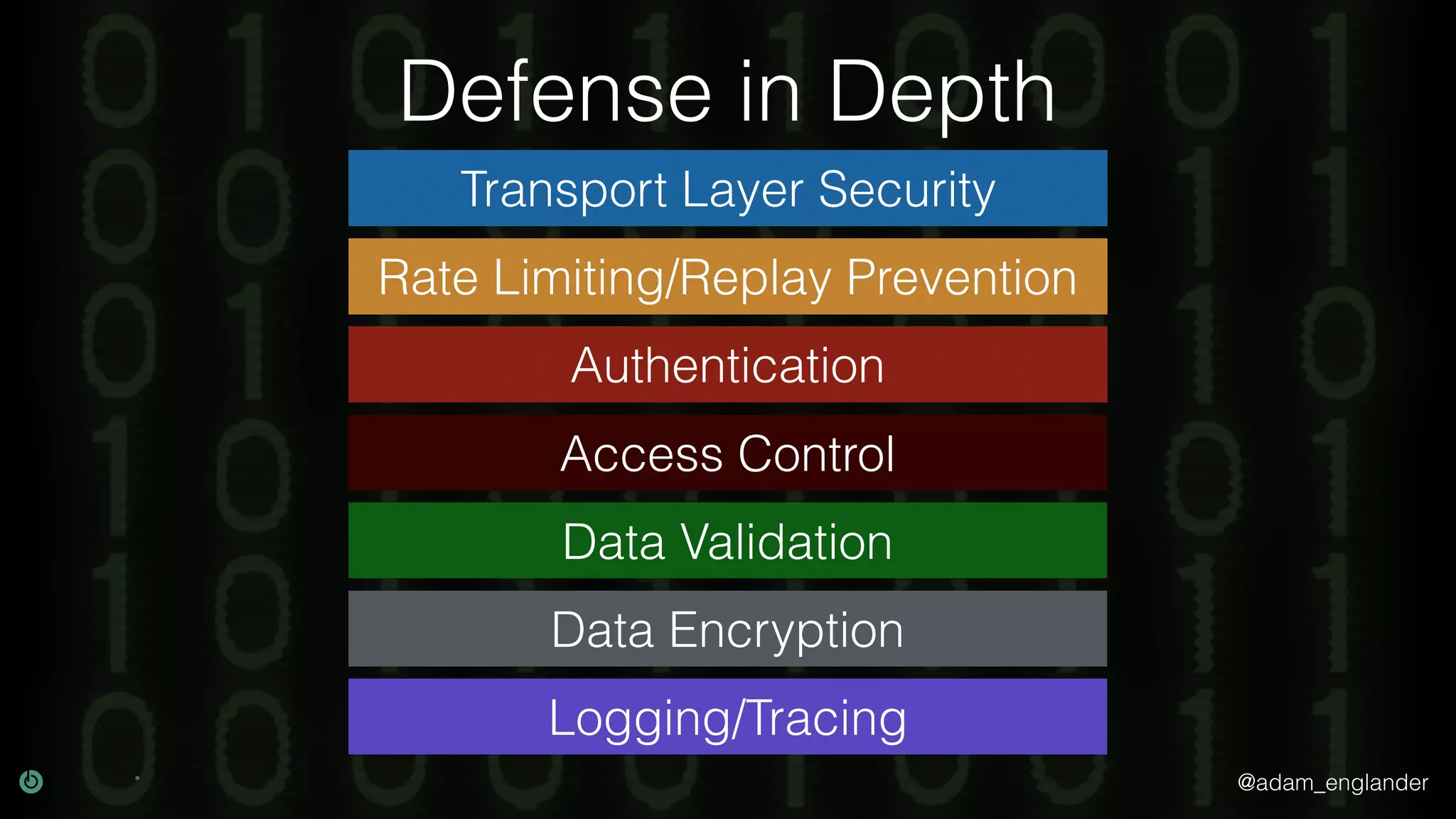
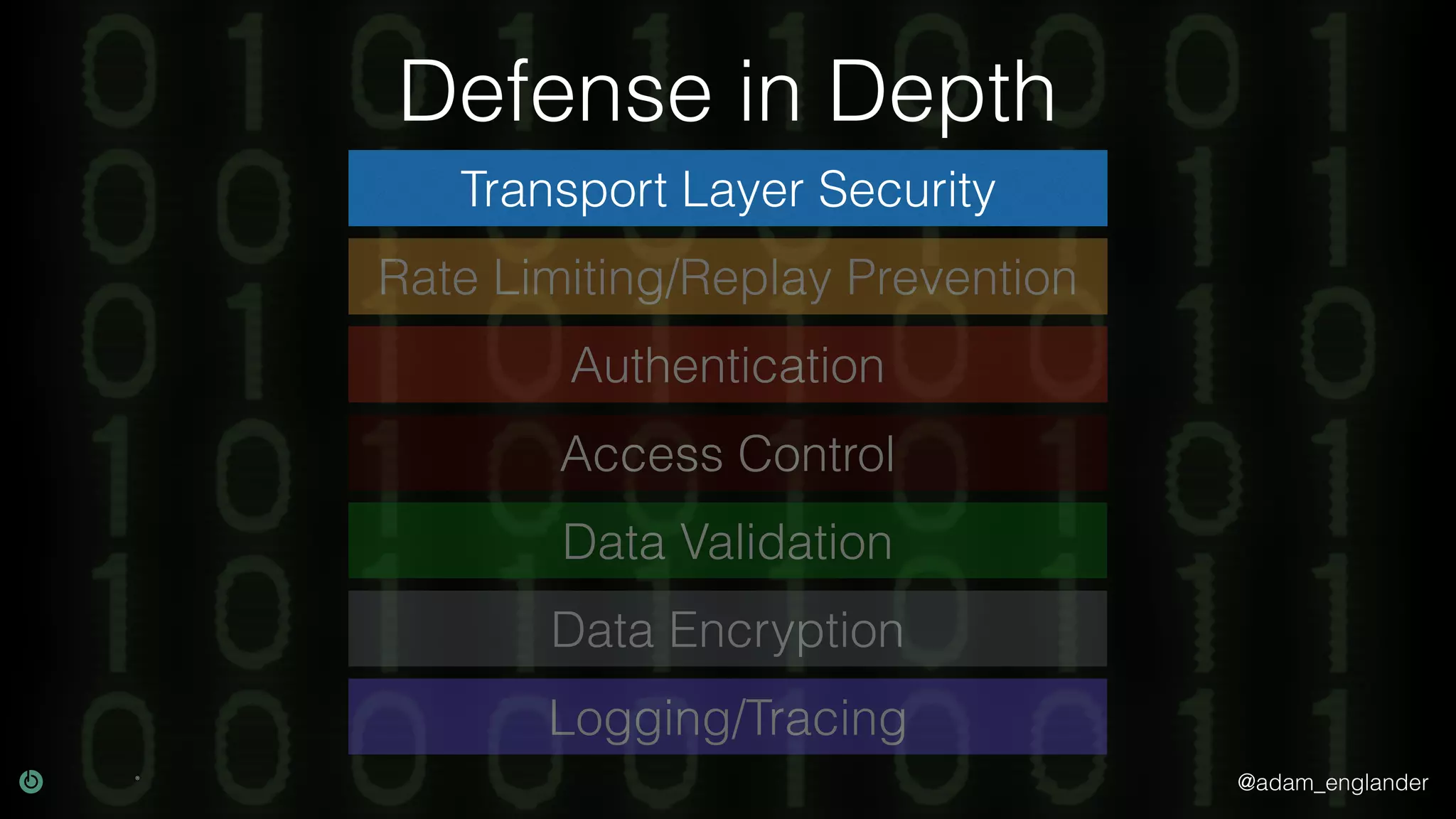
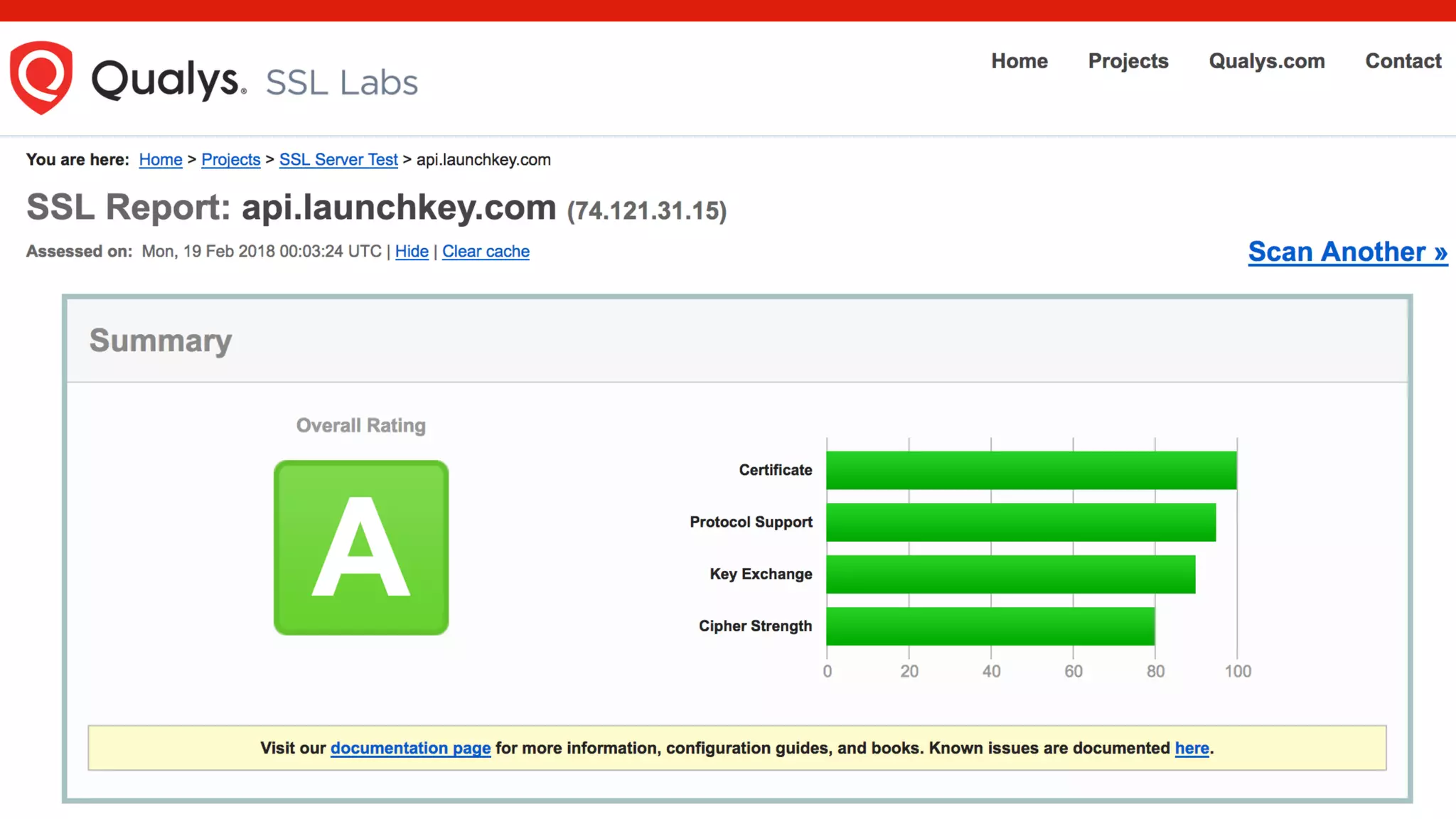
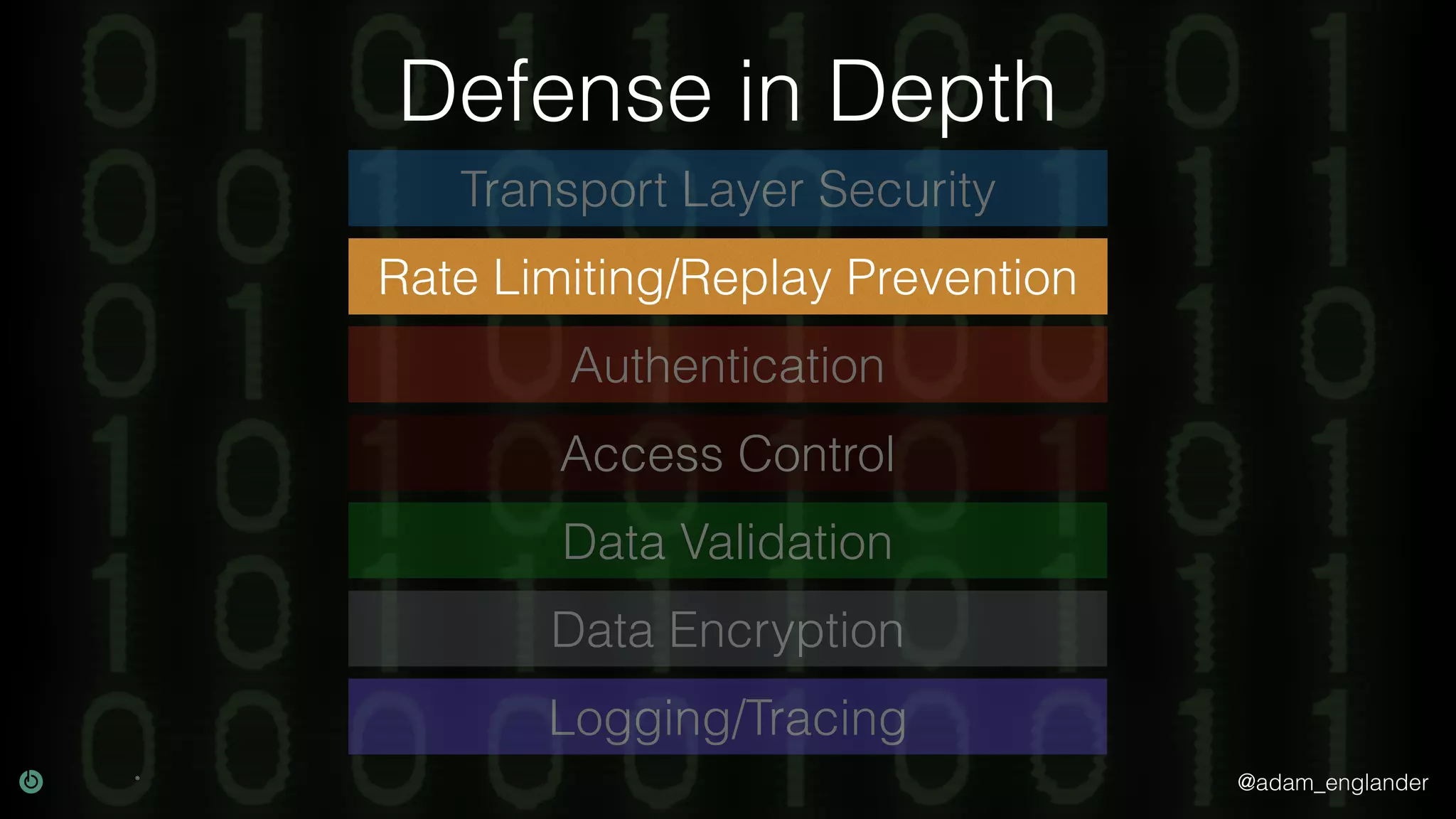
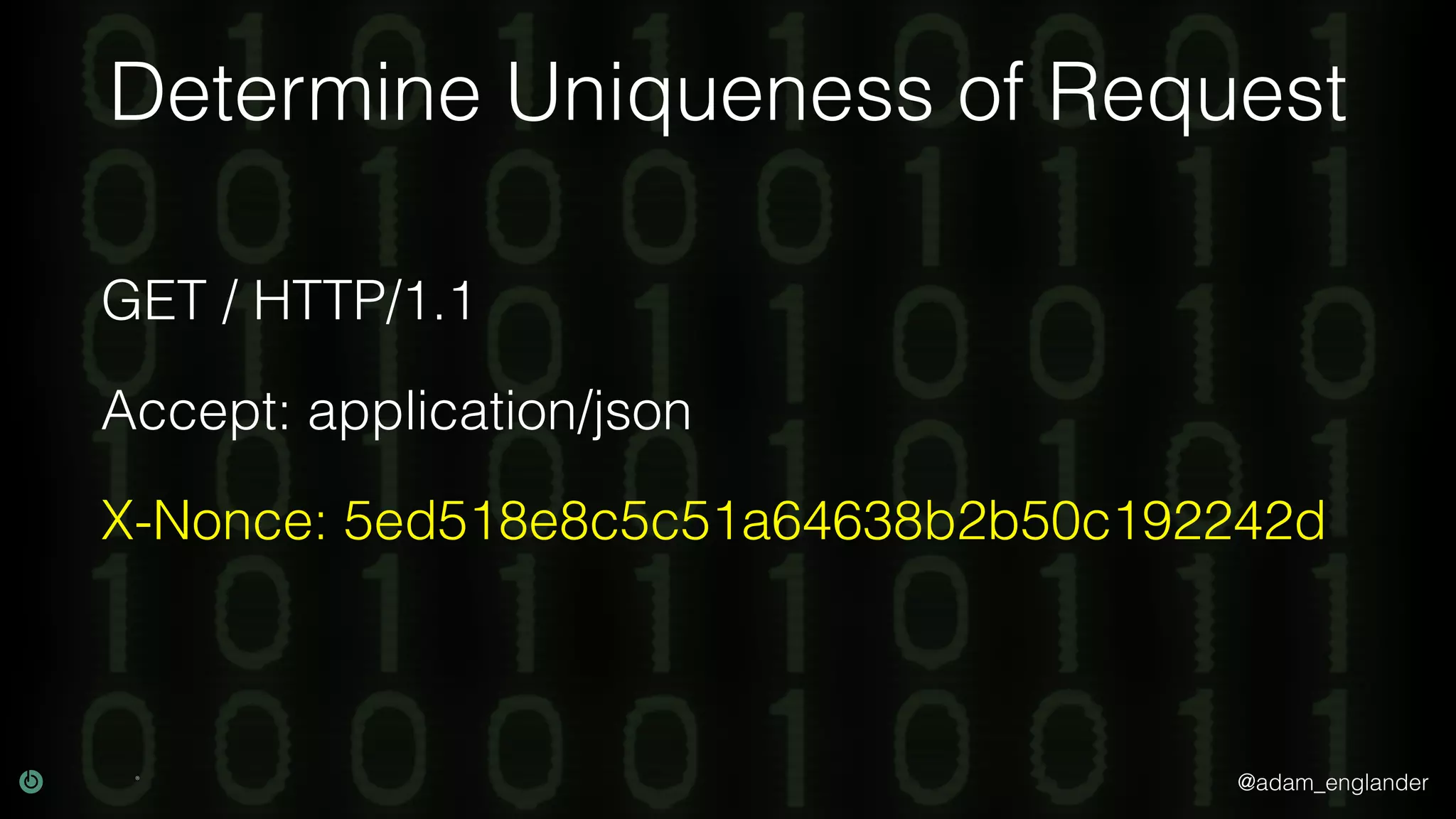
