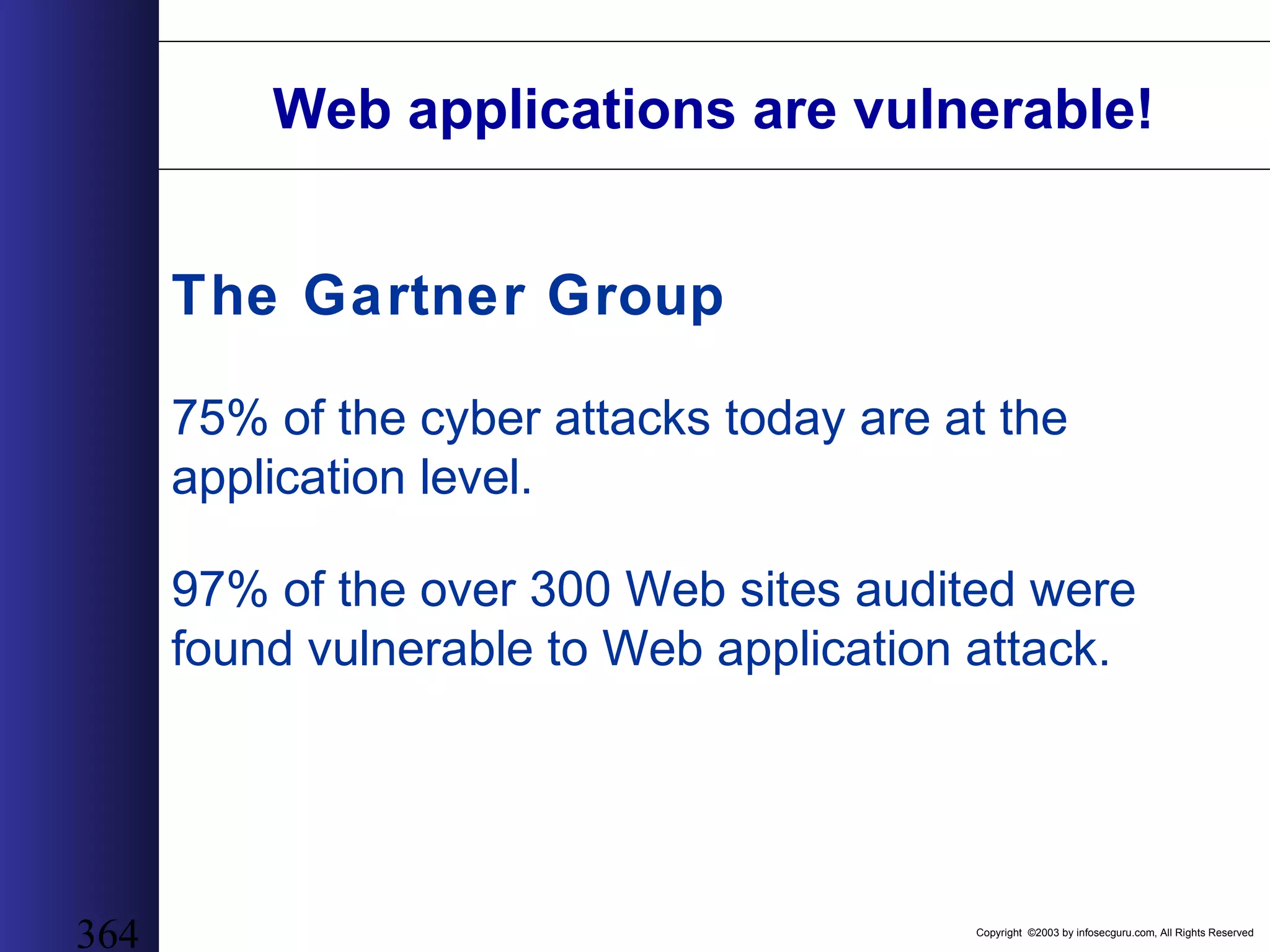
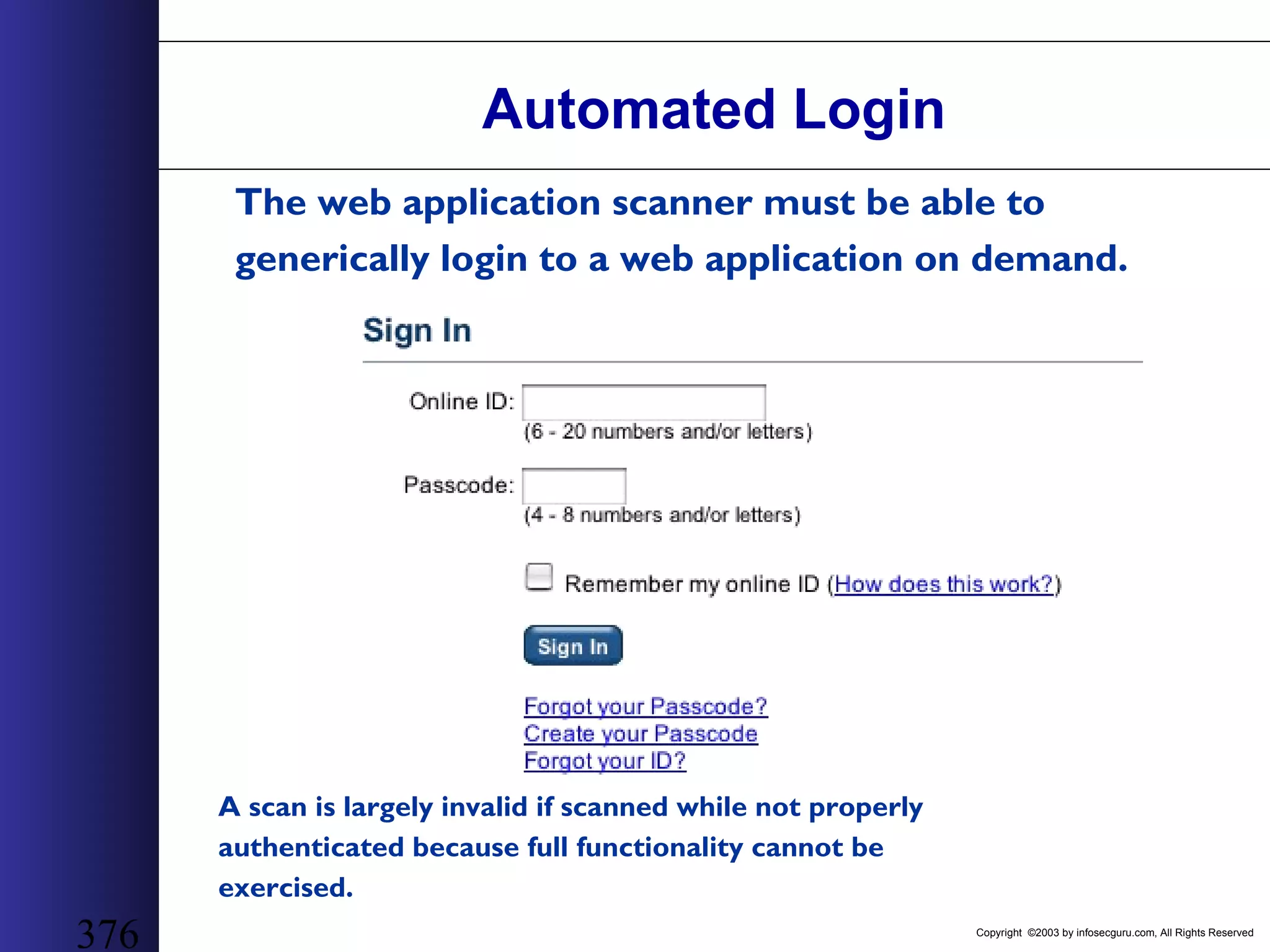
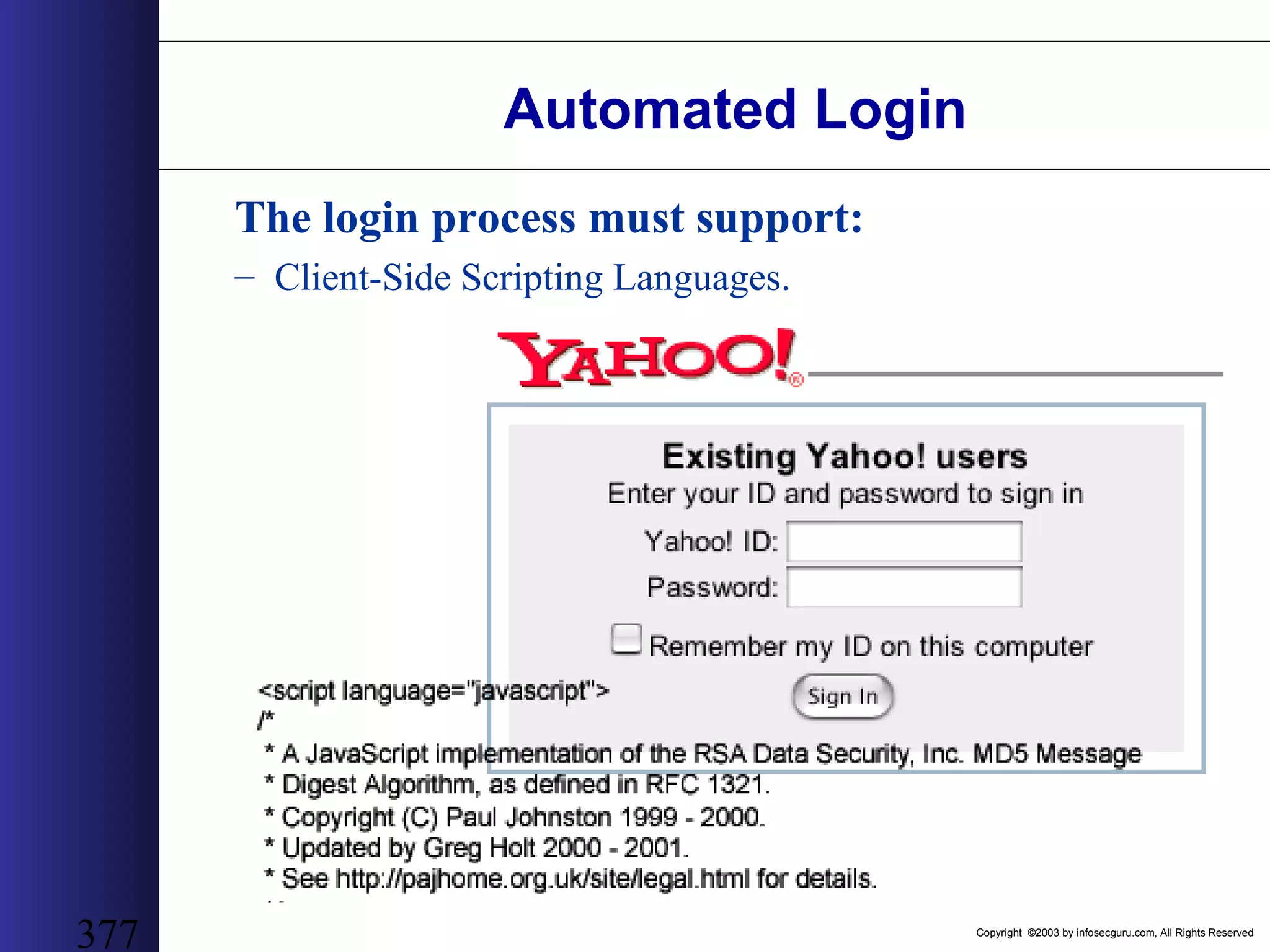
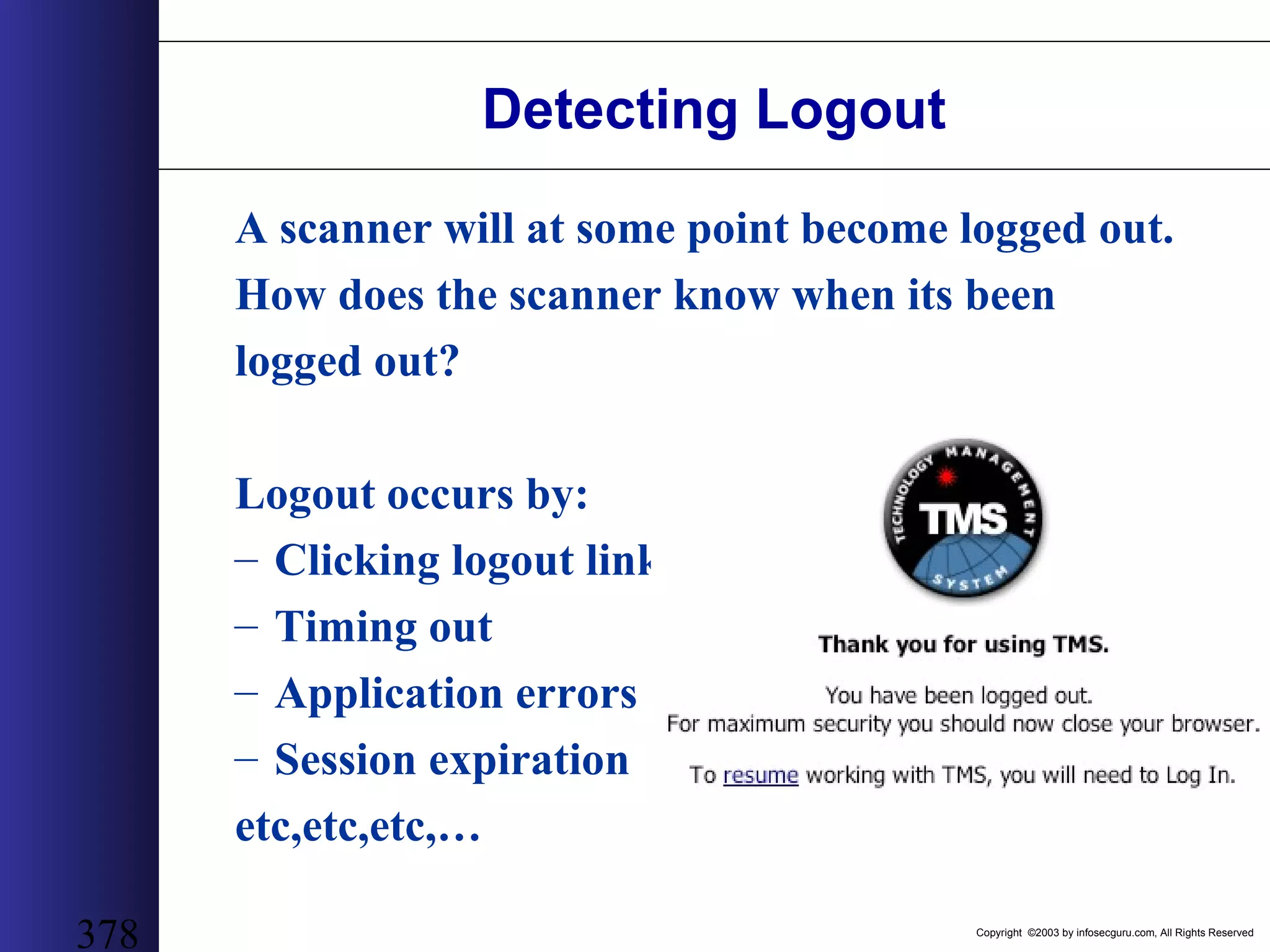
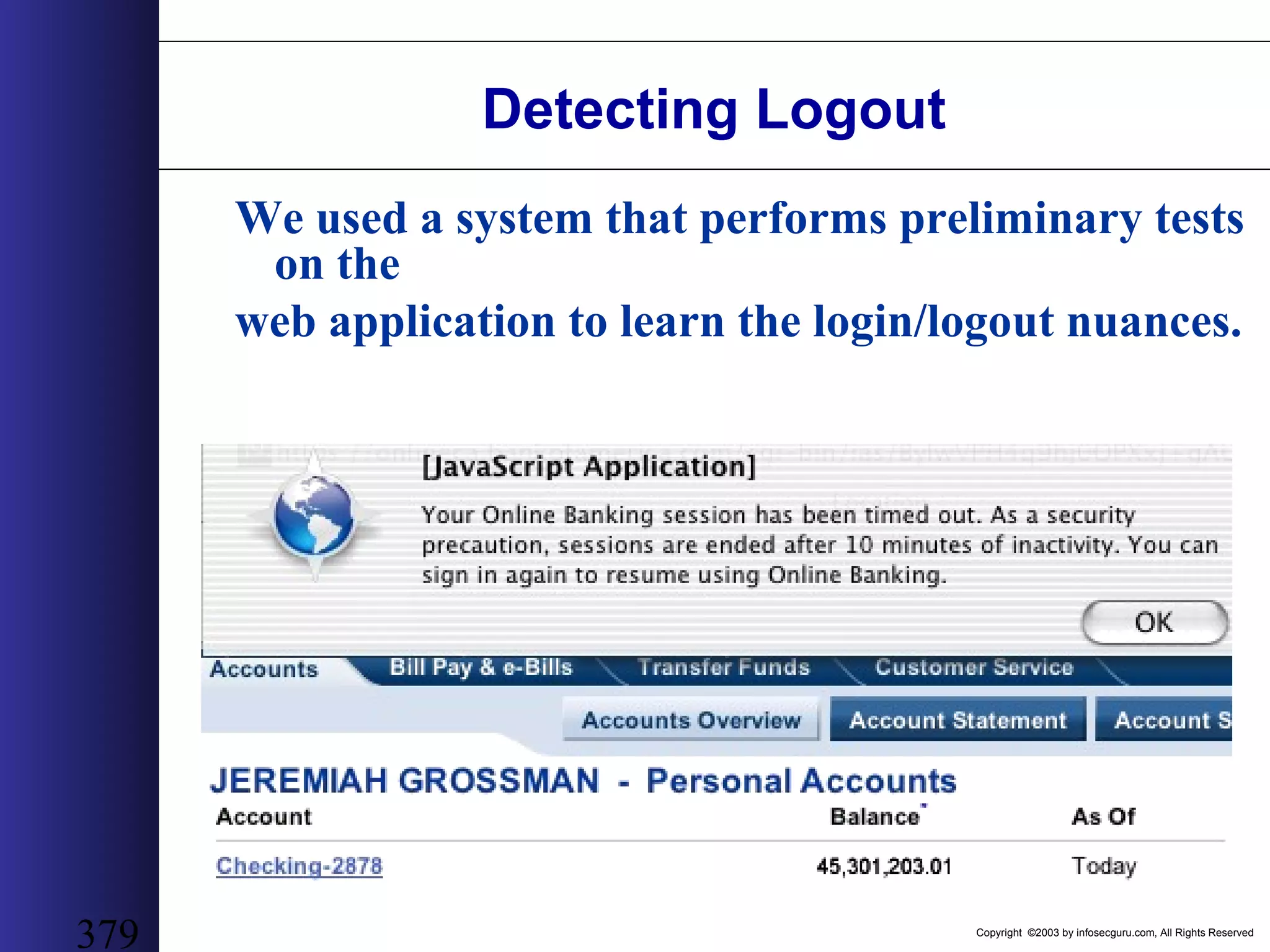
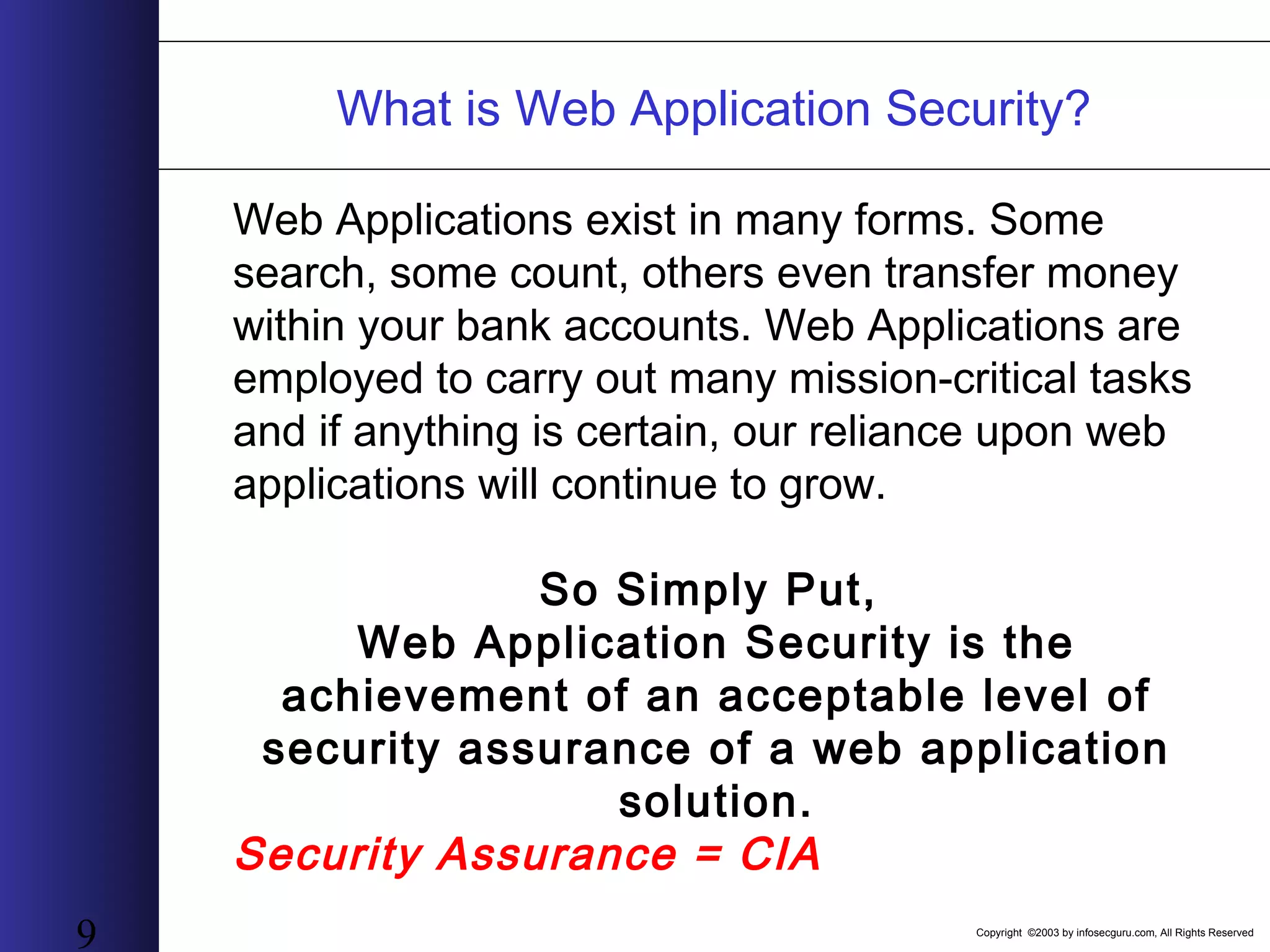
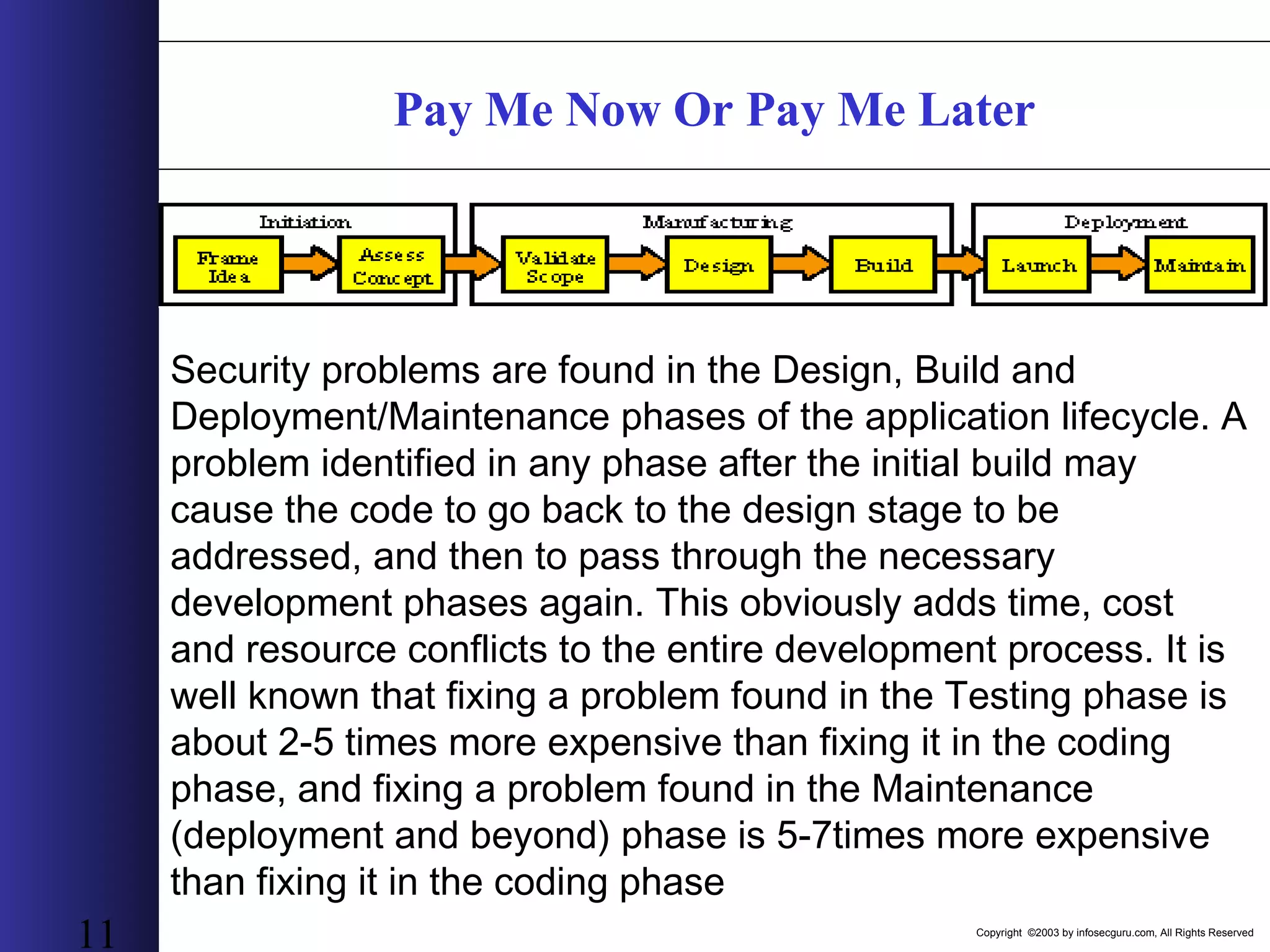
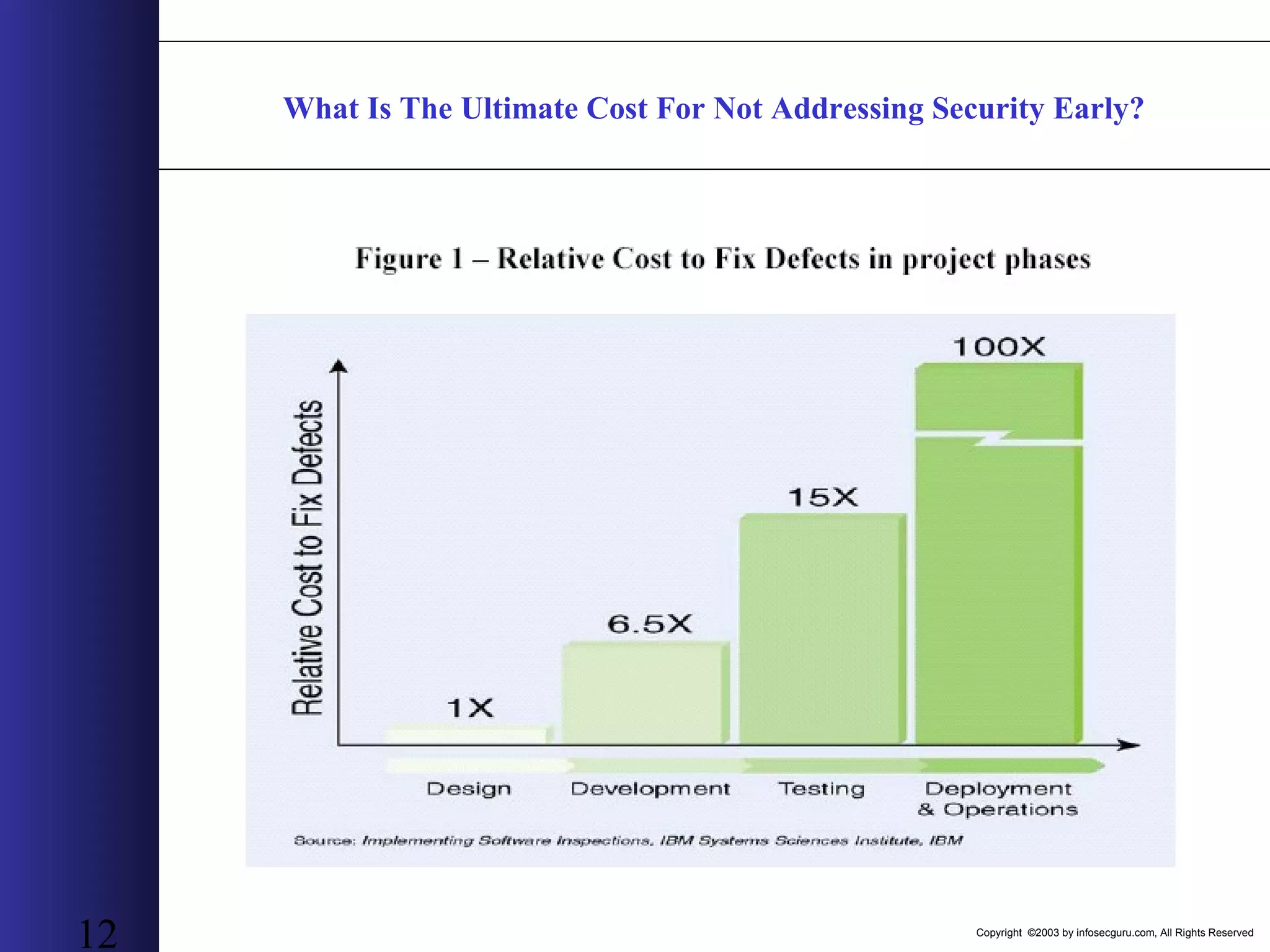
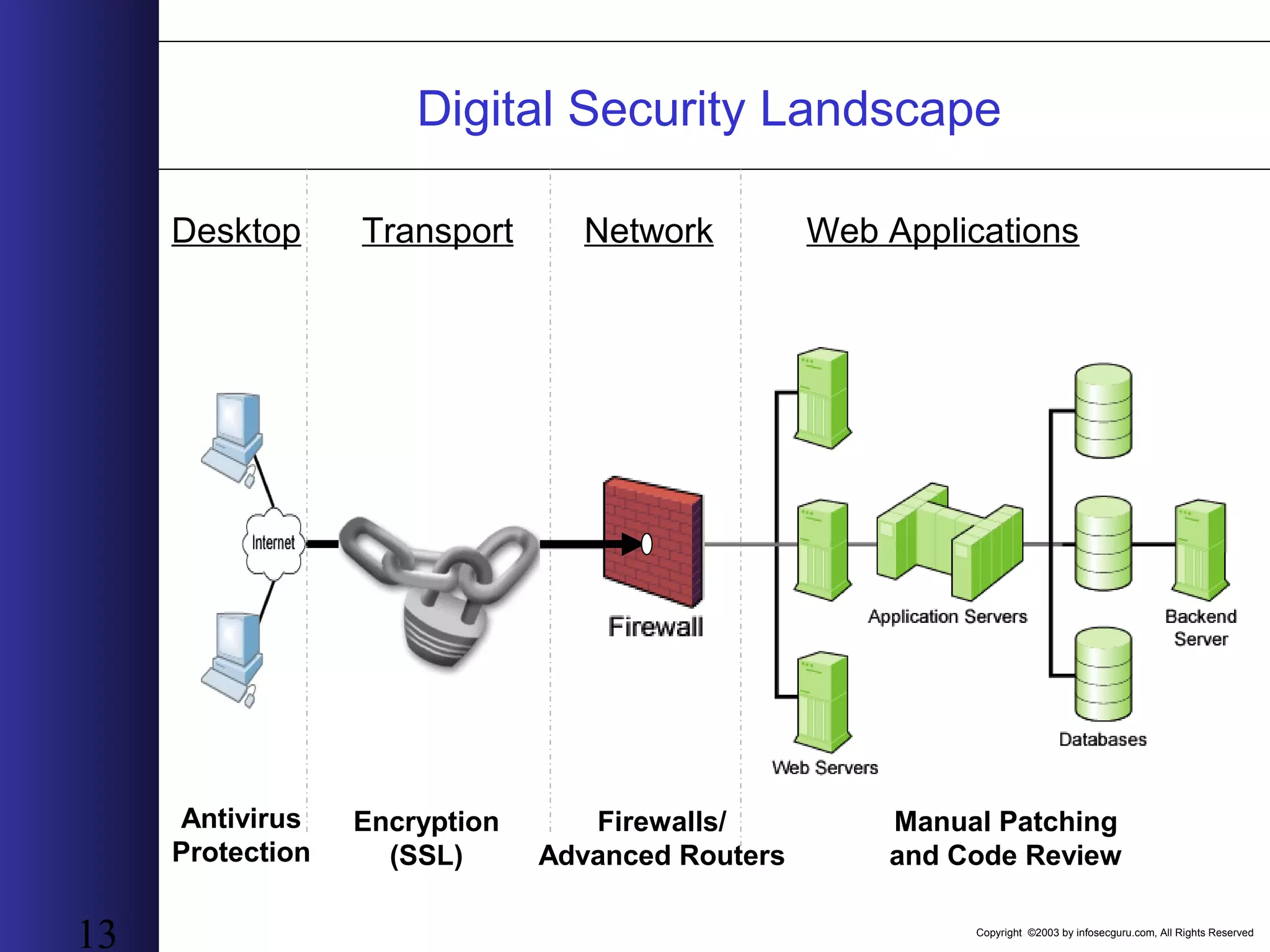
