The document presents new cryptographic algorithms using asymmetric keys for secure data communication, emphasizing the importance of personal privacy in a networked world. The proposed methods involve encrypting messages into nonlinear equations, making interception by unauthorized parties difficult. It also discusses various existing encryption techniques and potential attacks, ultimately introducing a three-level encryption process to enhance data security.
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 227 Cryptographic Algorithms for Secure Data Communication Zirra Peter Buba zirrapeter@yahoo.com Department of Mathematical Sciences Adamawa State University Mubi, 650221, Nigeria. Gregory Maksha Wajiga gwajiga@gmail.com Department of Mathematics and Computer Science Federal University of Technology Yola, 640284, Nigeria. Abstract Personal privacy is of utmost importance in the global networked world. One of the best tools to help people safeguard their personal information is the use of cryptography. In this paper we present new cryptographic algorithms that employ the use of asymmetric keys. The proposed algorithms encipher message into nonlinear equations using public key and decipher by the intended party using private key. If a third party intercepted the message, it will be difficult to decipher it due to the multilevel ciphers of the proposed application. Keywords: Cryptographic Algorithm, Asymmetric key, Communication, Nonlinear System 1. INTRODUCTION Some vital information that are disseminated within an office, across offices, between branches, of an organization and other external bodies and establishments at times get into the hands of the unauthorized persons who may tamper with the contents of the information. And if no security measures are taken, there is no doubt that such data and other sensitive information will be exposed to threats such as impersonation, insecrecy, corruption, repudiation, break-in or denial of services [1,2] that may cause serious danger on the individual or organization. A secure system should maintain the integrity, availability, and privacy of data [3]. Data