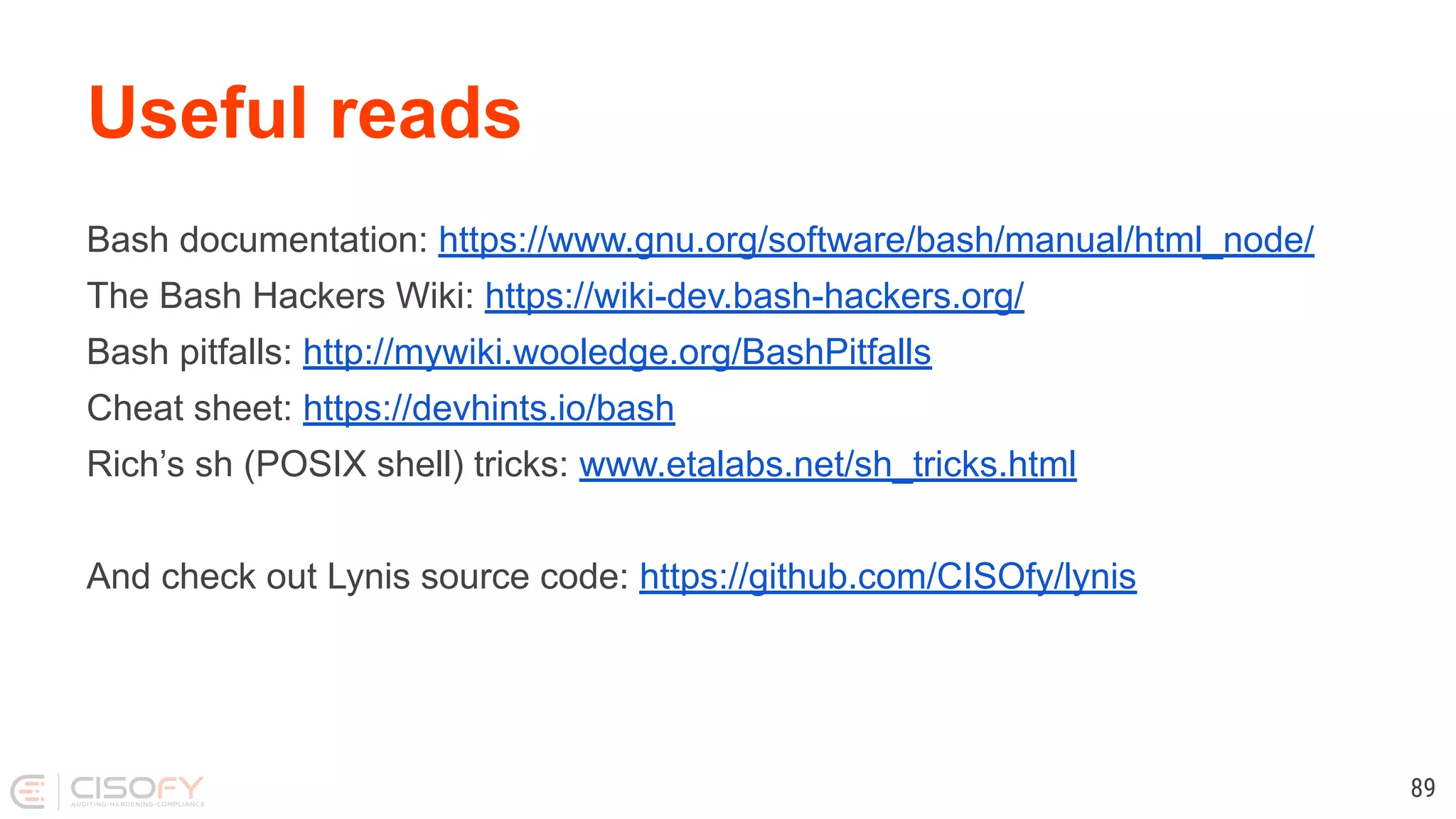
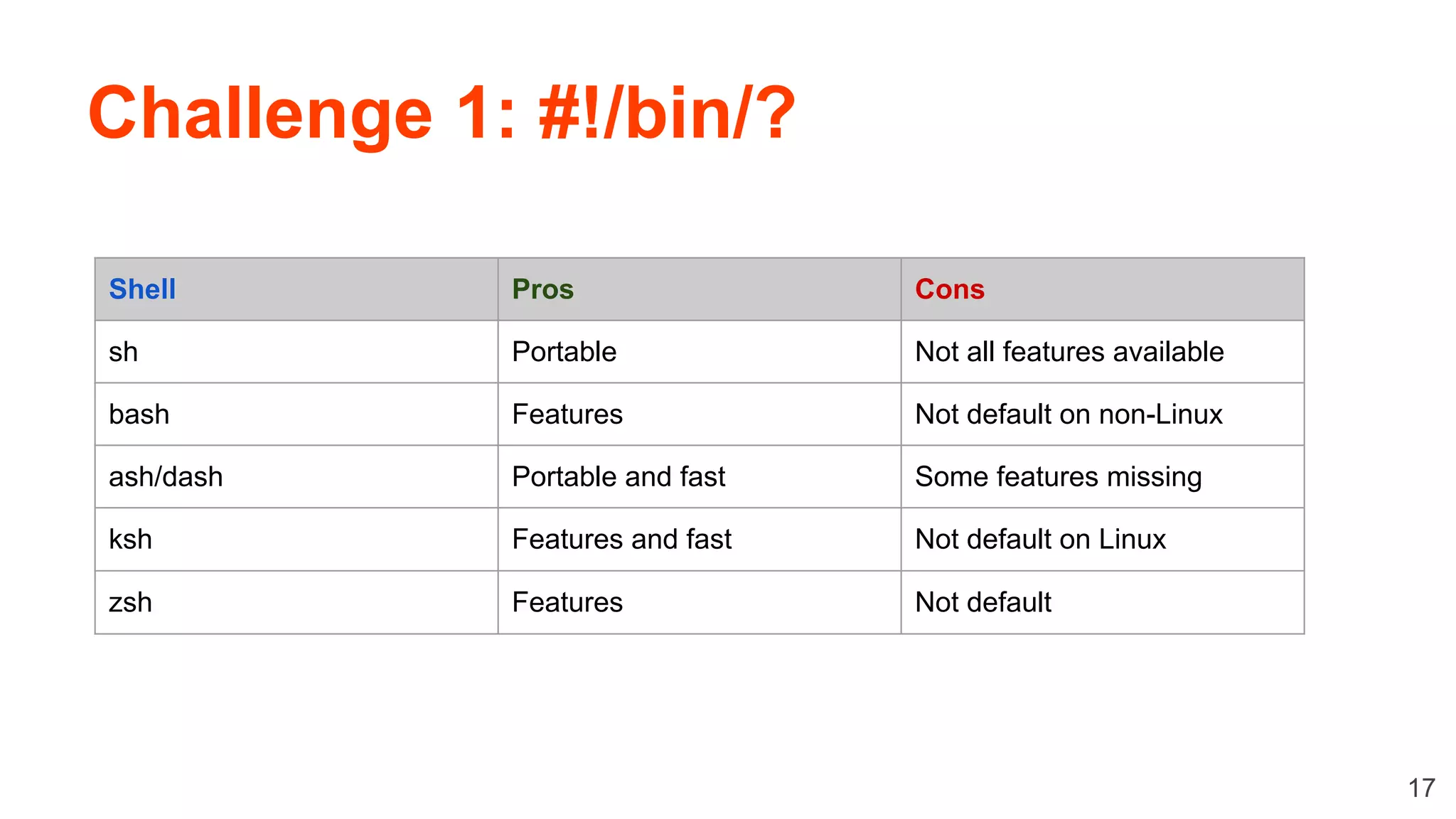
The document discusses best practices for shell scripting, highlighting the importance of readability, reliability, and security. It covers common mistakes, various tools, and defensive programming techniques to enhance script quality. The author, Michael Boelen, shares his goals of knowledge sharing and project improvement while emphasizing the significance of clean code and proper scripting techniques.














