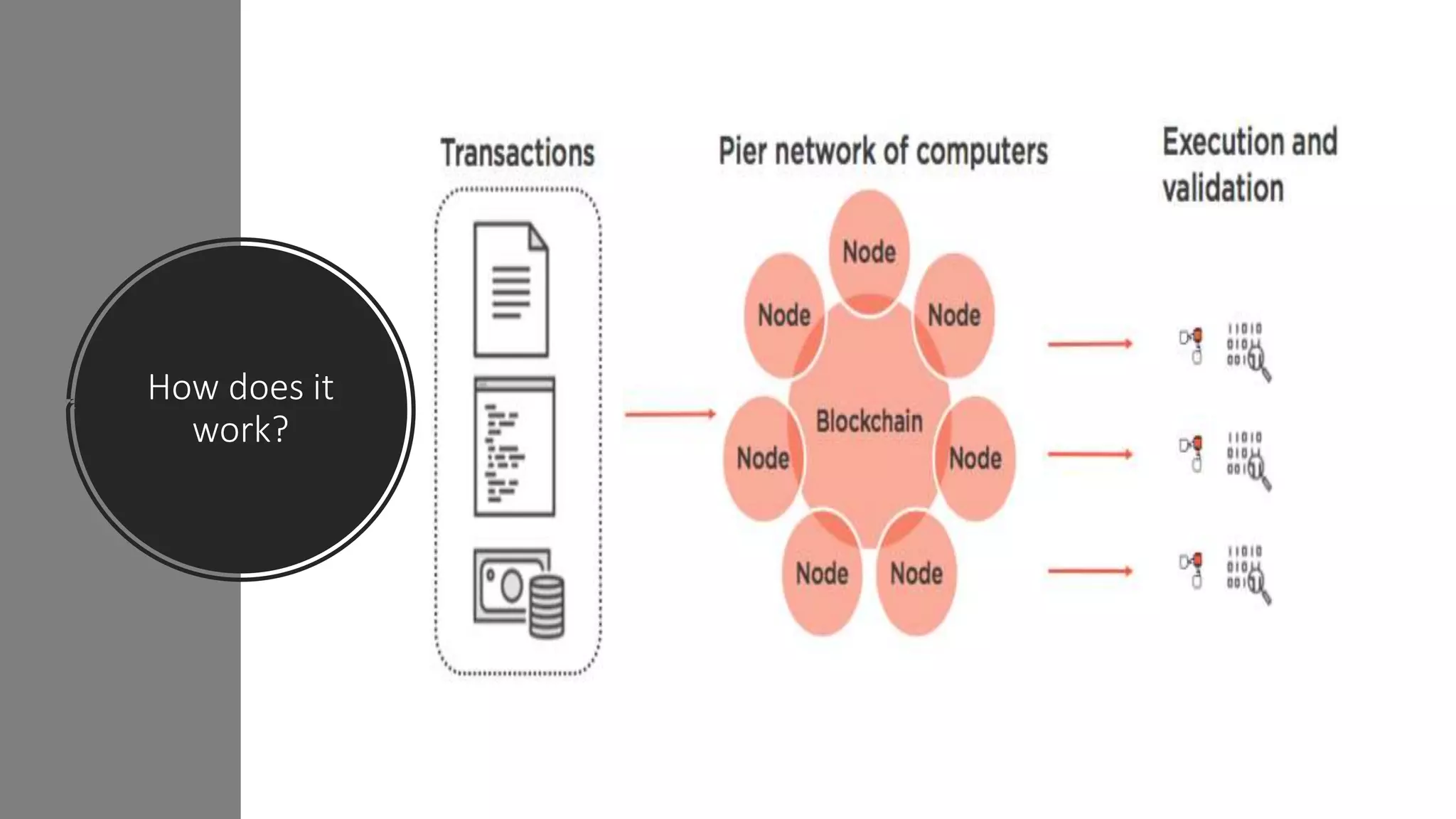
