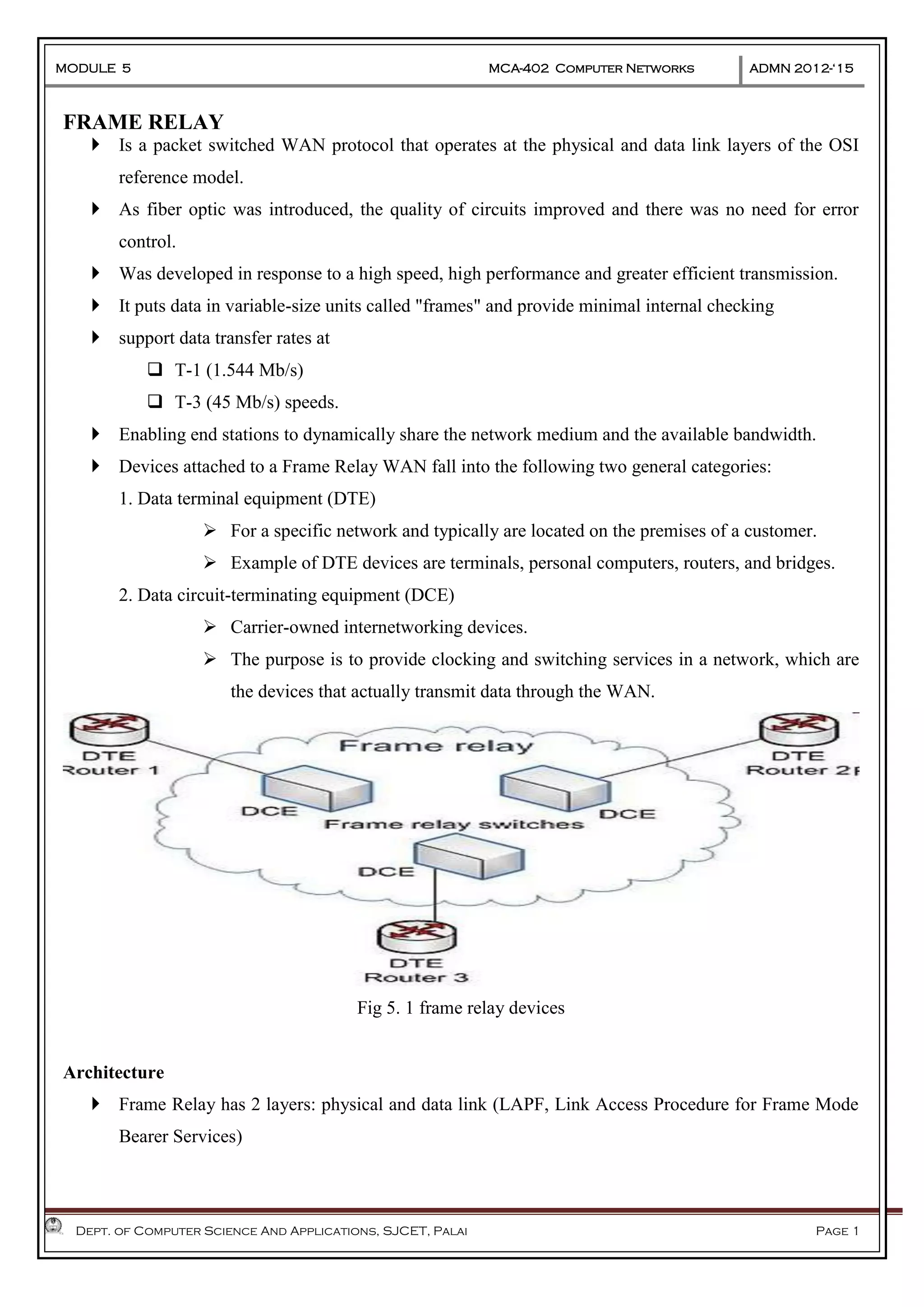
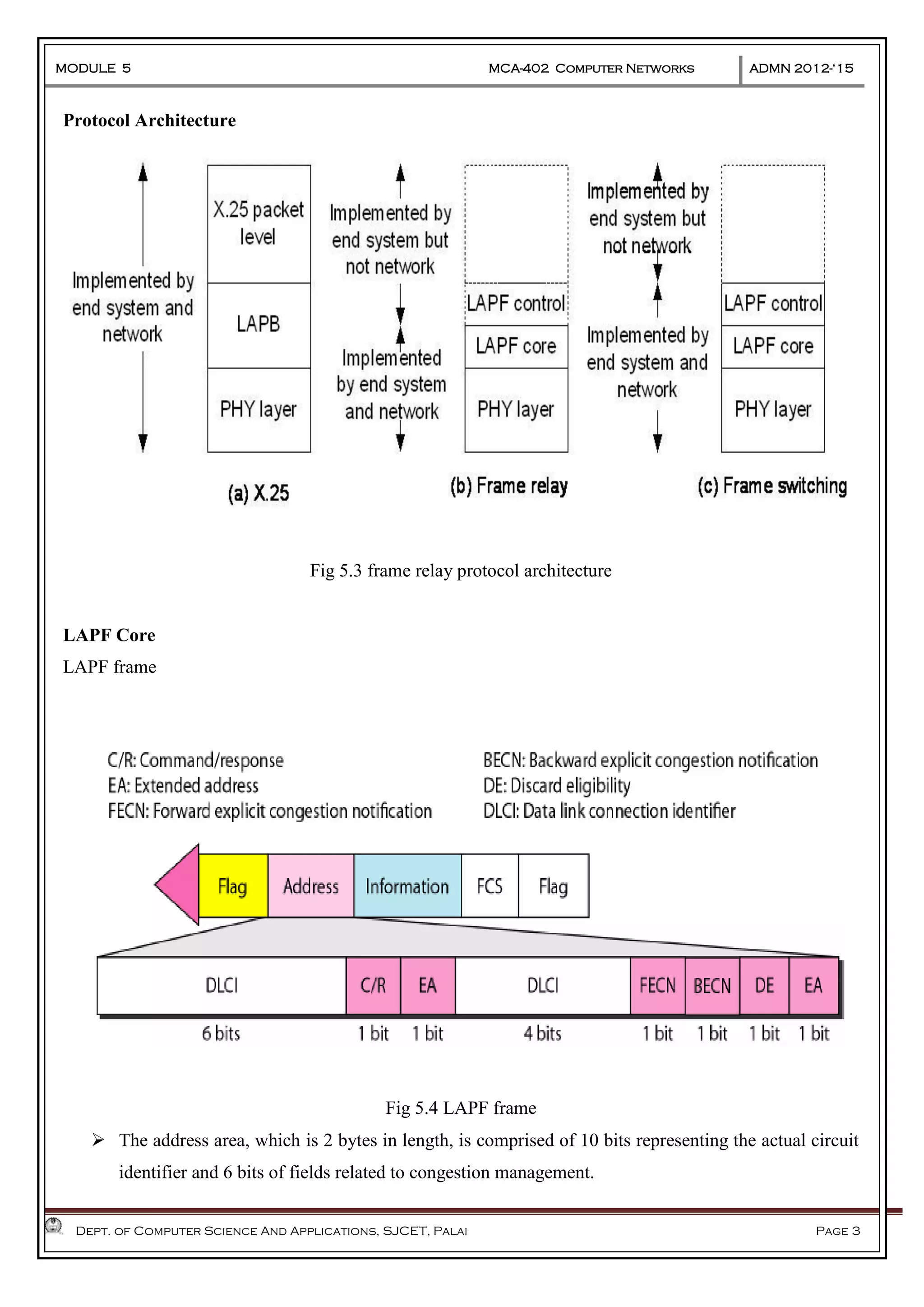
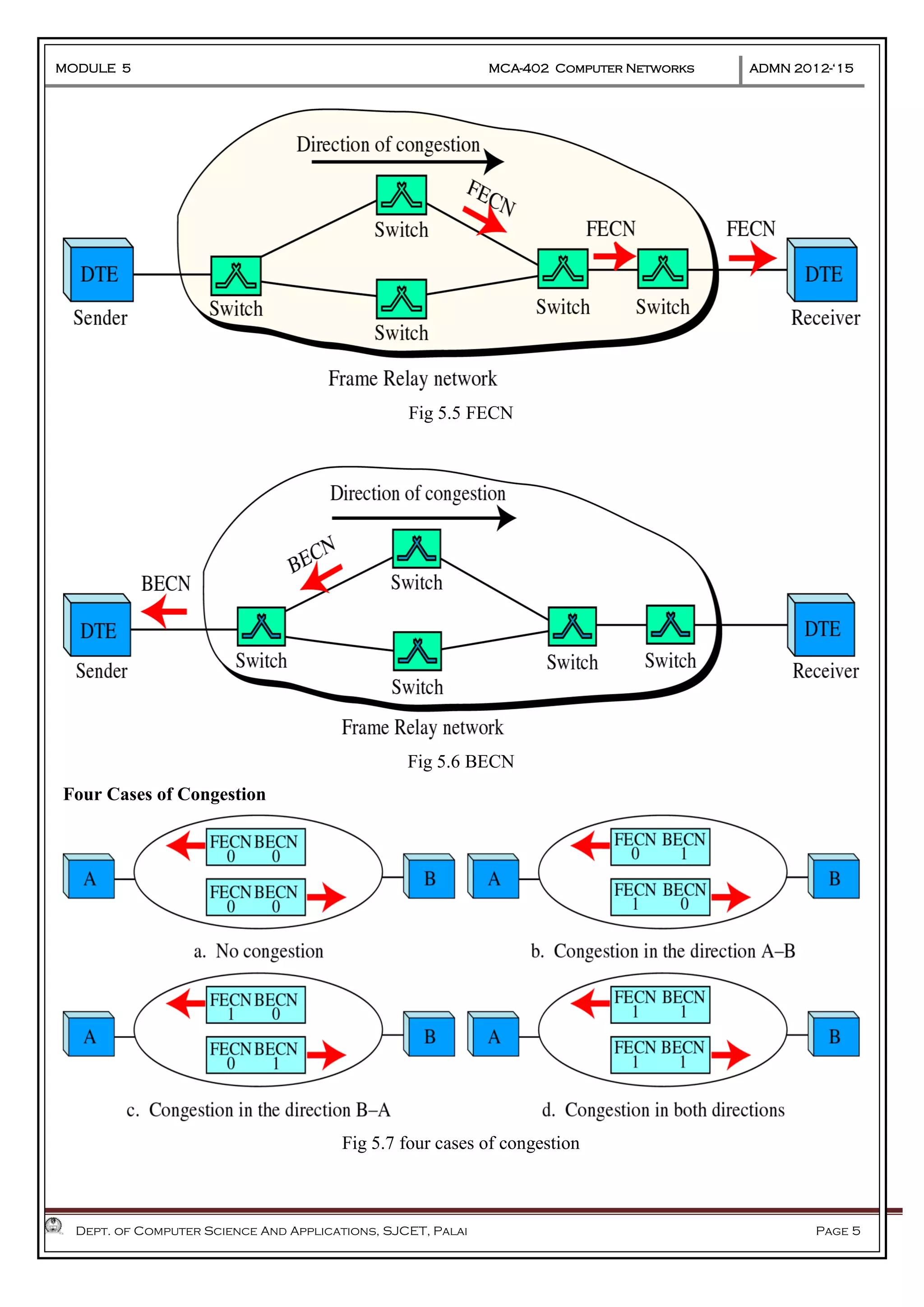
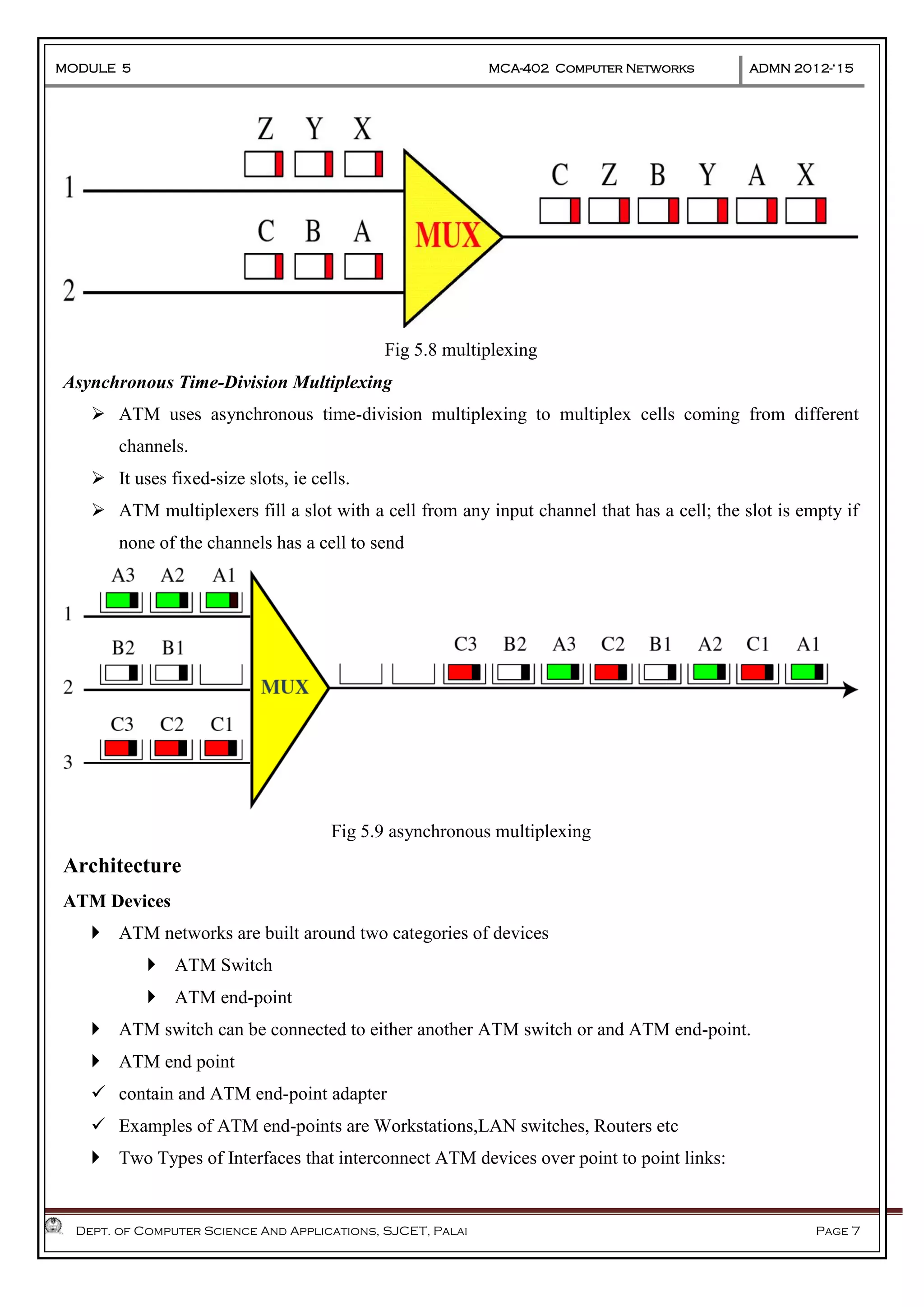