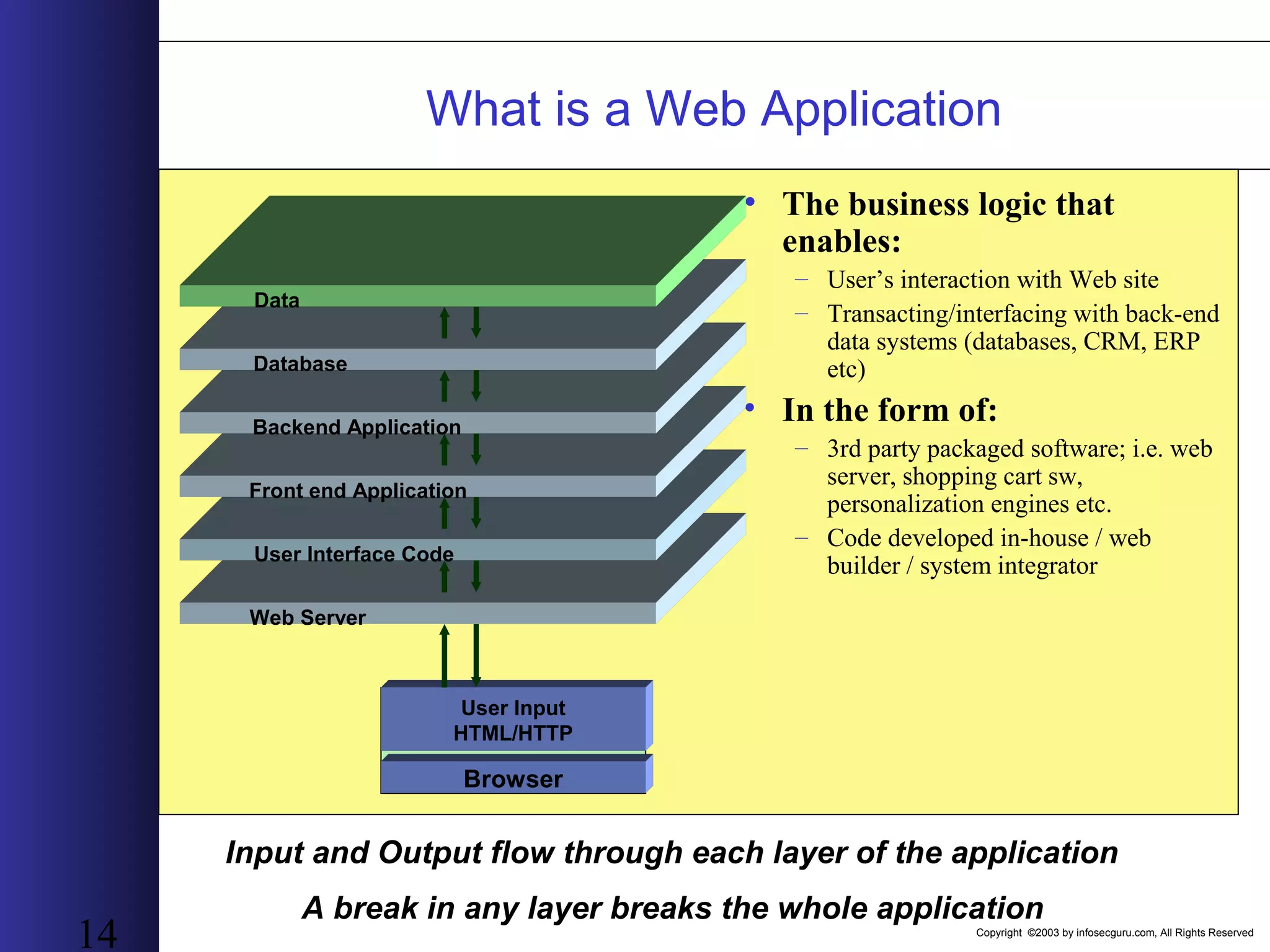
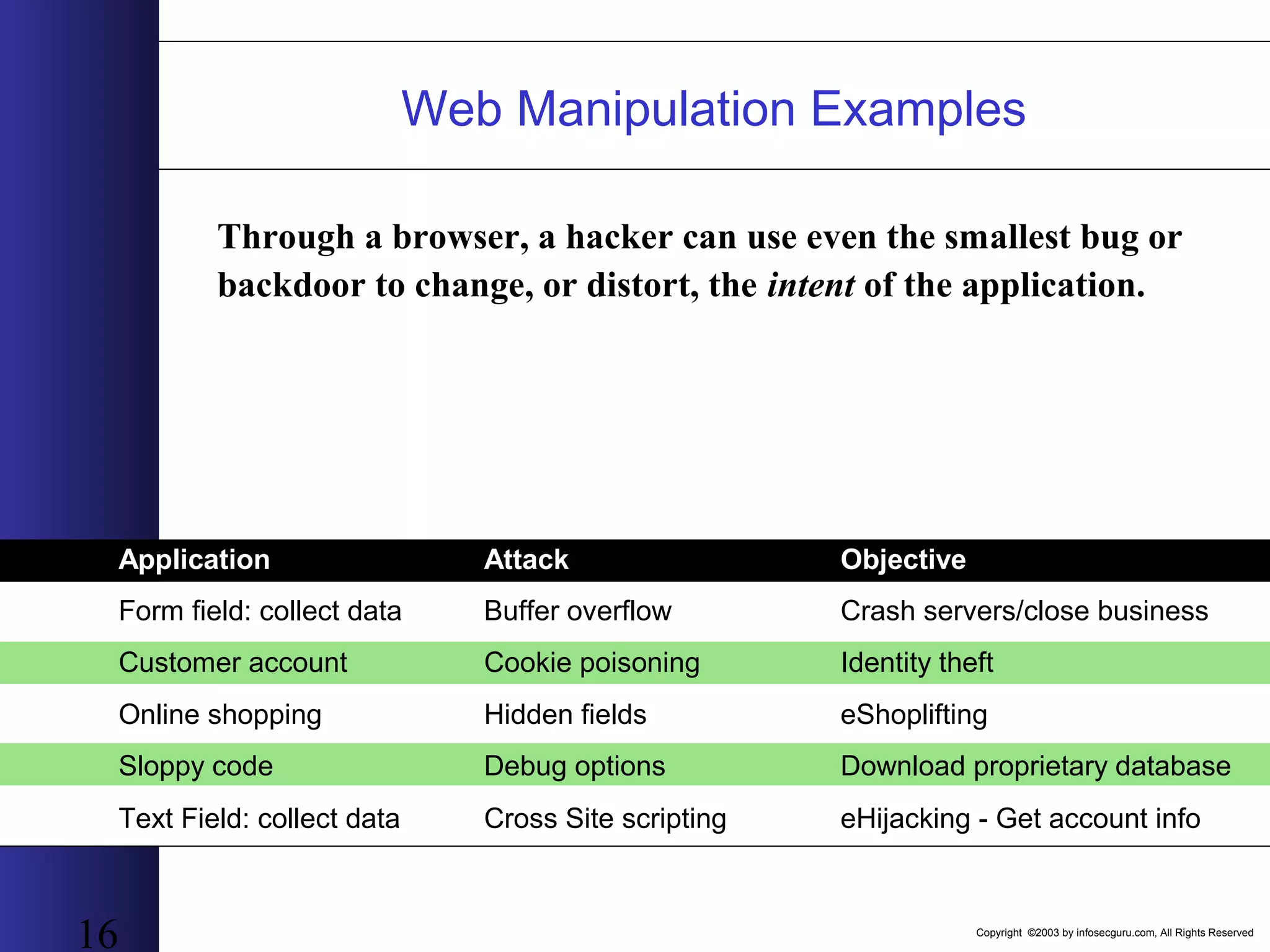
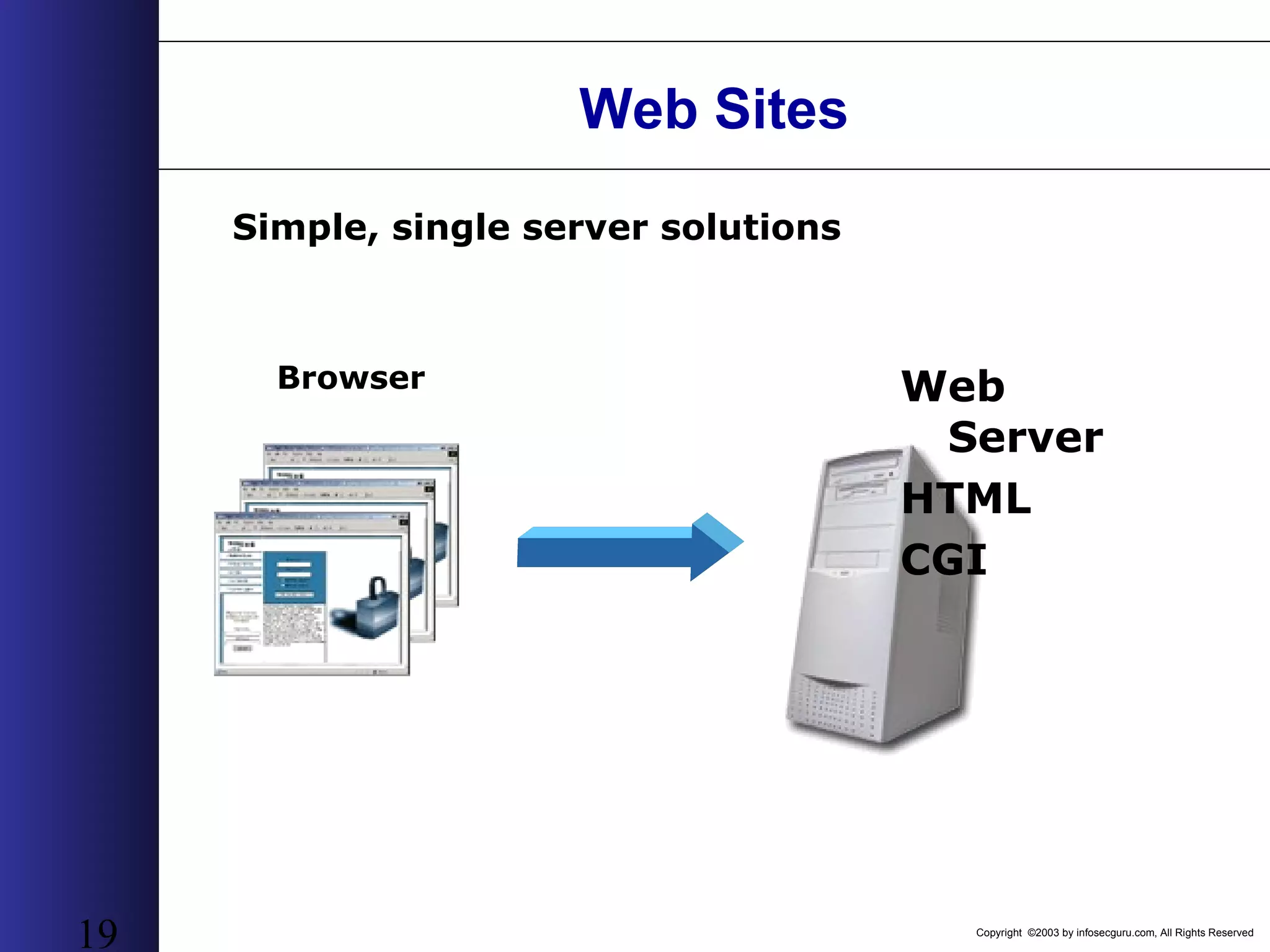
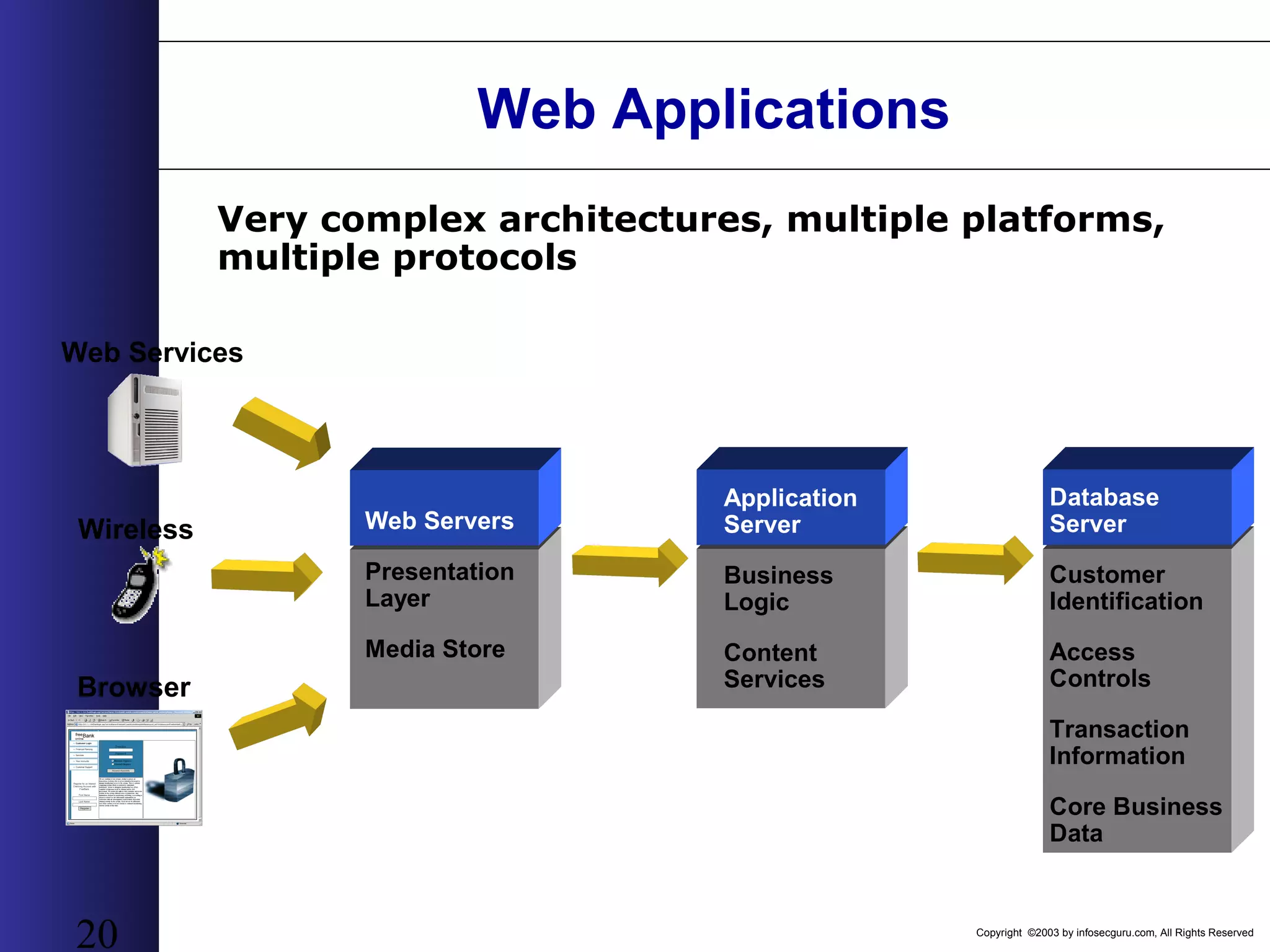
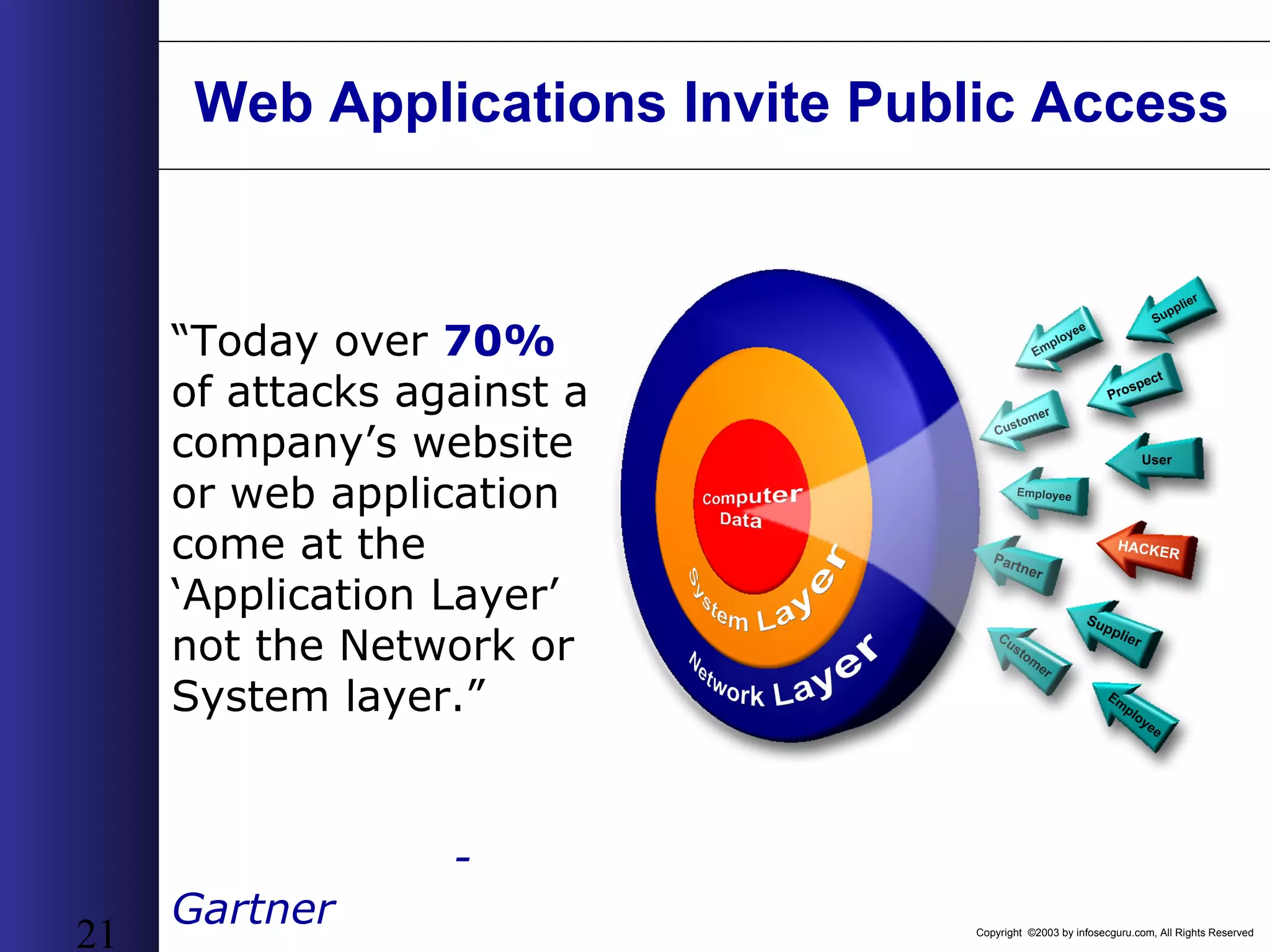
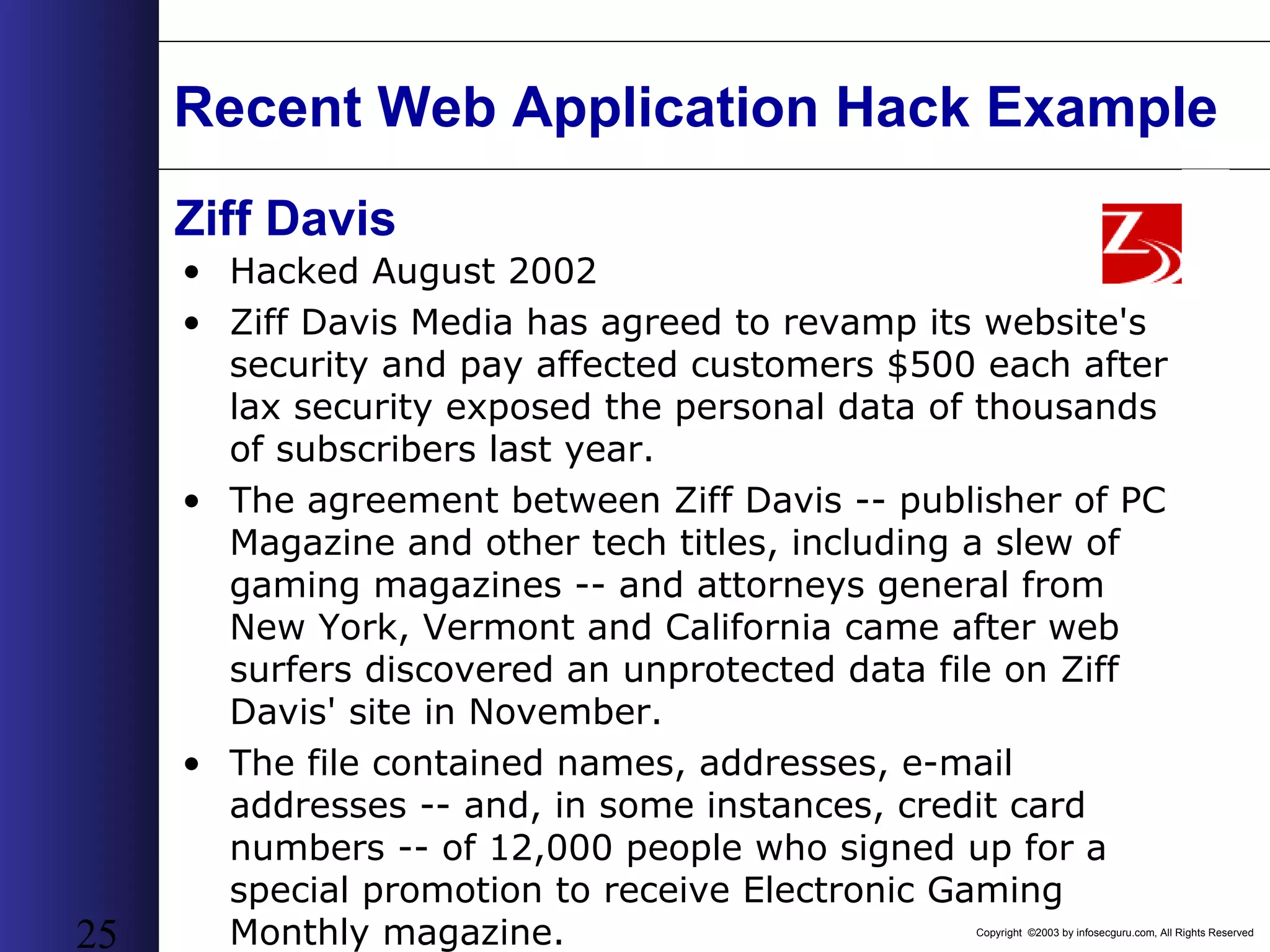
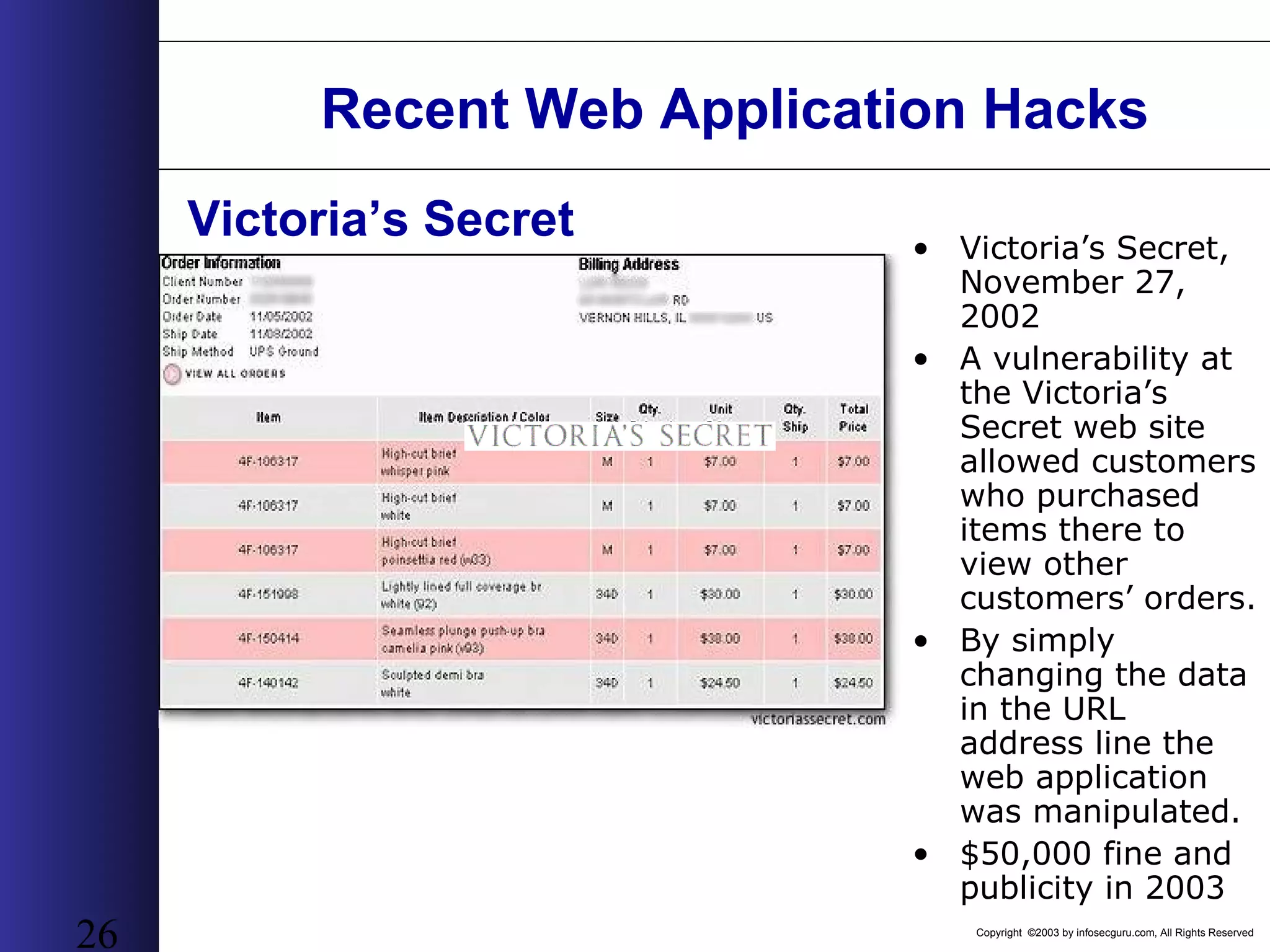
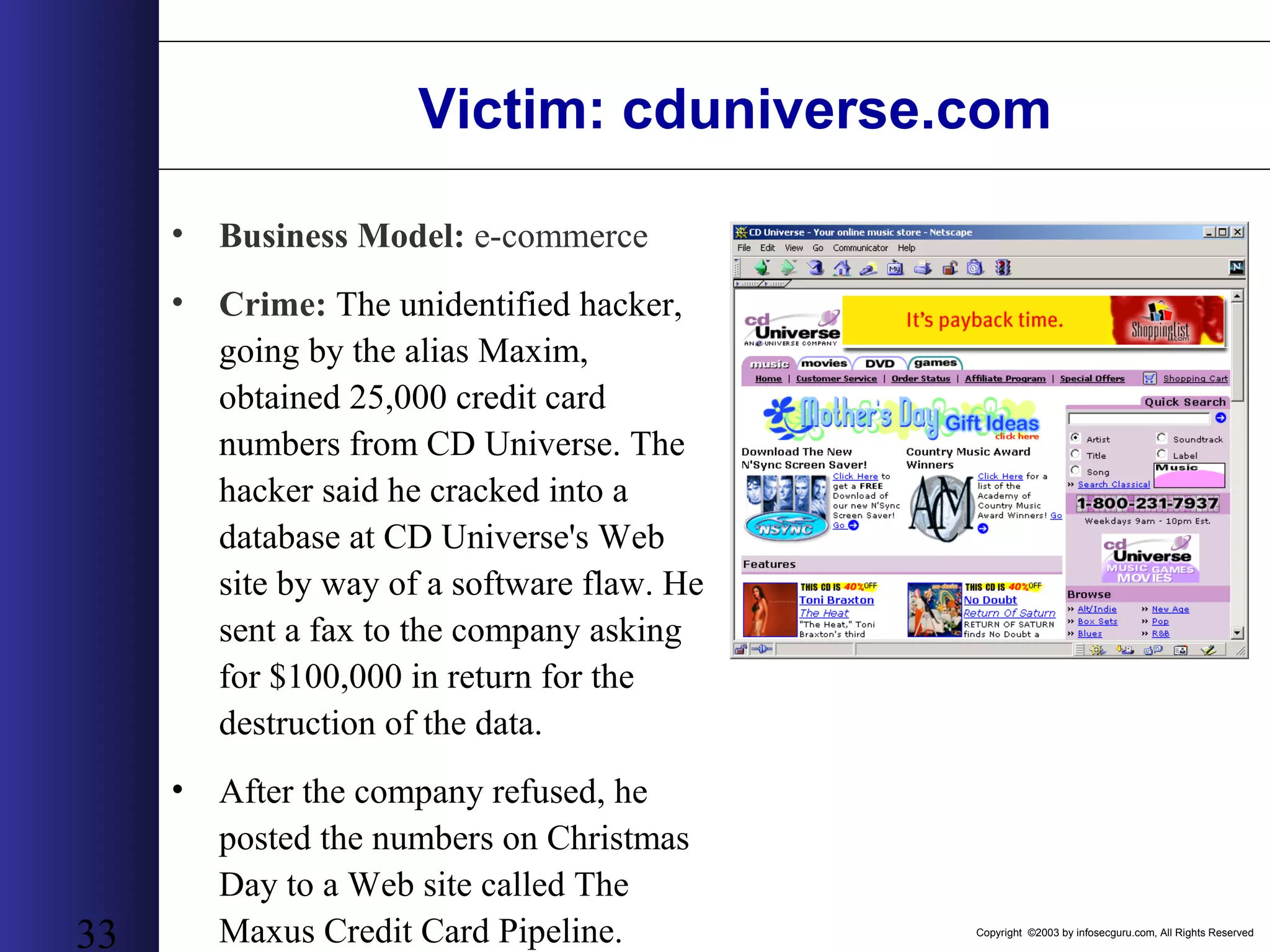
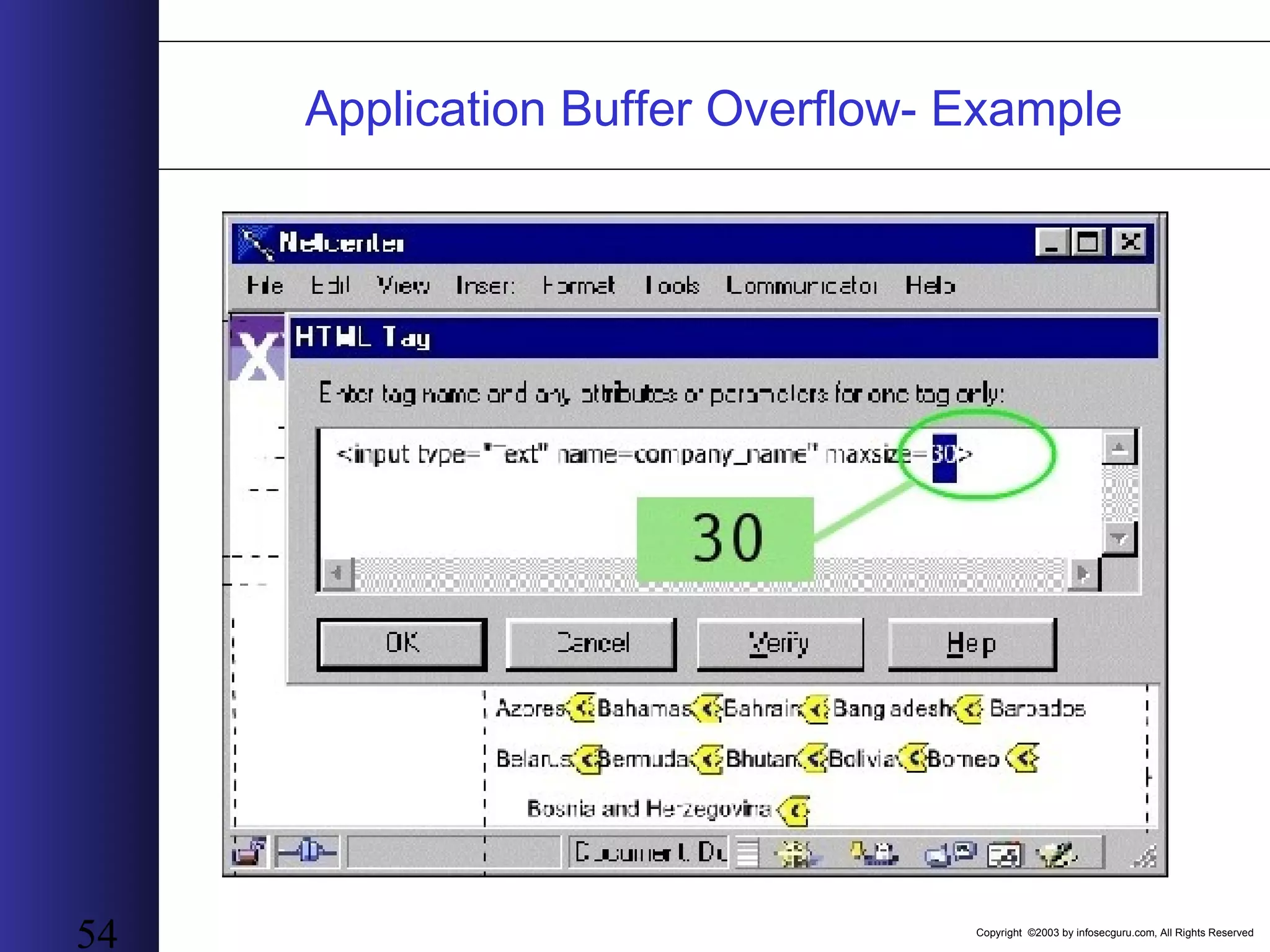