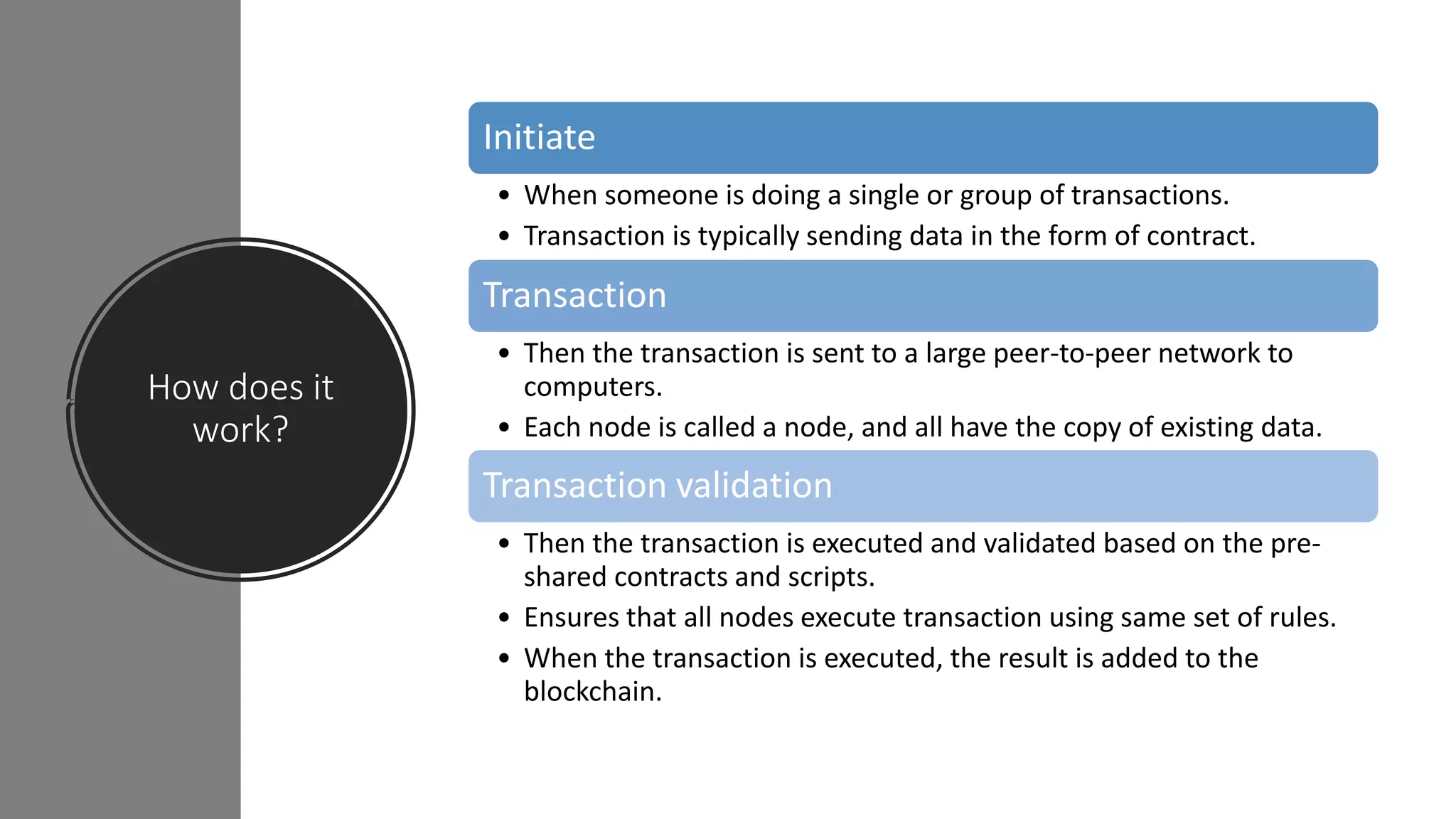