integrity usually means protection from unauthorized modification, resistance to penetration and protection from undetected modification. Therefore, algorithms which help prevent interception, modification, penetration, disclosure and enhance data/information security are now of primary importance. This paper suggests new methods for secured means of communication over unsecure channel. This is to ensuring that the intruders do not have access to the plaintext without a secret key. 2. PRELIMINARIES 2.1 Cryptography One way to strengthen security [4,5] in computer systems is to encrypt sensitive records and messages in transit and in storage. The basic model of a cryptographic system is illustrated in Figure 1. The original unenciphered text is called the plaintext. The act of converting a plain text message to its ciphertext form is called enciphering [6]. In its cipher form, a message cannot be read by anyone but the intended receiver. Reversing that act (i.e., ciphertext form to plain text message) is deciphering. Enciphering and deciphering are more commonly referred to as encryption and decryption, respectively.](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-1-2048.jpg)
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 228 fut yola fut yola hut them iyx cspe iyx cspe Decryption Key Encryption Key Cryptanalyst Encryption algorithm Decryption algorithm Receiver Sender Ciphertext Ciphertext Insecure Communication Channel Plaintext Plaintext abc cspe FIGURE 1: Encryption and Decryption Process 2.2 Modern Key-Based Cryptographic Techniques There are several modern key-based cryptographic techniques. The two common key based encryption techniques are symmetric and asymmetric key cryptography [7]. In symmetric key cryptography, the same key is used for both encryption and decryption. In asymmetric schemes, one key is used for encryption and another is used for decryption [8]. The increased confidence in the integrity of systems that use encryption is based on the notion that ciphertext should be very difficult to decipher without knowledge of the key [3]. 