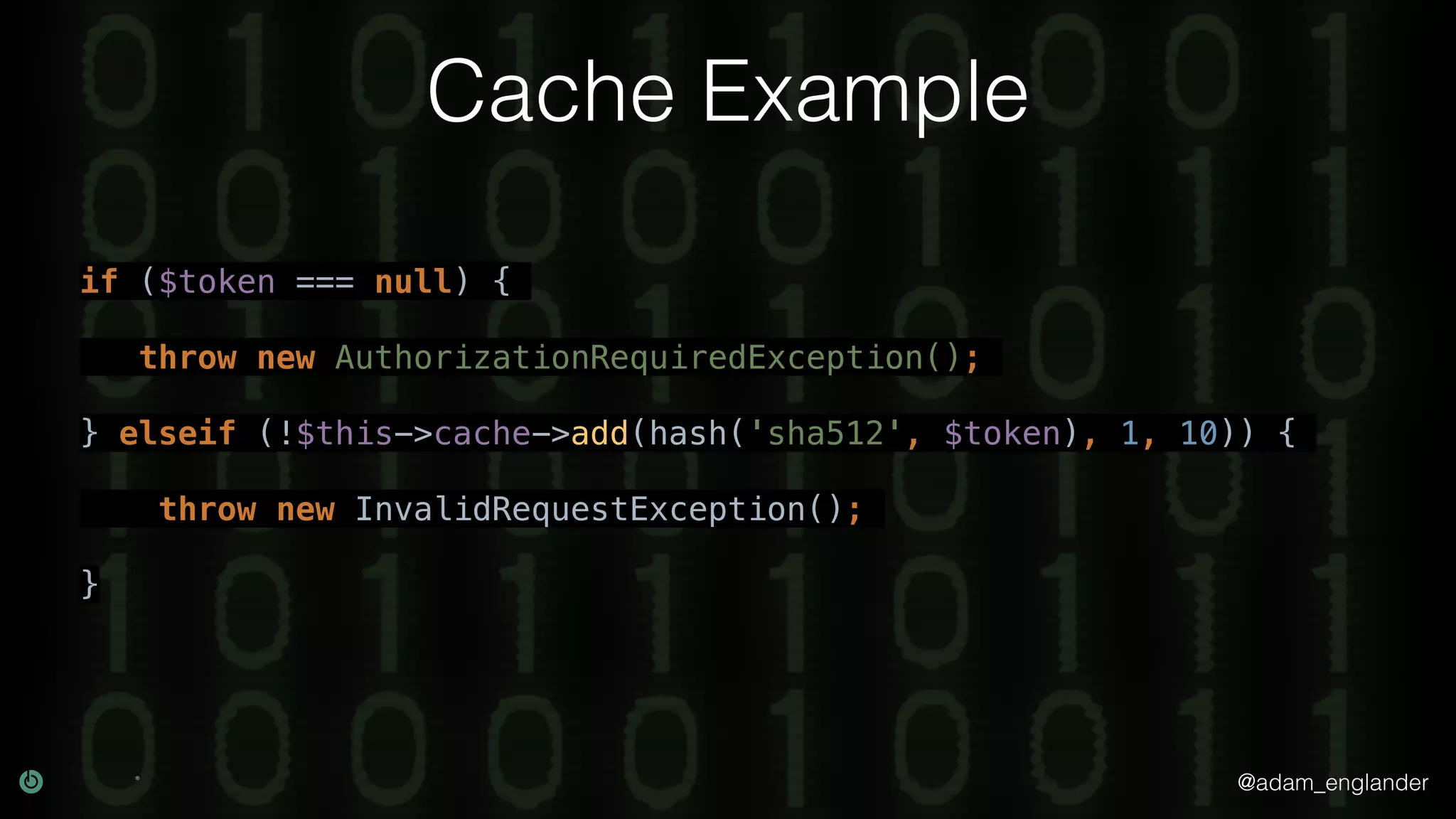
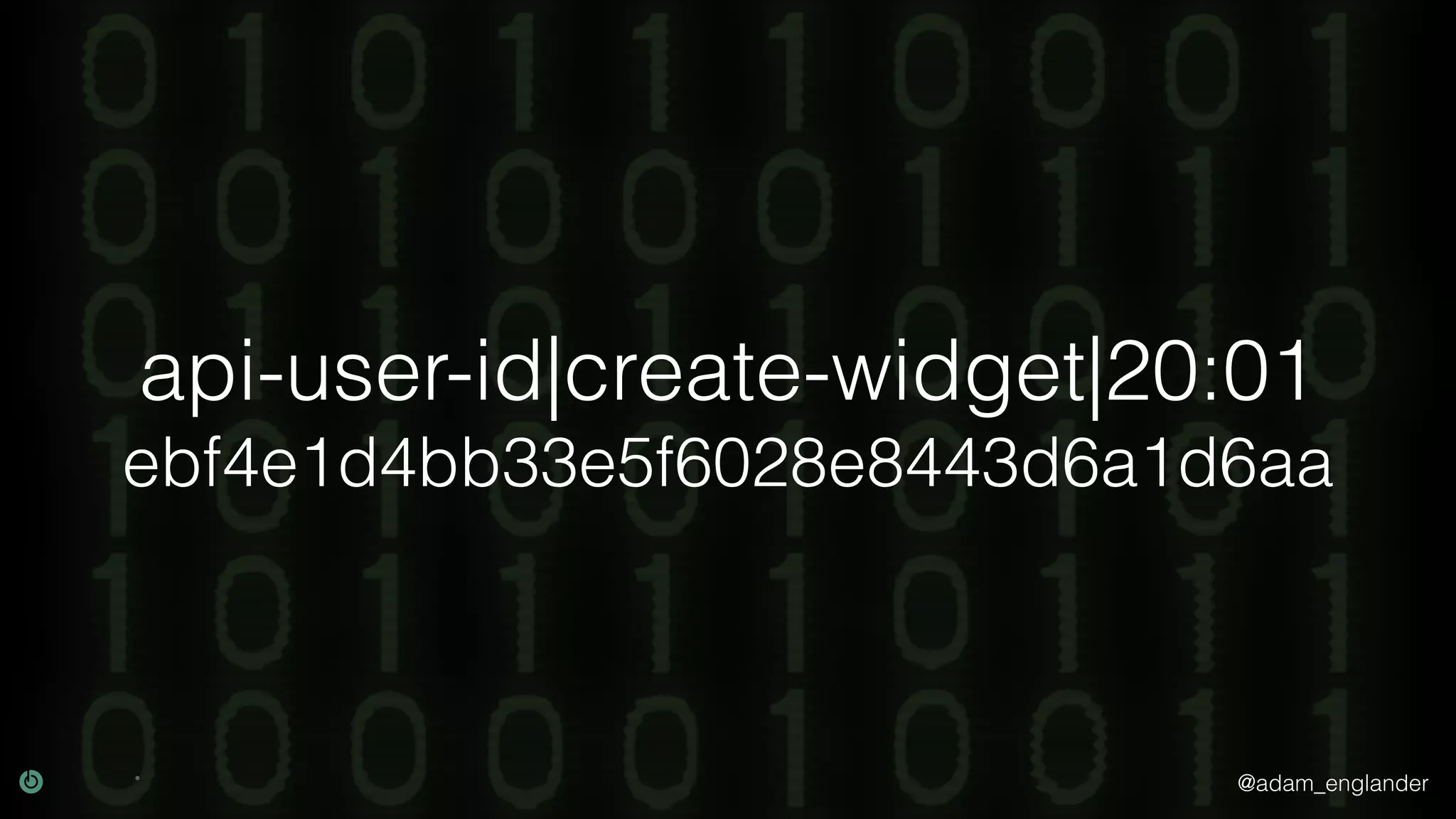
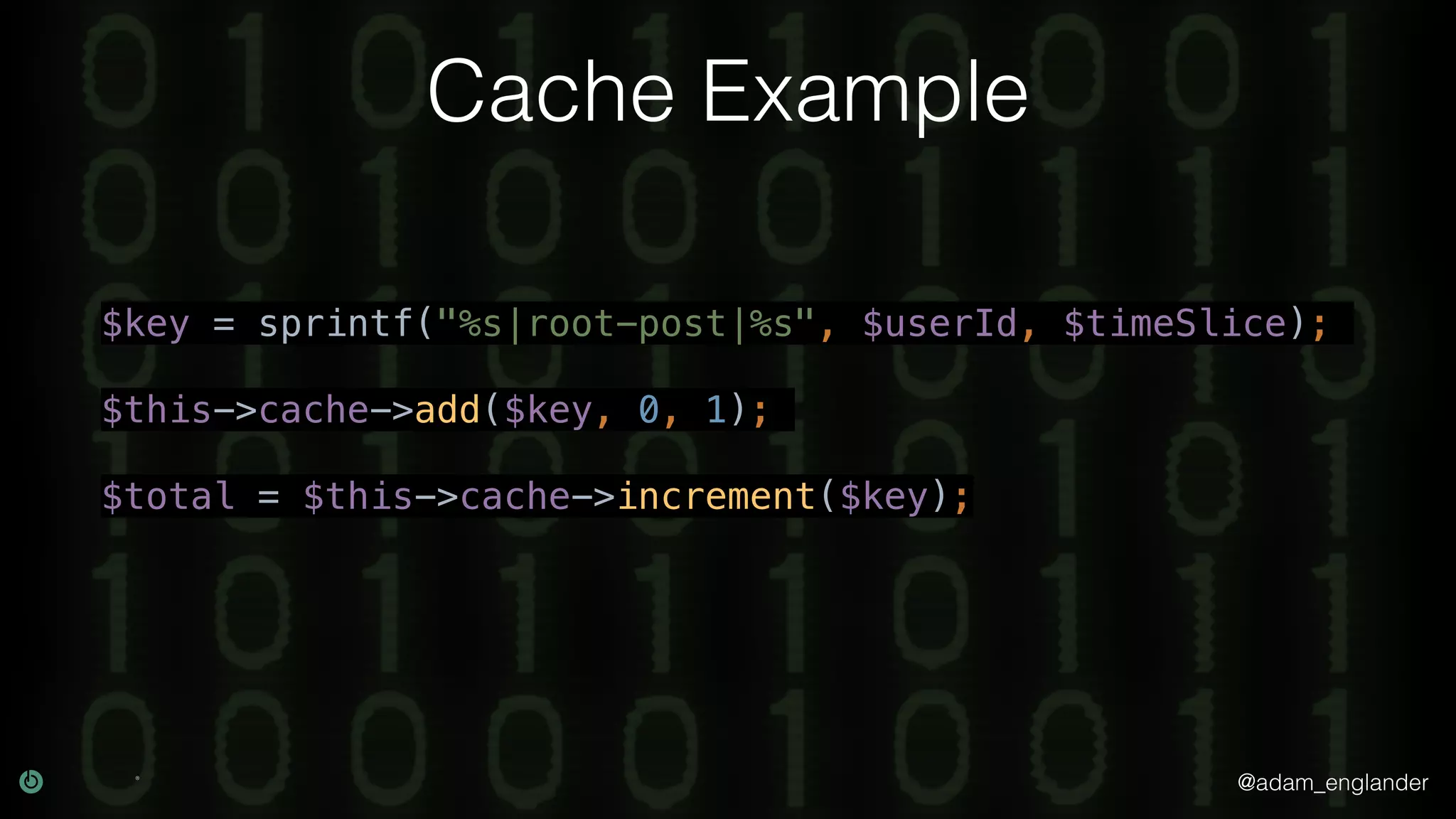
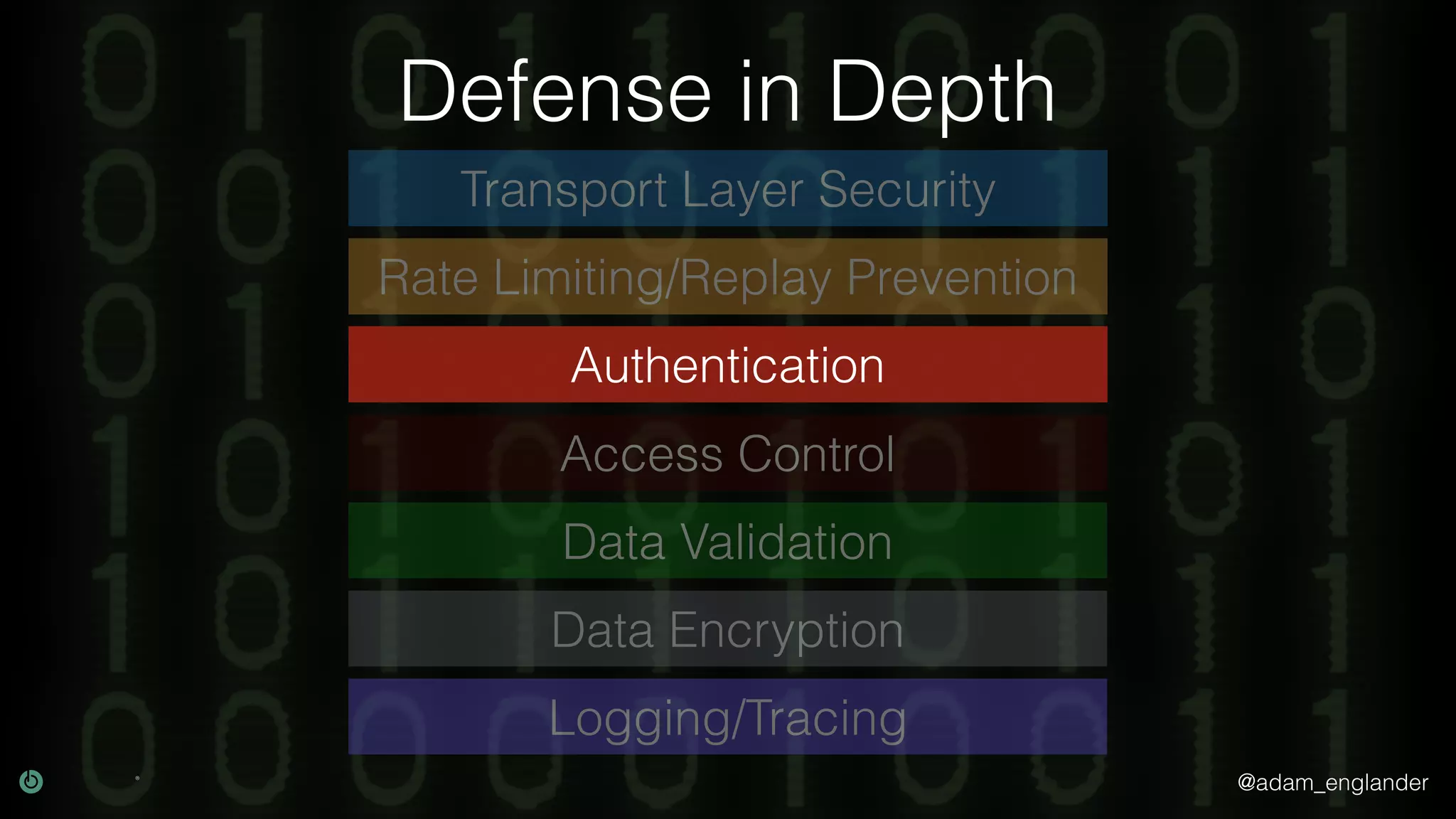
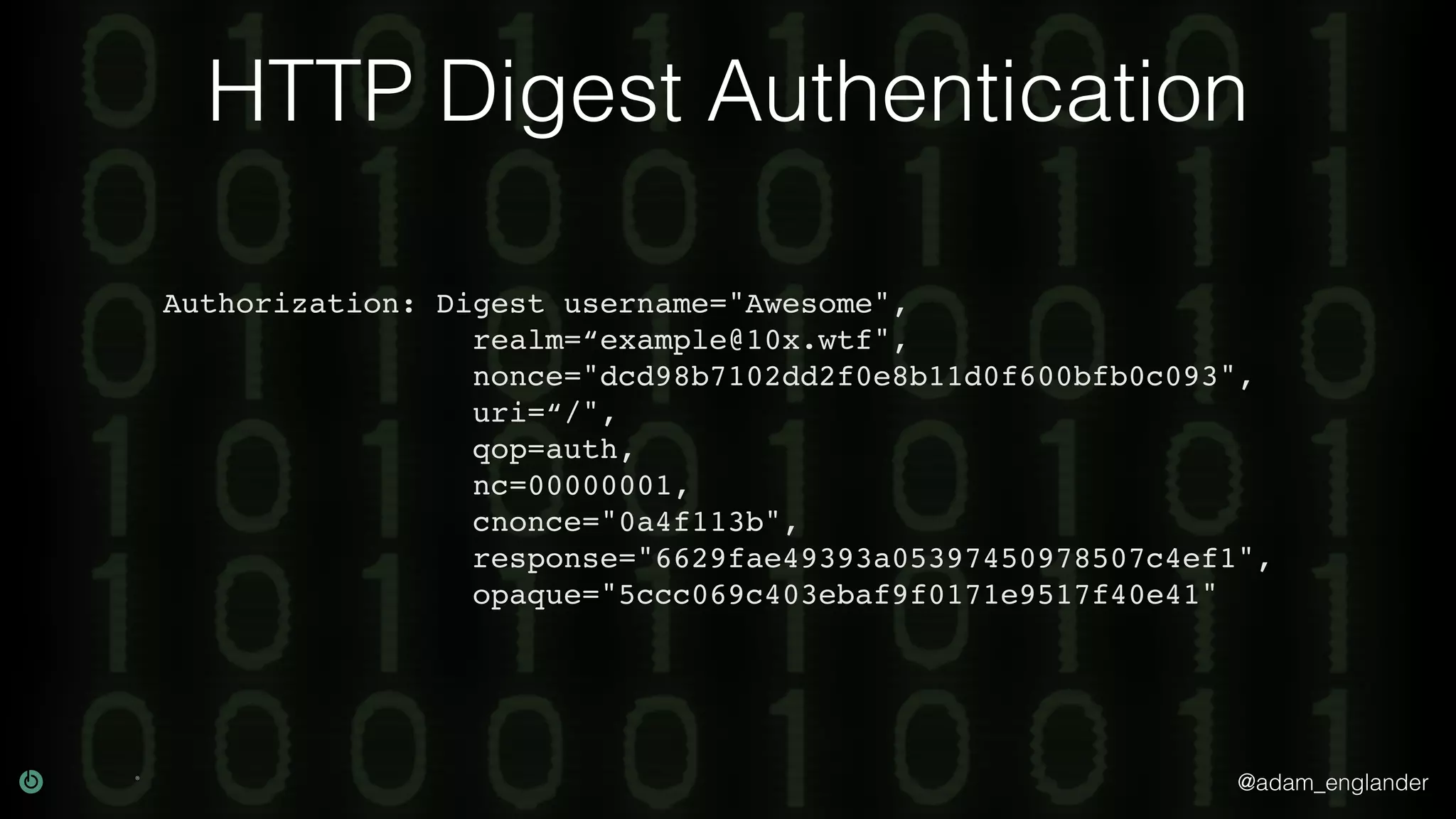
