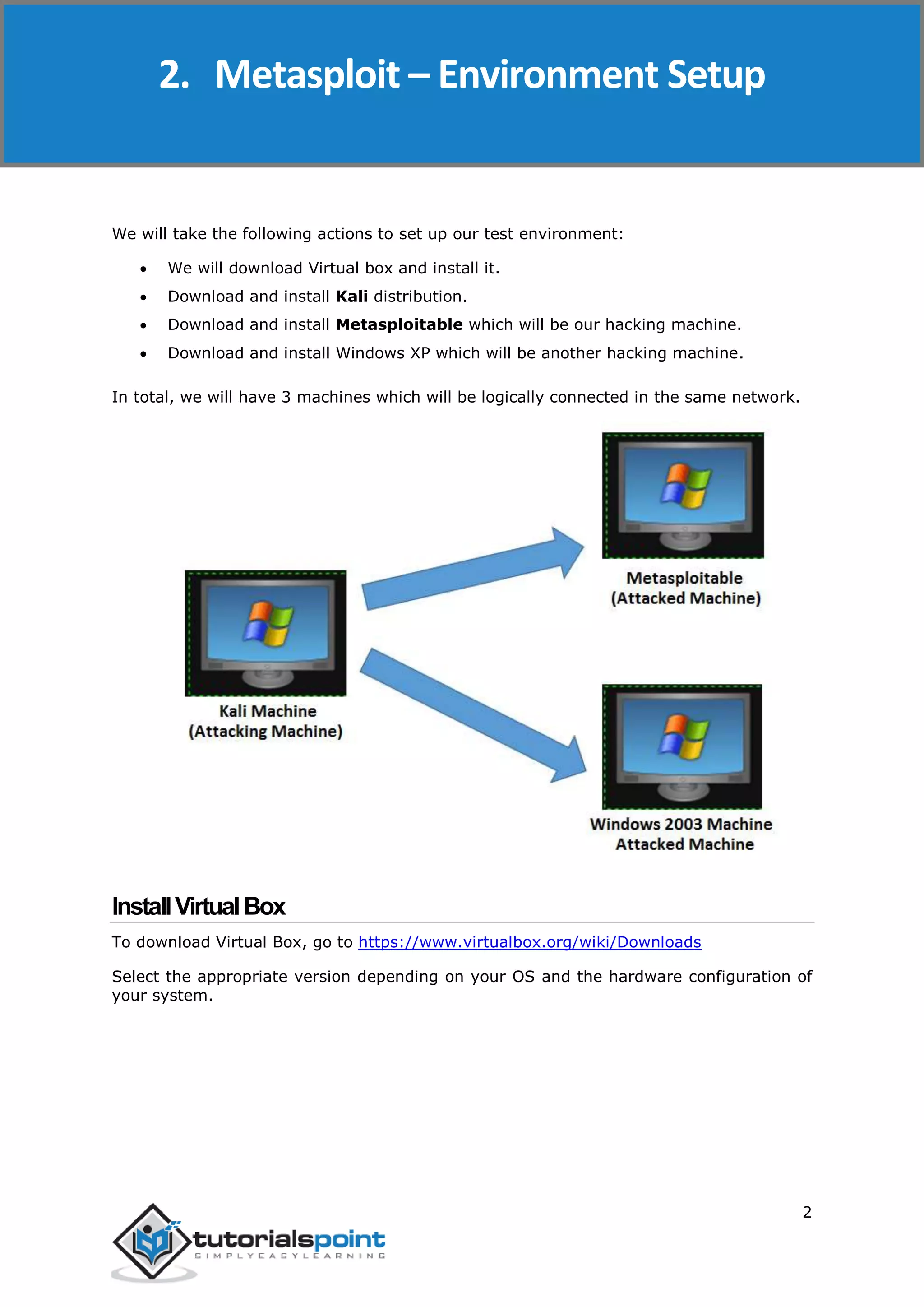
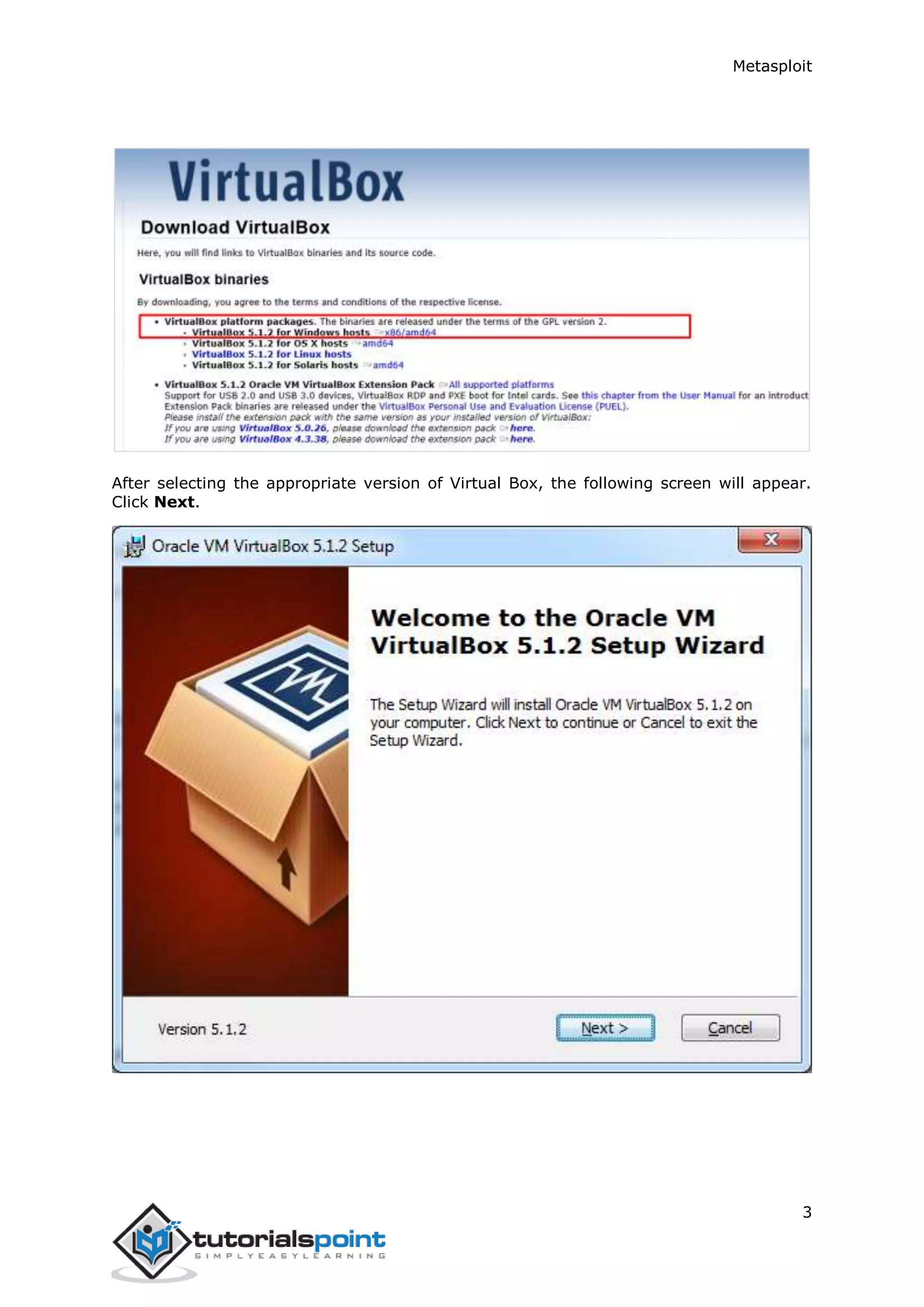