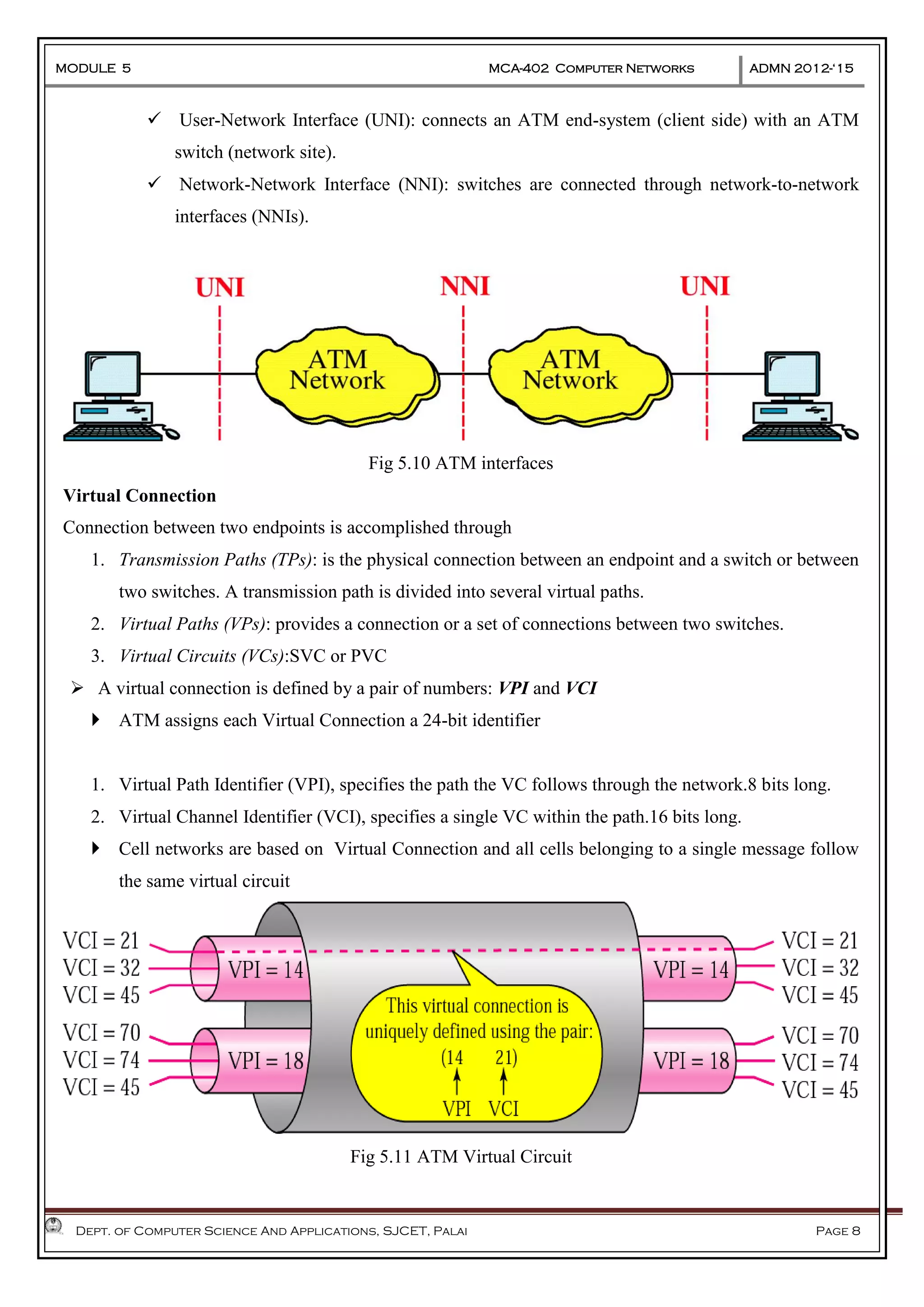
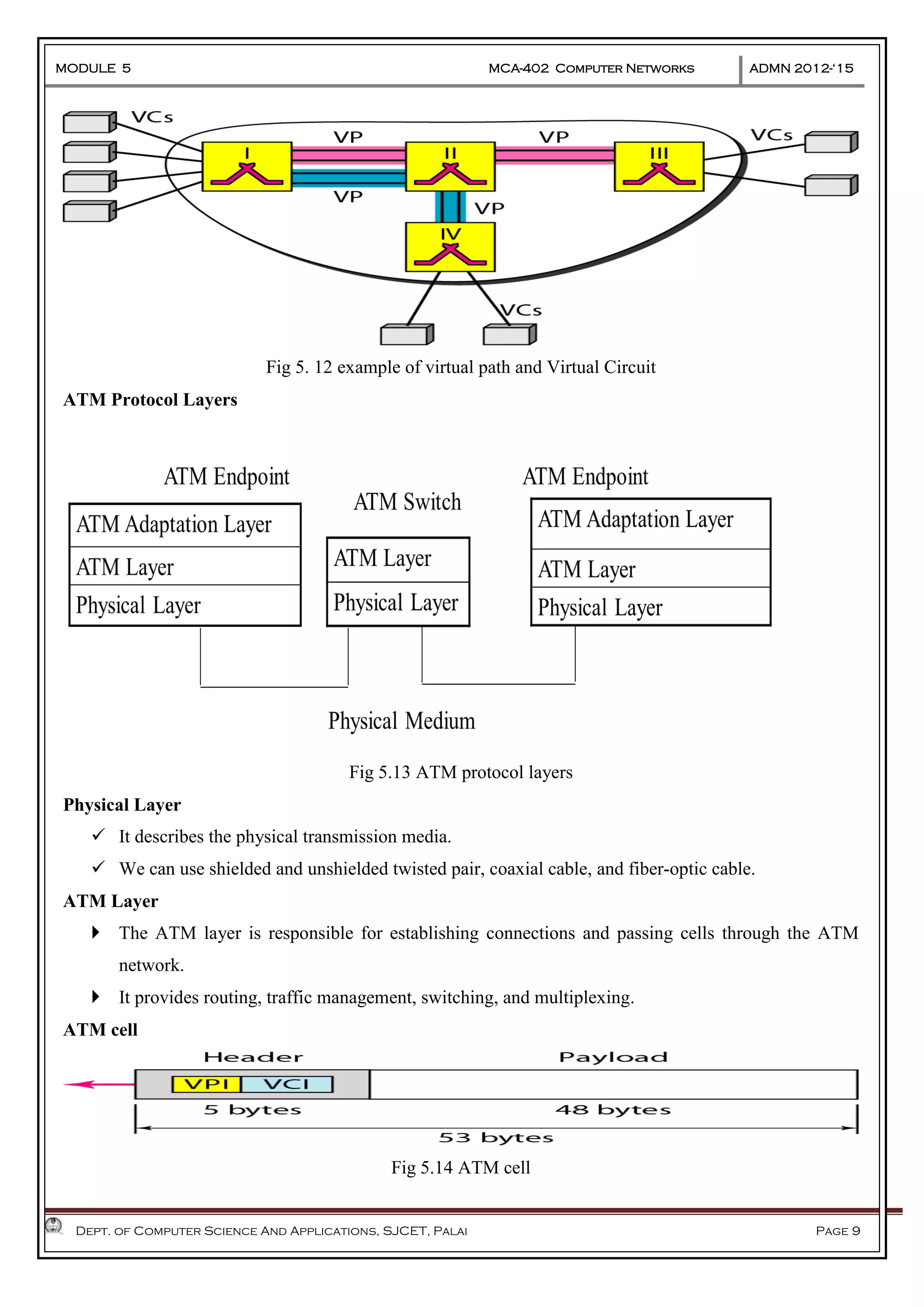
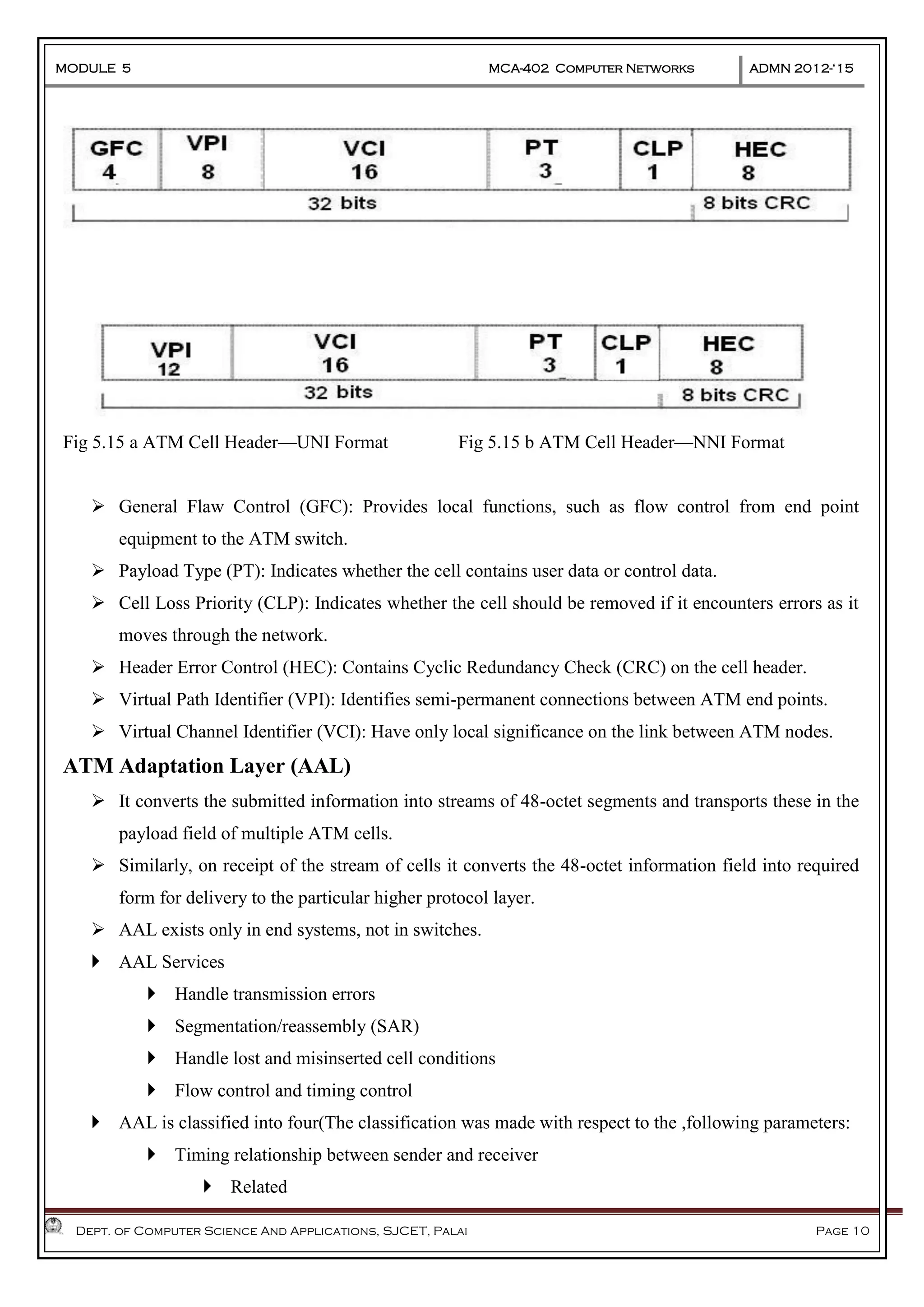
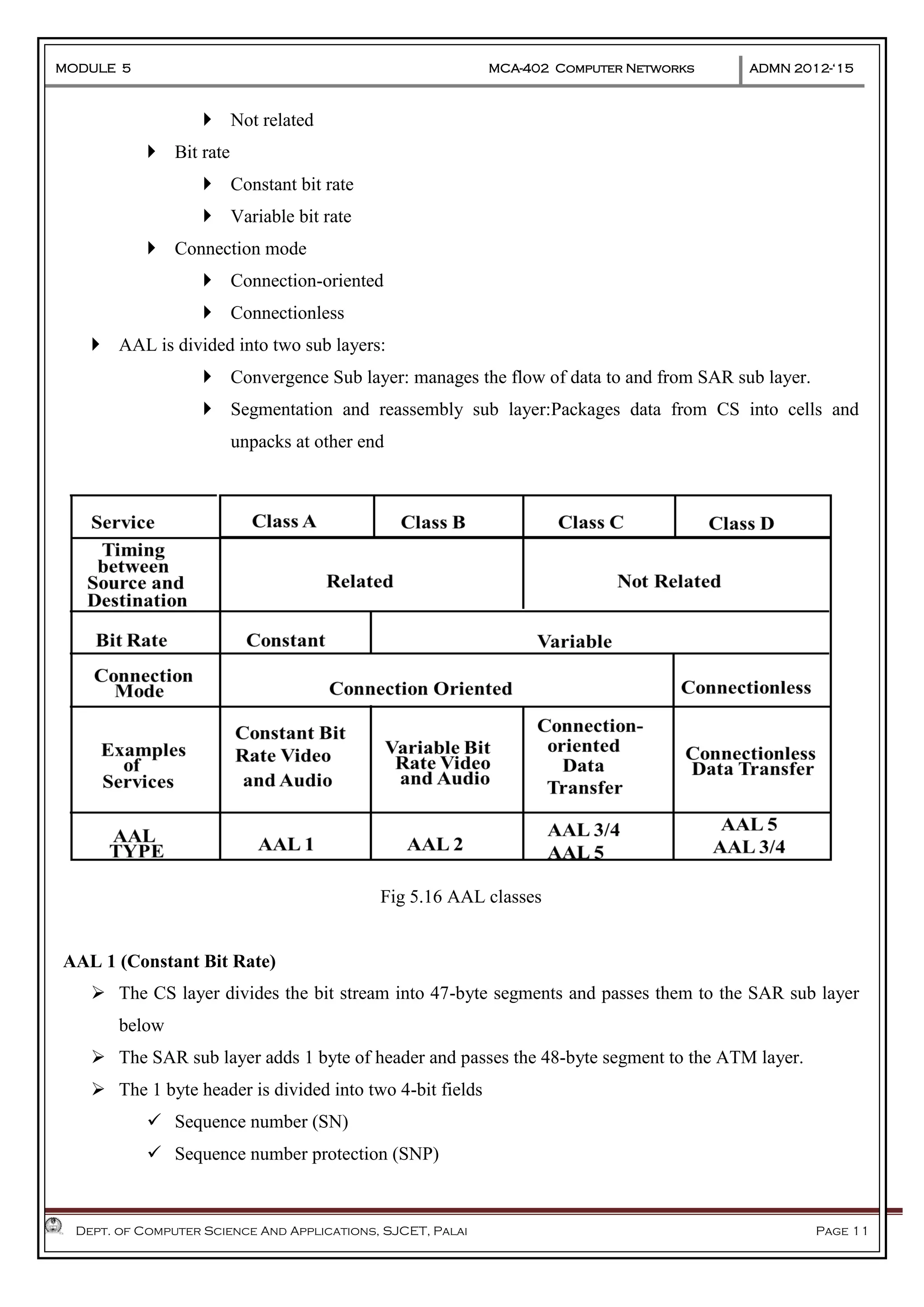