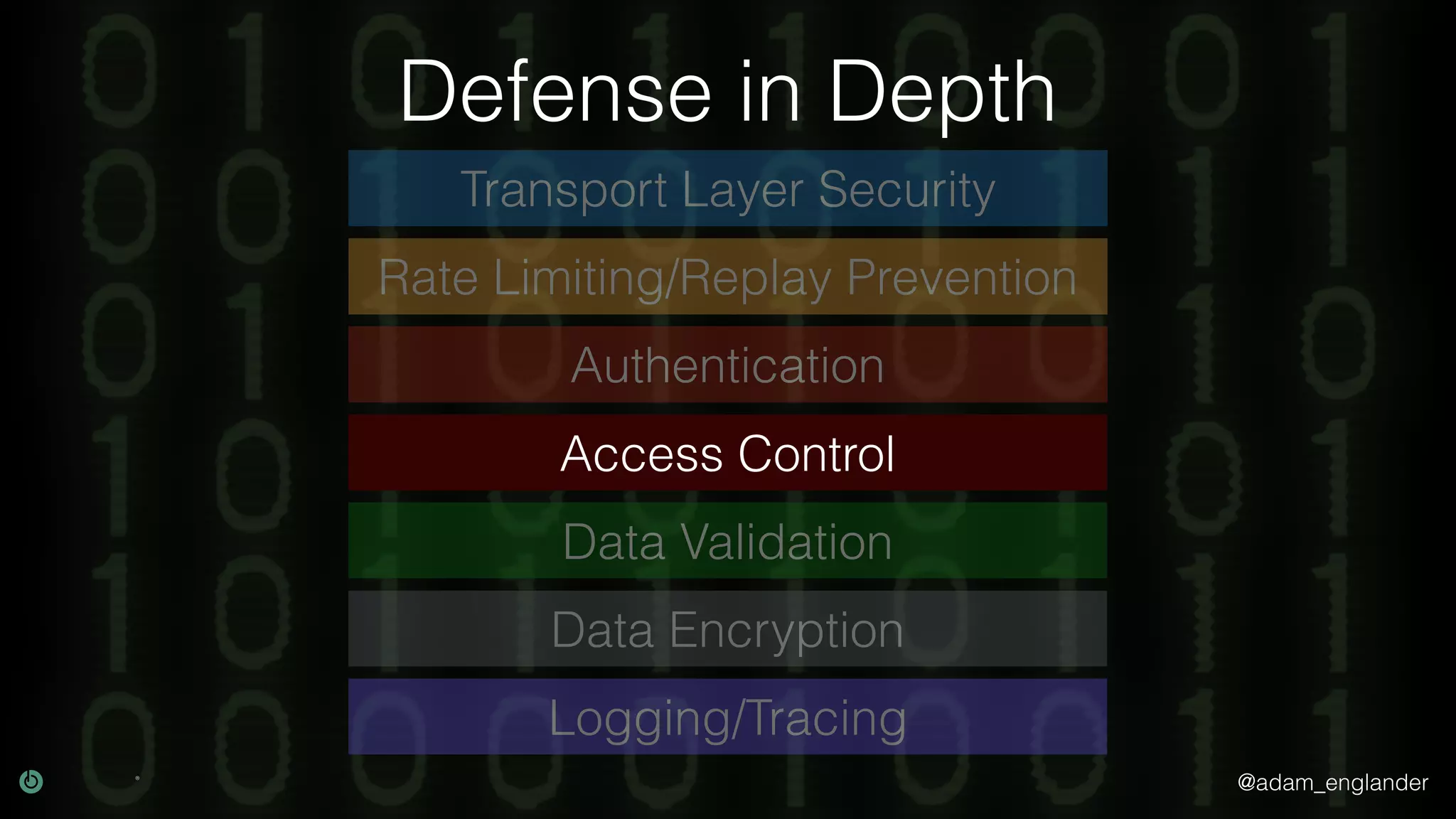
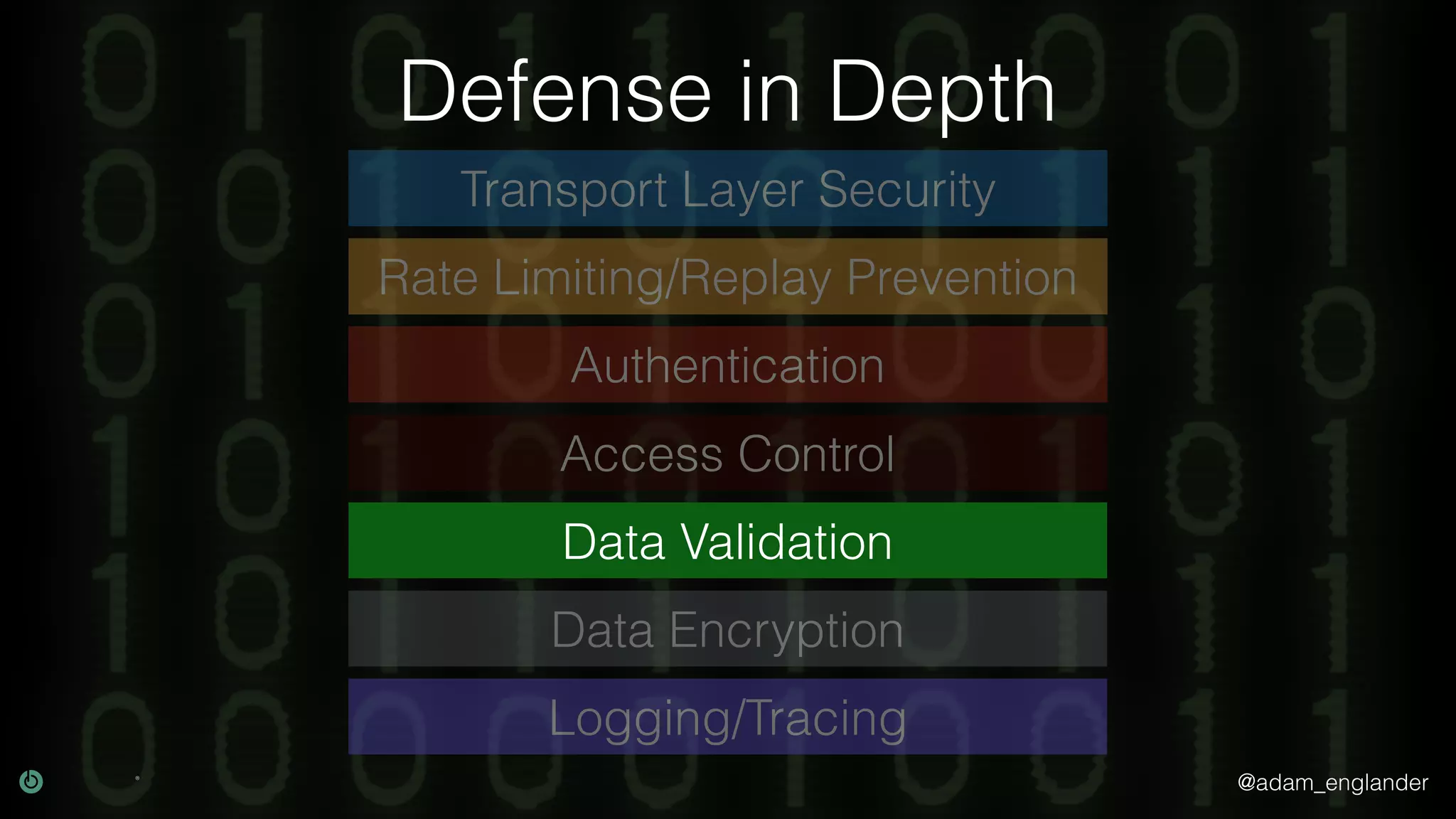
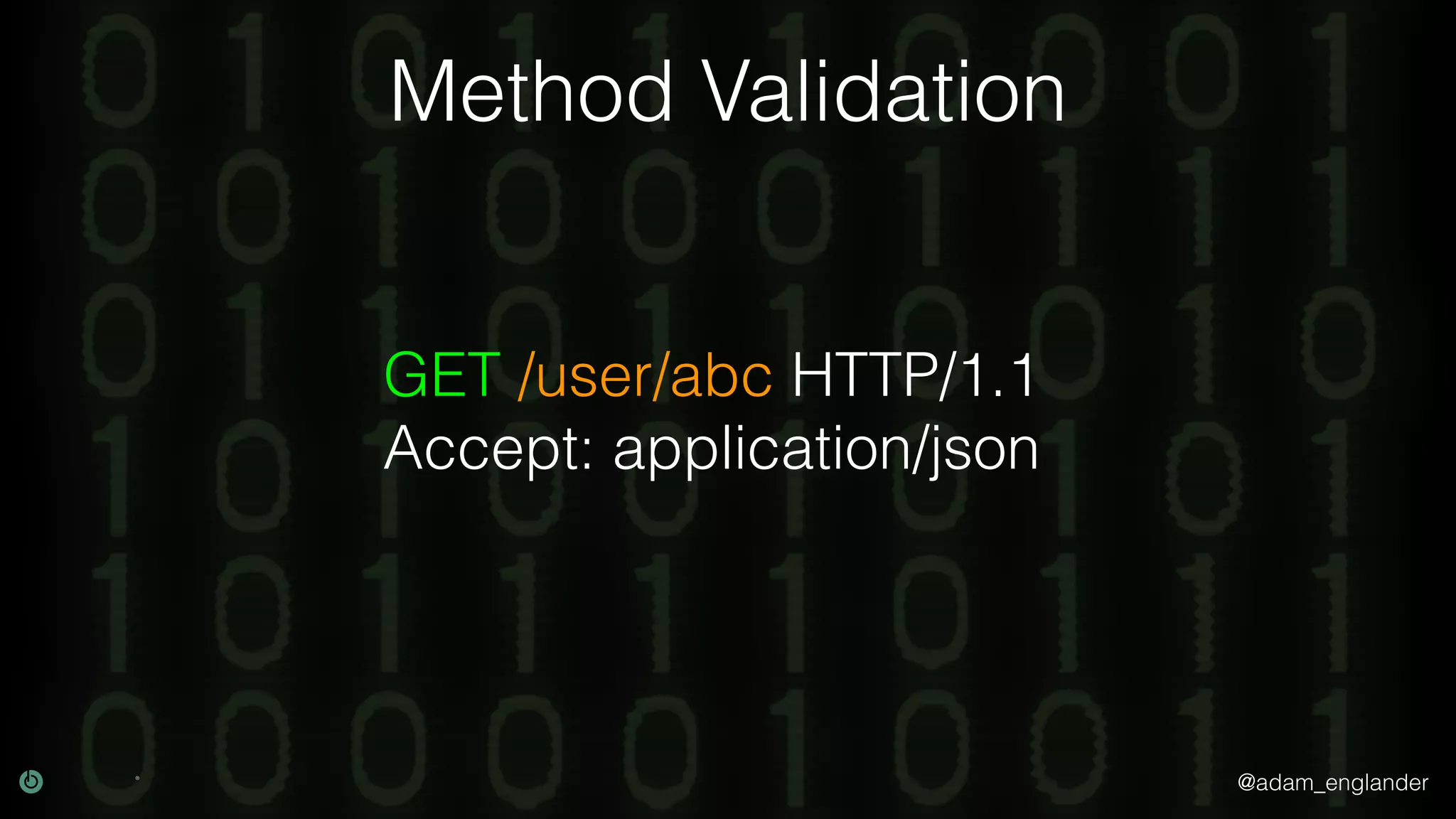
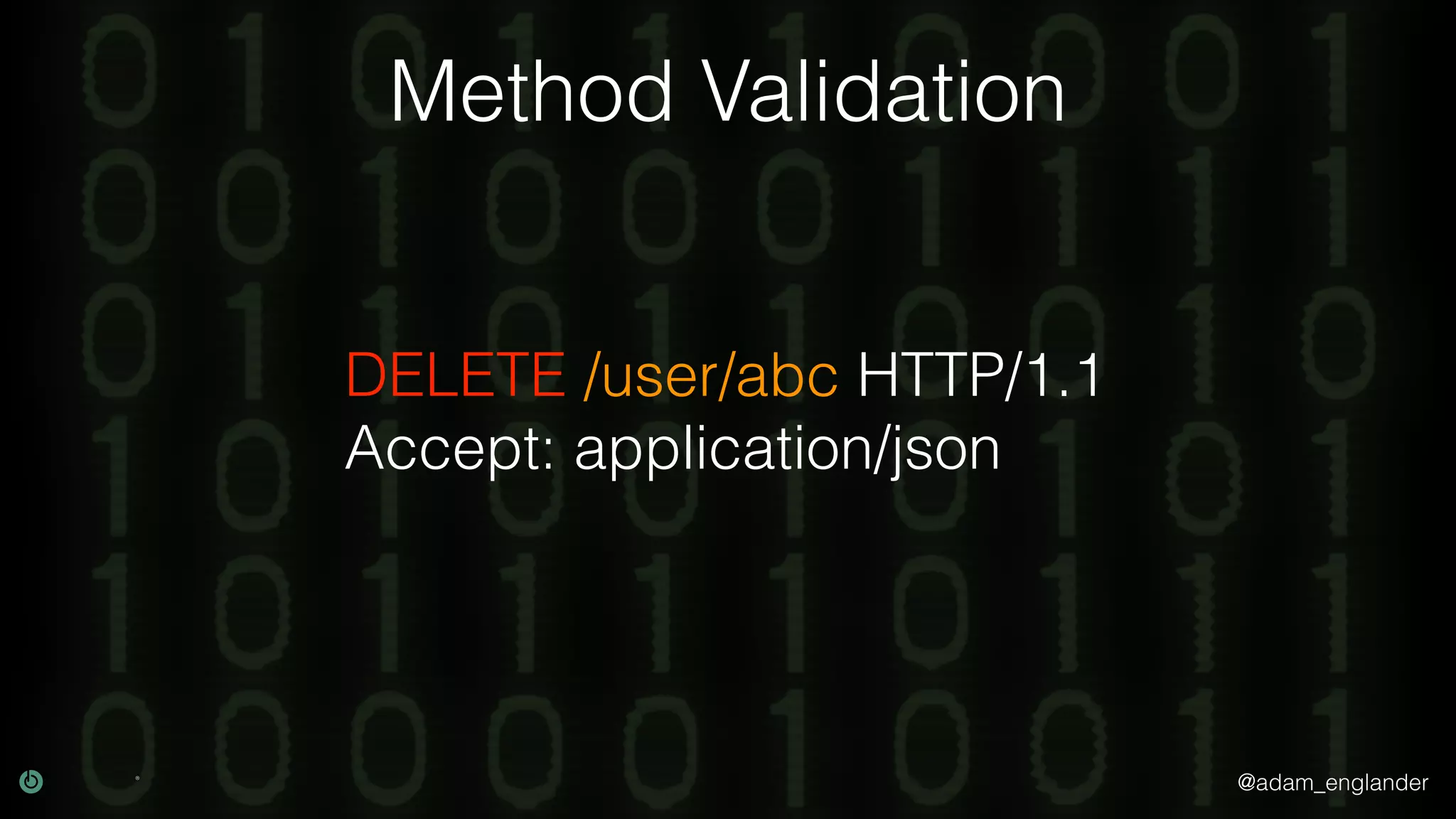
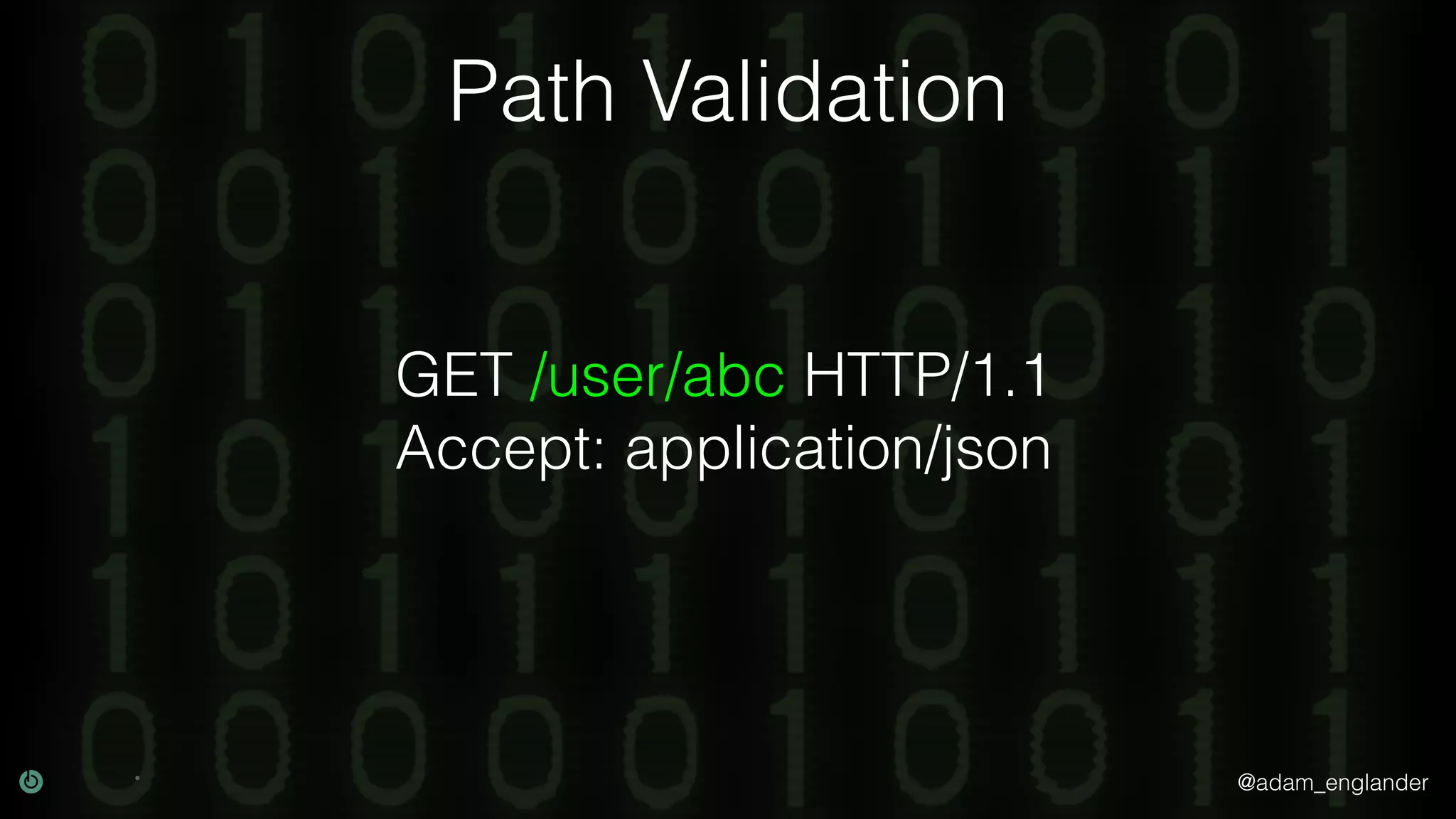
