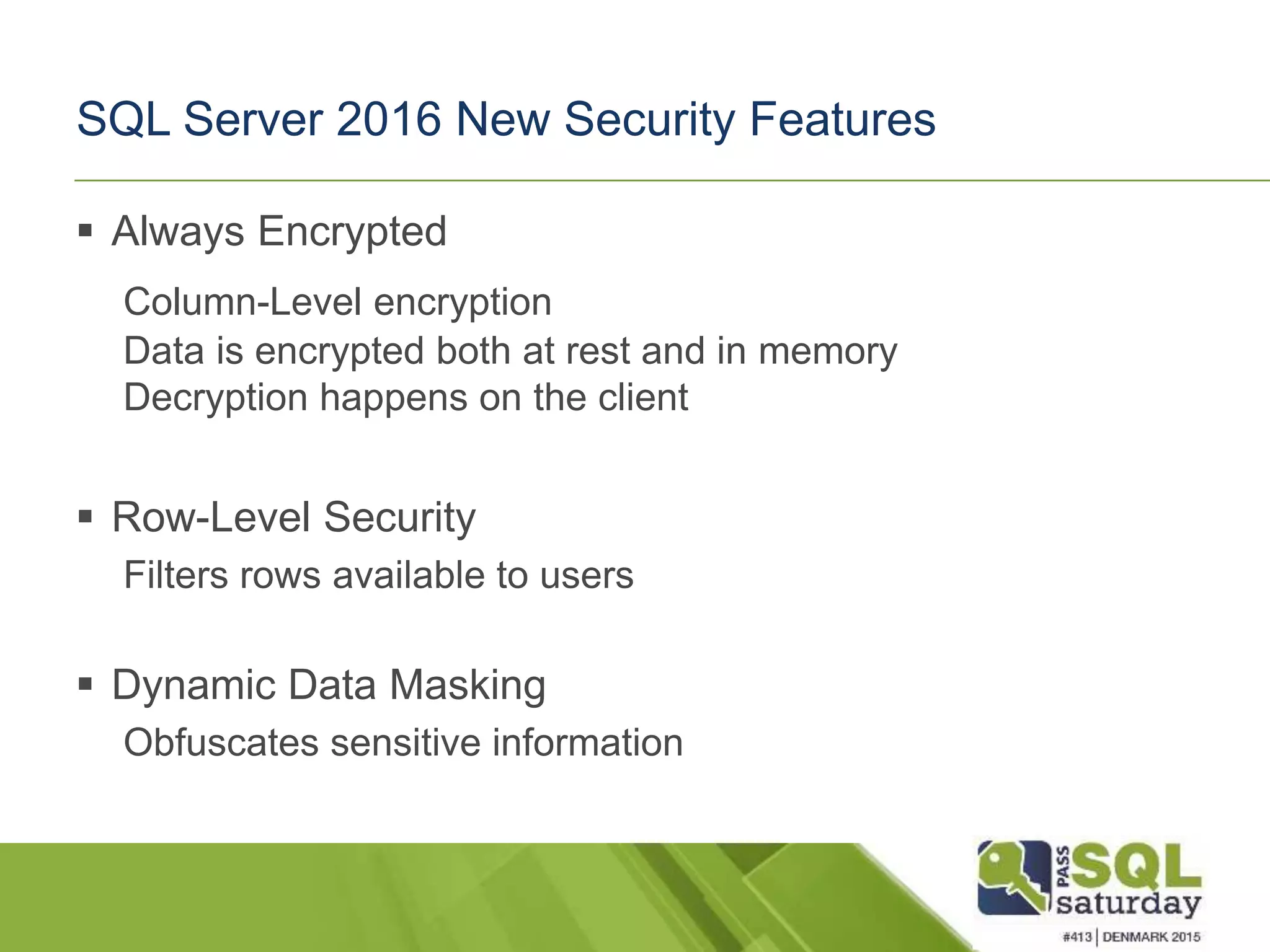
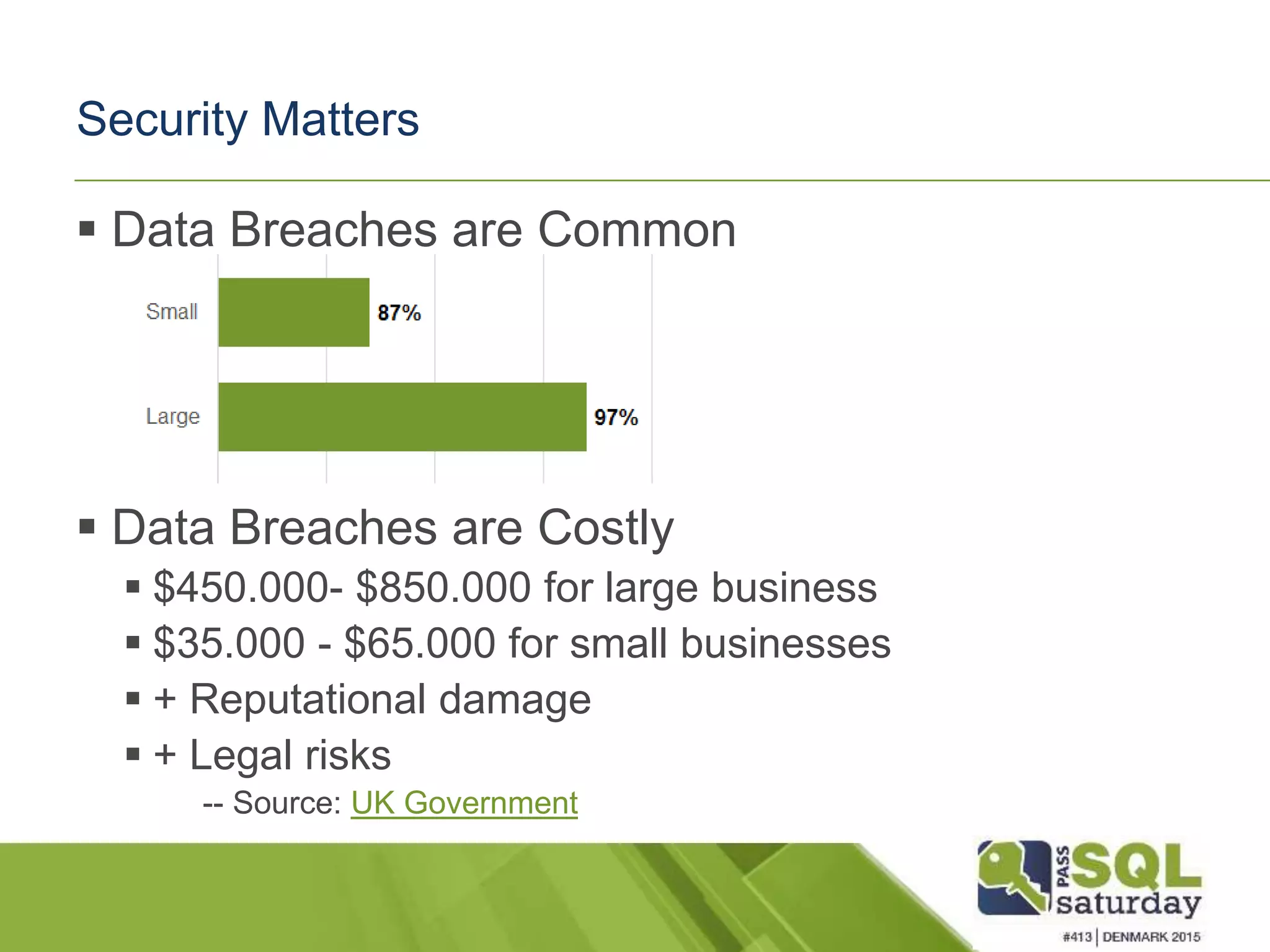
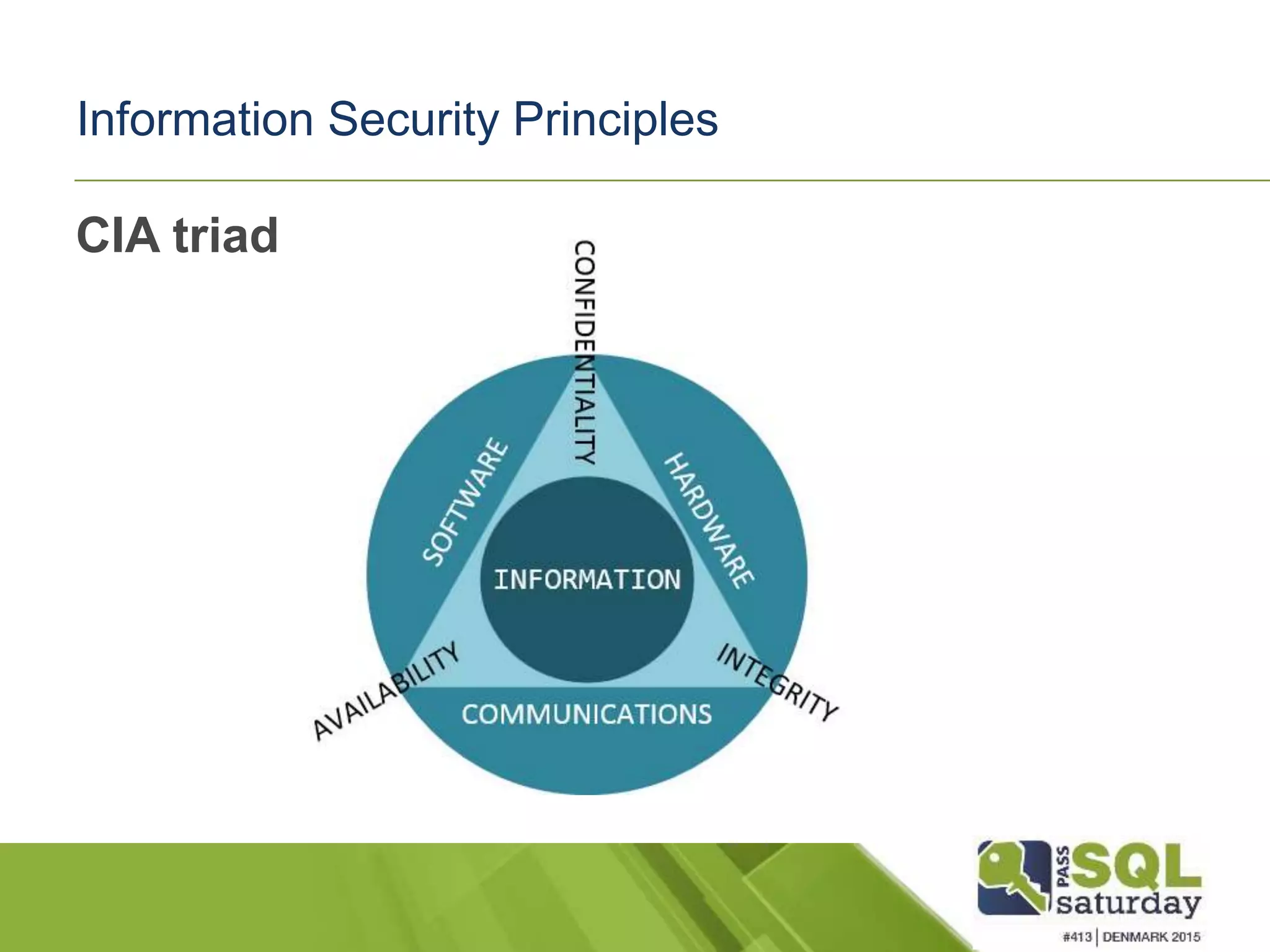
This document discusses SQL Server security best practices. It begins by noting that data breaches are common and costly for businesses. The presenter then covers security principles of confidentiality, integrity and availability. Various attack methods are described, demonstrating how quickly an unsecured system can be compromised. The presentation recommends implementing security policies across physical, network, host, application and database layers. Specific issues like SQL injection and authentication/authorization approaches are discussed. New SQL Server 2016 security features such as Always Encrypted and row-level security are also mentioned. Resources for further information are provided.







![DEMO How fast can a [poorly configured] system be compromised? … damn fast!](https://image.slidesharecdn.com/sqlserversecurityinsecureworld413-160302220811/75/Sql-server-security-in-an-insecure-world-11-2048.jpg)