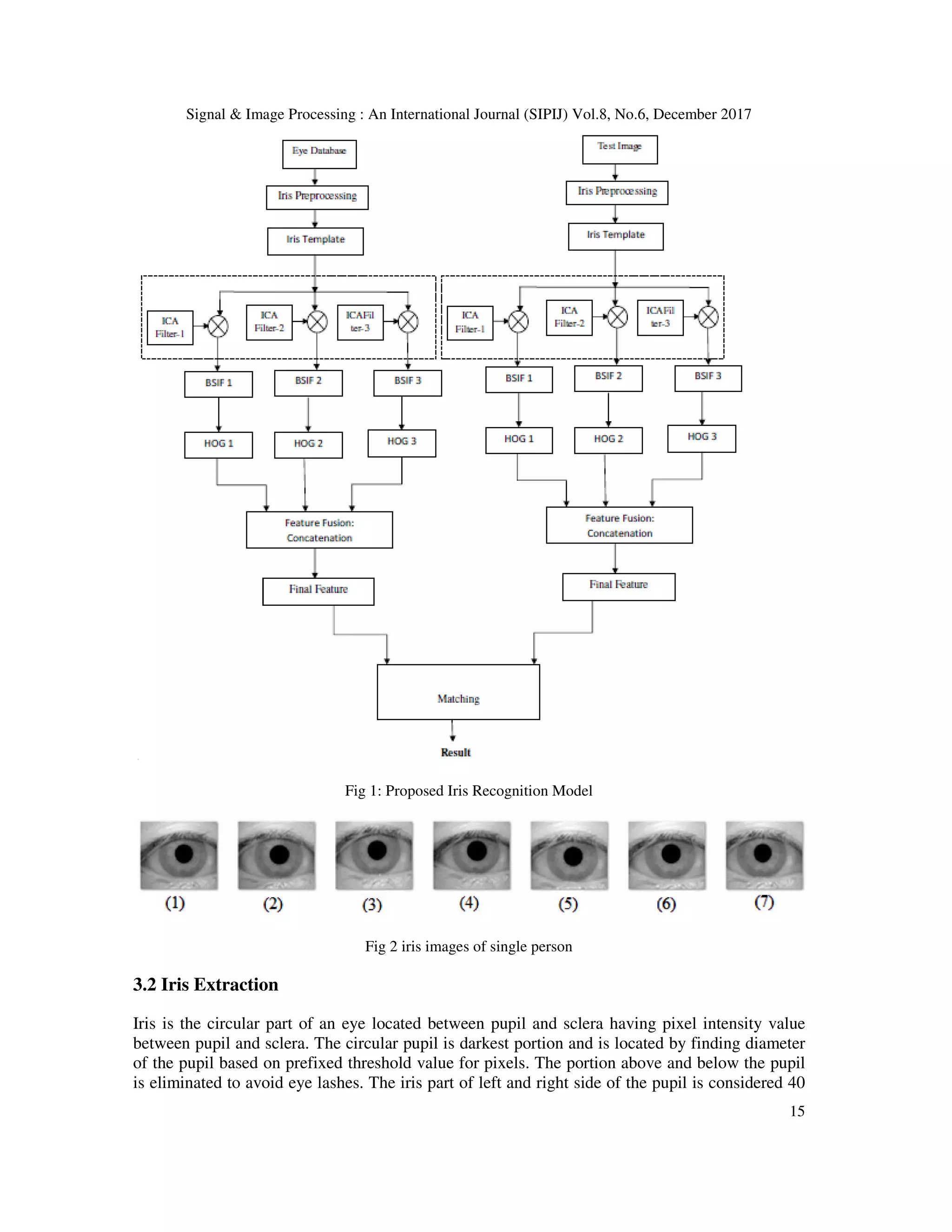
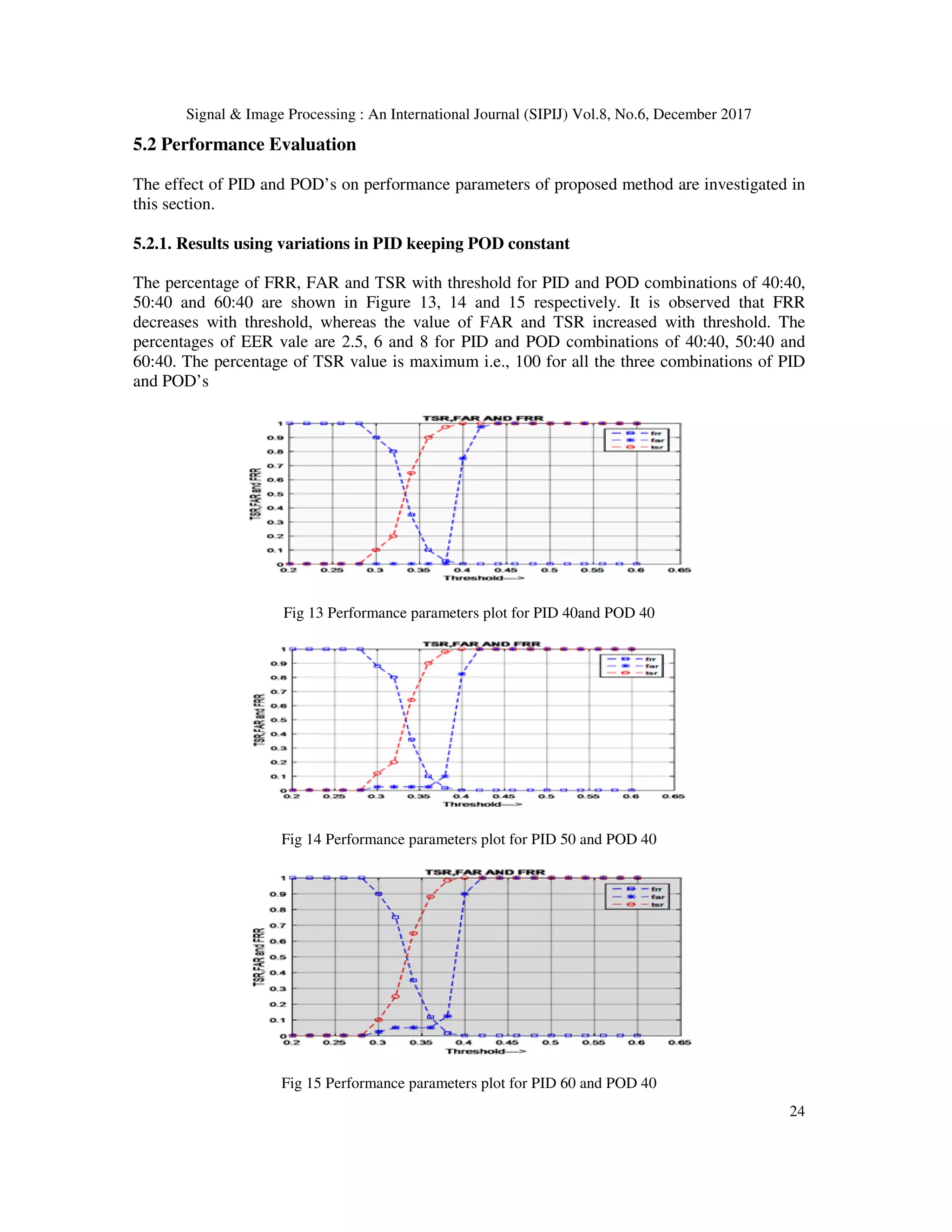
This paper proposes a multi-scale independent component analysis (ICA) based iris recognition system using binarized statistical image features (BSIF) and histogram of gradient orientation (HOG) for more accurate biometric identification. The methodology involves extracting specific portions of iris images and applying multi-scale ICA filters to generate BSIF, with final features obtained by fusing HOG coefficients. Performance comparisons indicate that this approach outperforms existing iris recognition methods.

