The document discusses mobile ad hoc networks (MANETs) and their vulnerability to attacks such as vampire and DDoS attacks, emphasizing the need for security solutions. It proposes a trust-based approach to mitigate these risks by forming clusters of nodes, identifying trusted nodes based on energy levels, and implementing methods to detect and recover from malicious activities. Additionally, it surveys existing literature on trust-based routing protocols for MANETs, highlighting various methods to improve network security and performance.



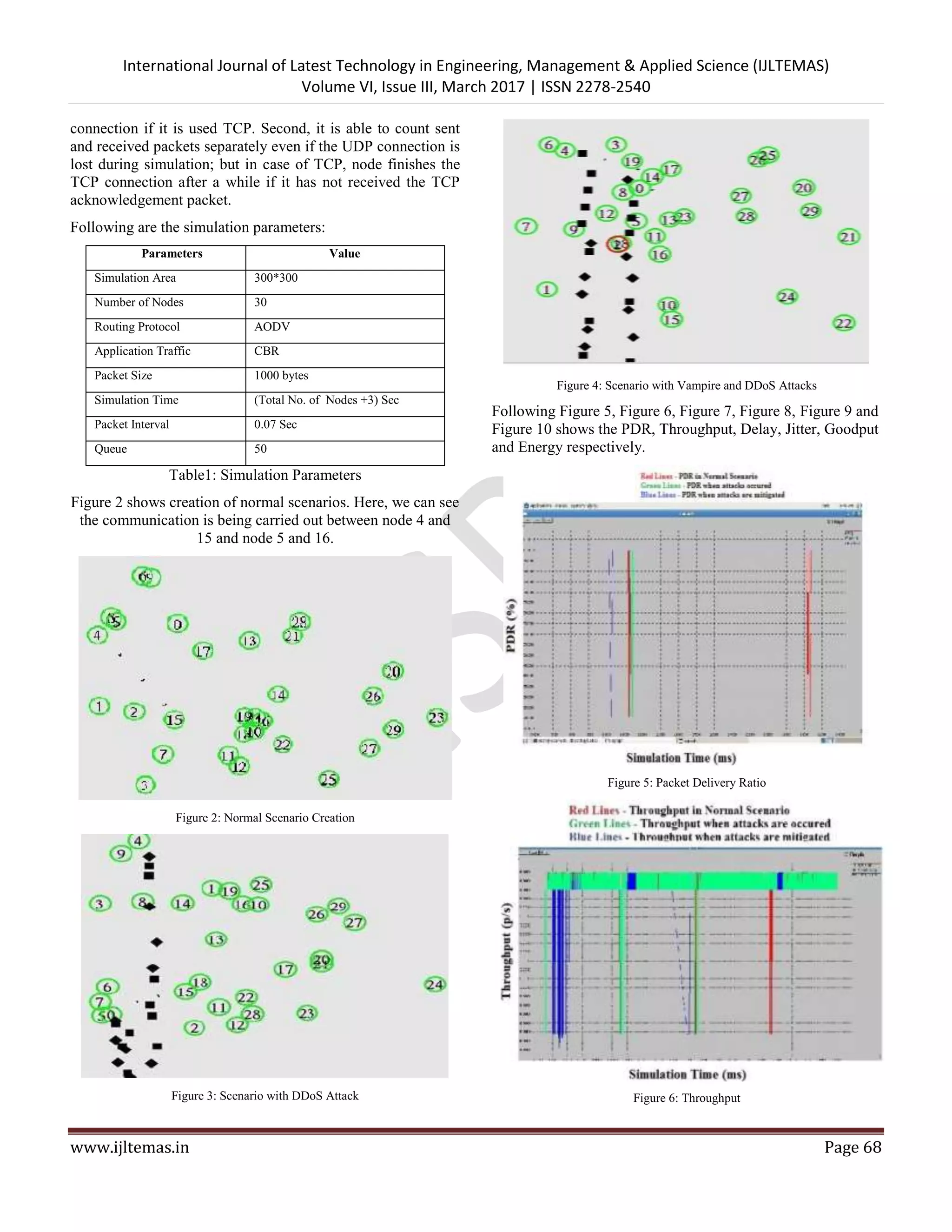
![International Journal of Latest Technology in Engineering, Management & Applied Science (IJLTEMAS) Volume VI, Issue III, March 2017 | ISSN 2278-2540 www.ijltemas.in Page 67 through these trusted nodes. That is trusted node in each cluster send the received packets to the destination or next trusted node in another cluster and so on. To find out the malicious nodes in the network, send and received packets as well as route response is calculated. Then the number of packets (send & received) compared to the threshold value, if it is less than the threshold value then particular node is considered as a malicious node. Cluster based network formation: The number of cluster depends on the total number of nodes in the network. Here maximum number of nodes in the cluster is considered as 10. To place the node in the cluster, the value of x and y coordinates of each cluster are determined to make sure that each x and y coordinates of each cluster to be within the specified range. For example, for a network of 300m x 300m, if the number of clusters are 3 then each node will be placed in 100m x 100x area. Selection of Trusted nodes: After formation of the network, the trusted nodes are determined (Nodes having highest energy). To choose the random energy of each node, rand () function is used. For example, expr rand ()*1000. We can also check the energy of each node by using, set e [$node (2) energy]; then print the value of e. After calculating the initial energy of each node in each cluster, nodes with highest and second highest energy have been chosen. These two are called as trusted nodes in each cluster. These nodes with highest and second highest energy are referred to as cluster head one and cluster head two respectively. All the communication will be carried out using these cluster heads. Counting packets (send & received) along with Route responses: The send and received packets are calculated for each node; also route response of each node is determined. This information is helpful to determine the malicious node in the network. Node having less route response and send packets may be considered as a malicious node. Comparison of packets with threshold to get malicious nodes: To get the malicious node, the number of packets (send & received) is compared with the threshold value to determine the malicious nature of any node. While calculating, the route response is also taken into consideration. The threshold value is set as 30. Here, we take into