2.3 Types of Attacks There are several types of code-breaking attacks. The first, known as the ciphertext attack, occurs when an adversary comes into possession of only the ciphertext [3]. The known plaintext problem occurs when the intruder has some matched portions of the ciphertext and the plaintext [9]. The most dangerous is the chosen plaintext problem, in which the attacker has the ability to encrypt pieces of plaintext at will. Brute-force is the ultimate attack on a cipher, by which all possible keys are successively tested until the correct one is encountered [9]. Codebook attacks are attacks that take advantage of the property by which a given block of plaintext is always encrypted to the same block of ciphertext as long as the same key is used. A "man-in-the-middle" attack is an attack that is placed by an active attacker who can listen to the communication between two entities and can also change the contents of this communication. While performing this attack, the attacker pretends to be one of the parties in front of the other party. 2.4. Types of Encryption Algorithms Currently, there are several kinds of key based encryption software in the market categorized by their function and target groups. The most common key based encryption techniques are given [7,10,11] as follows: i. The Caesar Cipher- one of the earliest cryptographic algorithms linked and attributed to Julius Caesar in the Gallic war for its usage. Julius Caesar used cipher to protect the messages to his troops by replacing each letter in a message by the third letter further along in the](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-2-2048.jpg)

![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 230 3.2 Encryption and Decryption Rules a) The encryption process requires that the sender must have the message and number of words that are left from Figure 2. b) To decipher the message in Equation (1b), the intended receiver must be given the following key which contains the associated terms and corresponding code. i. Solutions obtained from the system of nonlinear equations. ii. The values associated with the variable index in Table 2. iii. The formula . iv. A lookup character position in Table 1. 