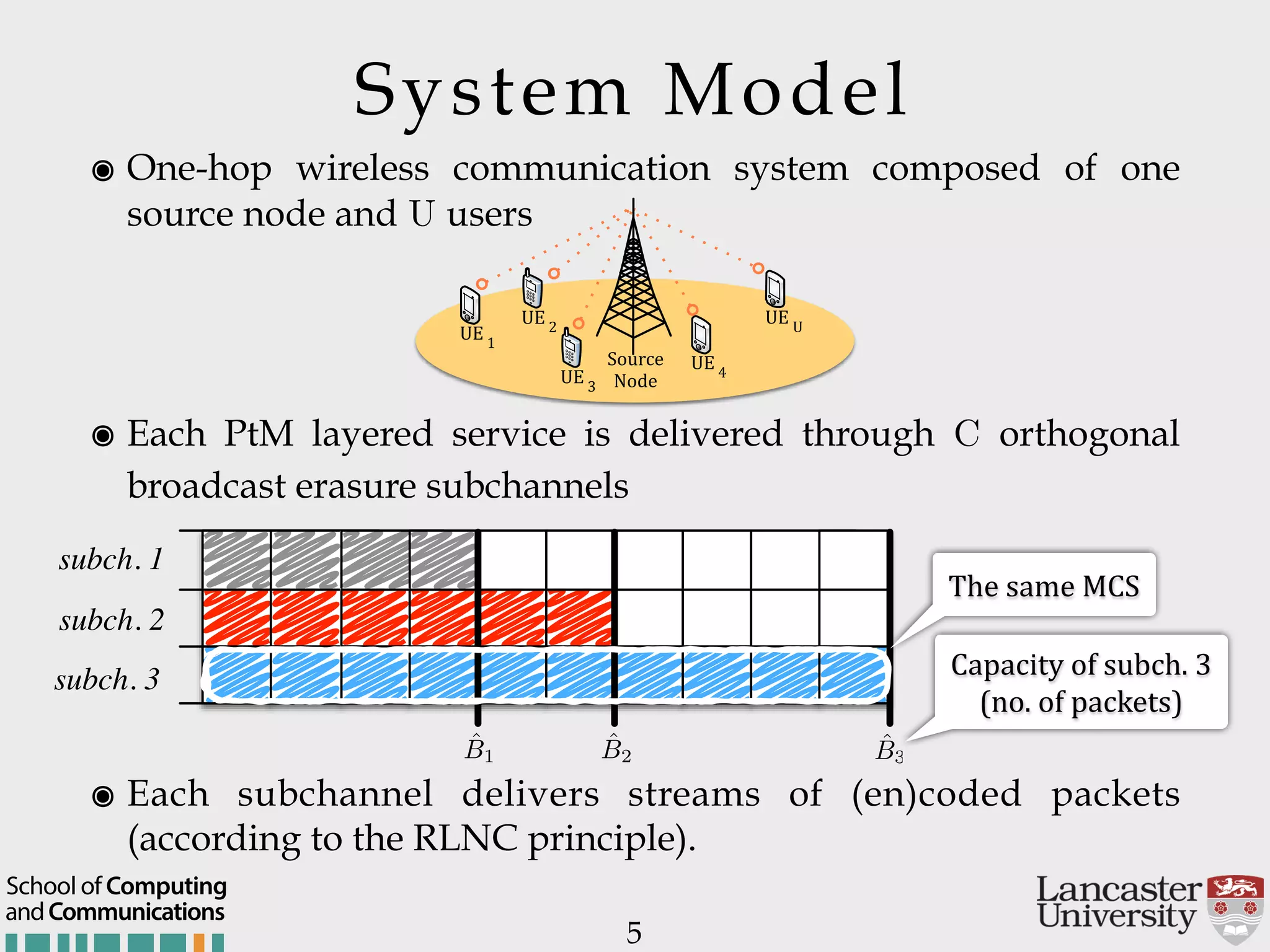
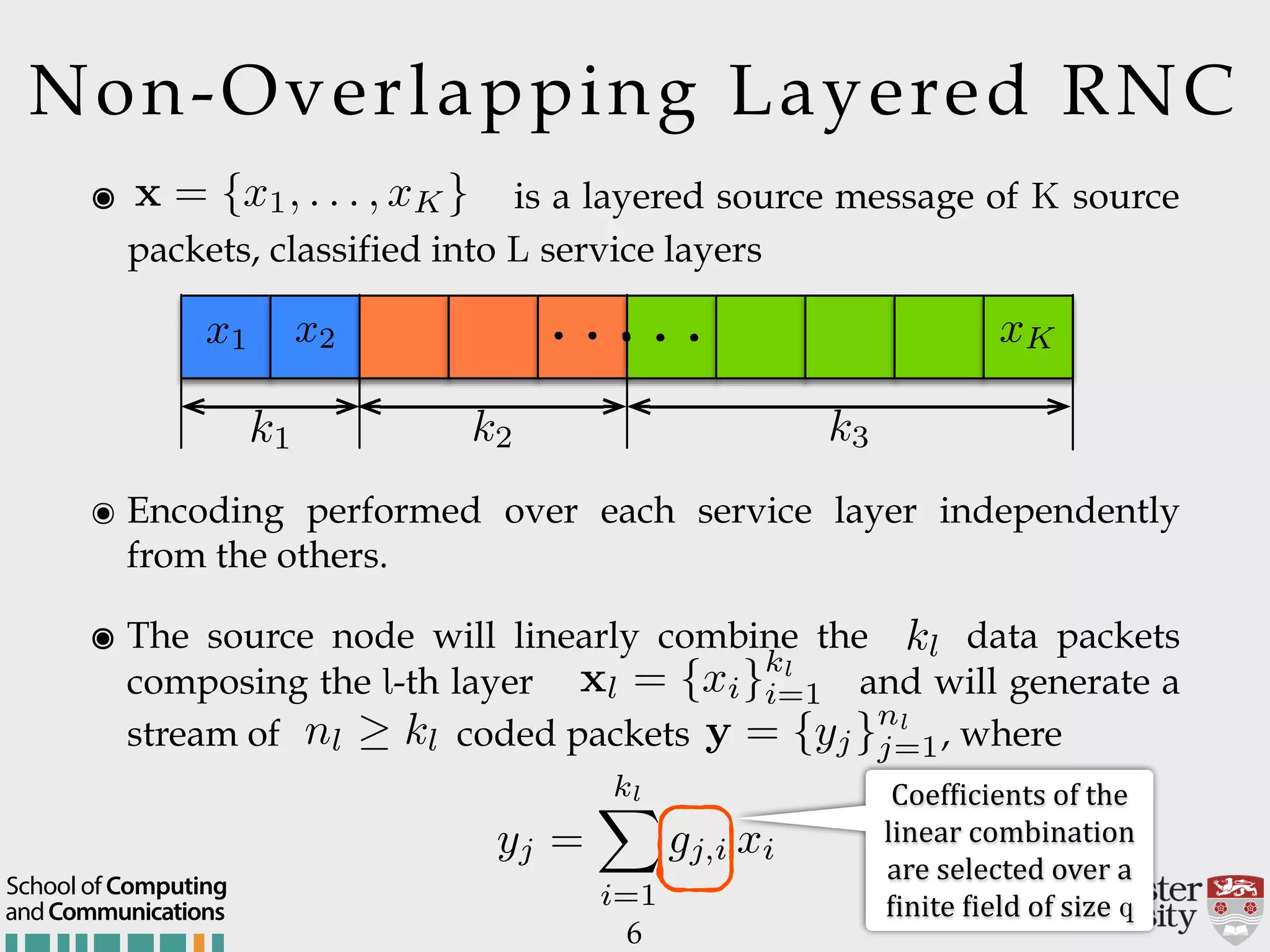
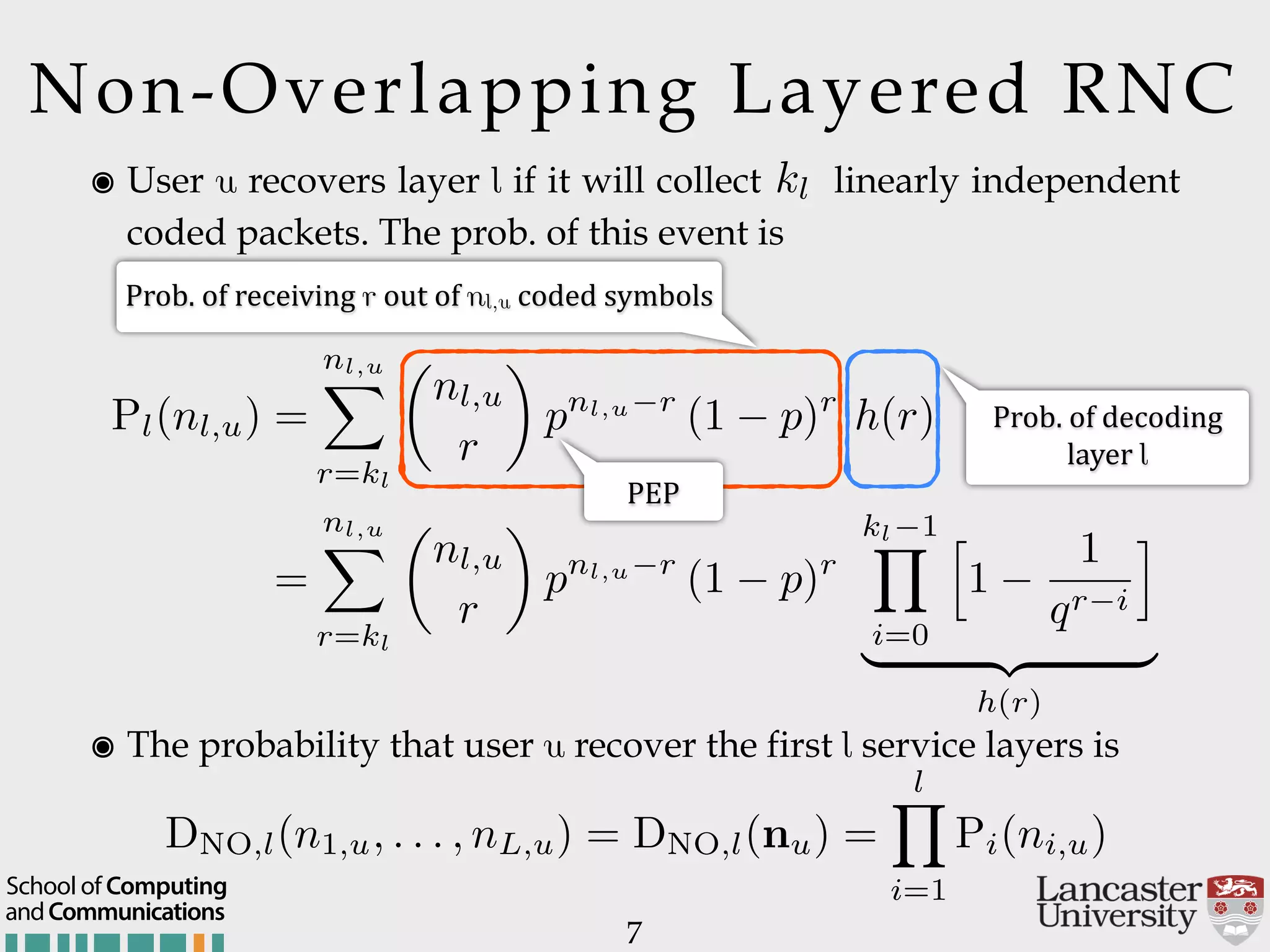
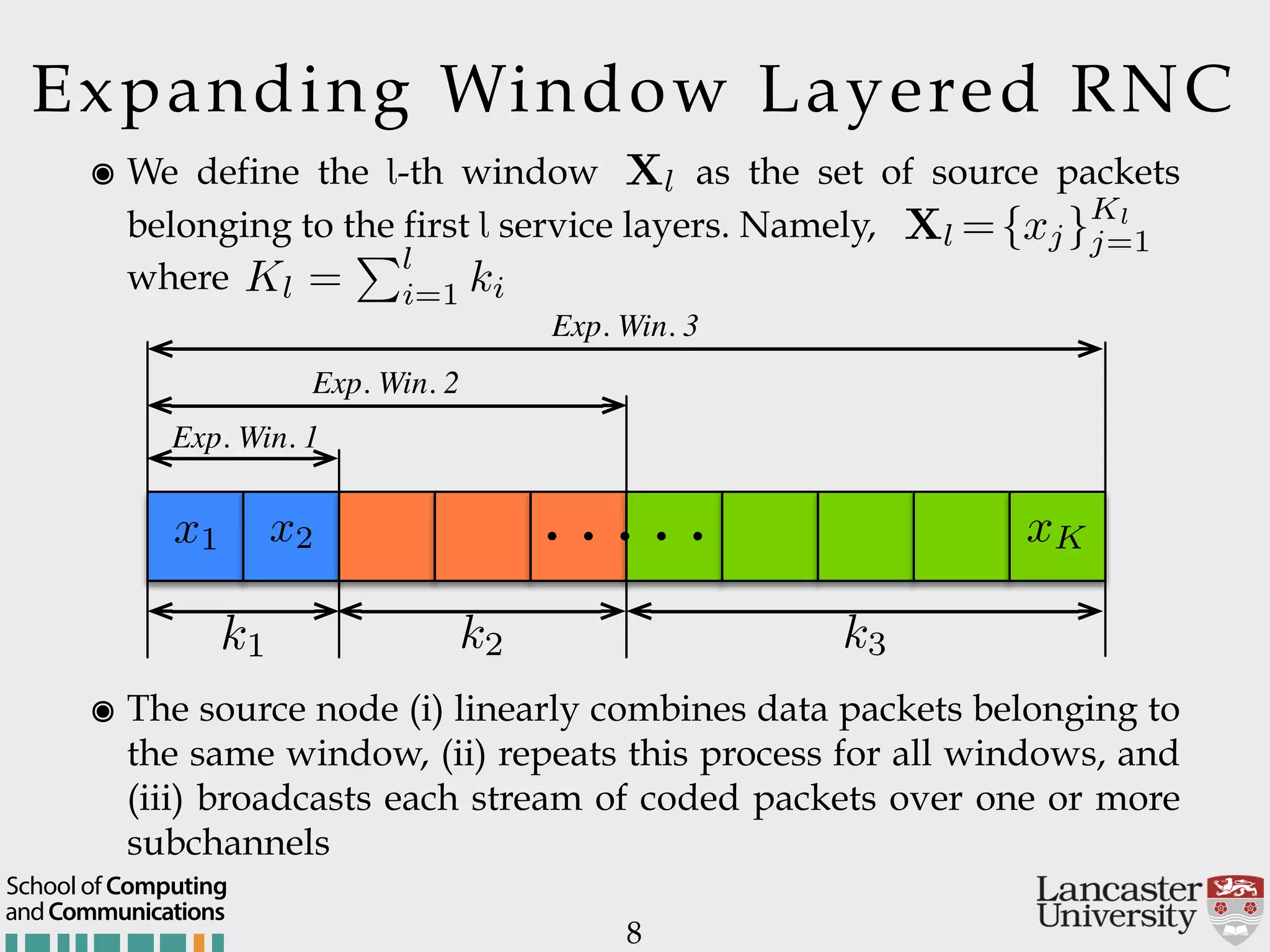
