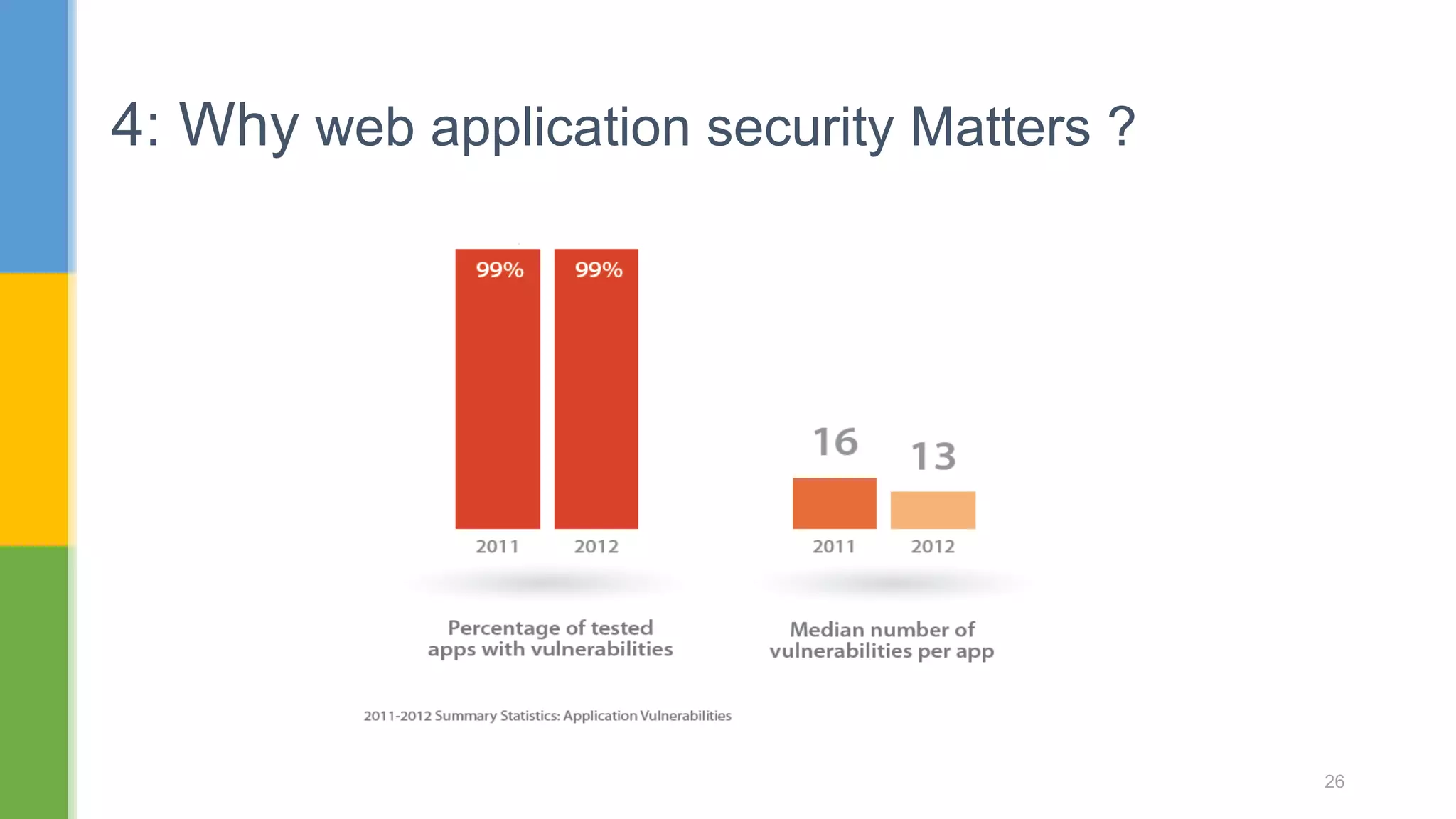
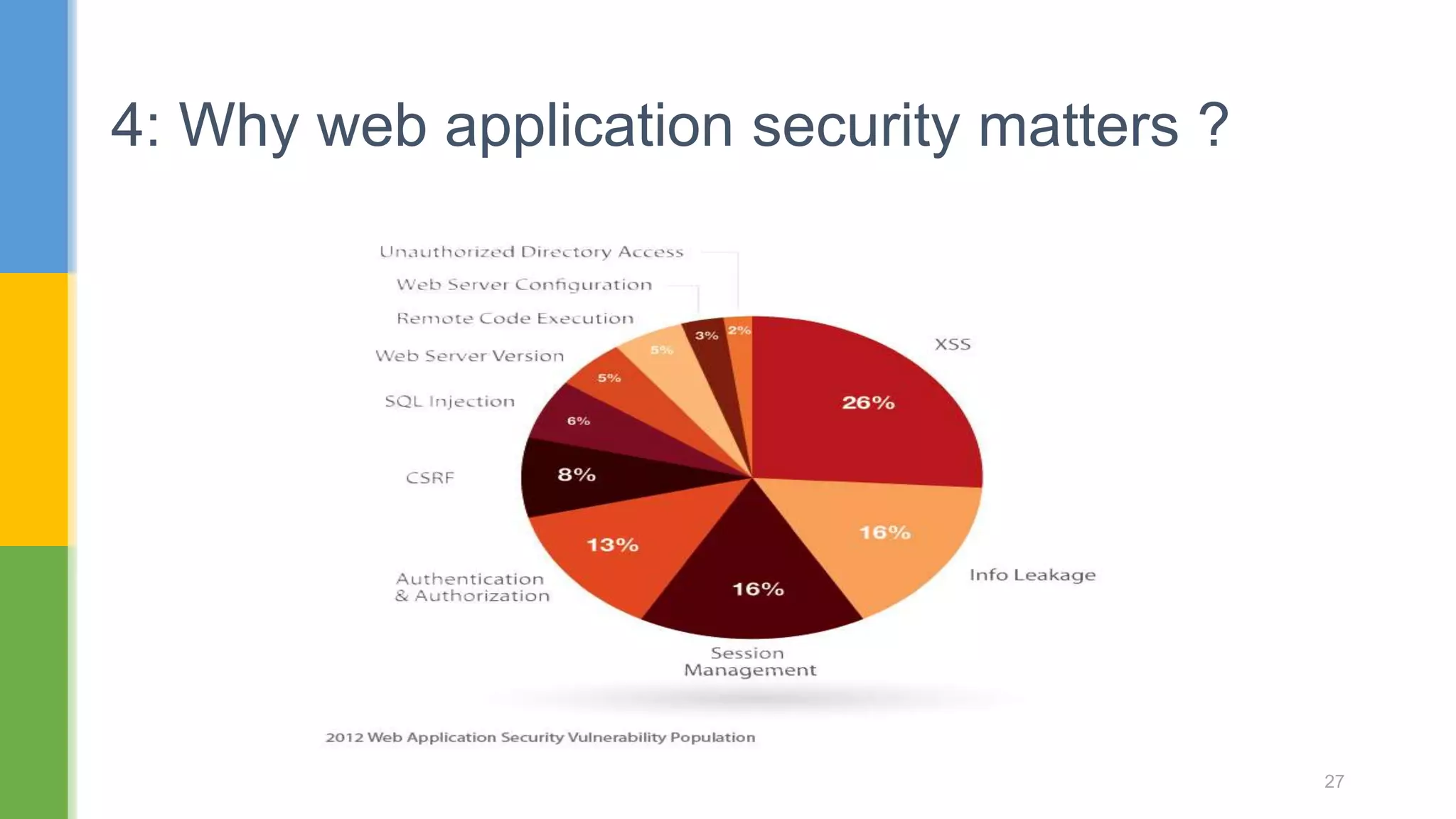
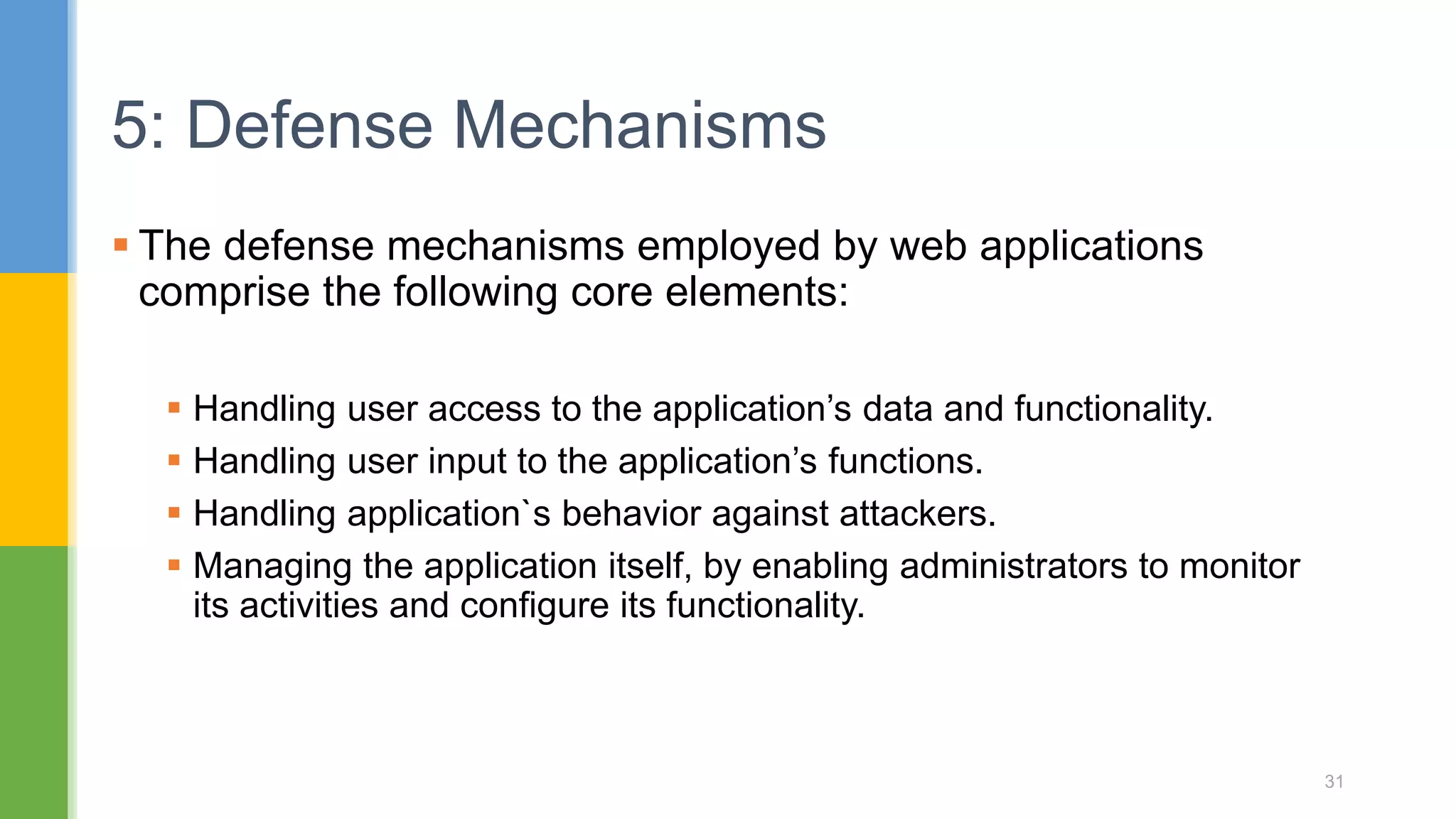
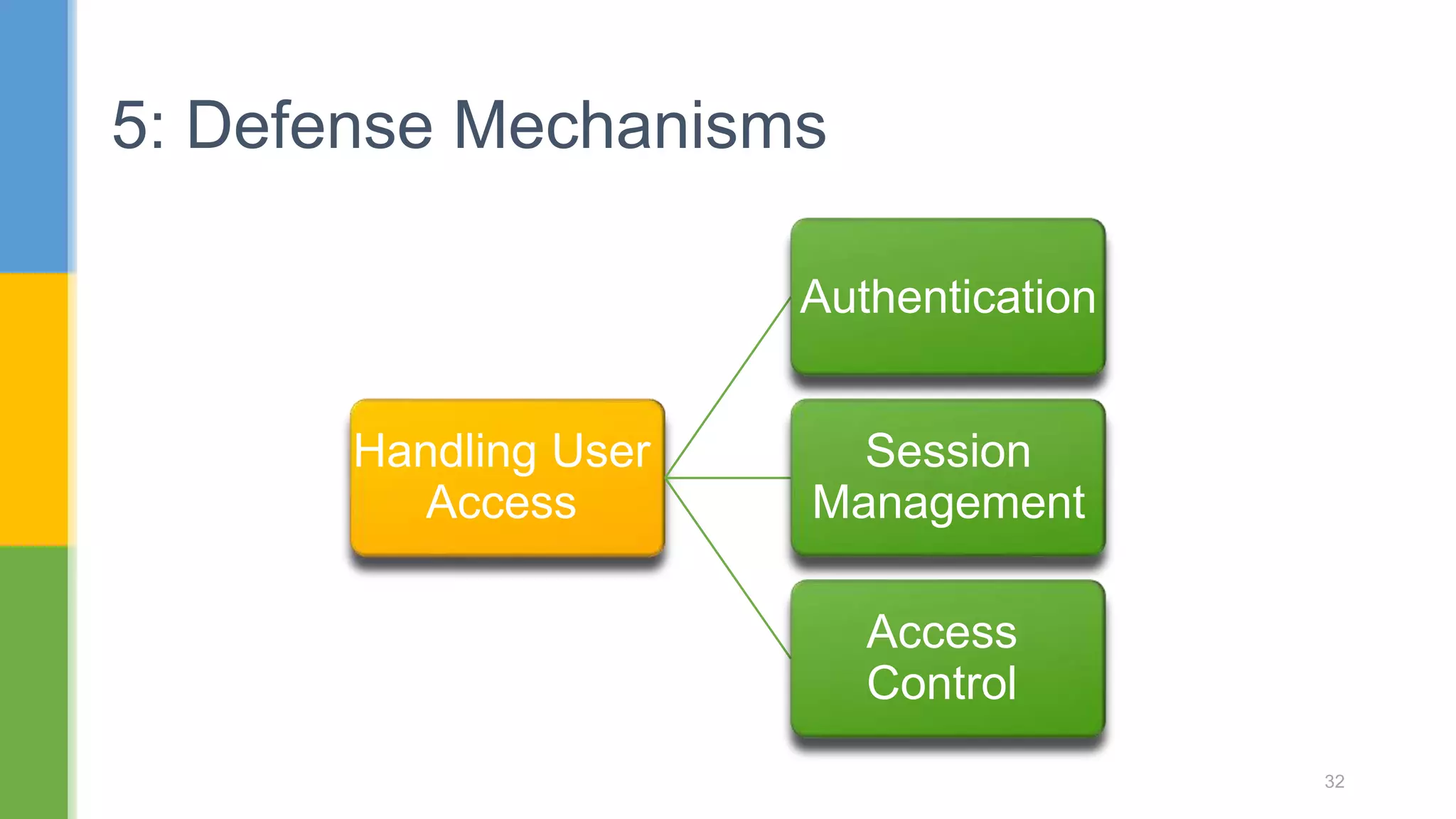
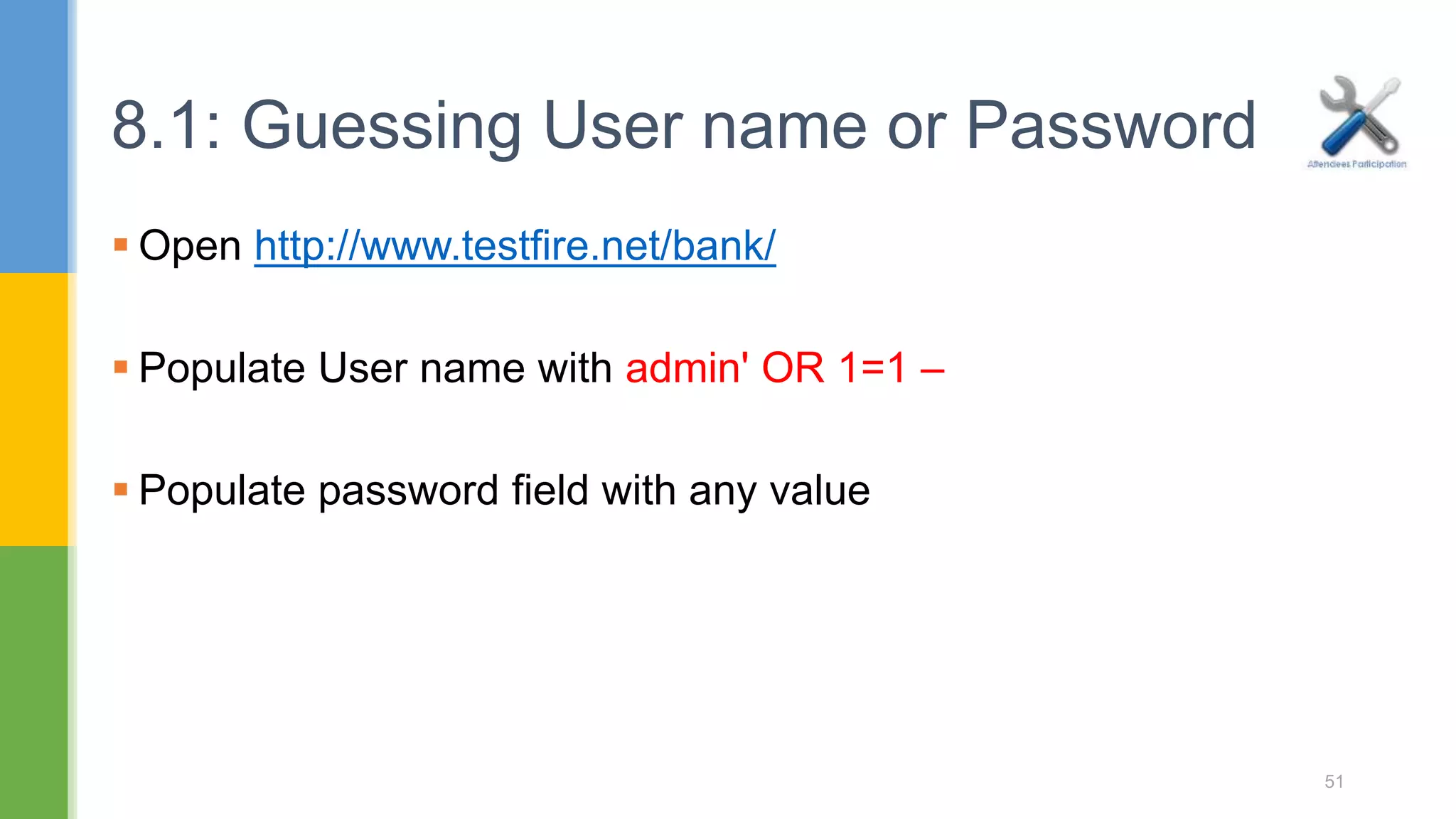