2 3 4 5 6 7 0 space 0 @ P ` P 1 ! 1 A Q a q 2 ‘’ 2 B R b r 3 # 3 C S c s 4 $ 4 D T d t 5 % 5 E U e u 6 & 6 F V f v 7 ‘ 7 G W g w 8 ( 8 H X h x 9 ) 9 I Y i y a * : J Z j z b + ; K [ k { c , < L l } d - = M ] m | e . > N ^ n f / ? O _ o N TABLE 1: A Lookup Character Position c) The key is typically shared by trusted entities and be kept secret from the unauthorized users. d) The variable indexes that represent the compressed characters in Equation (1b) are further hid in a file using delta encoding principle before transmission to the intended receiver to further create a state of confusion to the intruders. e) A copy of the generated decryption key is saved in a file and sends to recipient email or via any secure communication medium such as telephones Short Message Service (SMS) on or before the message reaches the intended recipient.](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-4-2048.jpg)
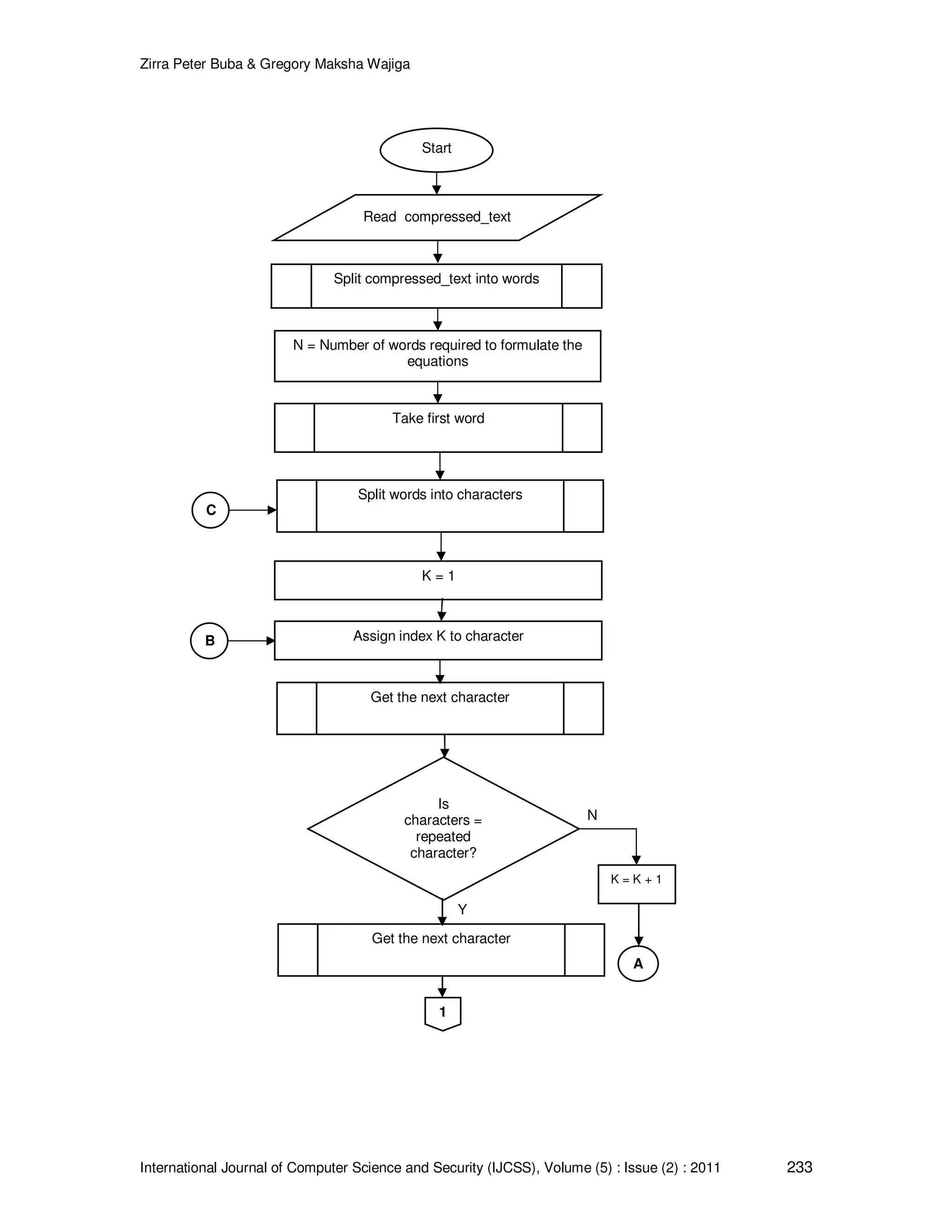
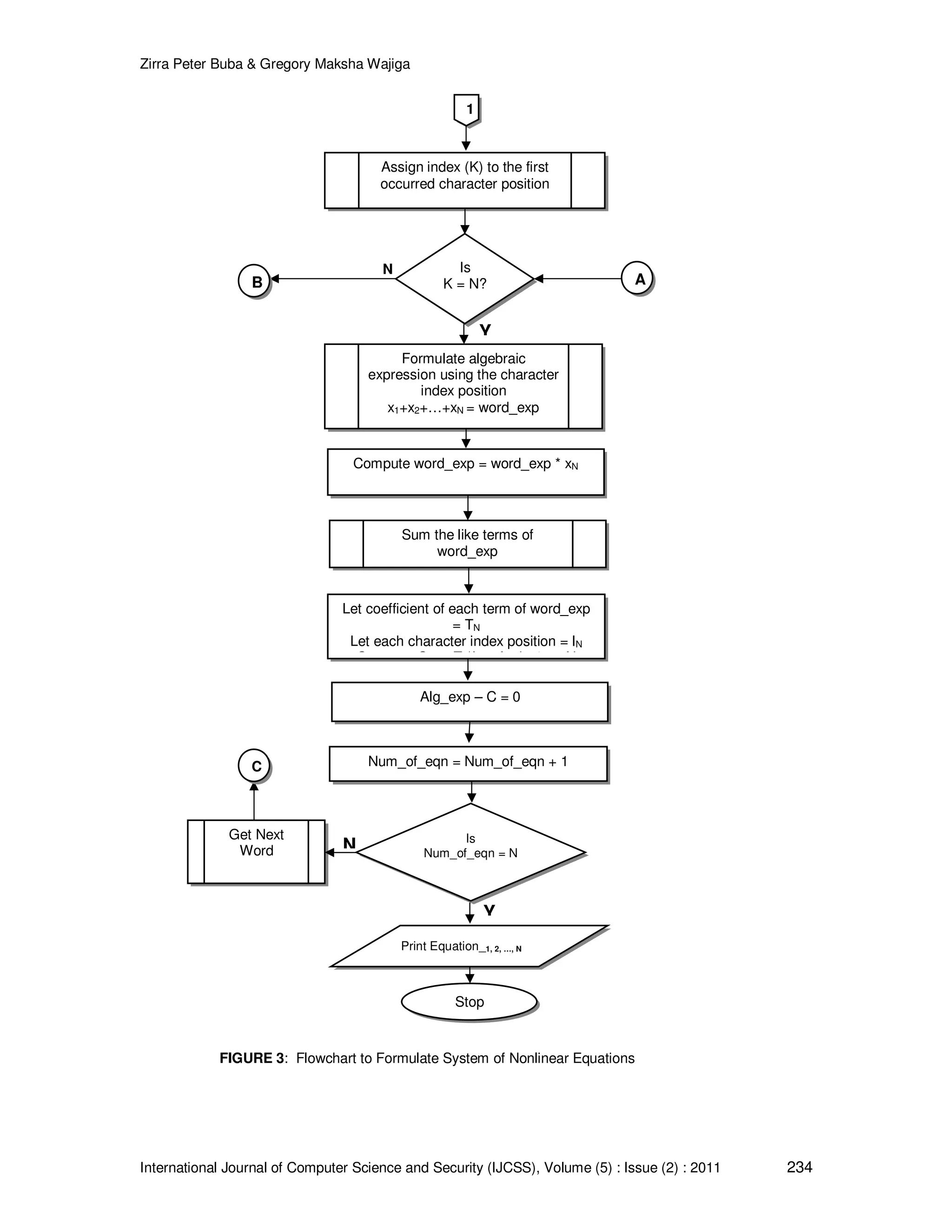
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 231 Y Start Read text Let wordtoken = textsplitted wordlength = textlength Word1=wordtoken [K] Let wordtoken = “ ”: word1 = empty wordlength = 0: k = 0; j=0: index = empty Set K =K+1 Is K < wordlength? Append K to index as index += K+ ”,” Print compressedtext N Stop Set J=0 Set J = J + 1 1 Y Is J < wordlength? Word2=wordtoken [J] A B Y A Print index of word](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-5-2048.jpg)
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 232 Y Y Y Append wordtoken[K] to compressedtext as compresstext += wordtoken[K] B Y NIs word2 empty? 1 Is word1≠empty? Is word1=word2? Append content of compressed words to compressed text as compressedtext+=compressedwords Append content of word1 to compressedtext as Compressedword + = ” ”+ word1 Let wordtoken[J] = empty Append the value of J to index as index += J + ”,” FIGURE 2: Word Compression Flowchart](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-6-2048.jpg)


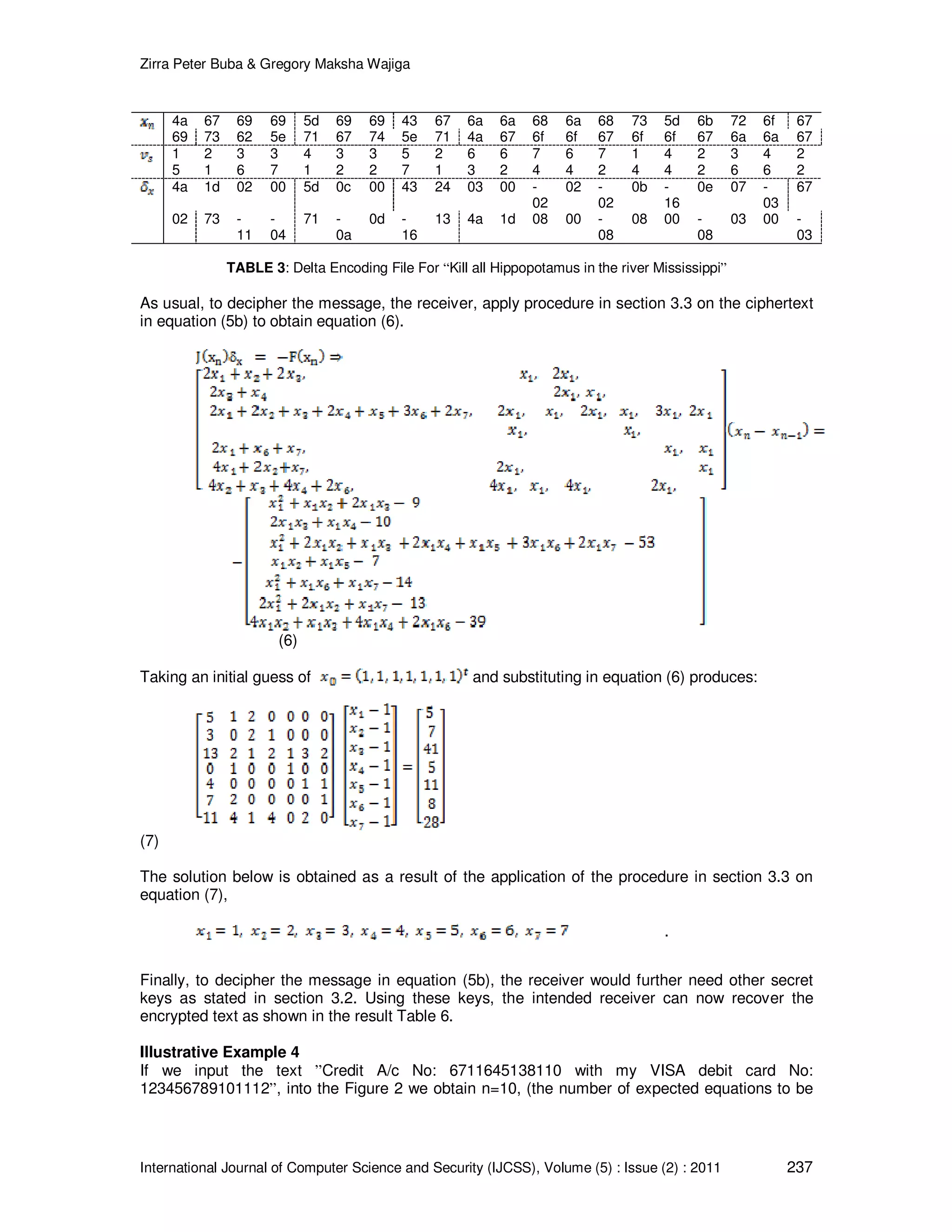


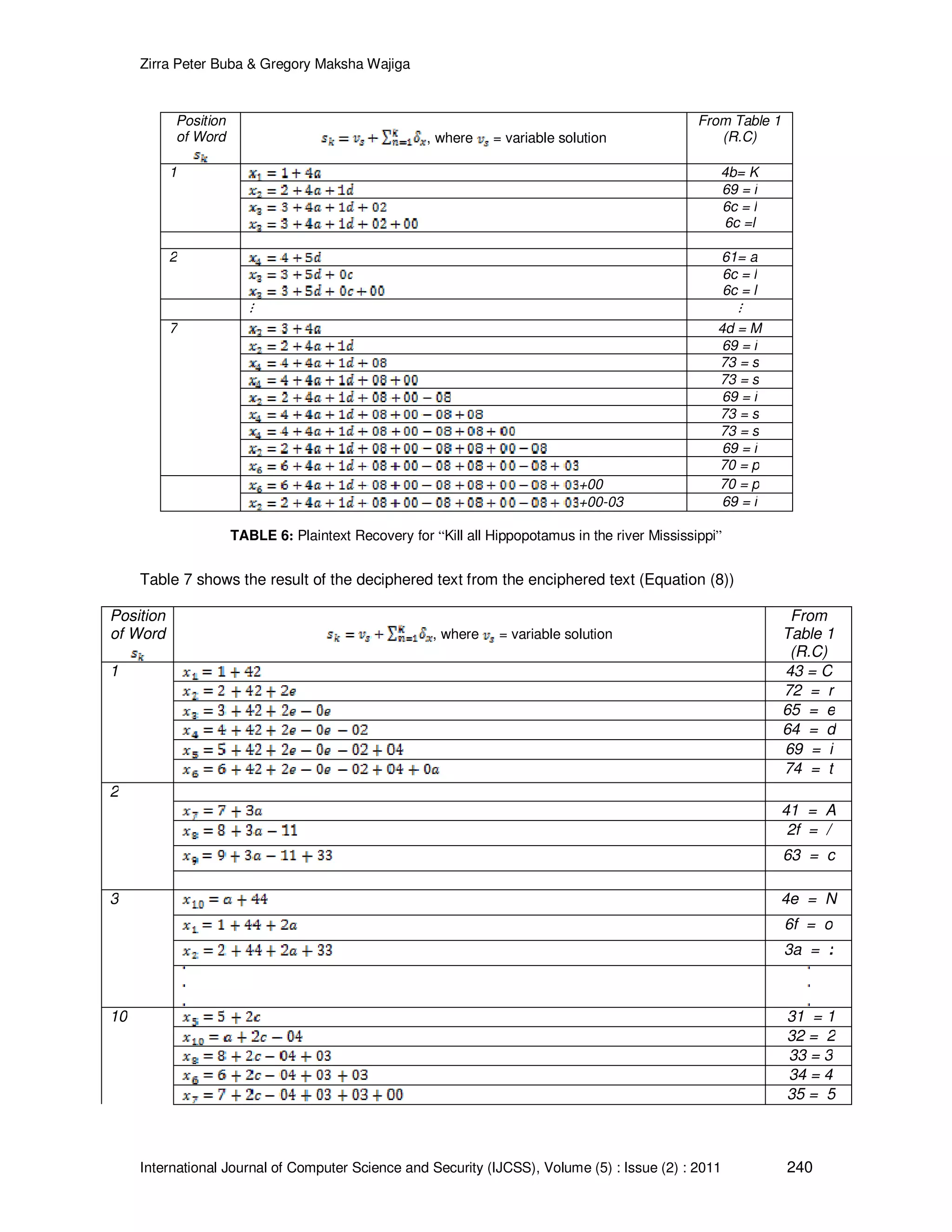