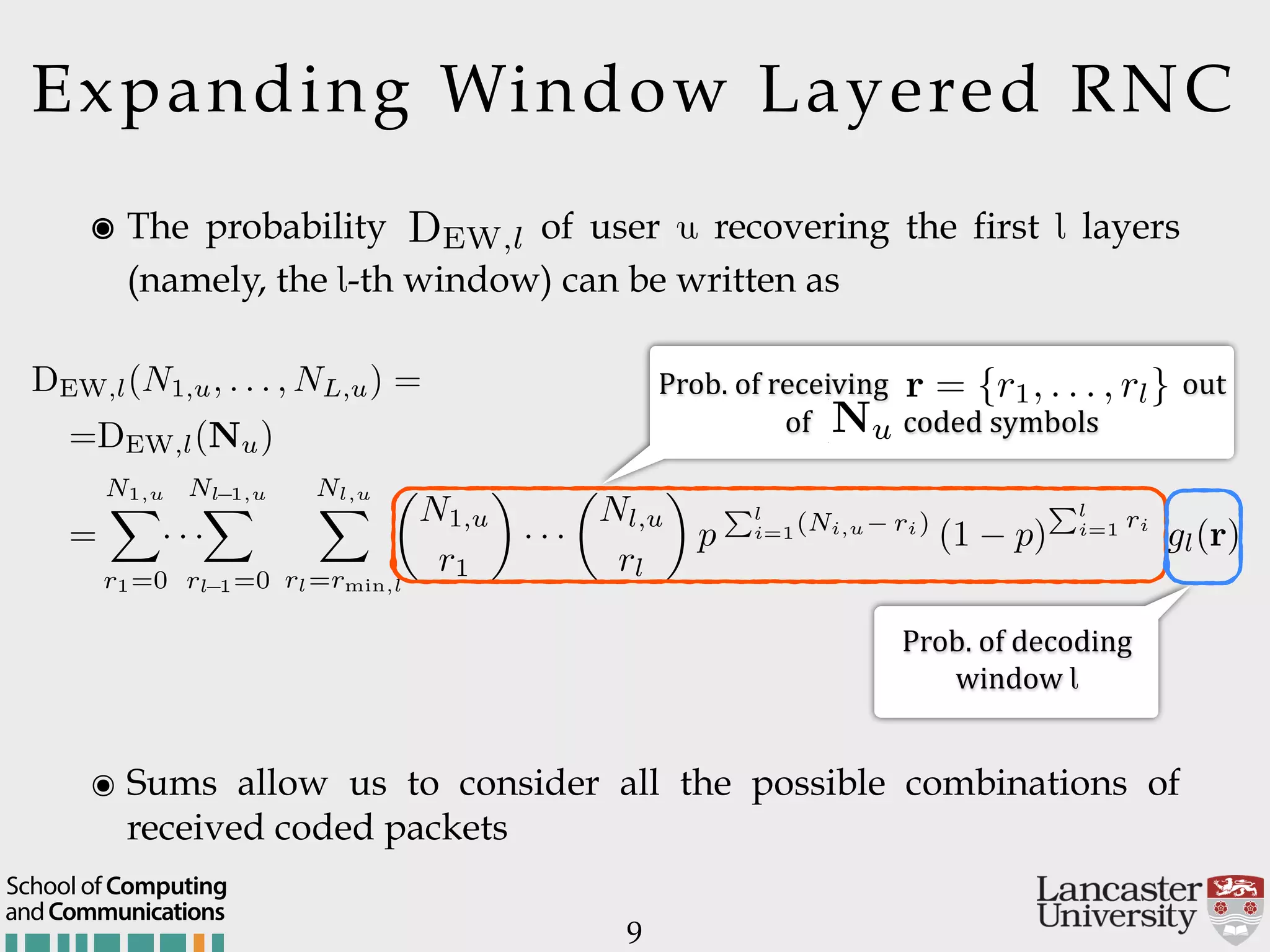
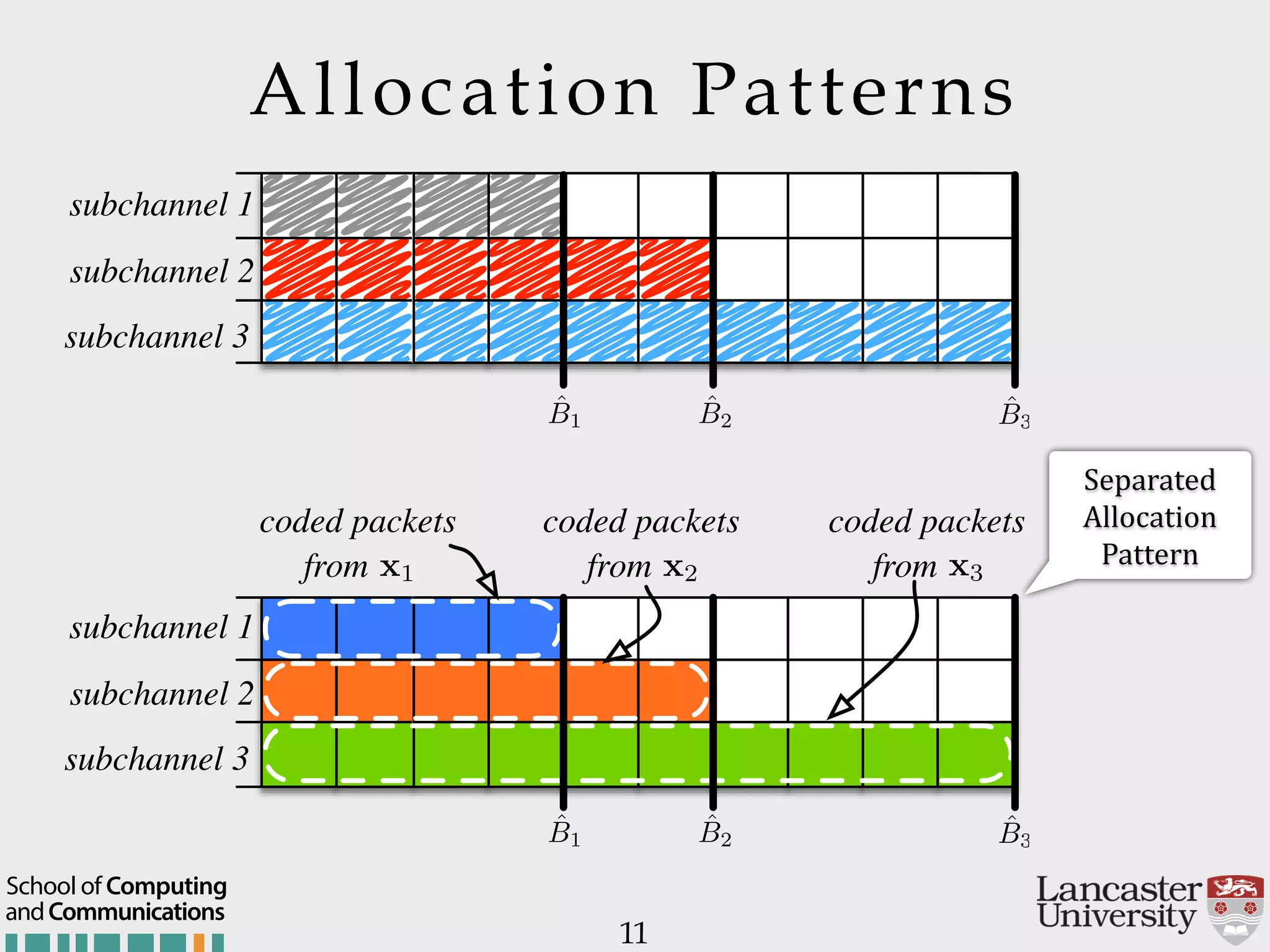
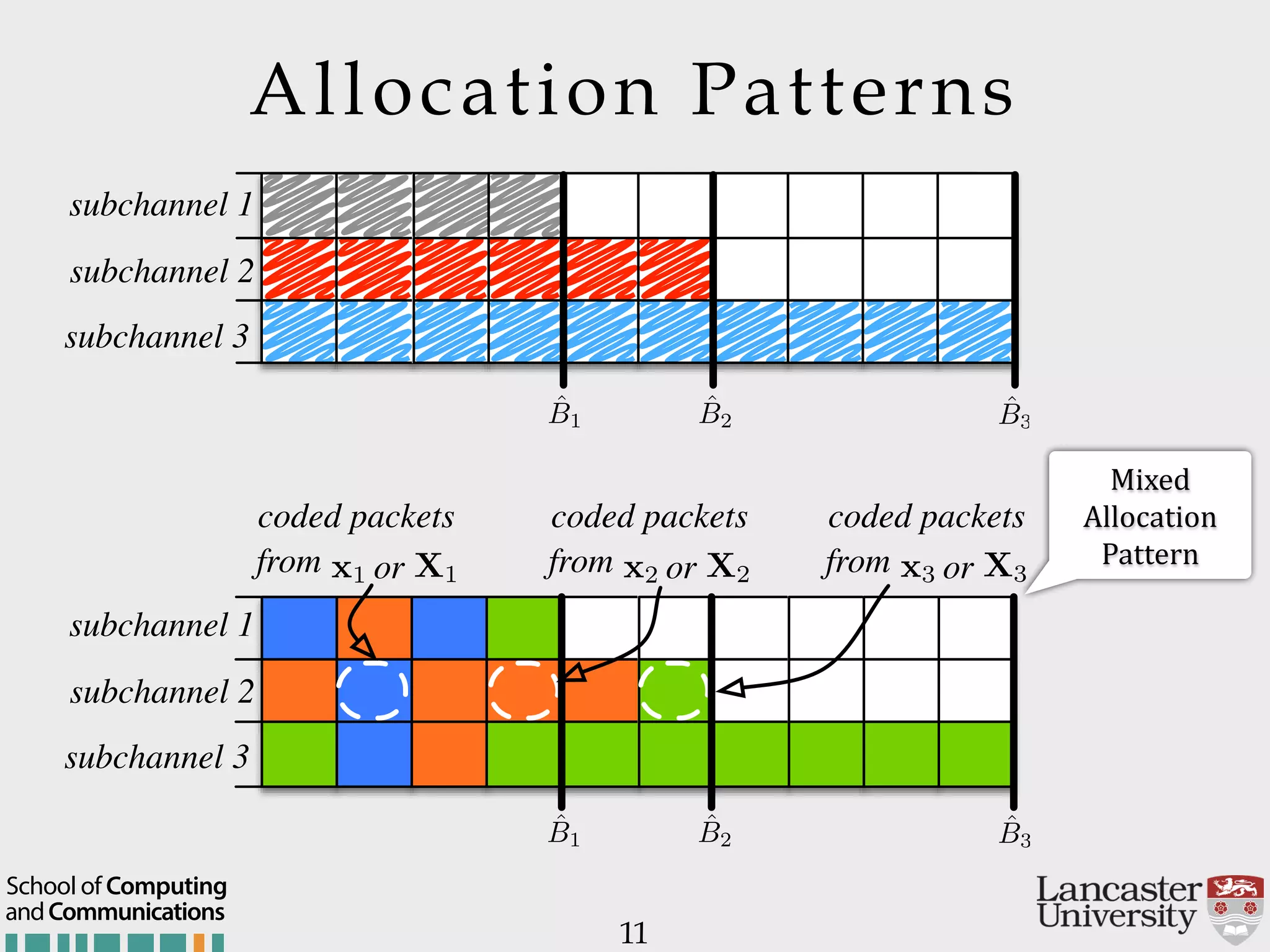
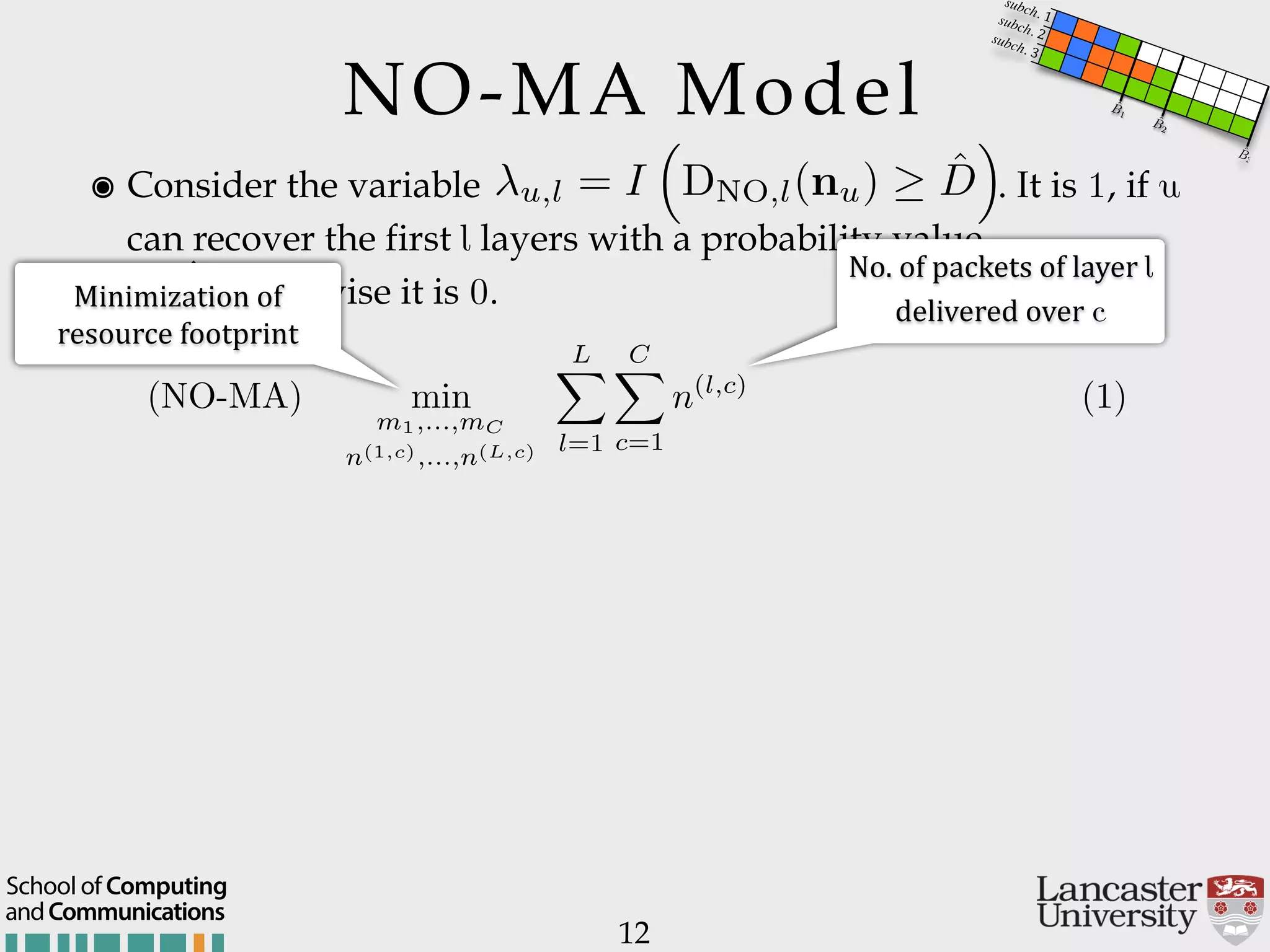
