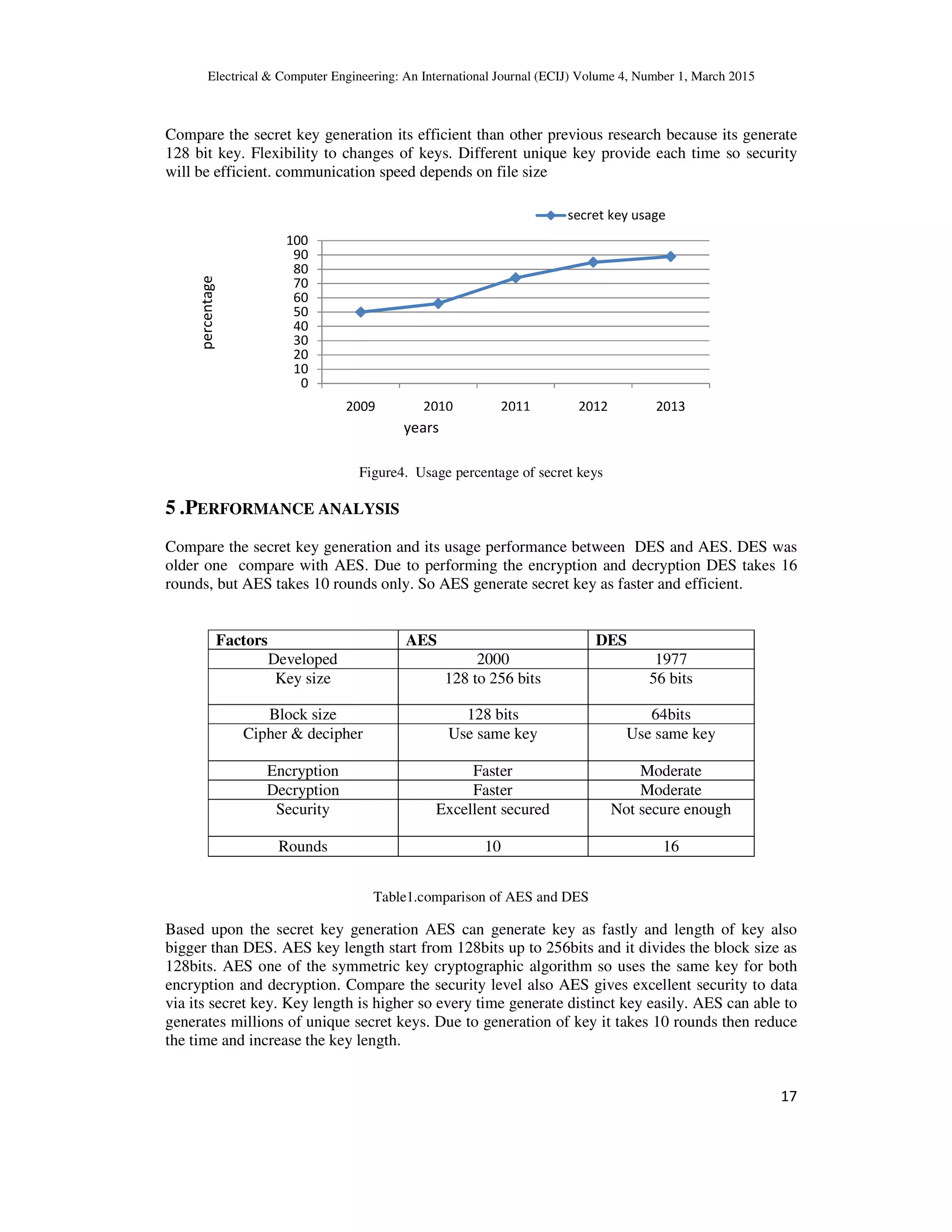
This document summarizes a research paper on generating secret keys for multiple wireless devices using multipath routing. It proposes a framework that uses AES encryption to generate unique 128-bit keys for each device pair, overcoming issues of limited signal range and centralized networks. The methodology observes devices to compare RSS signals and encrypts keys using AES. Performance analysis shows AES key generation is faster than DES and provides stronger security due to longer, randomly generated keys.