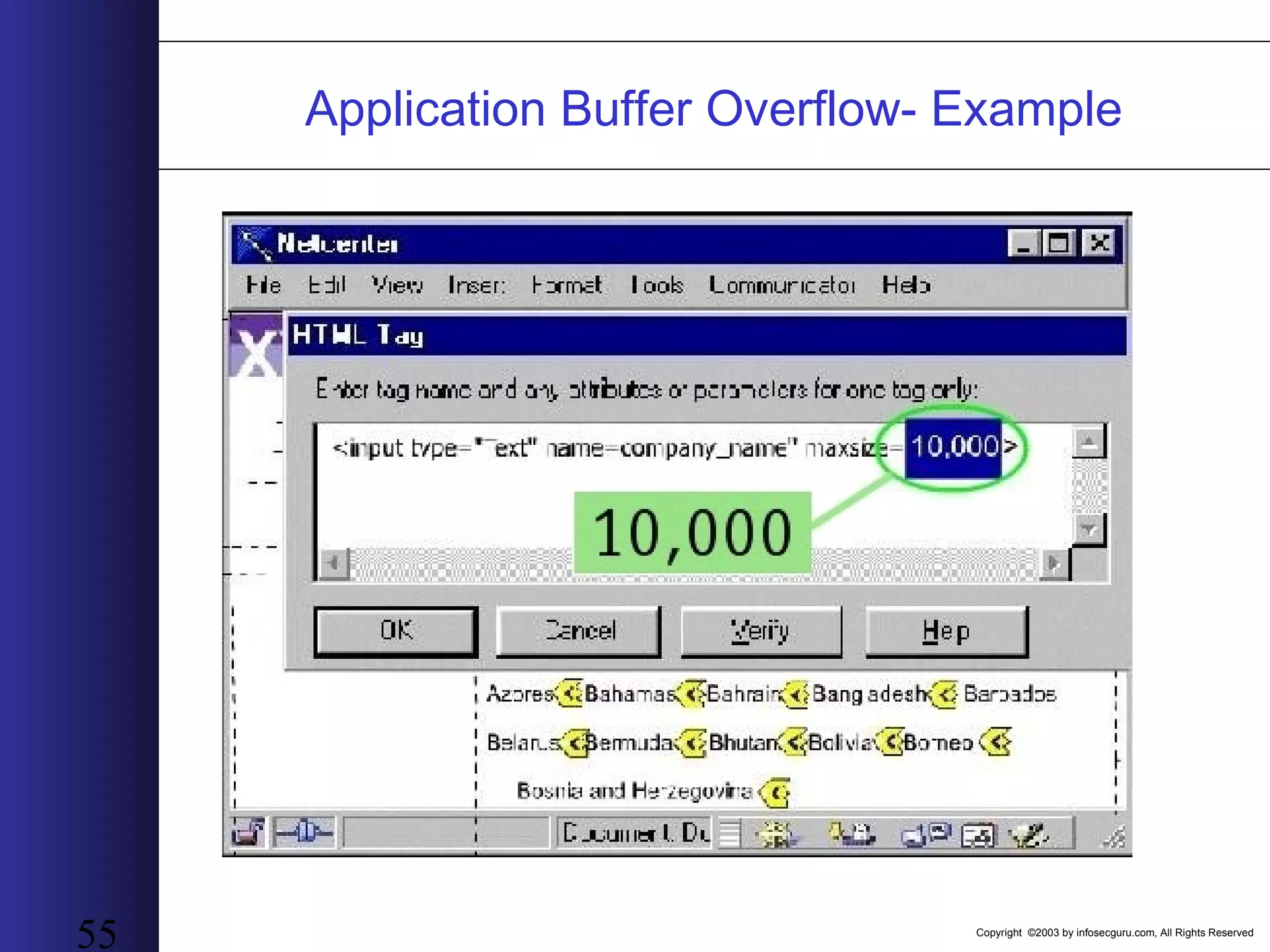
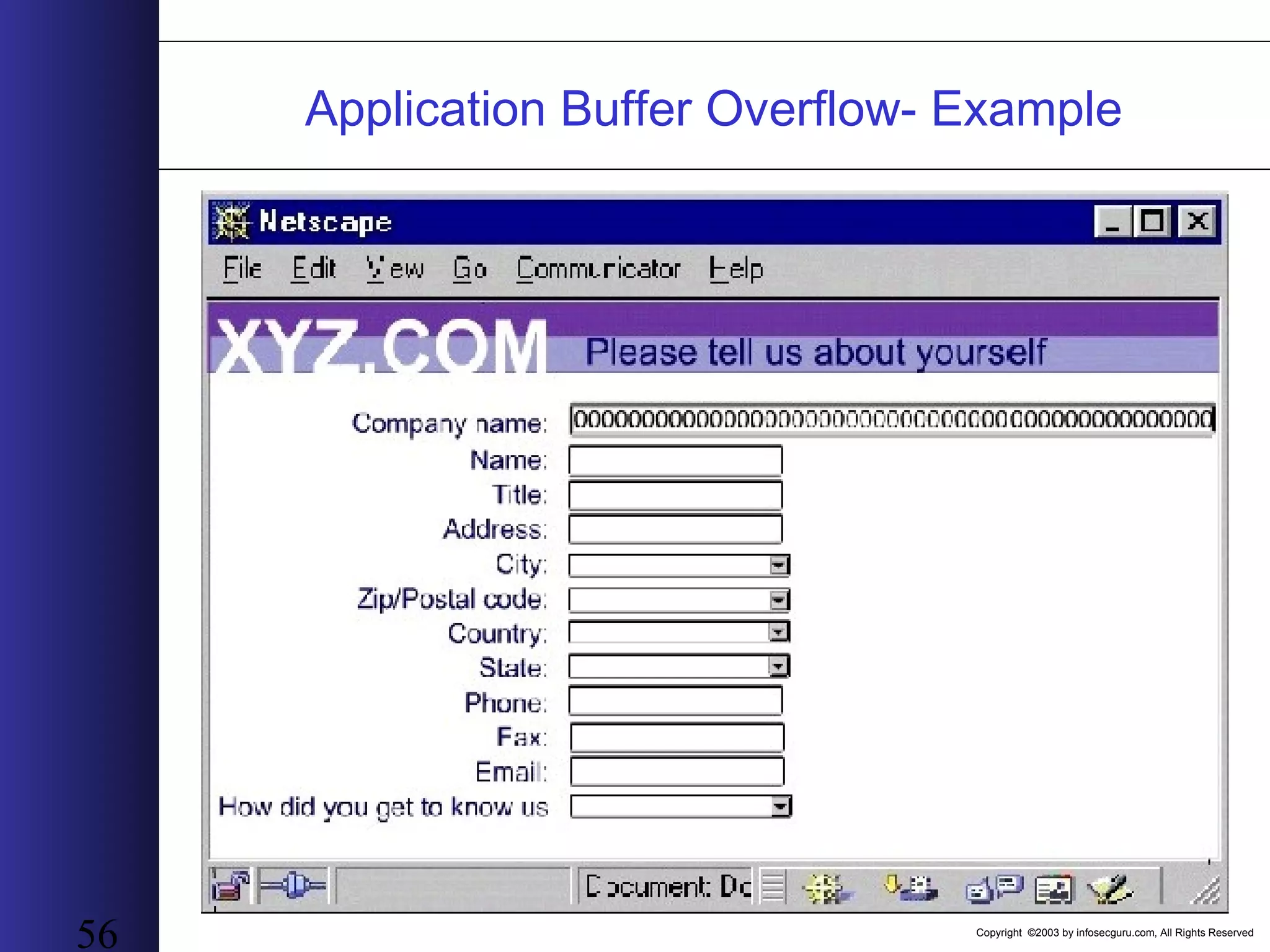
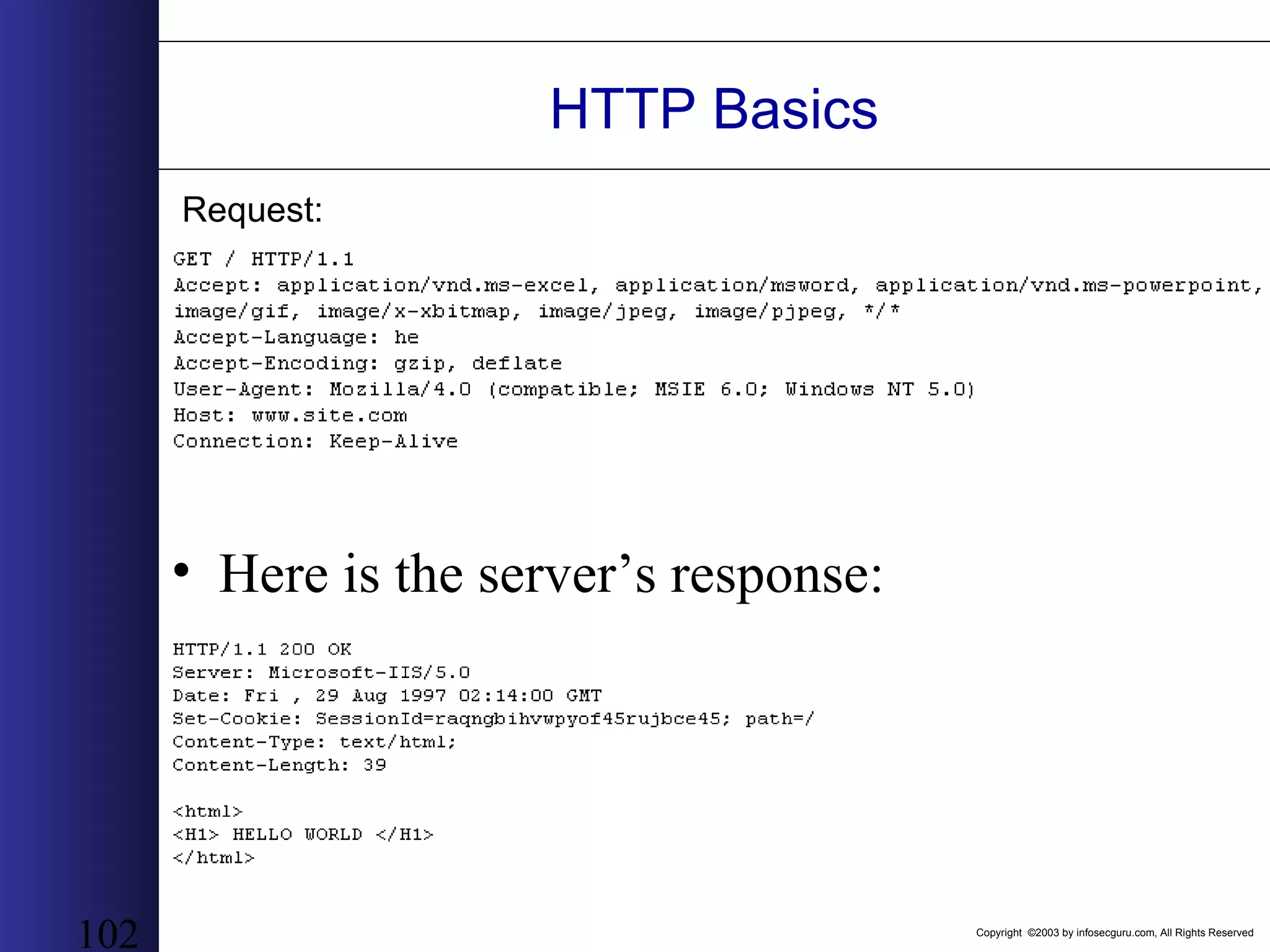
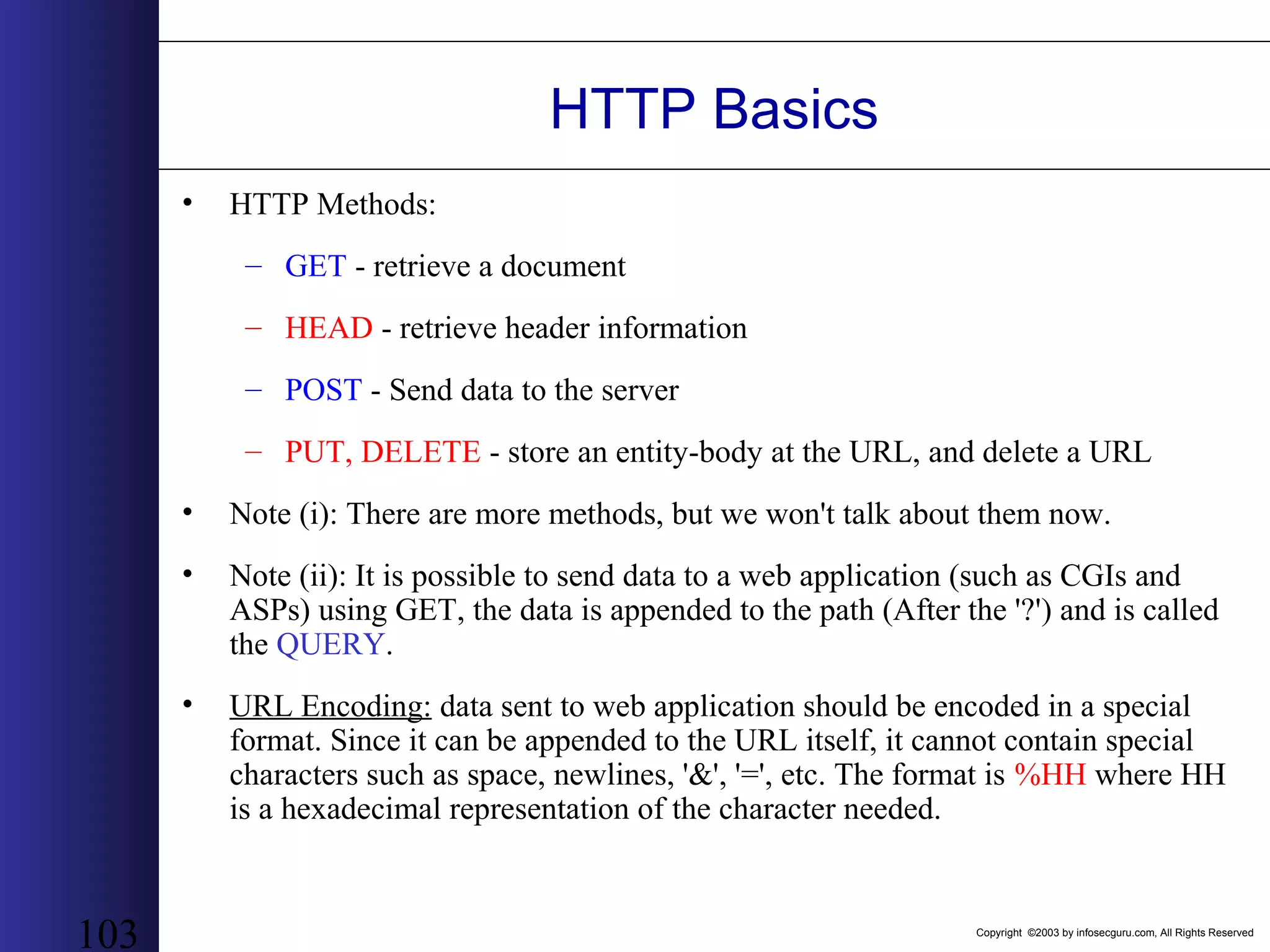
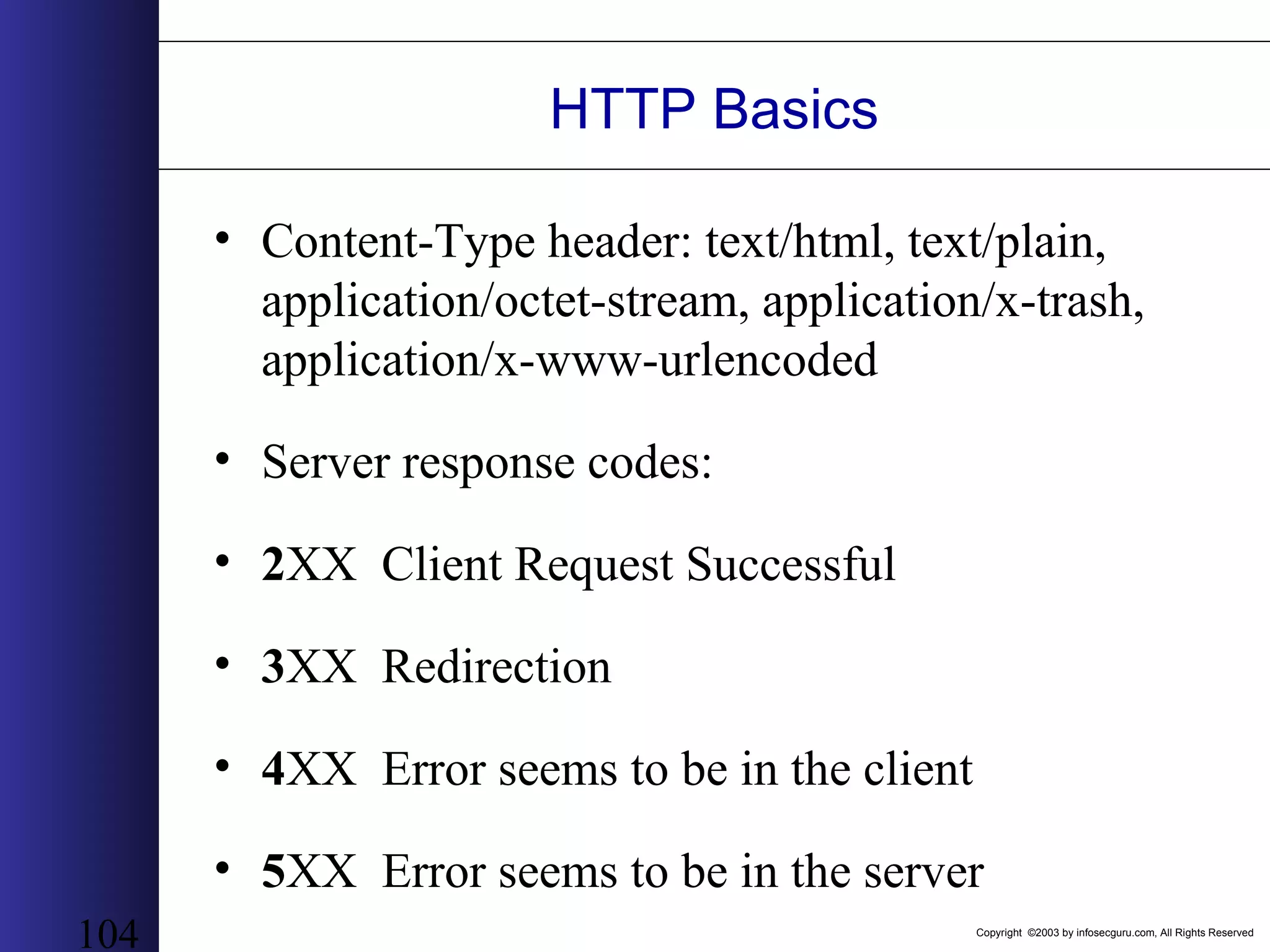
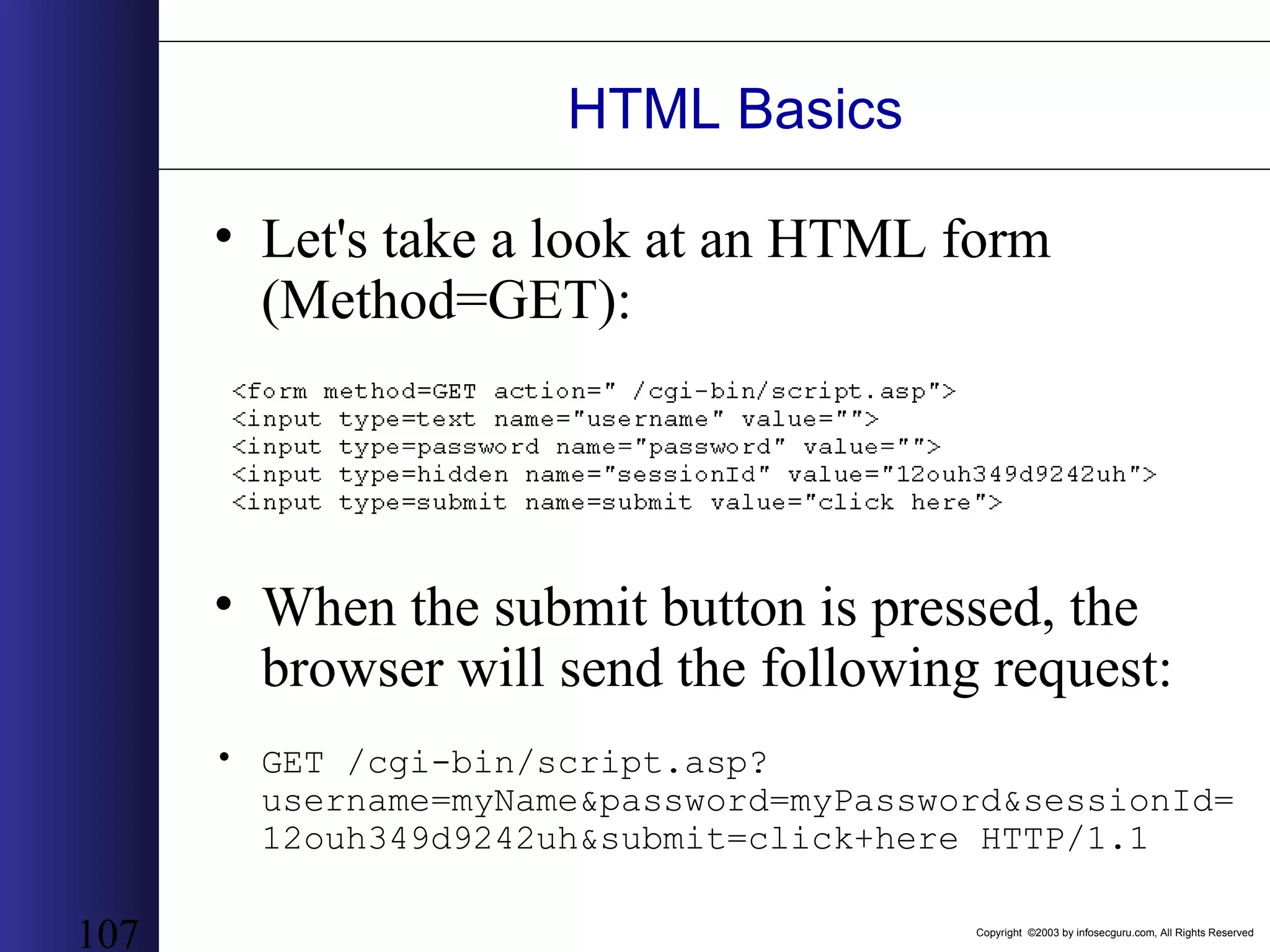
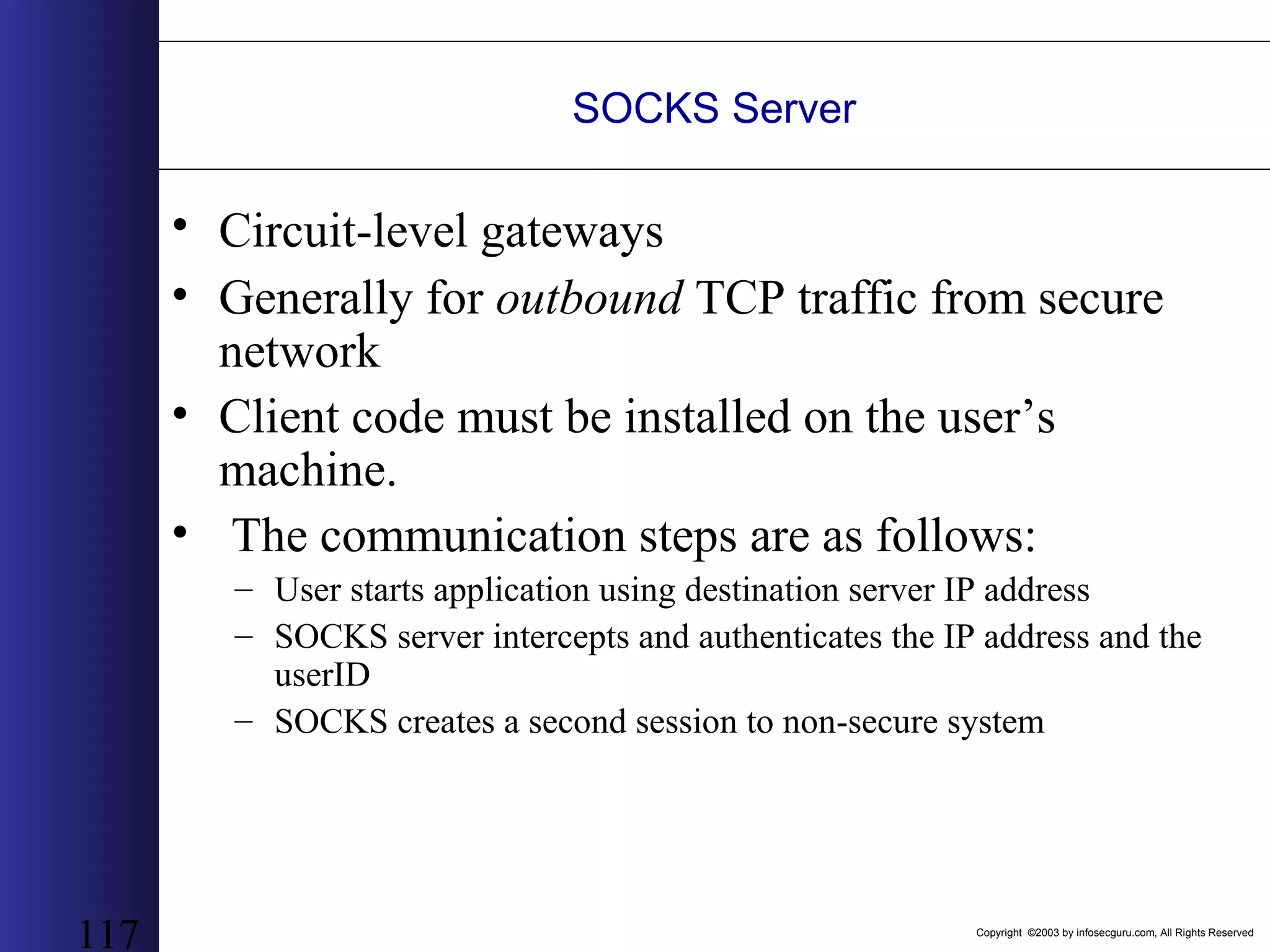
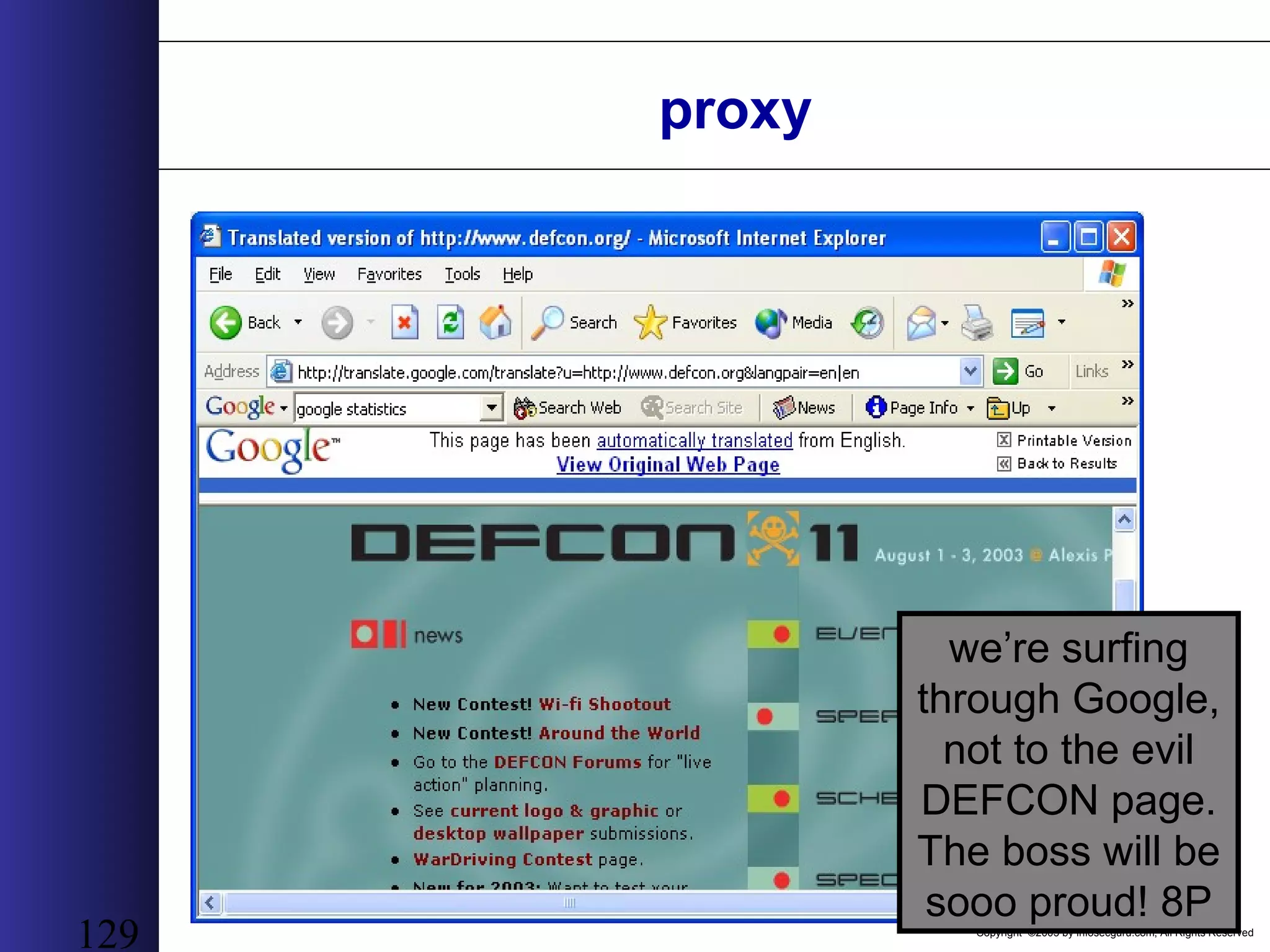
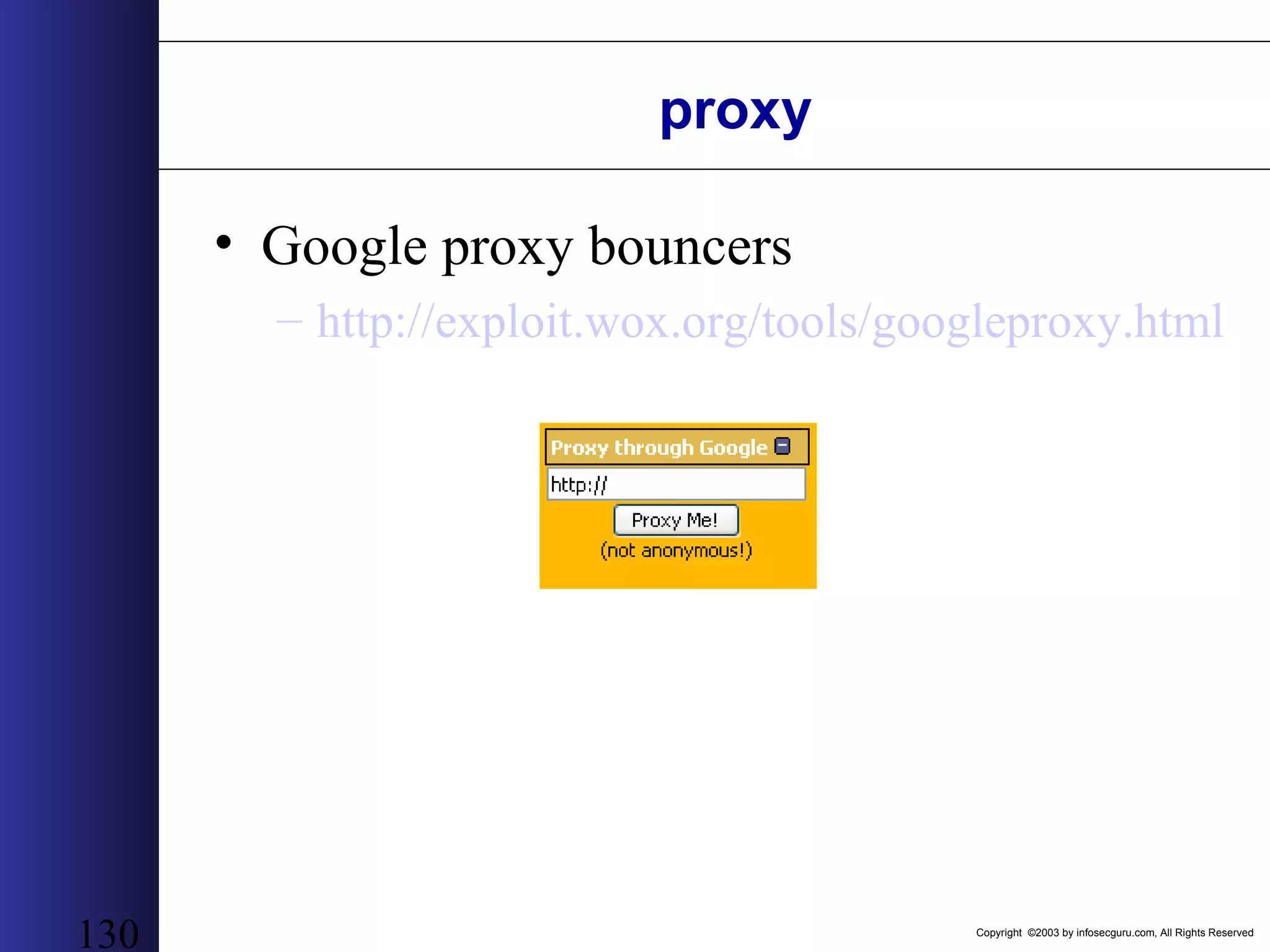