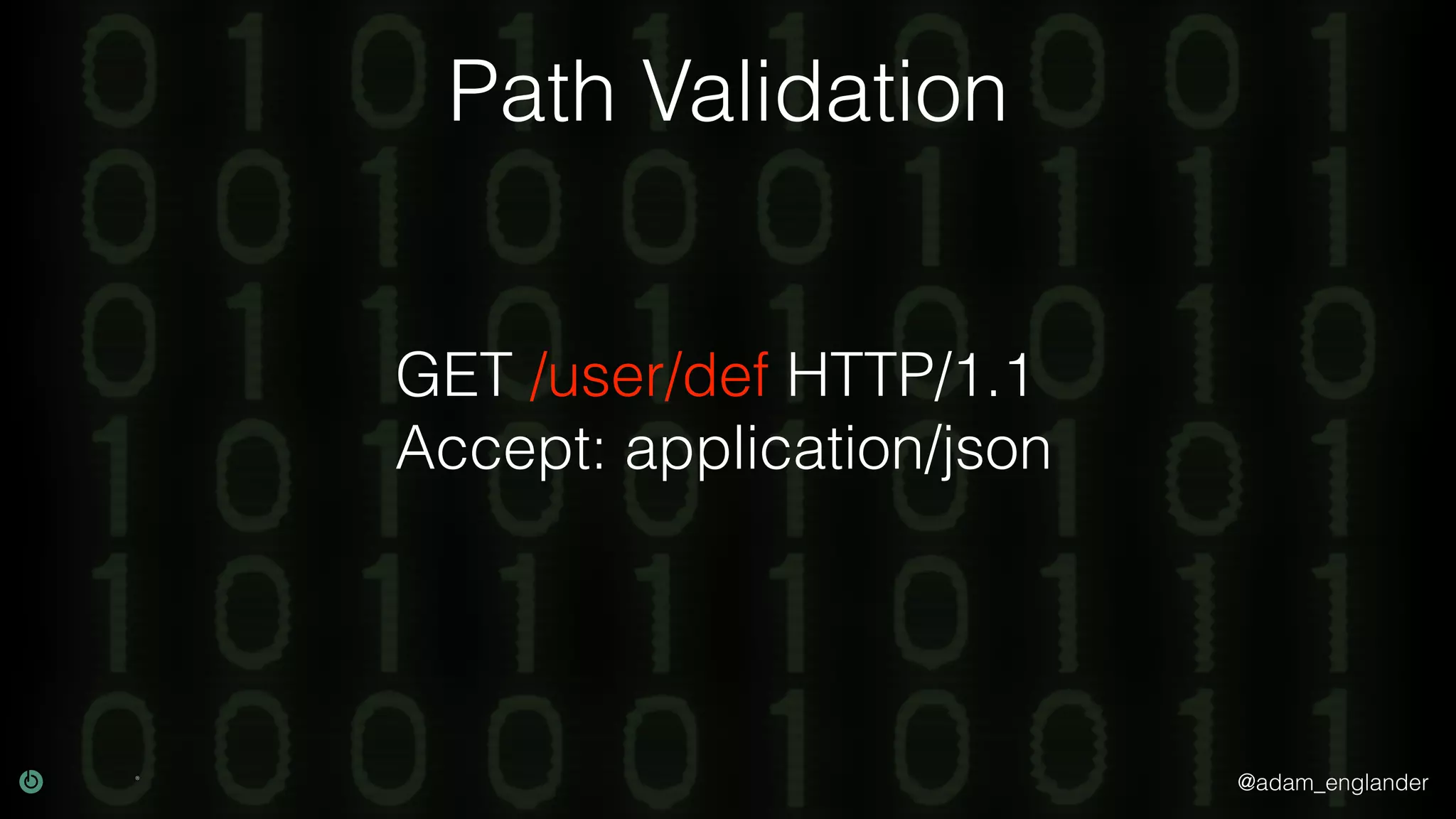
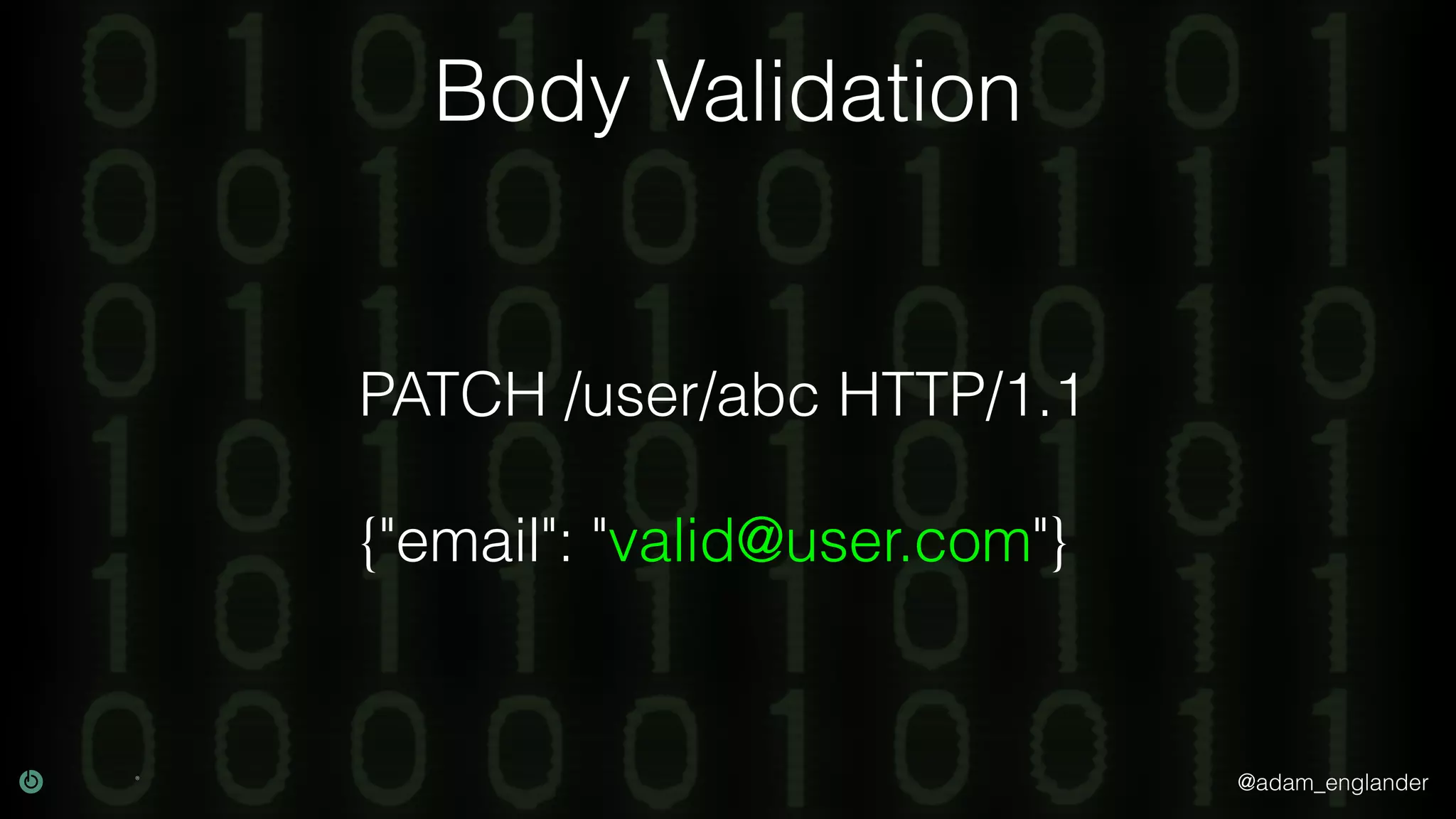
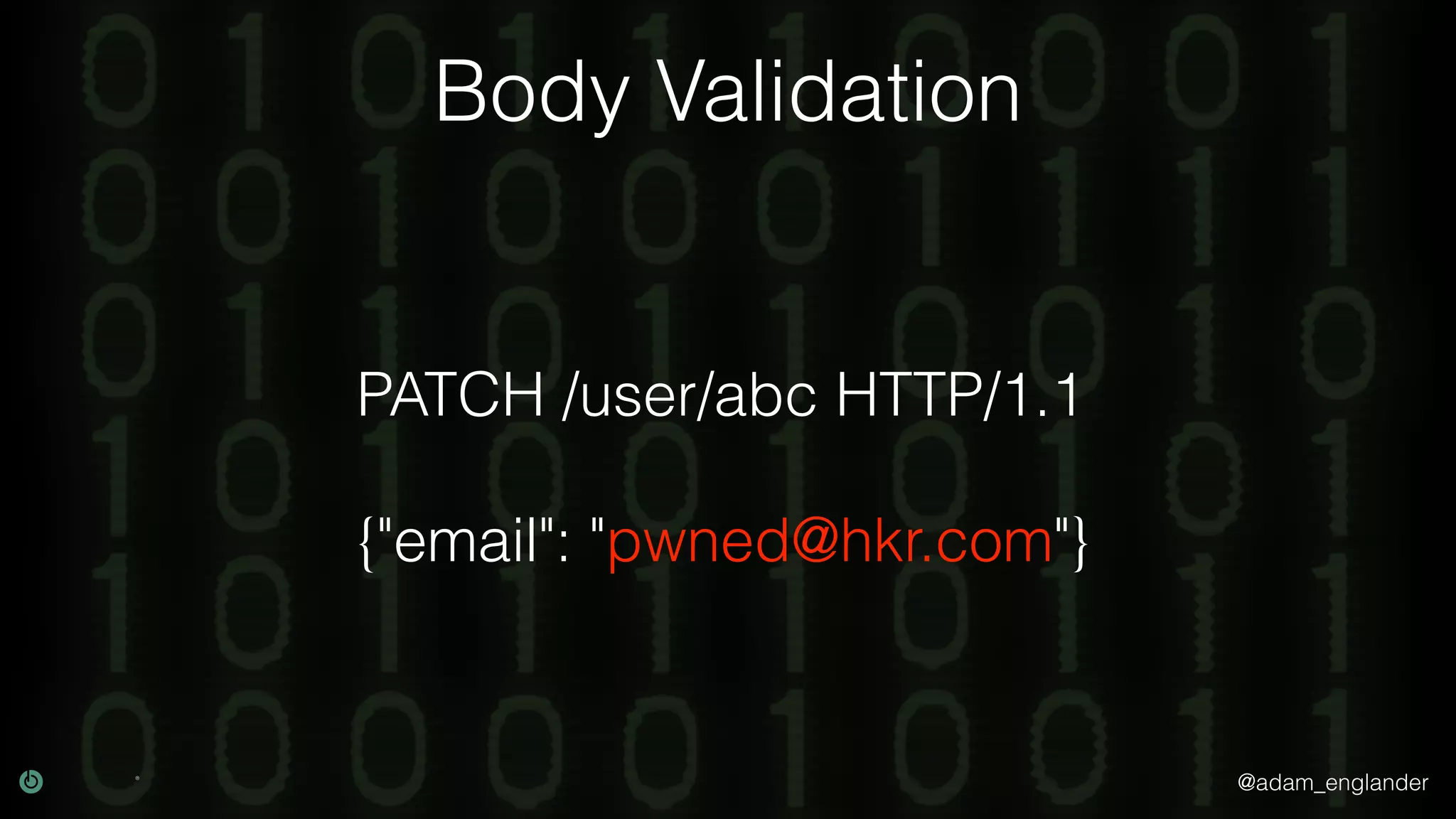
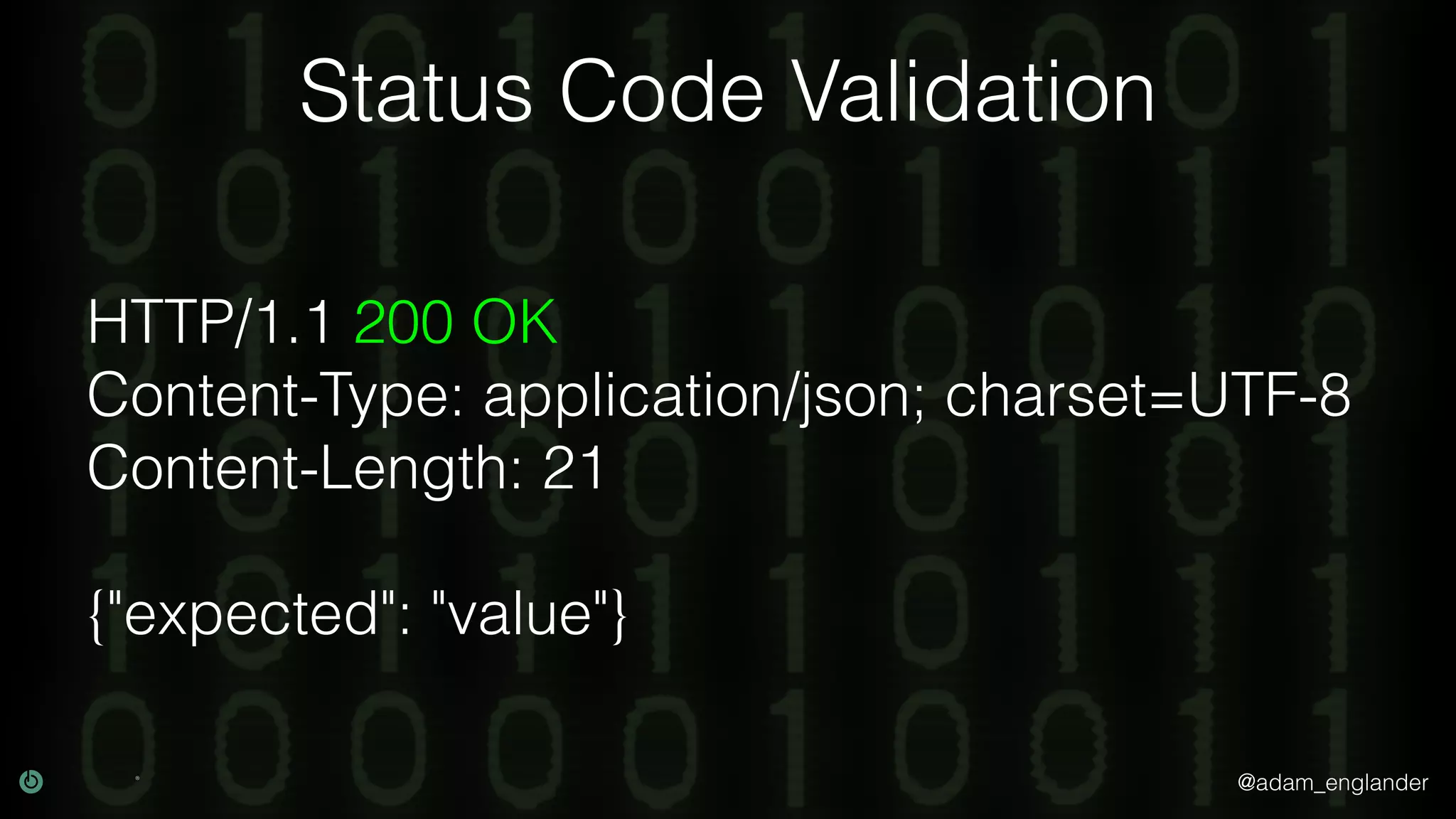
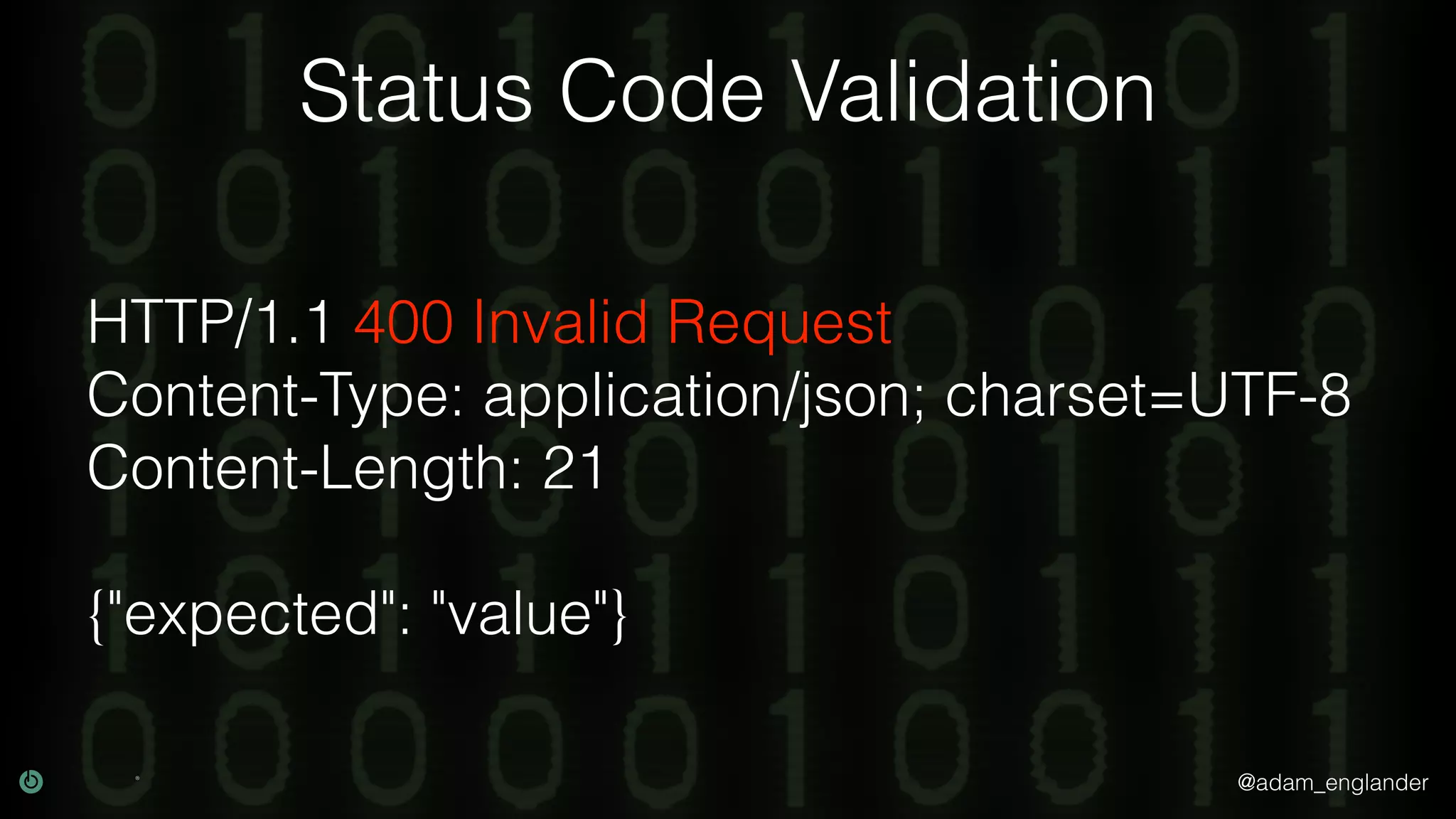