![Electrical & Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 14 Secure wireless communications is a challenging problem due to the share data between devices. Most existing security protocols apply encryption and decryption techniques for bit scrambling at the application layer by exploiting a shared secret key between pairs of communicating nodes. Secure keys are distinct for distinct pair wise links with a probability that the two users sharing a common link generate the same key [5].Security techniques that exploit the randomness of wireless channels for getting the secret key by performing encryption and decryption. Focus on pair wise key generation, its highly scalable and improve the key bit generation rate by a couple of orders [6]. In pair-wise independent network, every pair of terminals observes a common pair-wise source that is independent of all sources accessible to the other pairs[15]. Here three specific problems are investigated. One was each terminals are in observations with the others. All these terminals wish to generate a common secret key. Two was designated terminals wish to generate a secret key with the help of other terminals. Three was all the terminals wish to generate a common secret key. The communicating parties require some shared secret key with which to encrypt the message so that it cannot be understood by an enemy observer. The exchange of some information between the parties is necessary to achieve the bounds and various information [24]. Two cars to extract a secret key from RSSI values in such a way that nearby cars cannot obtain the same secret[30]. The main contribution of this work is to group of the physical channel characteristics with key generation algorithms to secure wireless networks. 2 .RELATED WORK In previous research are shared the secret keys to de vices and compare their lower bit mapping [13], they are using pin model. In a typical multipath environment, the wireless channel between each pair of terminal produces a random mapping between the transmitted and received signals which is time-varying and location specific. The novel methodologies which allow robust secret key extraction from radio channel measurements which user from real world non-reciprocities a prior unknown fading. The fading signal are verified with their neighbour devices.The secret key generation utilizing physical layer information of the radio channel it allows any two wireless devices within transmission range of each other to extract a share symmetric cryptographic key while does not require a fixed data range and destination range among the devices [1]. Based on the principle of two wireless devices can interact with secret bits independently by using the sampled sequence from the radio channel between them within the coherence time of the channel. Unlike existing key generation algorithms, such as Diffie-Hellman, which deals the secret key generation between pair of devices. It’s provided by the temporal and spatial variation of the radio channel can achieve information theoretical secrecy [4]. We place our work in the context of relate research in section II. We provide a feasibility study of using fine-grained channel response information for secret key extraction and present the attack model in section III. We present the proposed channel gain complement assisted key generation and extraction in section IV. Comparison and simulation results based on performance of secret key using AES as given in section V. 3 . ARCHITECTURE From the architecture diagram its shows multiple devices with unique secret key generation. There many devices are need to access the data. It require secret key to access data so they send request to key generator. Key generators observe the devices based on the RSS signal and encrypt](https://image.slidesharecdn.com/4115ecij02-191023063008/75/KEY-GENERATION-FRAMEWORK-FOR-MULTIPLE-WIRELESS-DEVICES-USING-MULTIPATH-ROUTING-2-2048.jpg)
![Electrical & Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 15 the keys send to device which is sent the request. Devices are get the unique keys after decrypt the key which are send by key generator by using AES algorithm, Key length 128bit so it’s little faster than previous system. Allows the devices to access the data by extract the secret keys via communication channel. Figure1. Architecture Diagram 4. METHODOLOGY The challenges arising from utilizing RSS measurements for group key generation. First, the RSS values obtain between a pair of devices cannot be securely passed to other devices making it hard to reach key agreement among multiple devices without the availability of a particular range. Second, due to the multiple of mobile devices, the devices within the group that need to establish a secret key may not be within each other’s communication range, making the existing RSS- based methods not applicable. To address these challenges, we define AES algorithm. Our frameworks consist of random number generation and key authentication.. Algorithm: For i=1 to n do K i=Ki-1+Ri Where |Pi|=128 Xi=Pi+Ci T=HASH(X1||X2||………Xn) Where C=C1||C2||……..Cn Let’s say Pi denotes the plaintext block, where 1<i<n, and n is total no of blocks. Key Expansion (byte key[16],word w[44]) Step 1:For i=0 to 4 do Step 2:W[i]= key[4*i],key[4*i+1],key[4*i+2], key[4*i+3] Decryp tion Decry ption Device1 Device2 Device n Key genera tor Observe the devices Encryption of keys Decry ption](https://image.slidesharecdn.com/4115ecij02-191023063008/75/KEY-GENERATION-FRAMEWORK-FOR-MULTIPLE-WIRELESS-DEVICES-USING-MULTIPATH-ROUTING-3-2048.jpg)
