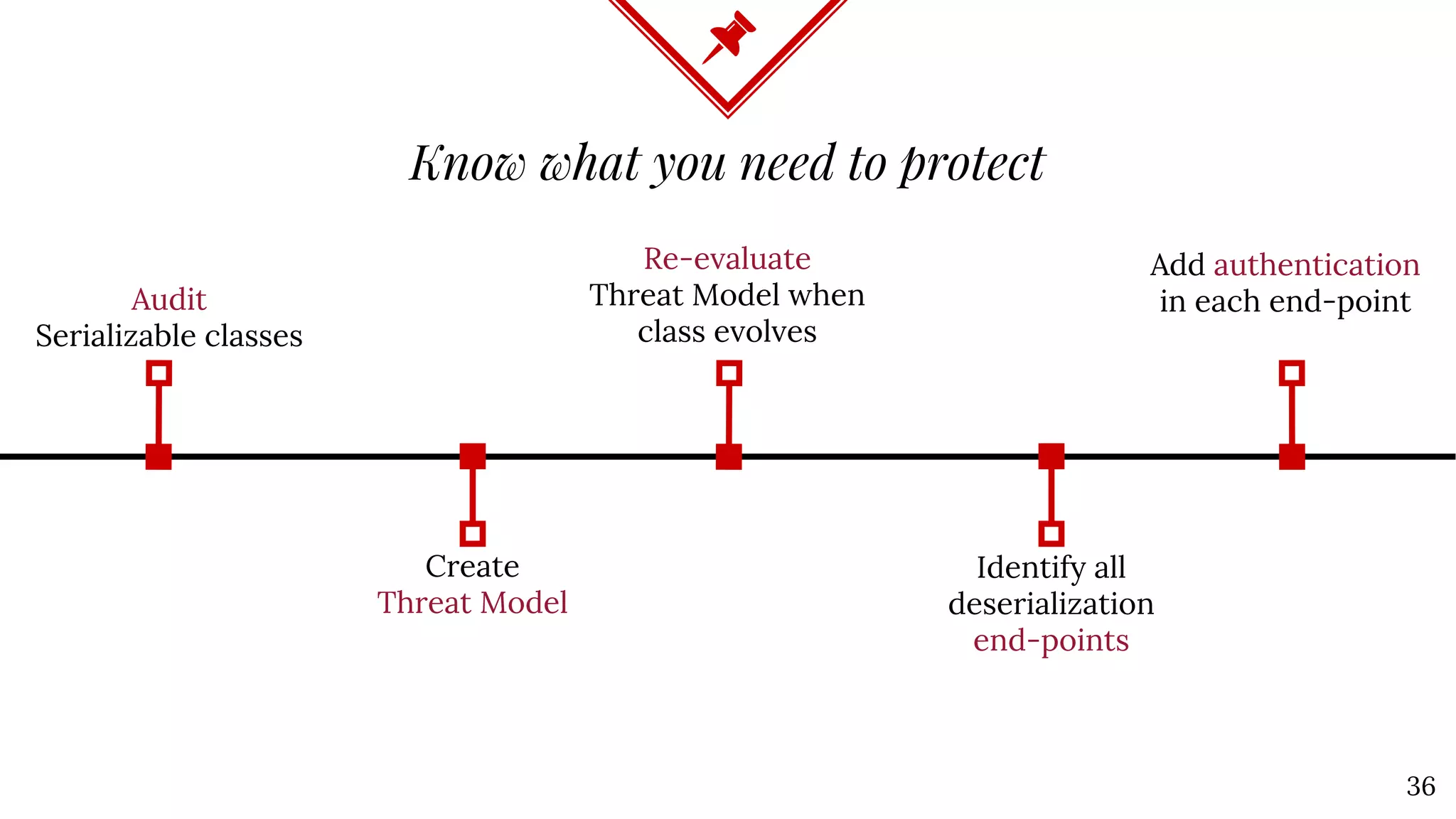
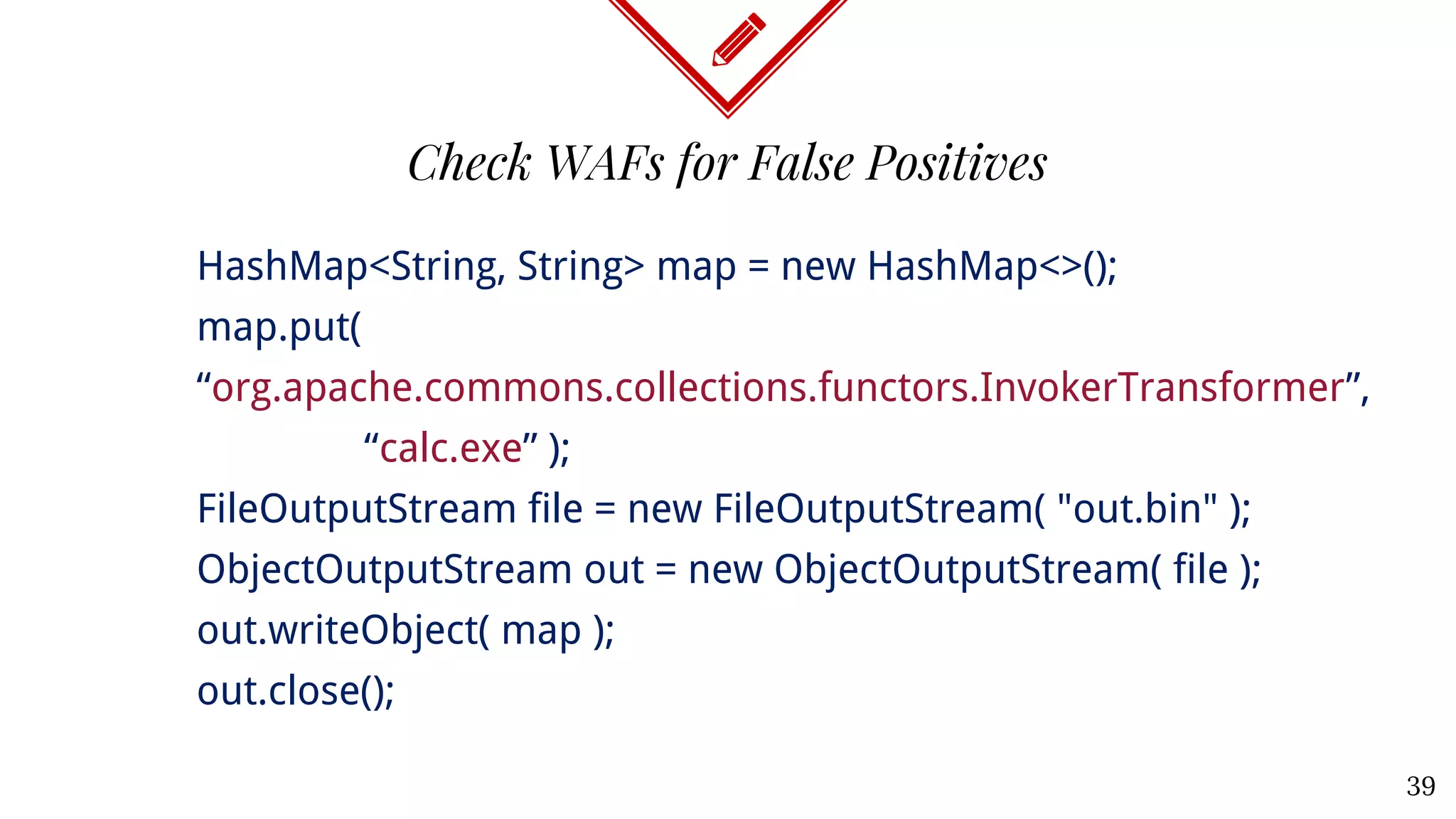
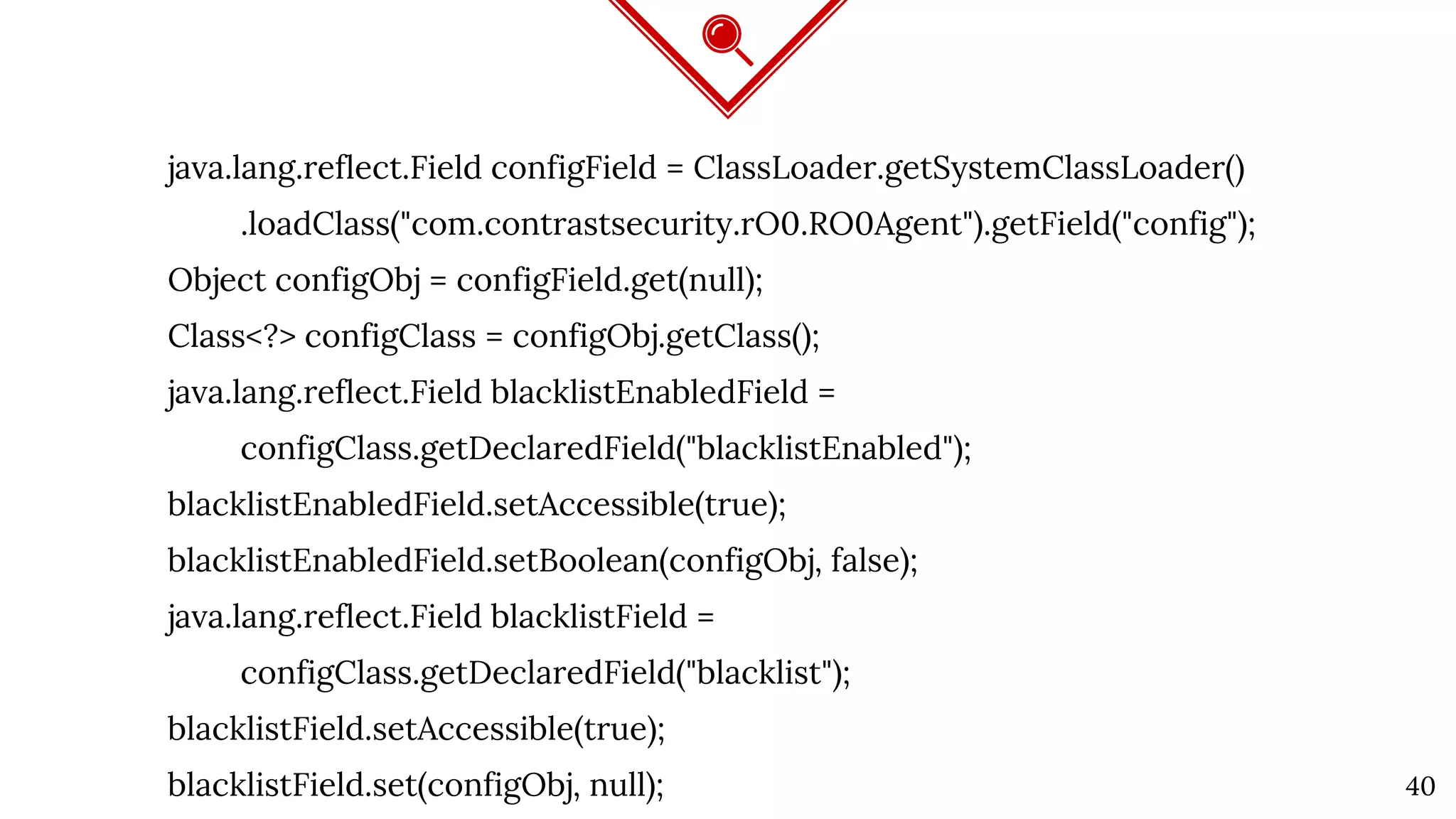
