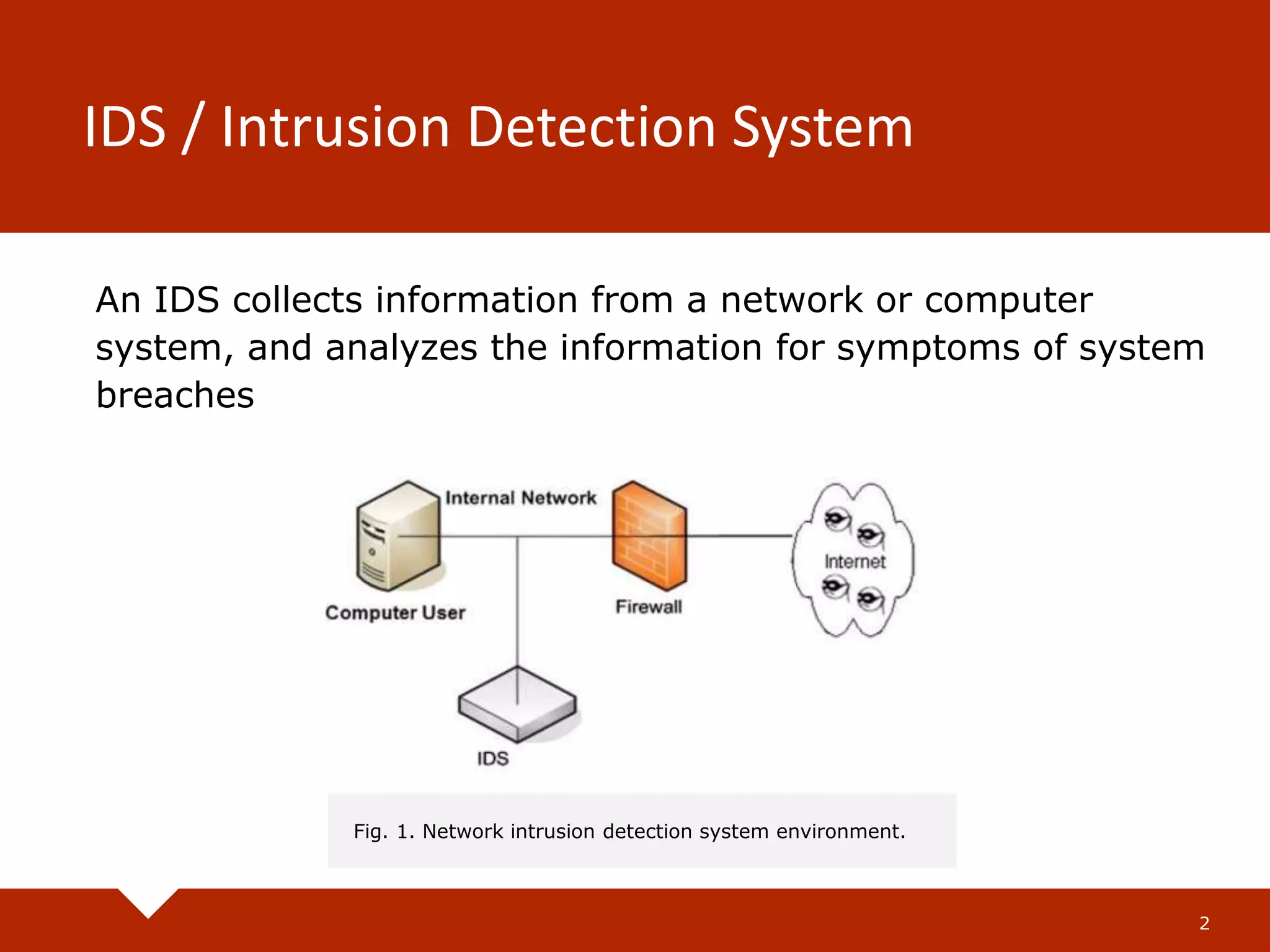
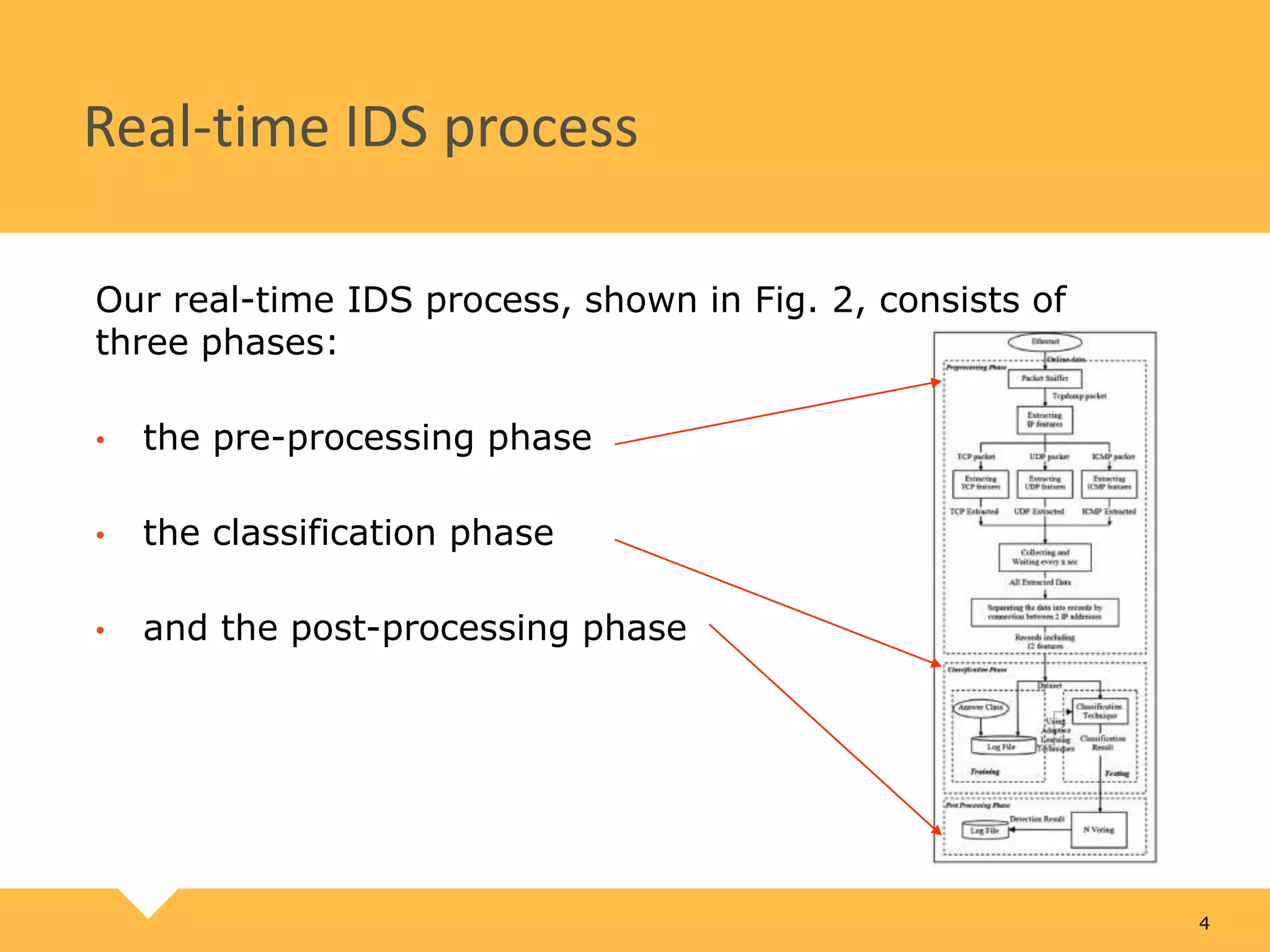
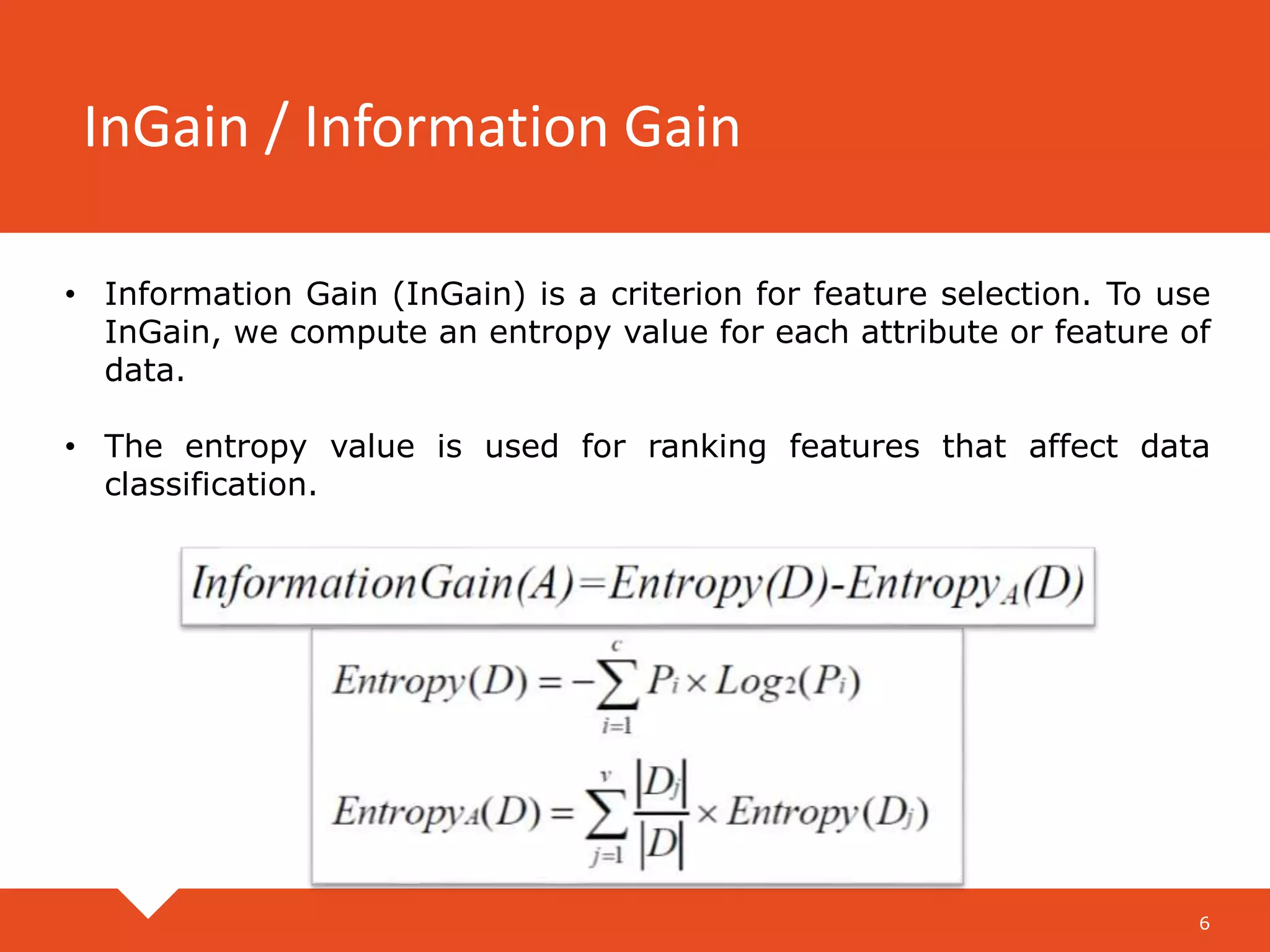