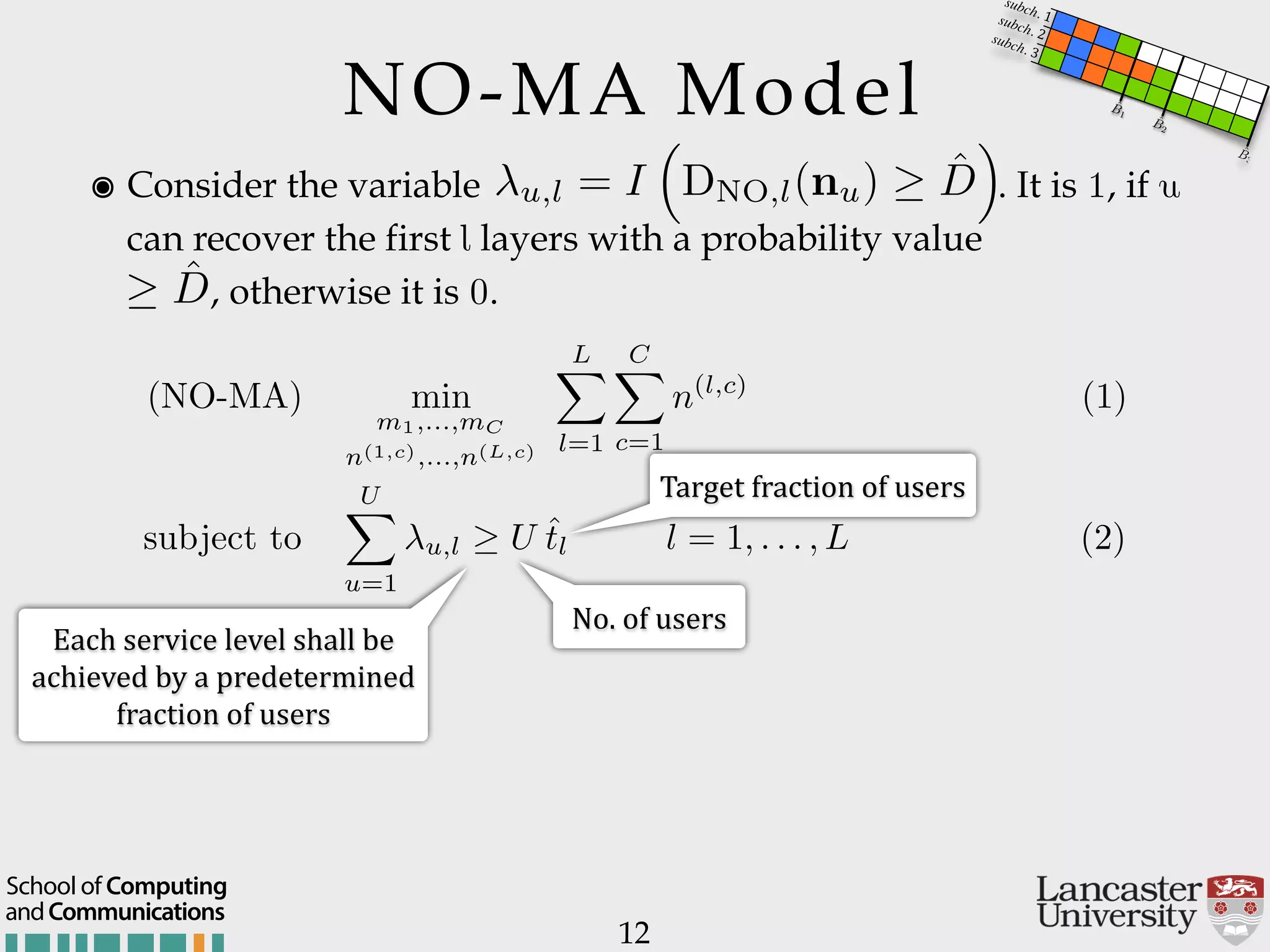
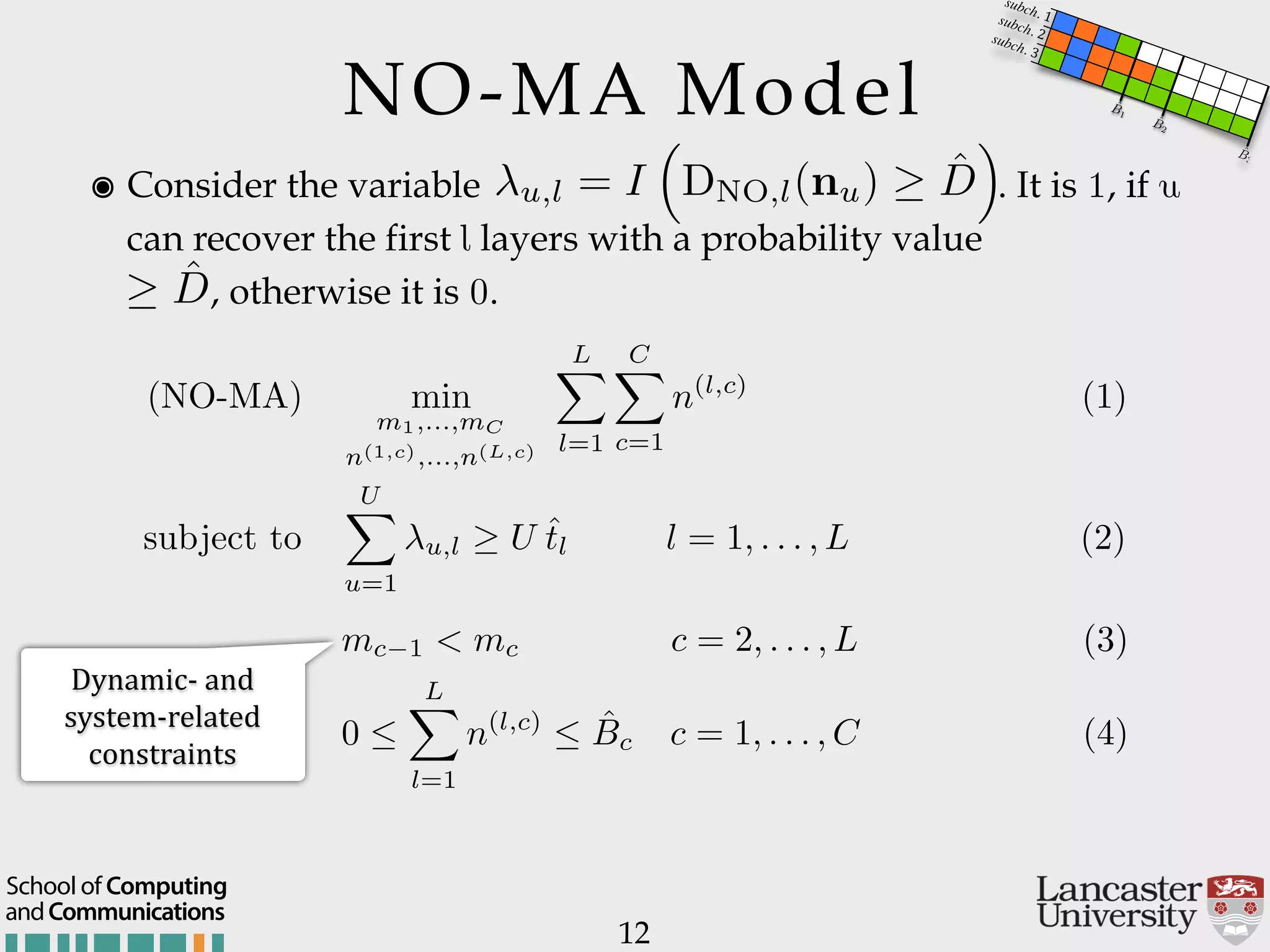
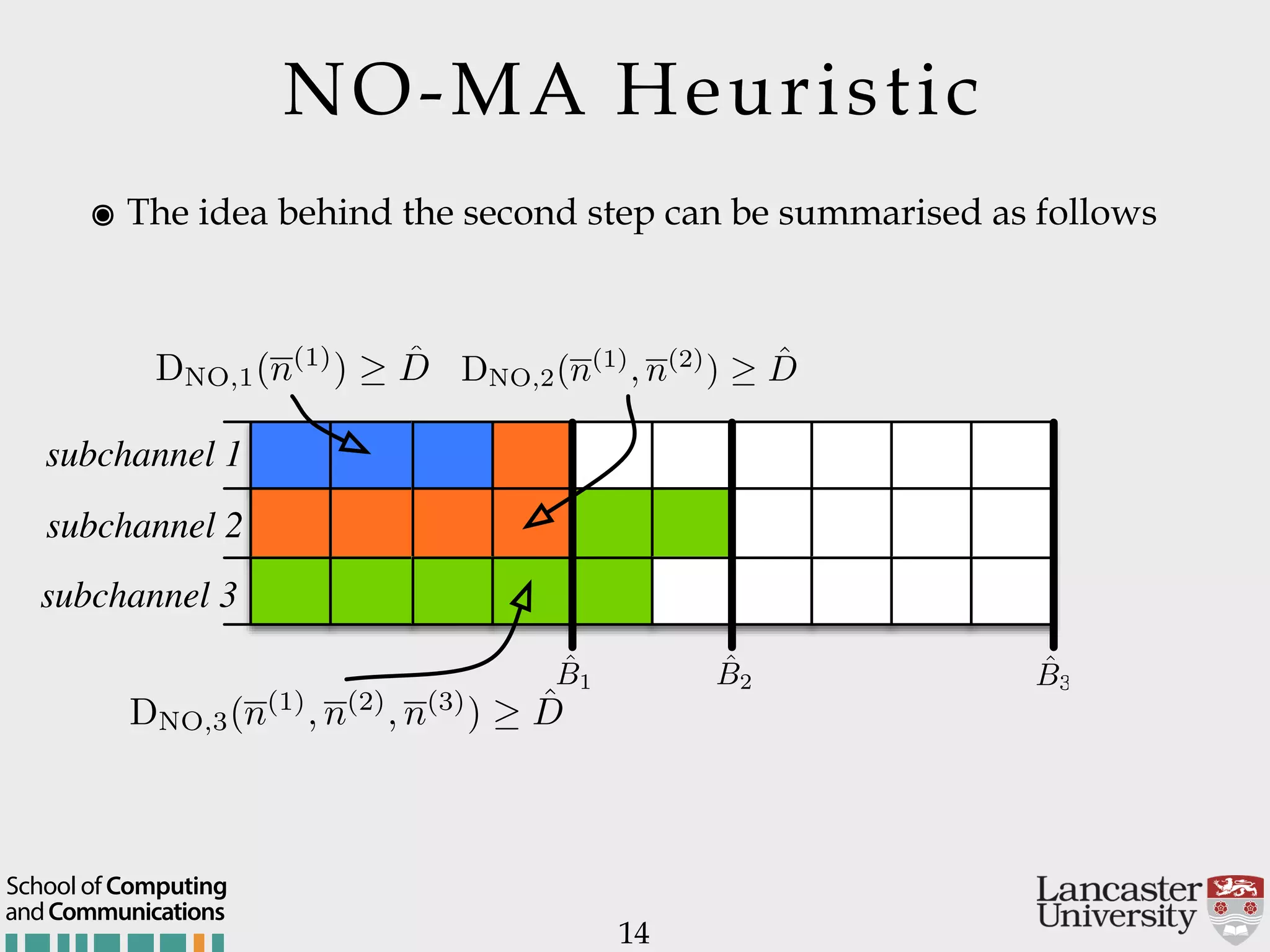
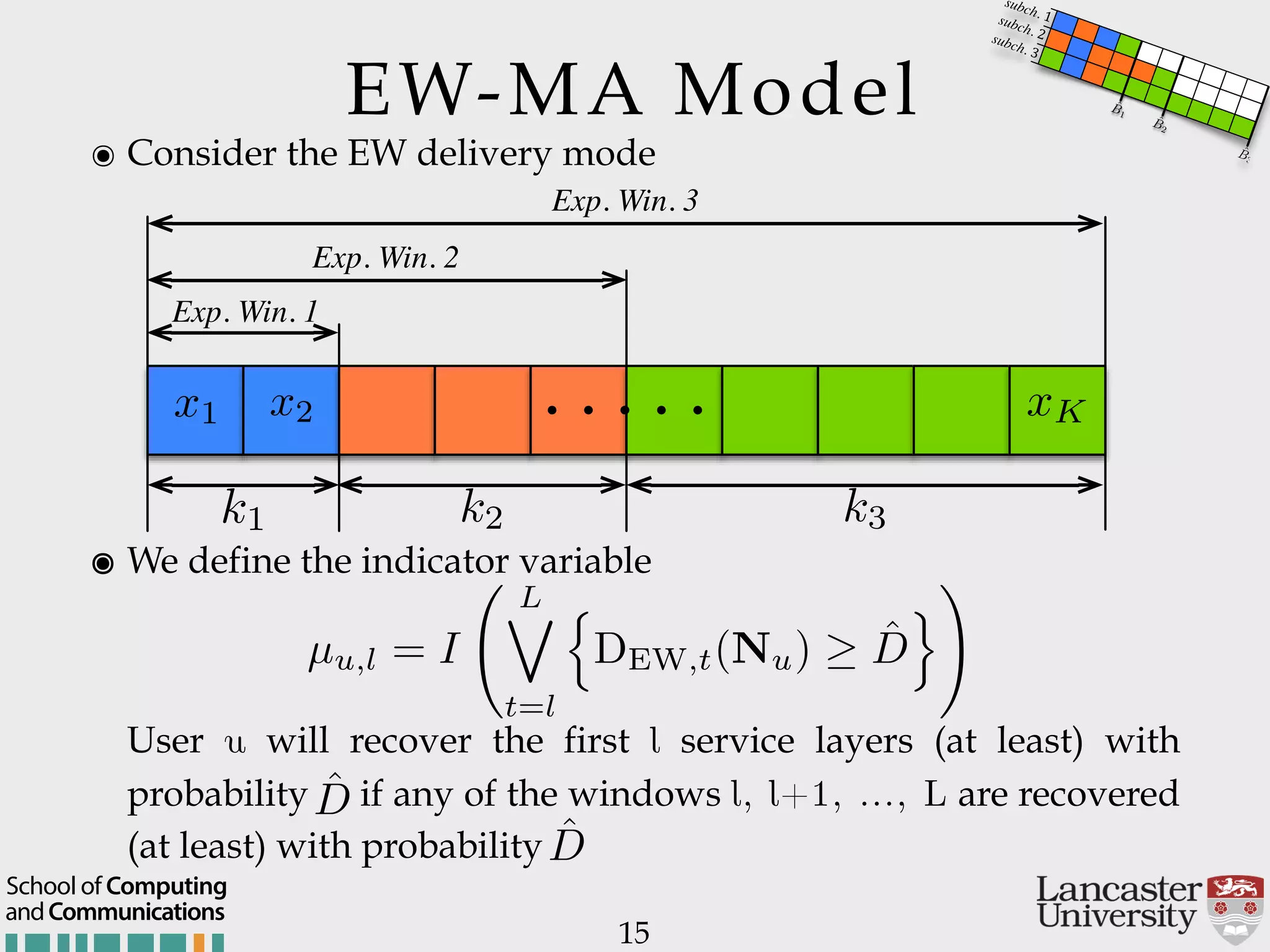
