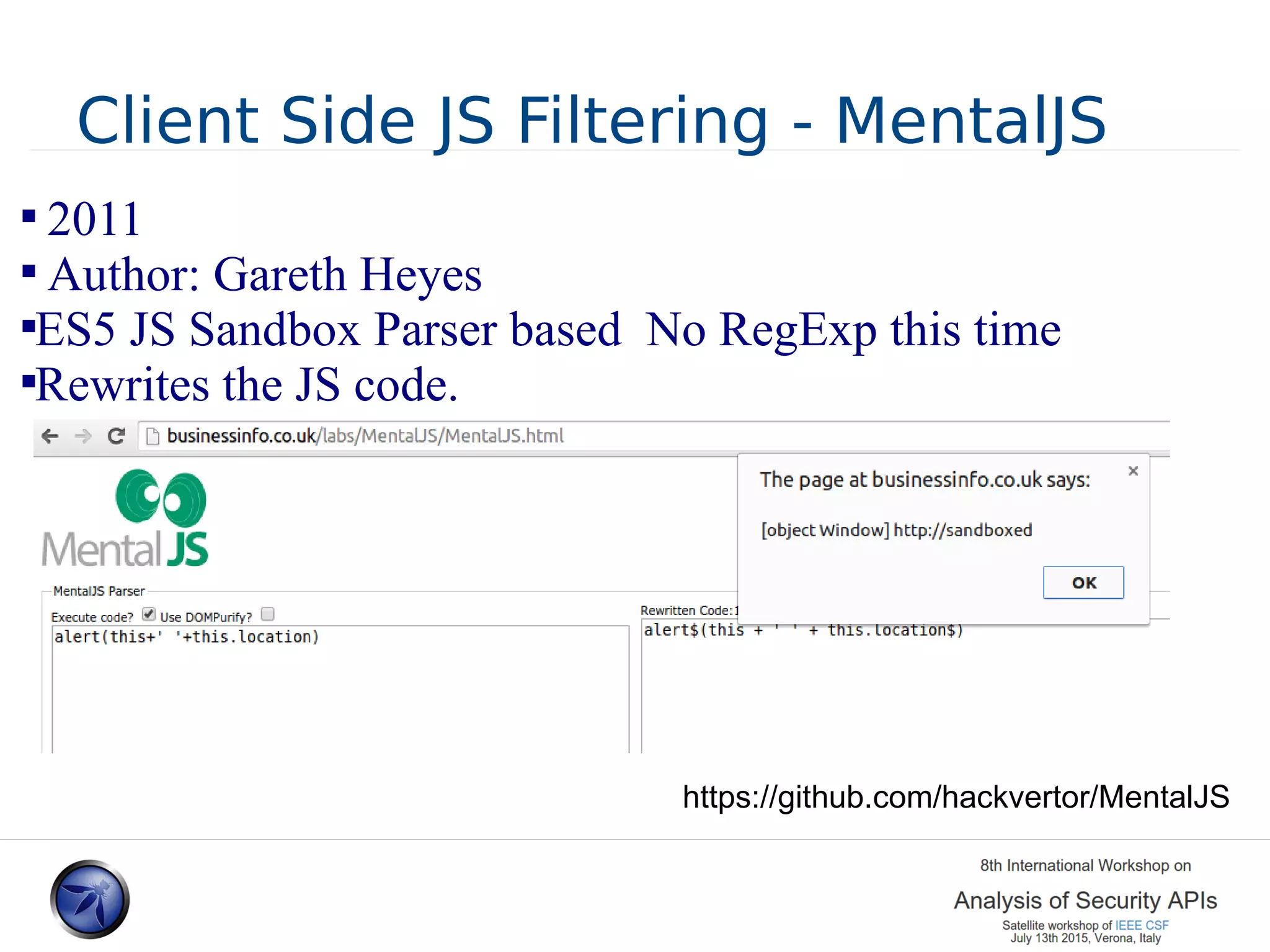
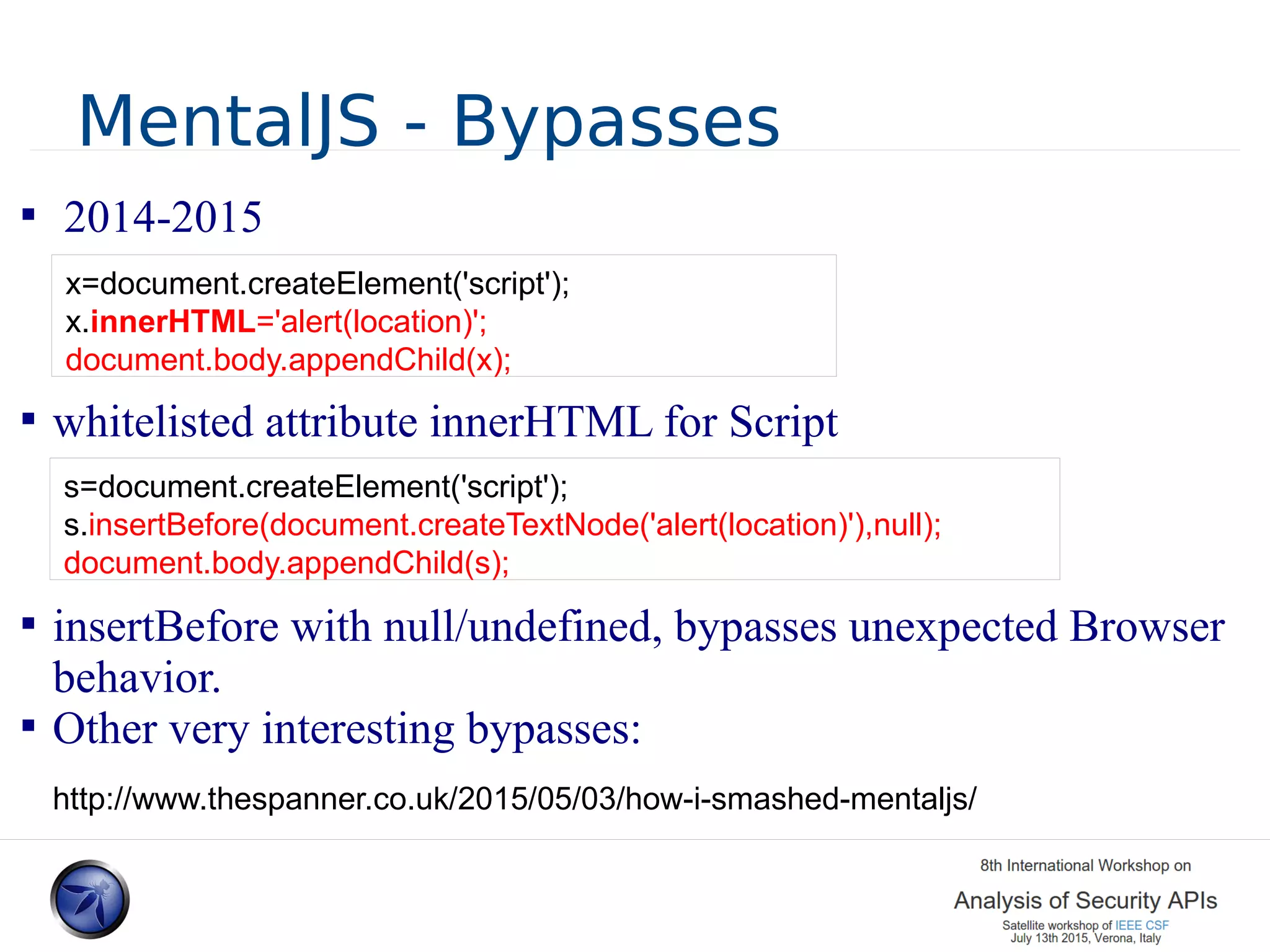
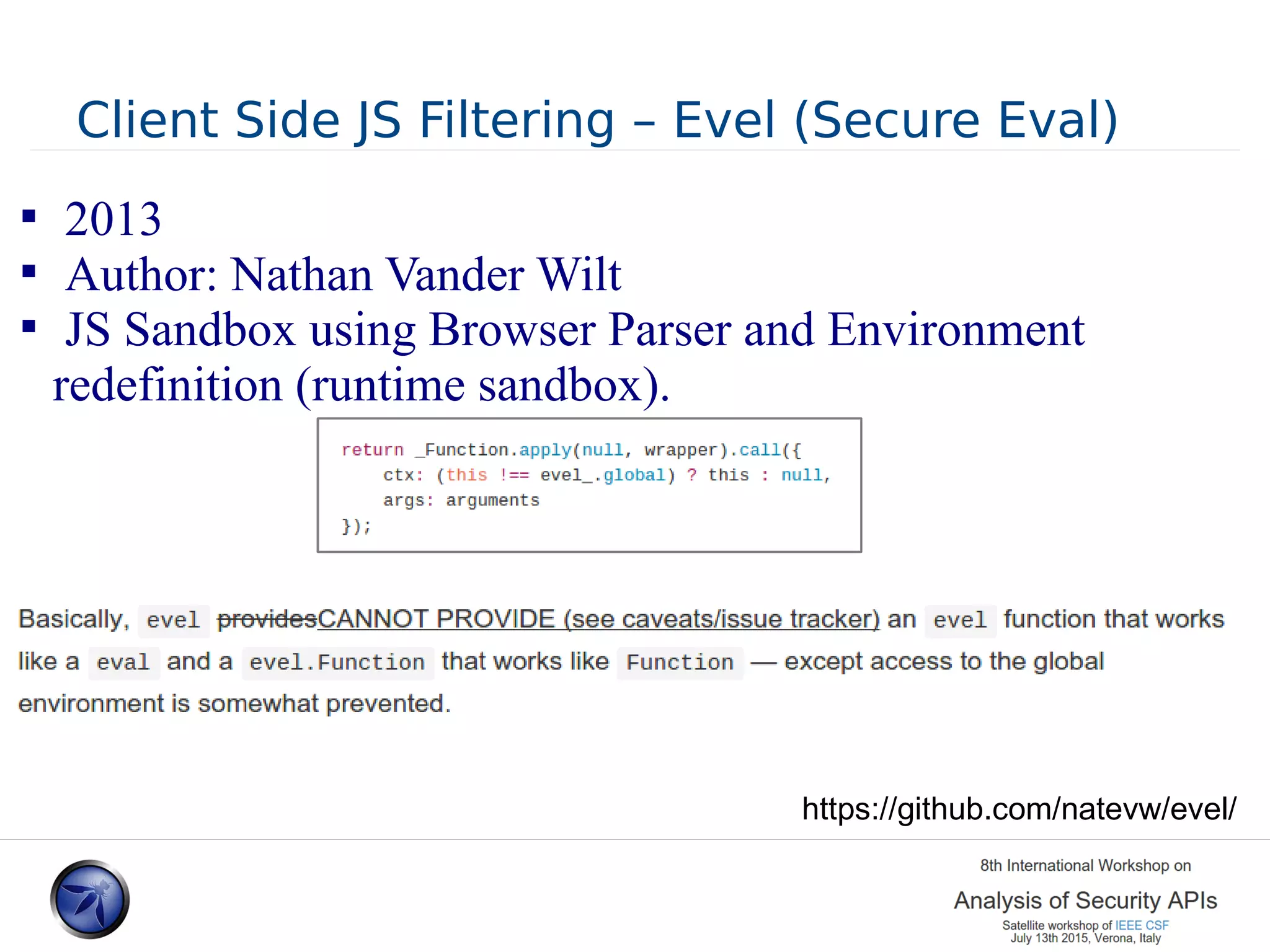
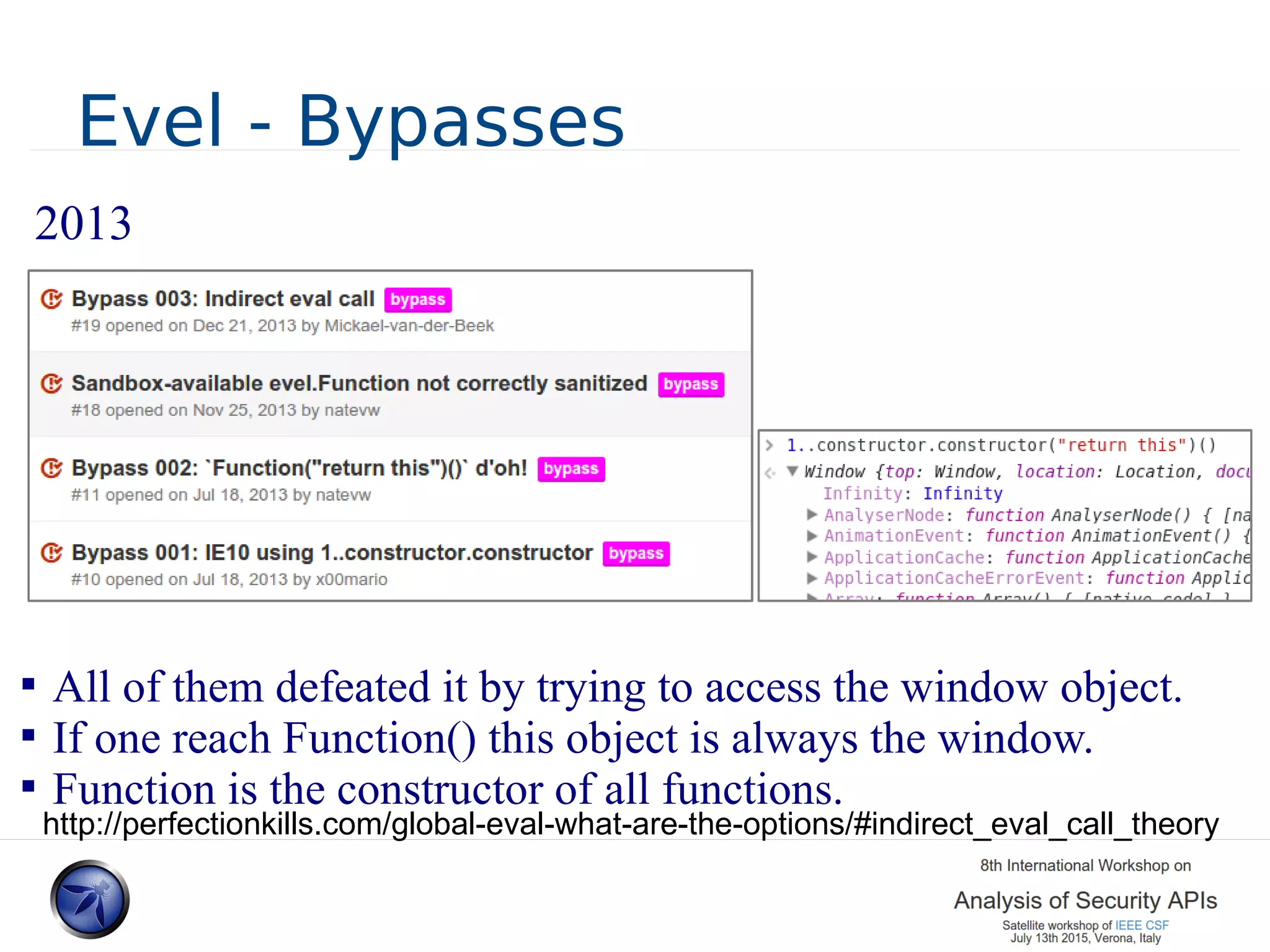
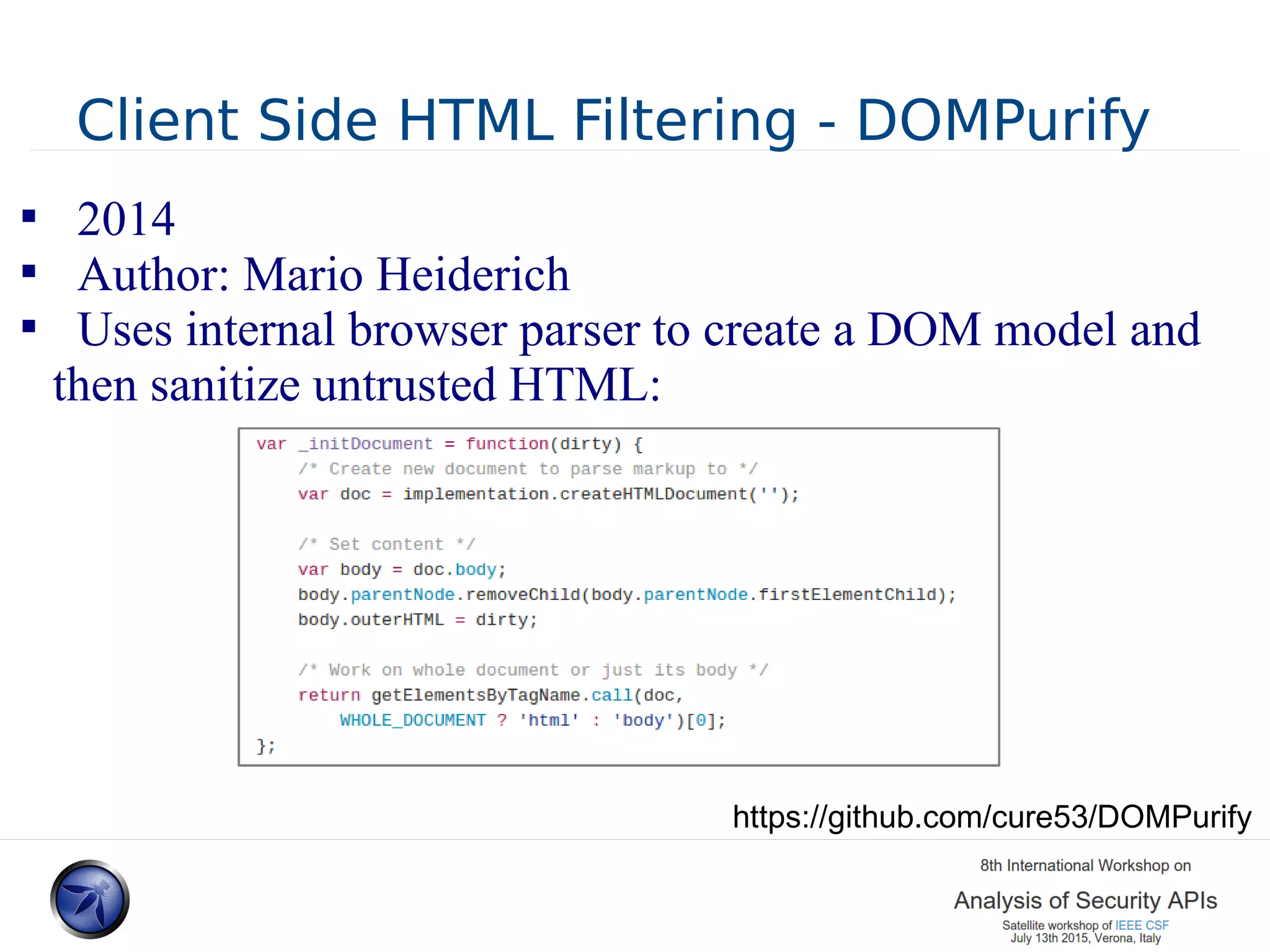