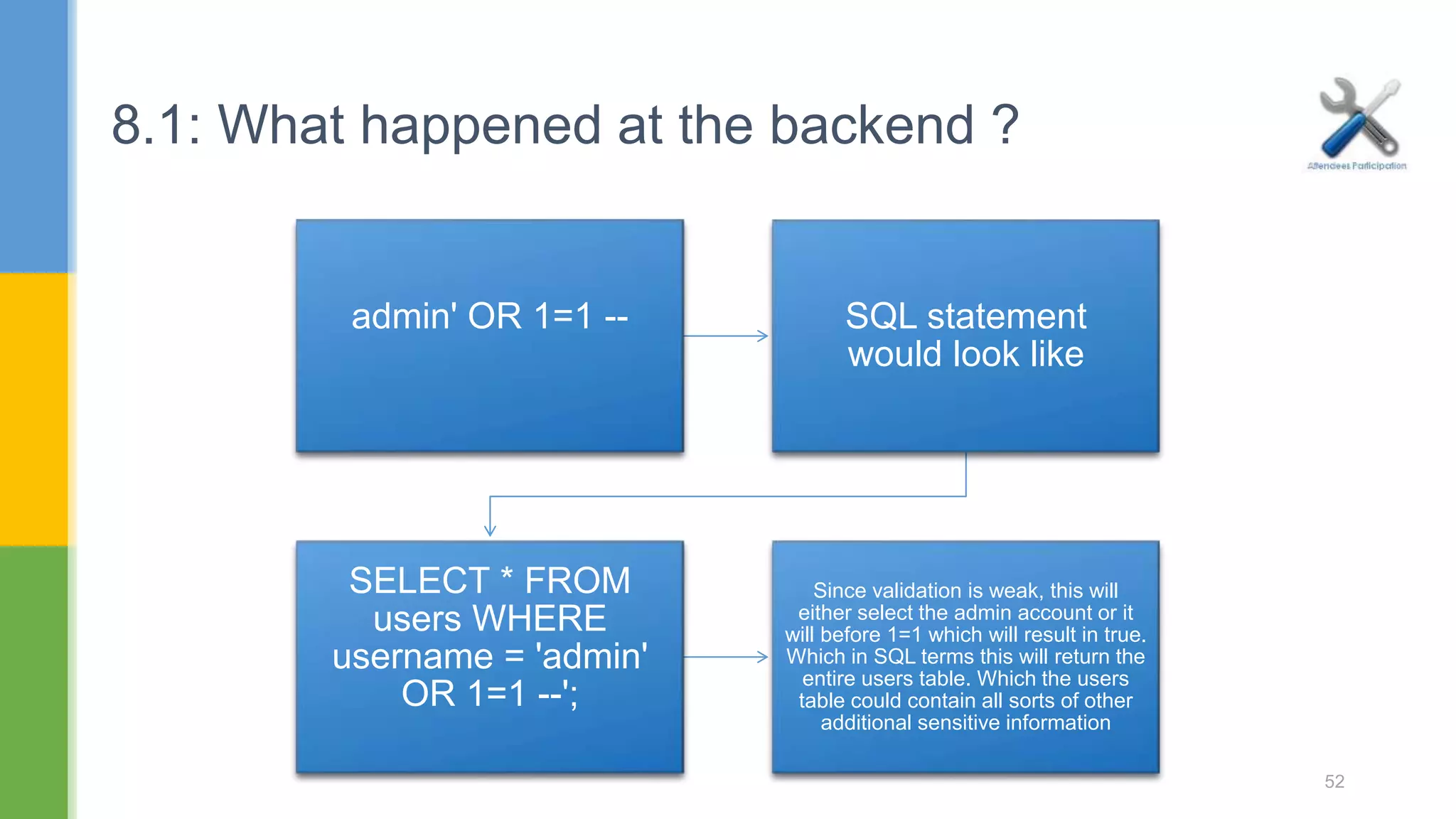
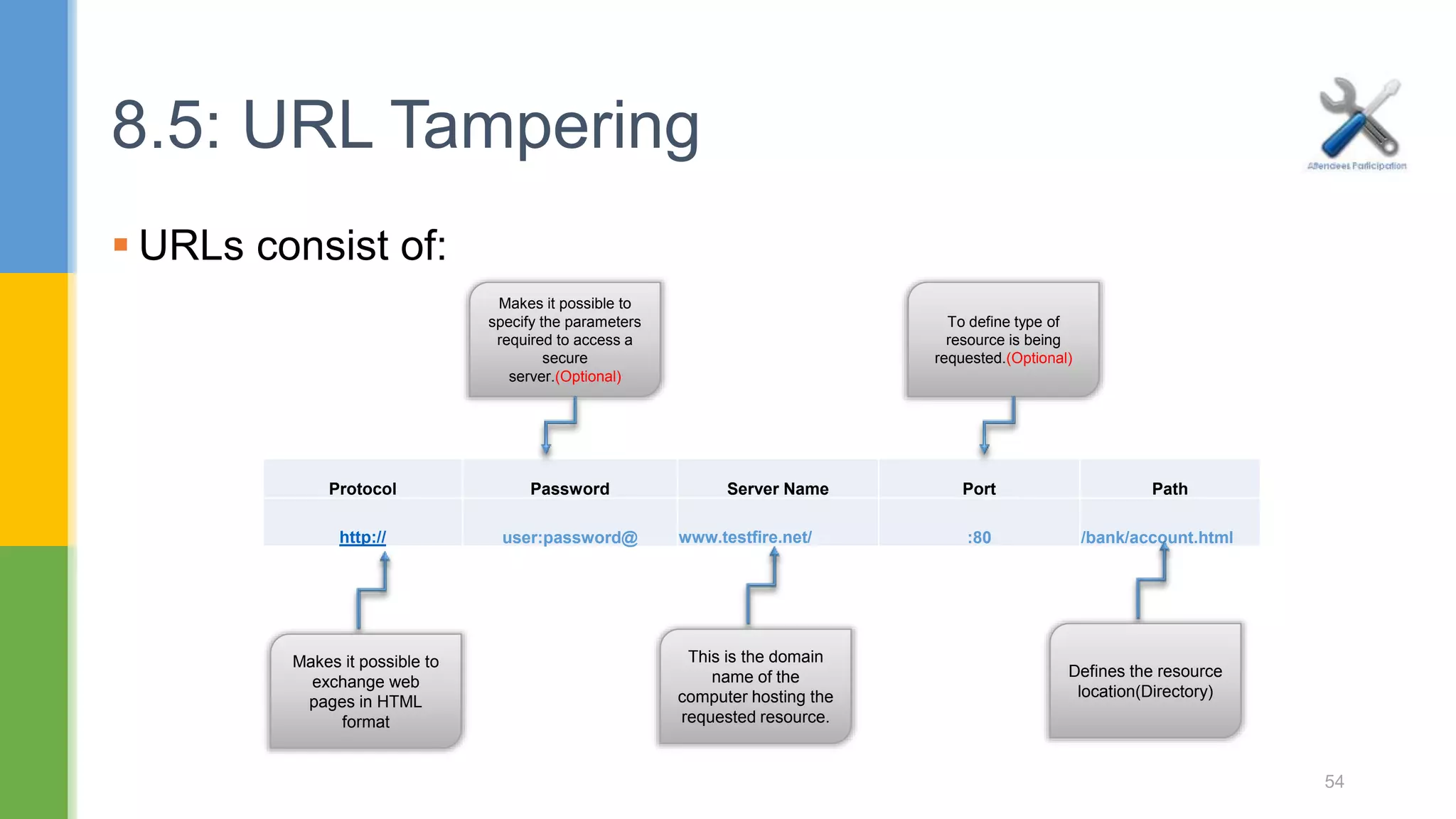
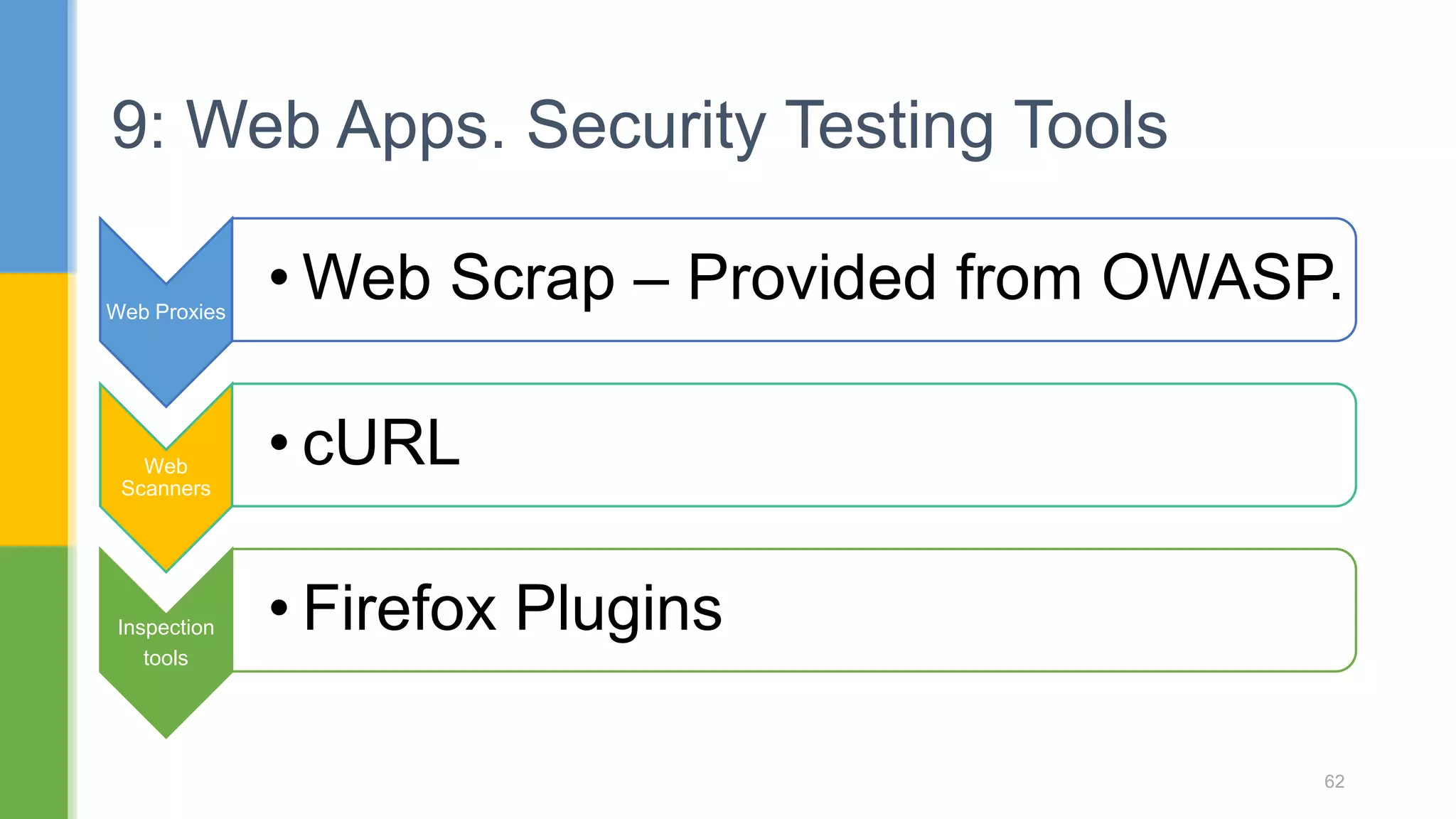
The document discusses web application security testing techniques. It covers topics like the difference between web sites and applications, security definitions, vulnerabilities like SQL injection and XSS, defense mechanisms, and tools for security testing like Burp Suite. The agenda includes discussing concepts, designing test cases, and practicing security testing techniques manually and using automated tools.