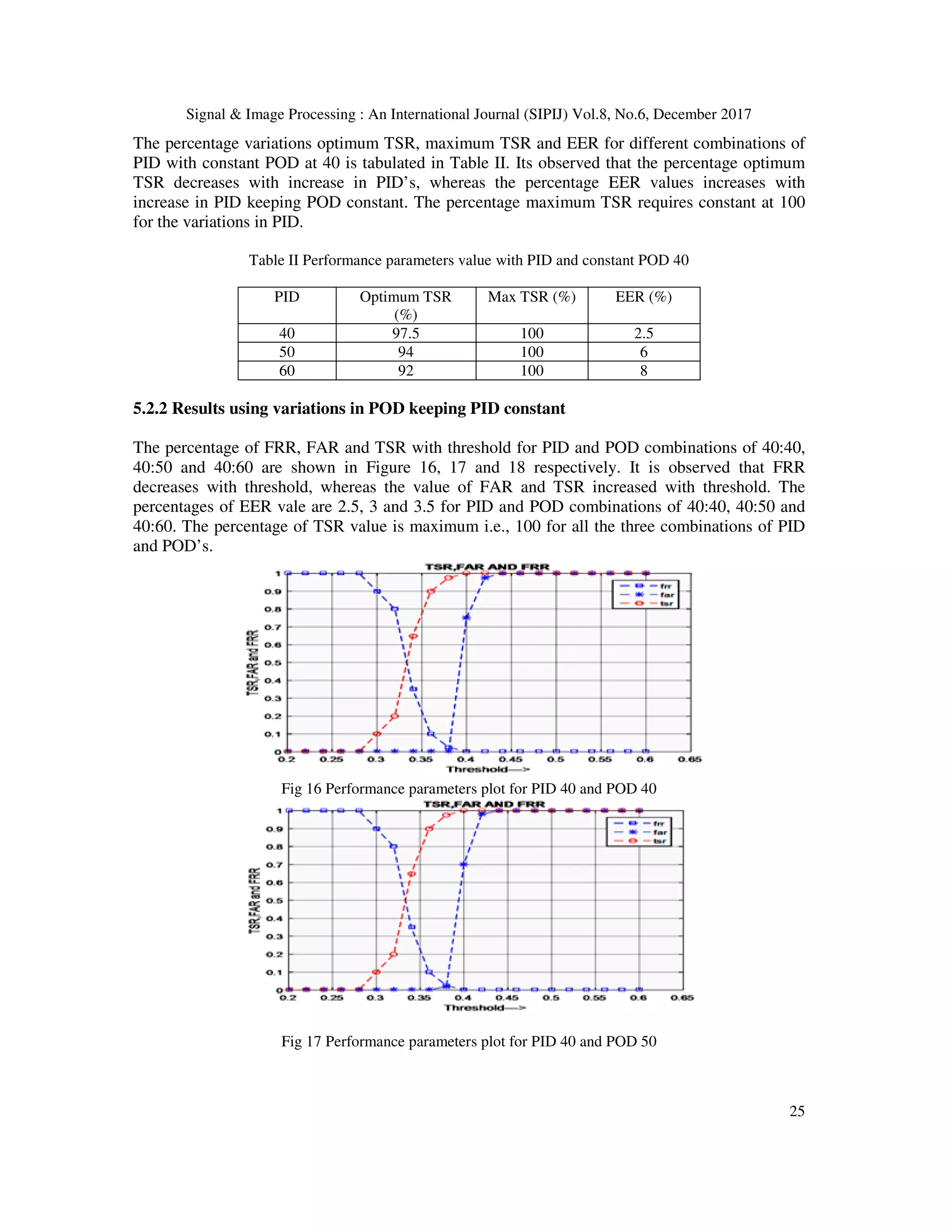
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 12 Contribution: - In this paper Multi-scale ICA based Iris Recognition using BSIF and HOG is proposed. The multi-scale ICA filters are correlated with iris templates to generate BSIF. The HOG is used on each BSIF to obtain HOG coefficients. The final features are extracted by concatenating HOG coefficients Organization: - The rest of the paper is organized as follows: Section 2 describes Literature Survey Section 3 describes the proposed Iris model; Section 4 describes the Proposed Algorithm. Section 5 explains the Experiment, Section 6discuss the conclusion. 2. LITERATURE SURVEY Various techniques have introduced in the field of iris biometric for personnel identification. Very early method is to extract iris part from eye image has introduced in Daugman’s Iris code [1] is used multi-scale quadrature wavelet to extract texture phase structure information of iris to generate 2048 bit iris code to compare the difference between a pair of iris representation by computing the Hamming distance via XOR gate. Circular Hough Transformation is used for iris localization. Canny Edge detection algorithm to generate edge map and finds out outer boundary of both iris and sclera. For finding out the radius for both iris and pupil to localize pupil part an effective integro-differential operator is used. In order to normalize Iris image, map each point on iris region to pair of polar coordinates. Rangaswamy and Raja [2] proposed an iris extraction system based iris template which localize the iris image based on threshold value by finding out the pupil part and get the centre and radius of the pupil based on the high intensity threshold. Once finds the pupil radius and centre adjust the pixel value to find the iris part and concatenated to form iris template. Baigang Huang et al., [3] proposed a texture extraction method using ICA filters for image classification. Firstly image patches are selected randomly from images in dataset as observation signal, from which a group of filters called ICA filters are extract using ICA method. Image patches are extracted from same image set and passed through non linear filters to enhance the frequency component of the image, and by the use of PCA it produce Eigen vectors and these Eigen vectors will produce a matrix called ICA filters. Hyvarinen and Oja [4] presented fundamental theory and application about ICA and explains how ICA filters are extracted.ICA is a method that will find a linear representation of non-Gaussian data so that the components are statistically independent. Raghavendra and Christoph Busch,[5] proposesd Iris Presentation Attack Detection Using Multiscale Binarized Statistical Image Features. Experiments are carried out on four different artifact iris databases. This method introduced an algorithm which uses the multi scale Binarized images along with Support Vector Machine (SVM). The Experiment carried out on both complete eye image and extracted iris image, both images are trained using both real and artifact images and decision have been using weighted majority voting. Raul Malutan et al., [6] described an iris biometric system based on HoG and LIOP. Histogram of Gradient orientation (HoG) procedure calculate occurrence of gradient orientation in the region of interest of an image. Images are divided into small regions, called cells and calculate histogram of gradient edge orientations of the pixels within the cell. Each can further divided into connected blocks and are overlapped in nature, means each cells will contribute more than once in orientation calculation. Zhenan Sun et al.,[7] proposed a texture pattern illustration method called Hierarchical Visual Codebook (HVC) is to encode the texture character of iris images. HVC method is a combination of two existing Bag-of-Words models, namely Vocabulary Tree (VT),](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-2-2048.jpg)