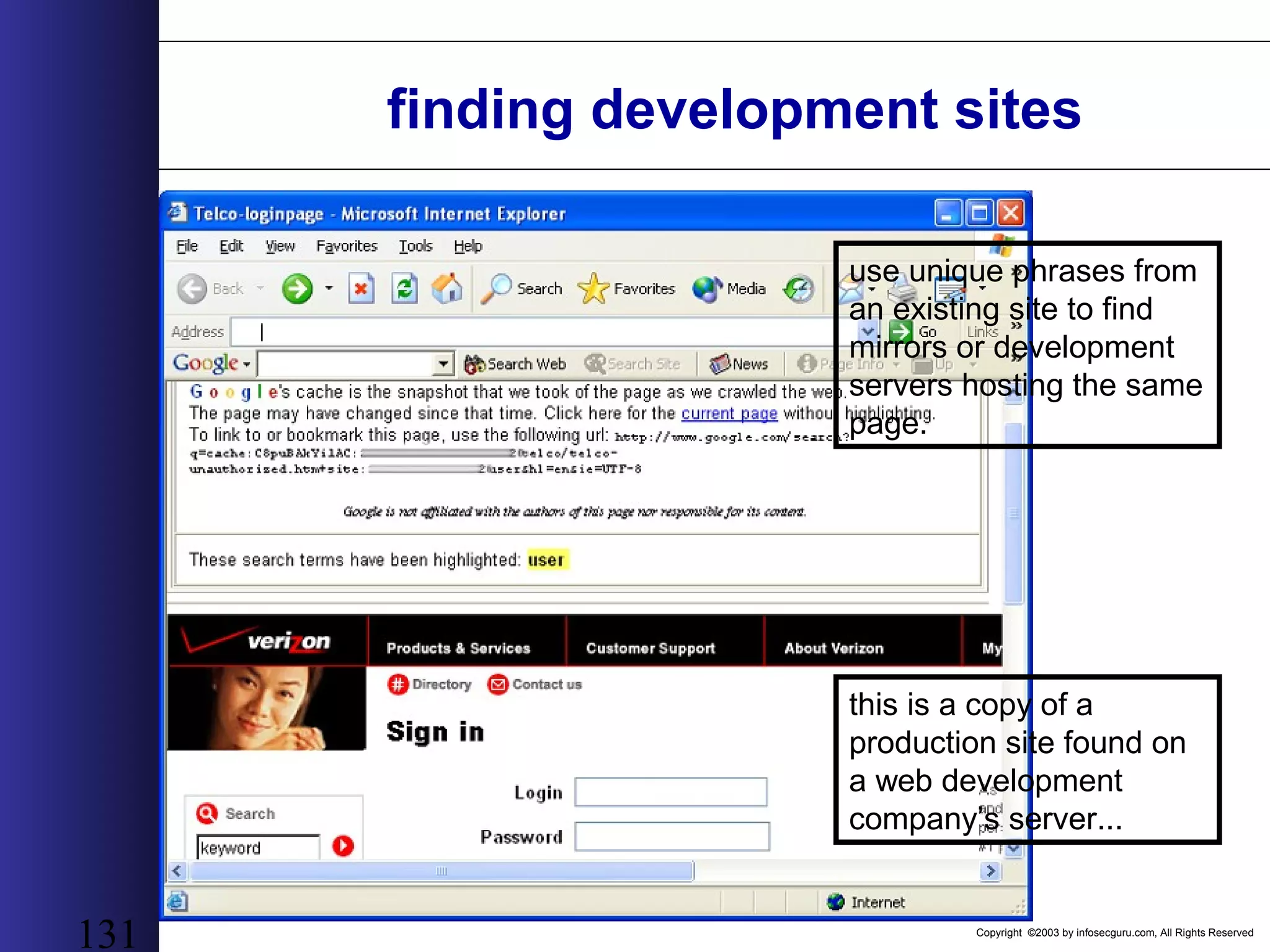
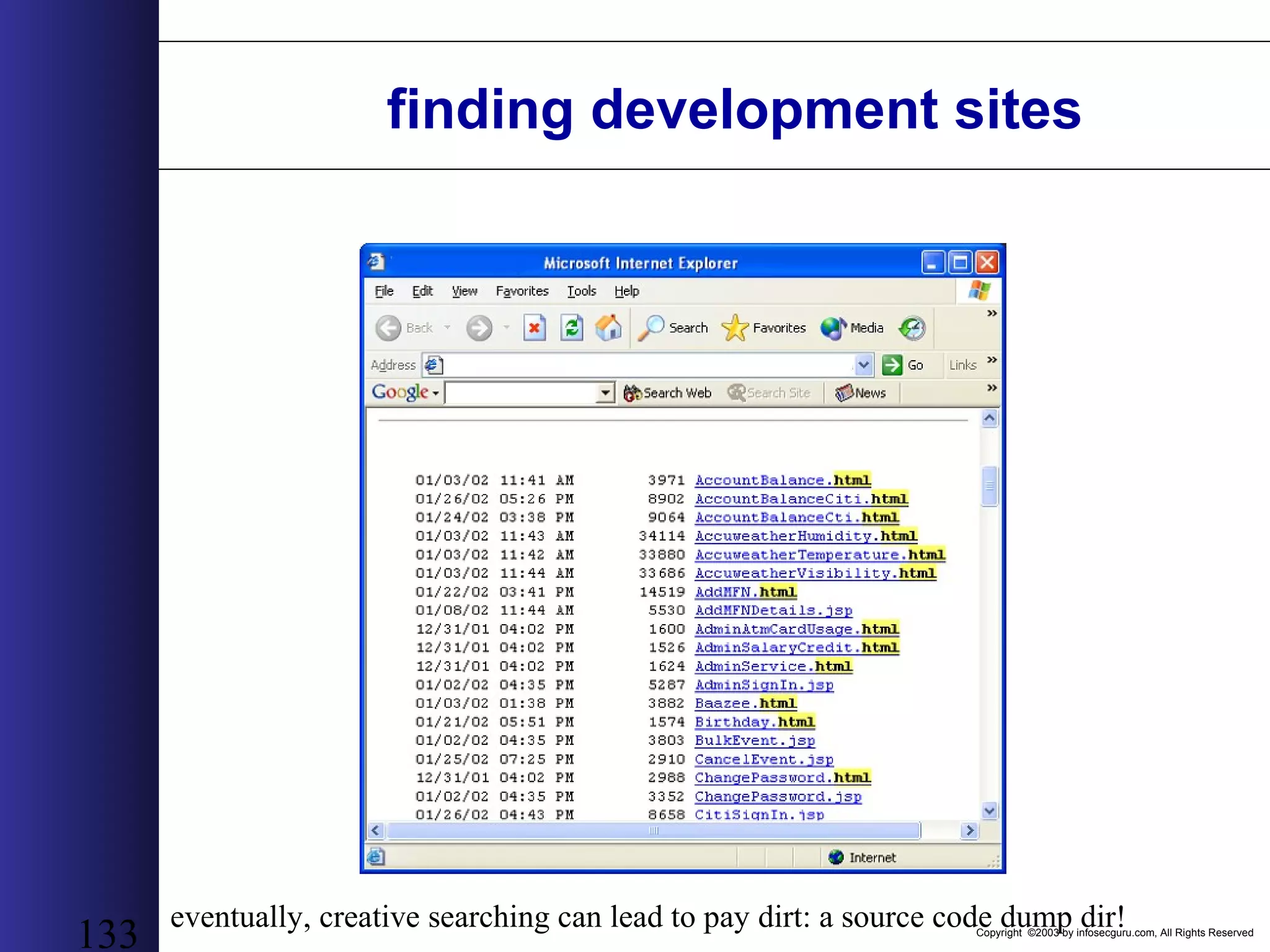
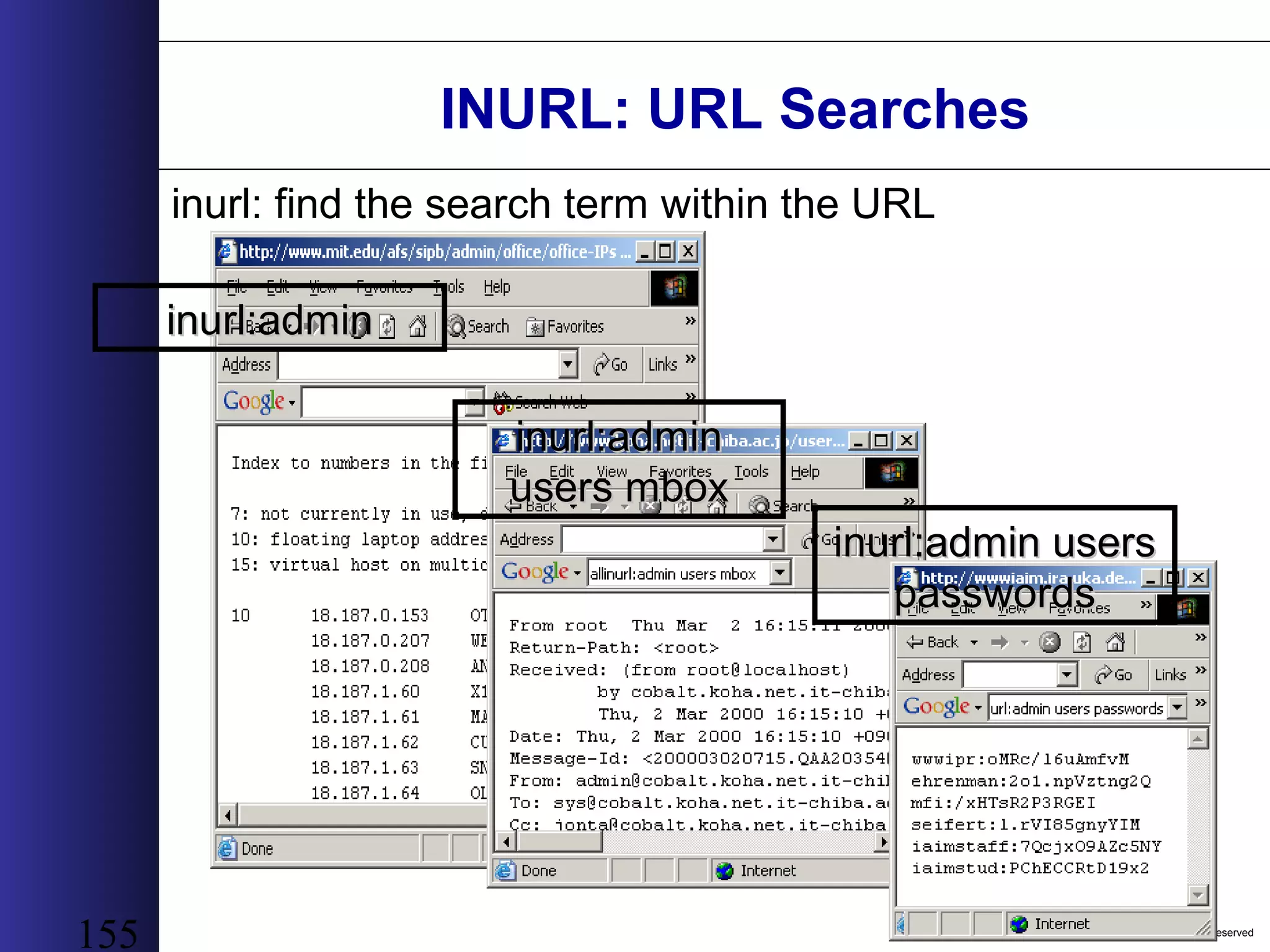
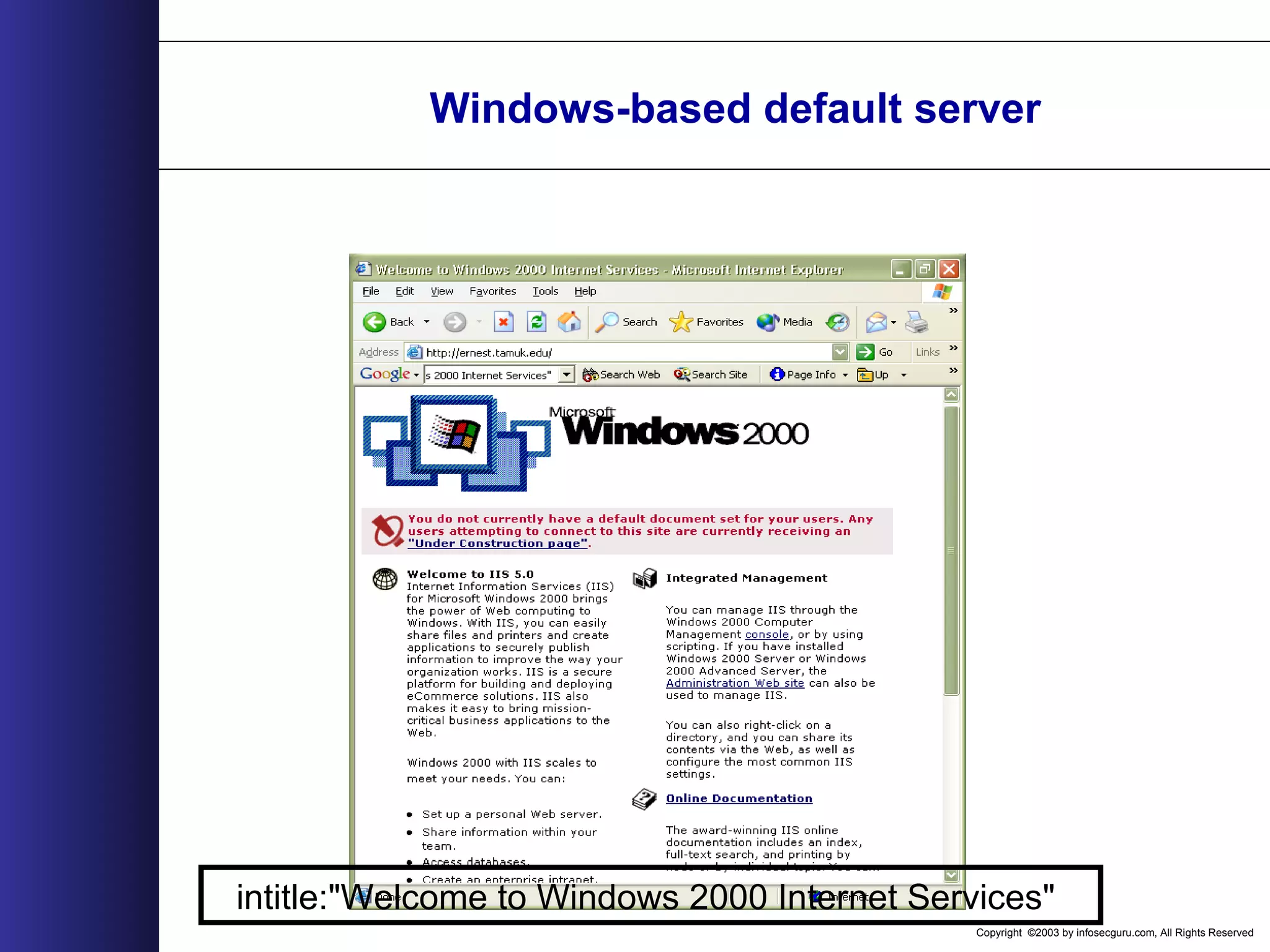
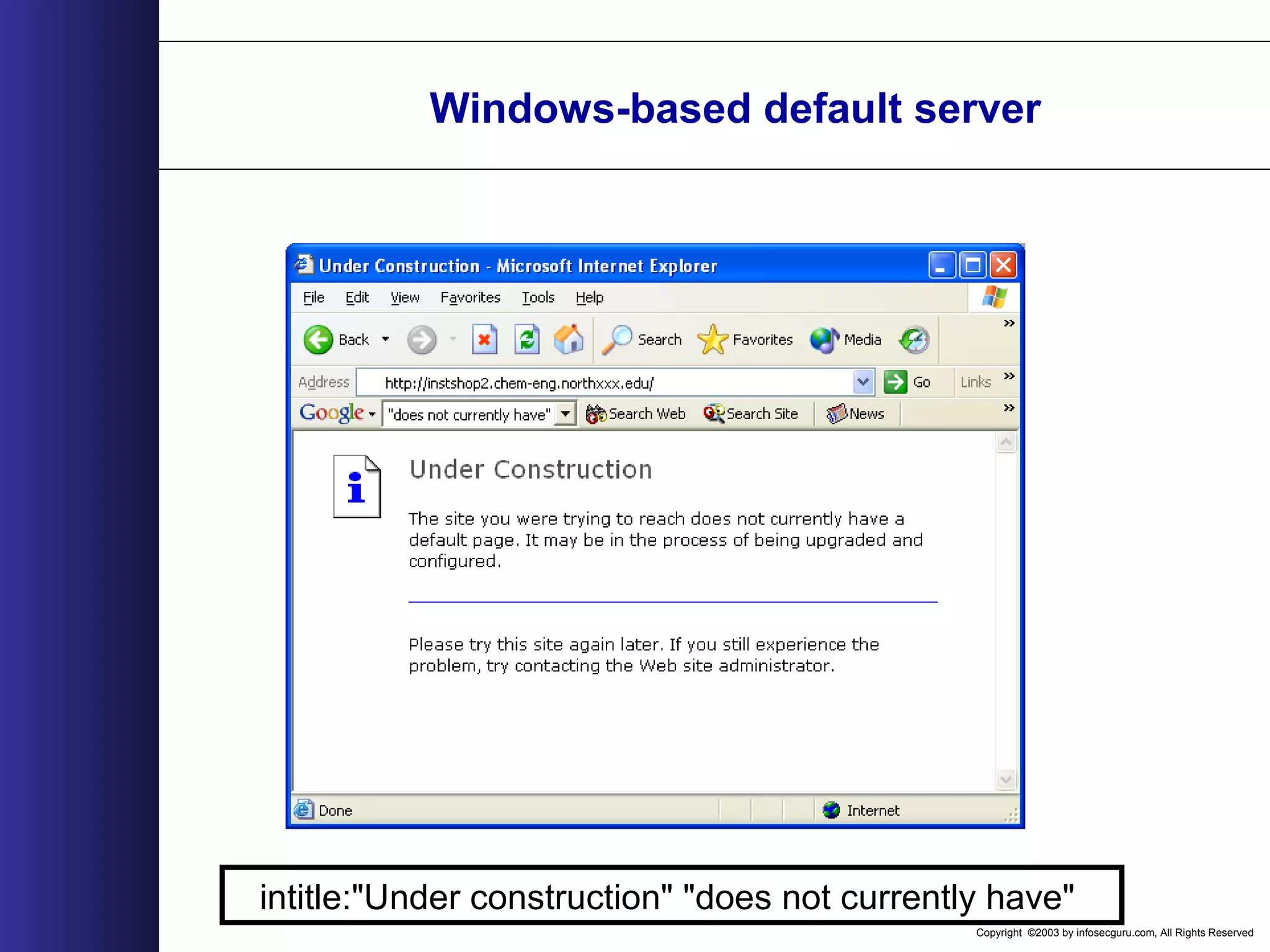
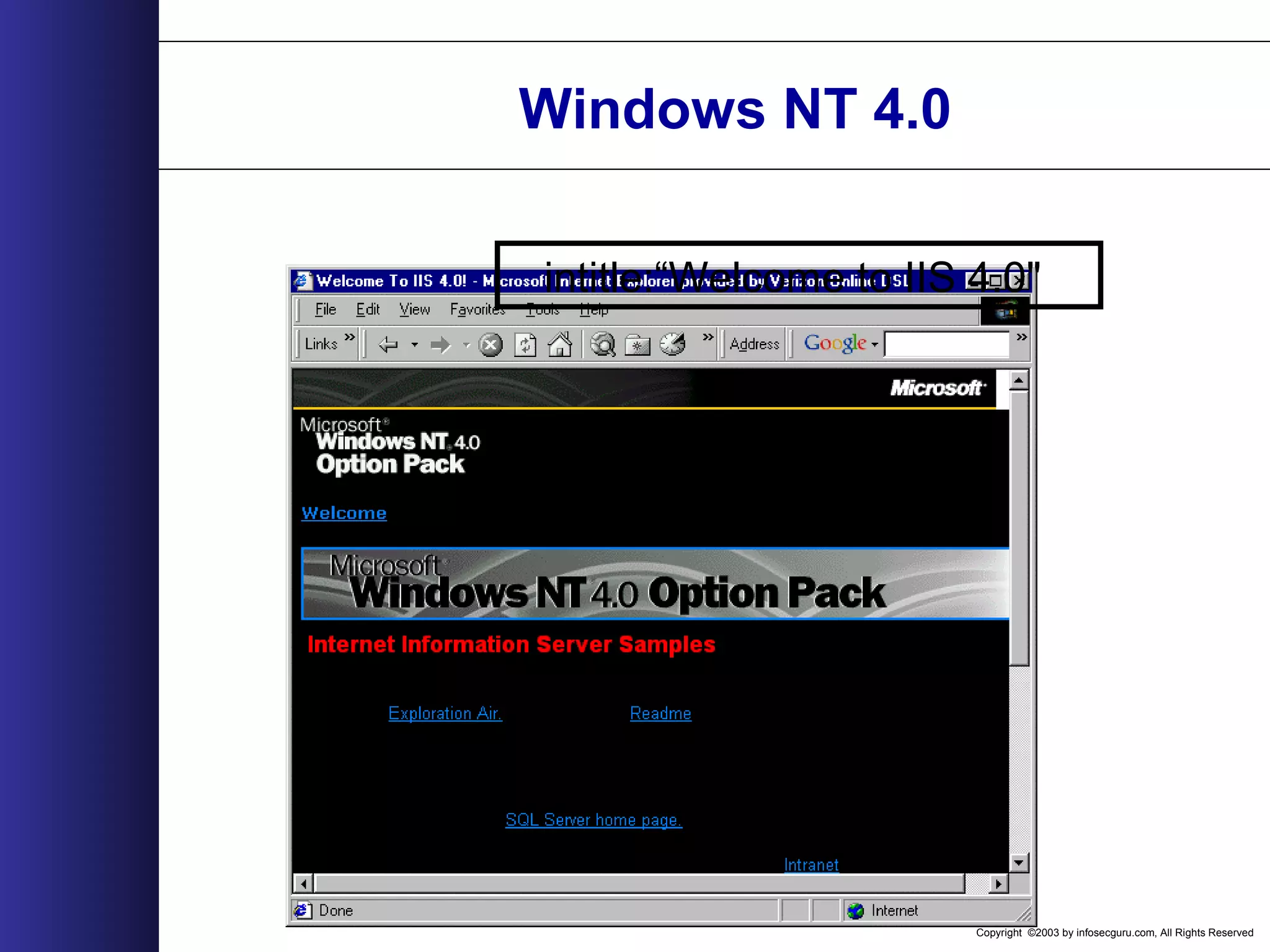
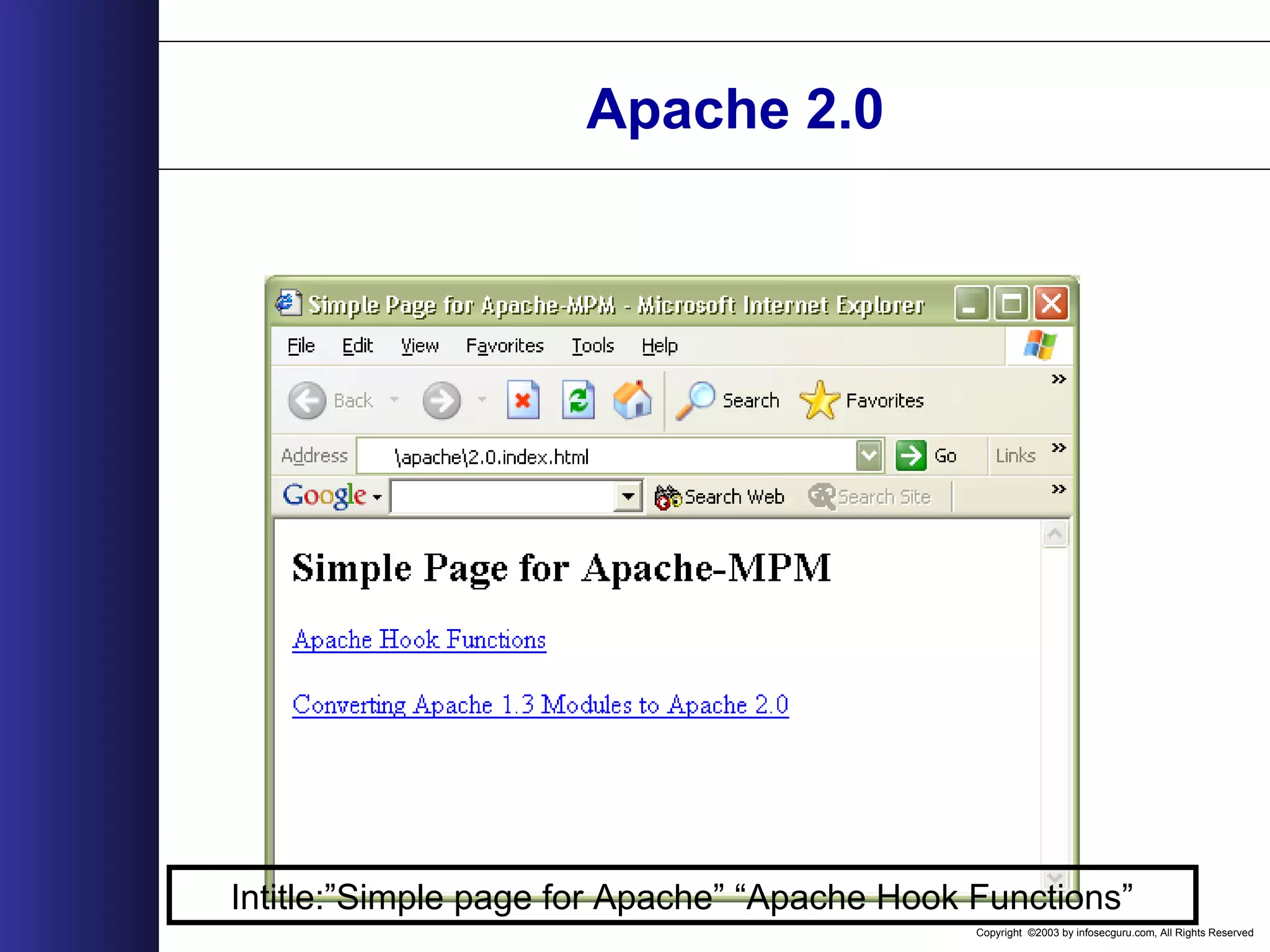
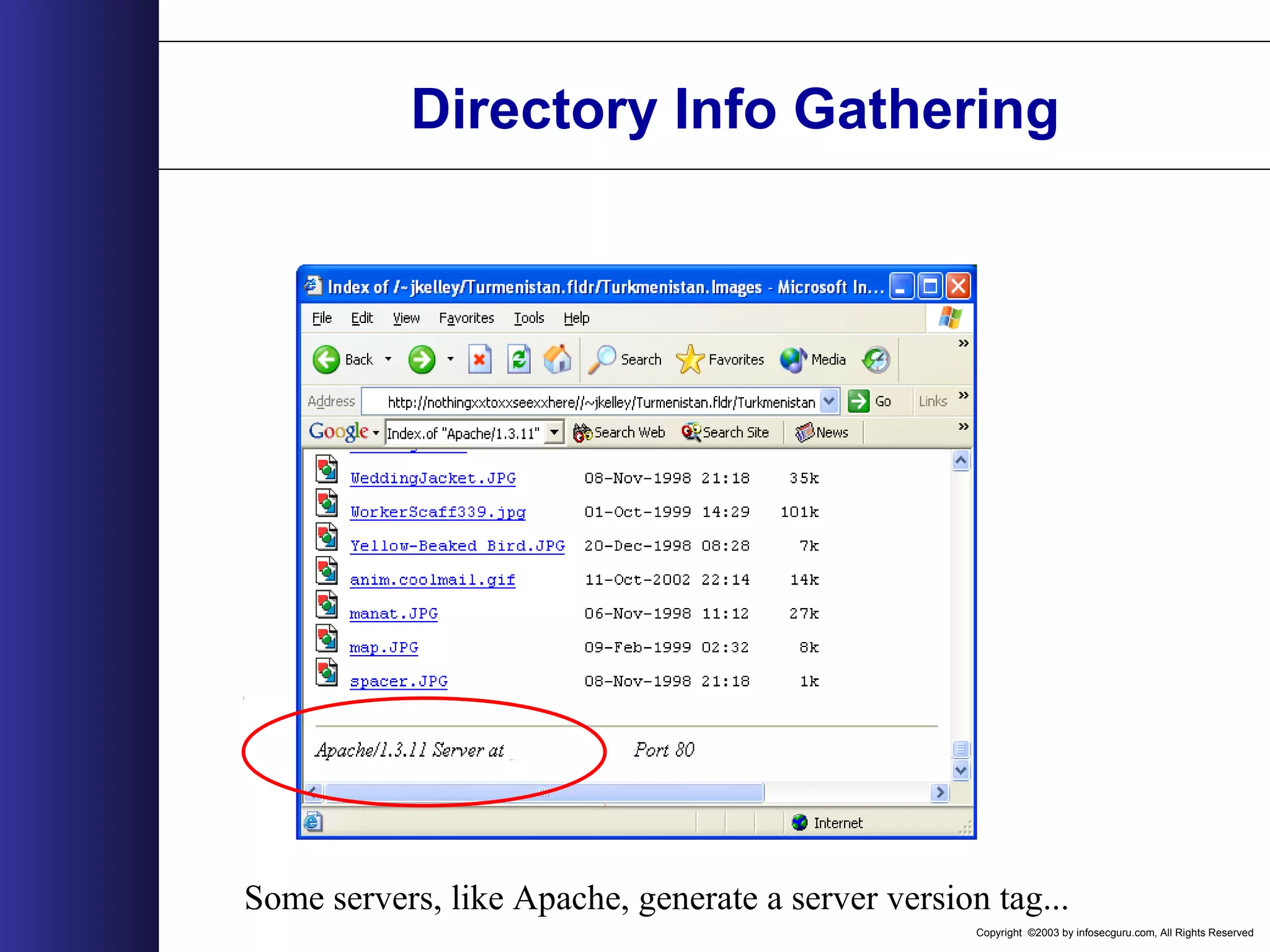