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 241 36 = 6 37 = 7 38 = 8 39 = 9 31 = 1 30 = 0 31 = 1 31 = 1 31 = 1 32 = 2 TABLE 7: Plaintext Recovery: Credit A/c No: 6711645138110 with my VISA debit card No: 123456789101112 In decompression, the characters are written as they appeared coupled with spaces between them and where there is an index value in place of new character, the index is interpreted and written in the place they appeared. Each time a word is written, a space is allowed between them. 4. DISCUSSION Examination of Tables 5, 6 and 7, showed that simple attack identified by [9] to find the decryption key by the cryptanalyst requires solving the systems of nonlinear equations in equations (1b), (5b) and (8), obtaining the values associated with the variable index in Tables 2, 3 and 4, the formula , and the lookup character position in table 1. This is notoriously difficult to obtain due to their high mathematical formulation. A good encryption algorithm should be designed so that, when used with sufficiently long keys, it becomes computationally infeasible to break as reported [12,13]. This is in accordance with another related literature that revealed that the strength of an encryption algorithm relied on the mathematical soundness of the algorithm [3]. It is also in agreement with an earlier study by [8] who revealed that resources required for revealing a secret message should be strong and complex enough through a hiding key. This study is designed on similar encryption techniques that use sufficiently long keys. The study also indicated that one key is used to encipher plaintext into ciphertext and another different key to decipher that ciphertext into plaintext as depicted in Tables 5, 6, and 7 [14,15,16]. The proposed scheme avoids the problem of sharing keys associated with the symmetric cryptography [16,17] that there is less risk associated with a public key than the symmetric key and the security based on that key is not compromised [18]. This study is designed on similar encryption techniques that use asymmetric key. The study showed that, the decipher keys were transmitted to the intended receiver secretly through