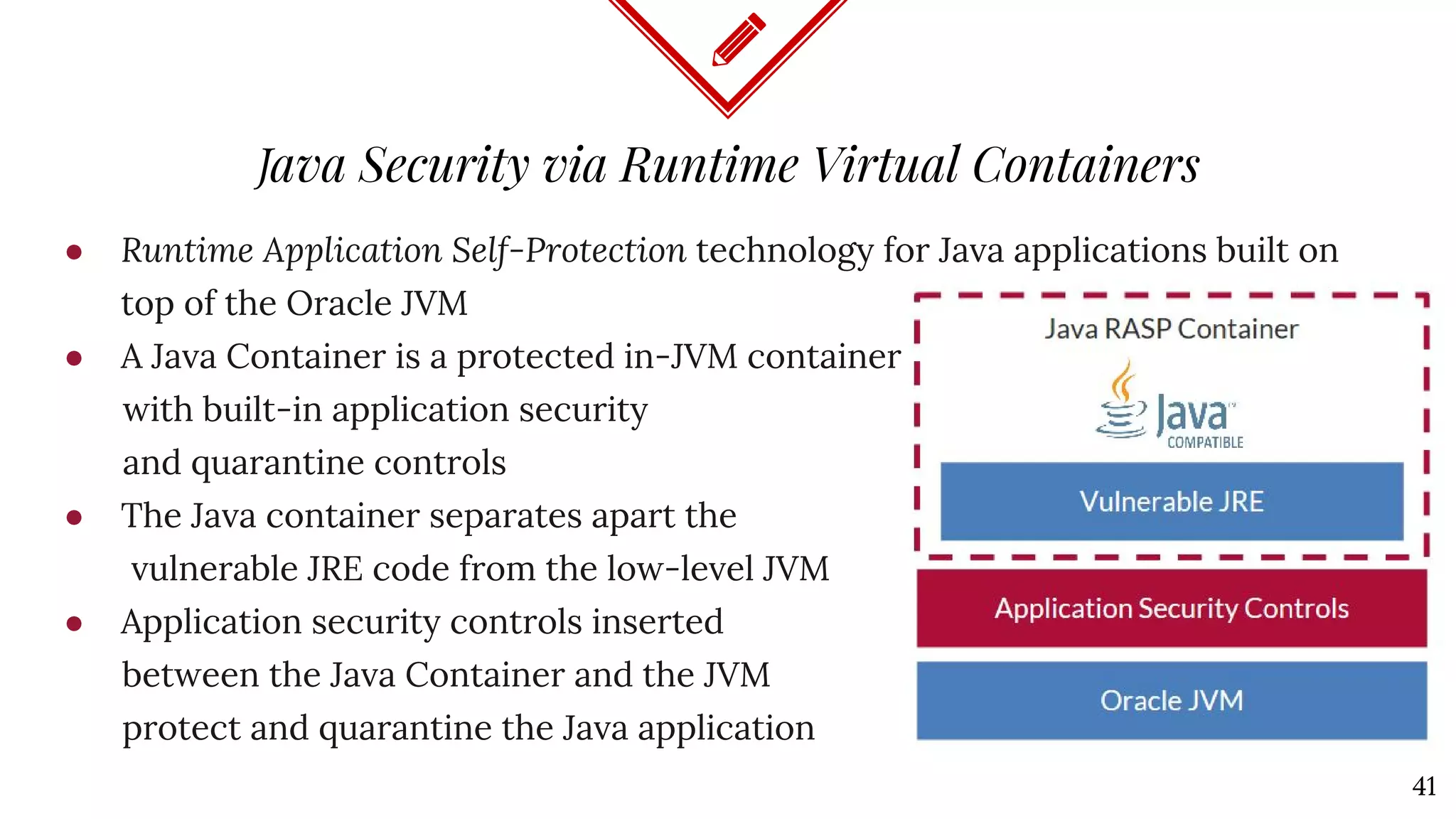
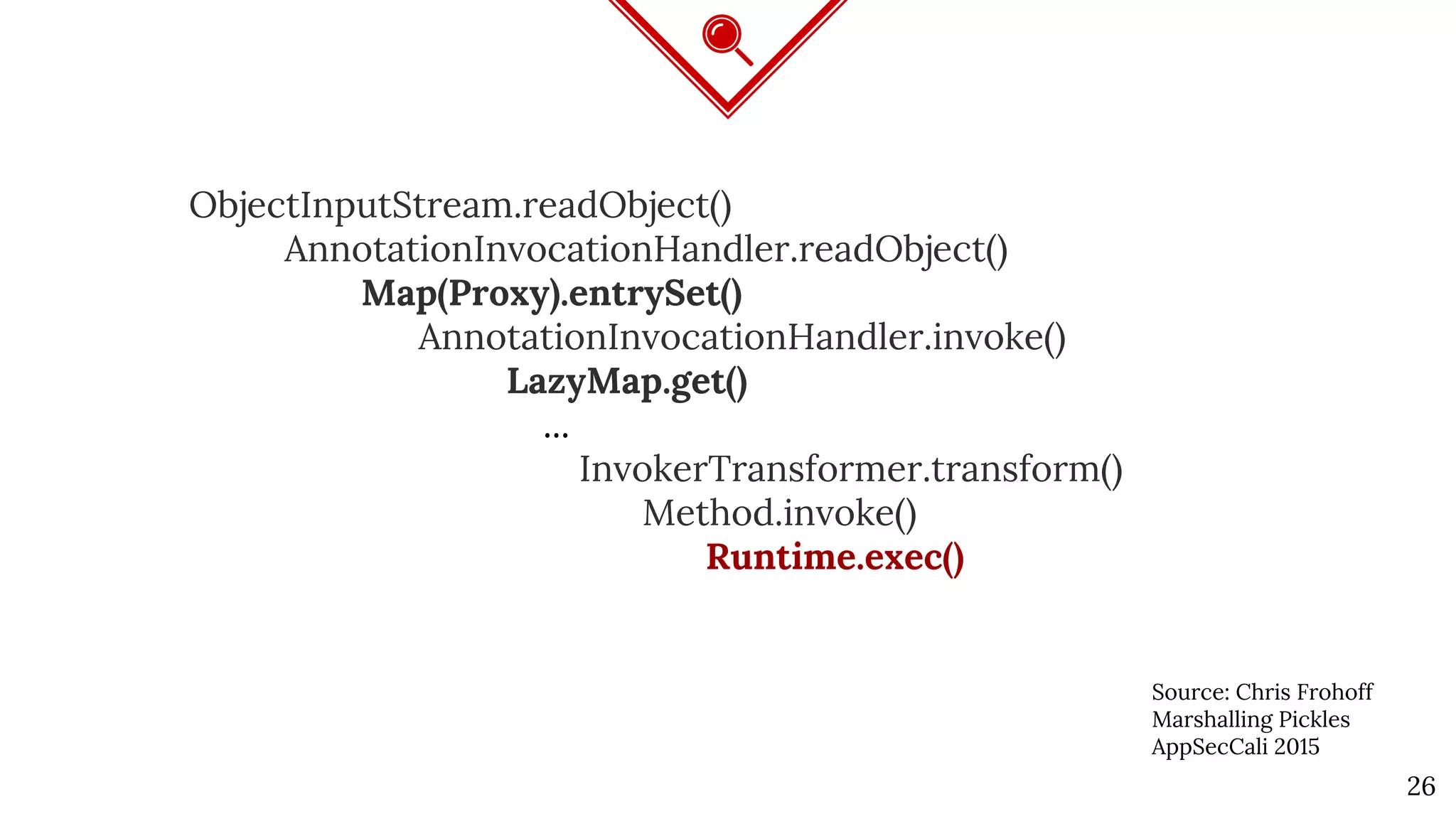
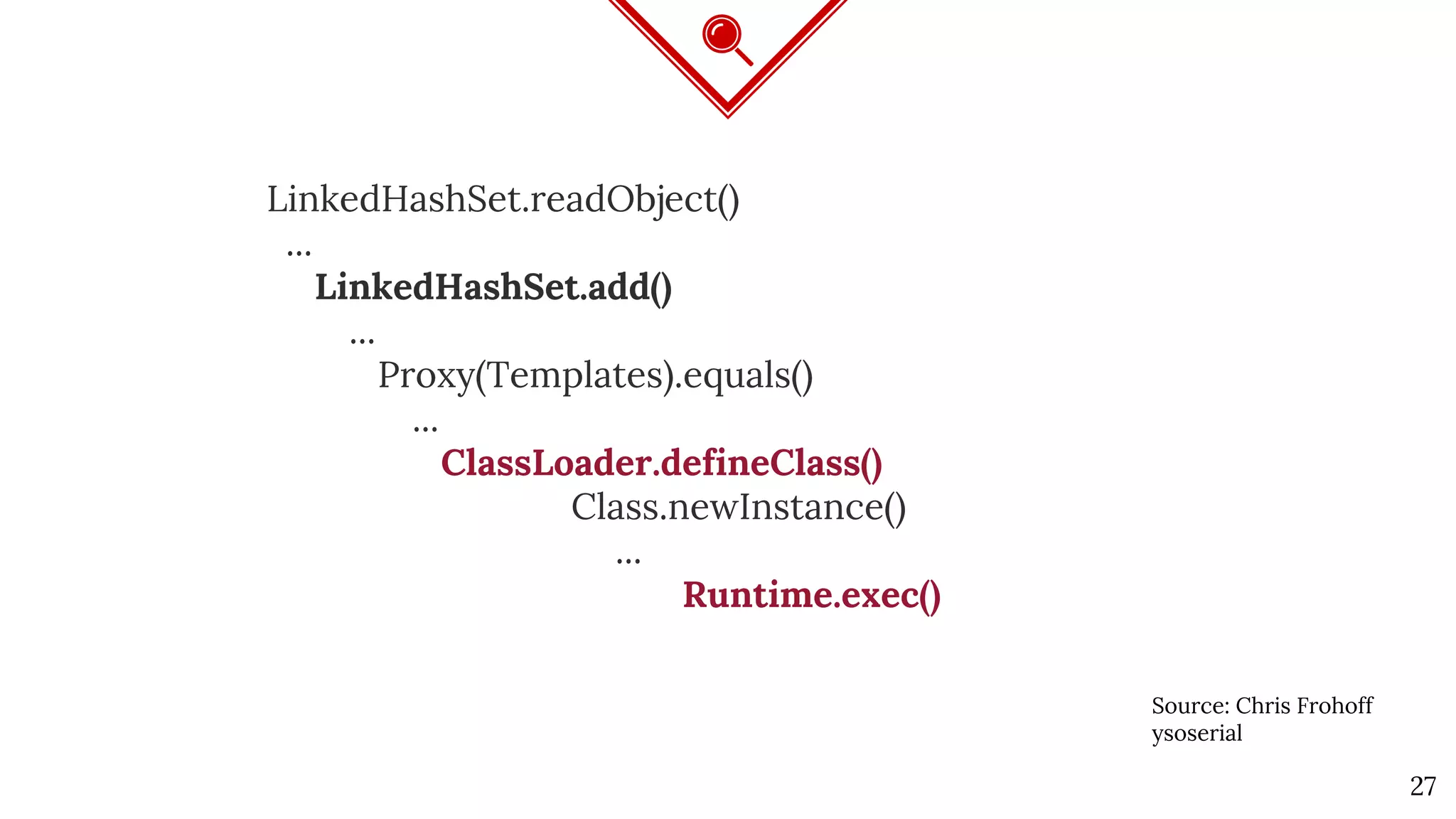