account the DDoS attack. This comparison is playing a vital role to determine the DDoS attacks. Routing table update: After determining the trusted nodes and malicious nodes in the network, the information is updated in the routing table. According to the routing table, most trusted path is selected for communication which helps to improve the network life as well as network performance. Figure 1: Work Flow V. PROPOSED WORK In the proposed work, the cluster based network is formed. Ten nodes are considered in each cluster. Total number of cluster is based on the total number of nodes in the network. Two nodes having maximum energy have been selected in each cluster. Selection of each cluster: Max_cluster=expr[val(nn)/Max_Node_in_Cluster] Here, val (nn) is the total number of nodes in the network and maximum ten nodes are considered in each cluster. Also X and Y coordinates (Maximum values of X and Y) have been calculated for each cluster: Set max_x[expr[expr $CURRENT_CLUSTER+1]* $val (x)/$MAX_CLUSTERS] To calculate the energy of nodes, rand() function is used. The two nodes with highest energies in each cluster have been calculated. These two nodes are called Cluster Head 1 and Cluster Head 2. In between Cluster Head 1 and Cluster Head 2, node with highest energy is selected as CLUSTER HEAD in each cluster. VI. SECURITY AND PERFORMANCE ANALYSIS For the simulation purpose Network Simulator 2 (NS-2.35) has been used. Simulation parameter are as follows: The simulation area is 300 m by 300 m. AODV protocol has been used, since AODV protocol is loop free, avoid counting to infinity problem and does not need any central administration system to handle routing process. The UDP is used as application traffic. UDP has two advantages over TCP: First, the source code continuously sends UDP packets even if malicious nodes drop them, while node finishes the](https://image.slidesharecdn.com/64-70-170405090220/75/Mitigating-Various-Attacks-in-Mobile-Ad-hoc-Networks-Using-Trust-Based-Approach-4-2048.jpg)
![International Journal of Latest Technology in Engineering, Management & Applied Science (IJLTEMAS) Volume VI, Issue III, March 2017 | ISSN 2278-2540 www.ijltemas.in Page 69 Figure 7: Goodput Figure 8: Delay Figure 9: Jitter Figure 10: Energy VIII. CONCLUSION AND FUTURE WORK The Vampire and DDoS attacks are resources consumption attacks which drain the energy of node in the network. This draining of the energy of the nodes will affect the packet forwarding process which in turn might degrade the performance of the underlying network. Here we have considered small network of 30 nodes which are divided into three clusters; each cluster included ten nodes. Simulation have been performed and various parameters have been considered. From the result, we can conclude that the Vampire and DDoS attacks have been mitigated using trust based approach. The future work is to use the proposed technique to mitigate Vampire and DDoS attacks with more number of nodes and increasing the simulation area and also for other types of attacks. REFERENCES [1]. Pallavi Kharti. Using Identity and Trust with Key Management for achieving Security in Ad-hoc network; IEEE; 978-1-4799-2572- 8/2014. [2]. Sandeep A. Throat and P.J.Kulkarni. Design Issues in Trust Based Routing for MANET; IEEE; July 11-13, 2014. [3]. Jenita T.and Jayshree P. Distributed Trust Node Selection for Secure Group Communication in MANET; IEEE; 978-1-4799- 4363-0/2014. [4]. H.Bharani , M.Kanchana, S,B.Dhivya , V.Kavitha and I.Vinnarasi Tharania . Vampire Attacks: Draining Life from Wireless Ad-Hoc Sensor Network; IJSTE; Vol. 1, Issue 1, July 2014. [5]. Prof.Ramya S. Pure, Gauri Patil and Manzoor Hussaion Hussaion . Trust based solution using counter strategies for Routing attacks in MANET; IJISET; Vol. 1, Issue 1, July 2014. [6]. G. Vijayanad and R. Muralidharan. Overcome Vampire Attacks Problem In Wireless Ad-Hoc Sensor Network By Using Distance Vector Protocols; IJCSMA; Vol. 2, Issue. 1, pg. 115-120, January- 2014. [7]. Naveen Kumar Gupta and Kavita Pandey. Trust Based Ad-hoc On Demand Routing Protocol for MANET; IEEE; 978-1-4799-0192- 0/2013. [8]. Naveen Kumar Gupta and Amit Garg. Trust and shortest path selection based routing protocol for mobile ad-hoc networks; IJCA; Vol. 76, No.12, August 2013.](https://image.slidesharecdn.com/64-70-170405090220/75/Mitigating-Various-Attacks-in-Mobile-Ad-hoc-Networks-Using-Trust-Based-Approach-6-2048.jpg)
![International Journal of Latest Technology in Engineering, Management & Applied Science (IJLTEMAS) Volume VI, Issue III, March 2017 | ISSN 2278-2540 www.ijltemas.in Page 70 [9]. Pallavi Kahtri and Aamir ohammed. TDSR: Trust Based DSR Routing Protocol for Securing MANET; International Journal of Networking and Parallel Computing. Vol. 1, Issue 3, January 2013. [10]. Radha Krishna Bar, Jyotsna Kumar Mandal and Moirangthem Marjith Singh. Quality of Service of mobile ad-hoc network through Trust based AODV routing protocol by exclusion of Black-hole attack; Science Direct; CIMTA 2013. [11]. Sumathy Subramaniam, R. Saravanan and Pooja K. Prakash. Trusted Based Routing to Improve Network Lifetime of Mobile Ad-hoc Networks: Journal of Computing and Information Technology; CIT 21, 2013. [12]. Issac Woungang, Mohmmed S. Obaidat, Sanjay Kumar Dhurandher, Han-Chieh Chao and Chris Liu. Trust enhanced Message Security Protocol for Mobile Ad-hoc Networks; IEEE; ICC 2012. [13]. Ahmed M. Abd El-Haleem and Ihab A. Al.TRIUMF: Trust-Based Routing Protocol with control degree of Selfishness for Securing MANET against Packet Dropping Attack; International Journal of Computer Science; Vol. 8, Issue 4, No. 1, July 2011. [14]. N. Bhalaji and Dr. A. Shanmugam. Defence Strategy using Trust based model to mitigate active attacks in DSR based mobile ad- hoc network; Journal of Advances in Information Technology; Vol. 2, No. 2, May 2011. [15]. Zhen Yan, Peng Zhang and Teemupekka Virtanen. Trust Evaluation Based Security Solution in Ad-hoc Networks; 2011.](https://image.slidesharecdn.com/64-70-170405090220/75/Mitigating-Various-Attacks-in-Mobile-Ad-hoc-Networks-Using-Trust-Based-Approach-7-2048.jpg)