![Challenge 3: The Unexpected #!/bin/sh filename="test me.txt" if [ $filename = "test me.txt" ]; then echo "Filename is correct" fi 3: [: test: unexpected operator 21](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-21-2048.jpg)



![Find the flaw (2) 1 if [-d $i] 2 then 3 echo "$i is a directory! Yay!" 4 else 5 echo "$i is not a directory!" 6 fi 29](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-29-2048.jpg)
![Find the flaw (2) if [ -d $i ] then echo "$i is a directory!" else echo "$i is not a directory!" fi 30](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-30-2048.jpg)


![Example Option 1 if [ "${var}" = "text" ]; then echo "found text" fi Option 2 [ "${var}" = "text" ] && echo "found text" 34](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-34-2048.jpg)
![Example: be concise? Option 1 command if [ $? -ne 0 ]; then echo "command failed"; exit 1 fi Option 2 command || { echo "command failed"; exit 1; } Option 3 if ! command; then echo "command failed"; exit 1; fi 35](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-35-2048.jpg)




![Defenses Intended operating system? 1 #!/bin/sh 2 if [ ! "$(uname)" = "Linux" ]; then 3 echo "This is not a Linux system and unsupported" 4 exit 1 5 fi 42](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-42-2048.jpg)


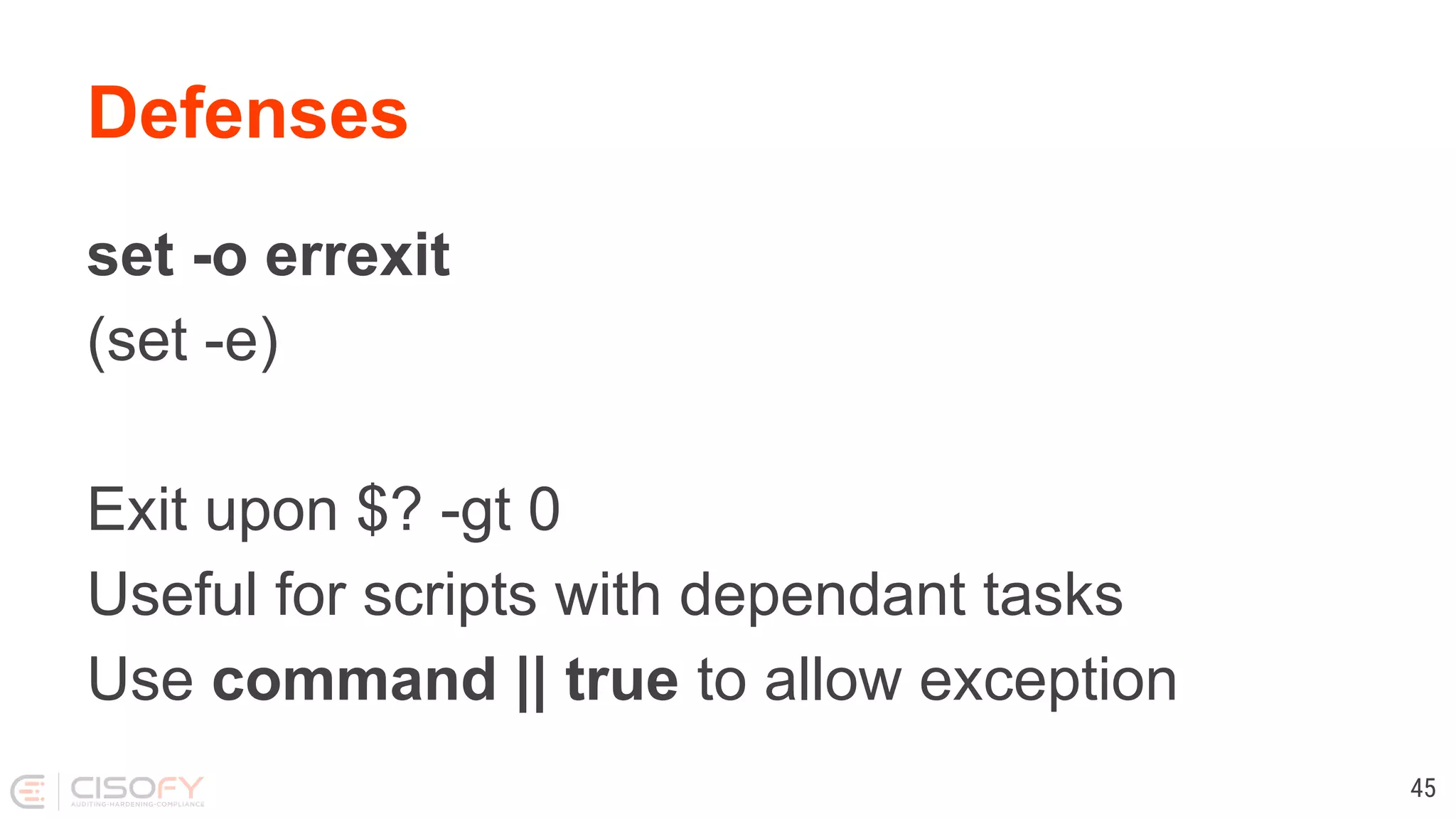
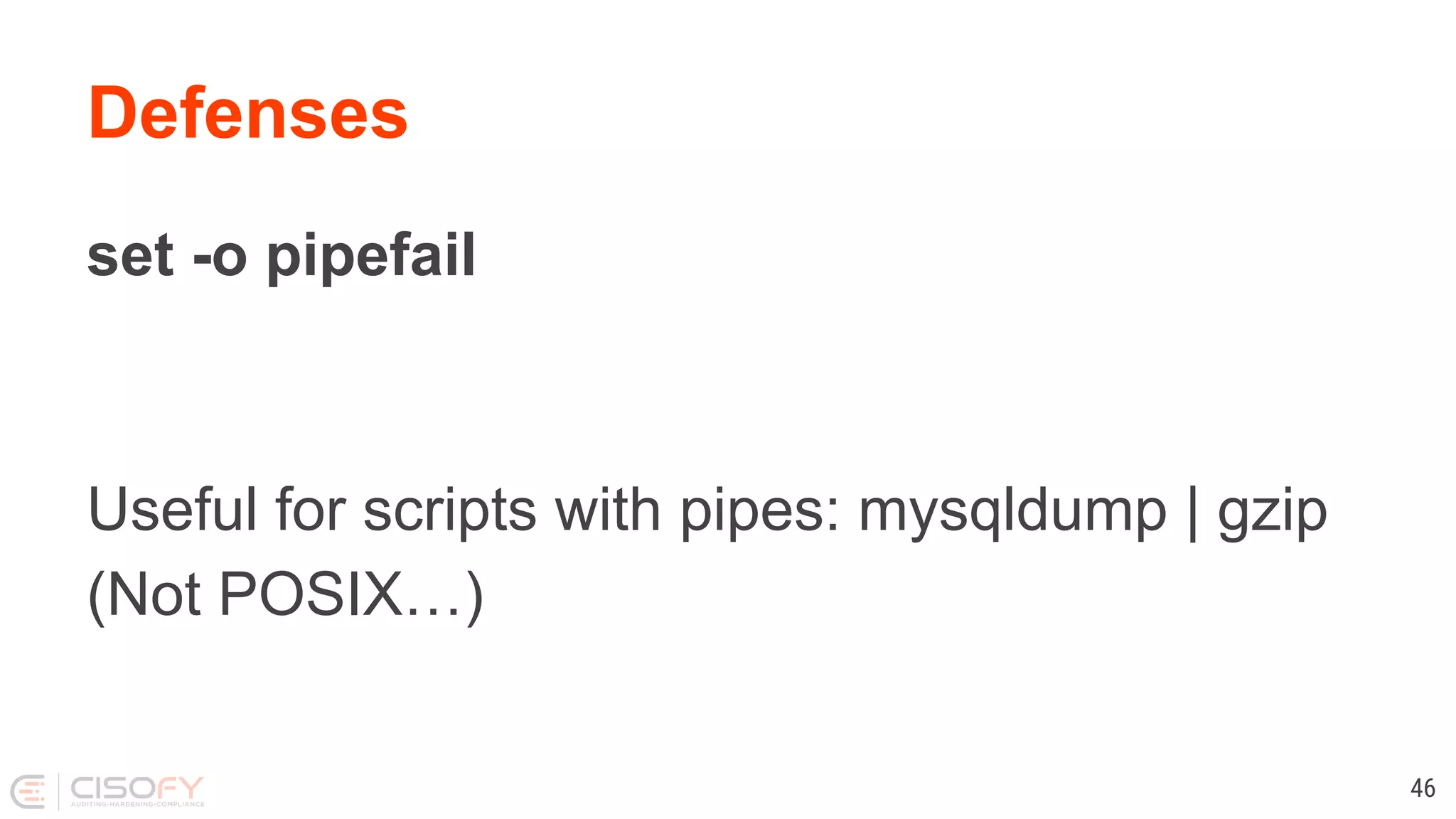