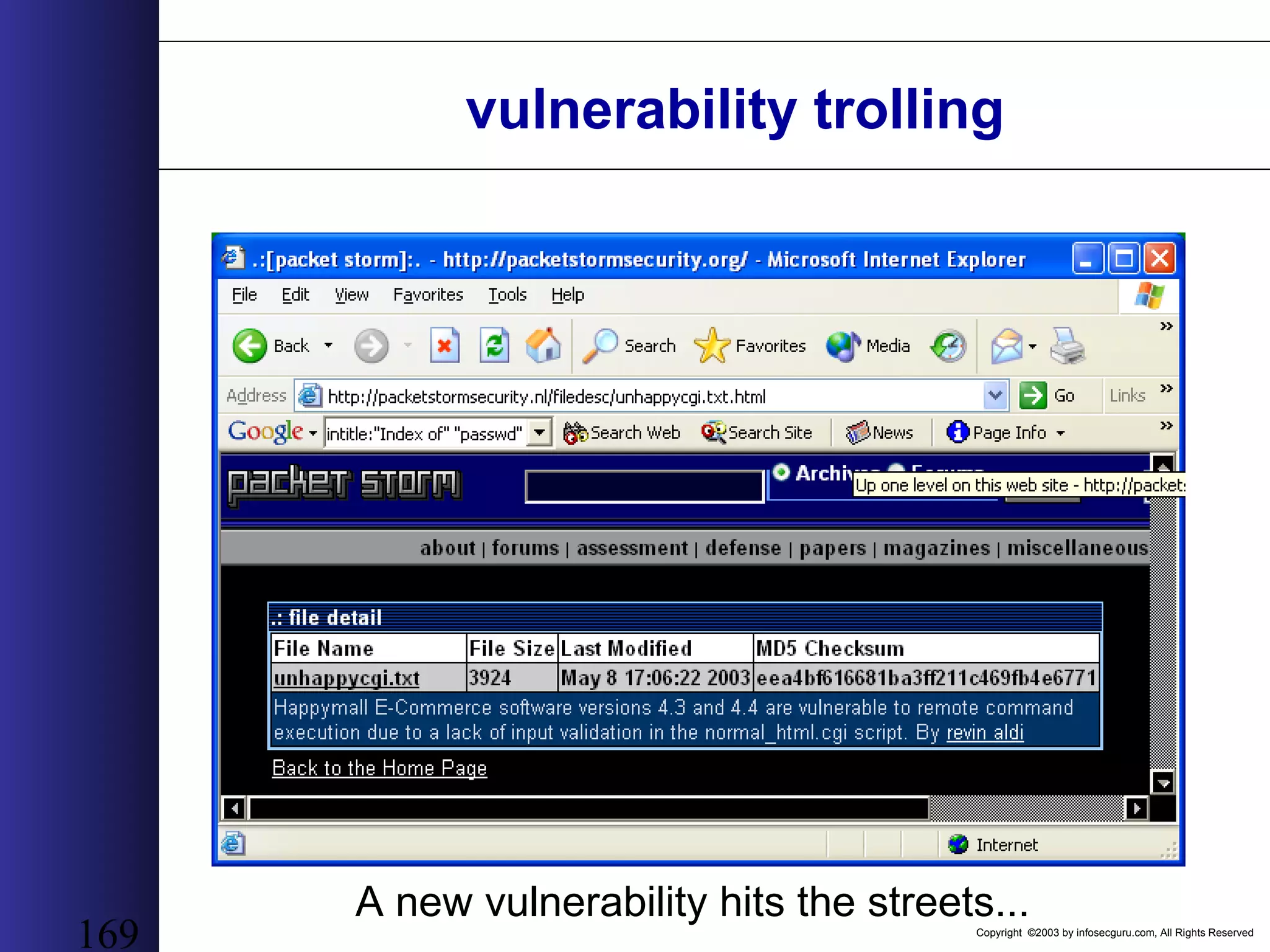
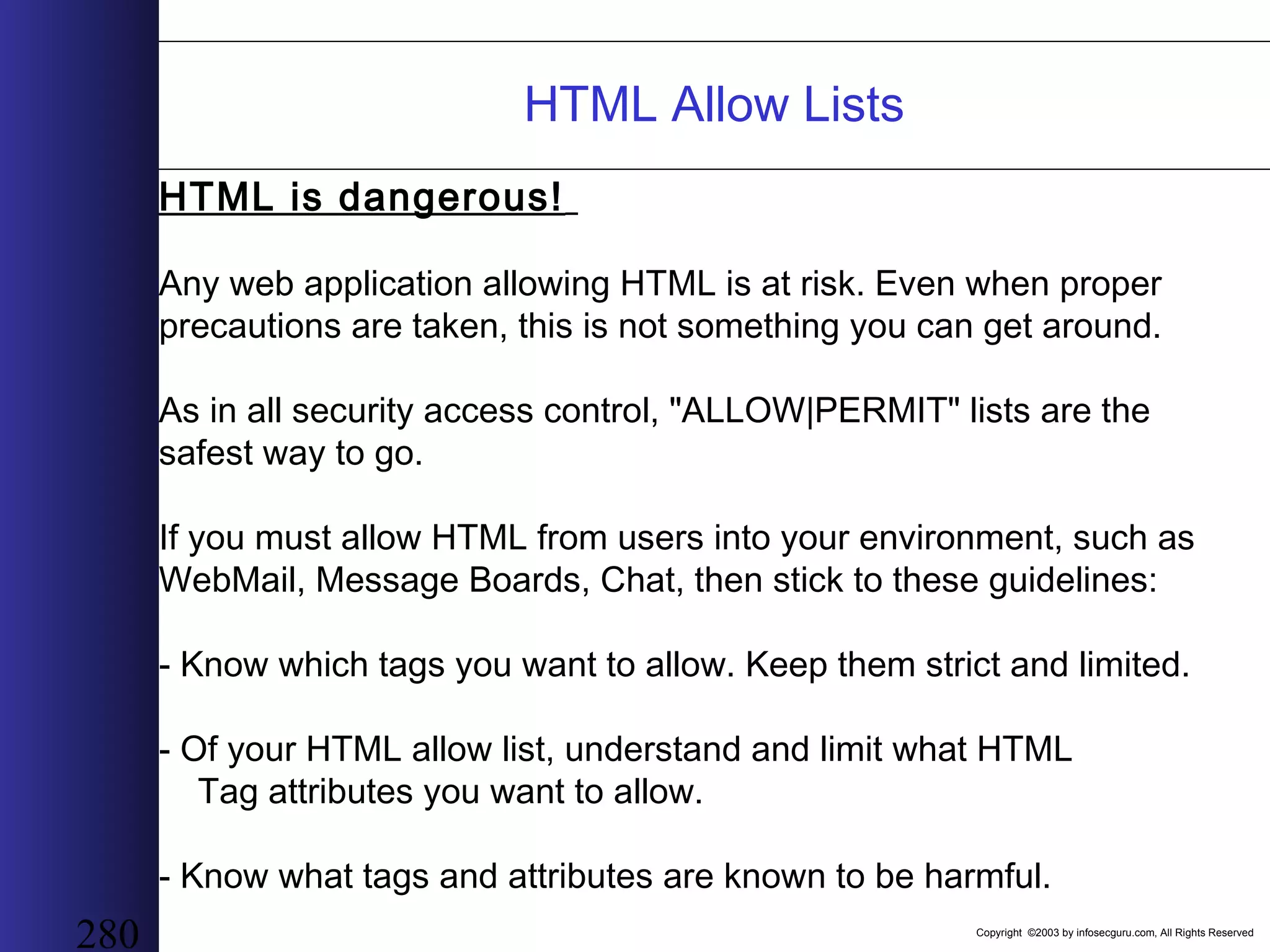
This document outlines an agenda for a two-day training on web application hacking. Day one covers topics like internet crime and motivation for web security, the OWASP top 10 list of vulnerabilities, HTTP and HTML, and Google hacking. Day two covers fingerprinting web servers, basic and advanced web application hacking techniques, and automated tool sets. The document provides background on why web application security is important given the prevalence of attacks on the application layer and examples of recent hacks. It establishes that web applications need to be secured as they now control valuable data and have become attractive targets for criminals.




