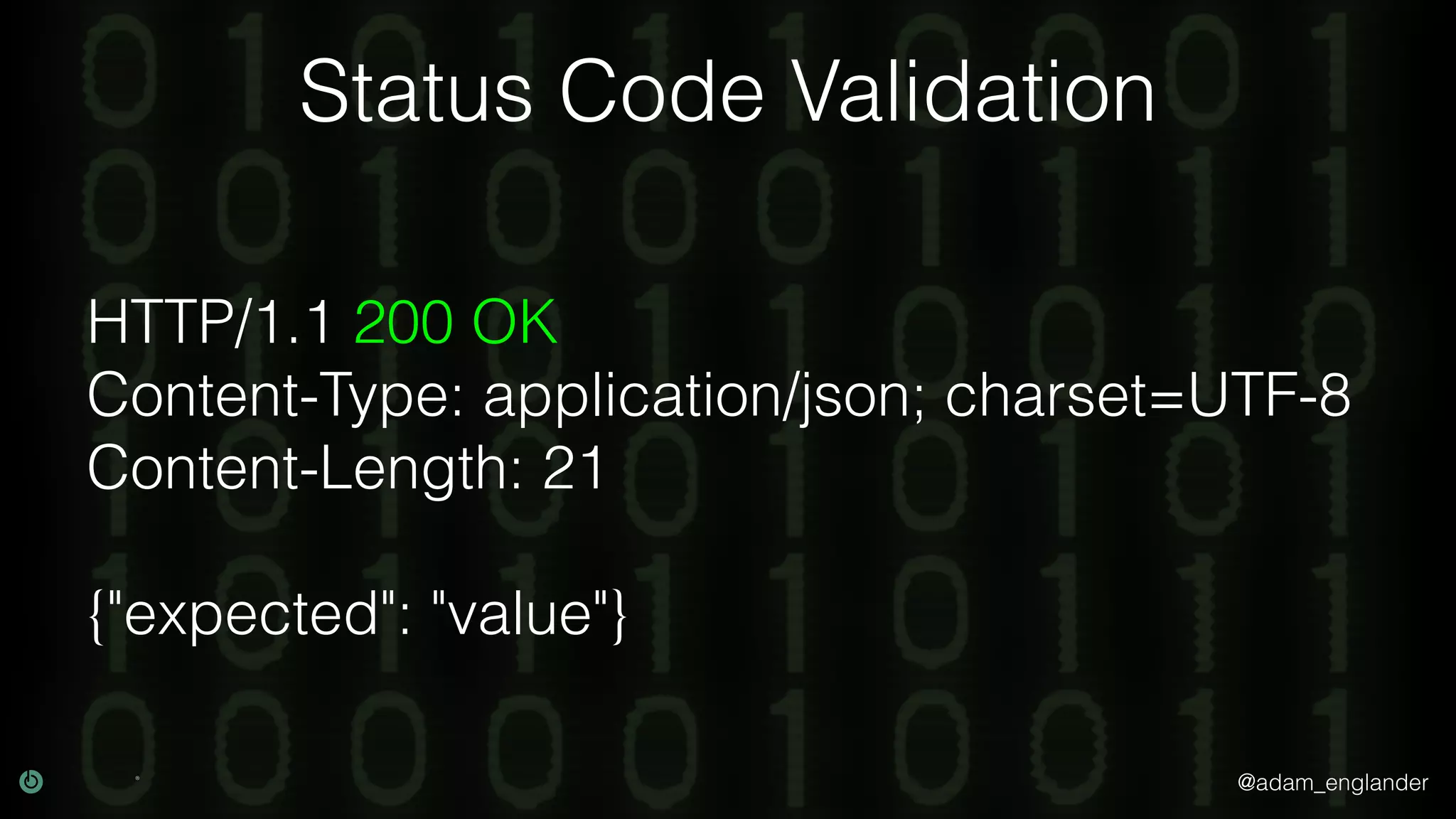
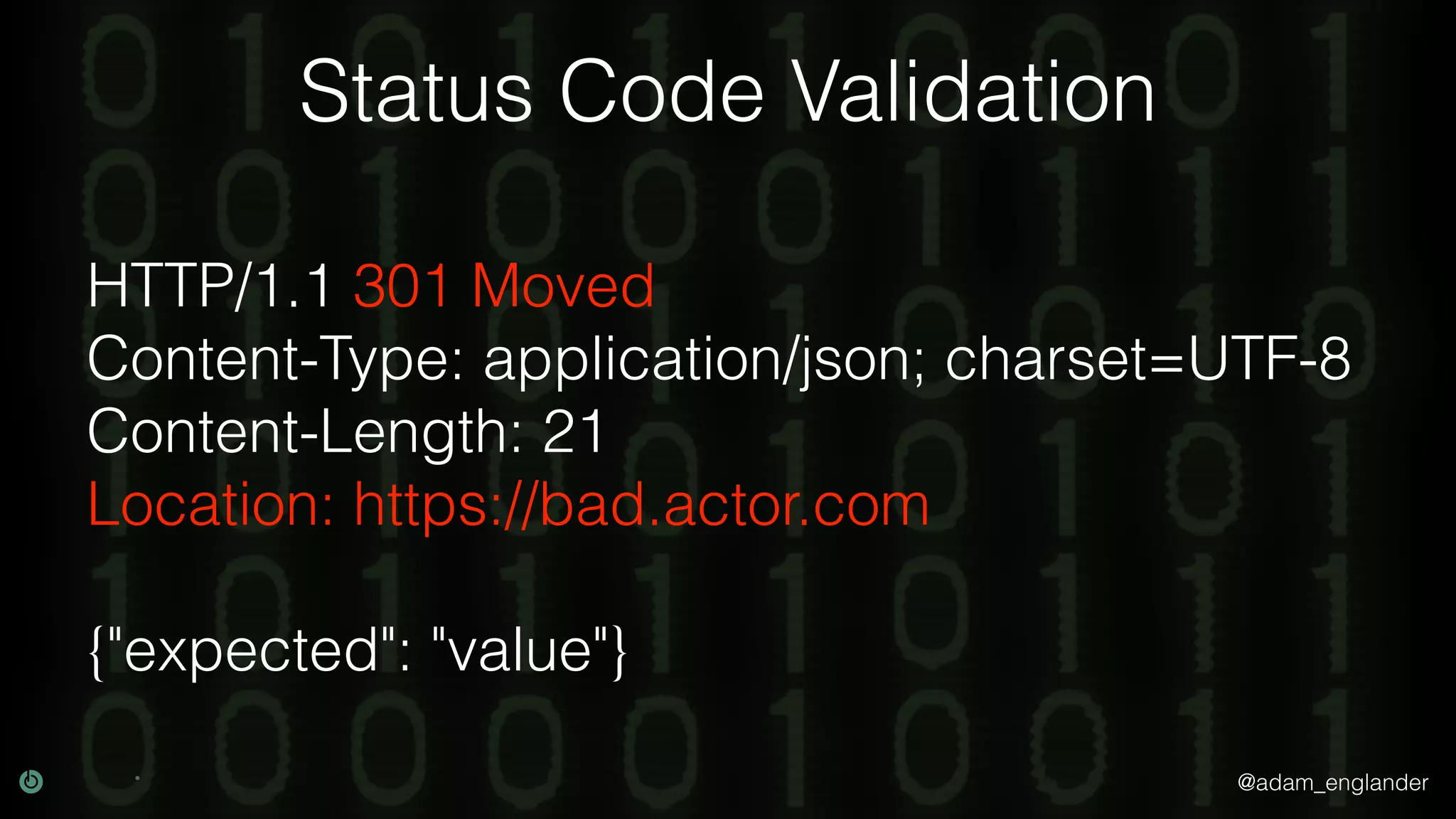
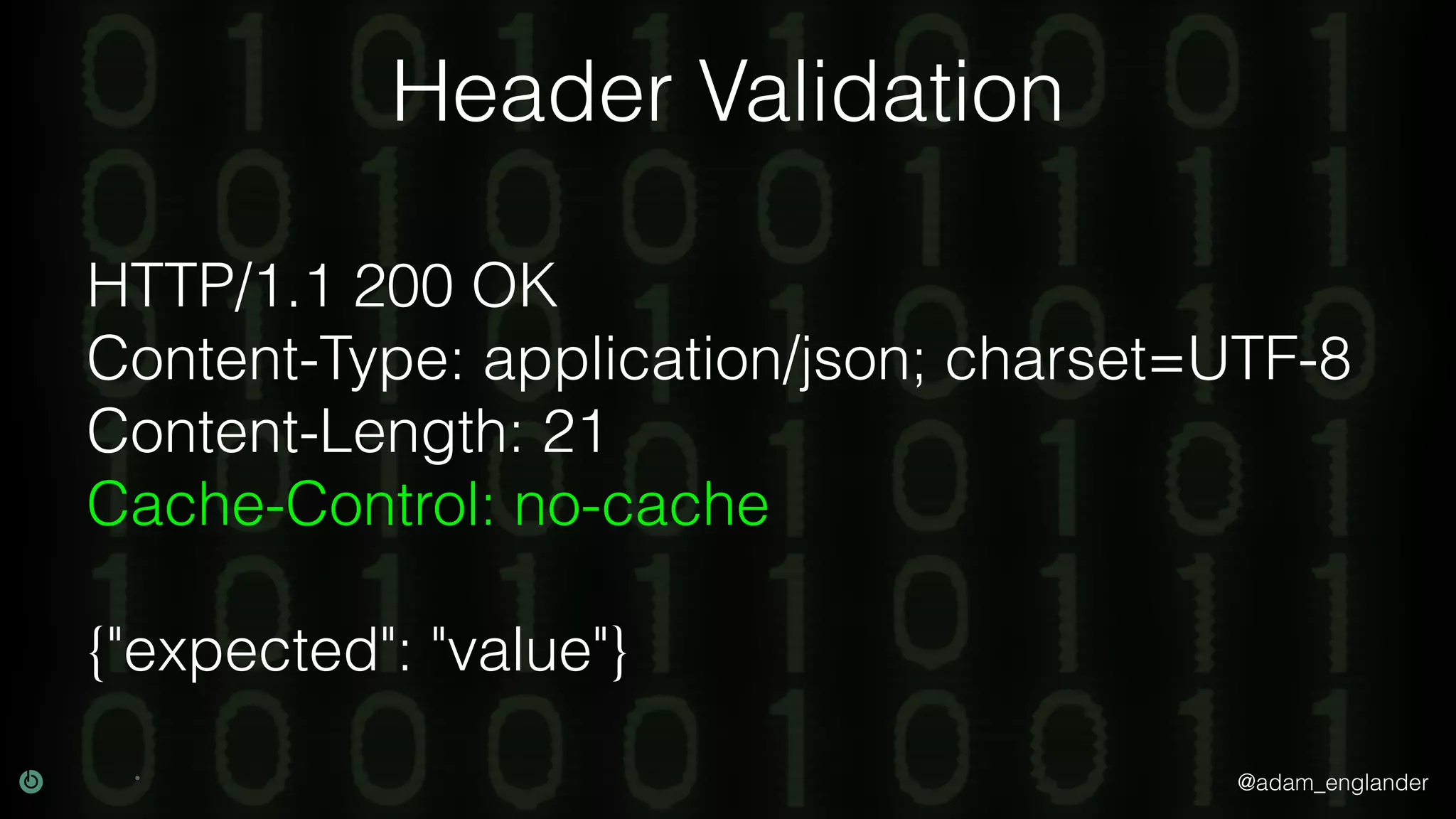
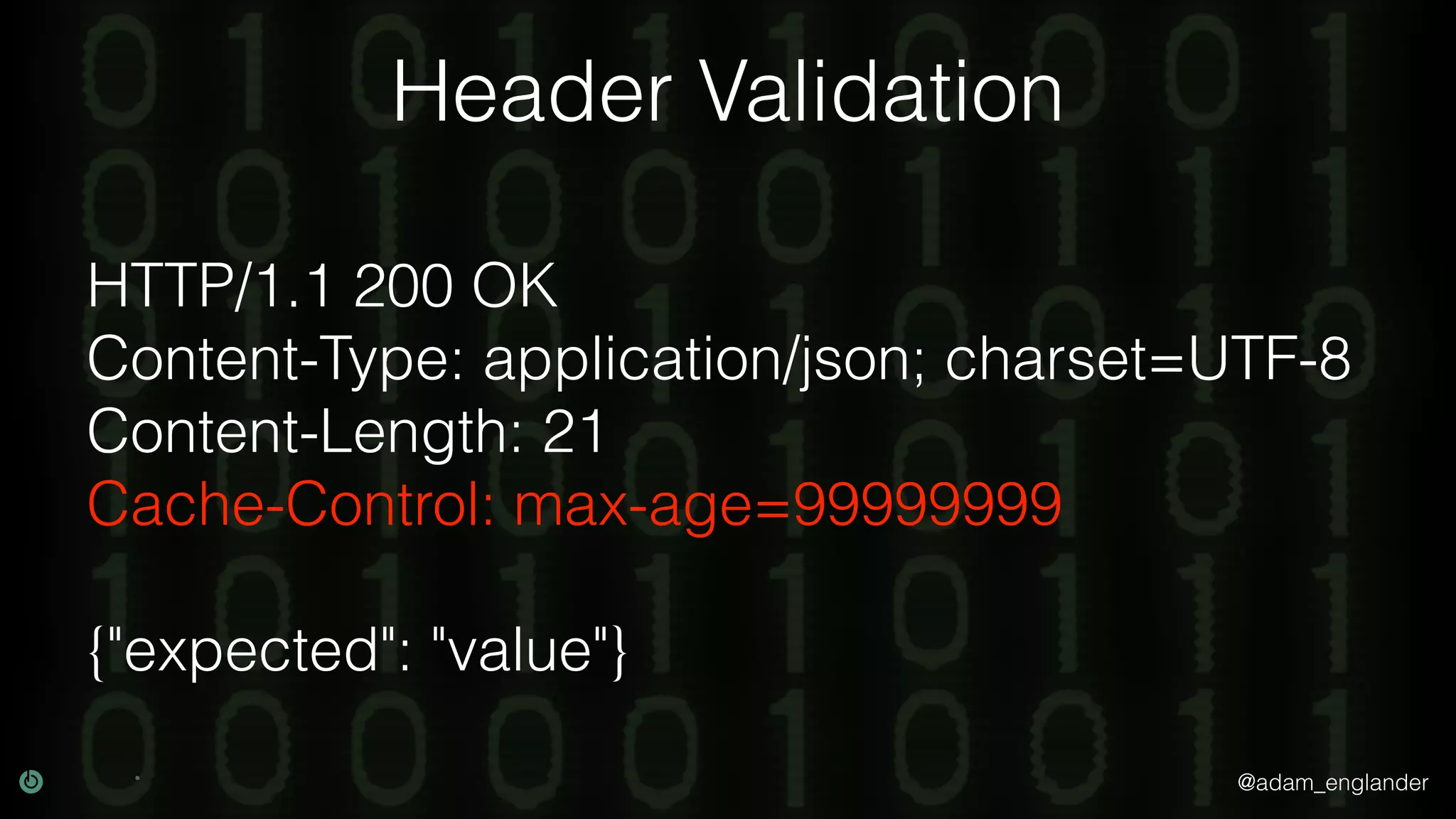
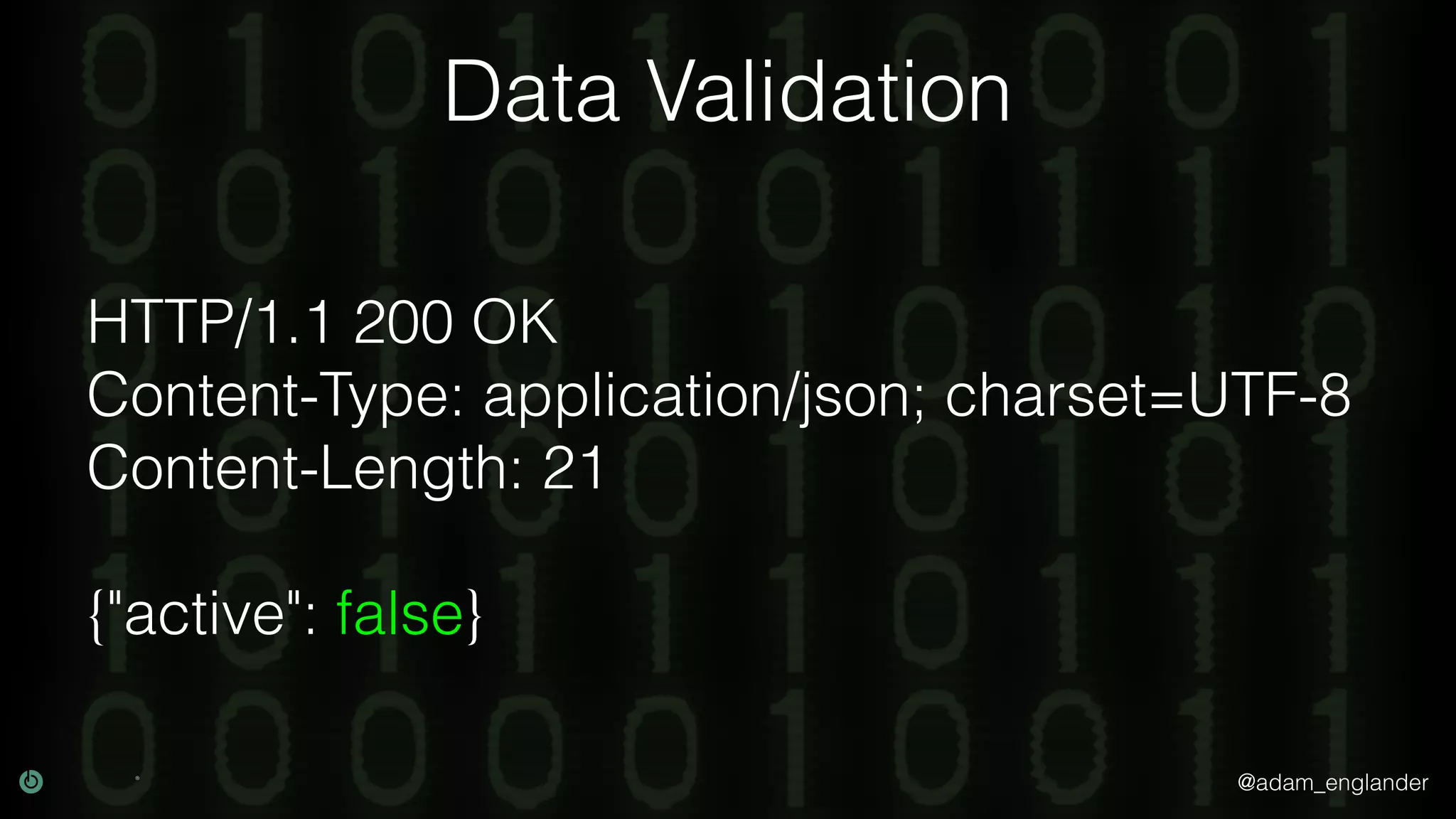