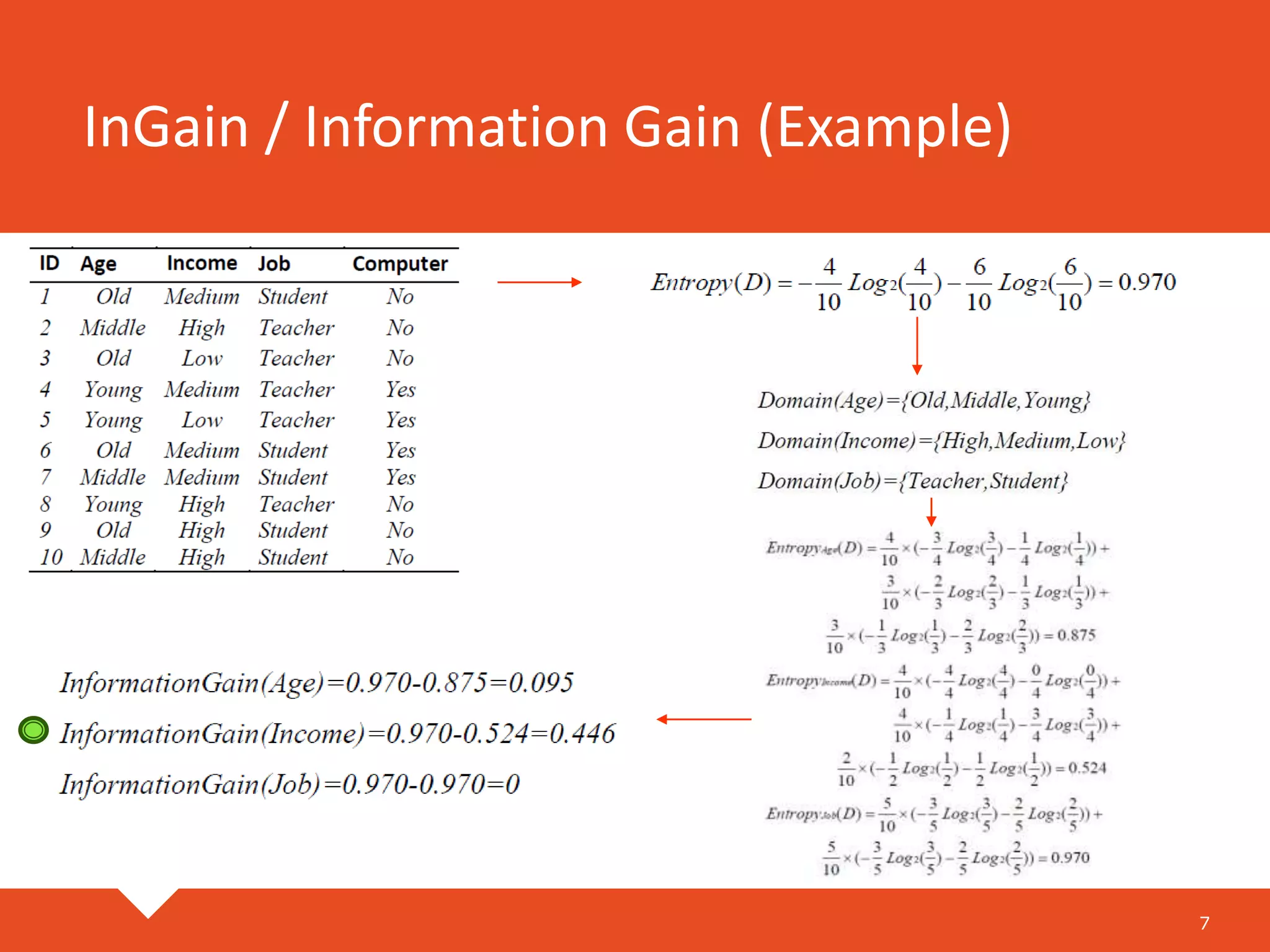
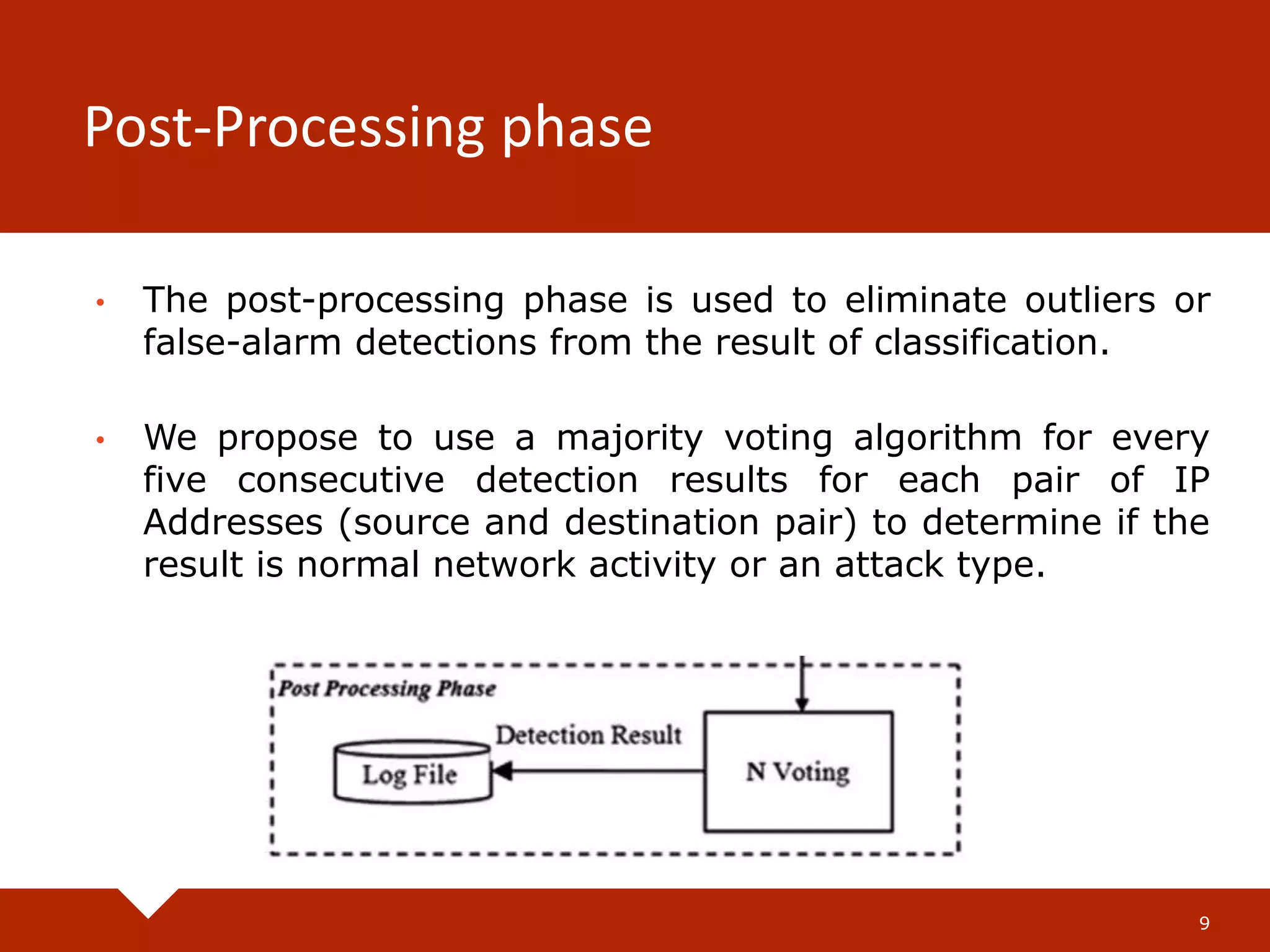
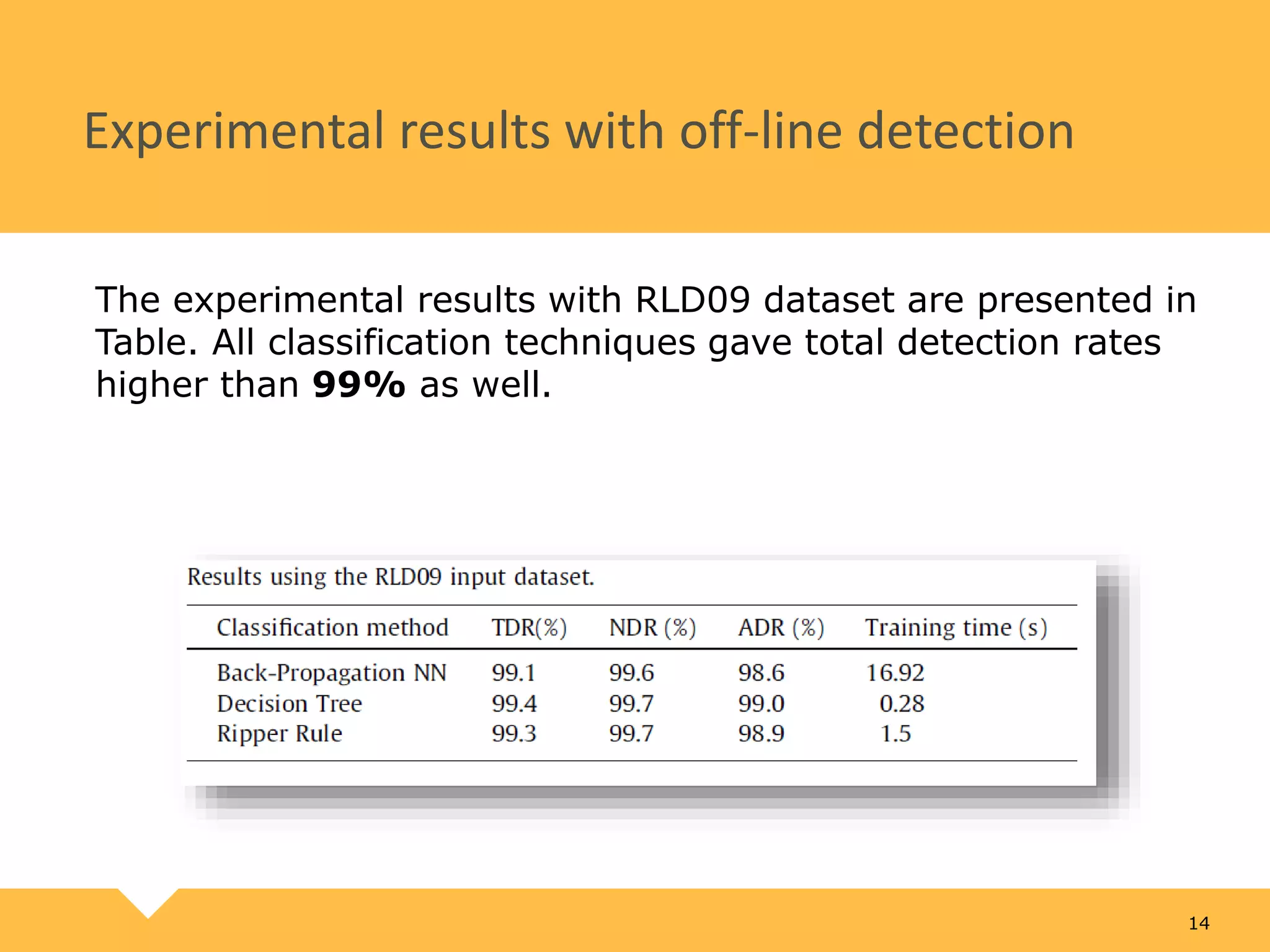
