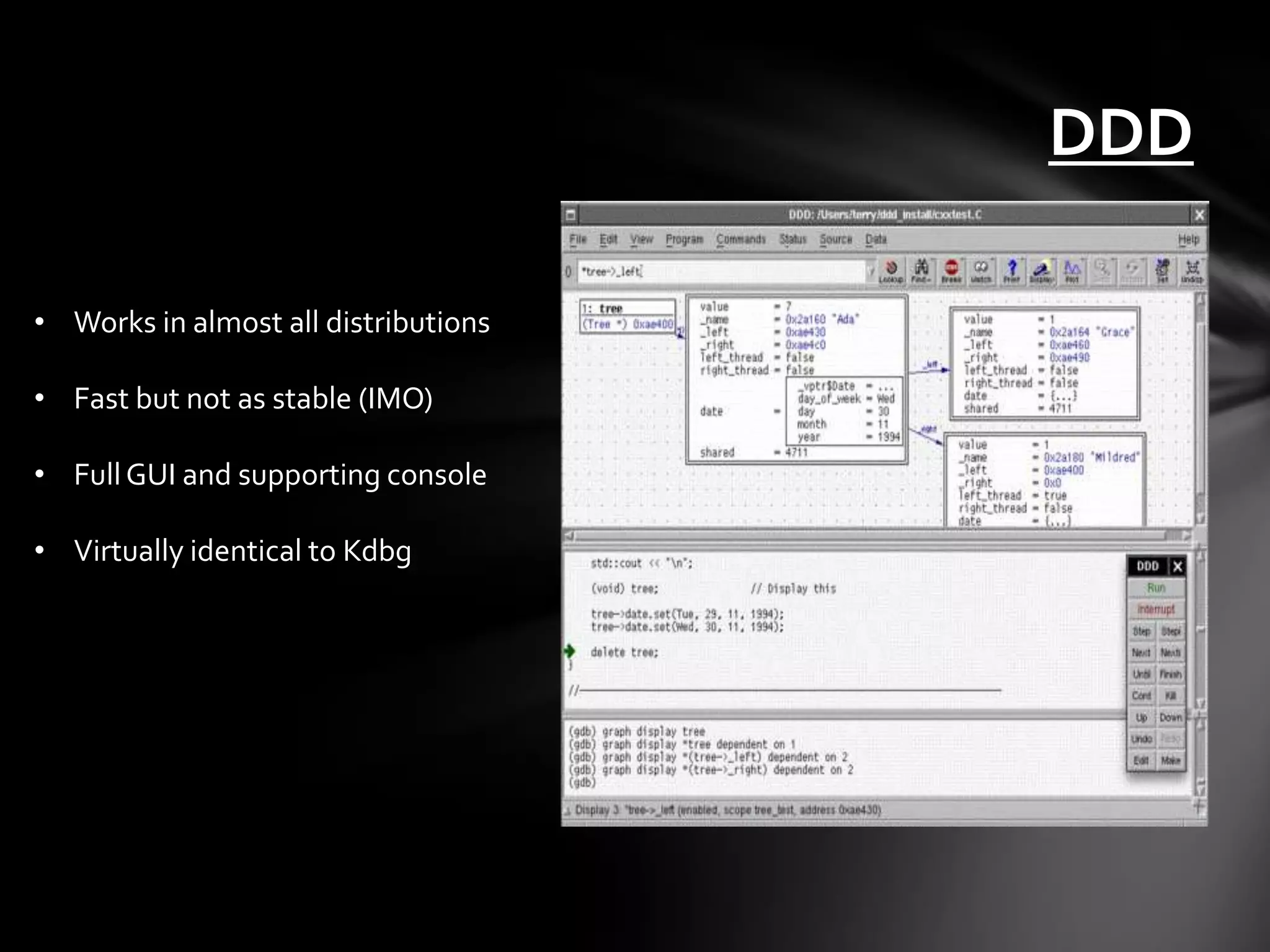
The document provides an overview of ELF (Executable and Linkable Format) files, assembly language, CPU registers, memory addressing, basic assembly instructions, and debugging tools like GDB. It describes the sections and structure of ELF files, number bases, memory layout, common instructions, and how to use GDB commands to debug programs.