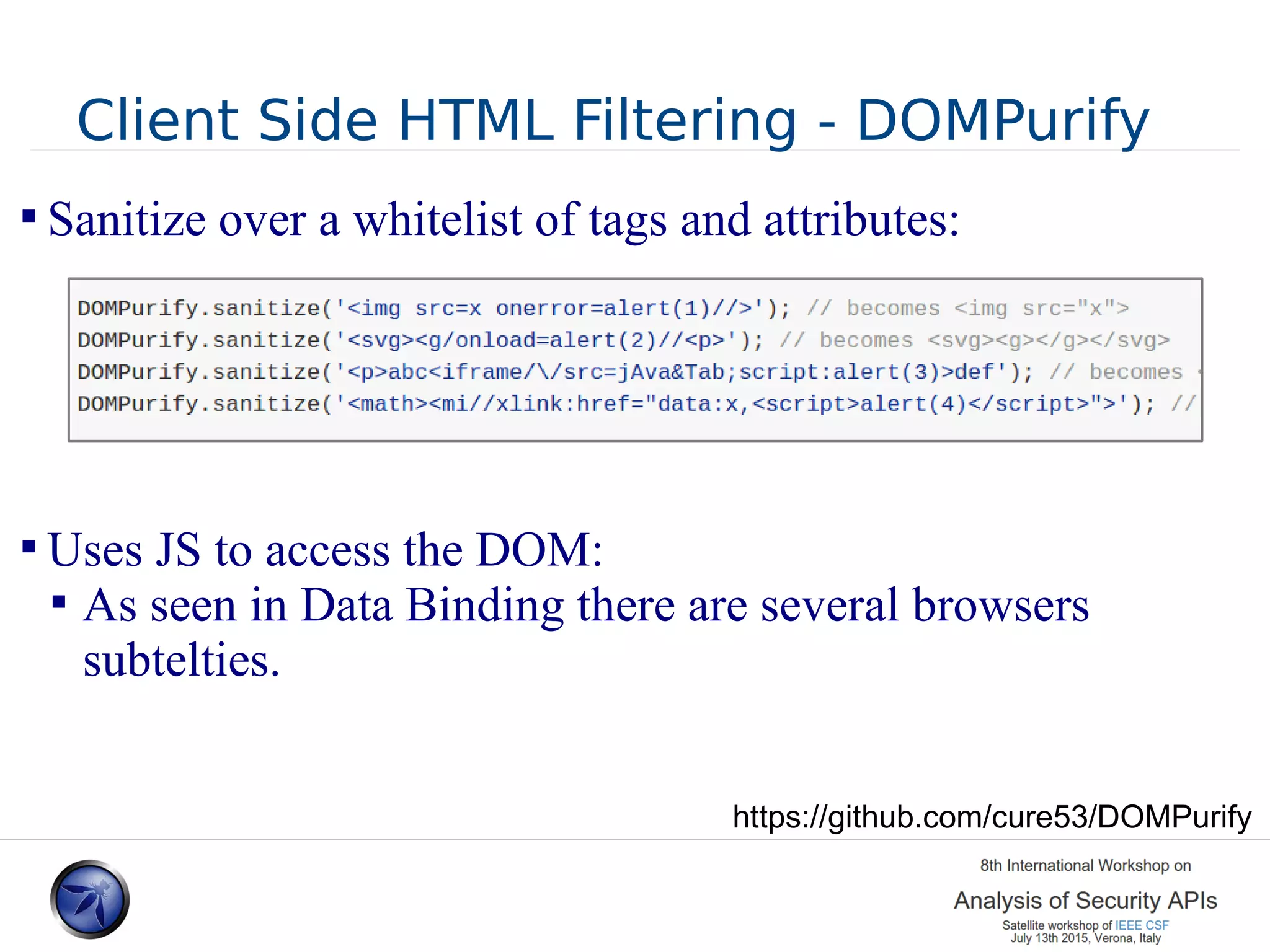
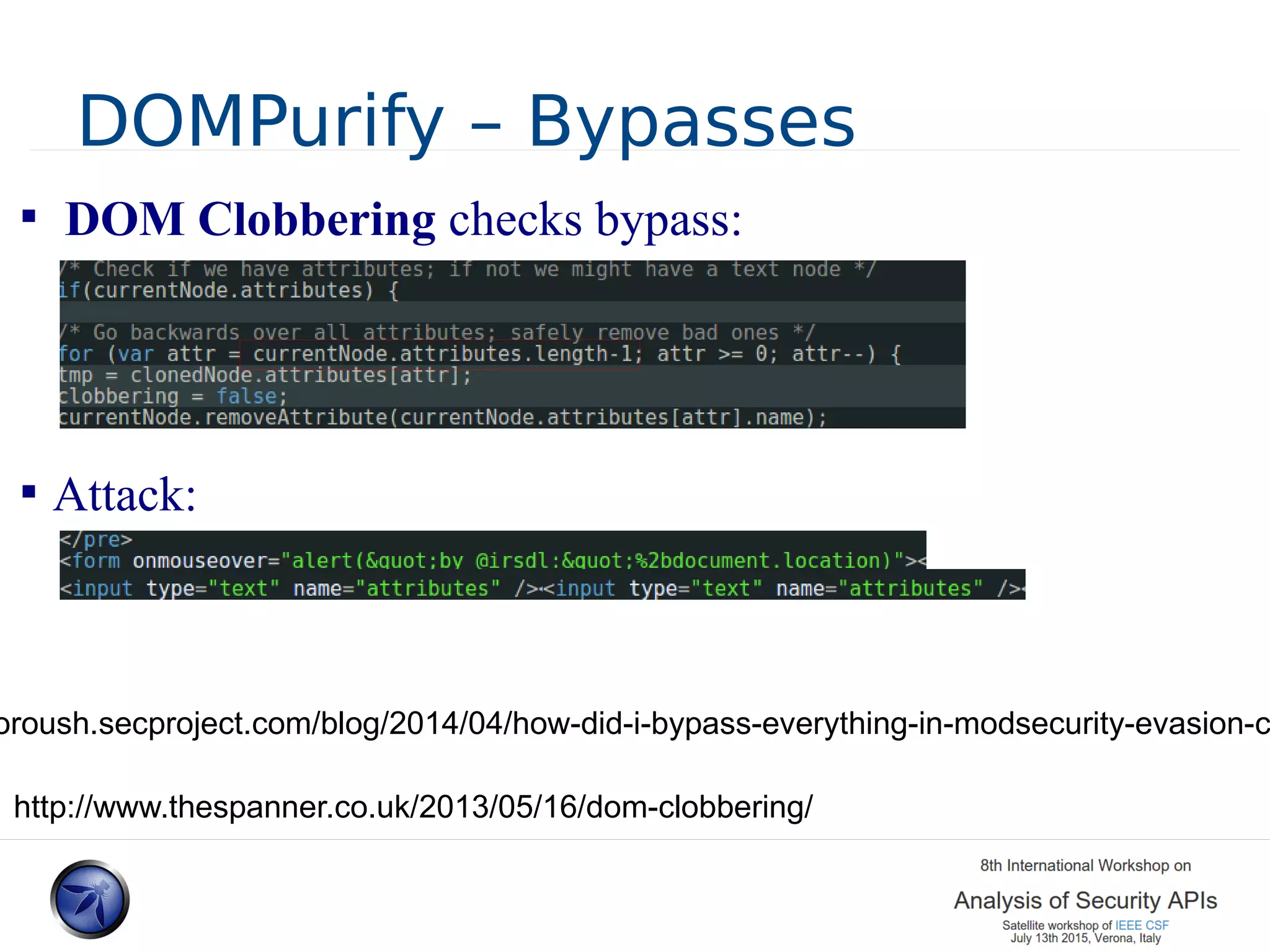
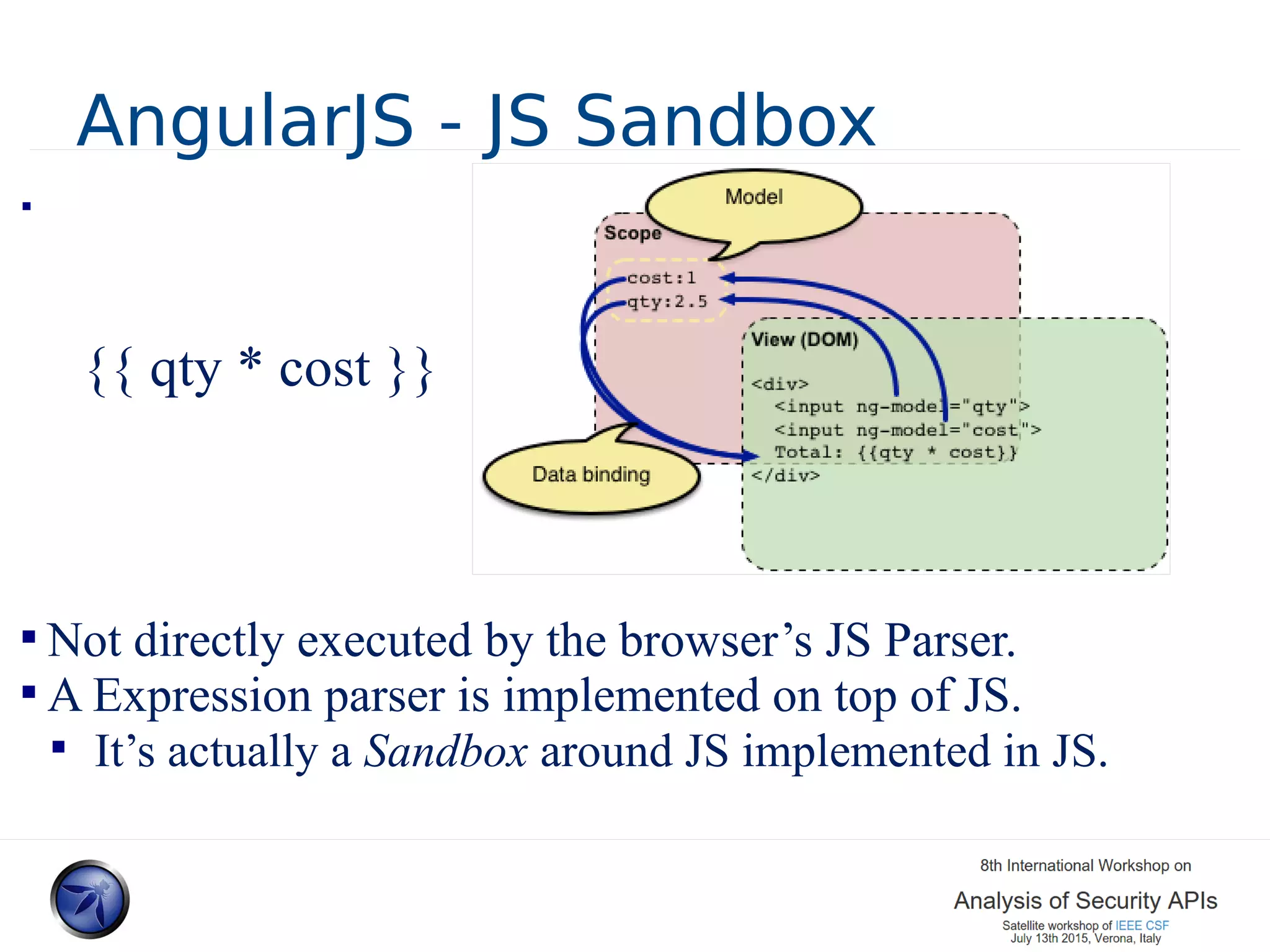
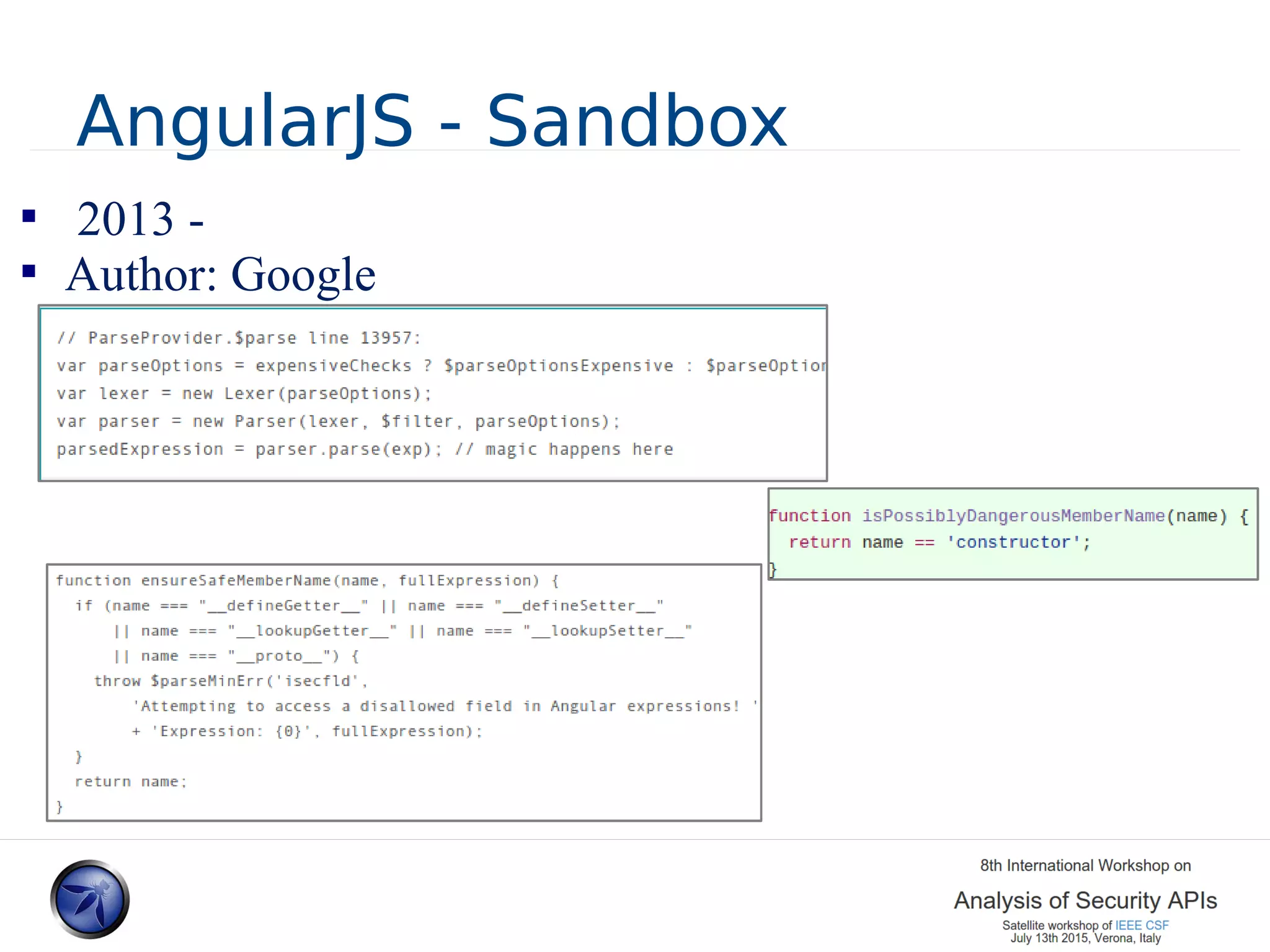
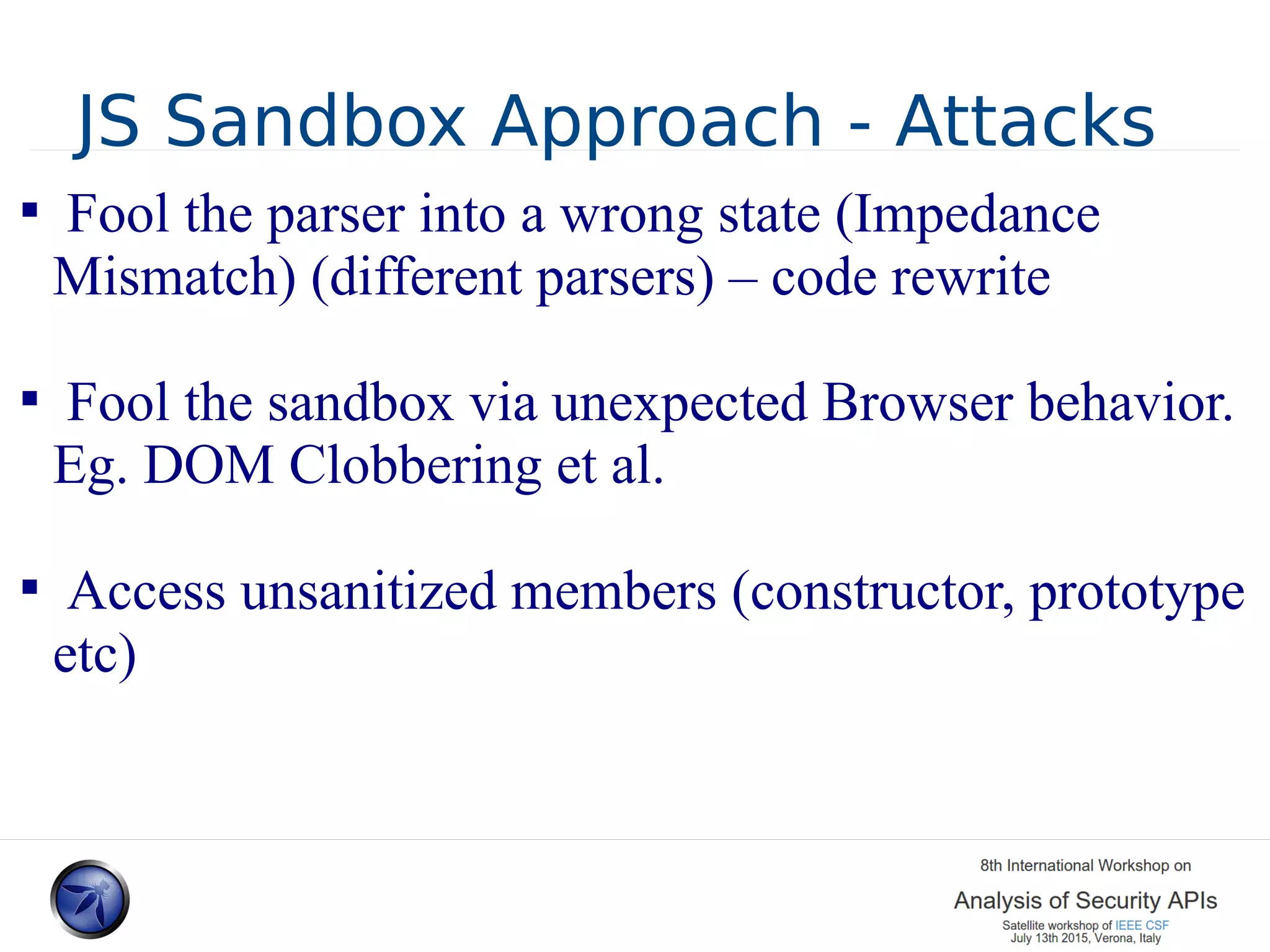