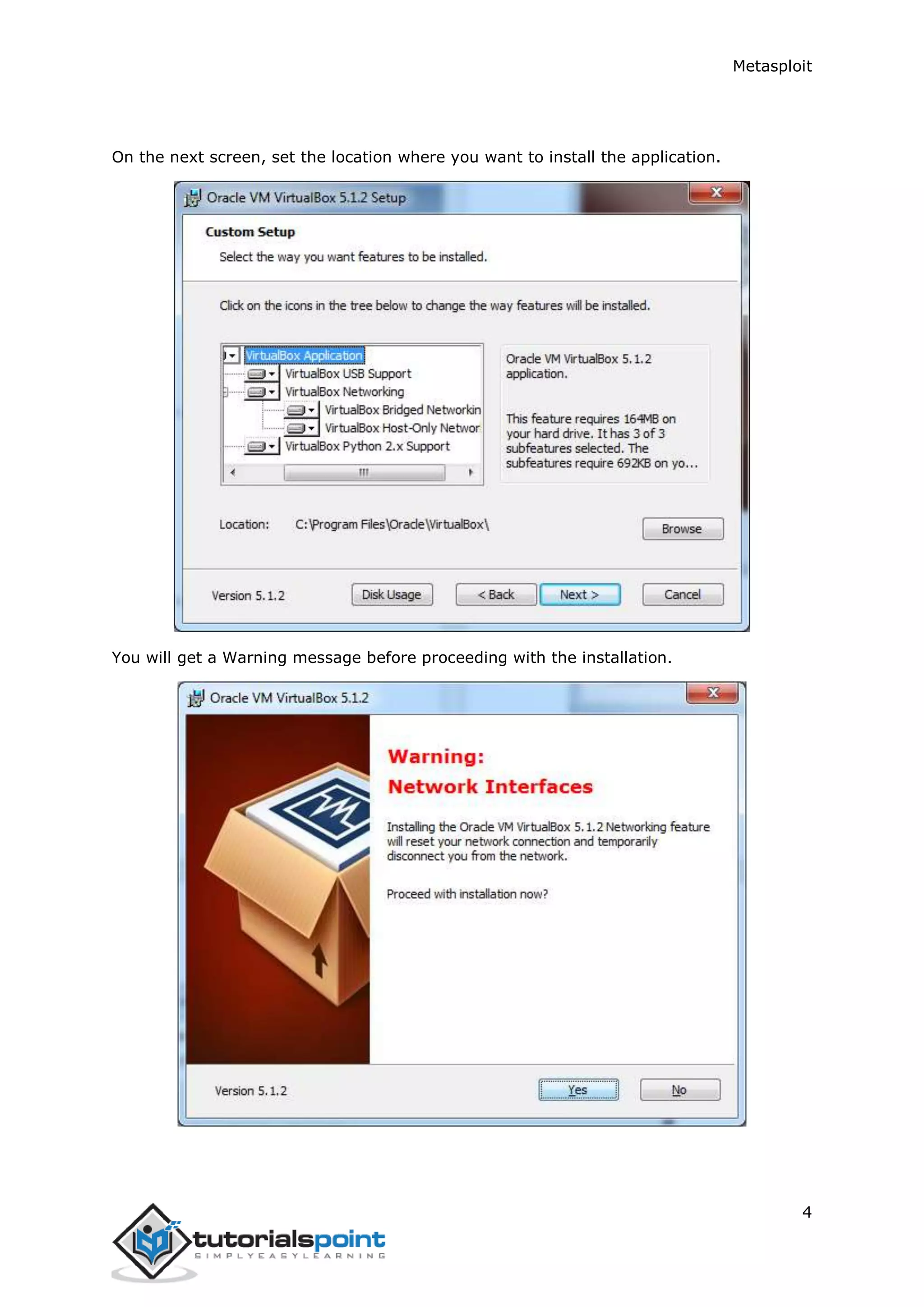
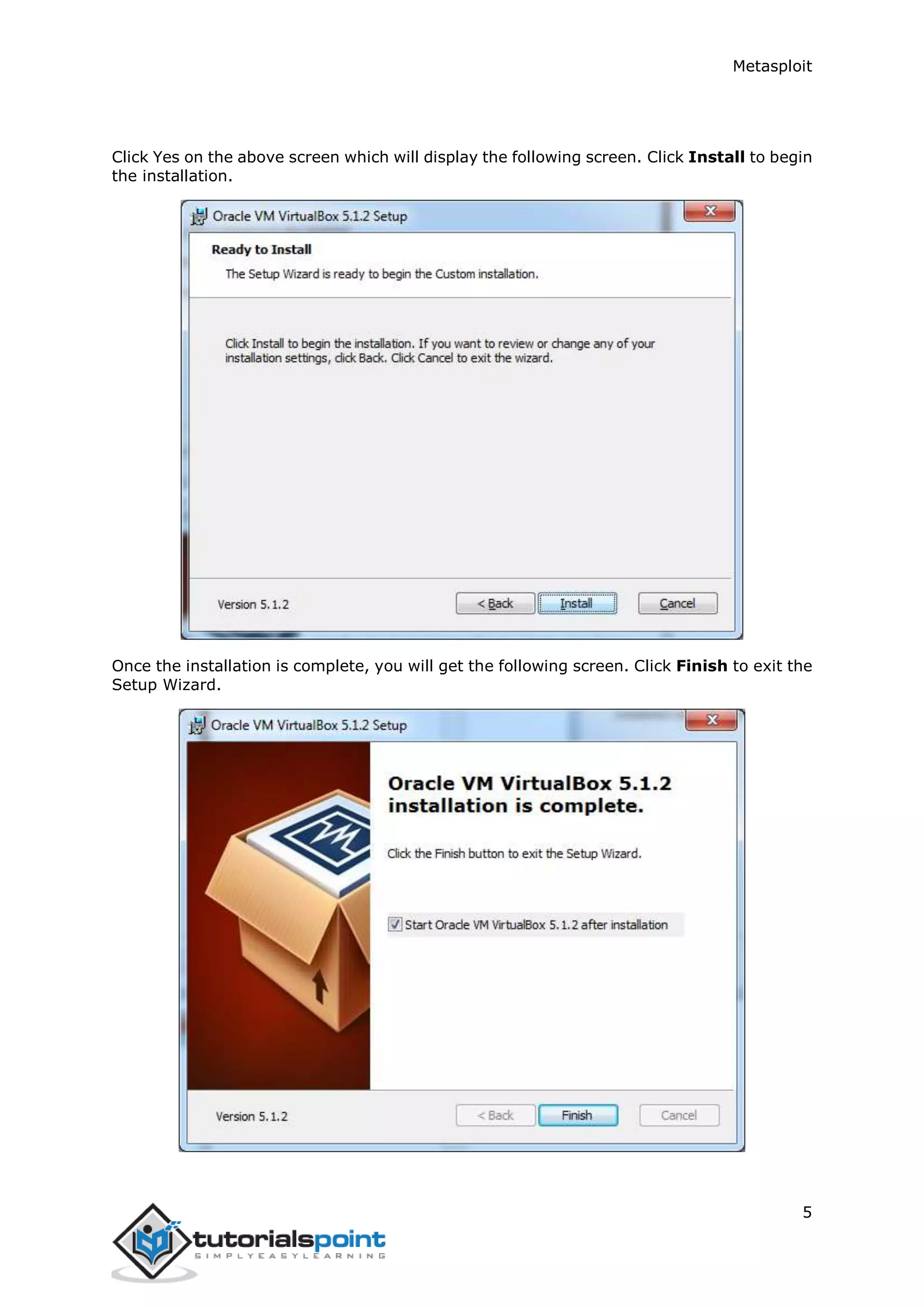
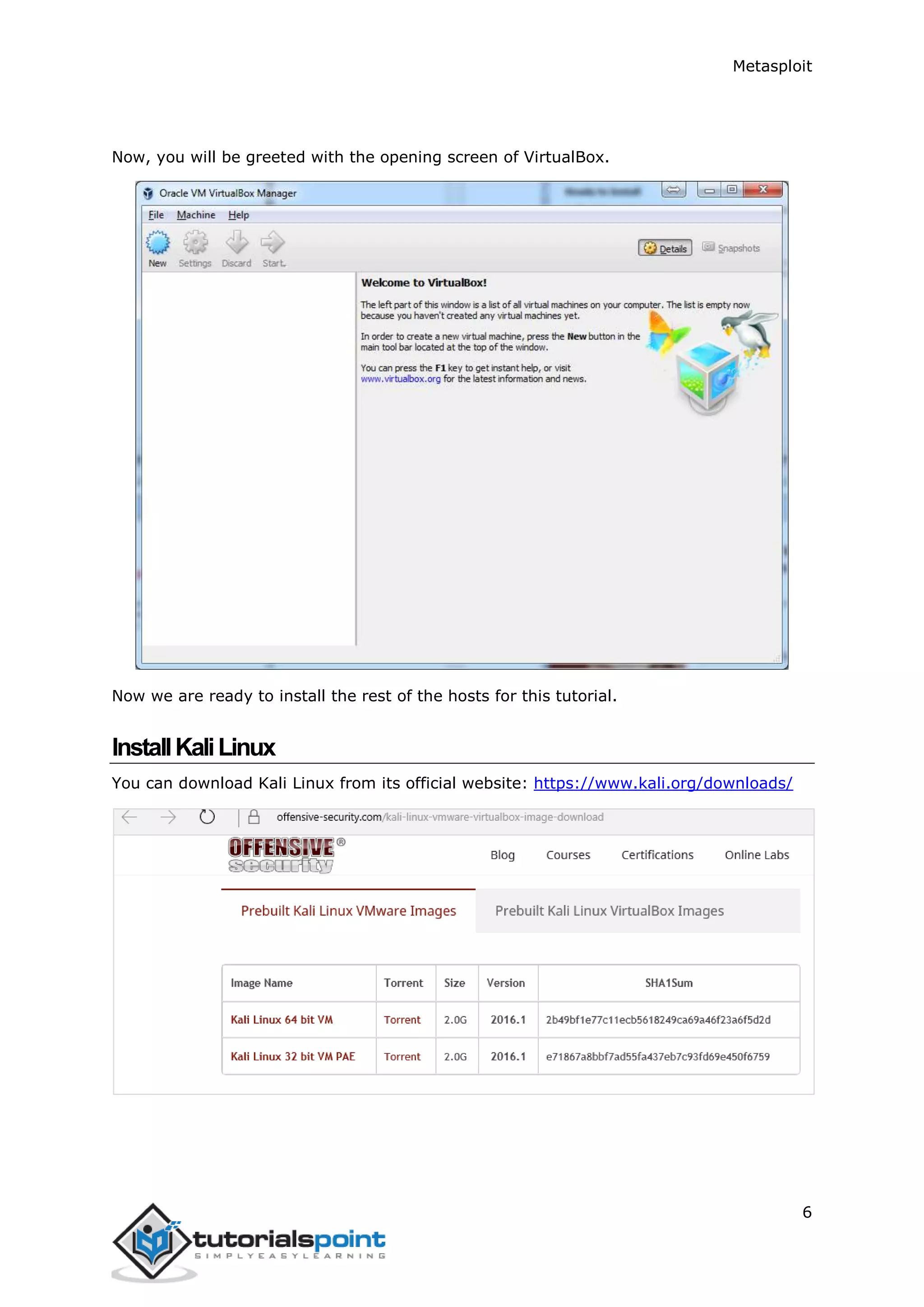