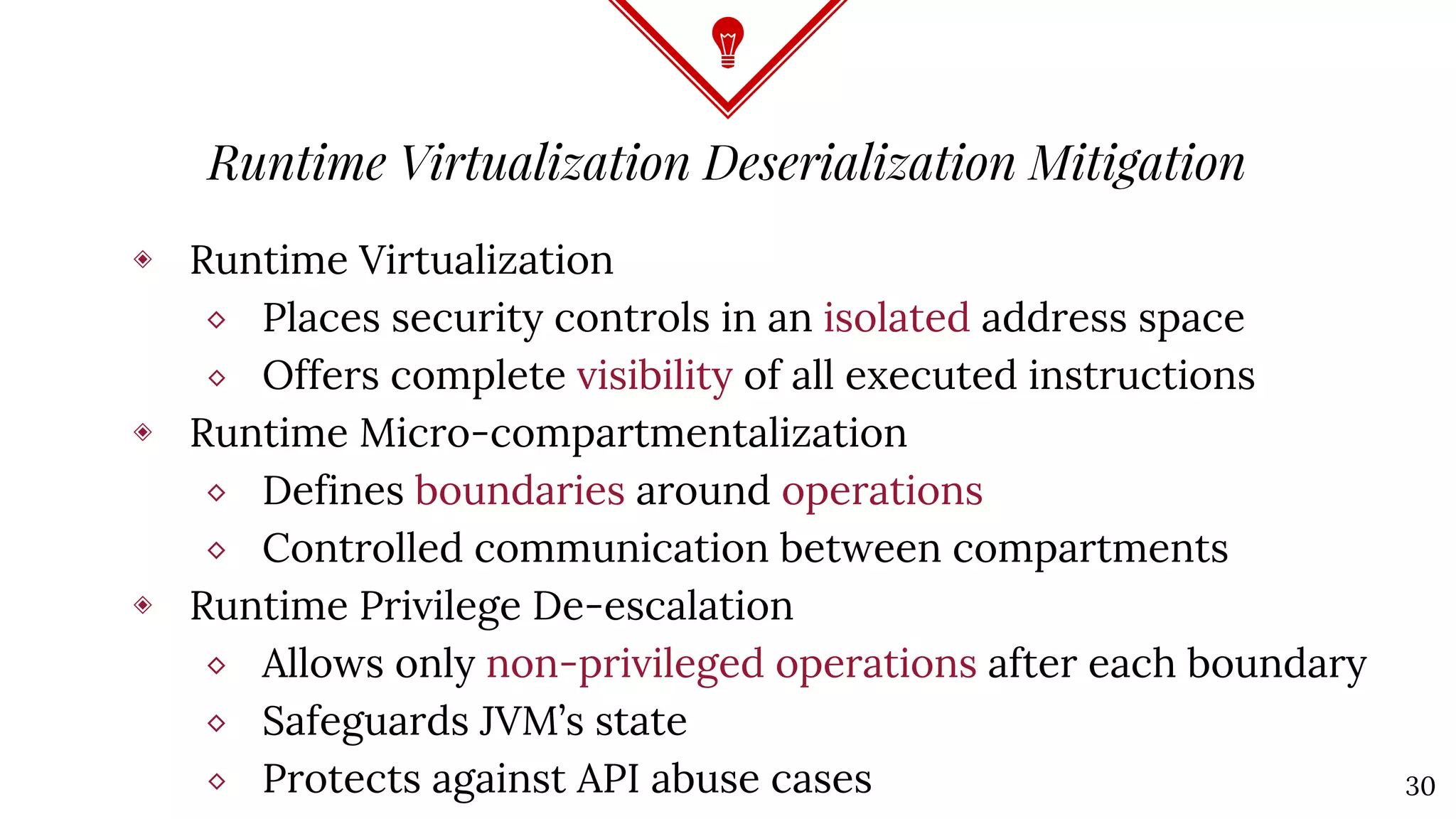
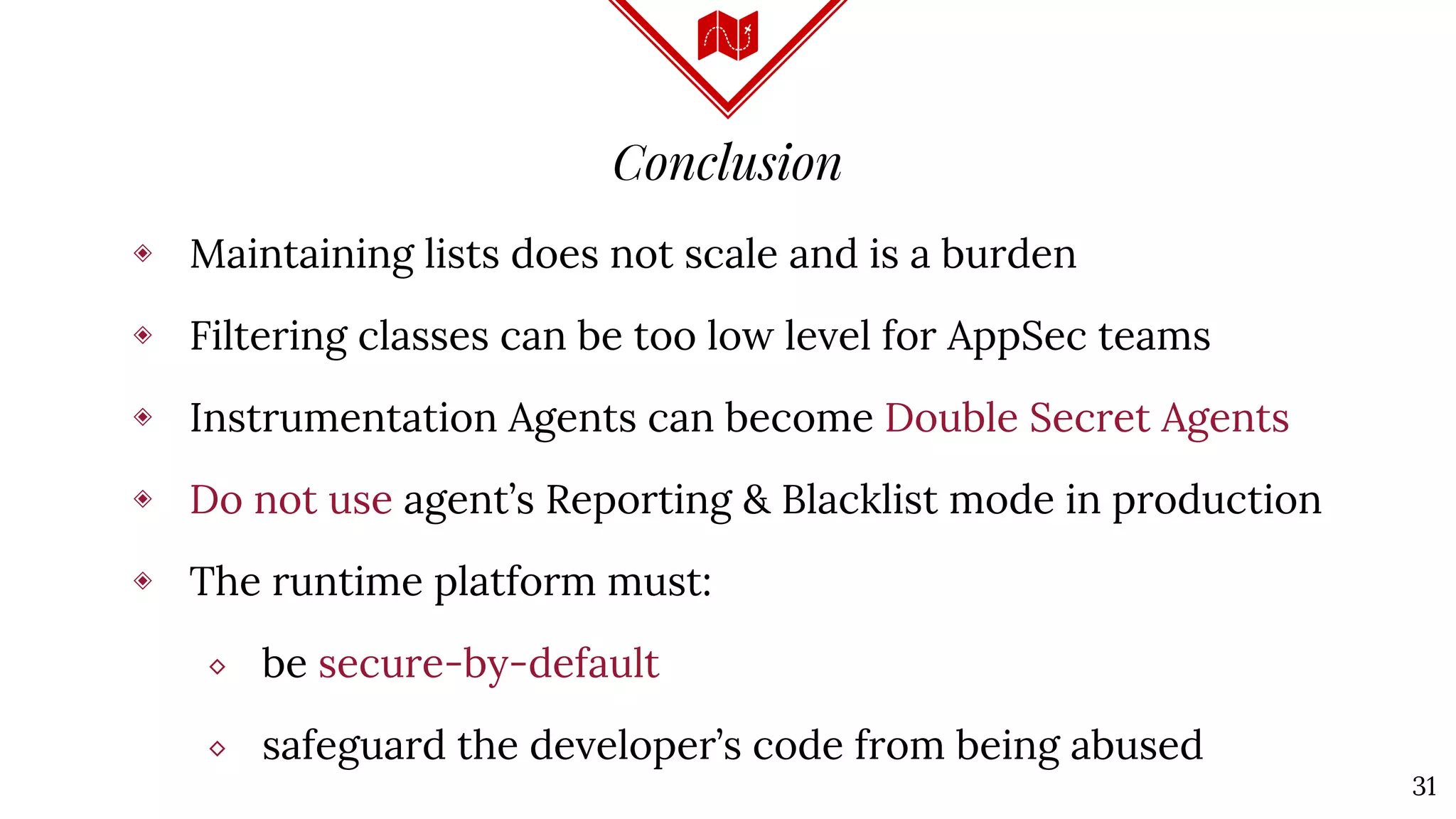
The document discusses Java deserialization attacks and their mitigation strategies by highlighting the vulnerabilities associated with deserializing untrusted data. It emphasizes that traditional methods like black/white listing and instrumentation agents are inadequate due to their complexity and potential for manipulation. The author advocates for runtime virtualization as a more effective solution to enhance security and manage application privileges during deserialization.