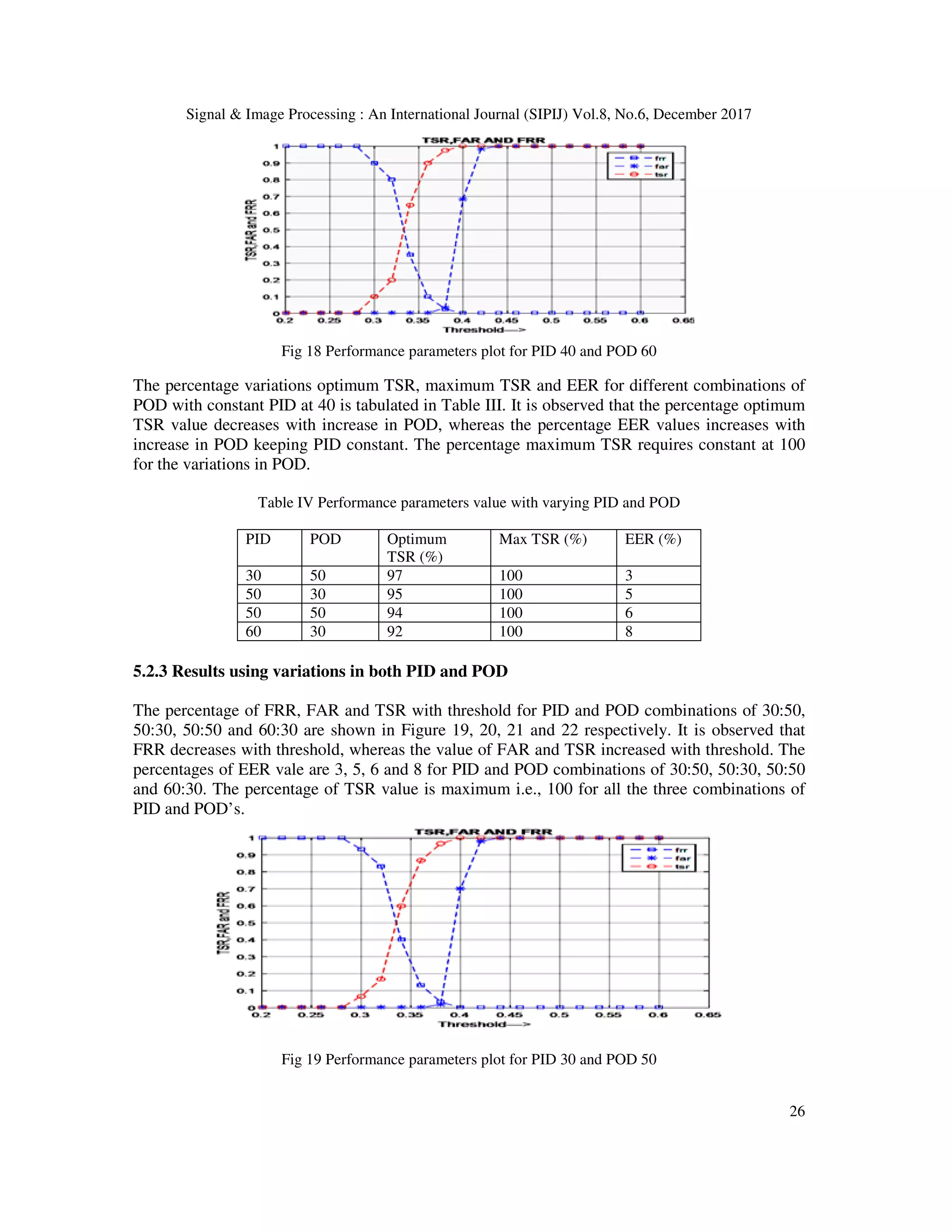
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 13 and Locality-constrained Linear Coding (LLC). The HVC implements a visual coding strategy and takes benefits of both VT and LLC for precise and sparse version of iris texture. Juho Kannala and Esa Rahtu [8] propsed a method to extract the binarized statistical image features using ICA filter for face images, using pre extracted ICA filter from natural texture images and using this filters database images are encoded to binary string. Encoded binary strings have been considered as final feature for matching and SVM is used as a matching technique. Nianfeng Liu et al., [9] proposed A Code-level Approach in heterogeneous iris recognition. Method adapted Markov network to model a non-linear relationship between binary feature codes of heterogeneous iris images. The learnt iris template and weight Map are used to build an iris matcher against the variations of imaging sensors with different condition. Pattabhi Ramaiah and Ajay Kumar [10] proposed a Cross-Spectral Matching Iris Recognition based on naive Bayes nearest neighbor classification method to estimate which is capable of learning domain knowledge. Method is to approximate visible iris sample from synthesis of iris patches in the near infrared iris images. Shejin Thavalengal et al., [11] described a method for Iris Liveness Detection that utilizes the acquisition workflow for iris biometrics on smart phones using both visible and near infra-red sensor. Pupil characteristics is determined the liveness of the identifier by using a fast, Multi-frame pupil localization technique along with an intermediate classifier related to Jenson-Shannon divergence. This method can identify the presentation attack even with 3-D face model. Jianxu Chen et al., [12] proposed a Human-Interpretable Features based iris recognition using iris crypts. This method is able to capture different crypts in different locations and able to match topological changes in the detection of the same crypt in different acquisitions. Yang Hu et al., [13] introduced a method to generate optimal iris code for iris recognition. Addition to the binarized code effective iris codes are obtained by adding terms to the objective functions to the optimization problem. First one exploits the spatial relationships of the bits in different positions of an iris code and the second objective term reduce the influence of less reliable bits in iris codes. Zhenhua Chai et al., [14] proposed a novel facial feature extraction method called Gabor ordinal measures (GOM), which adds the Gabor features and the robustness of ordinal measures as a solution to mutually handle intra person variations and inter person similarity in face images. In the proposed method have different kinds of ordinal measures are derived from magnitude, phase, real, and imaginary components of Gabor images, and then are jointly encoded as visual primitives in local regions. Adam Czajka et al., [15] proposed an Image orientation recognition for iris spoofing where it find the correct orientation of the iris image whether it is left or