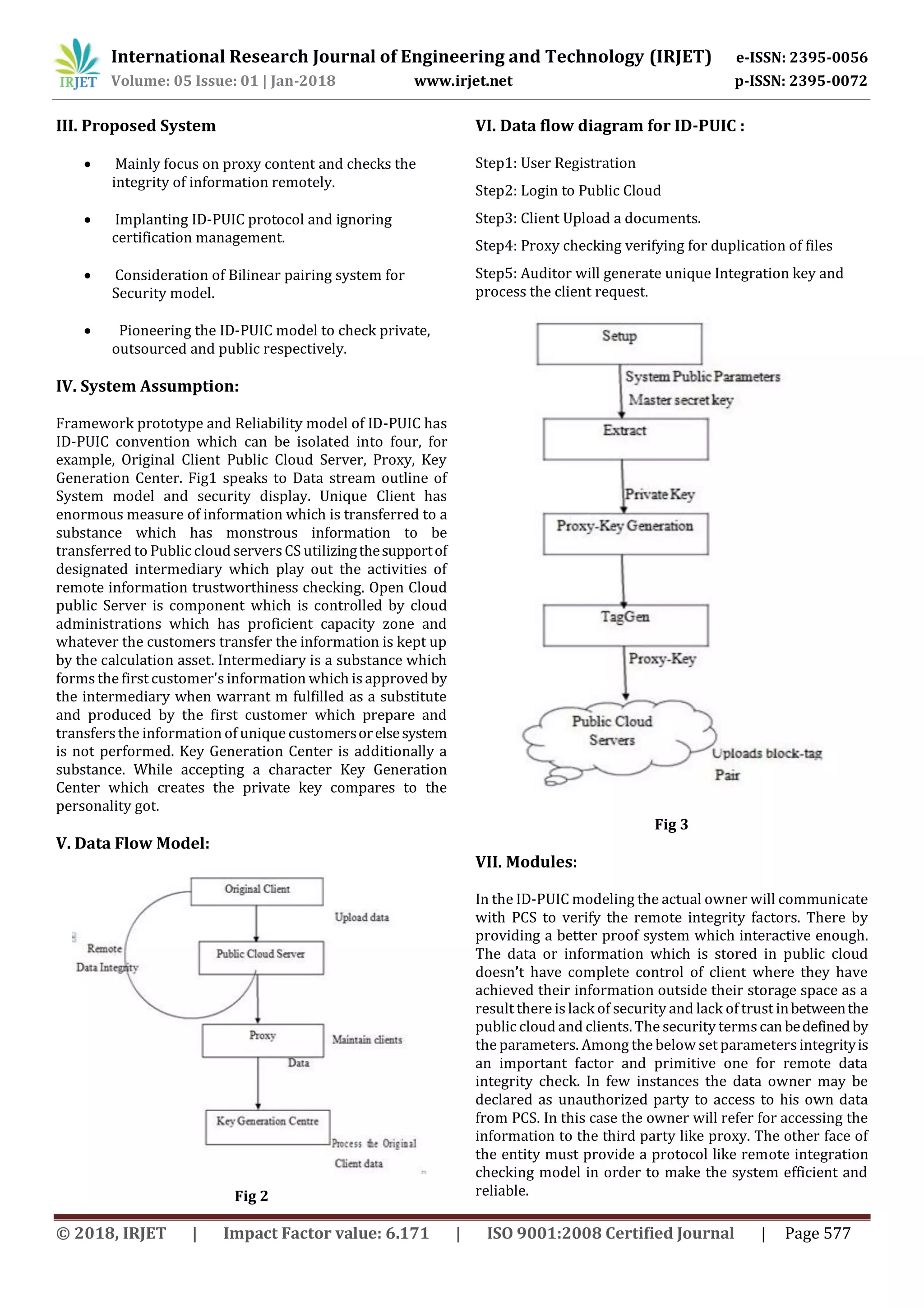
This document proposes an algorithm called ID-PUIC for remote data uploading and integrity checking in public clouds. It aims to address security issues when clients store sensitive data in public clouds, which they do not fully control. The proposed system uses a proxy to upload client data and perform remote integrity checks with the public cloud server. It introduces a protocol for the proxy to generate tags for file blocks and upload them along with the data for integrity verification. The ID-PUIC algorithm is more efficient for integrity checking than existing solutions as it ignores certificate management and uses bilinear pairings for security. The document outlines the system model, data flow, modules including key generation, tag generation and proofs to check integrity remotely between the client and public cloud server


![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 01 | Jan-2018 www.irjet.net p-ISSN: 2395-0072 © 2018, IRJET | Impact Factor value: 6.171 | ISO 9001:2008 Certified Journal | Page 579 community. The work specifies ID-PUIC's system prototype and framework illustrate. By then, the initial strong ID-PUIC procedure is used by compiling the bilinear pairingssystem. The robust ID-PUIC is provably privy and secured, and coercive by using the conventional securityconfirmationand capable of examine. On the other session, the suggested ID- PUIC manner to recognize privy remote trusted data checking, appointed remote data appropriateness checking and available remote data uniqueness and genuineness checking in aspect of the principal client's endorsement. IX. REFERENCES: [1] Z. Fu, X. Sun, Q. Liu, L. Zhou, and J. Shu, “Achieving efficient cloud search services: Multi-keywordrankedsearch over encrypted cloud data supporting parallel computing,” IEICE Trans. Commun., vol. E98-B, no. 1, pp. 190–200, 2015. [2] Y. Ren, J. Shen, J. Wang, J. Han, and S. Lee, “Mutual verifiable provable data auditing in public cloud storage,” J. Internet Technol., vol. 16, no. 2, pp. 317–323, 2015. [3] M. Mambo, K. Usuda, and E. Okamoto, “Proxy signatures for delegating signing operation,” in Proc. CCS, 1996, pp. 48– 57. [4]E.-J. Yoon, Y. Choi, and C. Kim, “New ID-based proxy signature scheme with message recovery,” in Grid and Pervasive Computing (LectureNotes in Computer Science), vol. 7861. Berlin, Germany: Springer- Verlag, 2013, pp. 945– 951. [5]B.-C. Chen and H.