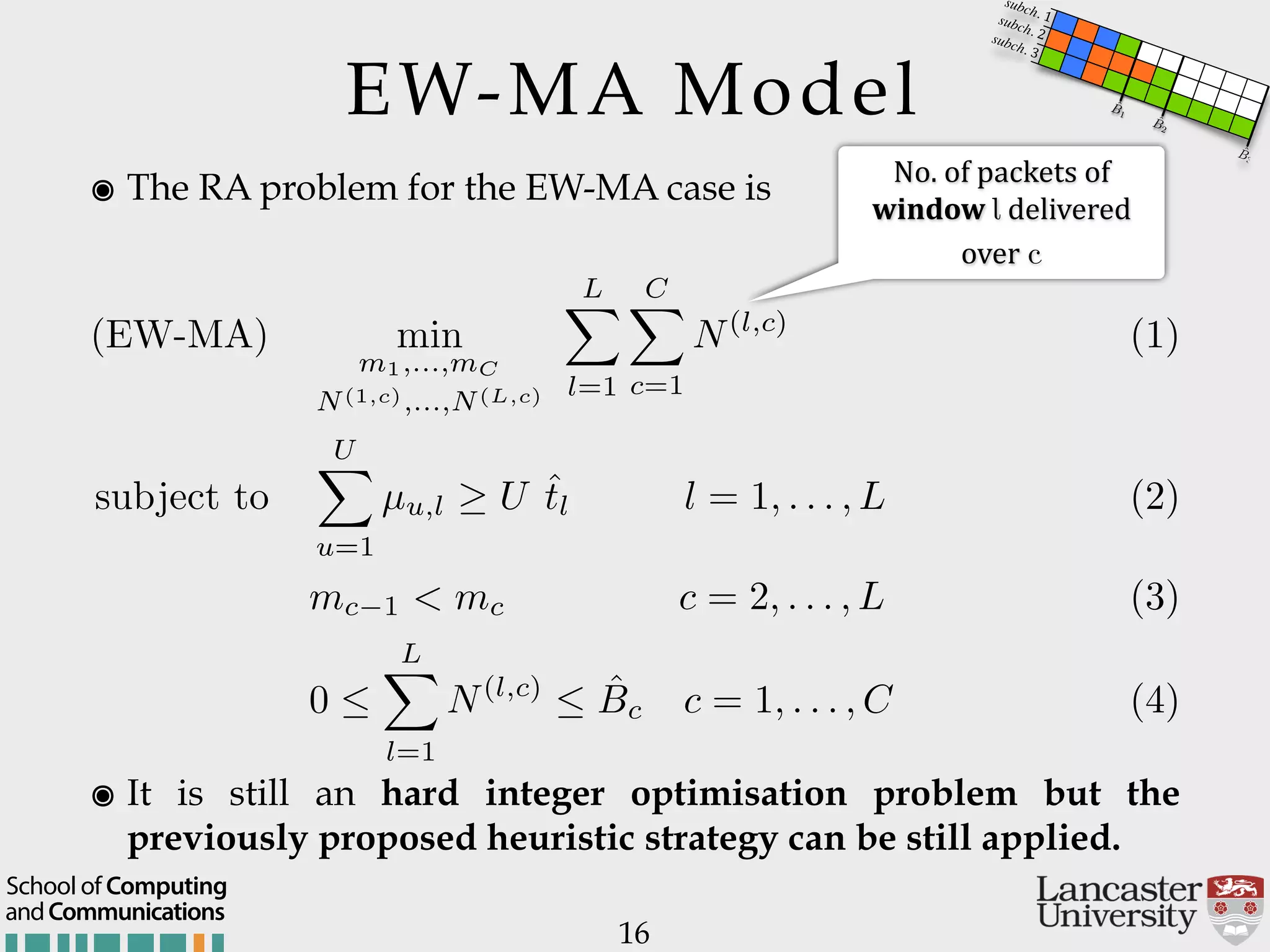
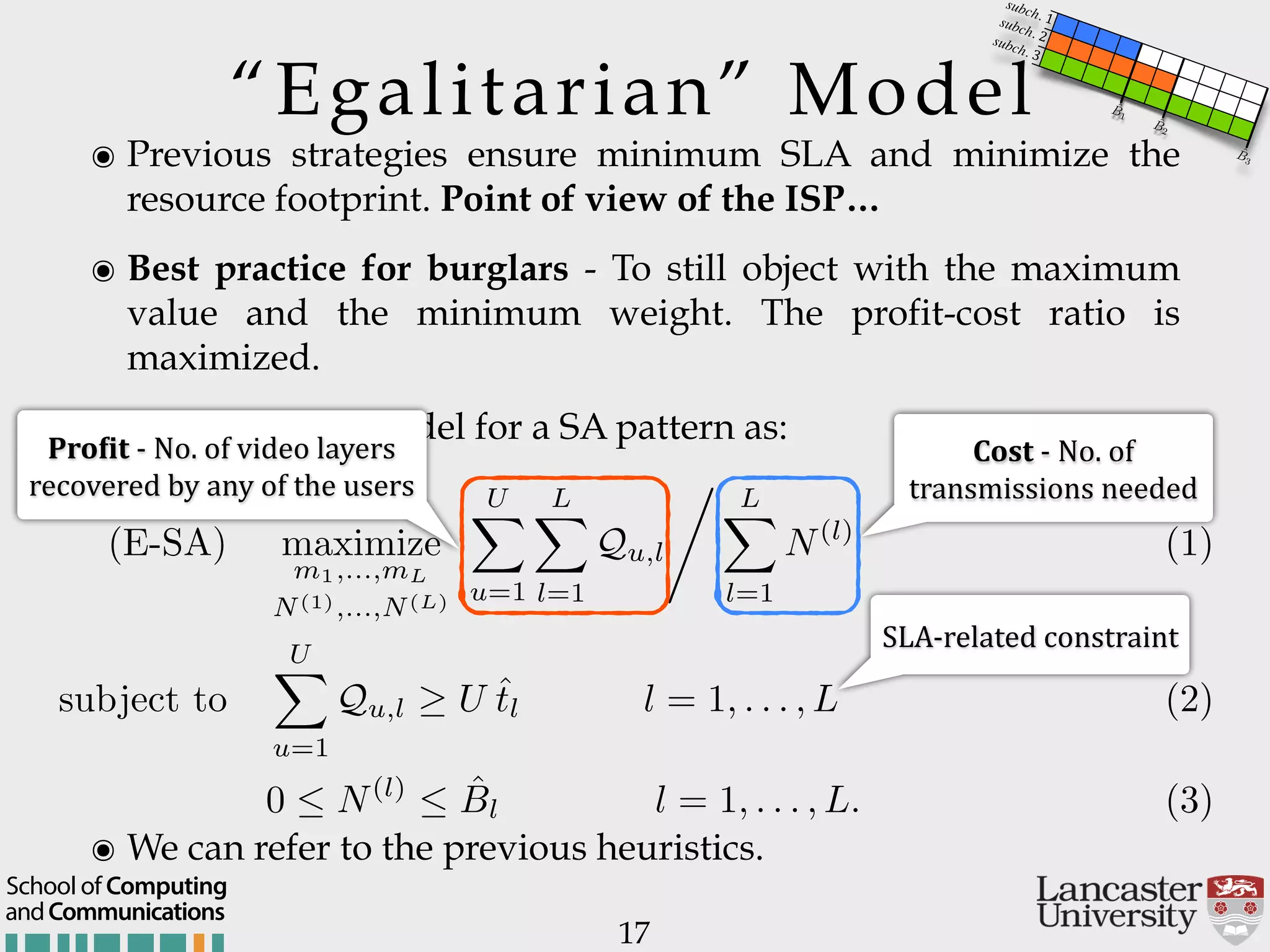
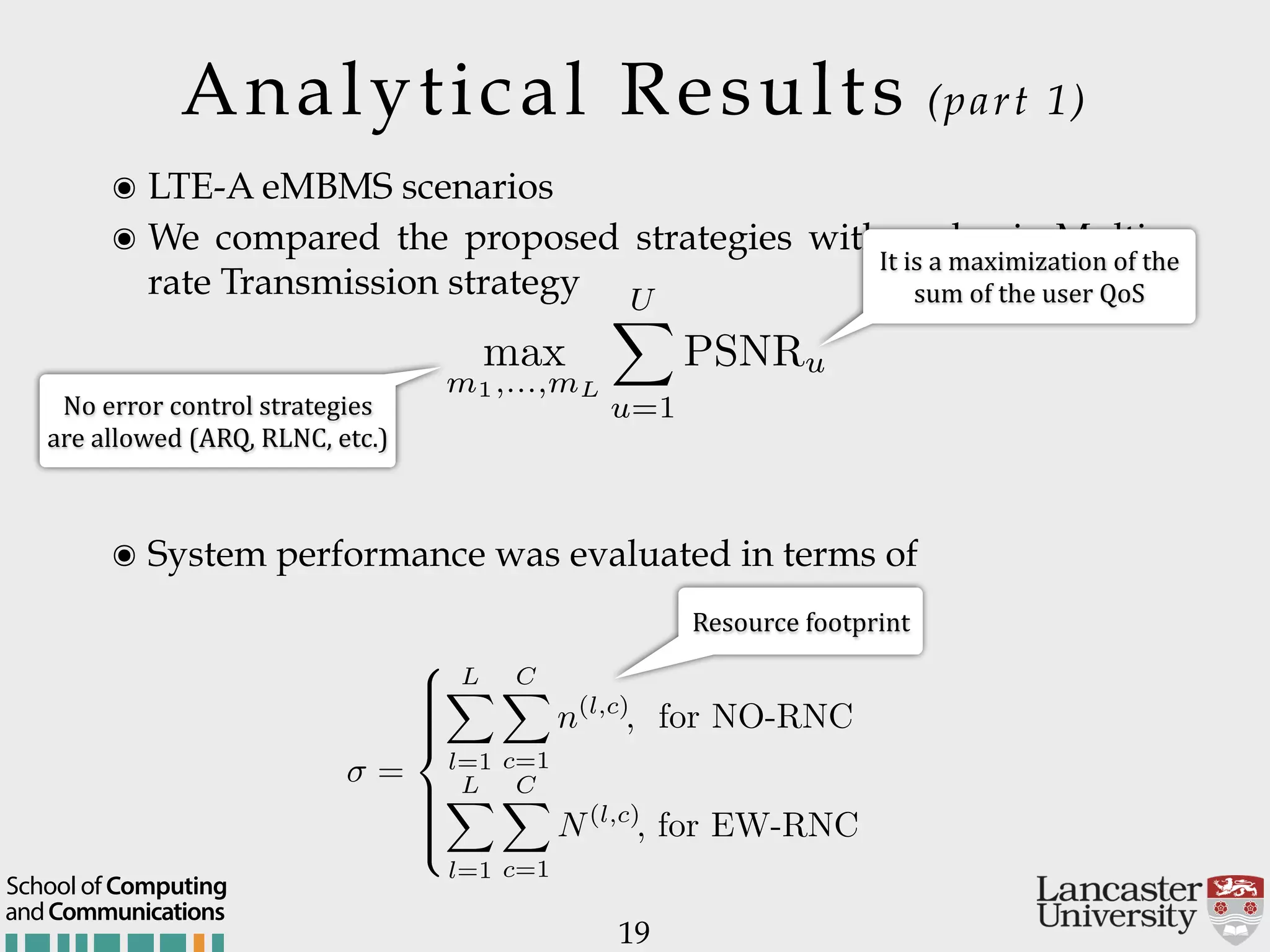
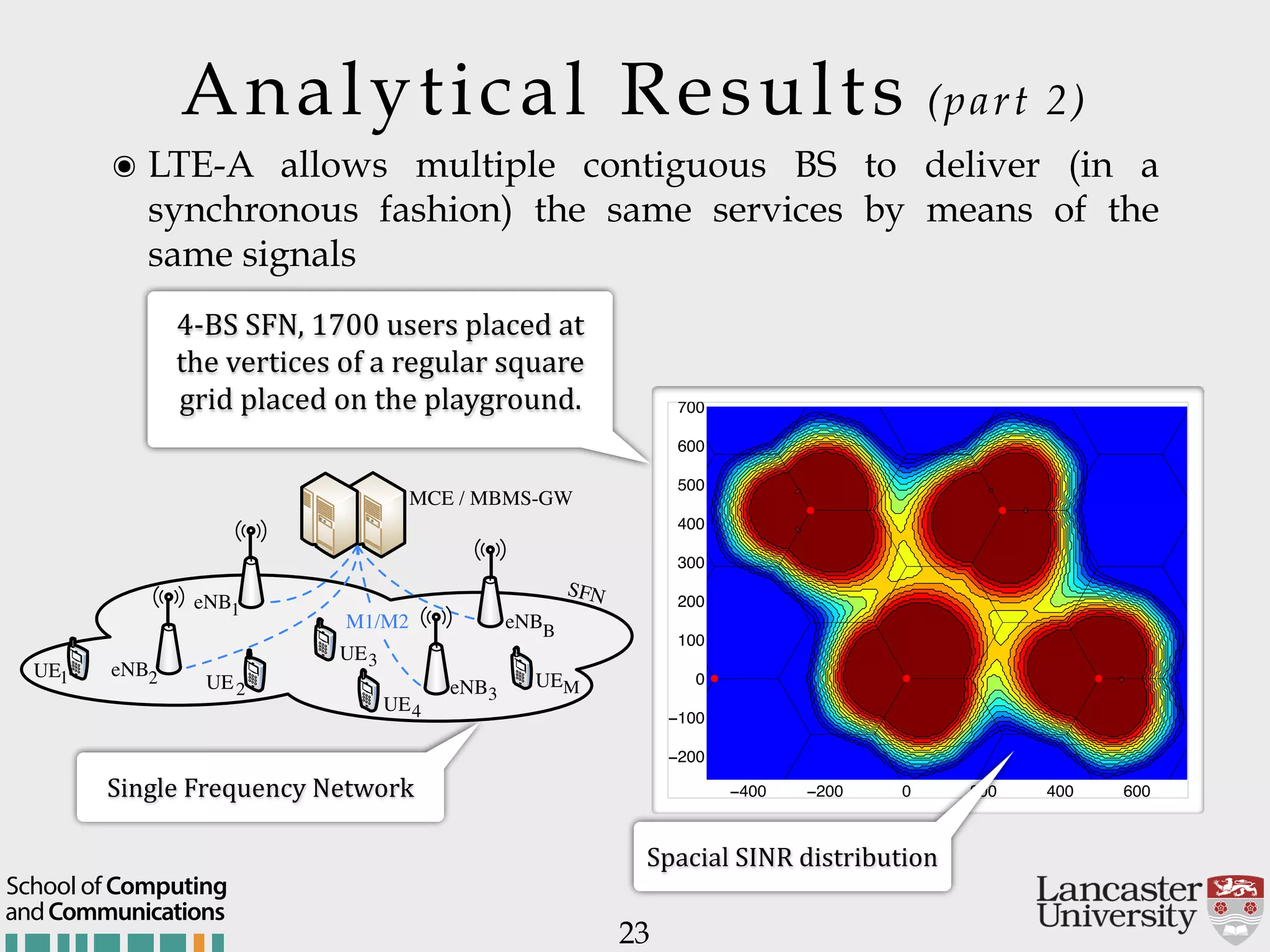