right and upright or upside down. This will help to identify the spoofing attacks which generate fake identities by rotating the iris sensor or image at the time of image acquisition. Two well known classifiers SVM and Convolutional Neural Network (CNN) are used for feature learning and classification. Karen Hollingsworth et al., [16] described an Iris recognition system that uses signal level fusion of frames from a video. From the iris video frames they created an average image. Use of single level fusion method they take benefit of the temporal continuity of iris video to increase matching performance. Fusion is done by pixel by pixel average and log-Gabor filter is used to produce code templates. Javier Galbally et al., [17] introduced image quality estimation for fake biometric detection that is used for multiple systems. They introduced liveness method in fast and non- disturbing manner and also assure the quality of test image is similar to that of the image at the time of acquisition. They trained the system with both the fake and original image sets and additional liveness system makes it more compatible with other recognition systems.](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-3-2048.jpg)
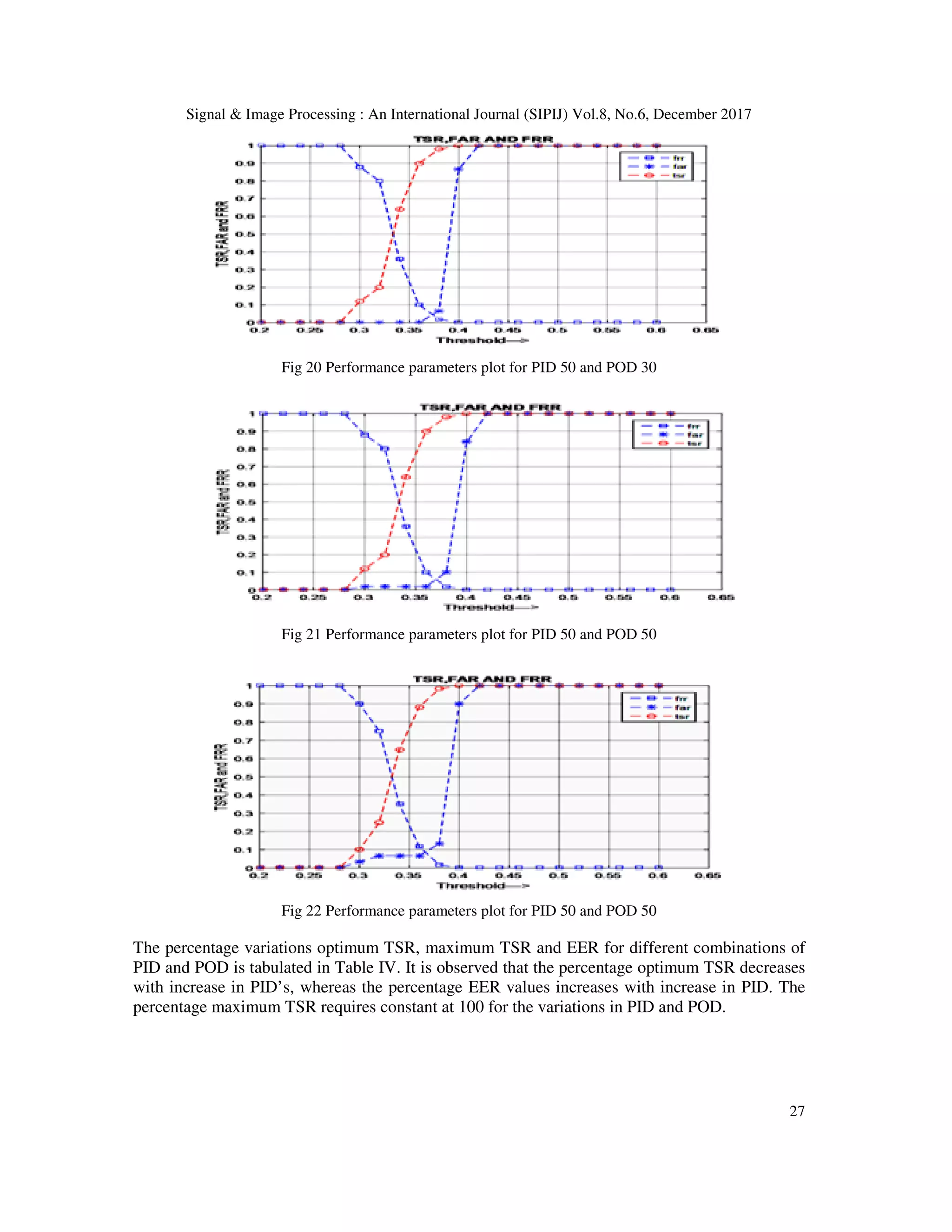
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 14 Dakshayadav et al., [18]described the consequence of textured contact lenses on iris recognition system. Use contact lenses will alter the natural iris patterns in iris image and it difficult to identify the person with contact lenses. They also proposed algorithm for same problem based on Modified LBP. Seventeen different classifiers are used to train feature sets of database with and without contact lenses and correct classification rate (CCR) is measured. They also analyzed different existing feature method along with the proposed method to identify the best me Andrey and Elena [19] proposed a Biometric Identification by Using Low-Frequency Eye Tracker. Eye tracking devices used to collect data and signals essential fragments like Saccades are detected and take out from the raw data by examine the eyes velocities. Shailendra et al., [20] proposed a score level fusion of fingerprint and iris. To obtain iris features Combination of 2- level Discrete Wavelet Transform (DWT) and Discrete Cosine Transform (DCT) are used and for fingerprint features a combination of 2-level DWT and Fast Fourier Transform (FFT) are used. Matching was achieved using Euclidean distance algorithm. Matching scores are fused using linear summation to acquire a combined score. Li Ma et al., [21] introduced a technique which used Hough transformation and extracted features by spatial filter; this procedure first converts the circular image of the iris into rectangular model by image unwrap method. Gabor filter is used for feature extraction. Gabor filtering is a familiar procedure in texture analysis. It can extract useful information in particular band pass channels and also decompose this information into bi orthogonal components in terms of spatial frequencies. Yang Hu et al., [22] proposed a signal- level information fusion method to diminish the influence of noise and degradations for less constrained iris recognition systems using Sparse-Error Low Rank Matrix Factorization method. The low rank component approximates the potential noiseless images, while the error component models the noise. Then, the error components and the low rank components are utilized to achieve signal level fusion producing two individually fused images. 