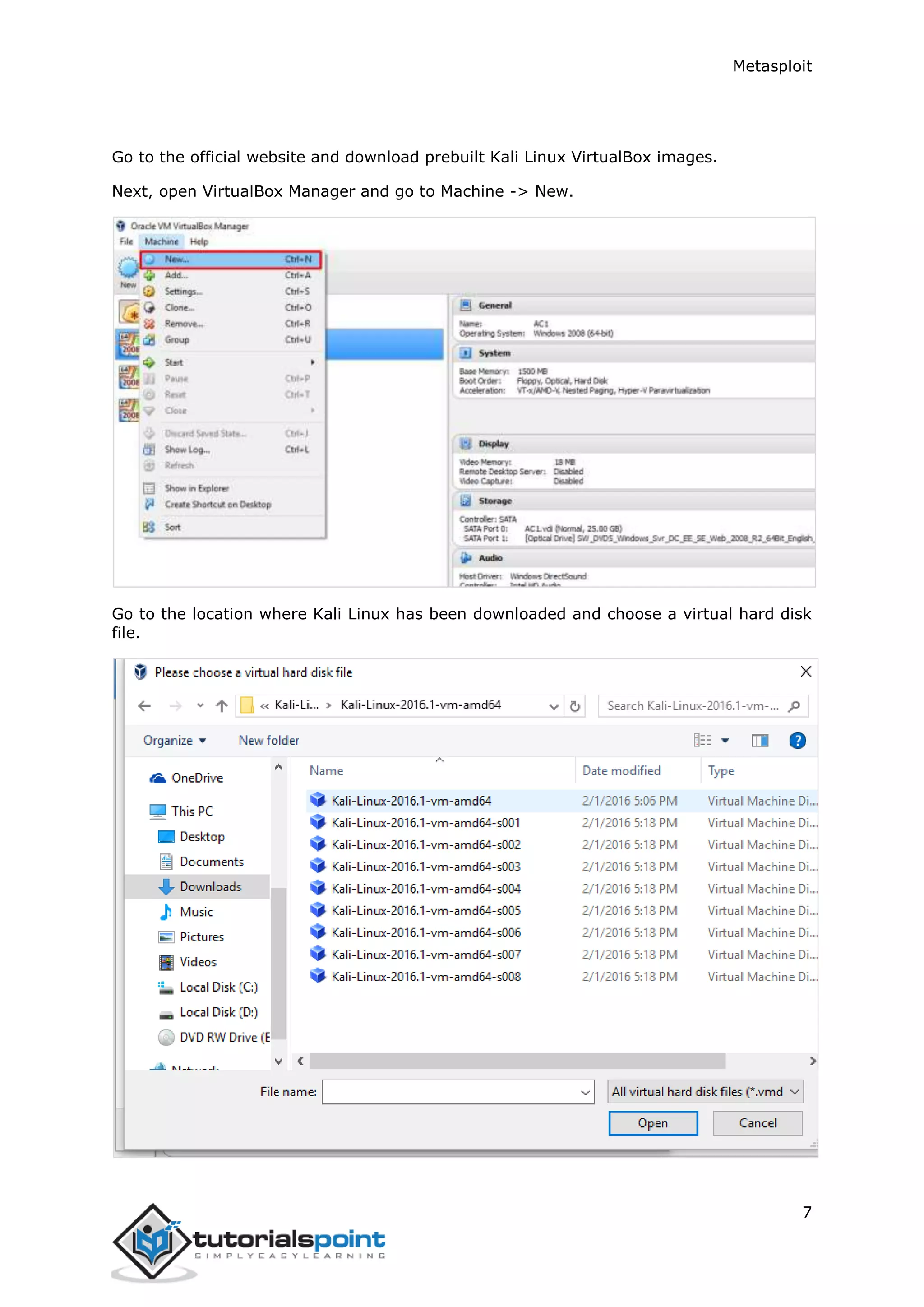
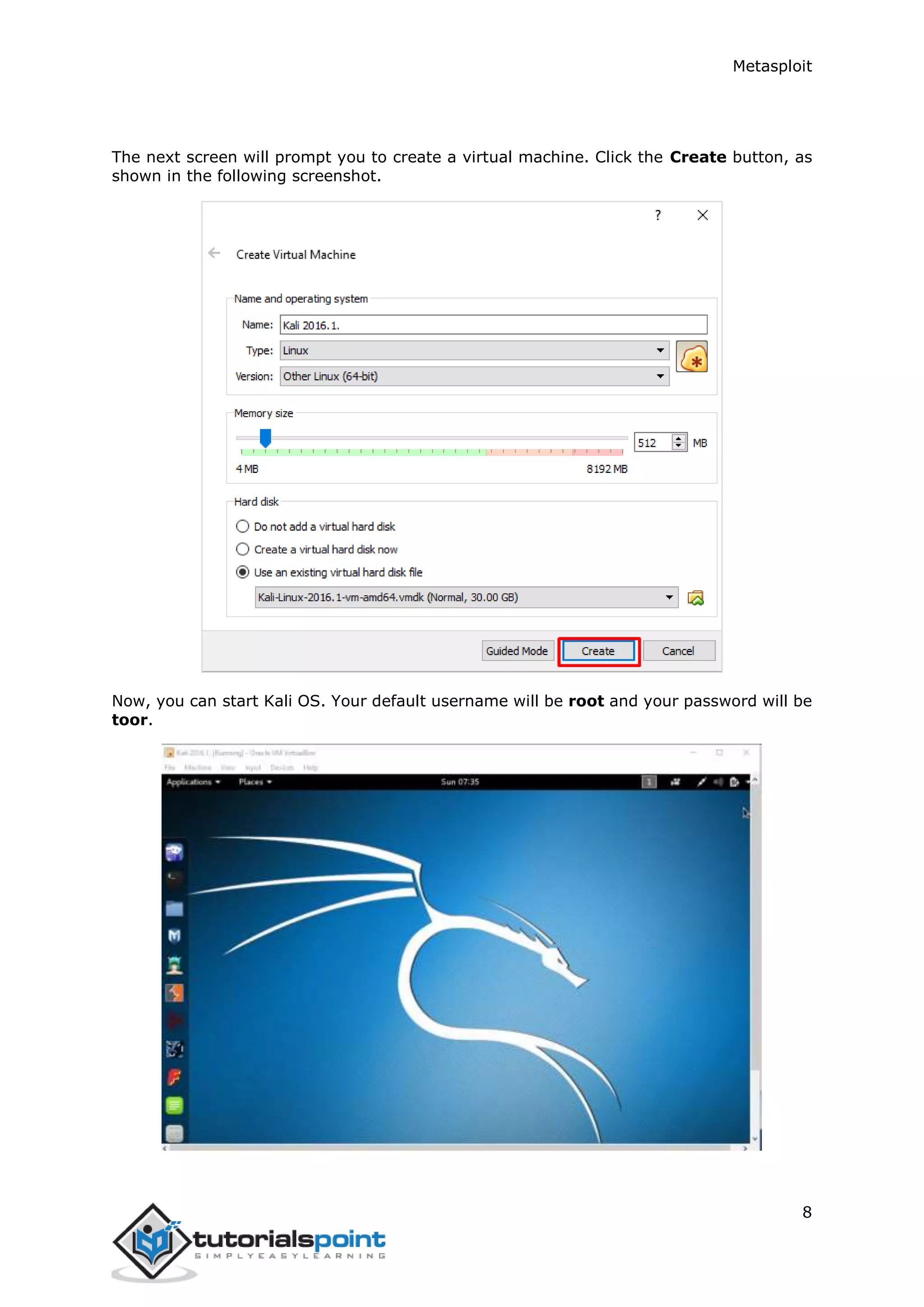