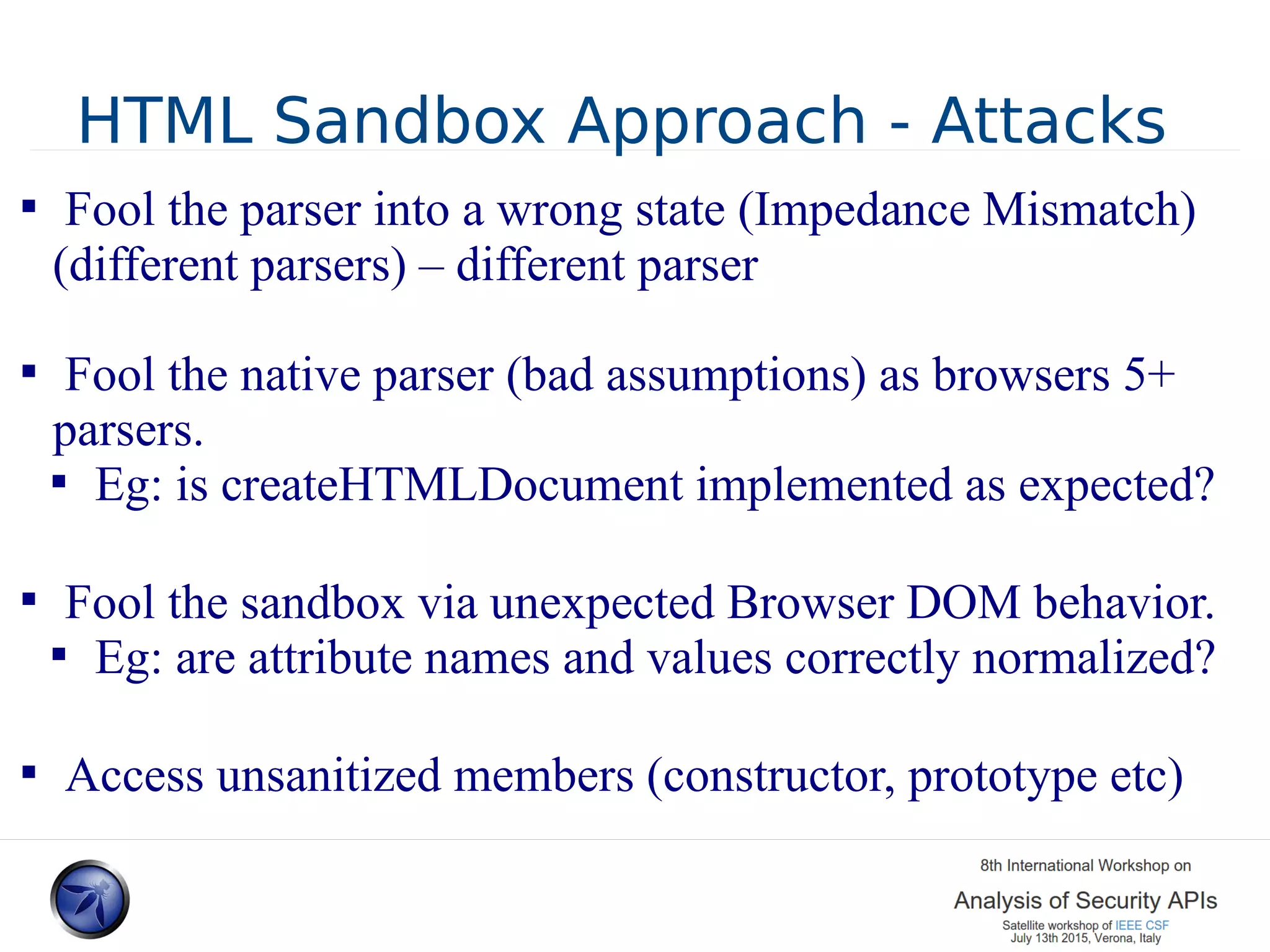
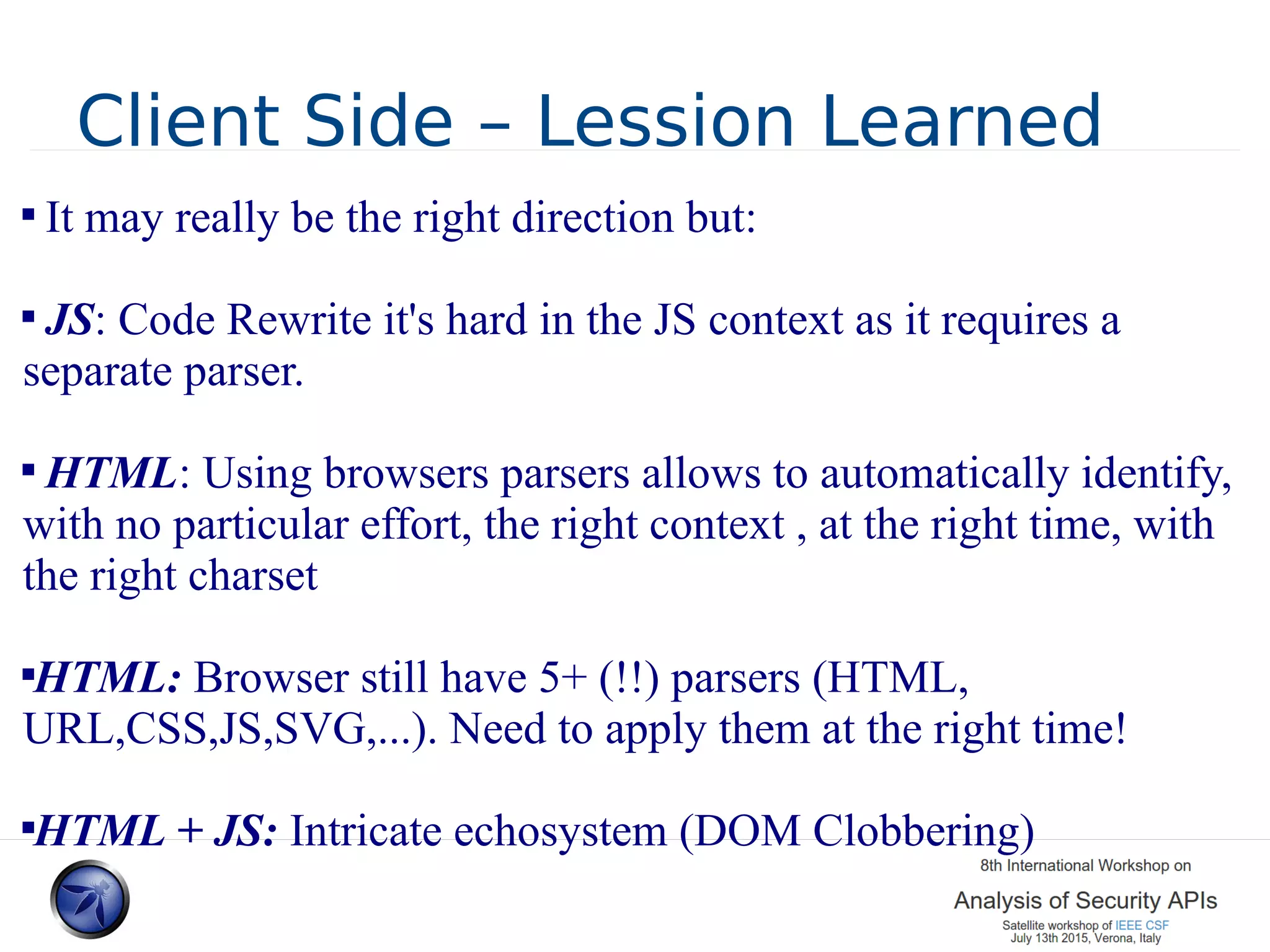
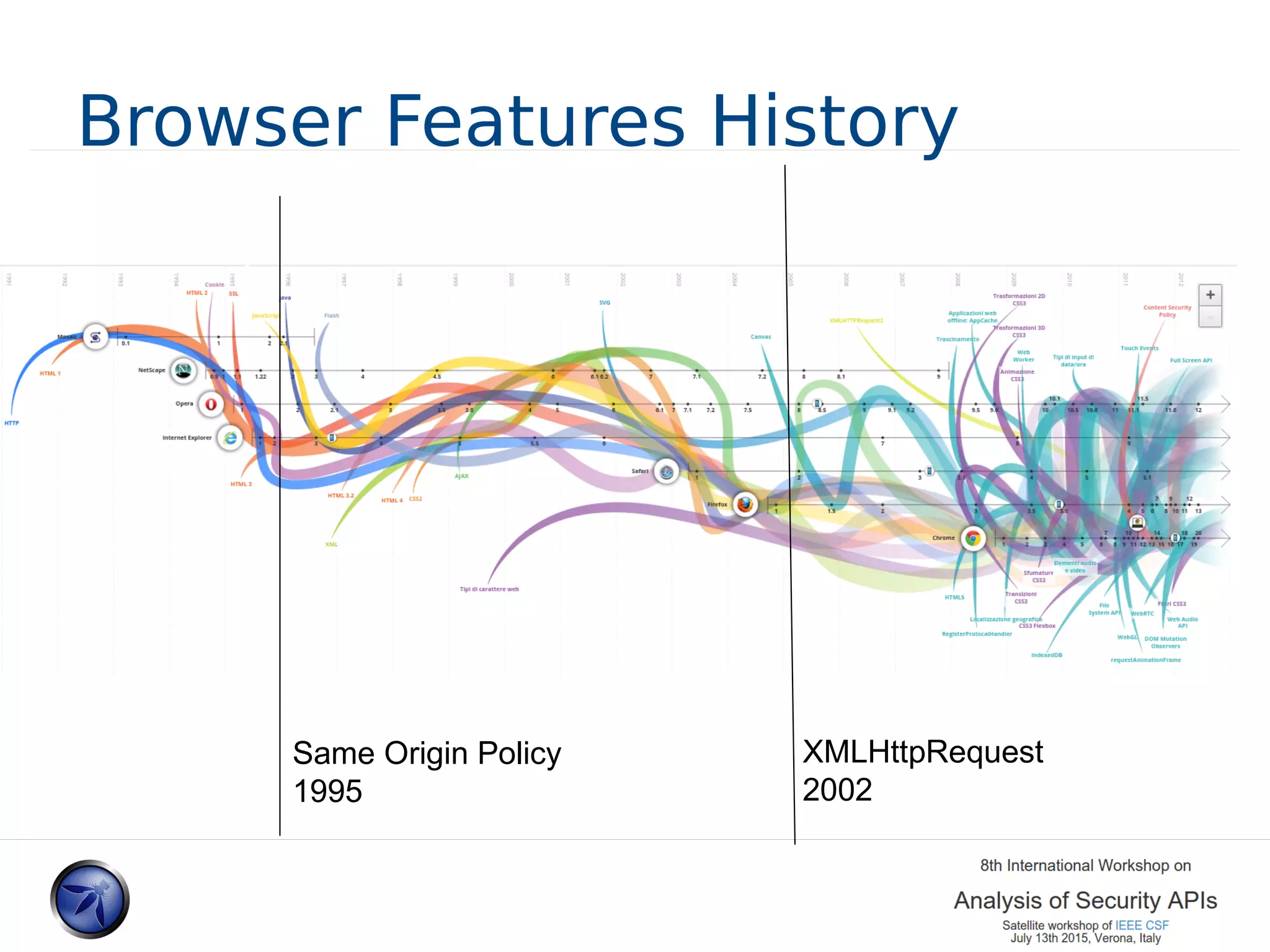
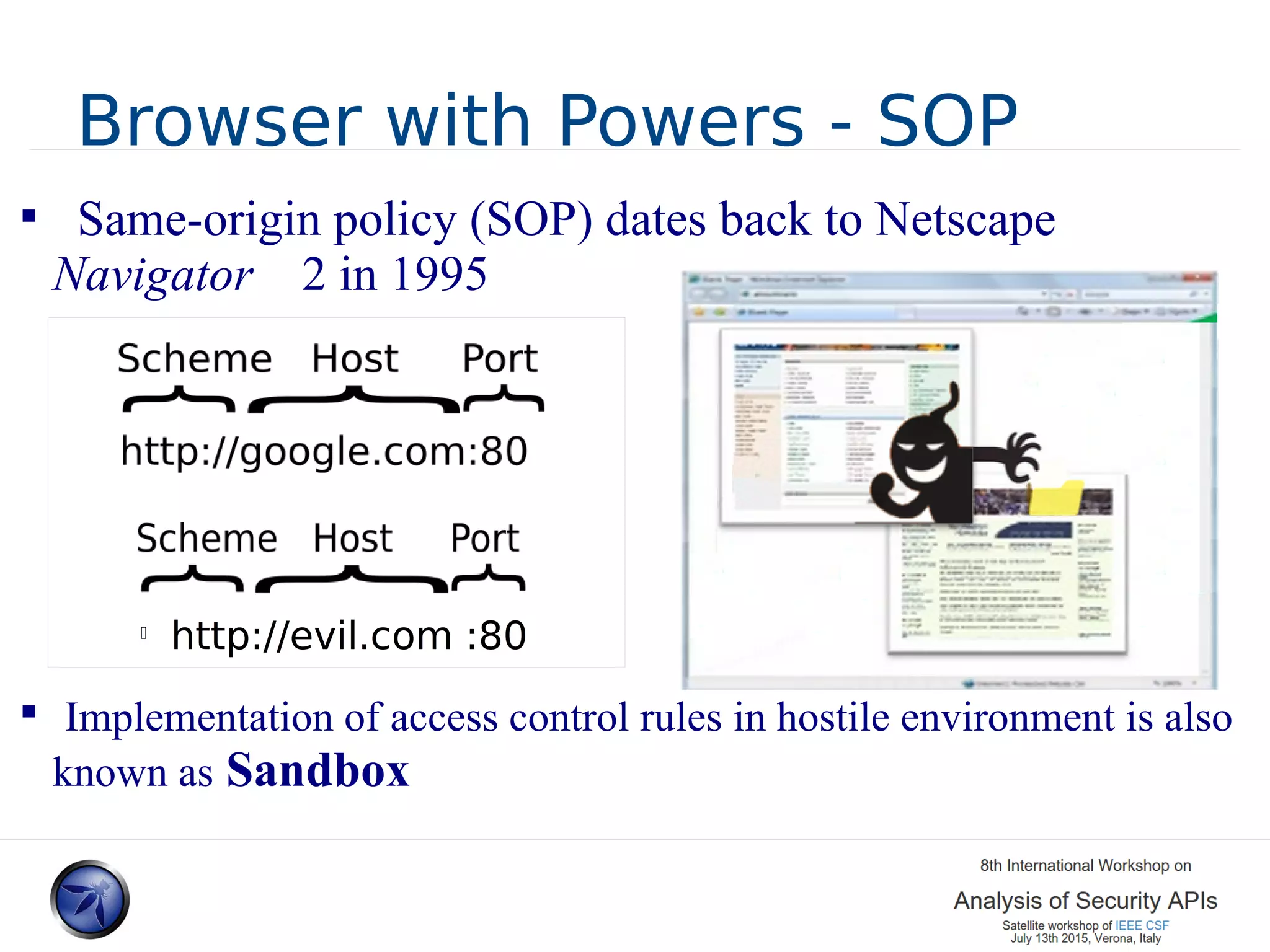
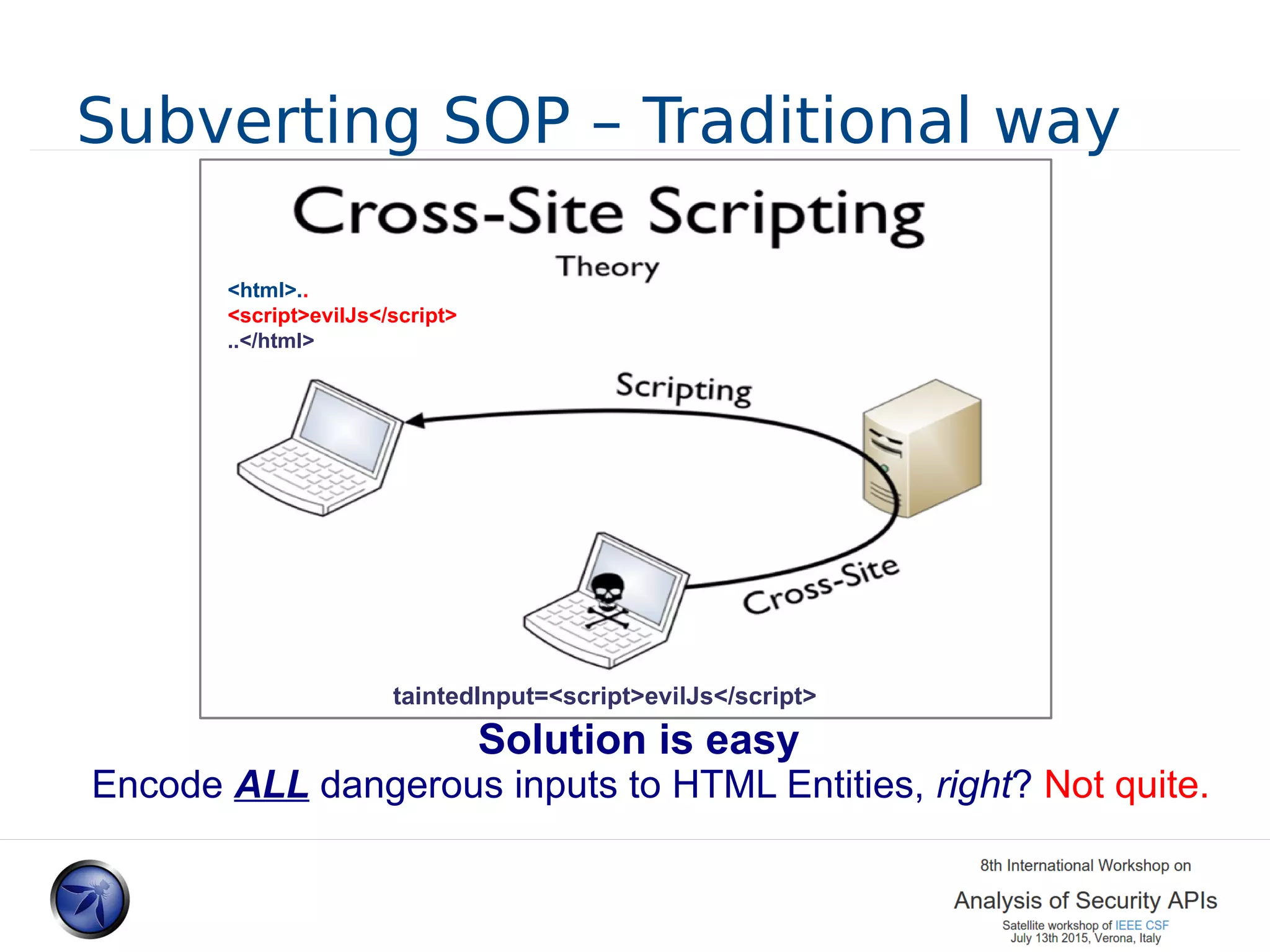