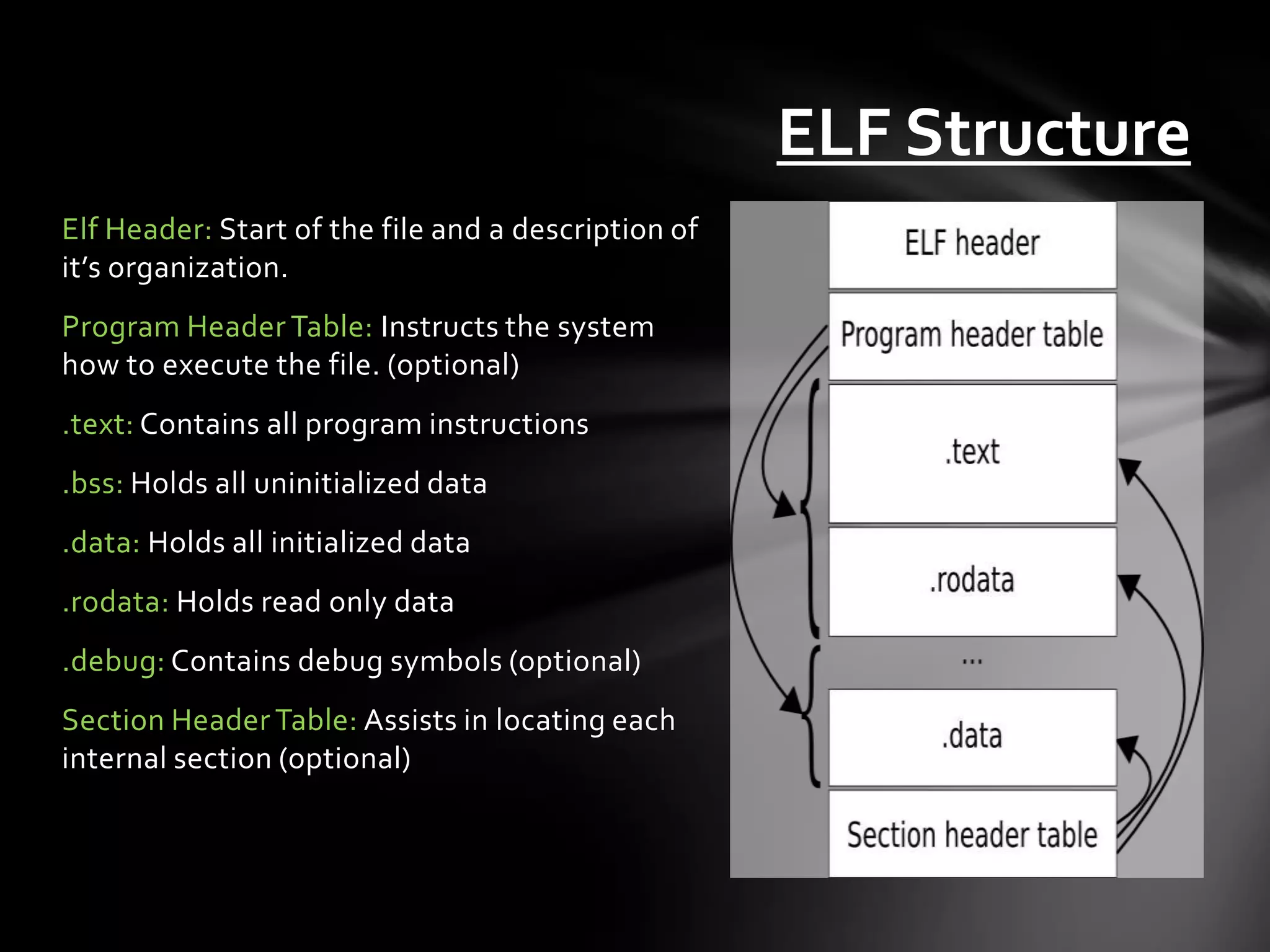


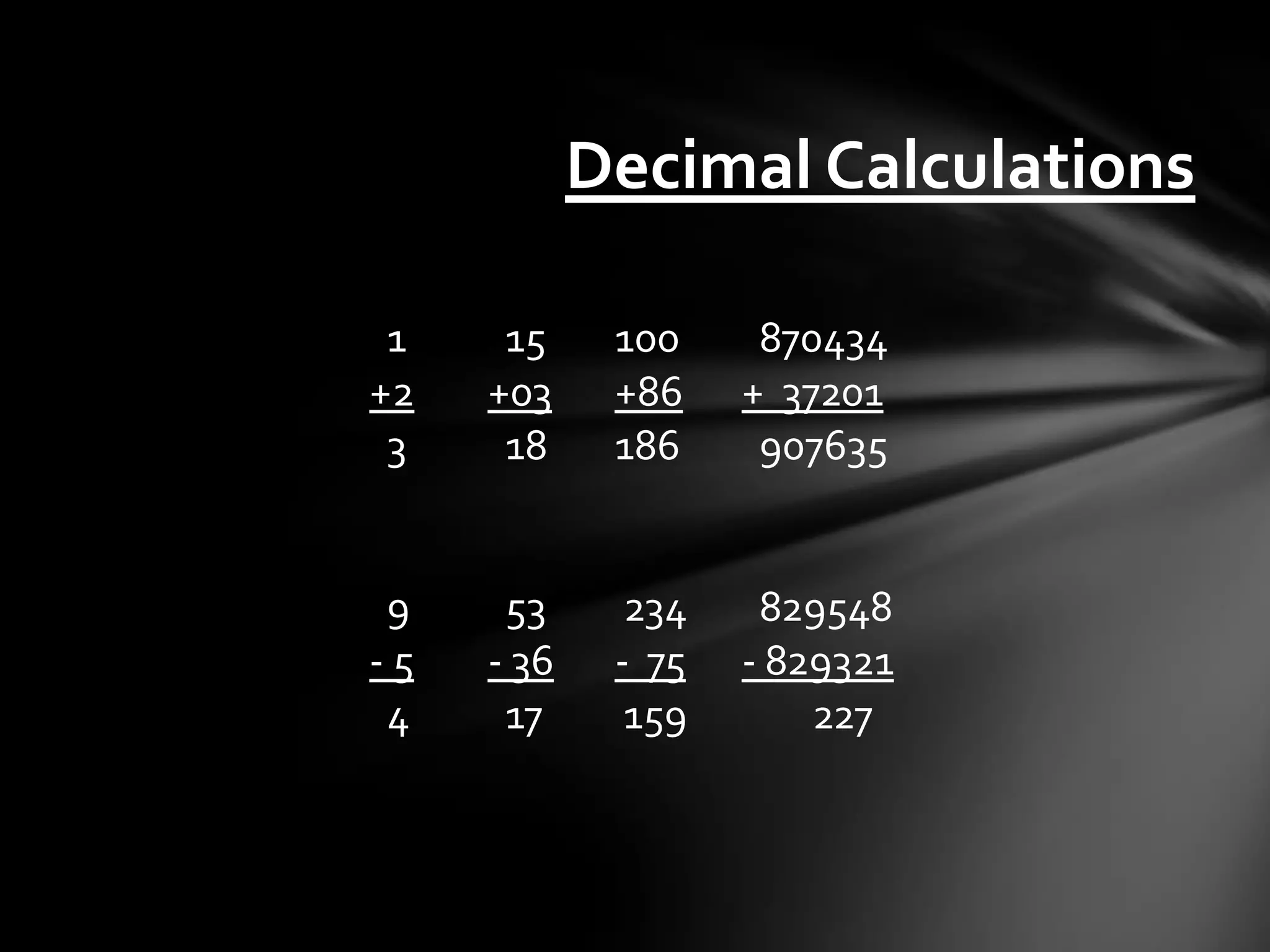
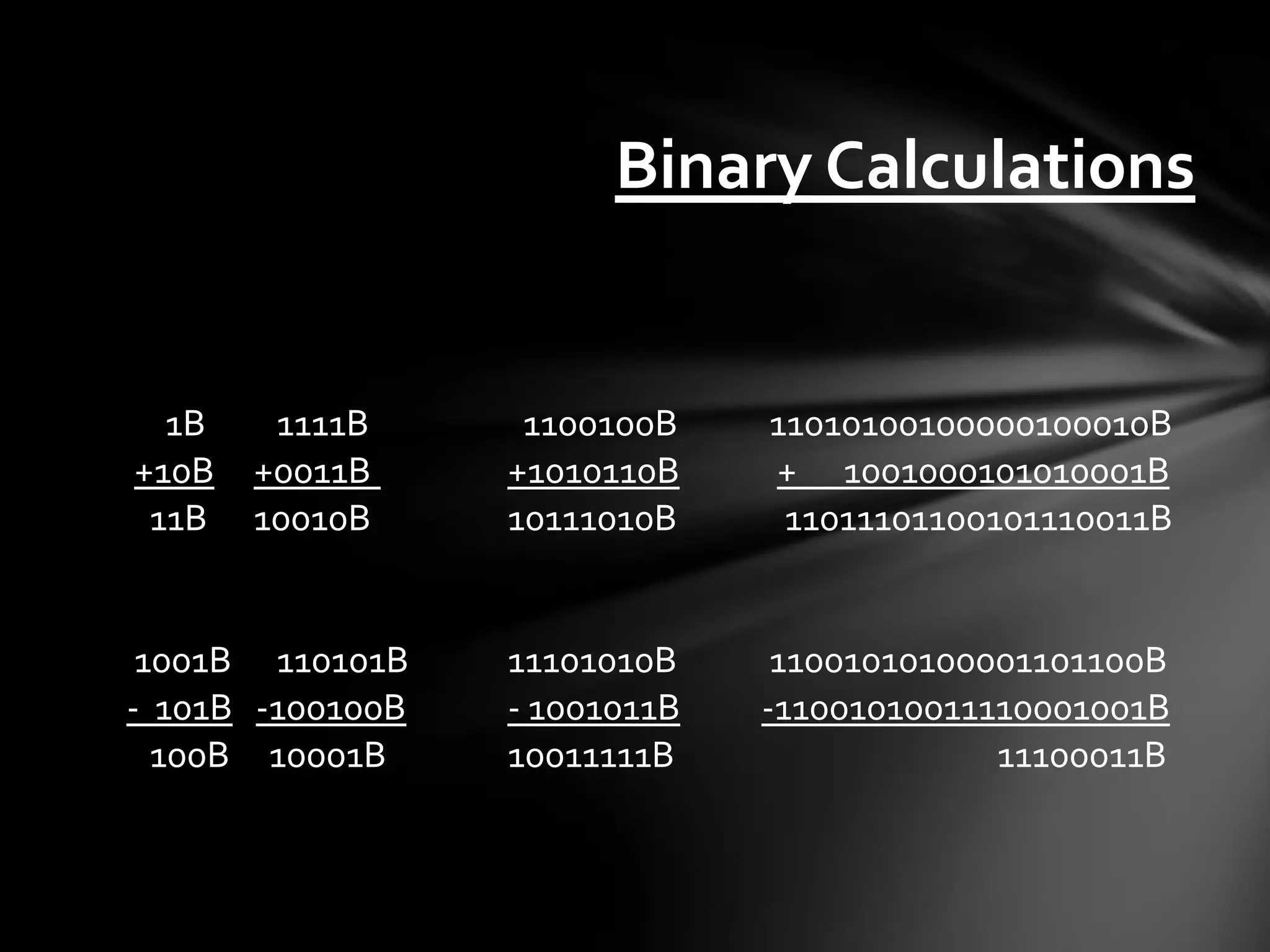
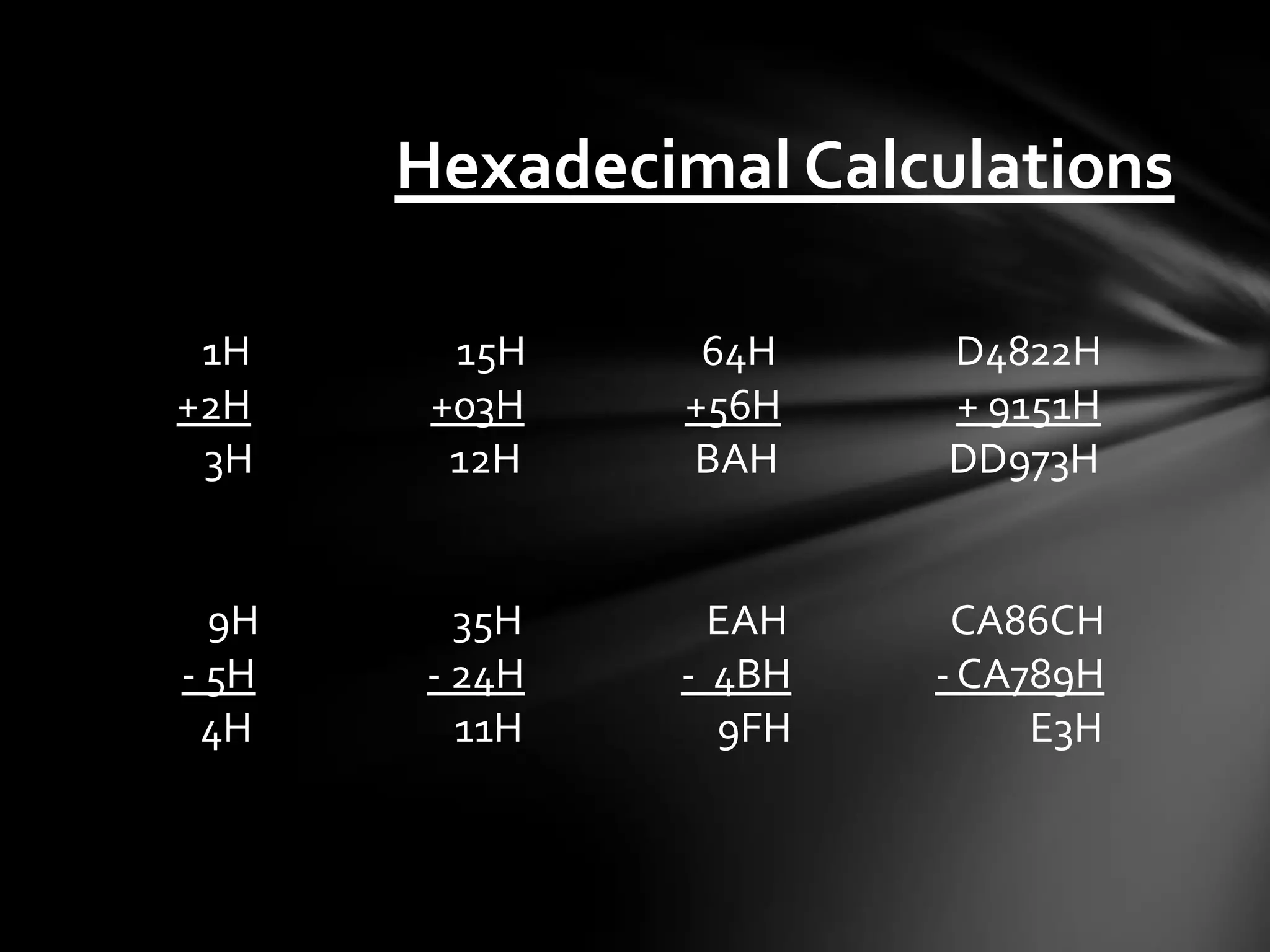

![The Stack • Stores data temporarily as an application may need it. • ESP = Top of the Stack EBP = Bottom of the Stack, or top of previous • Addressed by offsets of espebp or direct memory locations • Last in, First out (LIFO) or First in, Last out (FILO) • Push [value] – Adds to top of the Stack, then decreases ESP accordingly • Pop [value] – Removes from top of the