3. PROPOSED IRIS RECOGNITION MODEL In this section, we present new approach for iris recognition based on combination of ICA, BSIF and HOG. The proposed method is shown in figure 1, experimented using CASIA V 1.0 iris database with different combination of Person inside Database (PID) and Person outside Database (POD). 3.1 Iris Database The Chinese Academy of sciences Institute of Automation (CASIA V 1.0) Iris database [26] is considered to test the performance of the proposed method. The database has one hundred and eight persons with seven images per person i.e., total number of eye images are seven hundred and fifty six. Three images on the dataset are captured in one session and remaining four images are captured in second session. The captured images are stored in BMP format. The seven images of a person are shown in Figure 2.](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-4-2048.jpg)
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 16 pixel values to the end point pupil on each side. The left and right part is concatenated to form an iris image as shown in Figure 3. (a) Eye Image (b) Iris Template Fig.3 Extracted iris template from the database eye image. 3.3 Independent Component Analysis Independent Component Analysis [4] is a mathematical tool for separating multivariate signal into additive sub component by assuming the sub components are non Gaussian and are independent of each other. . The ICA model has N dimensional random vector RN are assumed to be a linear mixture of mutually statistically independent sources SL RN = MSL (1) Where, M represents the mixing matrix. M is unknown; aim is to find out the M and SL. For separation, we must approximate the separating matrix W that verifies: EL = WRN (2) Where EL is an estimation of the N sources R N. Substitute (1) into (2) we get EL = WMSL (3) From (3), if M is the inverse matrix of W, the independent sources SL can be recovered accurately. There is no direct formula to compute the W instead it achieved by using multiple iterations. By using these iterating method we estimate W so as to make SL is statistical independent as possible. So the ICA filter W are similar to simple cell receptive fields, cell that responds primarily to oriented edges and gratings i.e. they be similar to wavelets or Gabor filters. 3.3.1 Image Representation Images can be represented by the model in equation (1) and for computational prospect; small image patches , are considered which linear superposition of some basic functions x, y and c are coefficients is given in Equation 4](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-6-2048.jpg)


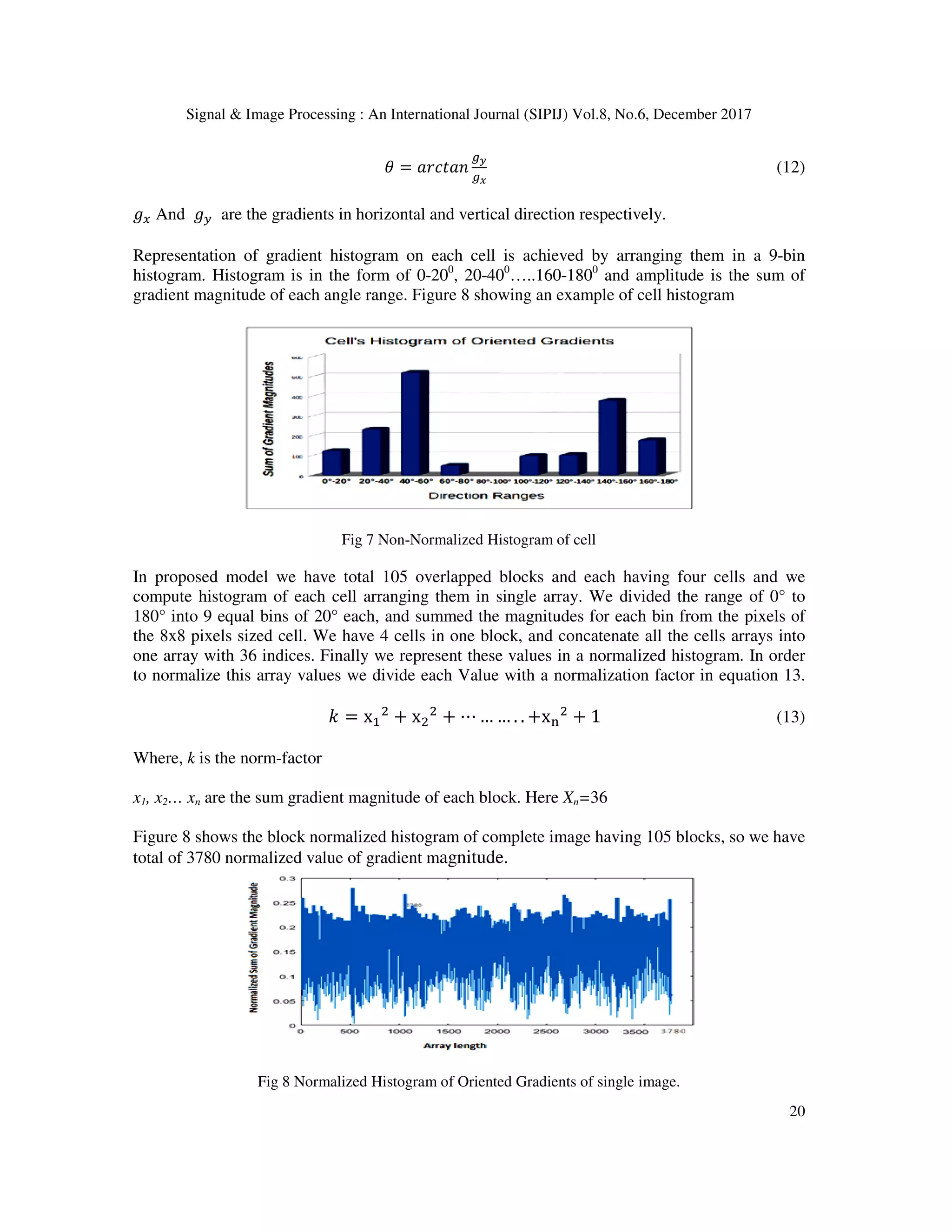
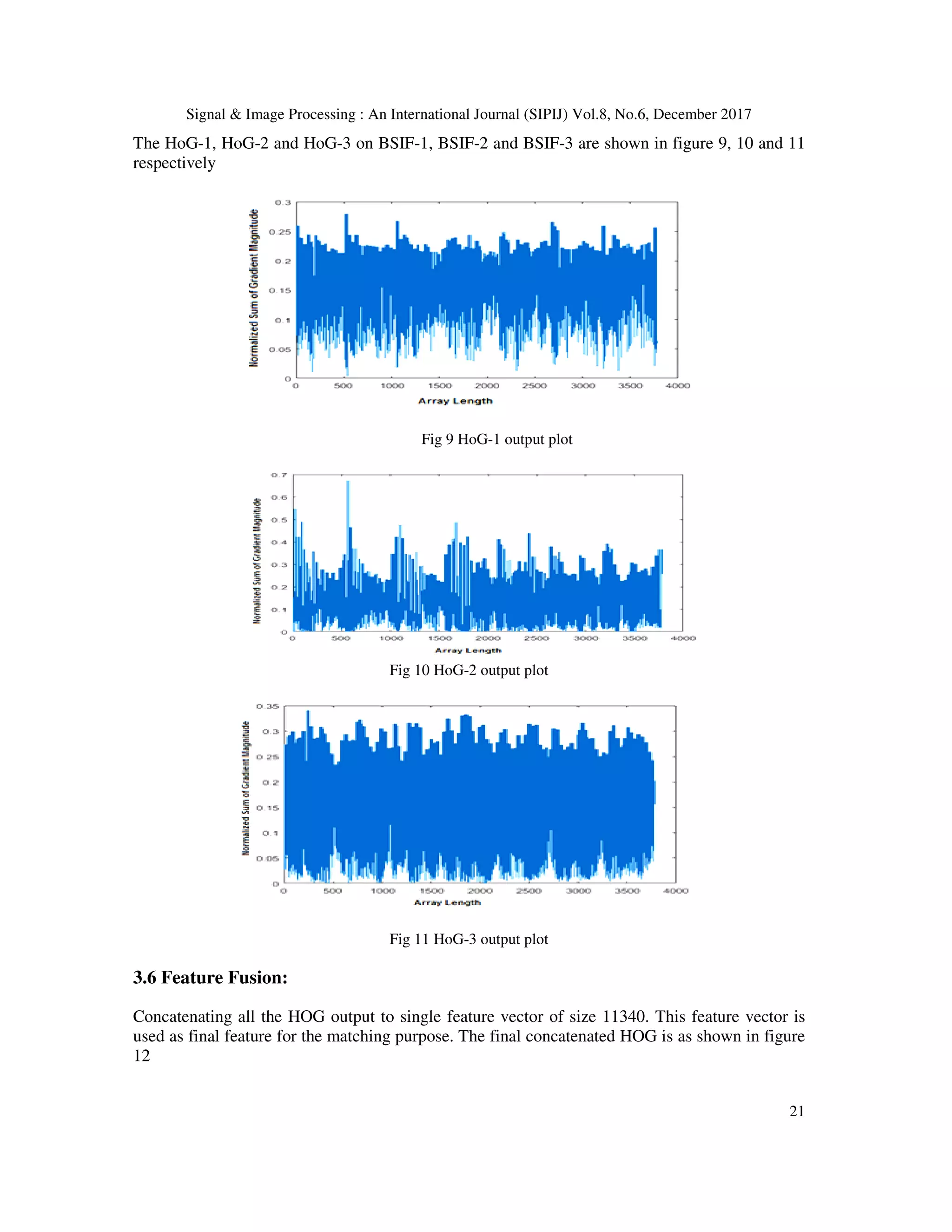
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 19 Fig 5 Binarized output of BSIF 2 3.4.3 BSIF 3 ICA Filter 3 contains twelve 17X17 windows with filter coefficients. Iris image is correlated using the filter and obtained the output by binarizing the image using Equation (10). Pixel values contain 12-bits. Figure 6 showing different bit streams and finally obtained 12-bit image of single iris template. Fig 6 Binarized output of BSIF 3 3.5 Histogram of Gradients (HOG) It is a fundamental tool in the field of object detection. It calculate occurrence of gradient orientation in sub blocks of an image. Each image is divided into blocks and each block is divided in to cell Steps used to obtained HoG descriptor • Output of BSIF is converted to 128X64 image • Divide image into 16X16 blocks with 50% overlap • Each block consist of 2X2 cells with 8X8 matrix size • Quantize the gradient into 9 bins (0-1800 ) histogram. • The concatenate the each cell histogram into single row vector of size 3780. The horizontal and vertical gradients for each 8X8 matrix are computed using kernels [-1 0 1] and [-1 0 1] T for X and Y directions. The magnitude and direction of gradients are computed using equation 11 and 12. B = CBD + BF (11)](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-9-2048.jpg)