-T. Yeh, “Secure proxy signatureschemes from the weil pairing,” J. Supercomput., vol. 65, no. 2, pp. 496–506, 2013. [6]X. Liu, J. Ma, J. Xiong, T. Zhang, and Q. Li, “Personal health records integrity erification using attribute based proxy signature in cloud computing,” in Internet and Distributed Computing Systems (Lecture Notes in Computer Science), vol. 8223. Berlin, Germany: Springer- Verlag, 2013, pp. 238– 251. [7] H. Guo, Z. Zhang, and J. Zhang, “Proxy re-encryption with unforgeable re-encryption keys,” in CryptologyandNetwork Security (Lecture Notes in Computer Science), vol. 8813. Berlin, Germany: Springer-Verlag,2014, pp. 20–33. [8] E. Kirshanova, “Proxy re-encryption from lattices,” in Public-KeyCryptography (Lecture Notes in Computer Science), vol. 8383. Berlin, Germany: Springer-Verlag, 2014, pp. 77–94. [9]P. Xu, H. Chen, D. Zou, and H. Jin, “Fine-grained and heterogeneous proxy re-encryption for secure cloud storage,” Chin. Sci. Bull., vol. 59, no. 32, pp. 4201–4209,2014. [10] S. Ohata, Y. Kawai, T. Matsuda, G. Hanaoka, and K. Matsuura, “Re-encryption verifiability: How to detect malicious activities of a proxy in proxy re-encryption,” in Proc. CT-RSA Conf., vol. 9048. 2015, pp. 410–428. [11] G. Ateniese et al., “Provable data possessionatuntrusted stores,” in Proc. CCS, 2007, pp. 598–609. [12] G. Ateniese, R. Di Pietro, L. V. Mancini, and G. Tsudik, “Scalable and efficient provable data possession,” in Proc. SecureComm, 2008, Art. ID 9. [13] C. C. Erway, A. Küpçü, C. Papamanthou, and R. Tamassia, “Dynamic provable data possession,” in Proc. CCS, 2009, pp. 213–222. [14] E. Esiner, A. Küpçü, and Ö. Özkasap, “Analysis and optimization on FlexDPDP: A practical solution for dynamic provable data possession,” Intelligent Cloud Computing (Lecture Notes in Computer Science), vol. 8993. Berlin, Germany: Springer-Verlag, 2014, pp. 65–83. [15]E. Zhou and Z. Li, “An improved remote data possession checking protocol in cloud storage,” in Algorithms and Architectures for Parallel Processing (Lecture Notes in Computer Science), vol. 8631. Berlin, Germany: Springer- Verlag, 2014, pp. 611– 617. [16]H. Wang, “Proxy provable data possession in public clouds,” IEEE Trans. Services Comput., vol. 6, no. 4, pp. 551– 559, Oct./Dec. 2013. [17]H. Wang, “Identity-based distributed provable data possession in multicloud storage,” IEEE Trans. Services Comput., vol. 8, no. 2, pp. 328–340, Mar./Apr. 2015. [18] H. Wang, Q. Wu, B. Qin, and J. Domingo-Ferrer,“FRR:Fair remote retrieval of outsourced private medical records in electronic health networks,” J. Biomed. Inform., vol. 50, pp. 226–233, Aug. 2014. [19]H. Wang, “Anonymous multi-receiver remote data retrieval for pay-TV in public clouds,” IET Inf. Secur., vol. 9, no. 2, pp. 108–118, Mar. 2015. [20]H. Shacham and B. Waters, “Compact proofs of retrievability,” in Proc. ASIACRYPT, vol. 5350. 2008, pp. 90– 107. [21]D. Cash, A. Küpçü, and D. Wichs, “Dynamic proofs of retrievability via oblivious RAM,” in Proc.](https://image.slidesharecdn.com/irjet-v5i1123-180316091849/75/IRJET-An-Algorithmic-Approach-for-Remote-Data-Uploading-and-Integrity-Checking-in-Public-Cloud-4-2048.jpg)