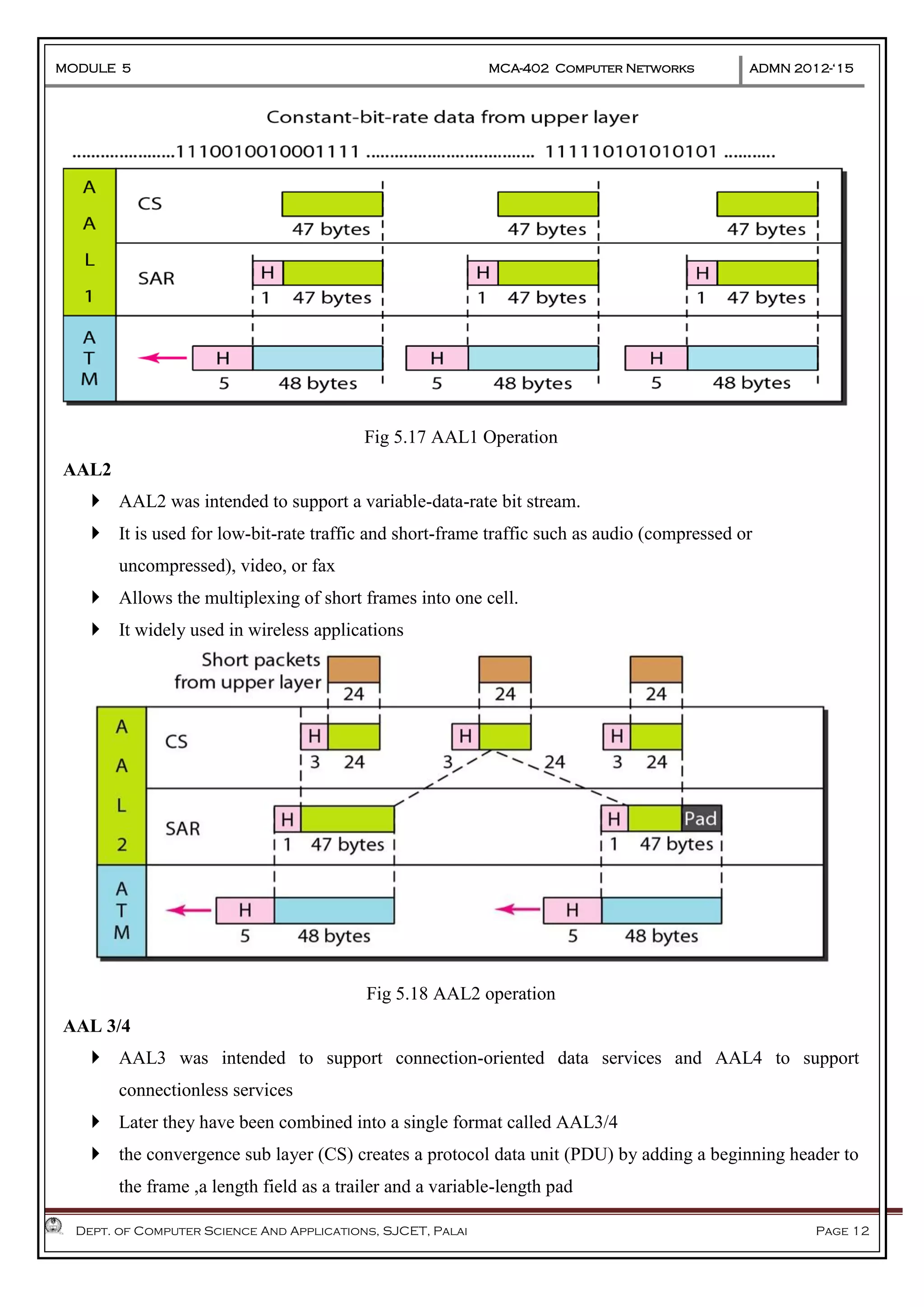
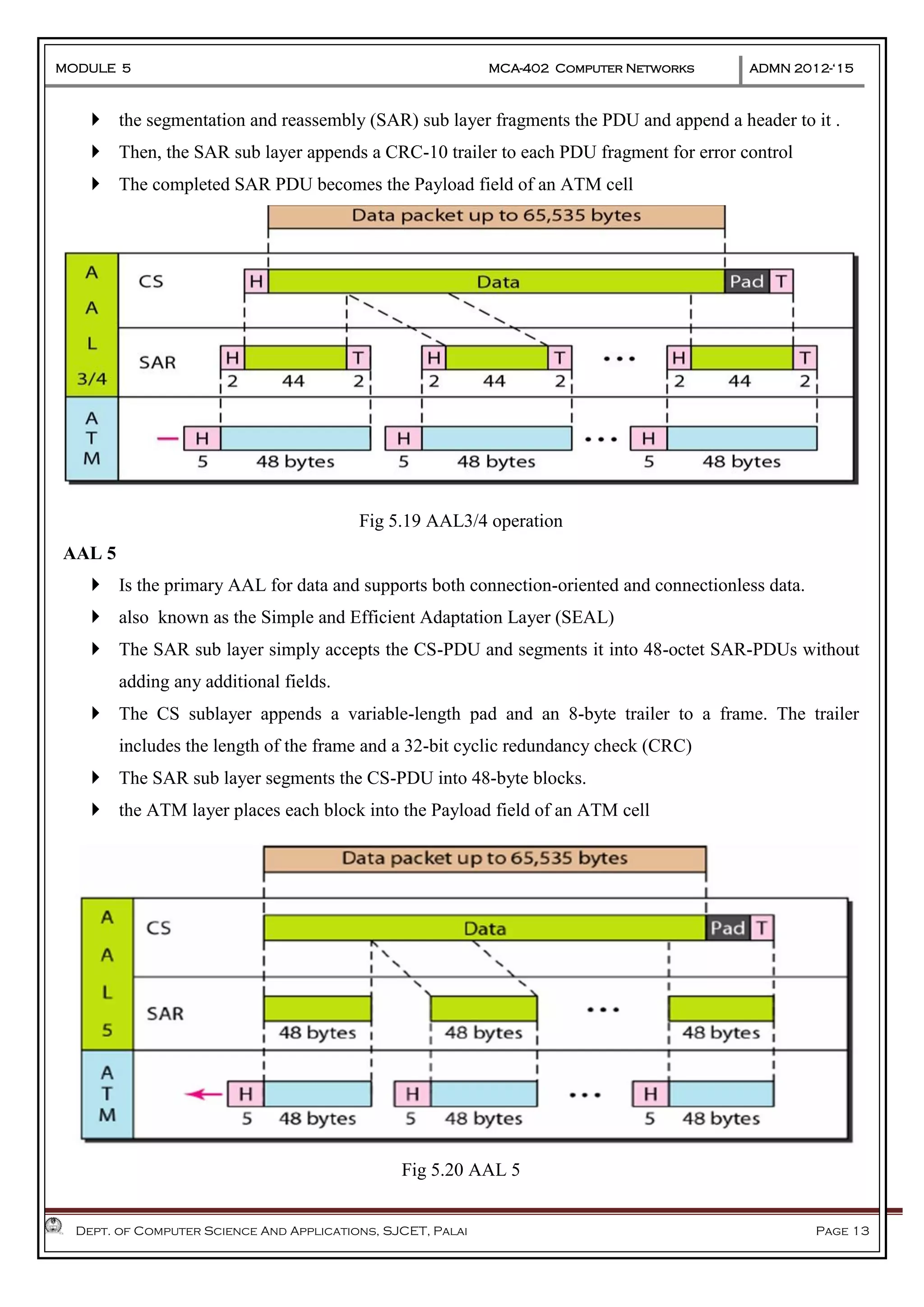
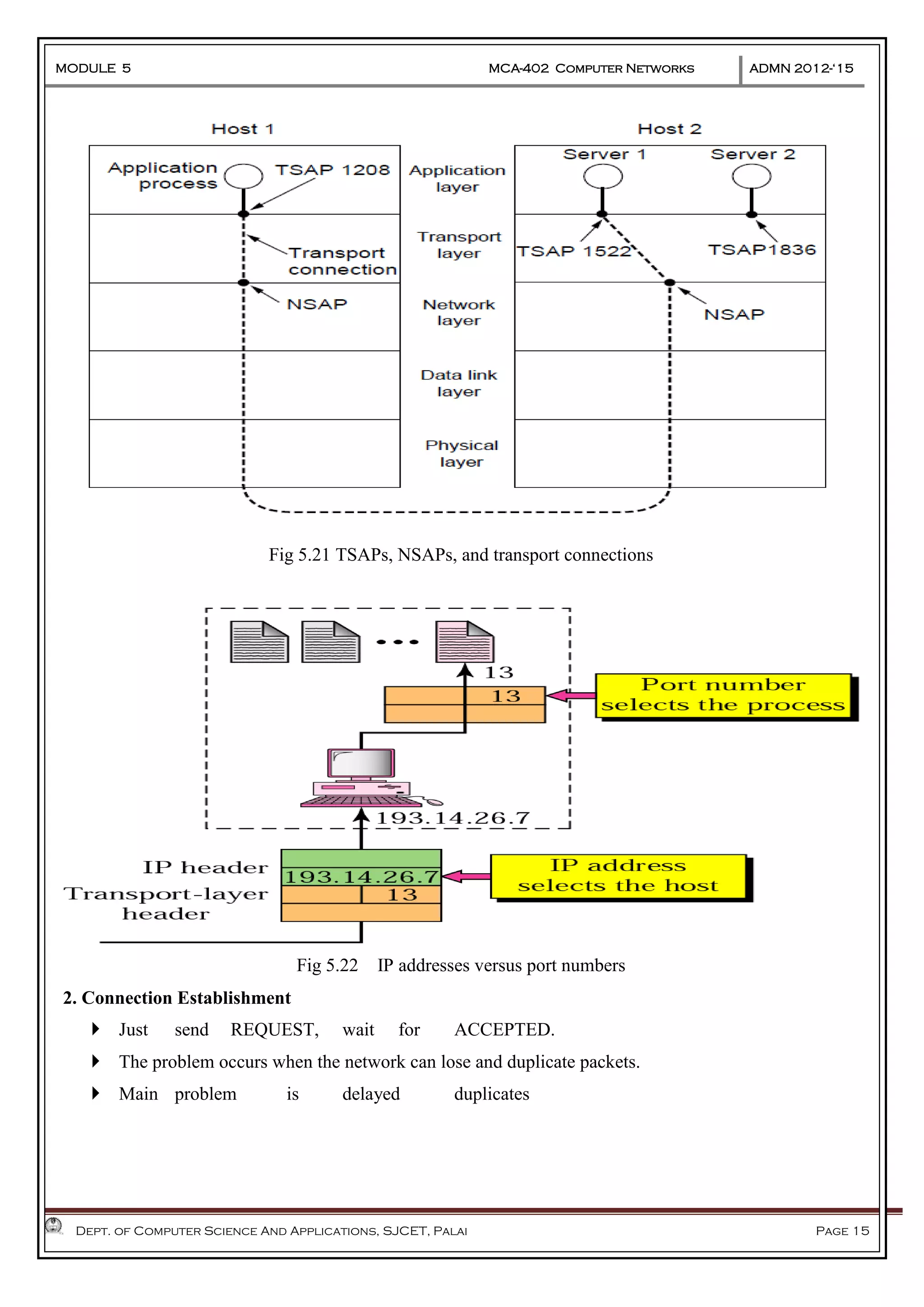
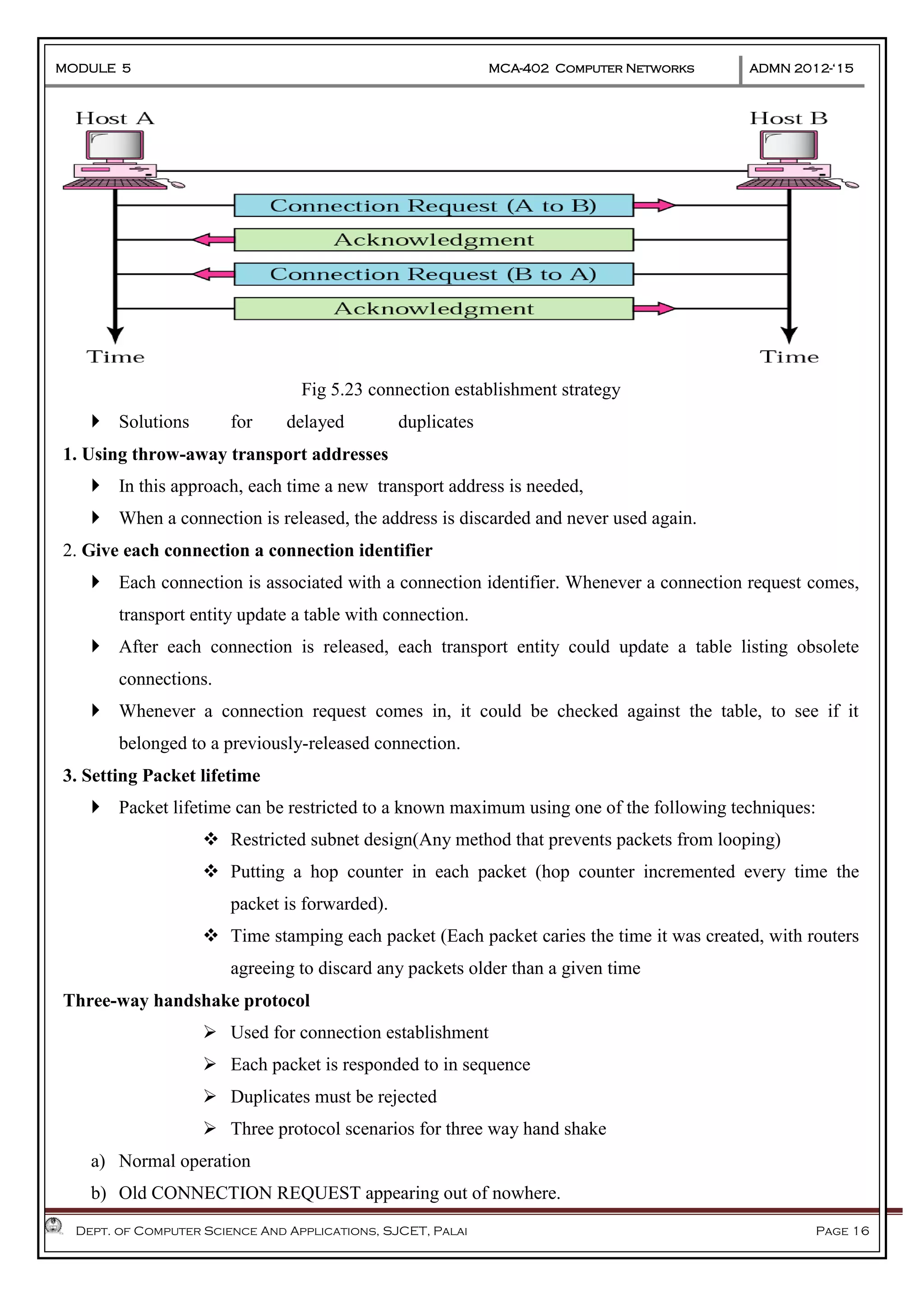