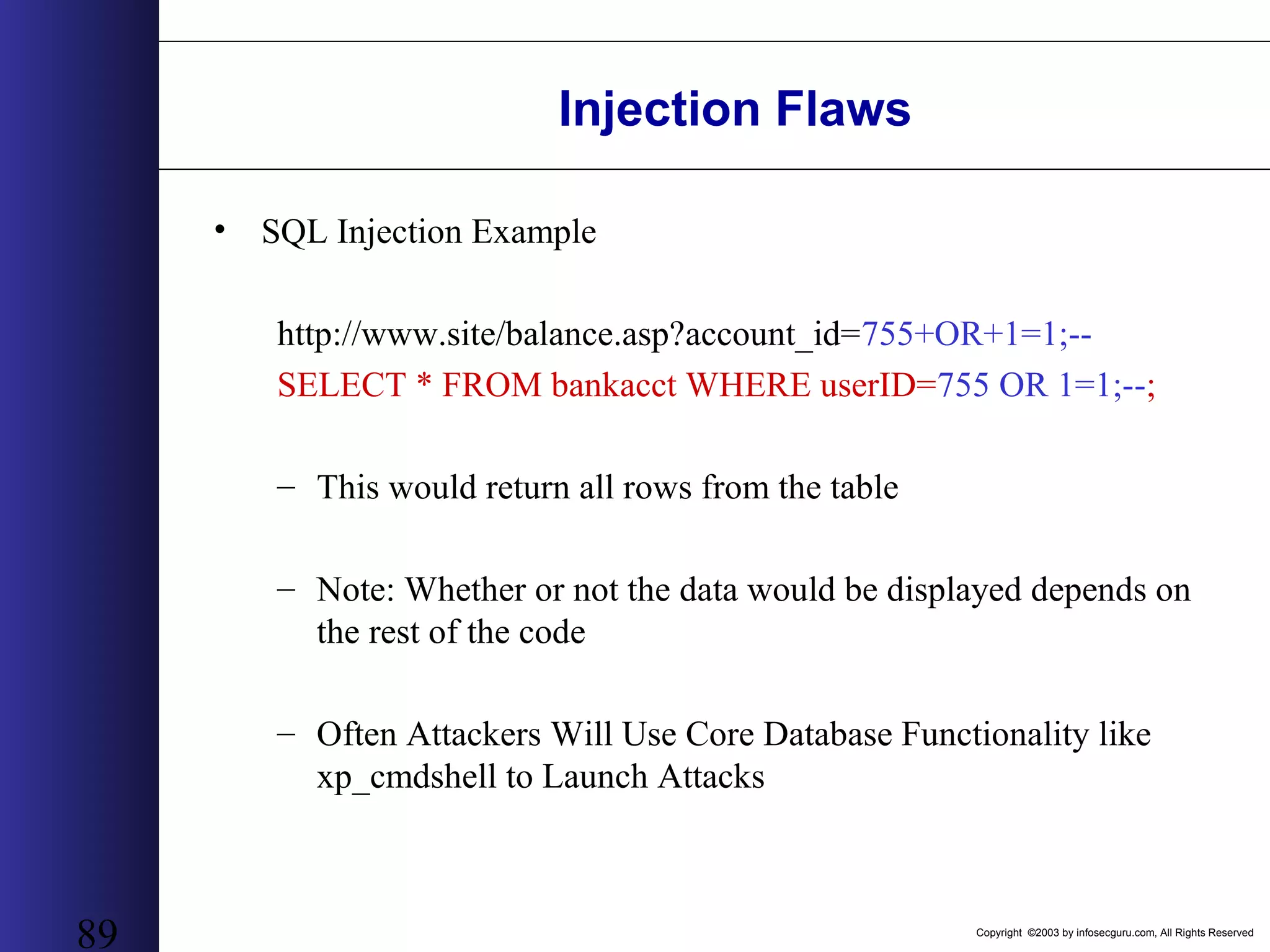



























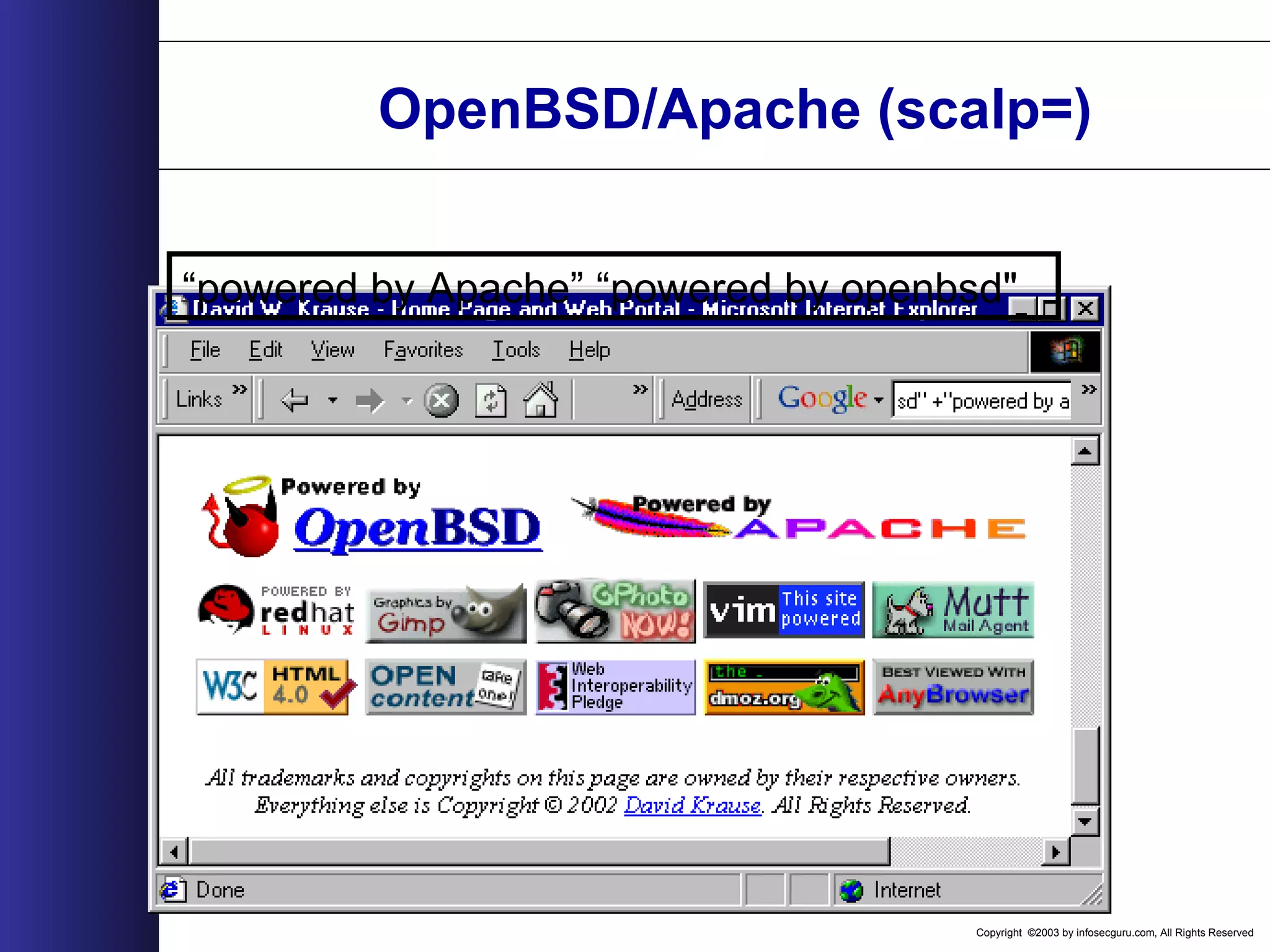
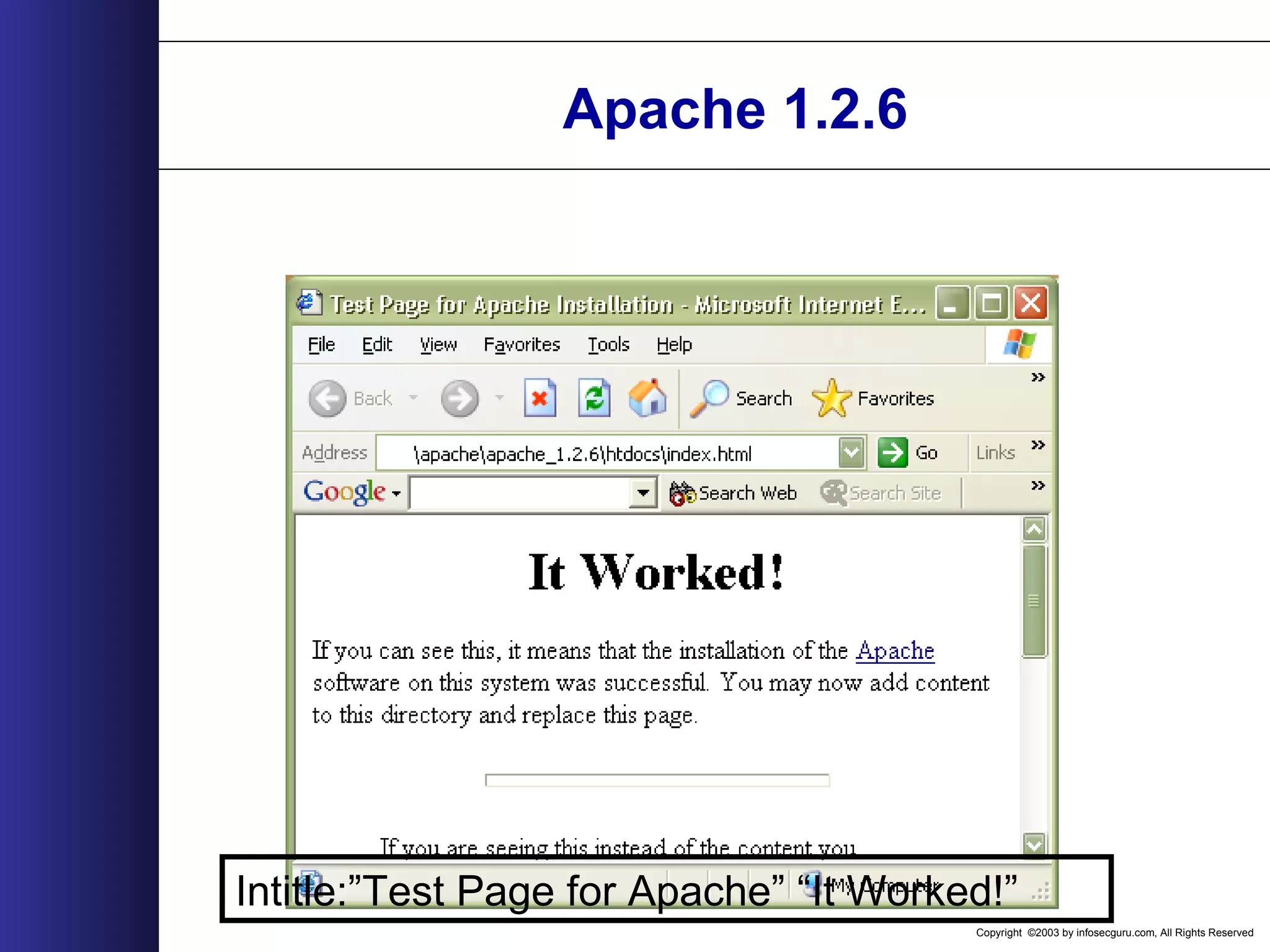
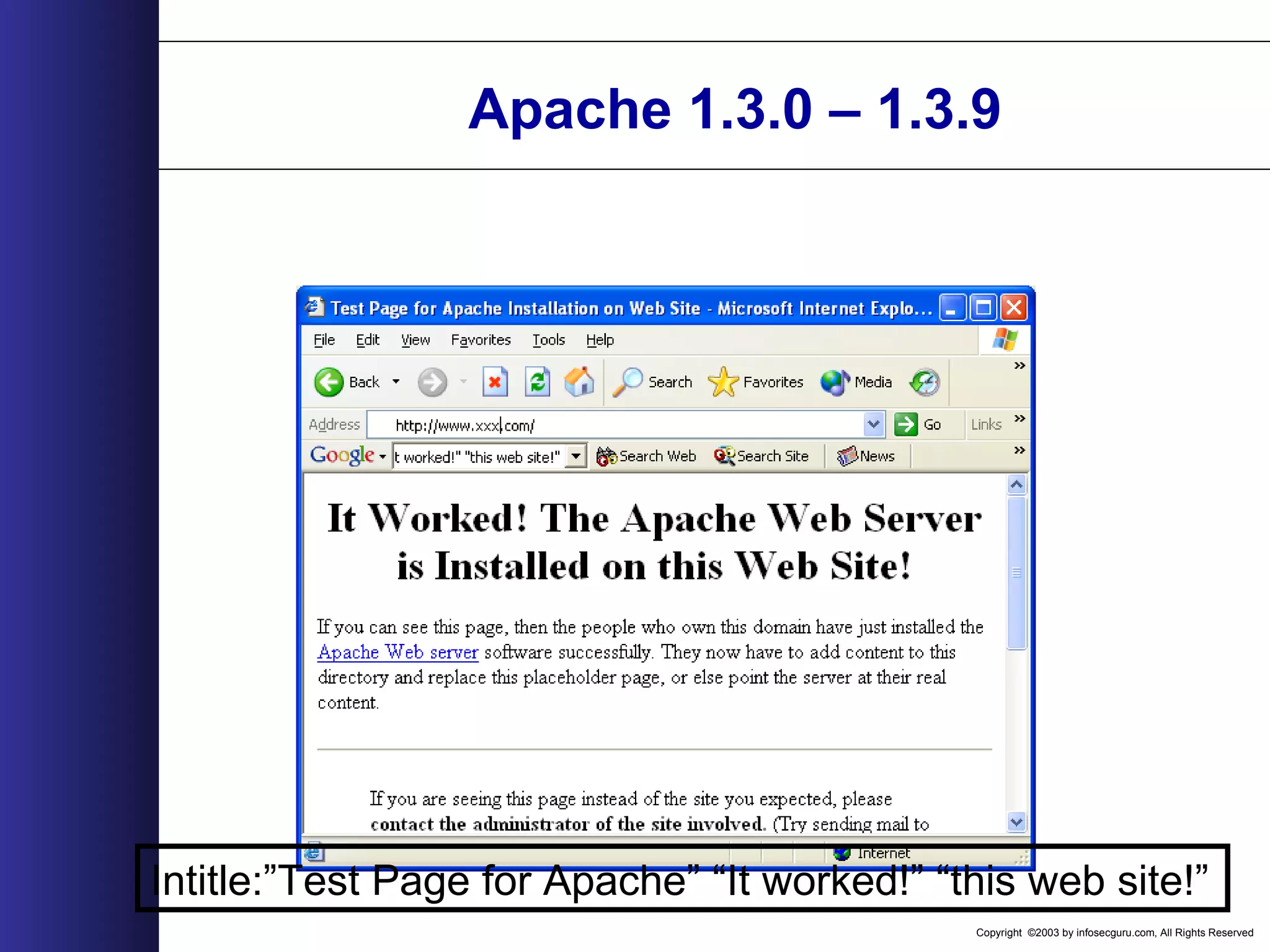
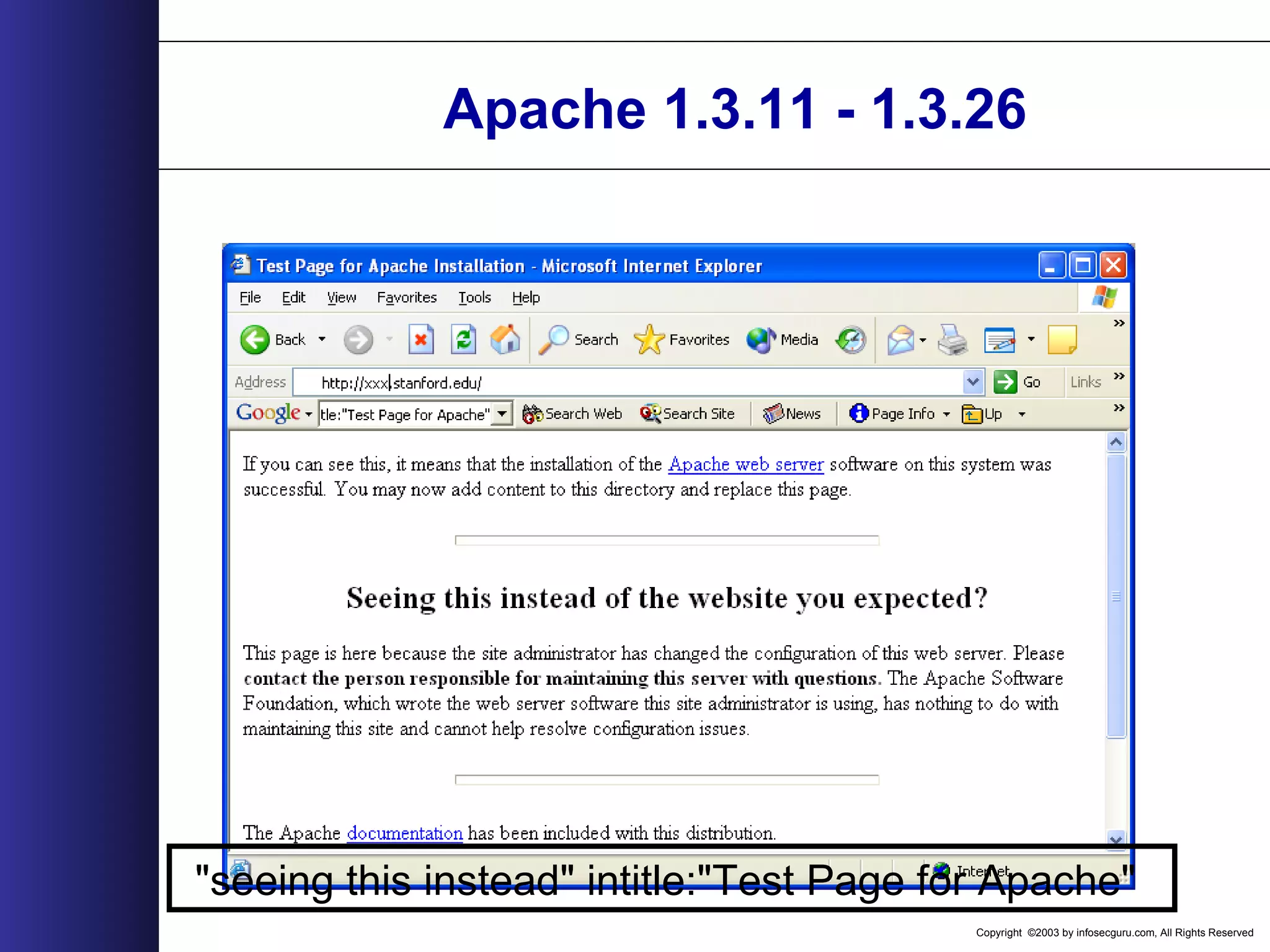
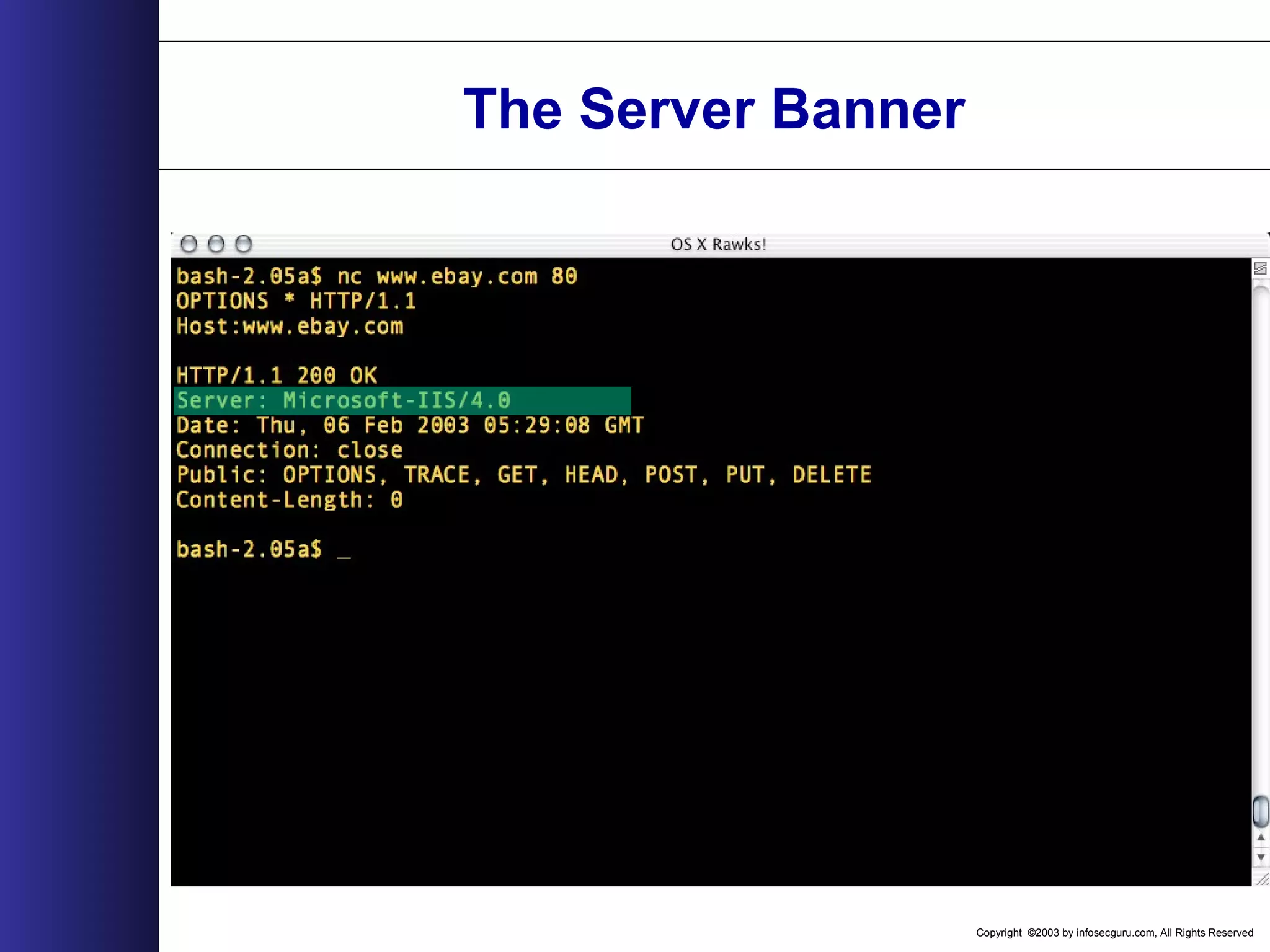
![Copyright ©2003 by infosecguru.com, All Rights Reserved Weird Apache Versions Esoteric Apache Versions found on Google query: intitle:"Index of" "Apache/[ver] Server at" 310 27,300 5 60,500 69,300 74 61 3 9 20 2 1,130 474 62,900 9,400 73933 30 207 93245 1,120 65,00064,200 45,200 0 10000 20000 30000 40000 50000 60000 70000 80000 1.2.6 1.3b6 1.3.0 1.3.1 1.3.2 1.3.4-dev 1.3.4 1.3.7-dev 1.3.11 1.3.15-dev 1.3.17 1.3.17-HOF 1.3.21-dev 1.3.23-dev 1.3.24-dev 1.3.26+interserver 1.3.xx 2.0.16 2.0.18 2.0.28 2.0.32 2.0.35 2.0.36 2.0.37-dev 2.0.40-dev A p a c h e V e r s i o n NumberofServers](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-167-2048.jpg)
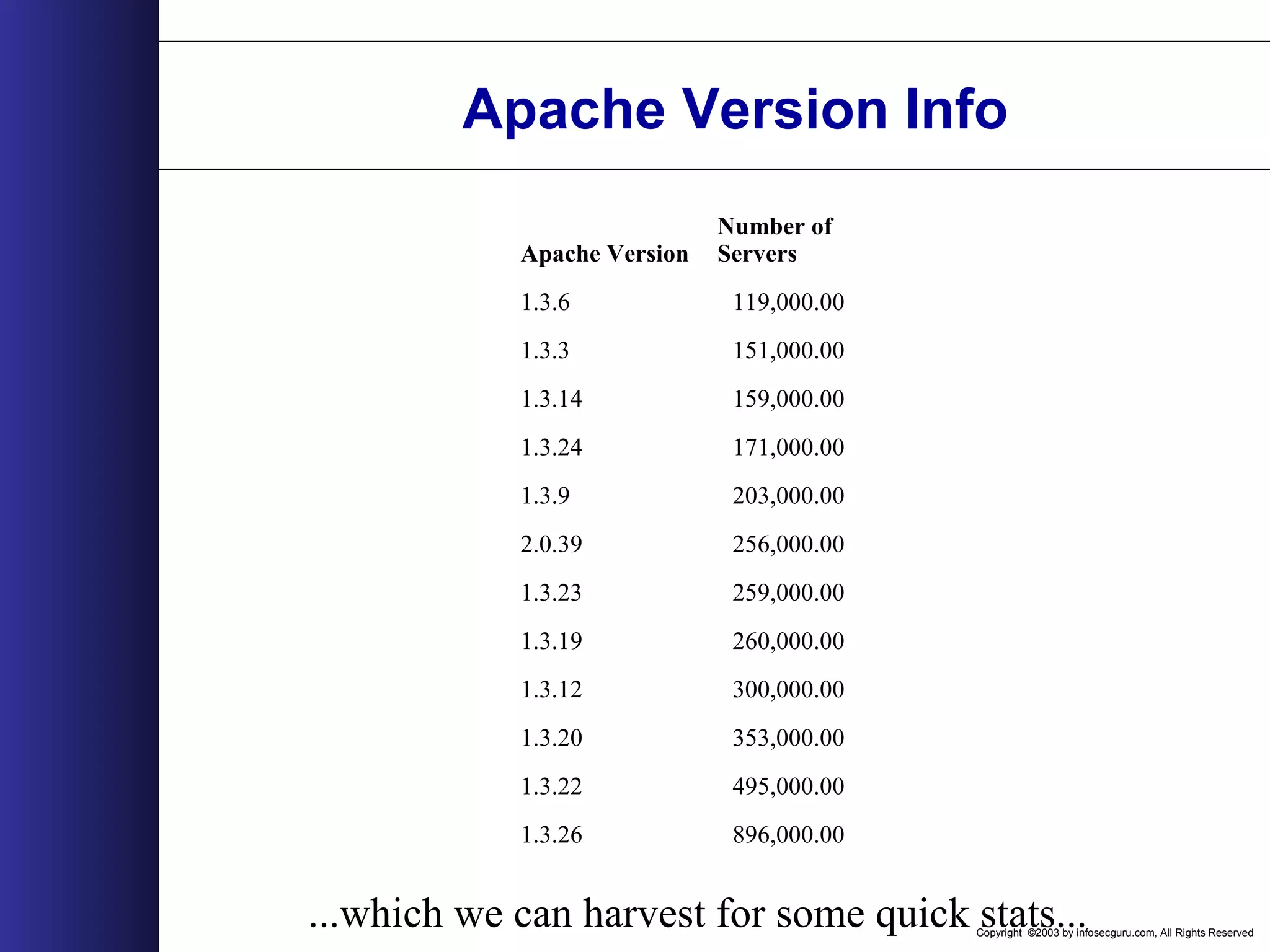
![Copyright ©2003 by infosecguru.com, All Rights Reserved Common Apache Versions Common Apache Versions found on Google query: intitle:"Index of" "Apache/[ver] Server at" 159,000 260,000 353,000 495,000 259,000 171,000 896,000 256,000 119,000 151,000 203,000 300,000 0.00 200,000.00 400,000.00 600,000.00 800,000.00 1,000,000.00 1.3.12 1.3.14 1.3.19 1.3.20 1.3.22 1.3.23 1.3.24 1.3.26 1.3.3 1.3.6 1.3.9 2.0.39 Apache Server Version NumberofServers](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-168-2048.jpg)




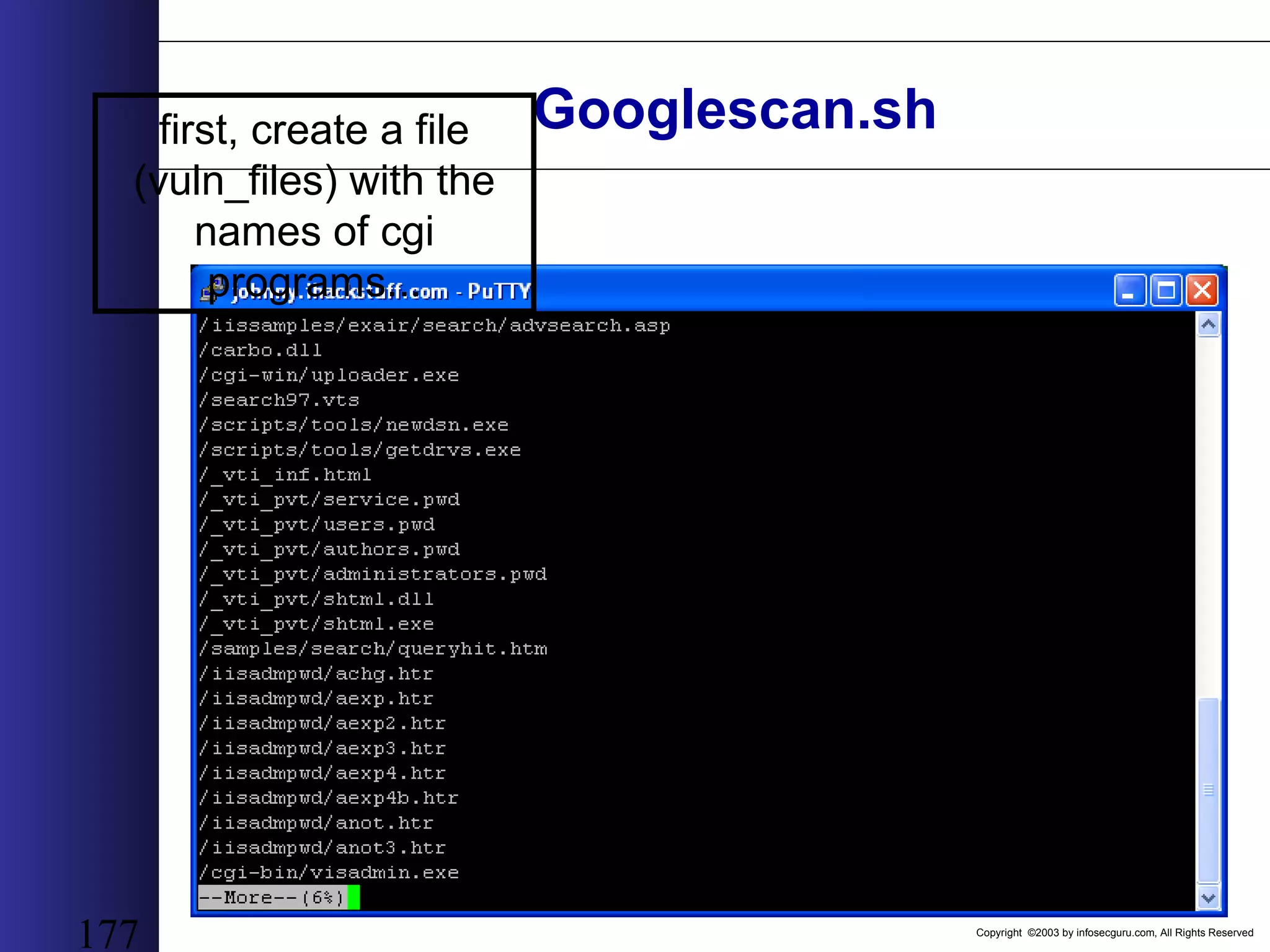
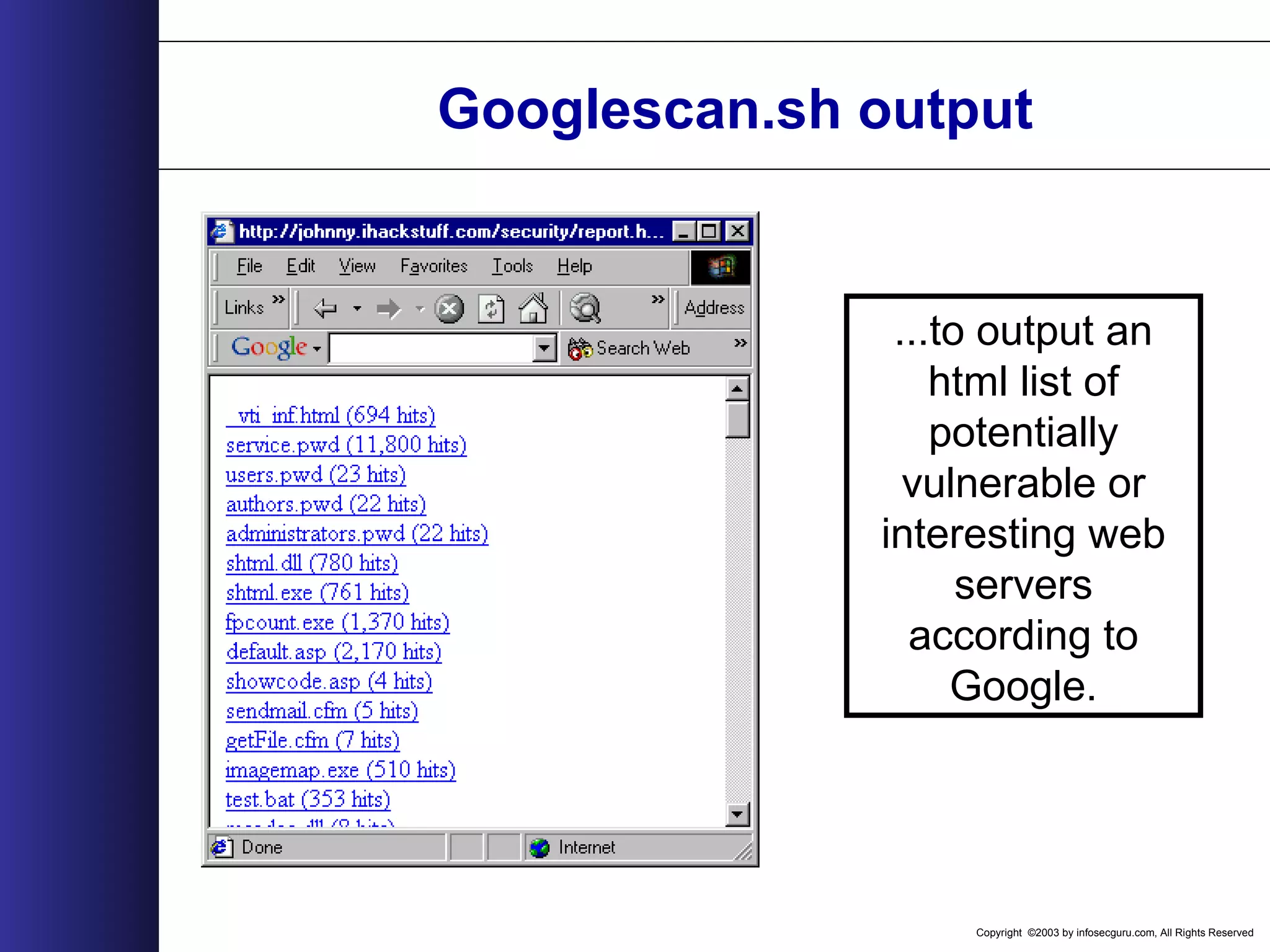
![Copyright ©2003 by infosecguru.com, All Rights Reserved Googlescan.sh rm temp awk -F"/" '{print $NF"|http://www.google.com/search?q= intitle%3A%22Index+of%22+"$NF}' vuln_files > queries for query in `cat queries` do echo -n $query"|" >> temp echo $query | awk -F"|" '{print $2}' lynx -source `echo $query | awk -F"|" '{print $2}'` | grep "of about" | awk -F "of about" '{print $2}' | awk -F"." '{print $1}' | tr -d "</b>[:cntrl:] " >> temp echo " " >> temp Done cat temp | awk -F"|" '{print "<A HREF="" $2 "">" $1 " (" $3 "hits) </A><BR><BR>"}' | grep -v "(1,770,000" > report.html ...then, use this shell script...](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-178-2048.jpg)