![What do the standards suggest? CERT Secure Coding Standards ◈ SER08-J. Minimize privileges before deserializing from a privileged context ◈ SEC58-J. Deserialization methods should not perform potentially dangerous operations MITRE ◈ CWE-250: Execution with Unnecessary Privileges ⬥ [...] isolate the privileged code as much as possible from other code. Raise privileges as late as possible, and drop them as soon as possible. ◈ CWE-273: Improper Check for Dropped Privileges ⬥ Compartmentalize the system to have "safe" areas where trust boundaries can be unambiguously drawn. 29](https://image.slidesharecdn.com/bsideslux-deserialization2-171022145229/75/Mitigating-Java-Deserialization-attacks-from-within-the-JVM-improved-version-29-2048.jpg)


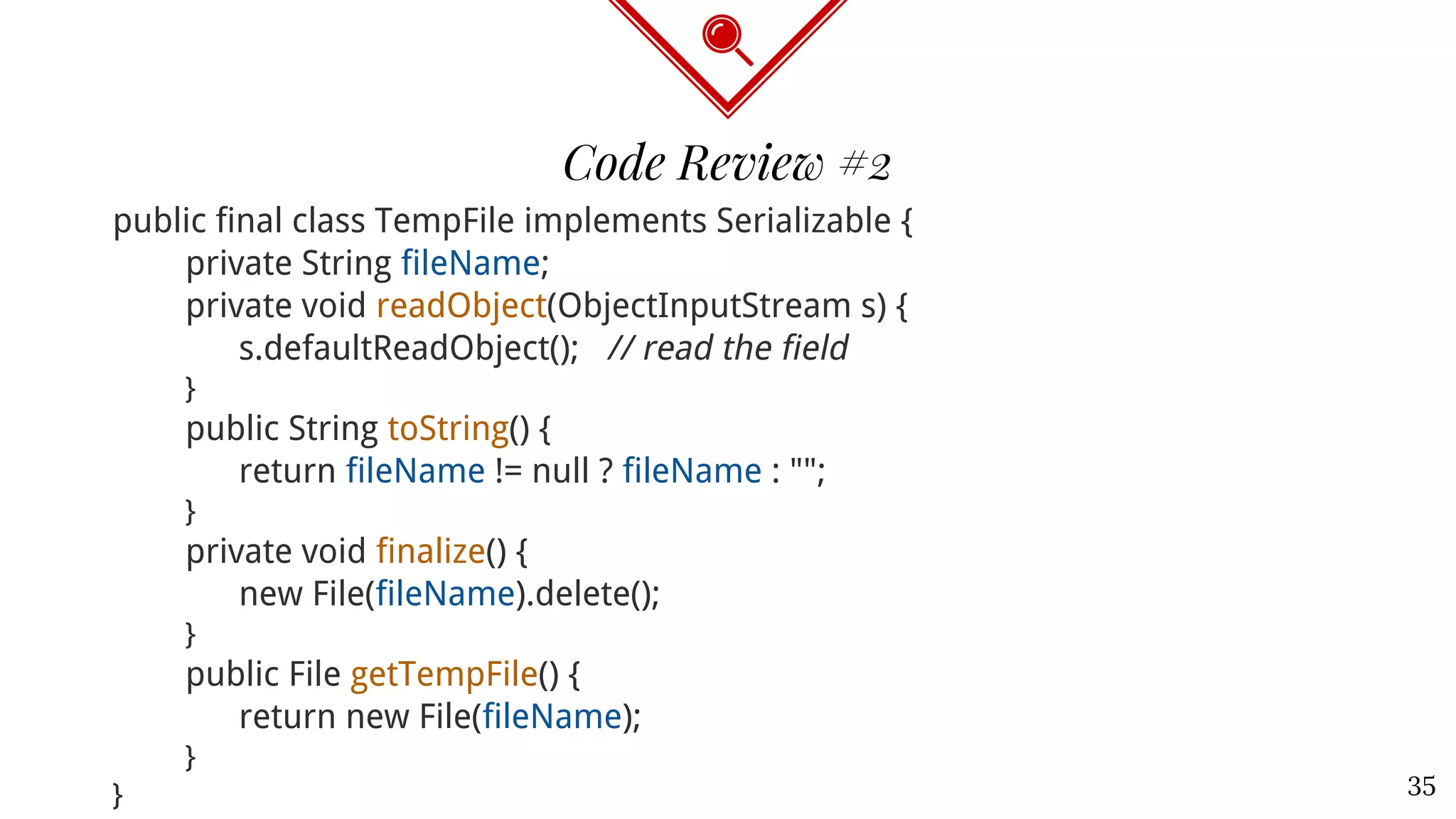
![public class LookupTable implements Serializable { private transient TableElement[] lookupTable; public LookupTable(int size) { int elements = Math.min(Math.max(4,size),32); lookupTable = new TableElement[elements]; } private void readObject(ObjectInputStream s) throws IOException, ClassNotFoundException { int numEntries = s.readInt(); lookupTable = new TableElement[numEntries]; } } Code Review #1 34](https://image.slidesharecdn.com/bsideslux-deserialization2-171022145229/75/Mitigating-Java-Deserialization-attacks-from-within-the-JVM-improved-version-34-2048.jpg)