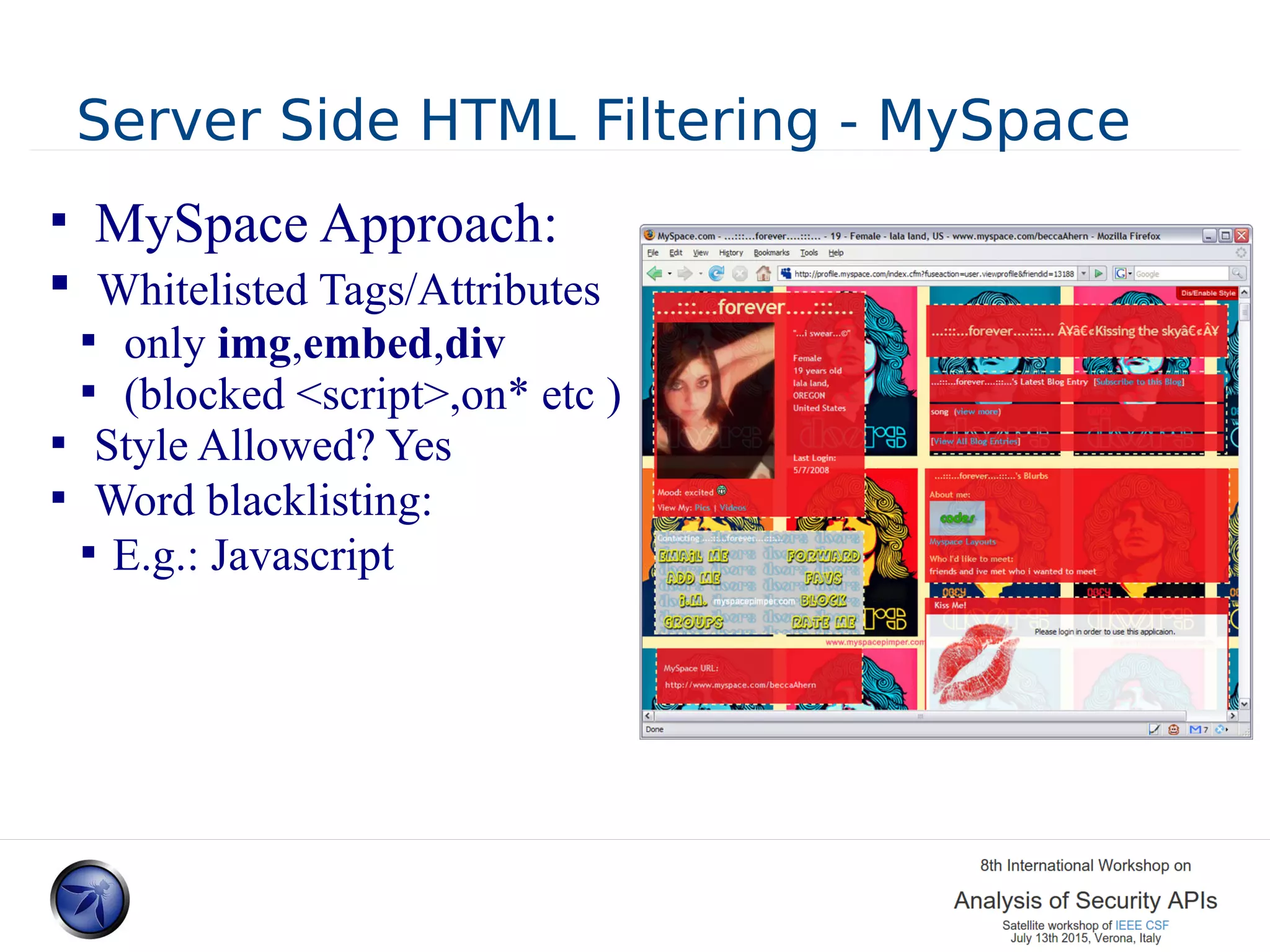
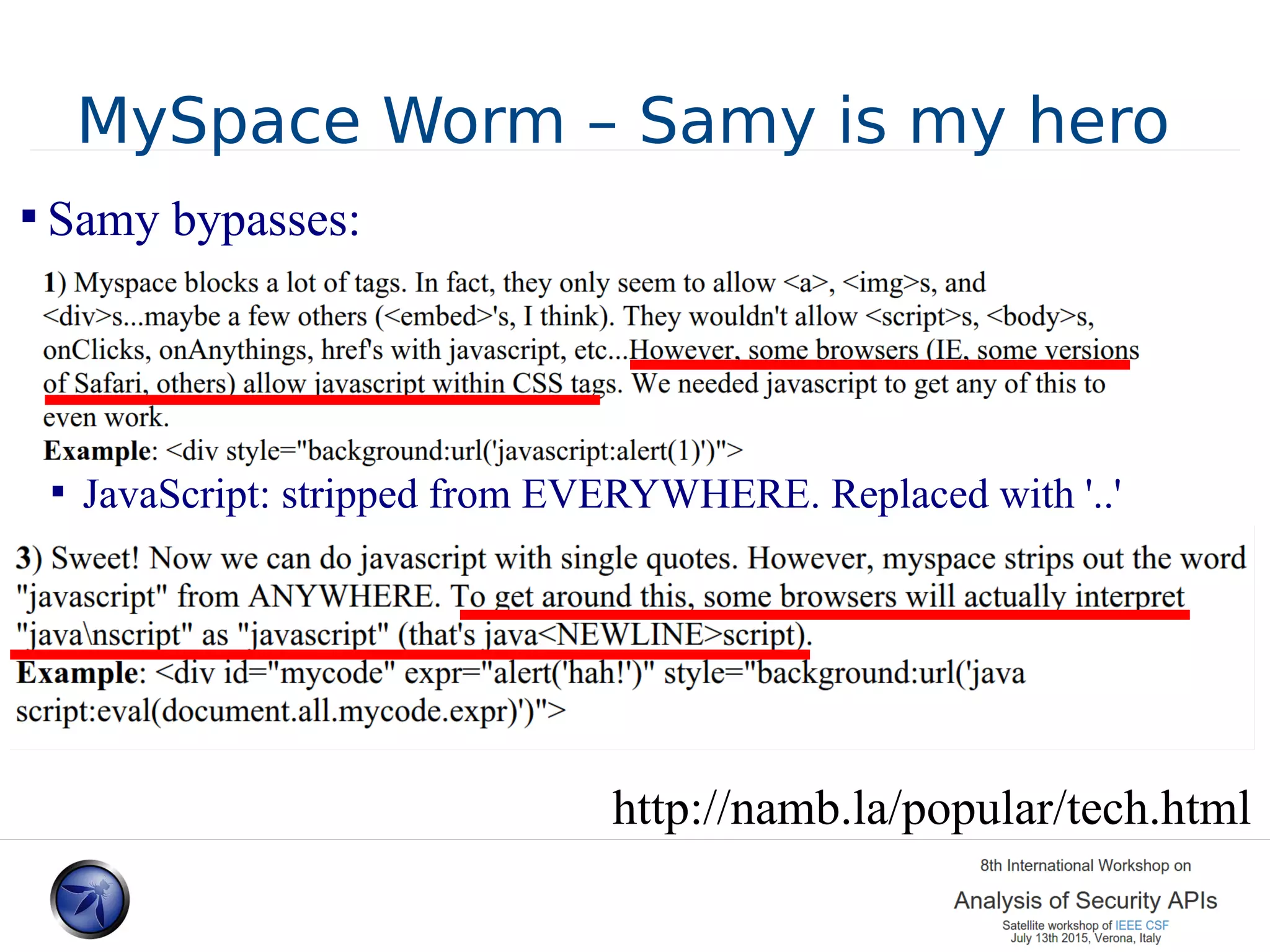
The document discusses various approaches and challenges in sandboxing HTML pages with API wrappers to counter malicious third-party code attacks. It analyzes the history of browser features like the same-origin policy and highlights numerous attempts at server-side and client-side filtering strategies, their drawbacks, and lessons learned. While some solutions improved security, the document concludes that a fully unbreakable solution has yet to be established due to complex interactions across different browser environments.