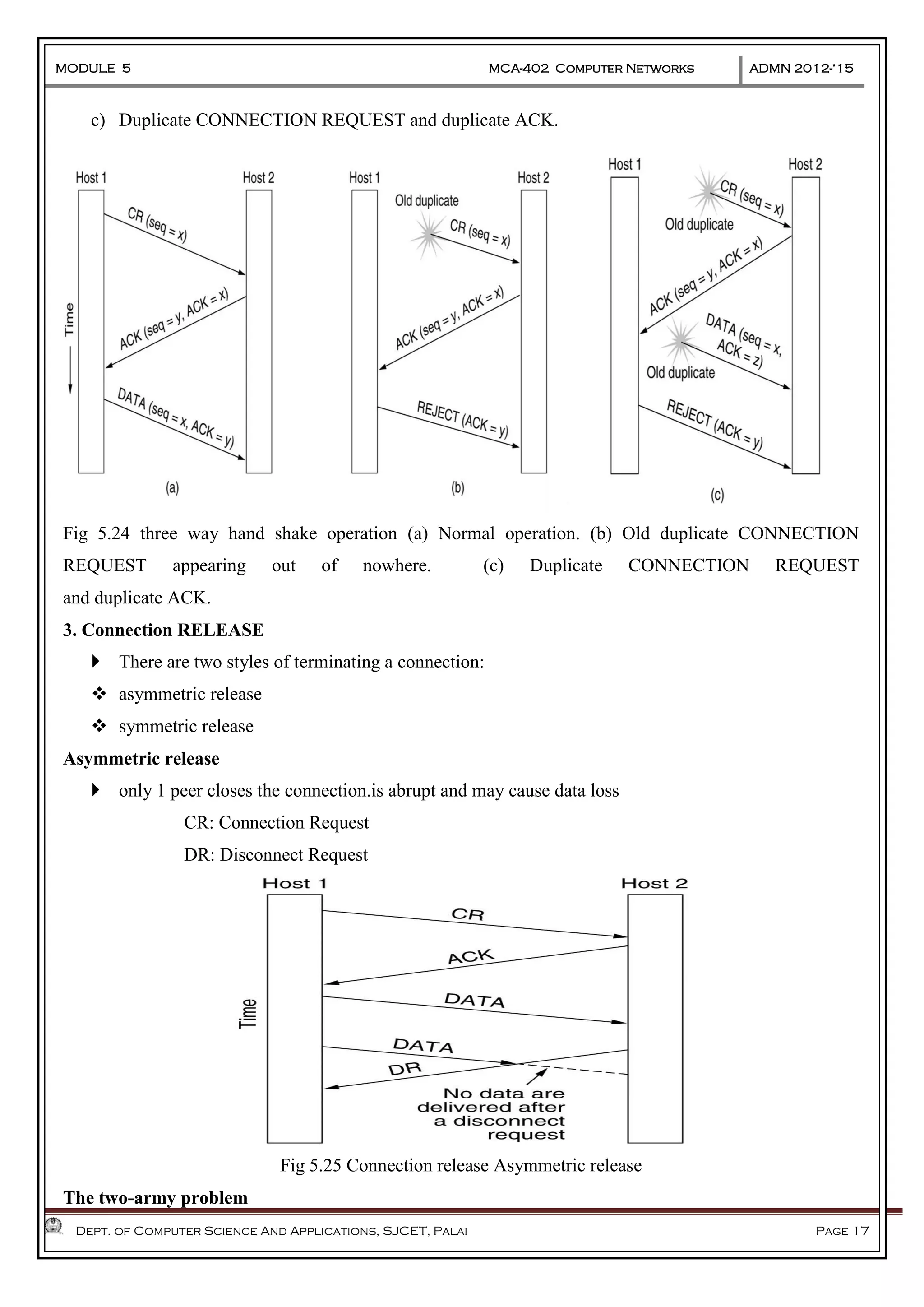
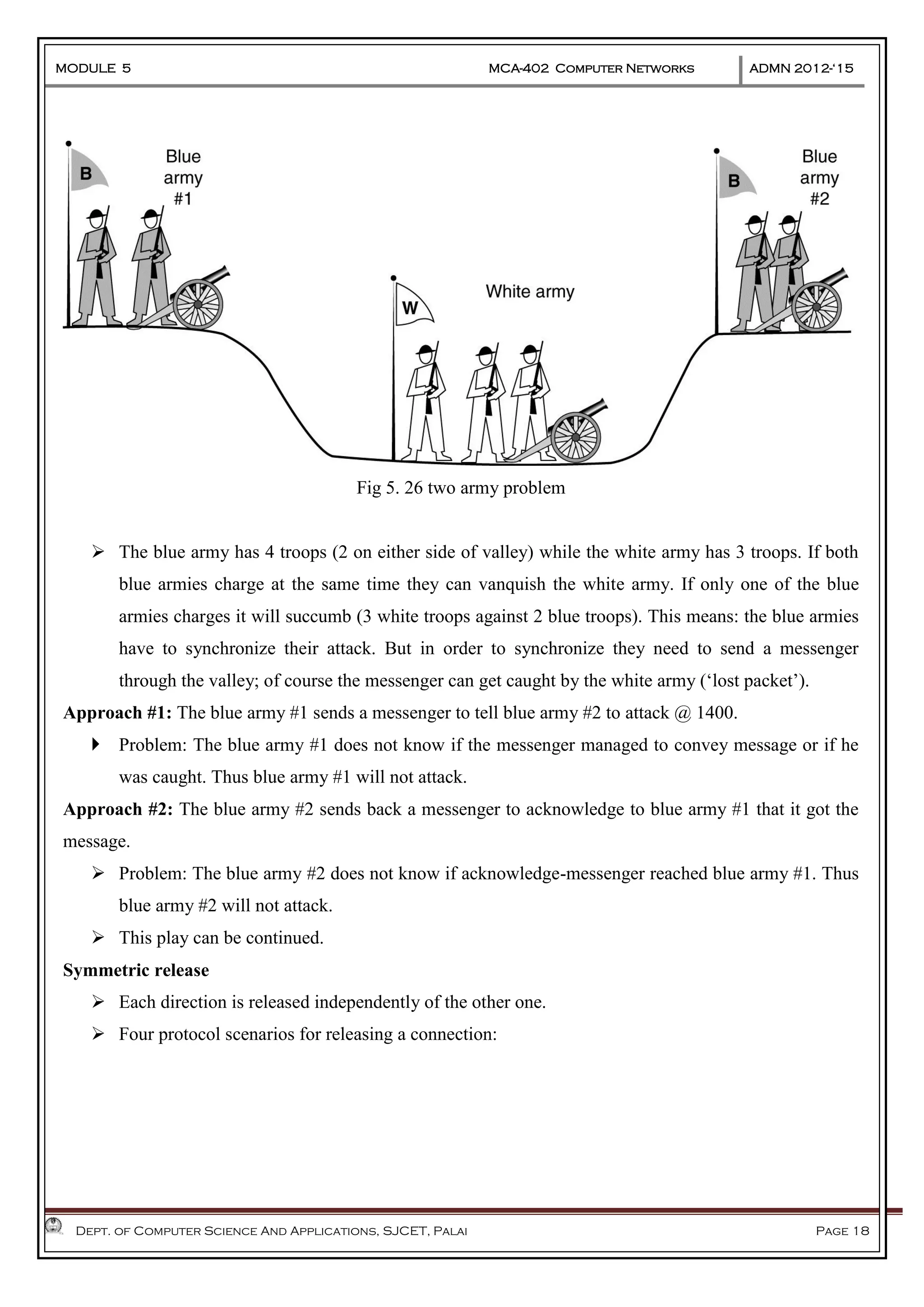
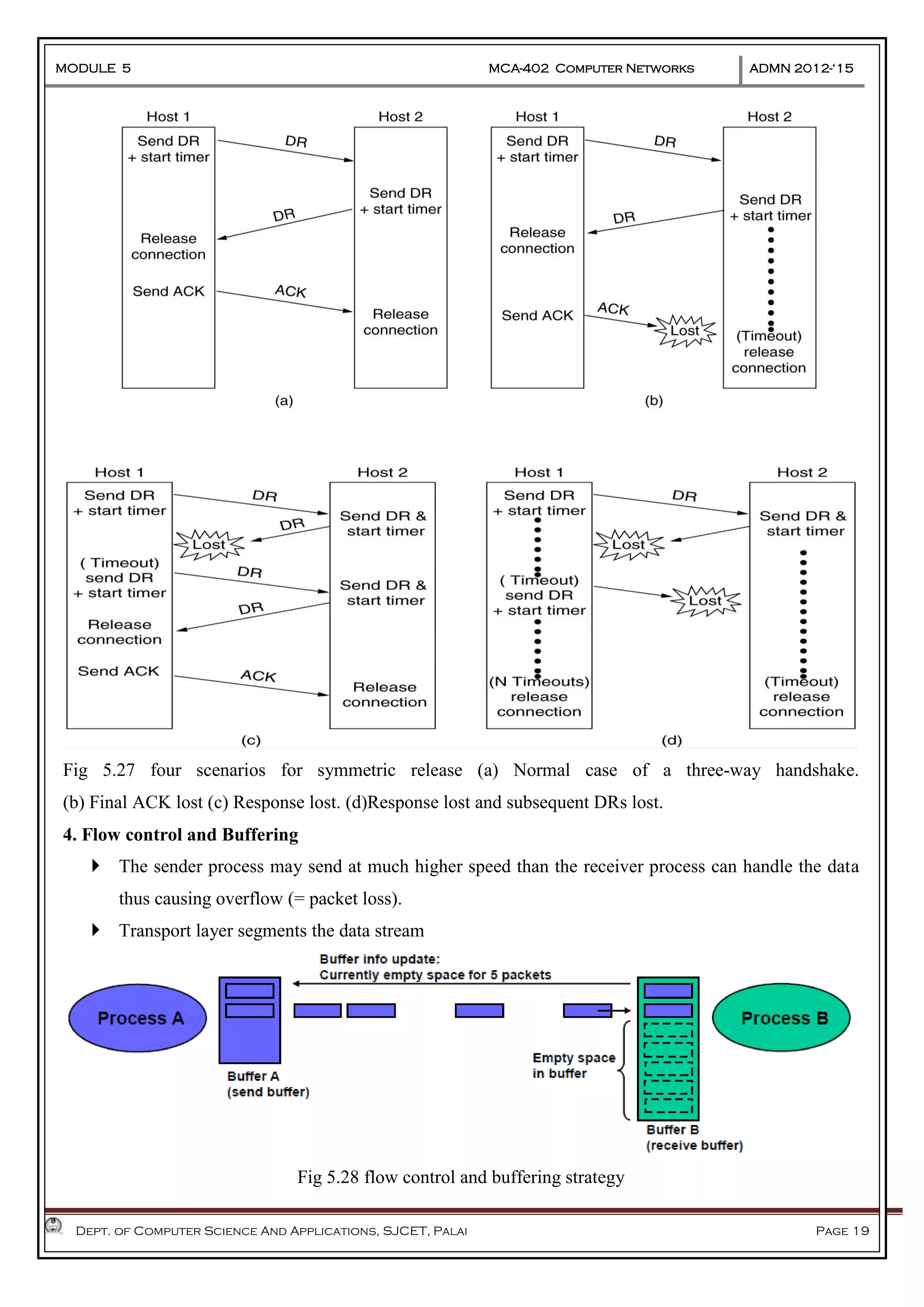
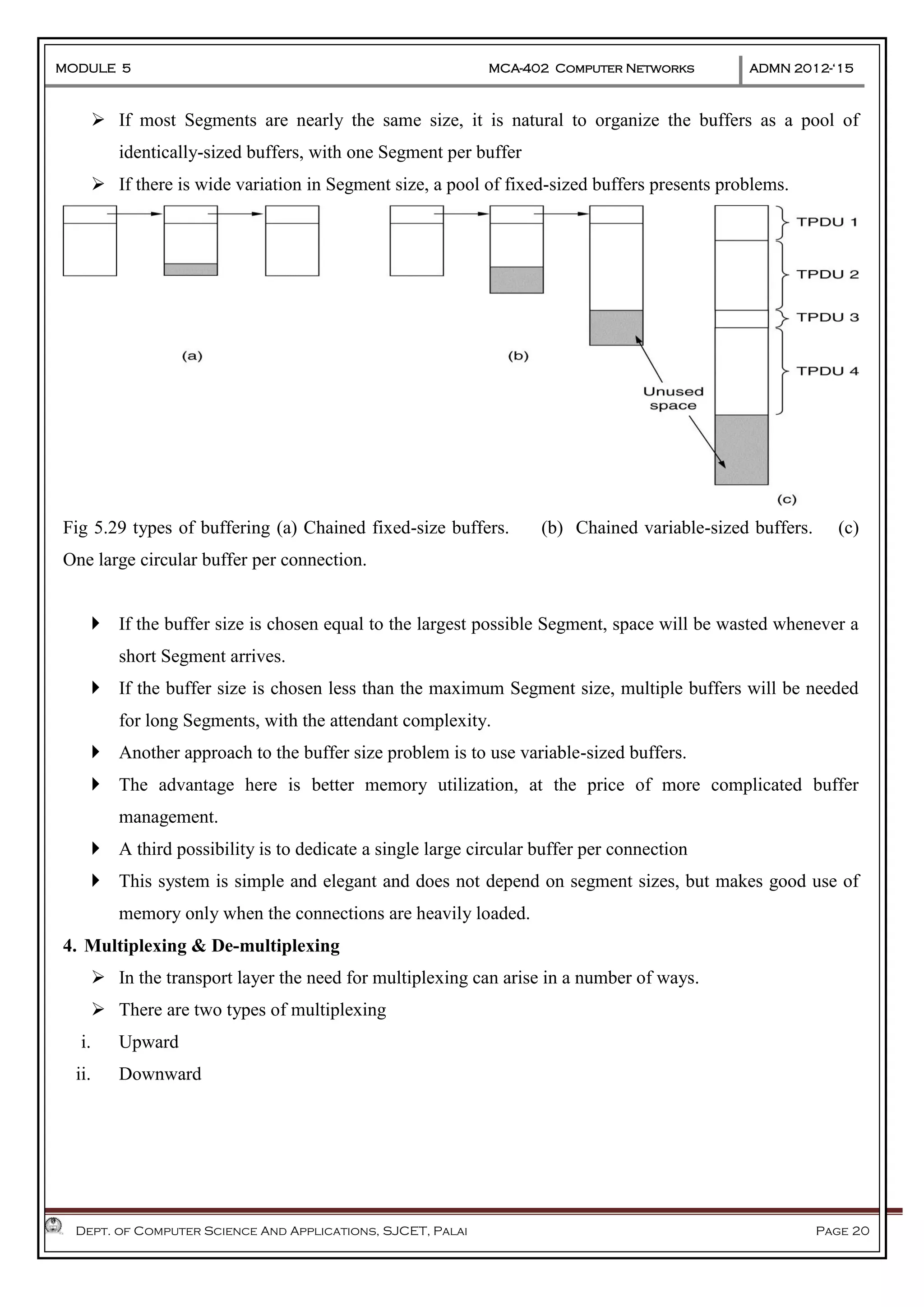