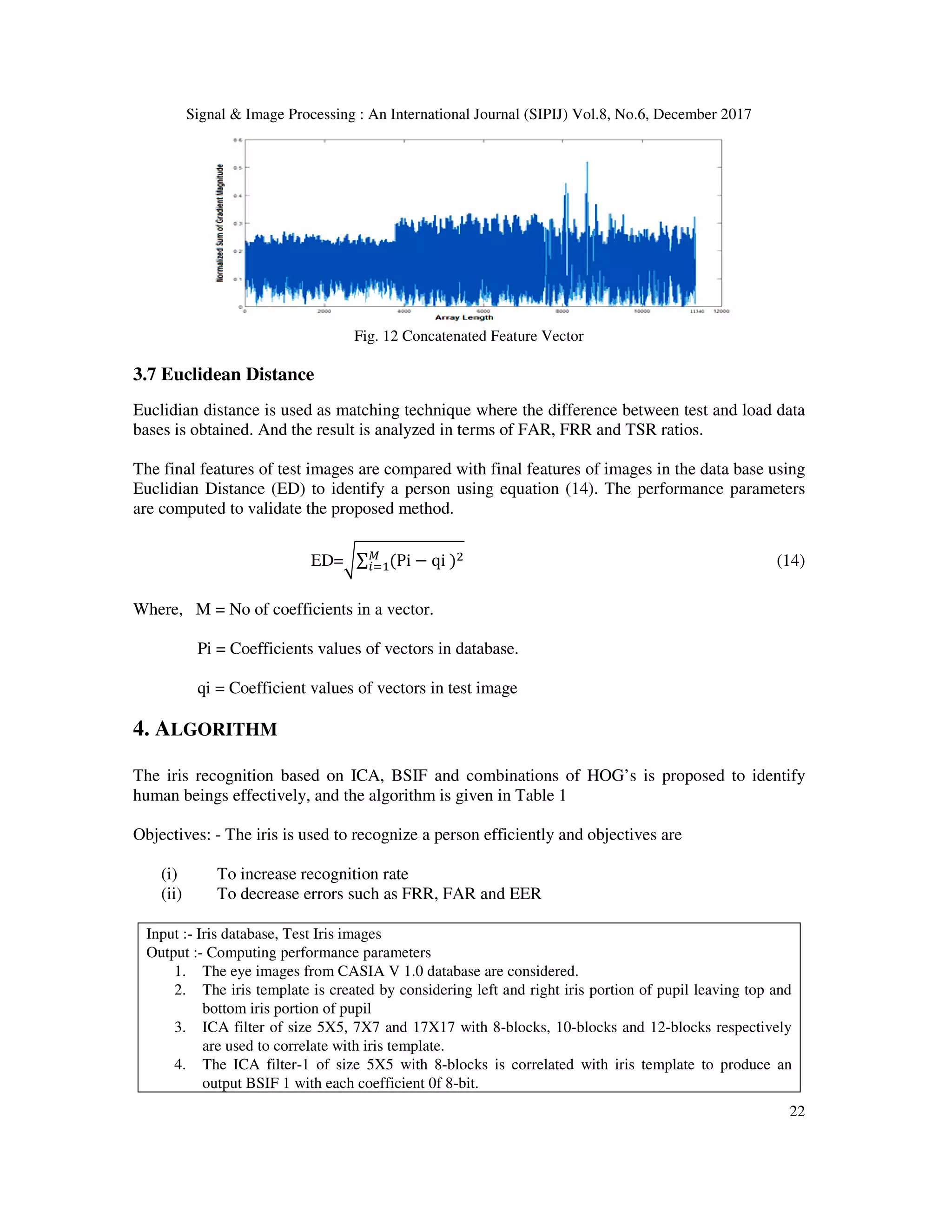
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 23 5. The ICA filter-2 of size 7X7 with 10-blocks is correlated with iris template to produce an output BSIF 1 with each t 0f 10-bit. 6. The ICA filter-1 of size 17X17 with 12-blocks is correlated with iris template to produce an output BSIF 1 with each coefficient 0f 12-bit. 7. The HOG-1, HOG-2 and HOG-3 are applied on BSIF 1, 2 and 3 to obtain initial features. 8. The initial features are concatenated to obtain final features. 9. The ED is used to compute final features of iris template database and test iris template to compute performance parameters. 5. EXPERIMENTS In this section the definition of performance parameters, performance evaluation of proposed method and comparison of proposed method with existing techniques are discussed. 5.1 Definitions of performance parameters The performance evaluation parameters such as FRR, FAR, EER and TSR are given 5.1.1 False Rejection Ratio (FRR) It is the measure of falsely rejected genuine persons and given in equation 15. 2-- = UV 7>? <9 >?@<1@ ->W>I#>X 9HY@>Y Z<#HY 1V 7>? <9 >?@<1@ 41@4X> #ℎ> XH#H7H@> 15 5.1.2 False Acceptance Ratio (FAR) It is the ratio of falsely accepted unauthorized persons to total number of persons outside the database and is given in equation 16 2- = UV 7>? <9 >?@<1@ II>]#>X 9HY@>Y #<#HY 1V 7>? <9 >?@<1@ <V#@4X> #ℎ> XH#H7H@> 16 5.1.3 Equal Error Rate (EER) It is the error rate at which both FRR and FAR are equal. 5.1.4 Total Success Rate (TSR) It is the value of accurate matching of test person to training set and obtained by taking the ratio of true matches to total number of samples inside the dataset and is given in equation 17 Z_- = UV 7>? <9 ]>?@<1@ H#Iℎ>X I<??>I#Y Z<#HY 1V 7>? <9 ]>?@<1@ 41@4X> #ℎ> XH#H7H@> 17](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-13-2048.jpg)
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 28 Table IV Performance parameters value with varying PID and POD PID POD Optimum TSR (%) Max TSR (%) EER (%) 30 50 97 100 3 50 30 95 100 5 50 50 94 100 6 60 30 92 100 8 5.2.4 Comparison of Proposed method with existing methods The performance of Proposed method is compared with existing methods presented by Rangaswamy and Raja [2] Kaushik Roy et al.,[23], Wang Anna et al.,[24], Conti et al.,[25], and Ruihui Zhu et al.,[26]. It is validate that the proposed approach achieved superior performance compared to existing methods.The percentage optimum TSR value is high in the case of proposed method compared to existing methods. TABLE V: Comparison of Optimum TSR with Existing Method Sl No Authors Techniques Optimum TSR % 1 Rangaswamy and Raja [2] AHE+HE+Gabor+FFT 90 2 Kaushik Roy et al.,[22] 2D-Gabor 97 3 Wang Anna et al.,[23] WNN+WPNN 94.5 4 Conti et al.,[24] Micro-Features 95 5 Ruihui Zhu et al.,[25] SIFT 90 6 Proposed Method Multi-ICA+HoG 97.5 6. CONCLUSION Iris recognition system is highly reliable and secure biometric system. in this paper, we proposed Multi-scale ICA based Iris Recognition using BSIF and HOG. The iris template is created by considering only iris horizontal