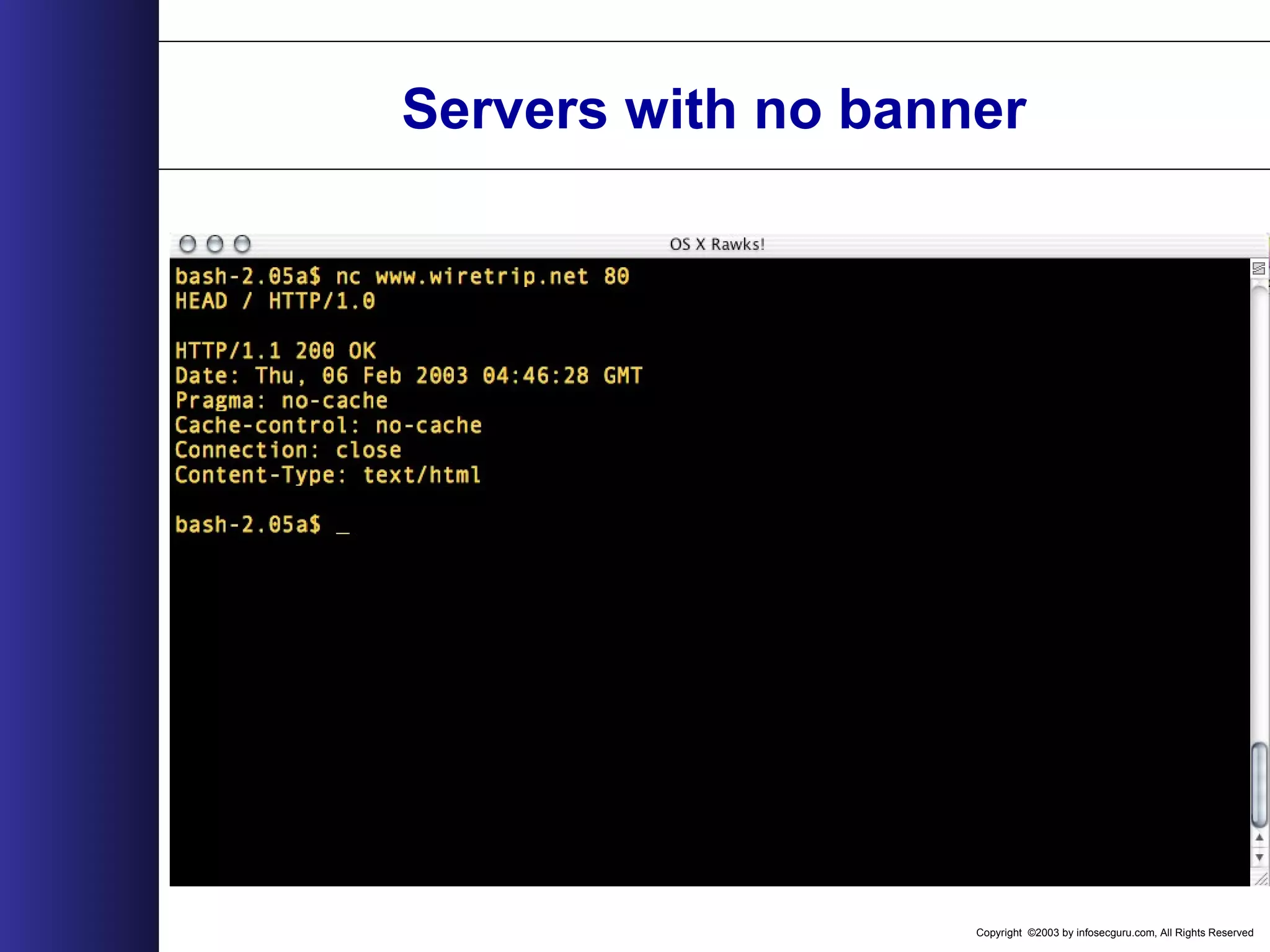


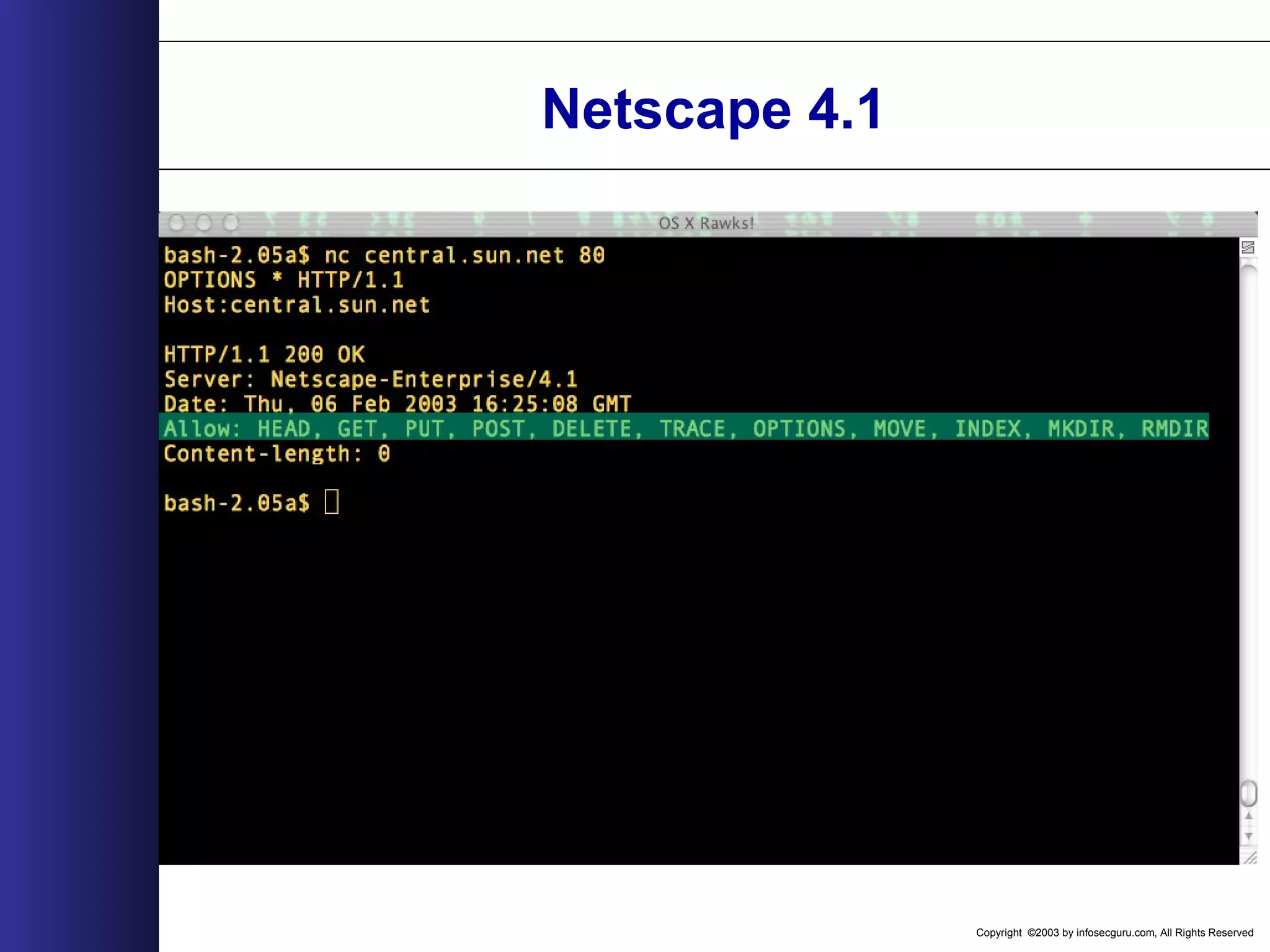






































![Copyright ©2003 by infosecguru.com, All Rights Reserved Server Specific Server Specific (Resolutions should be confirmed by appropriate vendor) IIS - URL Scan Apache - Source Code Modification - Mod_Rewrite Module RewriteEngine onRewriteCond %{REQUEST_METHOD} ^TRACERewriteRule .* - [F] (Thank you to Rain Forest Puppy) ** The Limit or LimitExcept directive in the httpd.conf file does not appear to be able to restrict TRACE. **](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-331-2048.jpg)
![Copyright ©2003 by infosecguru.com, All Rights Reserved Microsoft IIS URLScan Add the following line to your URLScan.ini file: [options] UseAllowVerbs=0 [Deny Verbs] TRACE Caution! Can cause some applications to break. (Frontpage,OWA)](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-332-2048.jpg)
![Copyright ©2003 by infosecguru.com, All Rights Reserved Apache mod_rewrite Add the following to your httpd.conf RewriteEngine onRewriteCond % {REQUEST_METHOD} ^TRACE RewriteRule .* - [F]](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-333-2048.jpg)





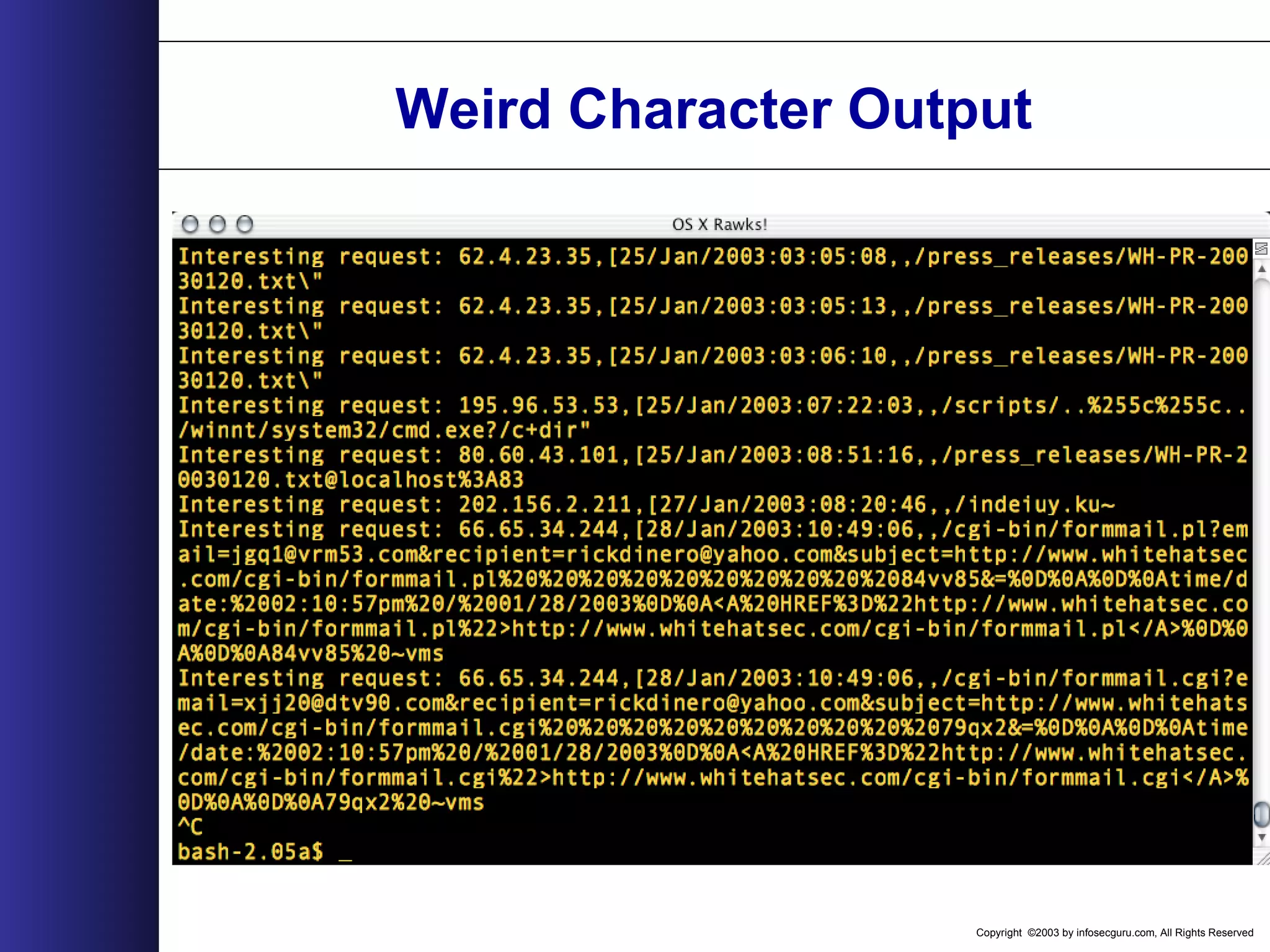
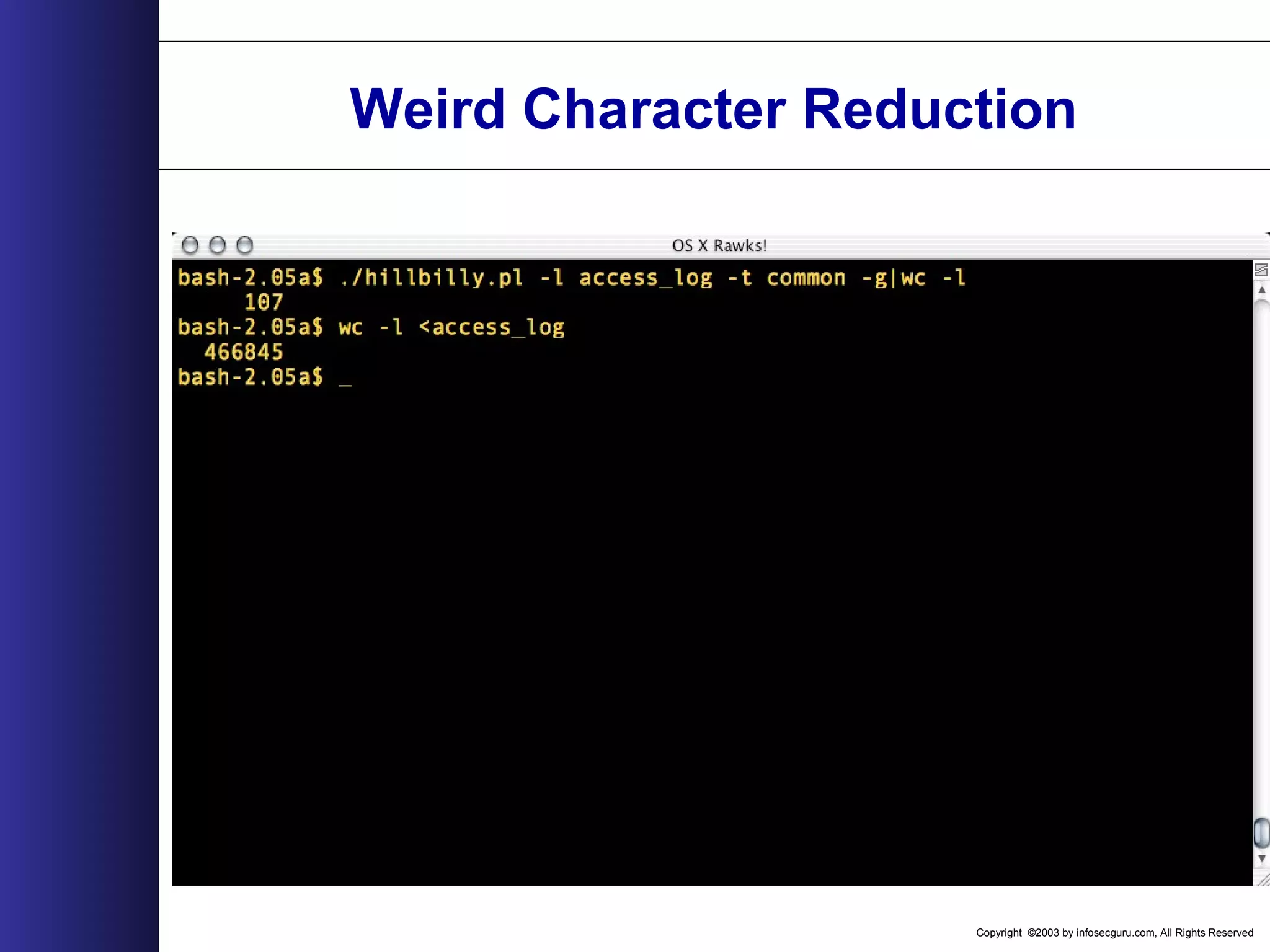
![Copyright ©2003 by infosecguru.com, All Rights Reserved Odd URL search ./hillbilly.pl -t common -l access_log -g Regex = /[^A-Za-z0-9./?(%20)=_&-]/ Looks for request that contain characters other than these. Will find Unicode,Double Decode, Cross Site Scripting, SQL Injection, Command Execution, Directory Traversal in a GET request.](https://image.slidesharecdn.com/wahreva-151017042349-lva1-app6891/75/Web-Application-Hacking-2004-351-2048.jpg)