![ Its one of software product attributes that bear on its ability to prevent unauthorized access, weather accidental or deliberate to programs and data. [ISO 9126 – ISTQB Glossary] 2: What is security ? 9](https://image.slidesharecdn.com/webapplicationssecurity-conferenceslides-170828073416/75/Web-applications-security-conference-slides-9-2048.jpg)
![ A non-functional testing type, to determine the security of the software product. [ISO 9126 – ISTQB Glossary] 2.1: What is security testing ? 10](https://image.slidesharecdn.com/webapplicationssecurity-conferenceslides-170828073416/75/Web-applications-security-conference-slides-10-2048.jpg)










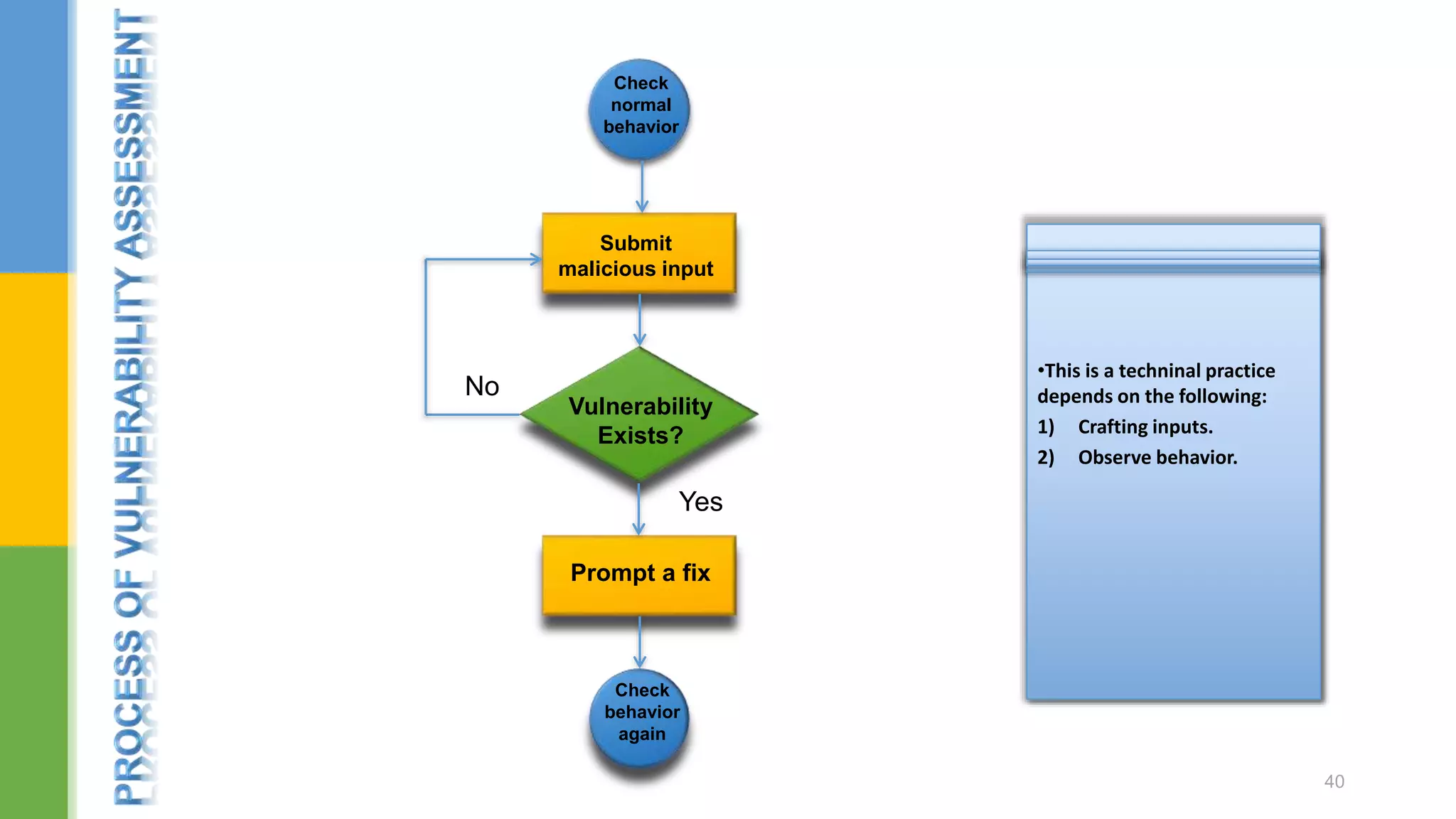