a different medium such as email, short message service or fax machine to the receiver before the receiver can have access to the plaintext. On the basis of this results, it is evident that unauthorized user will find it difficult to decrypt the message without the knowledge of the secret keys [3], since they were not transmitted together with the ciphered message. The strength of an encryption scheme is relies on the secrecy of the key [12]. This placed another level of security on the data in store or transit. From the results of the study it is clear that there is confidentiality, non- repudiation and integrity of our sensitive and classified information over the Internet from the hands of Internet terrorist as highlighted by [2] and [16]. This is due to the robustness design of the proposed algorithms.](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-15-2048.jpg)
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 242 5. CONCLUSION This paper has practically demonstrated how people can secure their vital and sensitive information stored or transmitted via insecure communication channels from cryptanalysts by using strong encryption and decryption keys. The proposed algorithm has proven to withstand any type of the attack. 7. REFERENCES [1] B. Figg. (2004). Cryptography and Network Security. Internet: http:/www.homepages.dsu.edu/figgw/Cryptography%20&%20Network%2 0Security.ppt. [March 16, 2010]. [2] A. Kahate, Cryptography and Network Security (2nd ed.). New Delhi: Tata McGraw Hill, 2008. [3] M. Milenkovic. Operating System: Concepts and Design, New York: McGrew-Hill, Inc., 1992. [4] P.R. Zimmermann. An Introduction to Cryptography. Germany: MIT press. Available: http://www.pgpi.org/doc/pgpintro, 1995, [March 16, 2009]. [5] W. Stallings. Cryptography and Network Security (4th ed.). Englewood (NJ):Prentice Hall, 1995. [6] V. Potdar and E. Chang. “Disguising Text Cryptography Using Image Cryptography,” International Network Conference, United Kingdom: Plymouth, 2004. [7] S.A.M. Diaa, M.A.K. Hatem, and M.H. Mohiy (2010). “Evaluating The Performance of Symmetric Encryption Algorithms” International Journal of Network Security, 2010, 10(3), pp.213-219 [8] T. Ritter. “Crypto Glossary and Dictionary of Technical Cryptography’. Internet: www.ciphersbyritter.com/GLOSSARY.HTM , 2007, [August 17, 2009] [9] K.M. Alallayah, W.F.M. Abd El-Wahed, and A.H. Alhamani.