![Server Side HTML Filtering - OWASP Anti Samy Attempts to solve the MySpace approach on the server side. Author: Arshan Dabirsiaghi Translates HTML to Well Formed XML Whitelist of Tags and Attributes Everything else is encoded One bypass so far (usual problem) – Fixed: <![CDATA[ .. ]]> ← AntiSamy Expects this, but ... <![CDATA[ .. ]> ← works on every browser. https://www.owasp.org/index.php/Category:OWASP_AntiSamy_Project](https://image.slidesharecdn.com/presodipaolafinal1-150714075353-lva1-app6891/75/Sandboxing-JS-and-HTML-A-lession-Learned-11-2048.jpg)
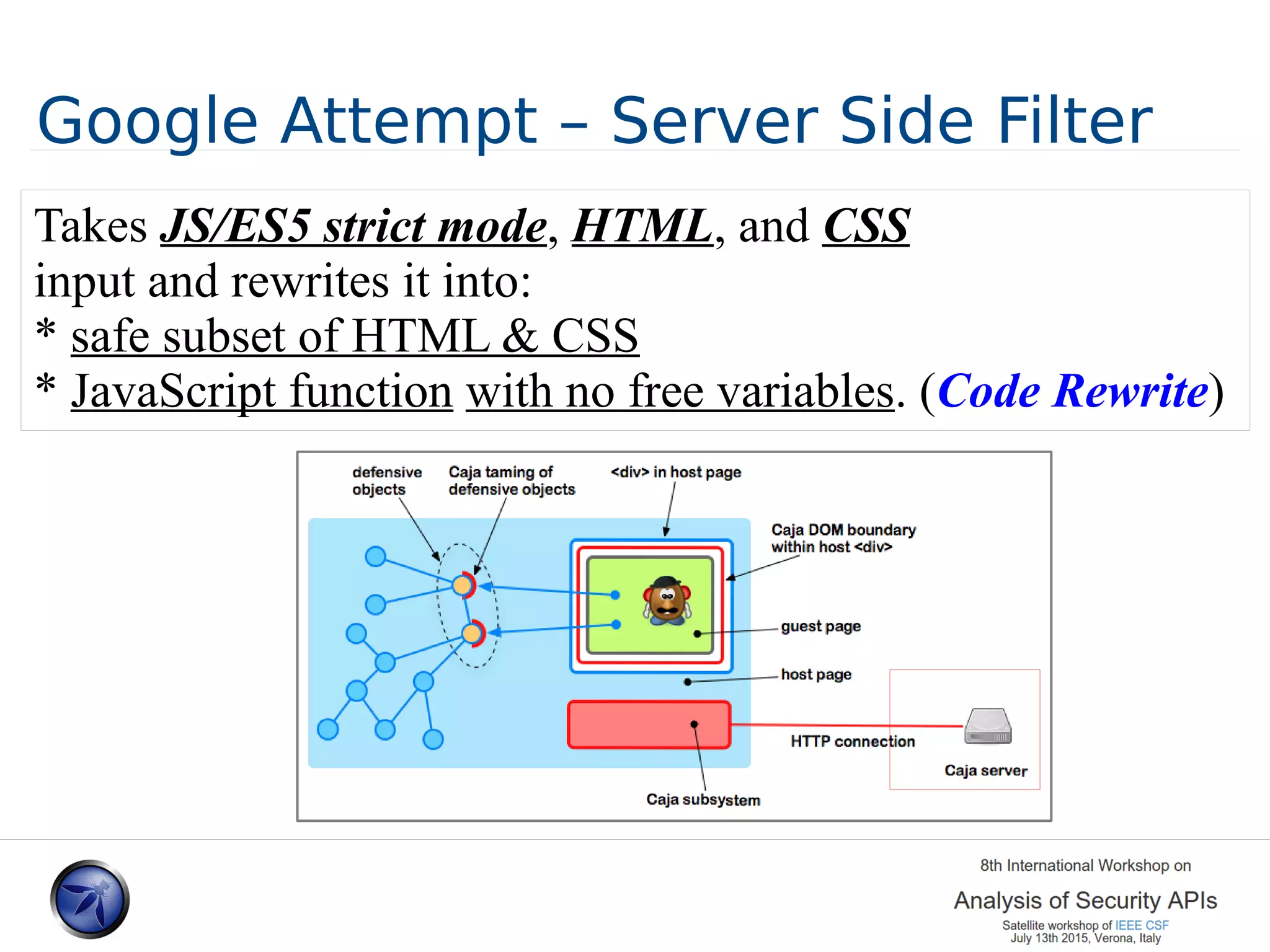
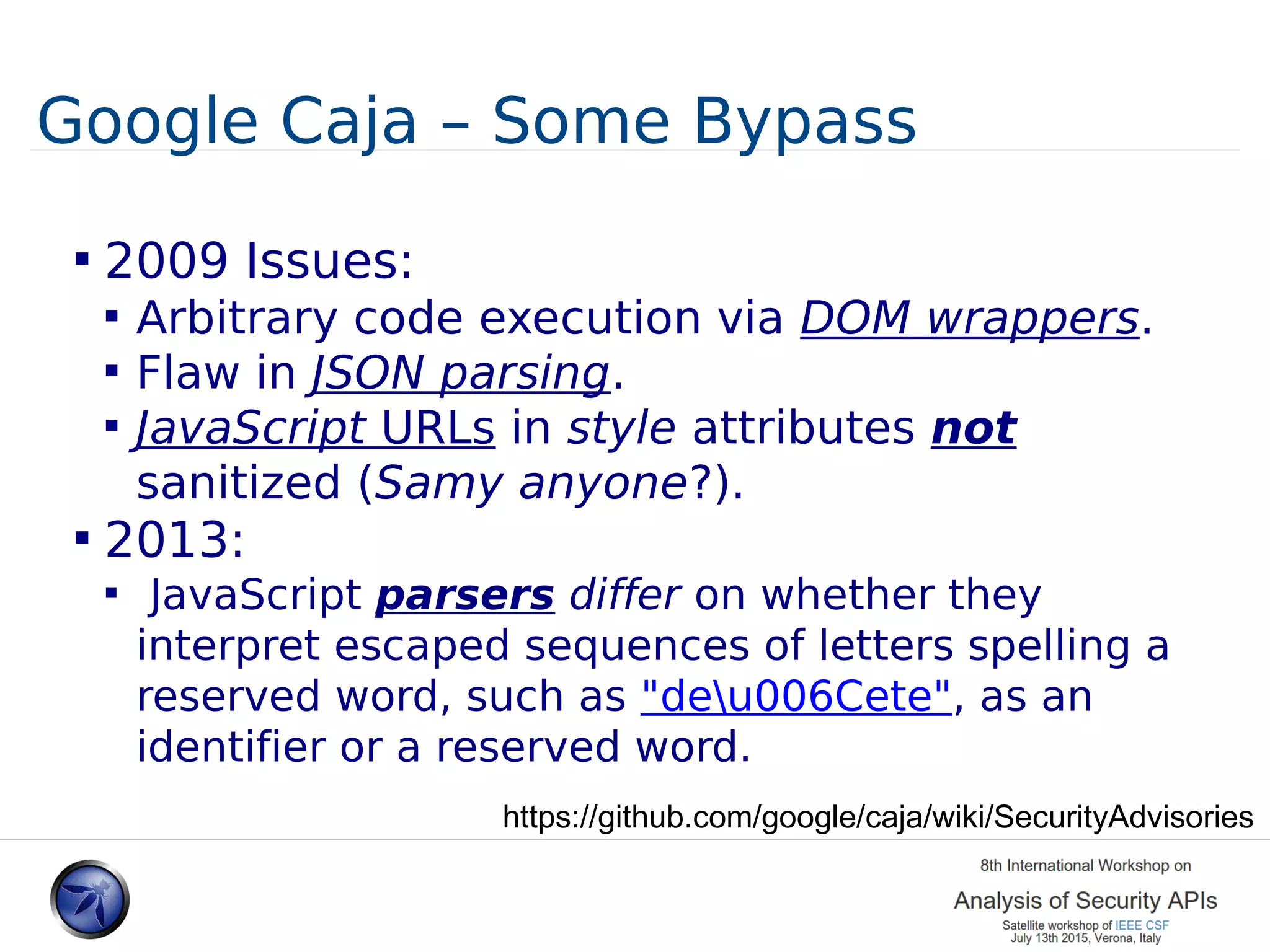
![Server Side JS/HTML Filter - Caja ~2008 Author: Google The 3rd party code problem Aka Sandboxed Advertising [...The Caja Compiler is a tool for making third party HTML, CSS and JavaScript safe to embed in your website. ..] https://developers.google.com/caja/docs/about/](https://image.slidesharecdn.com/presodipaolafinal1-150714075353-lva1-app6891/75/Sandboxing-JS-and-HTML-A-lession-Learned-12-2048.jpg)
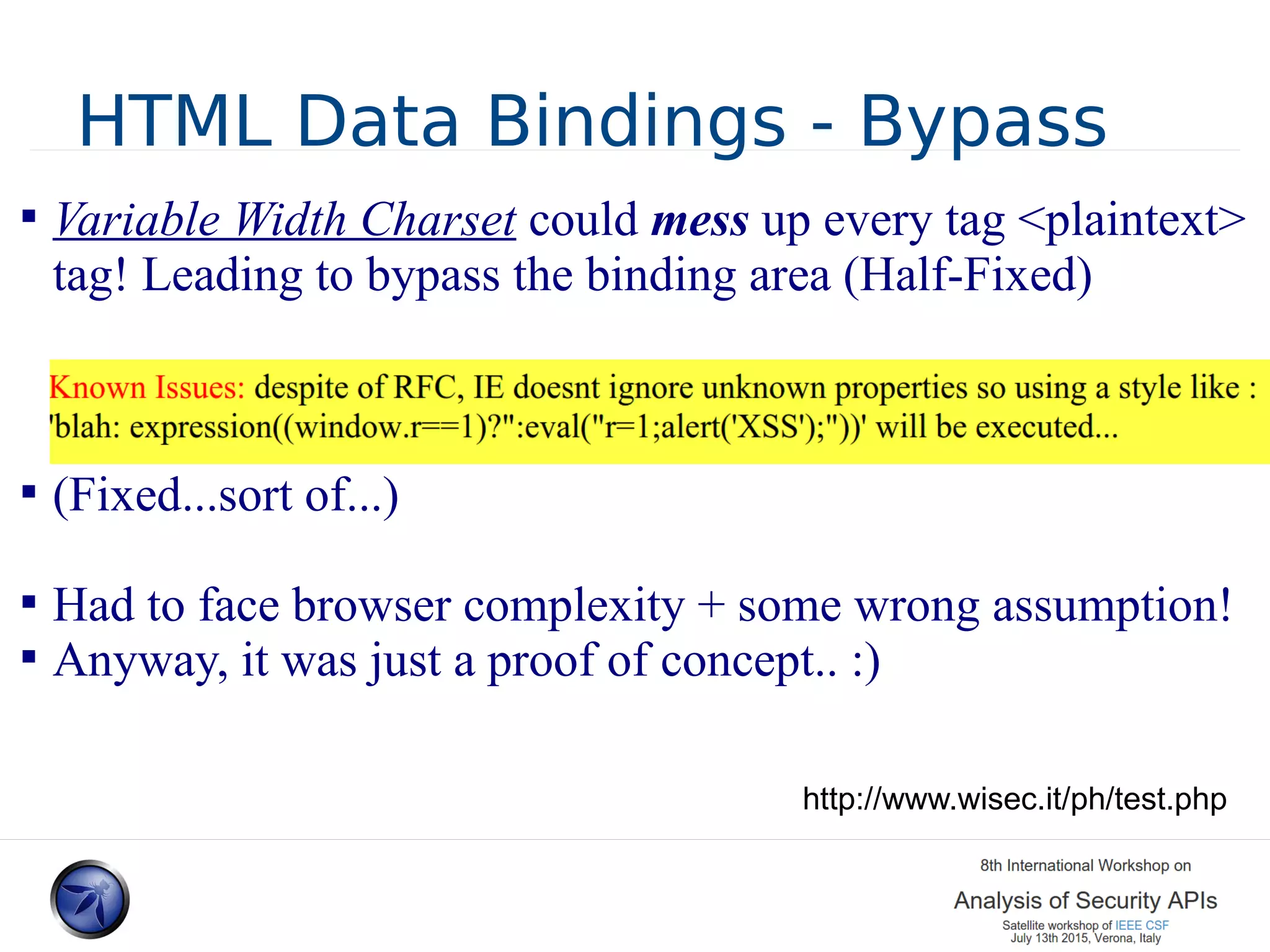