Stack, then increases ESP • Dynamically allocated, 32 bits wide • Grows from higher memory down](https://image.slidesharecdn.com/introductiontodebugginglinuxapplications-120706111608-phpapp01/75/Introduction-to-debugging-linux-applications-13-2048.jpg)

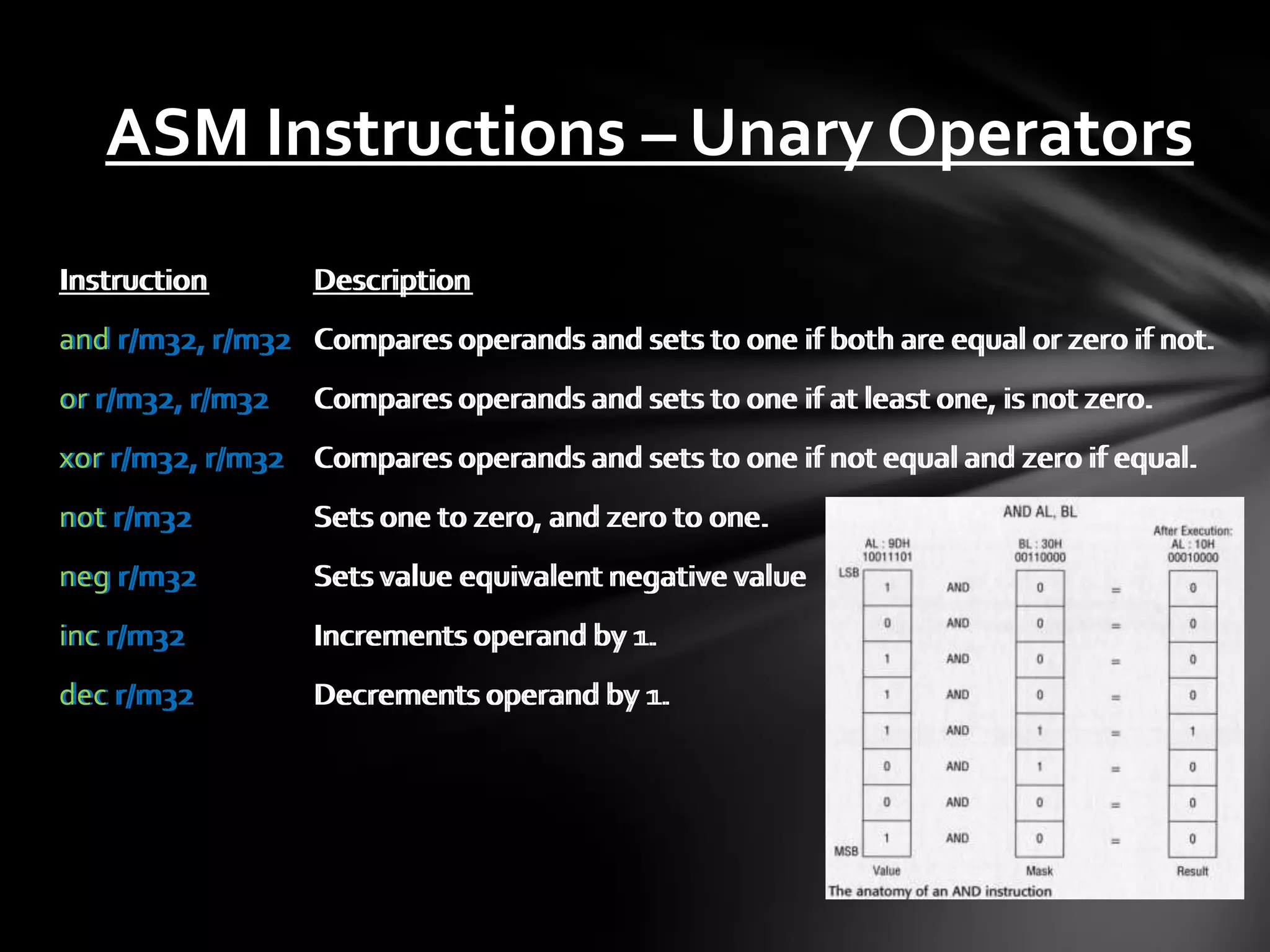
![ASM Instructions – Bit Manipulation Instruction Description shl r/m32, count Shifts bits left [count] times, stores overflow in CF, inserts zero shr r/m32, count Shifts bits right [count] times, stores overflow in CF, inserts zero rol r/m32, count