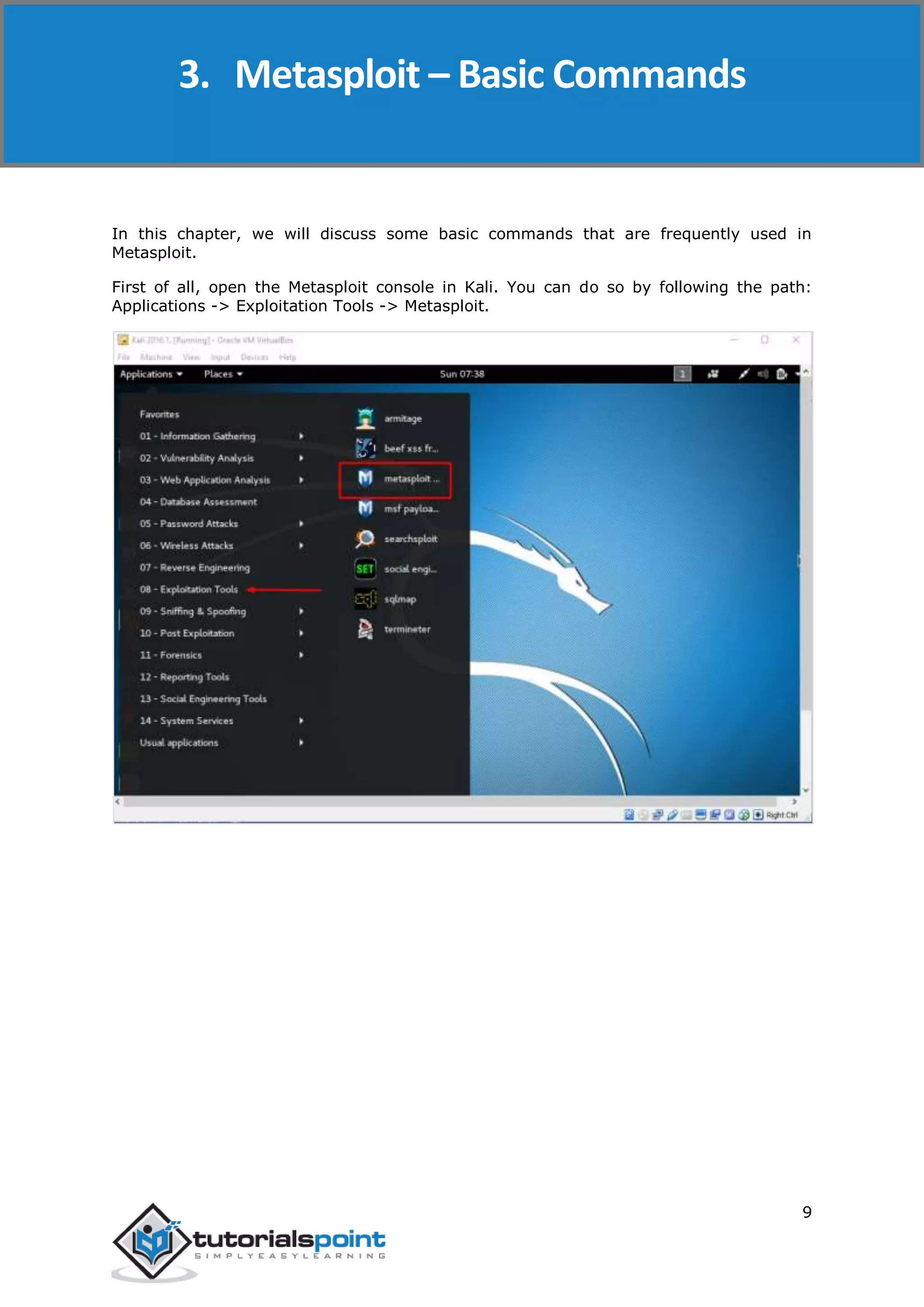
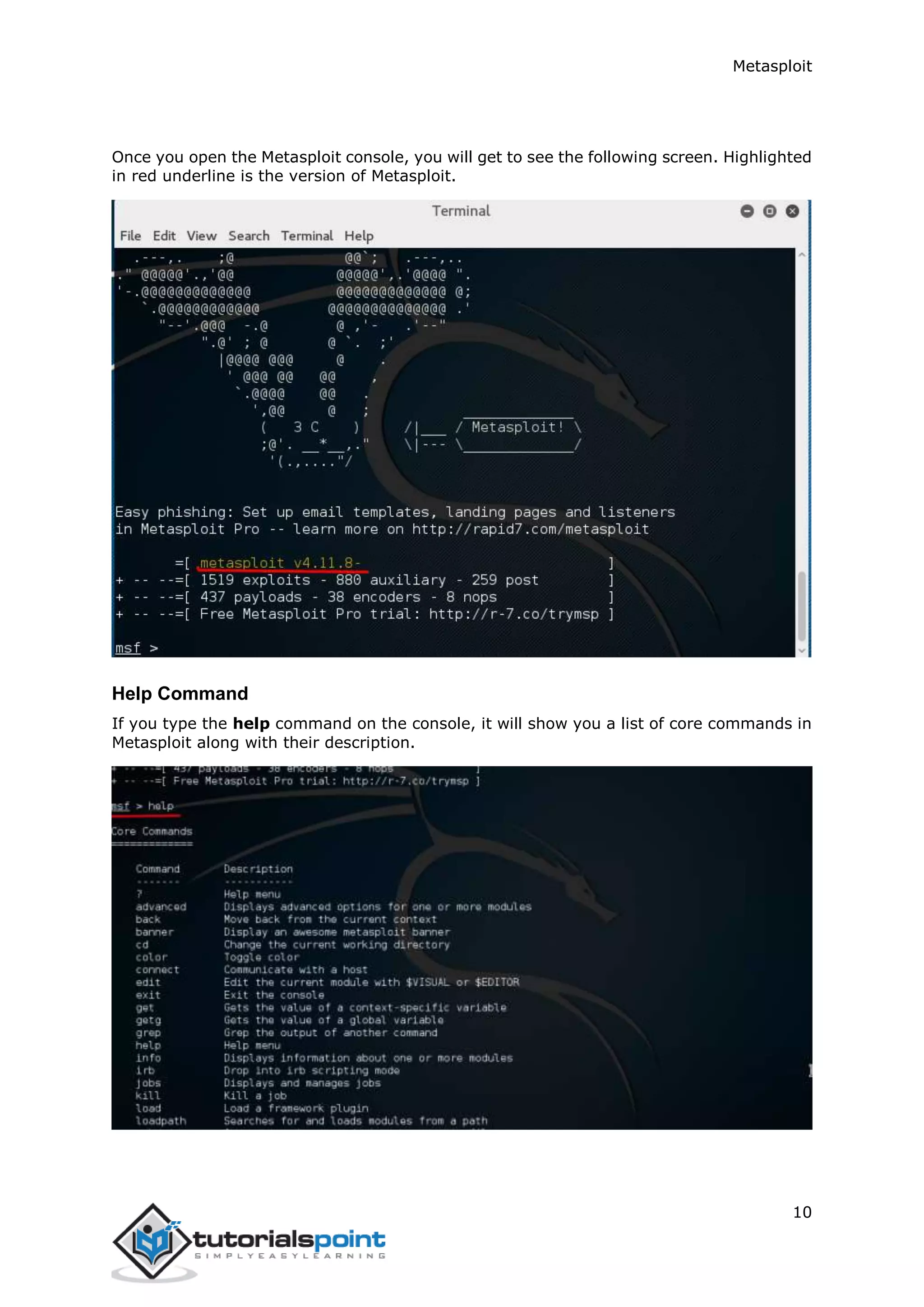
The document provides an overview and instructions for setting up Metasploit. It describes downloading and installing VirtualBox and Kali Linux in VirtualBox to create a test environment. Metasploit is a powerful penetration testing tool that can be used for both offensive and defensive security assessments. The document outlines downloading Metasploit images and installing them in VirtualBox to demonstrate its basic usage and commands.