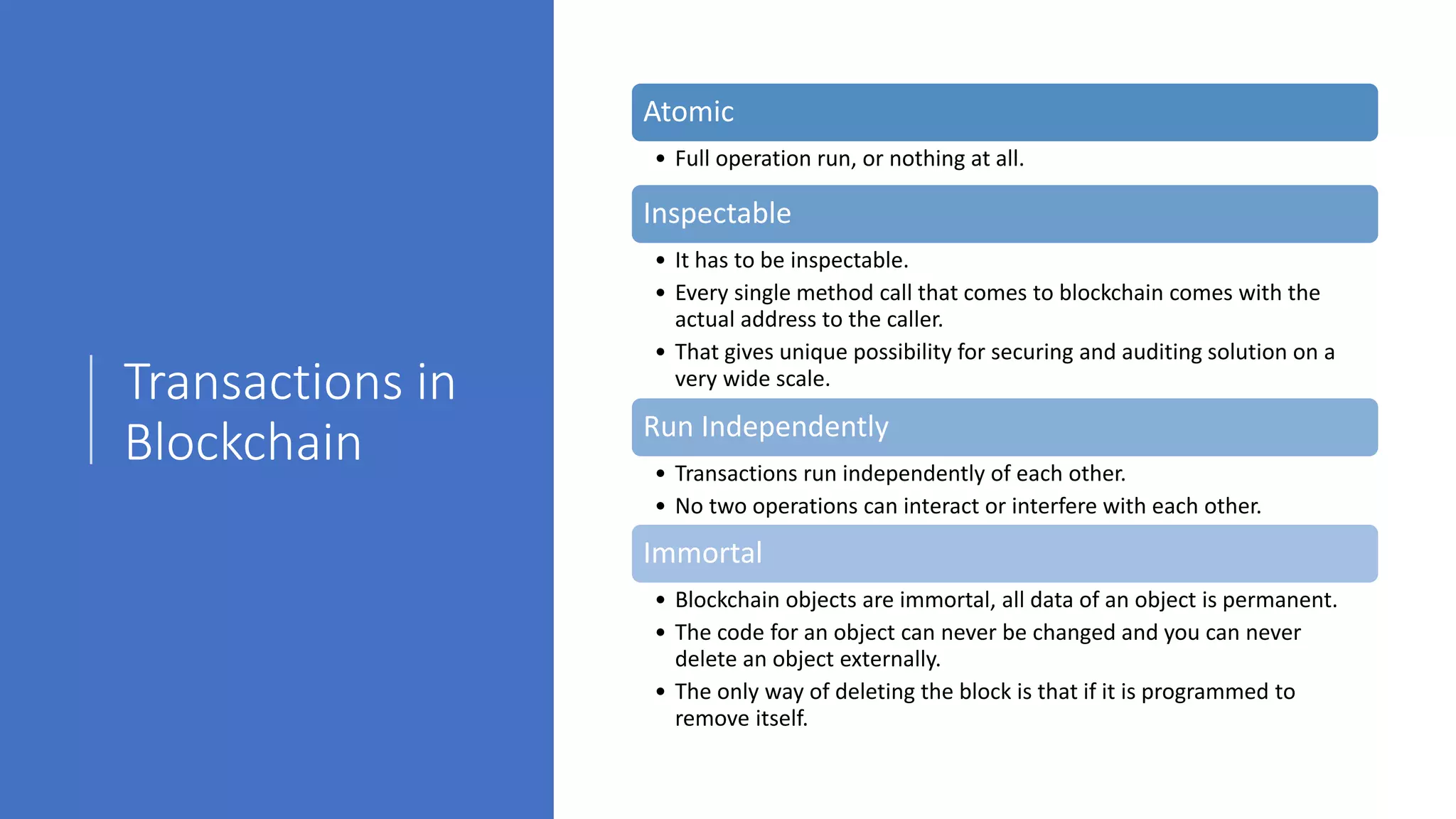