Rotates bits from left and inserts on right, no CF use ror r/m32, count Rotates bits from right and inserts on left, no CF use rcl r/m32, count Rotates left to right, storing the first value rotated off, and stored in CF, previous CF is set as right most value rcr r/m32, count Rotates left to right, storing the first value rotated off, and stored in CF, previous CF is set as right most value](https://image.slidesharecdn.com/introductiontodebugginglinuxapplications-120706111608-phpapp01/75/Introduction-to-debugging-linux-applications-18-2048.jpg)


![GBD Commands Instruction Description -tui Used while starting for semi-gui Break [line] Stops execution at set line and allows for inspection Tbreak [line] Stops execution at set line the first time hit only Watch [condition] Performs commands for condition arguments set Print [variable] Displays a variables value while execution is stopped Frame [number] Diplays trace of set stack frame Backtrace Displays entire stack layout](https://image.slidesharecdn.com/introductiontodebugginglinuxapplications-120706111608-phpapp01/75/Introduction-to-debugging-linux-applications-25-2048.jpg)
![GDB Instructions Run [arguments] Starts program execution with supplied arguments Continue Continues normal execution after being paused Step Executes line Stepi Executes next ASMmachine instruction Next Executes next line then pauses, skips over called functions Nexti Executes next ASMmachine instruction and pauses](https://image.slidesharecdn.com/introductiontodebugginglinuxapplications-120706111608-phpapp01/75/Introduction-to-debugging-linux-applications-26-2048.jpg)