“Attack Of Against Simplified Data Encryption Standard Cipher System Using Neural Networks”. Journal of Computer Science,2010, 6(1), pp. 29-35. [10] D. Rudolf. “Development and Analysis of Block Cipher and DES System”. Internet: http://www.cs.usask..ca/~dtr467/400/, 2000, [April 24, 2009] [11] H. Wang. (2002). Security Architecture for The Teamdee System. An unpublished MSc Thesis submitted to Polytechnic Institution and State University, Virginia, USA. [12] G.W. Moore. (2001). Cryptography Mini-Tutorial. Lecture notes University of Maryland School of Medicine. Internet: http://www.medparse.com/whatcryp.htm [March 16, 2009]. [13] T. Jakobsen and L.R. Knudsen. (2001). Attack on Block of Ciphers of Low Algebraic Degree. Journal of Cryptography, New York, 14(3), pp.197-210. [14] N. Su, R.N. Zobel, and F.O. Iwu. “Simulation in Cryptographic Protocol Design and Analysis.” Proceedings 15th European Simulation Symposium, University of Manchester, UK., 2003.](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-16-2048.jpg)
![Zirra Peter Buba & Gregory Maksha Wajiga International Journal of Computer Science and Security (IJCSS), Volume (5) : Issue (2) : 2011 243 [15] C.K. Laudan, and C.G. Traver. E-Commerce .Business .Technology .Society (2nd ed.). New York: Pearson Education, Inc., 2004. [16] G.C. Kessler. Handbook on Local Area Networks: An Overview of Cryptography. United Kingdom: Auerbach. Available http://www.garykessler.net/library/crypto.html. 2010, [January 3, 2010]. [17] M.A. Yusuf. Data Security: Layered Approach Algorithm. An unpublished MSc Thesis submitted to Abubakar Tafawa Balewa University, Bauchi, Nigeria, 2007. [18] J. Talbot and D. Welsh. Complexity and Cryptography: An Introduction. New York: Cambridge University Press, 2006](https://image.slidesharecdn.com/ijcss-450-160109122049/75/Cryptographic-Algorithms-For-Secure-Data-Communication-17-2048.jpg)