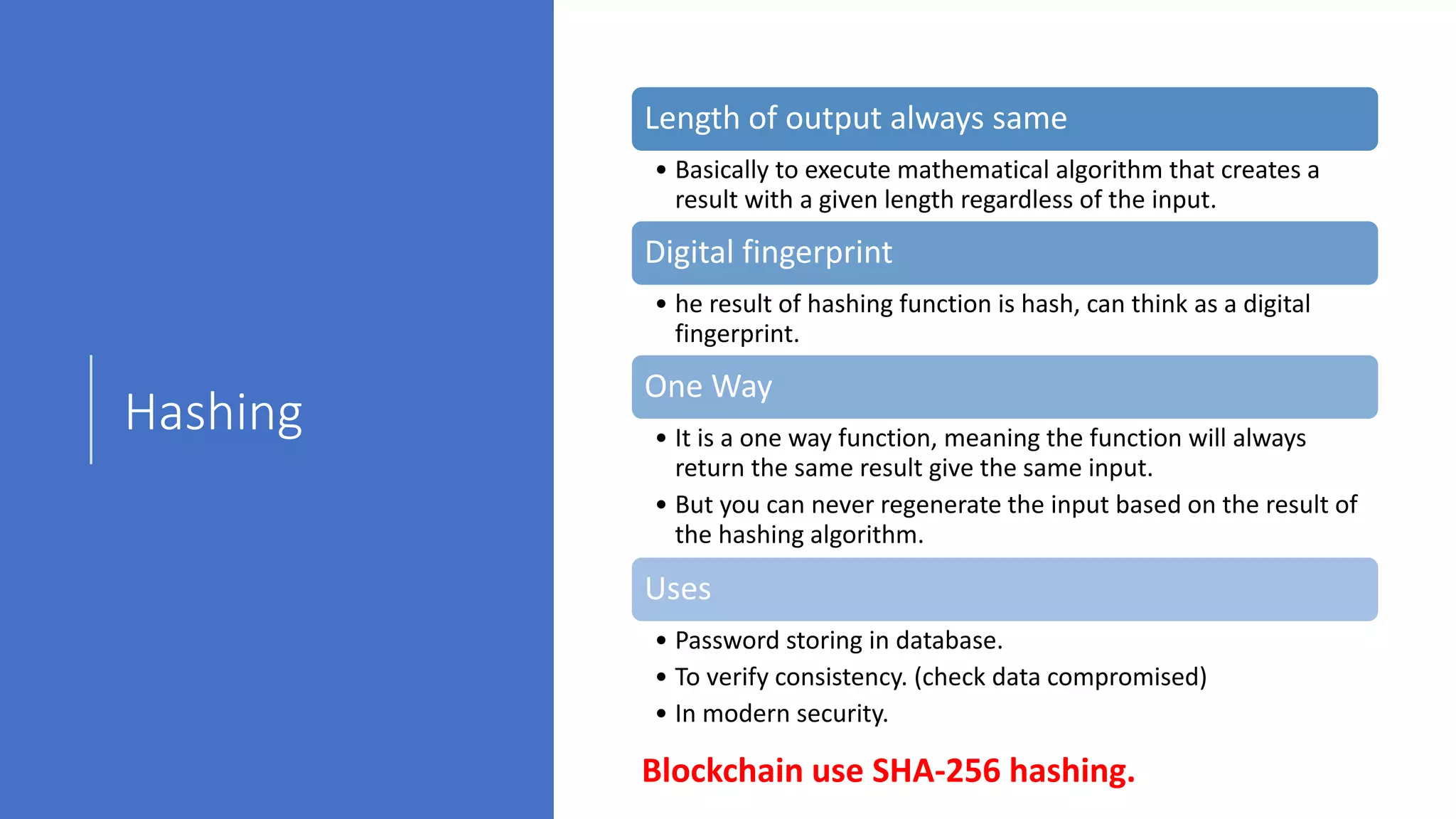