portion between pupil and sclera of an eye image. The ICA filters with multi-scales of 5X5, 7X7 and 17X17 are used to correlate with iris template to generate Multiple BSIF. The HOG is applied on each BSIF to generate initial feature. The final feature are obtained by concatenating three HOG features. The ED is used to compare final features of database and test images to test the performance of the proposed model. It is noticed that, the performance of proposed method is better compared to existing methods. In future, the BISF can be replaced by Local Binary Pattern with appropriate compression techniques to improve further improvement in result. REFERENCES [1] J. Daugman, “How Iris Recognition works, ”IEEE Transactions on Circuits and systems for video Technology, vol. 14, no. 1, pp. 21-30, January 2004. [2] Rangaswamy Y and K B Raja, “Iris Recognition based on Translation of Iris Templates, AHE, HE and Gabor Wavelet Filter, ”International Journal of Computer Science and Network, vol. 5, no. 5, pp. 842-853,October 2016](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-18-2048.jpg)
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 29 [3] Baigang Huang, Junshan Li, and Shuangyan Hu, “Texture Feature Extraction using ICA Filters,” Proceedings of the World Congress on Intelligent Control and Automation, pp.7631-7635, June, 2008 [4] A. Hyva¨rinen, E. Oja, “Independent component analysis: algorithms and applications,” Elsevier International Journal of, vol. 13, no.4, pp.411-430, June 2000. [5] R. Raghavendra and Christoph Busch, “Robust Scheme for Iris Presentation Attack Detection Using Multiscale Binarized Statistical Image Features,” IEEE Transactions on Information Forensics and security, vol. 10, no. 4, pp. 703-715, April, 2015 [6] Raul Malutan, Simina Emerich, Olimpiu Pop and Laszlo Lefkovit, “Half Iris Biometrie System Based on HOG and LIOP,” Second International Conference on Frontiers of Signal Processing, pp. 99-103, October 2016 [7] Zhenan Sun, Hui Zhang, Tieniu Tan and Jianyu Wang, “Iris Image Classification Based on Hierarchical Visual Codebook,” IEEE Transaction on Pattern Analysis and Machine Intelligence, vol. 36, no. 6, pp. 1120-1133, June 2014. [8] JuhoKannala and EsaRahtu, “BSIF: Binarized Statistical Image Features”, http://www.cse.oulu.fi/Downloads/BSIF. [9] Nianfeng Liu, Jing Liu, Zhenan Sun, and Tieniu Tan, ” A Code-level Approach to Heterogeneous Iris Recognition,” IEEE Transactions on Information Forensics and Security, vol.12, no.10, pp.2373- 2386, October 2017 [10] N Pattabhi Ramaiah and Ajay Kumar, “Towards More Accurate Iris Recognition using Cross- Spectral Matching,” IEEE Transactions on Image Processing, vol.26, no.1, pp.208-221, January 2017. [11] Shejin Thavalengal, Tudor Nedelcu, Petronel Bigioi and Peter Corcoran, “Iris Liveness Detection for Next Generation Smartphones,” IEEE Transactions on Consumer Electronics, vol. 62, no. 2, pp.95- 102, May 2016. [12] Jianxu Chen, FengShen, Danny Z. Chen and Patrick J. Flynn, “Iris Recognition Based on Human- Interpretable Features, ”IEEE Transactions on Information Forensics and Security, vol.11, no. 7, pp. 1476 -1485, July 2016. [13] Yang Hu, Konstantinos Sirlantzis, and Gareth Howells, “Optimal Generation of Iris Codes for Iris Recognition,” IEEE Transactions on Information Forensics and Security vol.12, no.1, pp.157-171, January 2017. [14] Adam Czajka, Kevin W. Bowyer, Michael Krumdick, and Rosaura G. VidalMata, “Recognition of Image-Orientation-based Iris Spoofing,” IEEE Transactions on Information Forensics and Security,vol.12, no. 