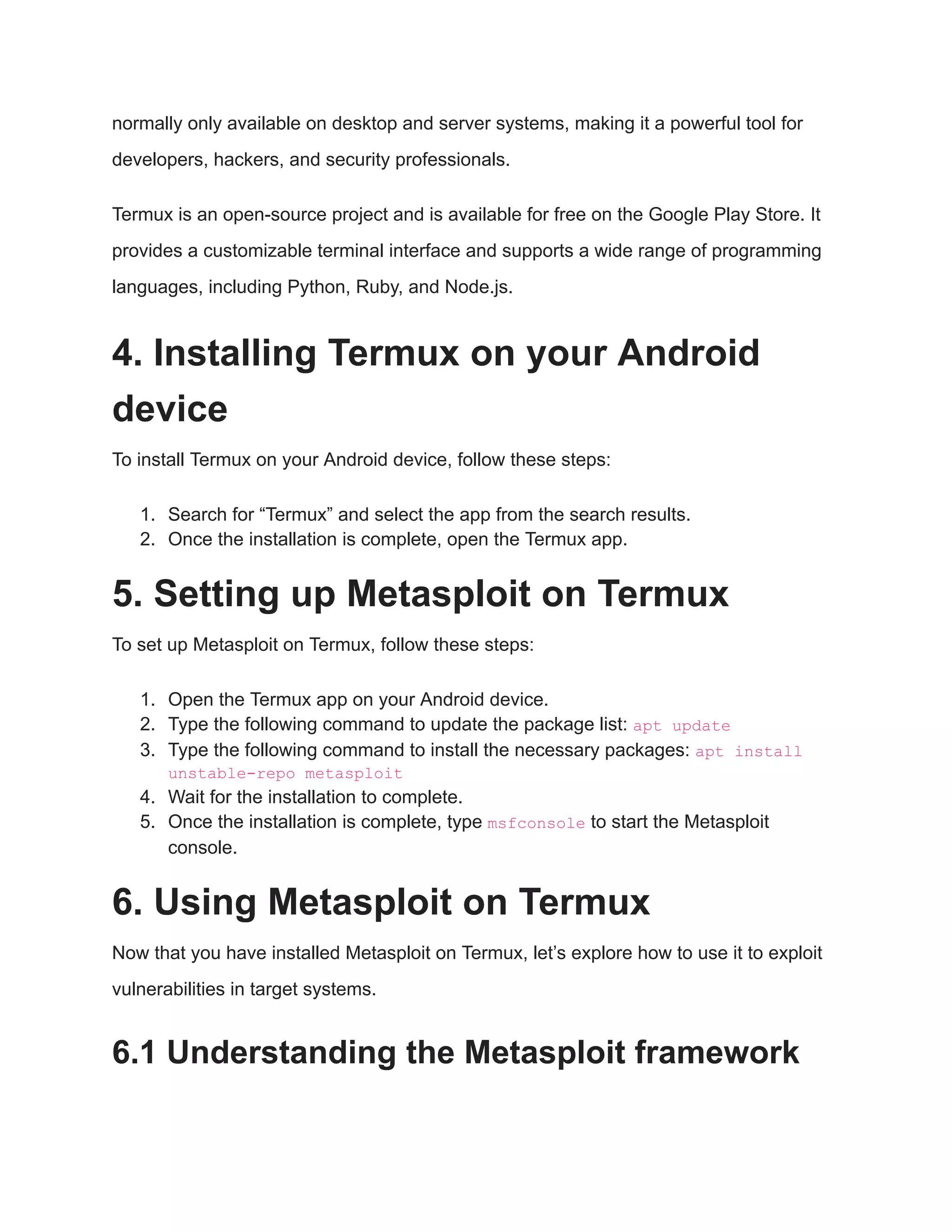
The document provides a comprehensive guide on using Metasploit with Termux on Android devices, covering installation, setup, and exploitation of vulnerabilities. It explains the functionalities of both Metasploit and Termux, detailing their commands and usage for effective security testing. Additionally, it includes tips for responsible use and custom exploit writing, emphasizing the importance of permission when testing systems.