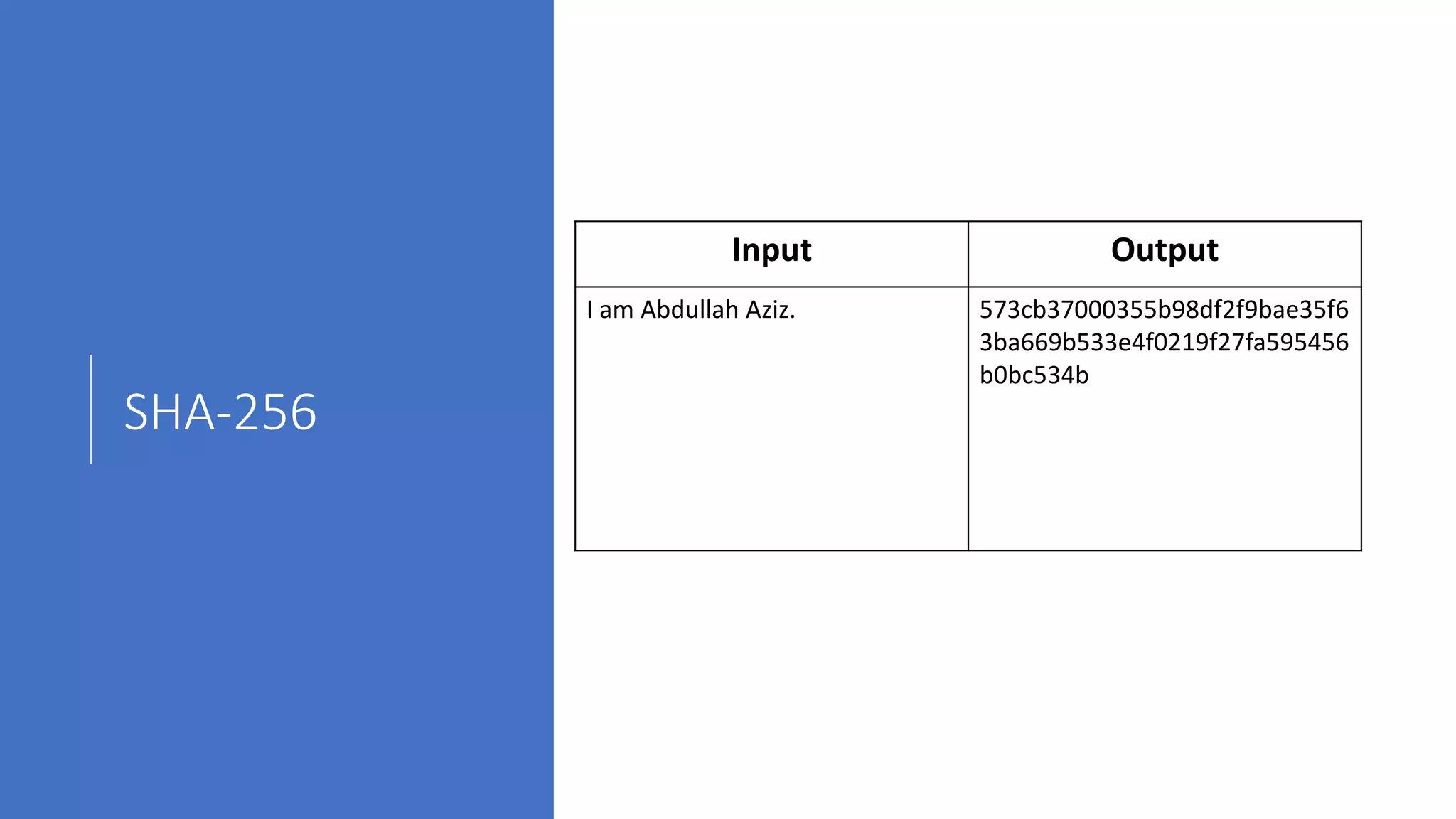