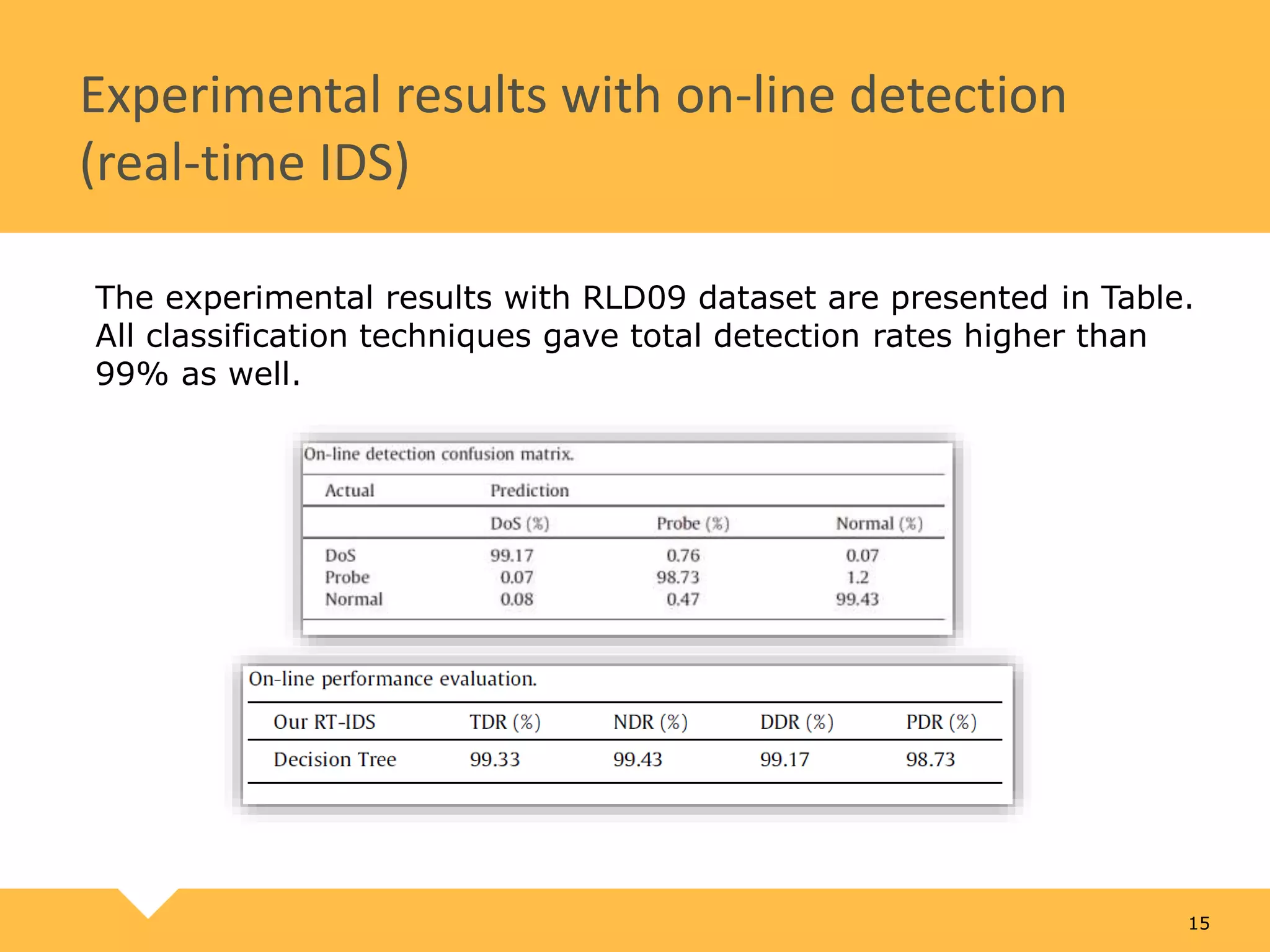
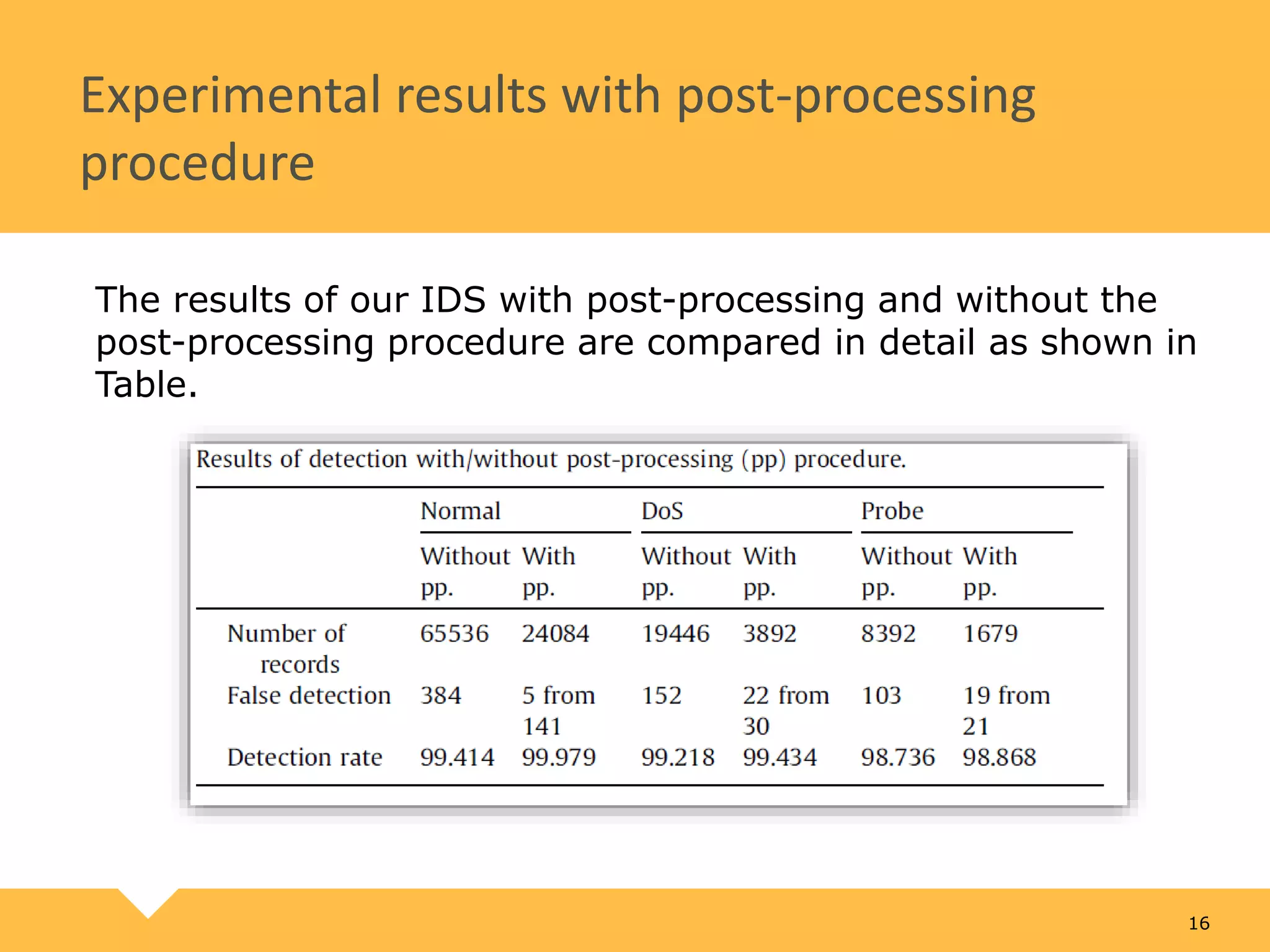
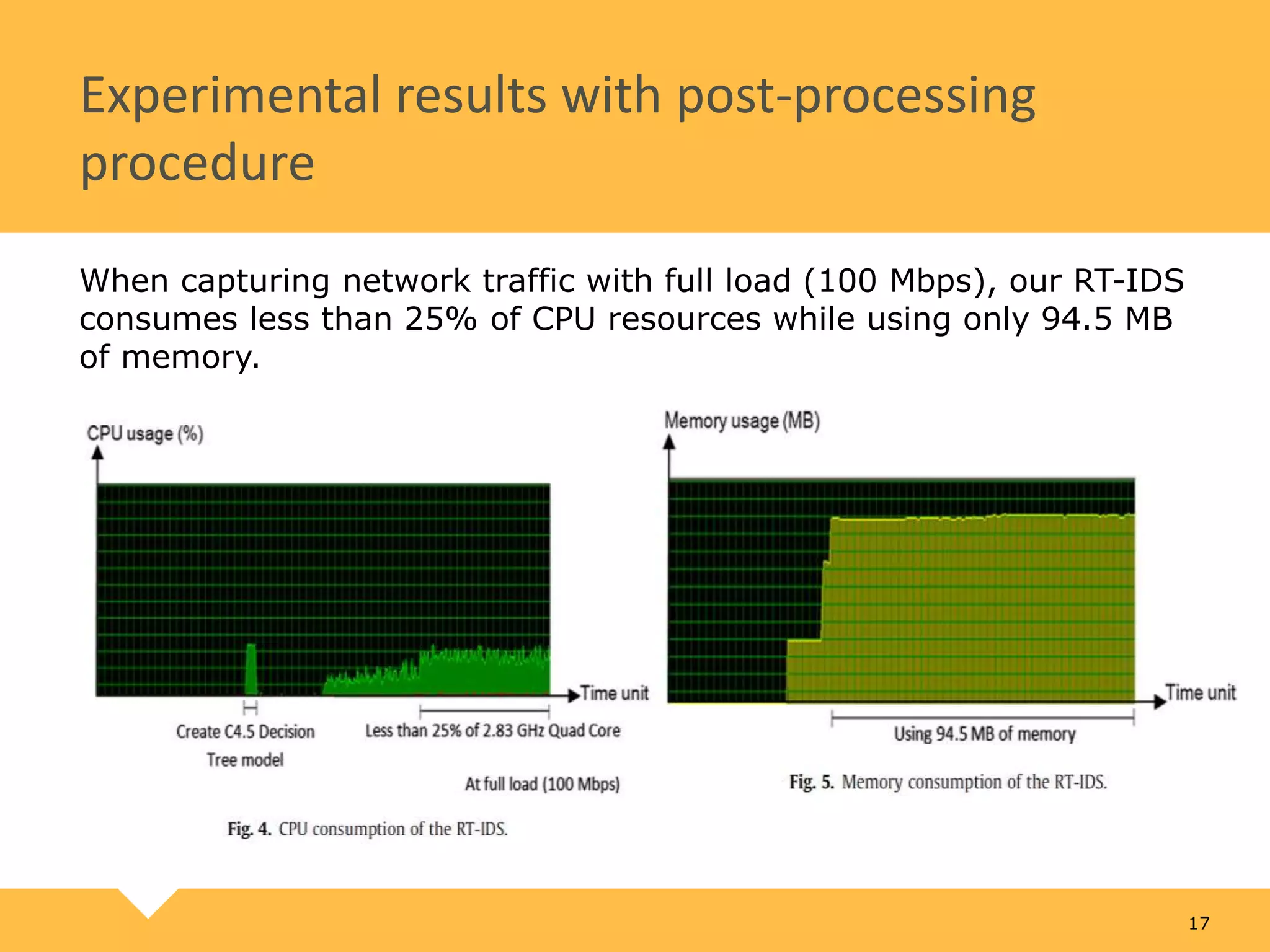
The document describes a practical real-time intrusion detection system (IDS) utilizing machine learning approaches, outlining its three main phases: pre-processing, classification, and post-processing. It details the process of extracting network packet information, the criteria for feature selection using information gain, and the performance metrics used to evaluate detection effectiveness. Experimental results demonstrate high detection rates for Distributed Denial of Service (DDoS) and probe attacks, confirming the IDS's efficiency with minimal resource consumption.