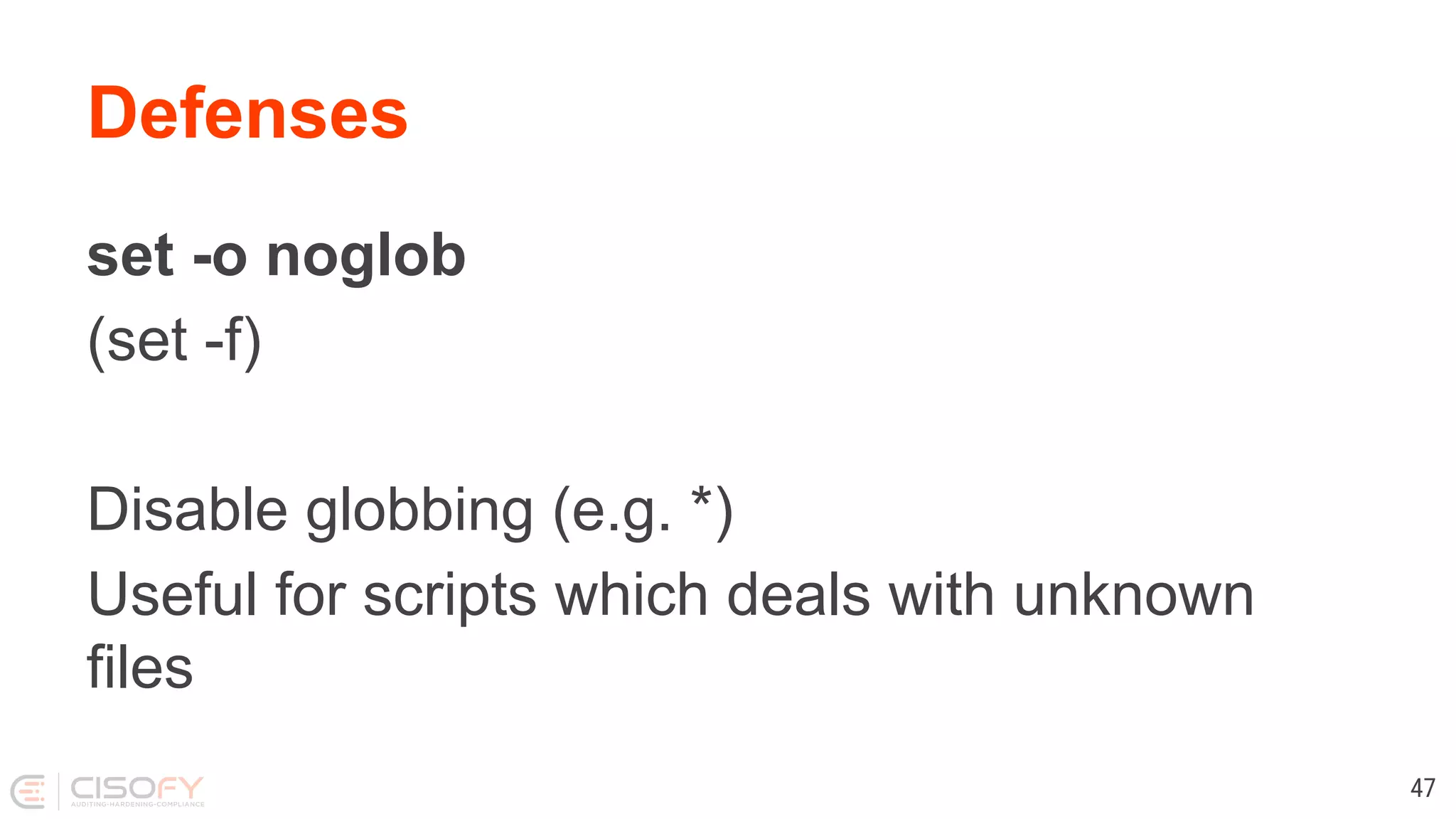
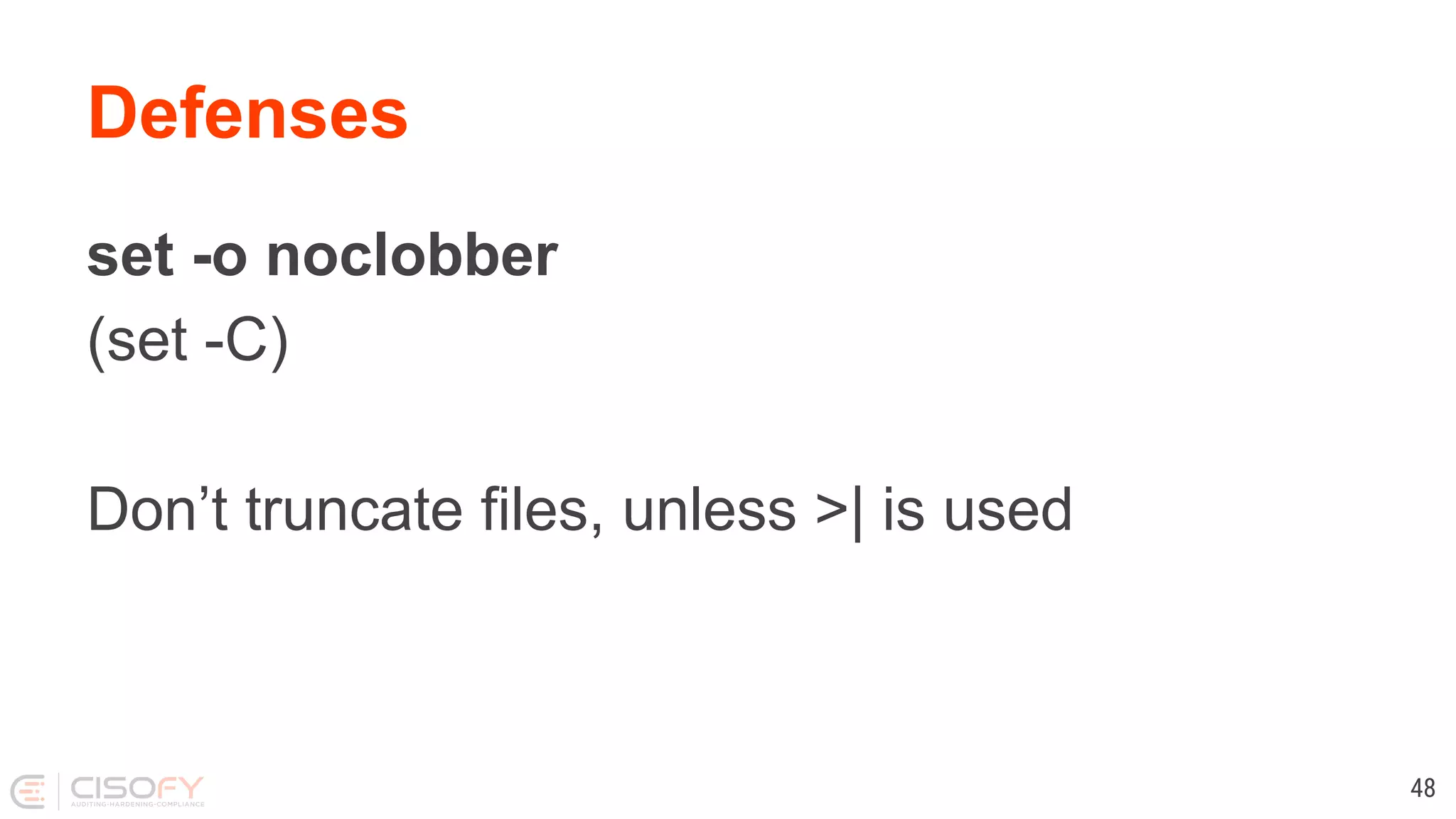

![Defenses Use quotes and curly brackets, they are free [ $foo = "bar" ] [ "$foo" = "bar" ] [ "${foo}" = "bar" ] 53](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-53-2048.jpg)


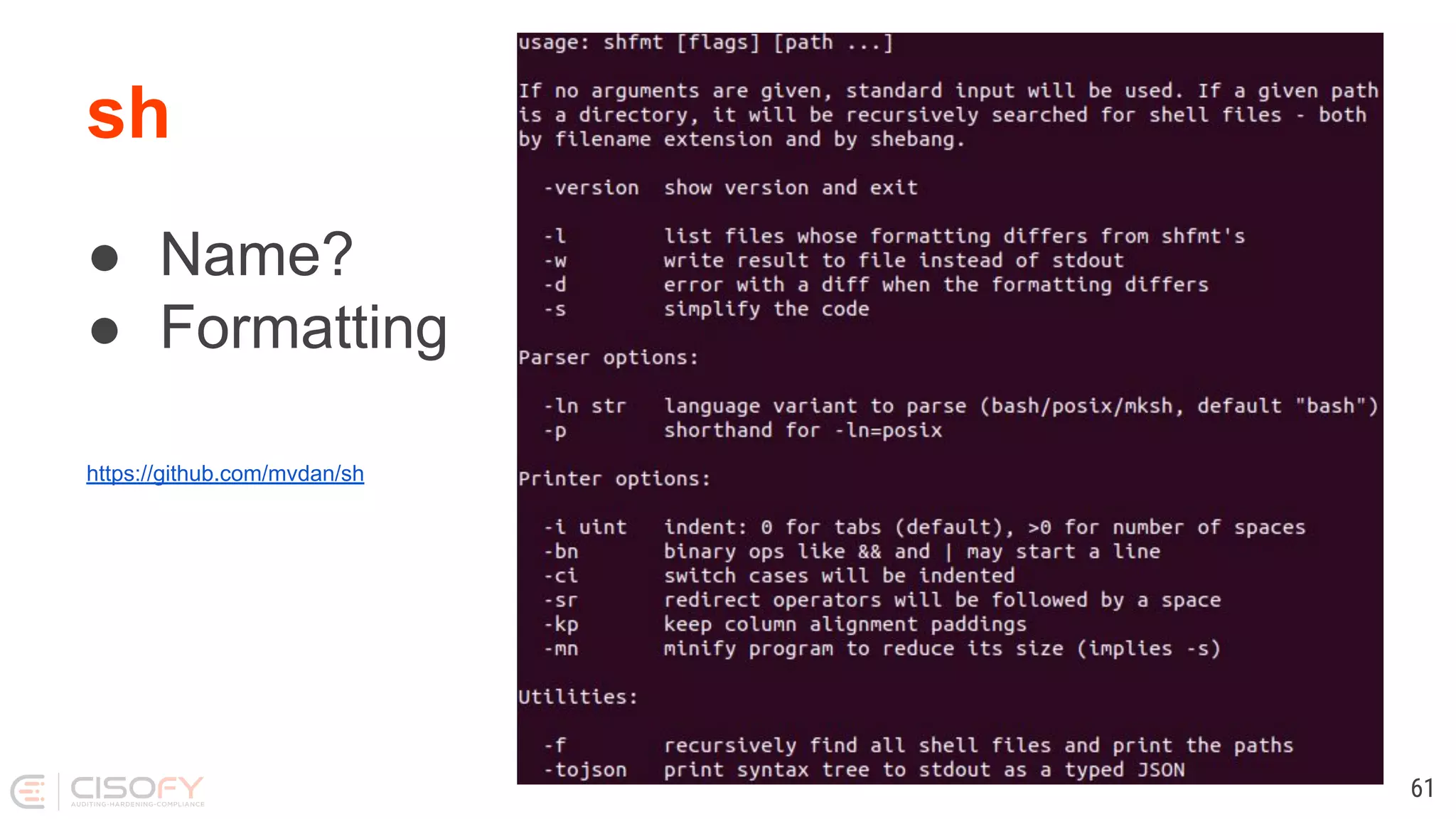

![Tool: checkbashisms $ checkbashisms Usage: checkbashisms [-n] [-f] [-x] script ... or: checkbashisms --help or: checkbashisms --version This script performs basic checks for the presence of bashisms in /bin/sh scripts and the lack of bashisms in /bin/bash ones. 63](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-63-2048.jpg)

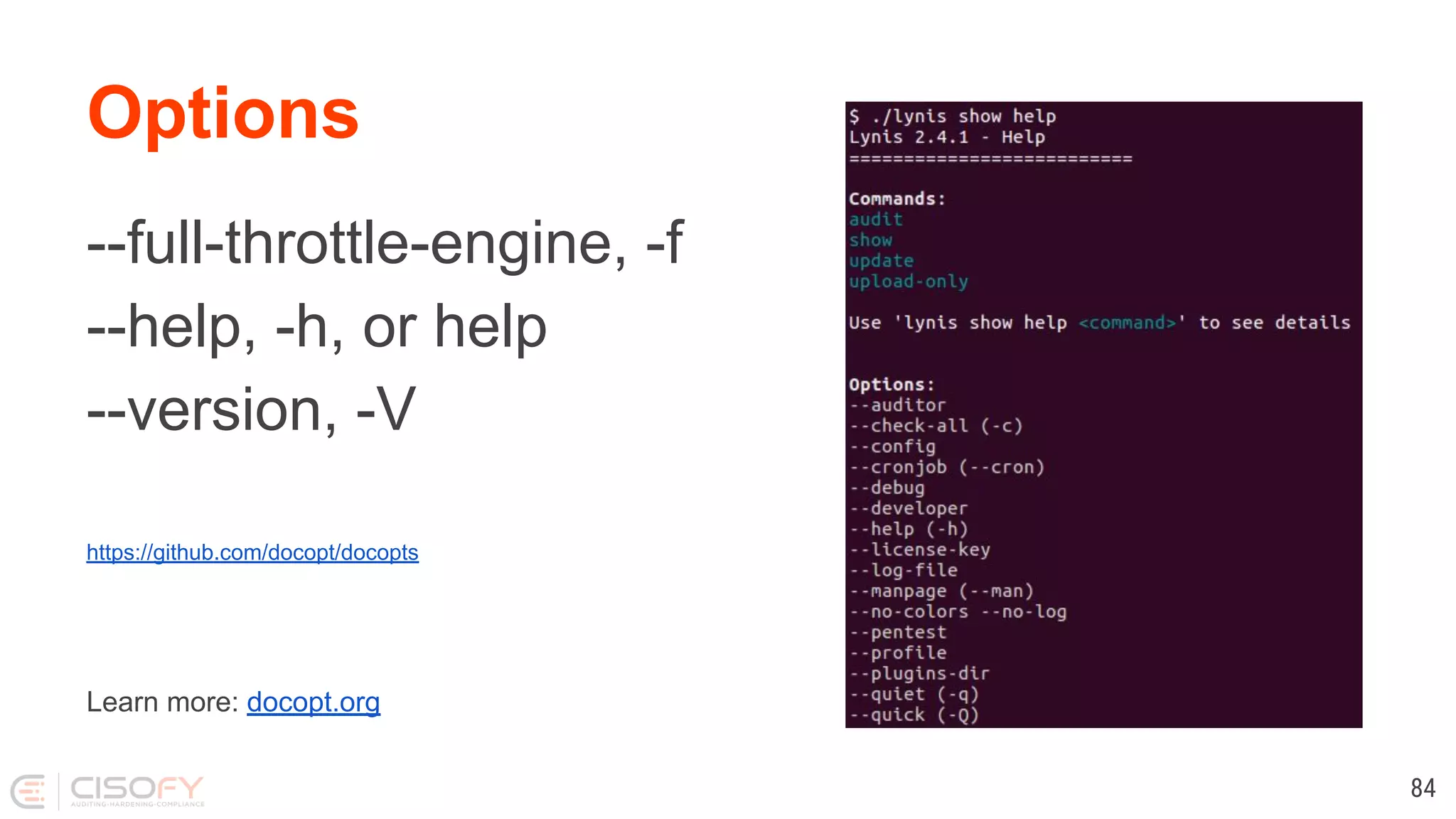