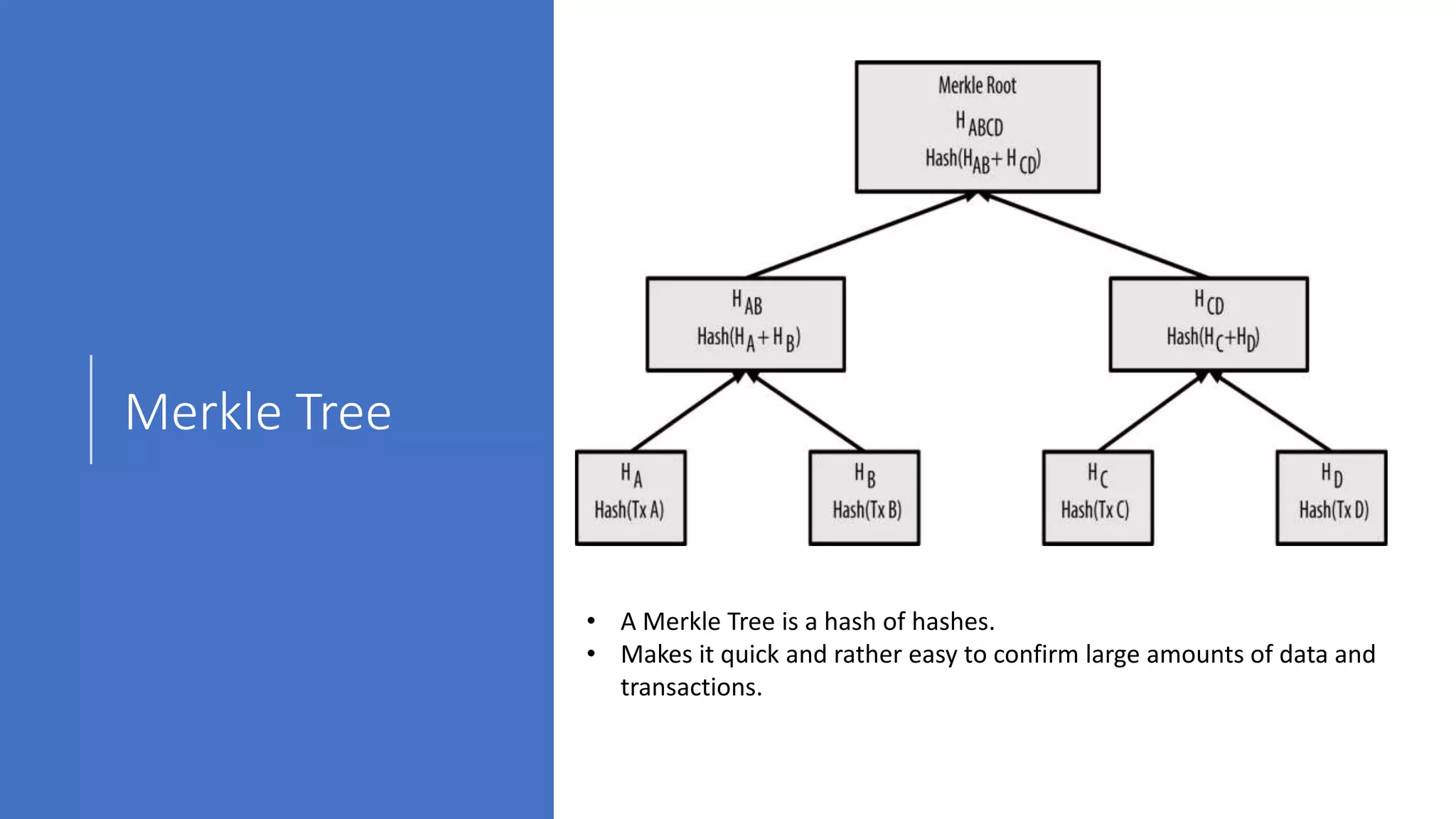