9, pp.2184-2196, September 2017. [15] Karen Hollingsworth, Tanya Peters, Kevin W. Bowyer, and Patrick J. Flynn, “Iris Recognition Using Signal-Level Fusion of Frames from Video,” IEEE Transactions on Information Forensics and Security, vol.4, no.4, pp. 837-848, December 2009. [16] Javier Galbally, Sébastien Marcel and Julian Fierrez, “Image Quality Assessment for Fake Biometric Detection: Application to Iris, Fingerprint, and Face Recognition IEEE Transactions on Image Processing, vol.23, no. 2, pp.710-724, February 2014.](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-19-2048.jpg)
![Signal & Image Processing : An International Journal (SIPIJ) Vol.8, No.6, December 2017 30 [17] DakshaYadav,NamanKohli,James S. Doyle,Richa Singh,MayankVatsa andKevin W Bowyer, “Unraveling the Effect of Textured Contact Lenses on Iris Recognition,” IEEE Transactions on Information Forensics and Security, vol.5, no.5, pp.851-862, December 2014. [18] Andrey V. Lyamin and Elena N. Cherepovskaya,“An Approach to Biometric Identification by Using Low-Frequency Eye Tracker,” IEEE Transactions on Information Forensics and Security, vol.12, no.4, pp.881-891, April 2014 [19] ShailendraTiwari, sudhakar Tripathi and K V Arya, “Score Level Fusion iris and fingerprint using Wavelet Features, ”Fourth International Conference on Parallel, Distributed and Grid Computing, pp.456-461, December 2016. [20] Li Ma, Y. Wang and T. Tan, “Iris Recognition Based on Multichannel Gabor Filtering,” Proc. of the Asian conference on Computer Vision, vol. 1, pp. 279-283, June. 2002. [21] Yang Hu, Konstantinos Sirlantzis, and Gareth Howells, “Signal-Level Information Fusion for Less Constrained Iris Recognition using Sparse-Error Low Rank Matrix Factorization,” IEEE Transactions on Information Forensics and Security, vol.11, no.7, pp.1549-1564, July 2016. [22] Kaushik Roy, Darrel Hudgin, Prabir Bhattacharya and Ramesh Chandra Debnath, “Iris Recognition:A Java based Implementation,” IEEE international conference on Computer and information technology, December 2007. [23] Wang Anna,ChenYu, Wujie and Zhangxinhua, “Iris Recognition Based on wavelwet Transform and Neural Network,” IEEE International Conference on Complex Medical Engineering, pp.758-761, May 2007. [24] V. Conti, G. Milici, F. Sorbello and S.Vitabile, ”A Novel Iris Recognition System Based on Micro- Features,” IEEE Workshop on Automatic Identification Advanced Technologies, pp.253-258, June 2007. [25] Ruihui Zhu, Jinfeng Yang and Renbiao Wu, “Iris Recognition Based on Local Feature Point Matching,” IEEE International Symposium on Communications and Information Technologies, pp.451-454, October 2006. [26] http://forensics.idealtest.org/casiav1 AUTHORS Ganapathi V Sagar in the Dept. of Electronics and Instrumentation Engineering at Dr.AmbedkarInstitute of Technology, Bangalore. He obtained his B.E. degree in Instrumentation Technology from BDT, College of EngineeringDavangere. His specialization in Master degree was Bio-Medical Instrumentation from VTU,Belgaum and currently he is pursuing Ph.D. in the area of Image Processing under the guidance of Dr. K Suresh Babu, Professor, Dept of Electronics and Communication Engineering, University Visvesvaraya college of Engineering, Bangalore. He has over 30 research publications in referred International Journals and Conference Proceedings.His area of interest is in the field of Signal Processing and Communication Engineering.](https://image.slidesharecdn.com/sipij02-180111072522/75/MULTI-SCALE-ICA-BASED-IRIS-RECOGNITION-USING-BSIF-AND-HOG-20-2048.jpg)