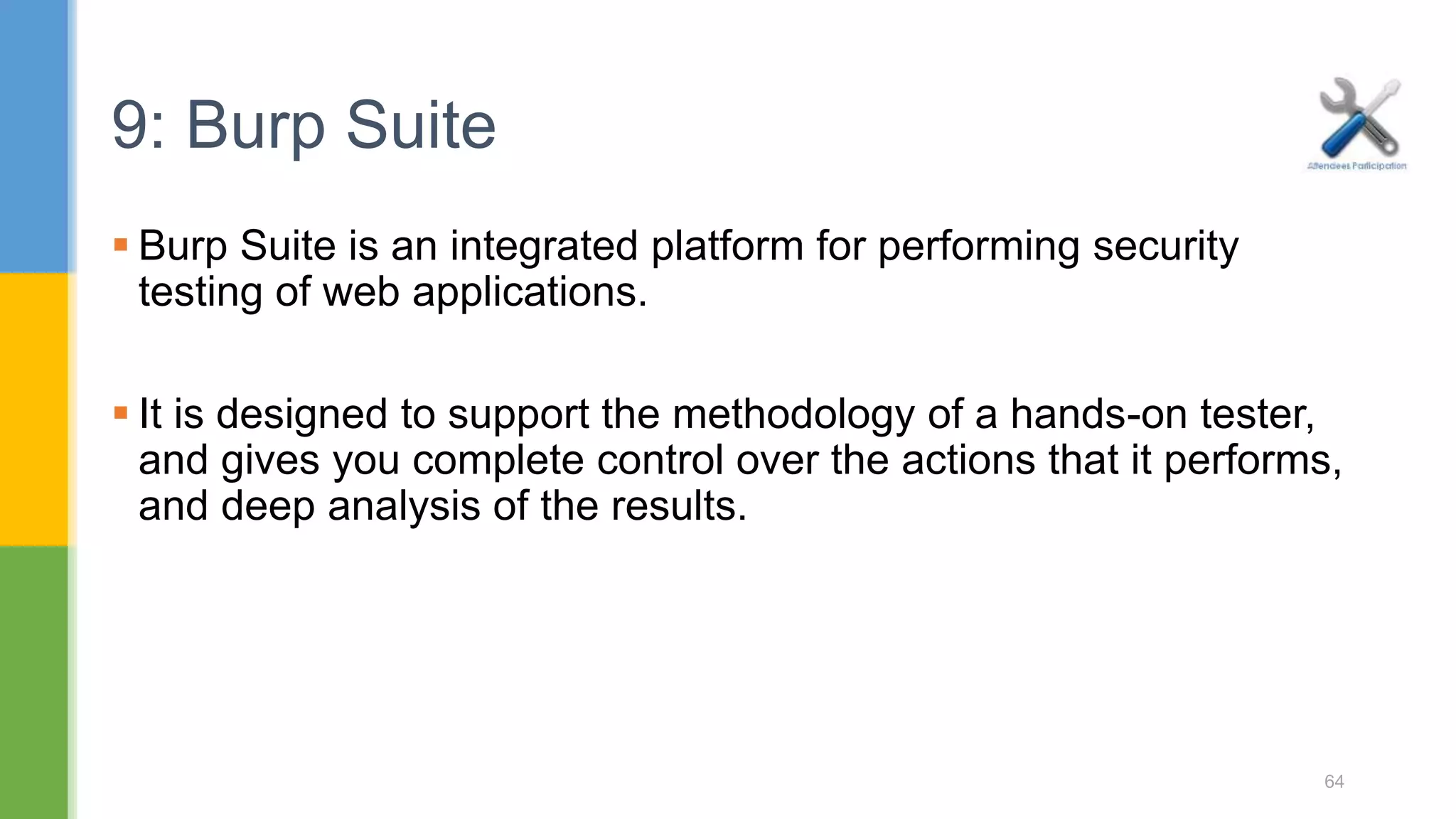
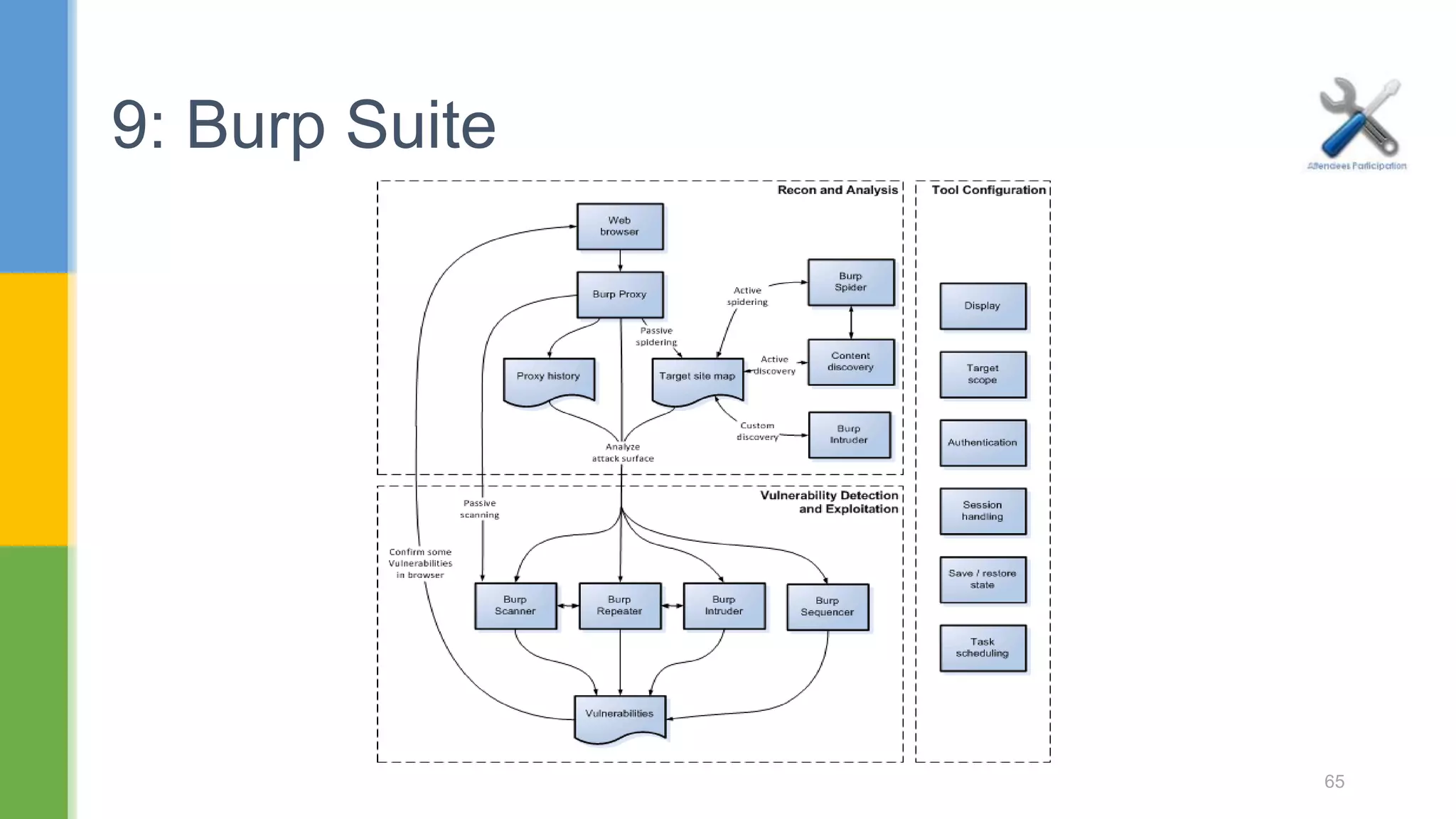
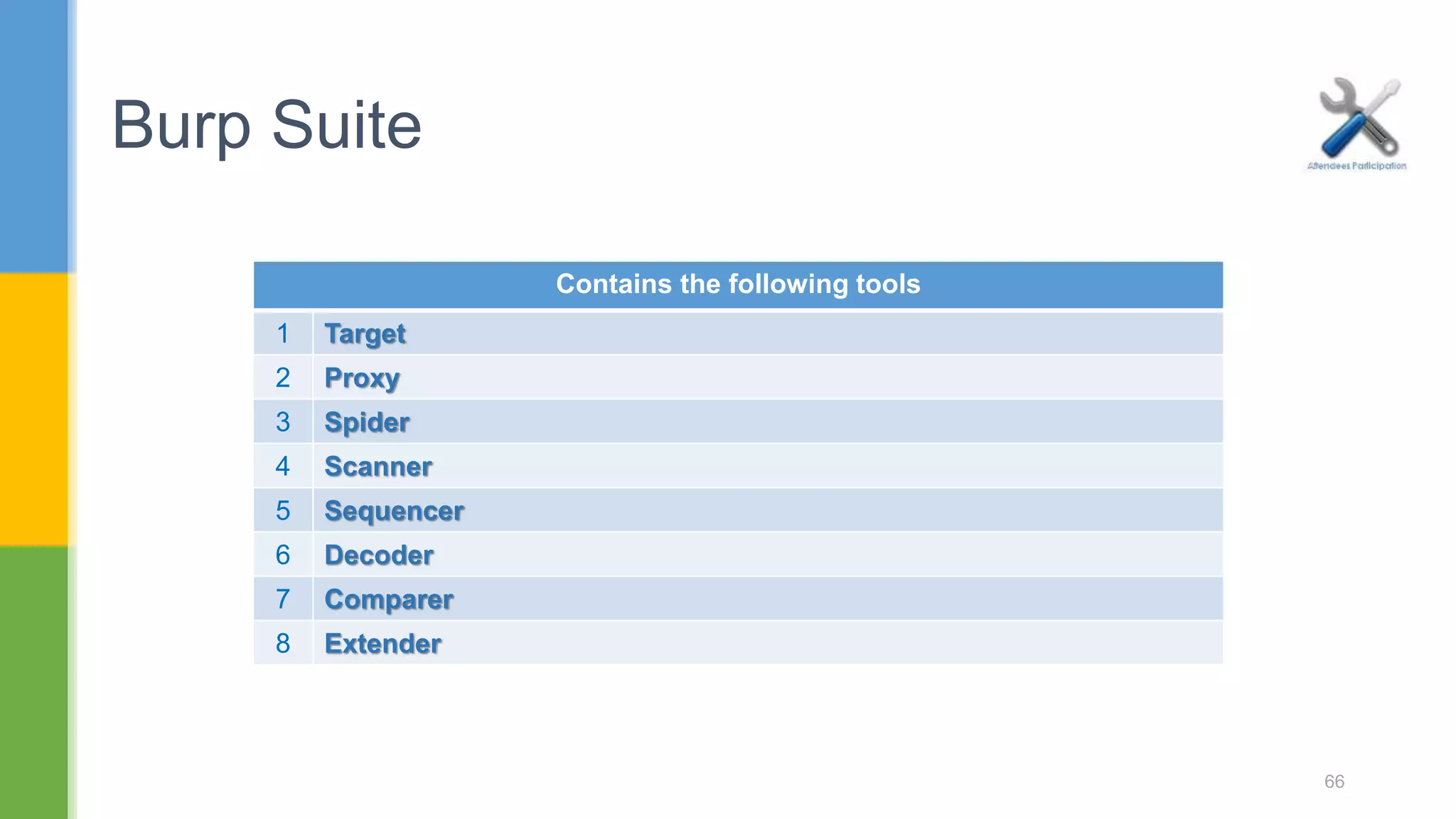
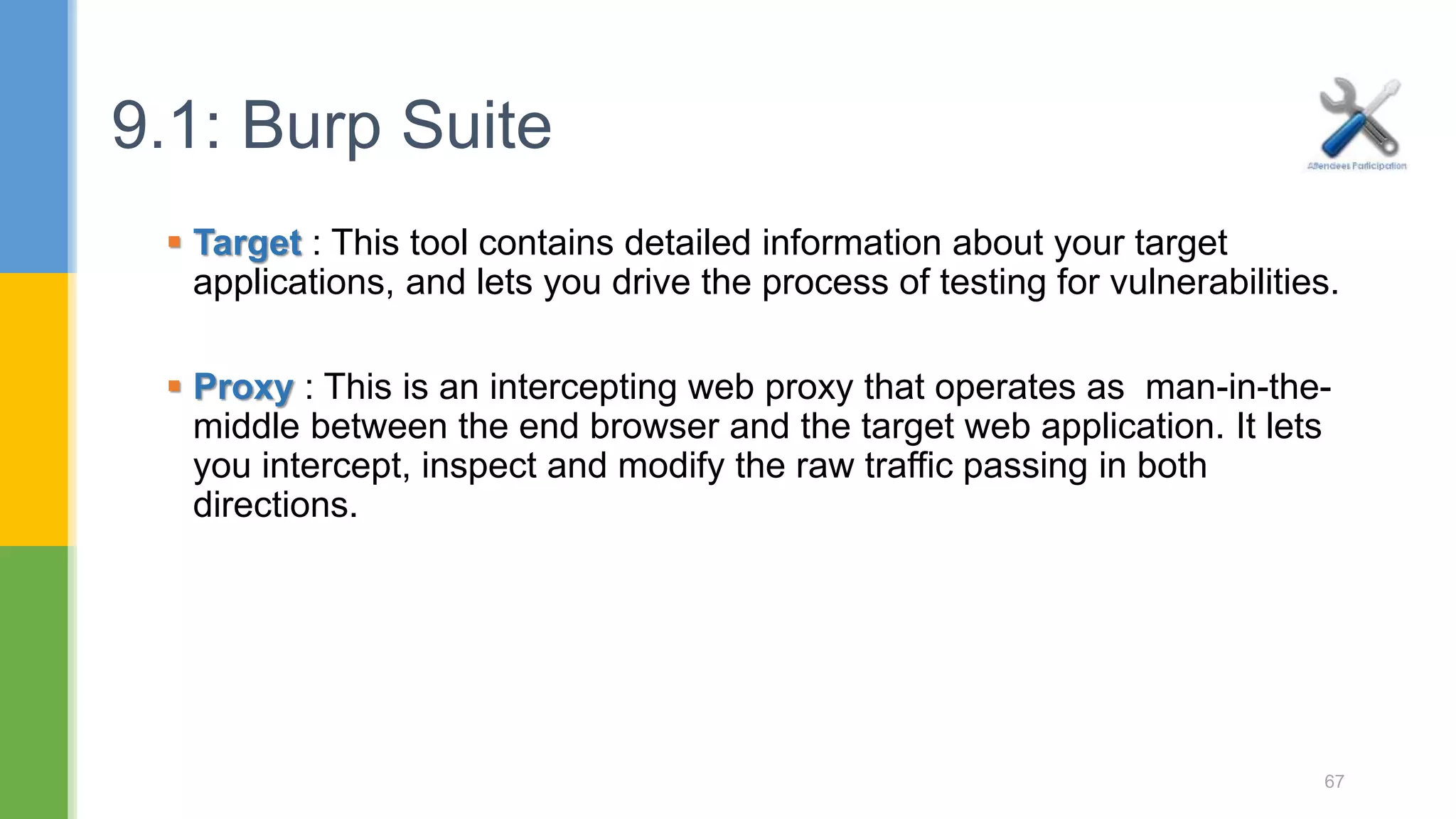
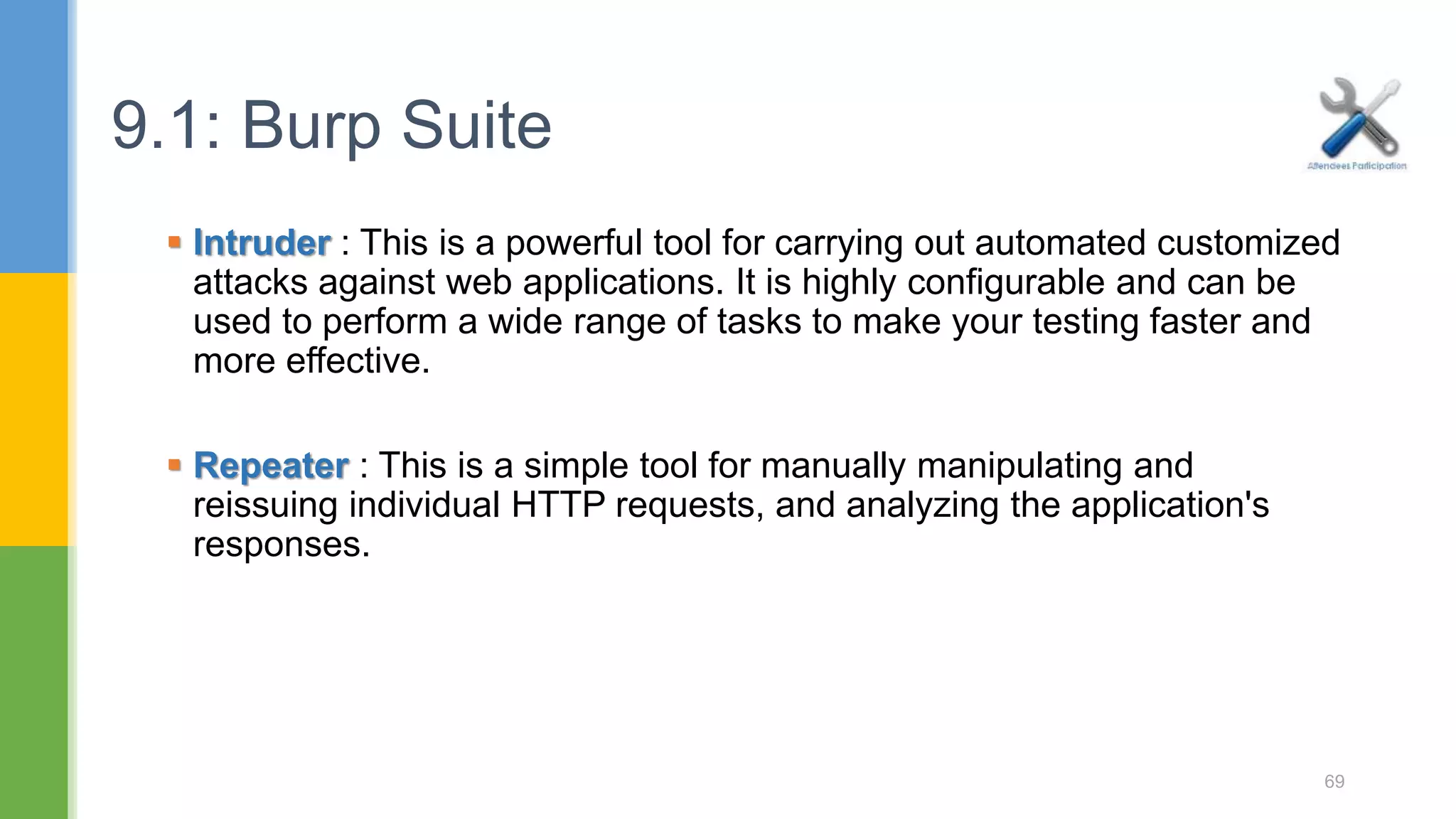
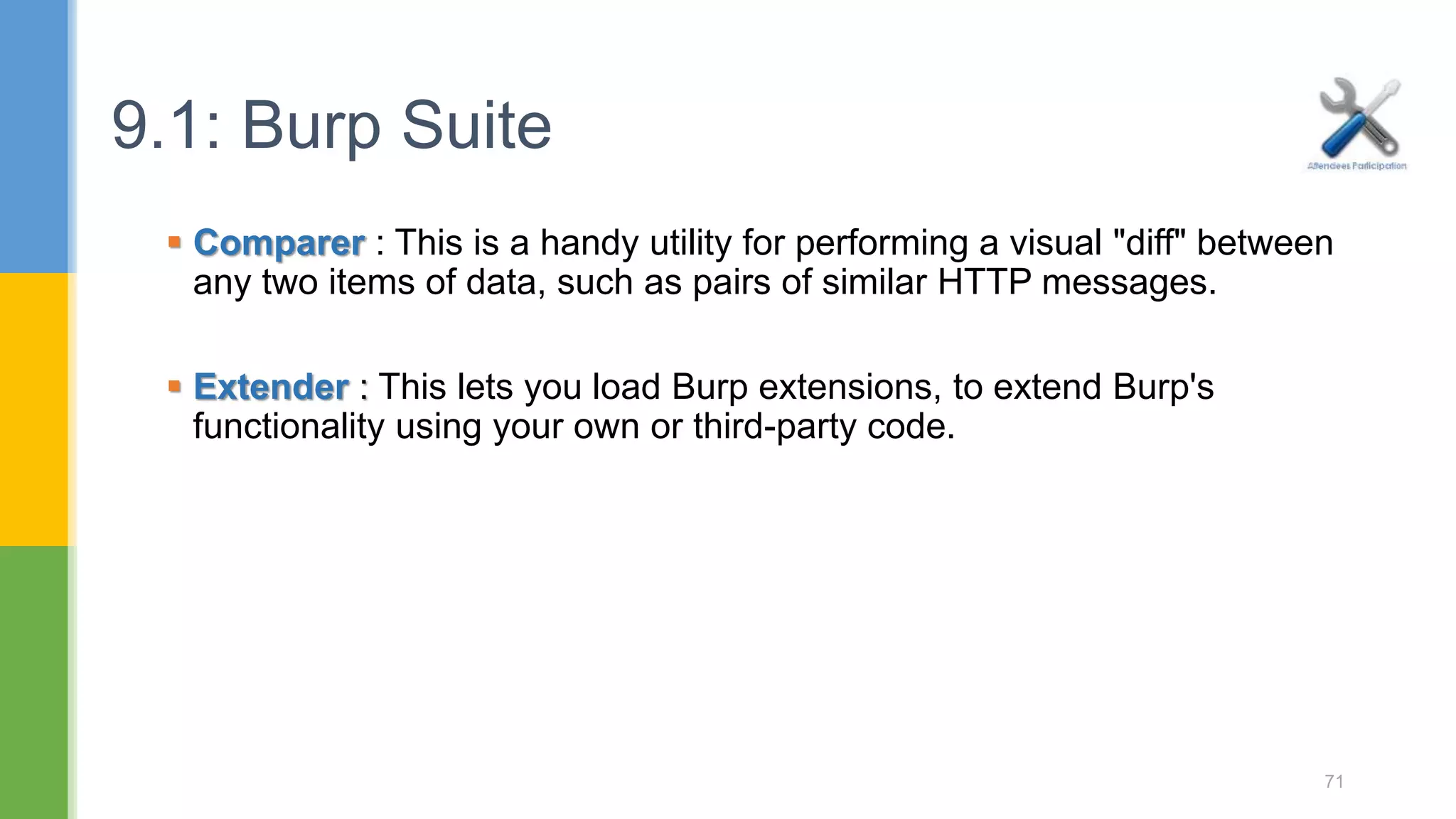
![ Spider : This is an intelligent application-aware web spider that can crawl an application to locate its content and functionality. Scanner : [Pro version] - This is an advanced web vulnerability scanner, which can automatically discover numerous types of vulnerabilities. 9.1: Burp Suite 68](https://image.slidesharecdn.com/webapplicationssecurity-conferenceslides-170828073416/75/Web-applications-security-conference-slides-68-2048.jpg)