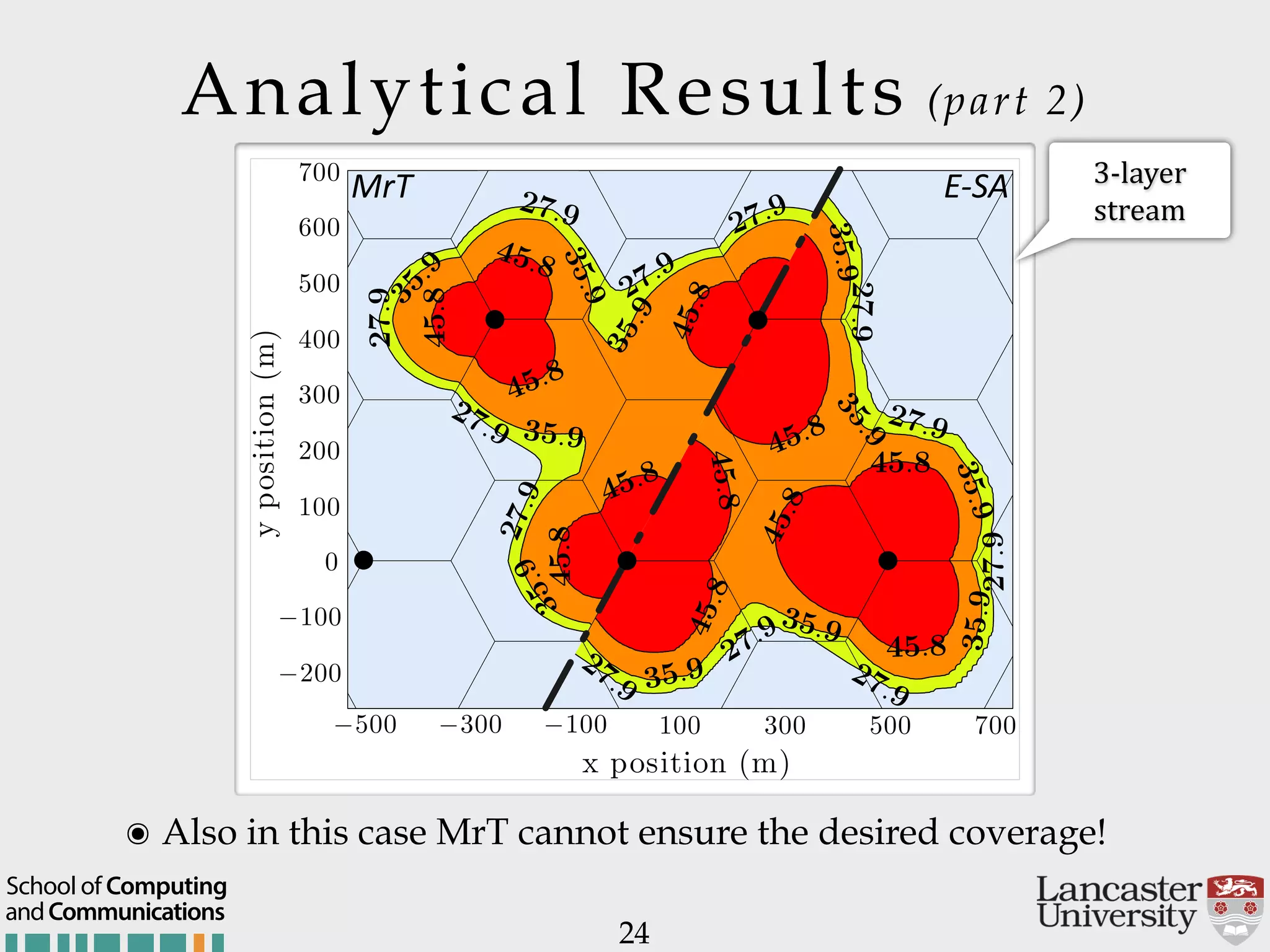
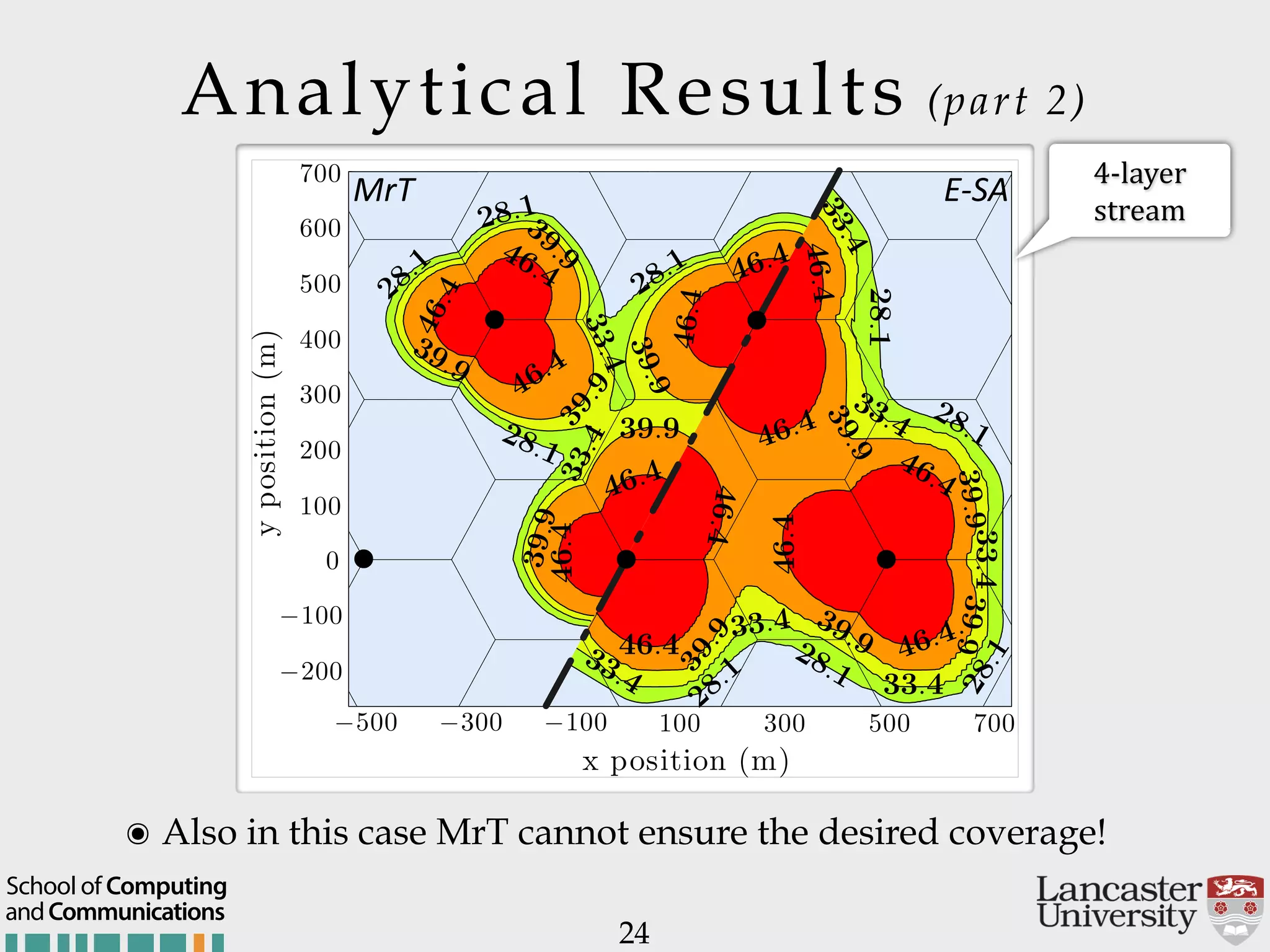
The document outlines the R2D2 project focused on optimizing data delivery for multimedia broadcasting over 4G/5G networks, particularly through error control and resource optimization strategies. It discusses a multi-rate transmission system that delivers layered services to users based on their channel conditions, utilizing techniques like Random Linear Network Coding (RLNC). Additionally, various resource allocation models and heuristic strategies are proposed to enhance the efficient delivery of service levels while minimizing radio resource usage.