![Electrical & Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 Step 3:For i=4 to 44 do Step 4:T=w[i-1] Step 5:If i|4 =0 Step6:T=subword * rotword (T)+rcon[i/4] Step 7:W[i]-w[i-4]=T; The key is divided by four parts of encryption and decryption then expanded key W[i] depends on the immediate preceeding word, w[i Rotword-is a one byte word. This was transformed the input word. Subword-submit the input word We now turn to a discussion of each of the four transformations used in AES. For each stage, we mention the forward (encryption) algorithm, the inverse (decryption) algorithm, and the rational for the design of that stage. Design of that secret key betwe compared and mapped each other. A device can communicate with any other devices which are connected in the network. Figure2. Comparison of devices and its range due to transfer the data Compare the devices and their data transfer different various speed. If data sizes Numbers of devices are no problem. Figure3. Comparison existing and proposed 0 0.5 1 1.5 2 2.5 3 3.5 4 4.5 0-25 devices 0 100 percent age Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 Step6:T=subword * rotword (T)+rcon[i/4] The key is divided by four parts of encryption and decryption then expanded key W[i] depends on the immediate preceeding word, w[i-1] and the word four positions back w[i-4]. a one byte word. This was transformed the input word. We now turn to a discussion of each of the four transformations used in AES. For each stage, we mention the forward (encryption) algorithm, the inverse (decryption) algorithm, and the rational for the design of that stage. Design of that secret key between inputs bits and output bits, bits rate compared and mapped each other. A device can communicate with any other devices which are Figure2. Comparison of devices and its range due to transfer the data their data transferring rate, comparison of four devices it allows t various speed. If data sizes are increases than speed of devices will become low. no problem. Figure3. Comparison existing and proposed 26-50 51-75 76-100 AES DES range of files tranfer 0 100 proposed existing functionality Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 16 The key is divided by four parts of encryption and decryption then expanded key W[i] depends We now turn to a discussion of each of the four transformations used in AES. For each stage, we mention the forward (encryption) algorithm, the inverse (decryption) algorithm, and the rational en inputs bits and output bits, bits rate compared and mapped each other. A device can communicate with any other devices which are comparison of four devices it allows are increases than speed of devices will become low. 100 DES](https://image.slidesharecdn.com/4115ecij02-191023063008/75/KEY-GENERATION-FRAMEWORK-FOR-MULTIPLE-WIRELESS-DEVICES-USING-MULTIPATH-ROUTING-4-2048.jpg)
![Electrical & Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 18 Figure5. Comparison of time taken A number of files in different sizes were showed into the simulation test. From the comparative study all possible factors can possible to print secret keys as fast and secure. Comparing the security level our secret key generation is very secure than existing. The key length taken up to 256 bits. so it can generate the millions of different keys, key length was another one important advantage here not easy to judge the key . This can provide the more security to data and increase the hardware and software performances. 6.CONCLUSION Secret key designed and group secret key generation for multiple wireless devices. The scheme take an advantages of provides different key for each action performance. We given the solution for access the data from anywhere it’s no need range of wireless device. Key length has been expanded A result from implementation of secret key is faster than DES with help of using AES algorithm. REFERENCES [1] B. Azimi sadjadi, A. Kiayias, A. Mercado, and B.Yener, “Robust key generation from signal envelopes in wireless networks“ , in ACM CCS, pp. 401-410(2007). [2] A. sayeed and A. Perrig, “secure wireless communications: Secret keys through multipath”, in IEEE ICASSP,pp.3013-3016.0(2008). [3] Q. Wang, H. Su, K. Ren and K. Kim, “Fast and scalable secret key generation exploiting channel phase randomness in wireless networks”, in IEEE INFOCOM, (2011). [4] N.Patwari, J. Croft, S. Jana and S. Kasera, “High rate uncorrelated bit extraction for shared secret key generation from channel measurements”, IEEE Transactions on mobile computing, pp, 17- 30(2009). [5] J.Croft, N. Patwari, and S. Kasera, “Robust uncorrelated bit extraction methodologies for wireless sensors”, in ACM/IEEE ICNP, pp, 70-81(2010). [6] Y. Kim, A. Perrig and G.Tsudik, “Tree- based group key agreement”, TISSEC(2004). [7] S. Nitinawarat, C. Ye, A. Barg, P. Narayan, and A. Reznik, “Secret key generation for a pair wise independent network model, “IEEE TIFS, vol.2, no.3, pp. 364-375(2007). [8] S.Nitinawarat and P. Narayanan, “Perfect omniscience, perfect secrecy, and steiner tree packing,” IEEE Transactions on information Theory(2010). [9] C. Ye and A. Reznik, “Group secret key generation algorithms,” in IEEE ISIT(2007). 0 10 20 30 40 50 60 70 80 90 0.5Mb 1Mb 1.5Mb 2Mb DES AES timeinseconds file size](https://image.slidesharecdn.com/4115ecij02-191023063008/75/KEY-GENERATION-FRAMEWORK-FOR-MULTIPLE-WIRELESS-DEVICES-USING-MULTIPATH-ROUTING-6-2048.jpg)
![Electrical & Computer Engineering: An International Journal (ECIJ) Volume 4, Number 1, March 2015 19 [10] R. Wilson, D. Tse, and R. Scholtz, “Channel identification” Secret sharing using reciprocity in ultrawideband channels,” IEEE TIFS, vol.2, no.3, pp.364-375(2007). [11] Z. Li, W. Xu, R. Miller and W. Trappe, “Securing wireless systems via lower layer enforcements,” in Proceeings of the 5th ACM workshop on Wireless security, pp.33-42(2006). [12] I. Csiszar and R. Ahlswede, “secrecy capacities for multiple terminals,”IEEE Transactions on Information Theory , vol. 50,pp. 3046-3061, (2004). [13] H. Liu, J. Yang, and Y.Chen, “Collaborative secret key extraction leveraging received signal strength in mobile wireless networks, “ in IEEE INFOCOM, pp. 927-935(2012). [14] O. Arazi and H.Qi,”Self-certified group key generation for ad hoc clusters in wireless networks,” in IEEE INFOCOM(2005). [15] U. Maurer and S. Wolf,”Secret key agreement over a non authenticate chanel part iii,”IEEE Transactions on Information Theory, vol.49,pp.822-851(2003).](https://image.slidesharecdn.com/4115ecij02-191023063008/75/KEY-GENERATION-FRAMEWORK-FOR-MULTIPLE-WIRELESS-DEVICES-USING-MULTIPATH-ROUTING-7-2048.jpg)