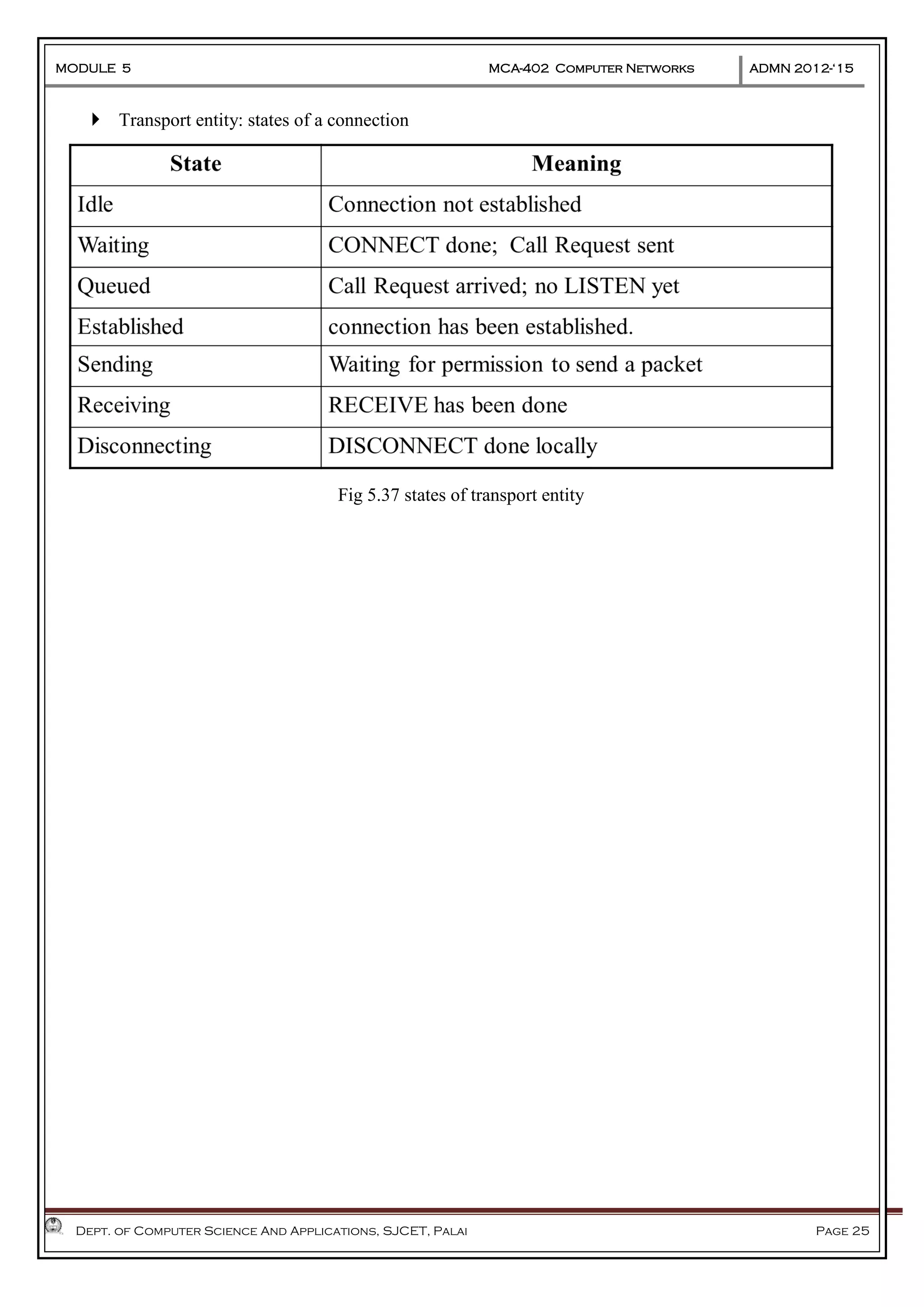
The document discusses Frame Relay and Asynchronous Transfer Mode (ATM) as WAN protocols that operate at the physical and data link layers, emphasizing their structure, functionality, and the types of connections they establish. Frame Relay uses variable-size data units called frames and offers switched and permanent virtual circuits for communication, while ATM employs fixed-size packets called cells to facilitate multiplexing and manage various types of traffic efficiently. Additionally, the transport layer is explored, detailing its role in providing reliable user connections and efficient transfer of data across networks.