![Tool: ShellCheck Usage: shellcheck [OPTIONS...] FILES... --check-sourced Include warnings from sourced files --color[=WHEN] Use color (auto, always, never) --include=CODE1,CODE2.. Consider only given types of warnings --exclude=CODE1,CODE2.. Exclude types of warnings --format=FORMAT Output format (checkstyle, diff, gcc, json, json1, quiet, tty) --enable=check1,check2.. List of optional checks to enable (or 'all') --source-path=SOURCEPATHS Specify path when looking for sourced files ("SCRIPTDIR" for script's dir) --shell=SHELLNAME Specify dialect (sh, bash, dash, ksh) --severity=SEVERITY Minimum severity of errors to consider (error, warning, info, style) --external-sources Allow 'source' outside of FILES 65](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-65-2048.jpg)




![When to use bash 74 declare/typeset Define a variable type (integer, array) arrays Data entries type Describe command extended globbing Expand file names for loops with integers for ((i=0; i<10; i++)); do echo $i; done extended operator if [[ "$1" =~ ^m*$ ]]; then and more...](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-74-2048.jpg)

![Variables Variable possibly unset? Use: if [ "${name:-}" = "Michael" ]; then … fi 78](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-78-2048.jpg)




![Let’s torn down something! #!/bin/sh set -u hostname=$(hostname) lockfile=/var/lock/create-backups timestamp=$(date "+%s") today=$(date "+%F") gpgkey=$(gpg --keyid-format LONG --list-keys backup@rootkit.nl 2> /dev/null | awk '/^pub/ { print $2 }' | awk -F/ '{ print $2 }' | head -1) if [ -z "${hostname}" ]; then echo "Error: no hostname found"; exit 1; fi if [ ! -z "${lockfile}" ]; then if [ -f ${lockfile} ]; then echo "Error: Backup still running. Removing lock file to prevent backup script running next day" rm ${lockfile} exit 1 fi fi touch ${lockfile} # Add a daily timestamp to the file for restore checking echo "${hostname}-${timestamp}-${today}" > /etc/backup.data 88](https://image.slidesharecdn.com/lets-make-better-scripts-191202163953/75/Lets-make-better-scripts-88-2048.jpg)