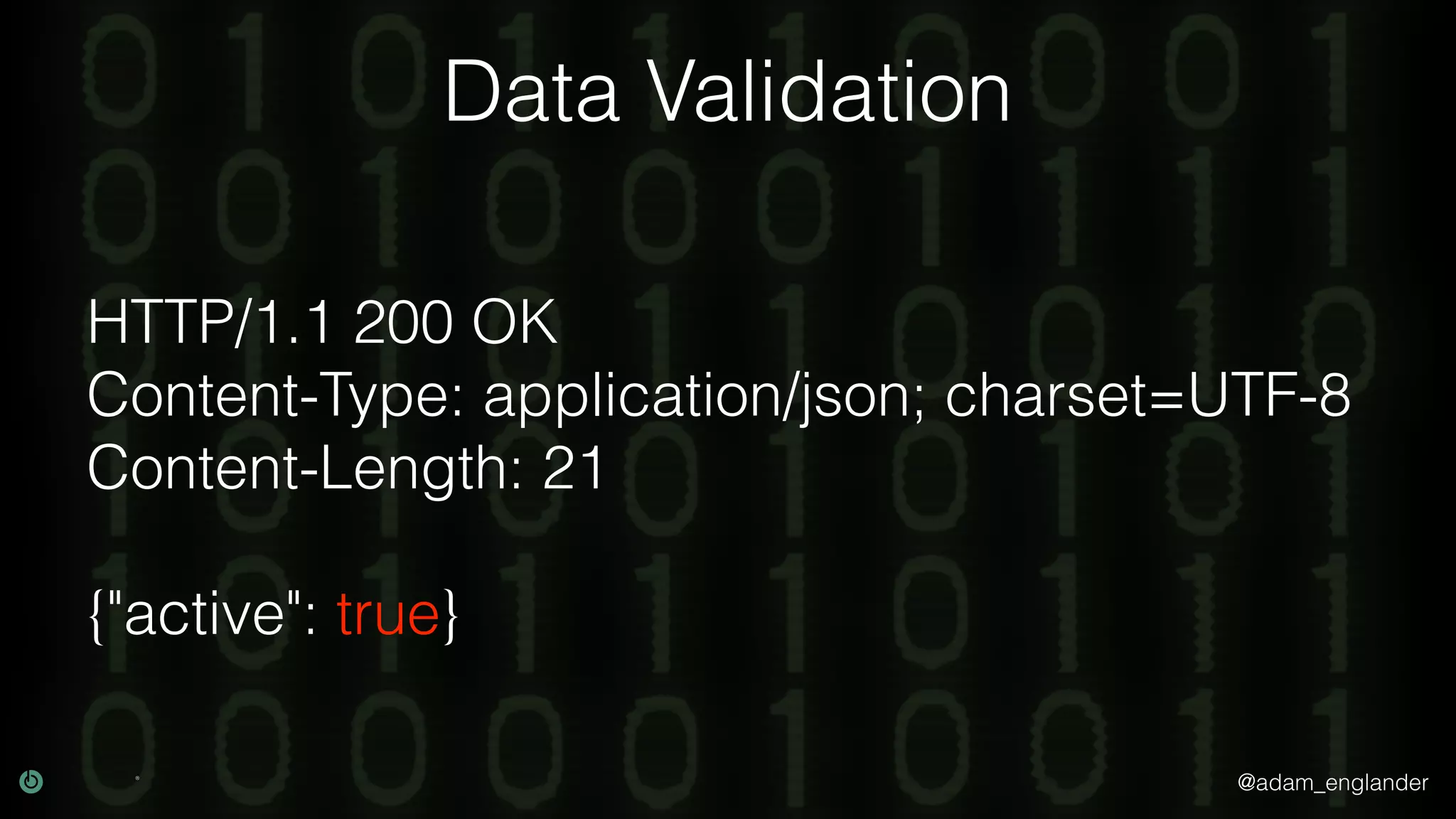
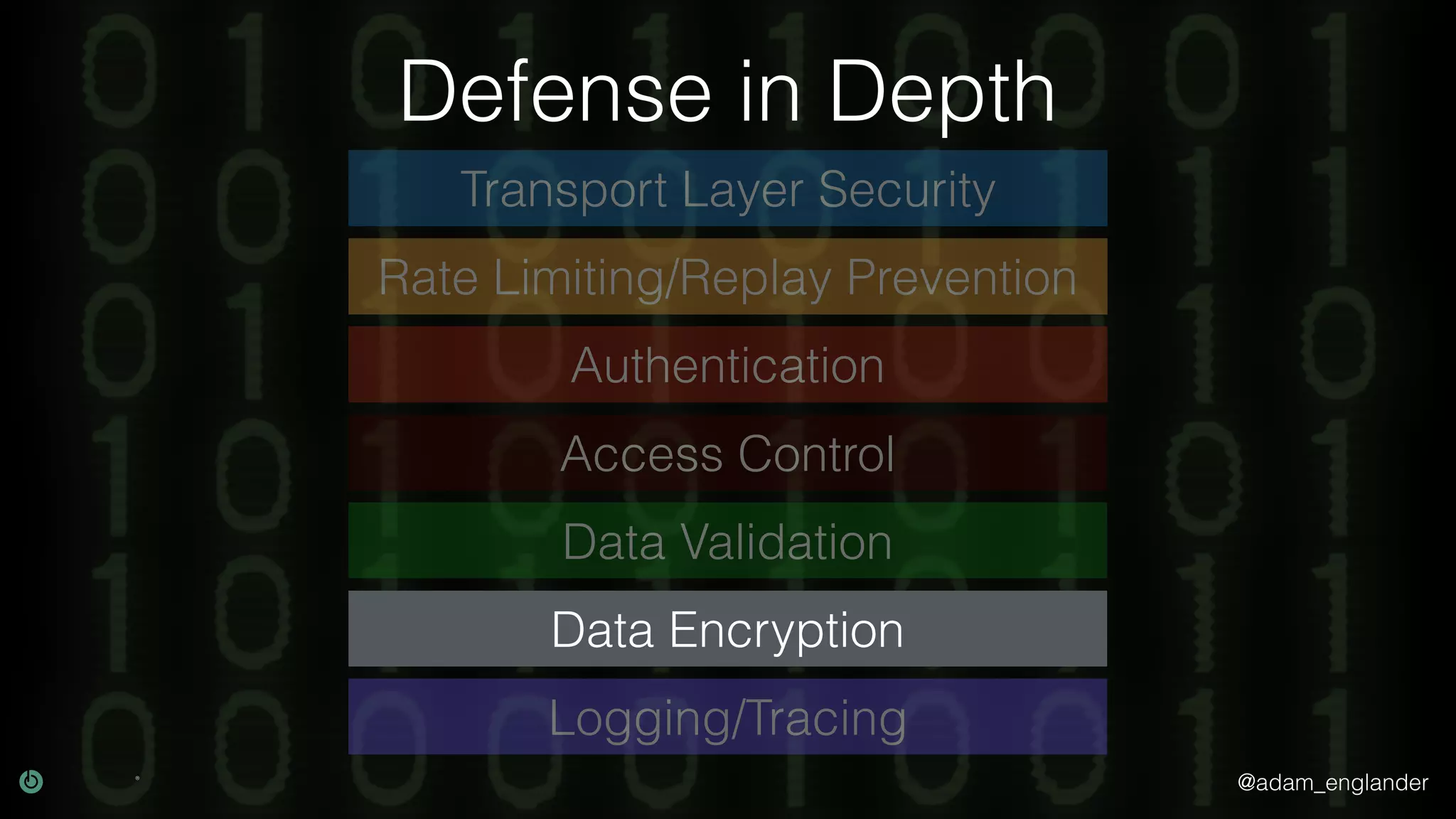
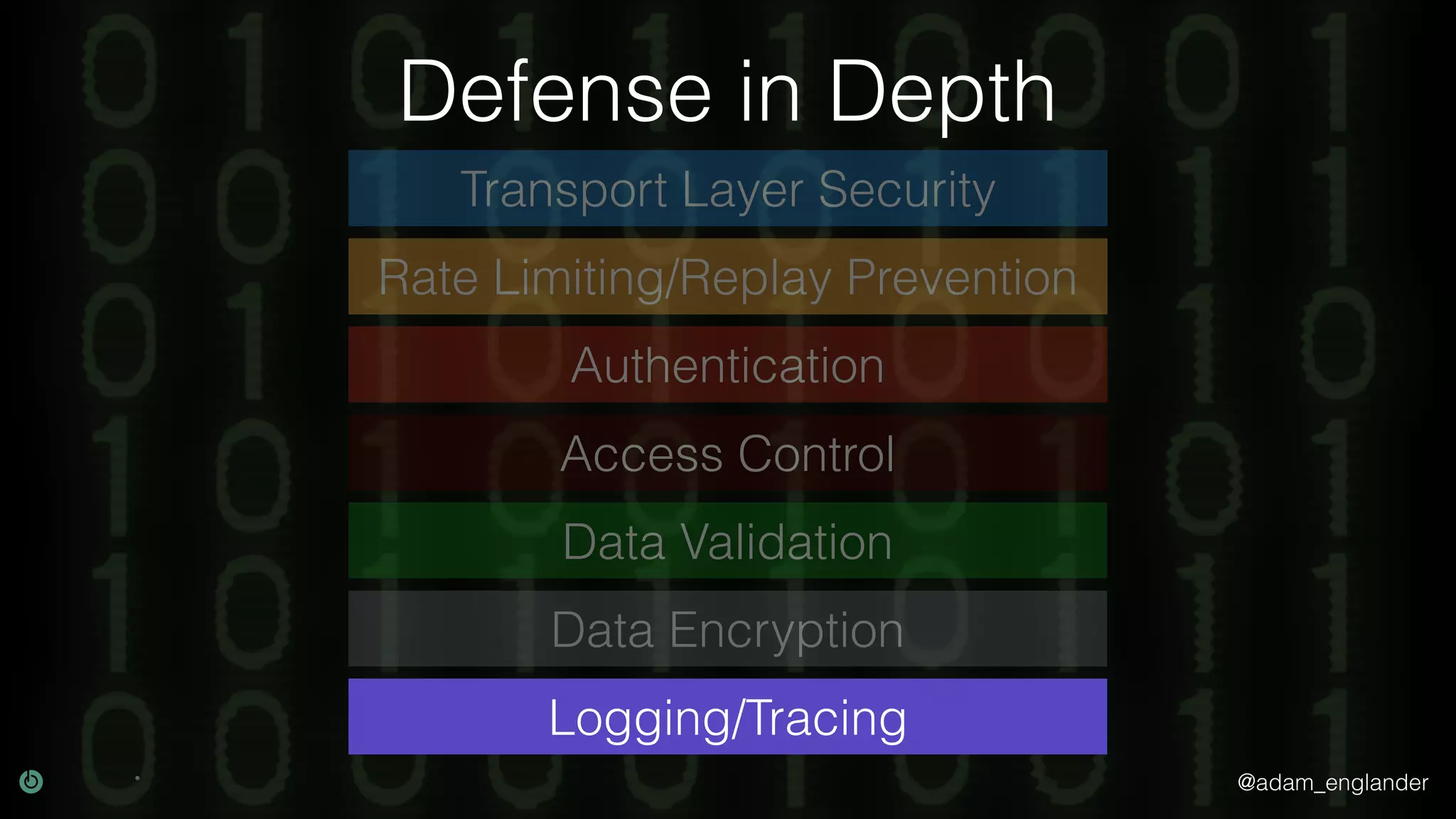
This document discusses various techniques for API security including defense in depth with layers like transport layer security, rate limiting, authentication, data validation, encryption, logging and access control. It provides examples of implementing replay prevention using nonces, rate limiting using caching, authentication with JSON Web Tokens and encrypting data at rest and in transit. The importance of logging details about requests, responses and system state is also emphasized.