![Client side HTML Filtering - HTML Data Bindings 2007 HTML Data Binding – Author: Stefano Di Paola Tries to overcome the server side problem HTML Sanitizer using JS + SQL Prepared Statements approach and uses the browser native parser. http://www.wisec.it/sectou.php?id=46c5843ea4900 // URL Native Parsing var a = document.createElement('A'); return a.protocol var el=document.getElementById('someid') var val = document.createTextNode(binding['id']) el.appendChild( val );](https://image.slidesharecdn.com/presodipaolafinal1-150714075353-lva1-app6891/75/Sandboxing-JS-and-HTML-A-lession-Learned-16-2048.jpg)
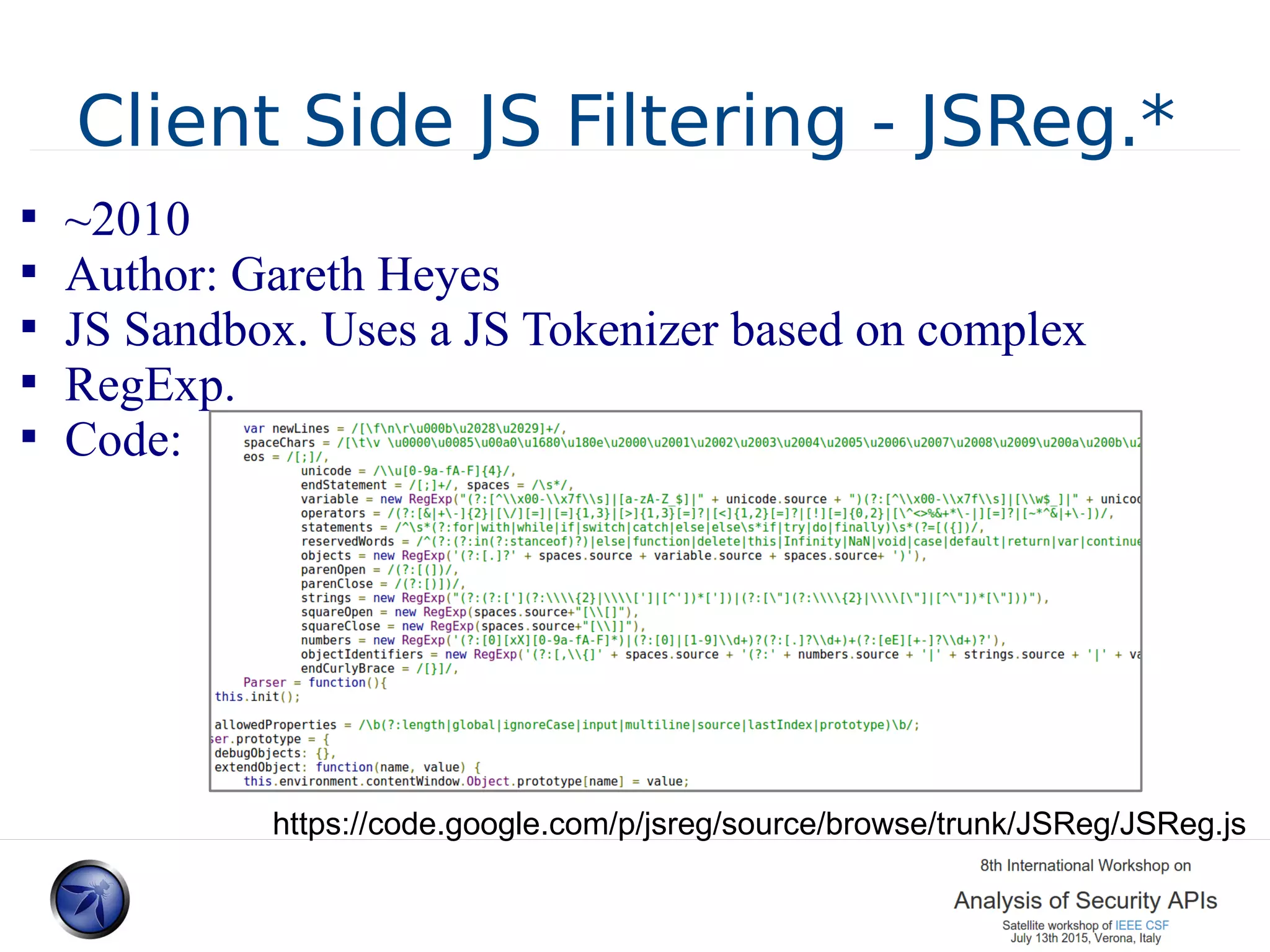
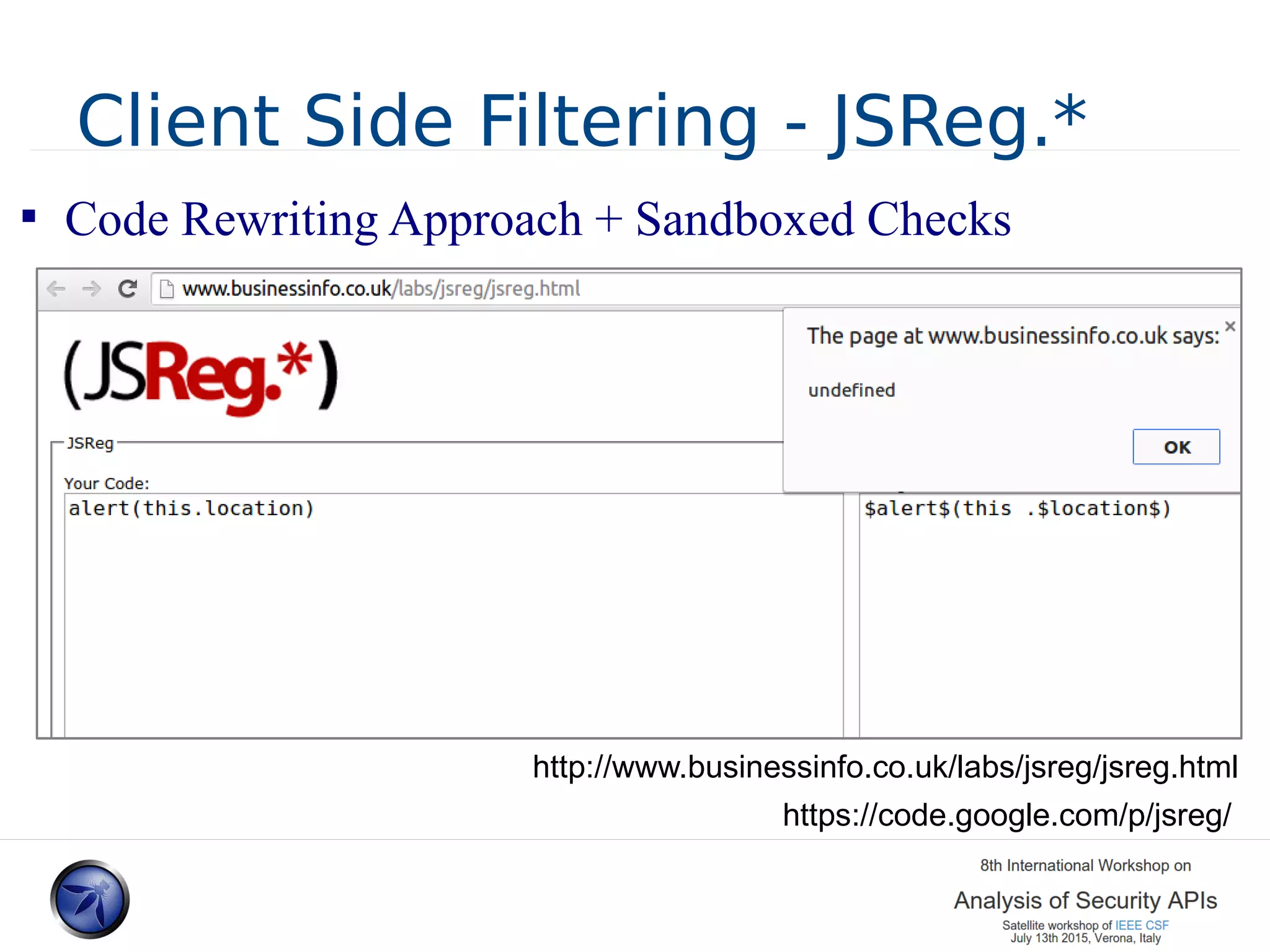
![JSReg.* – Bypasses 2010-2011 (/[/]/)[/(/))/+alert(top)+"/"/i] .. first is the failure to strip the single line comment which then fools the regex rule into thinking that the code is a regex object and not function calls .. http://marc.info/?l=websecurity&m=126855547523766 http://www.thespanner.co.uk/2010/10/31/jsreg-bypasses/](https://image.slidesharecdn.com/presodipaolafinal1-150714075353-lva1-app6891/75/Sandboxing-JS-and-HTML-A-lession-Learned-20-2048.jpg)