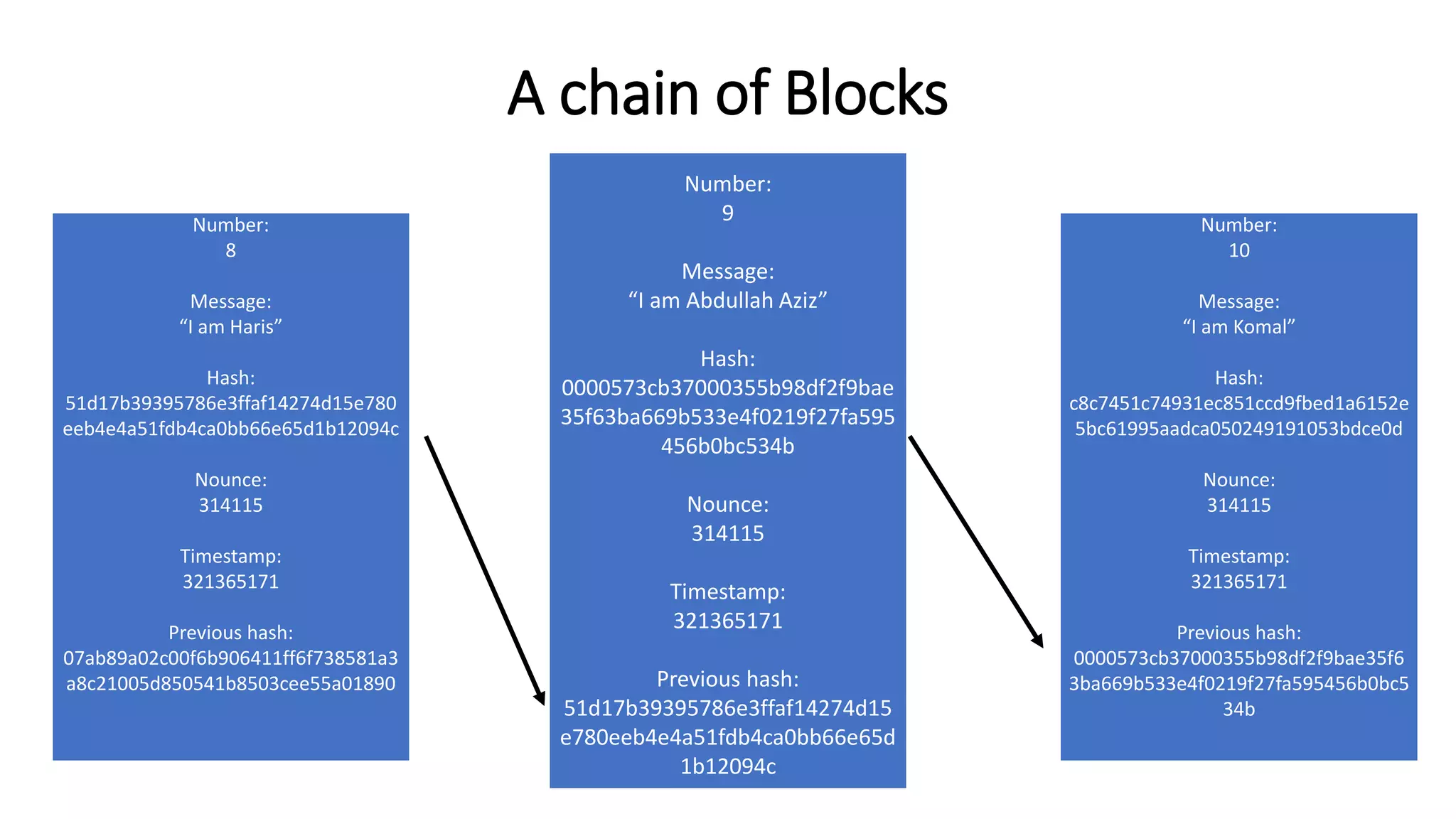
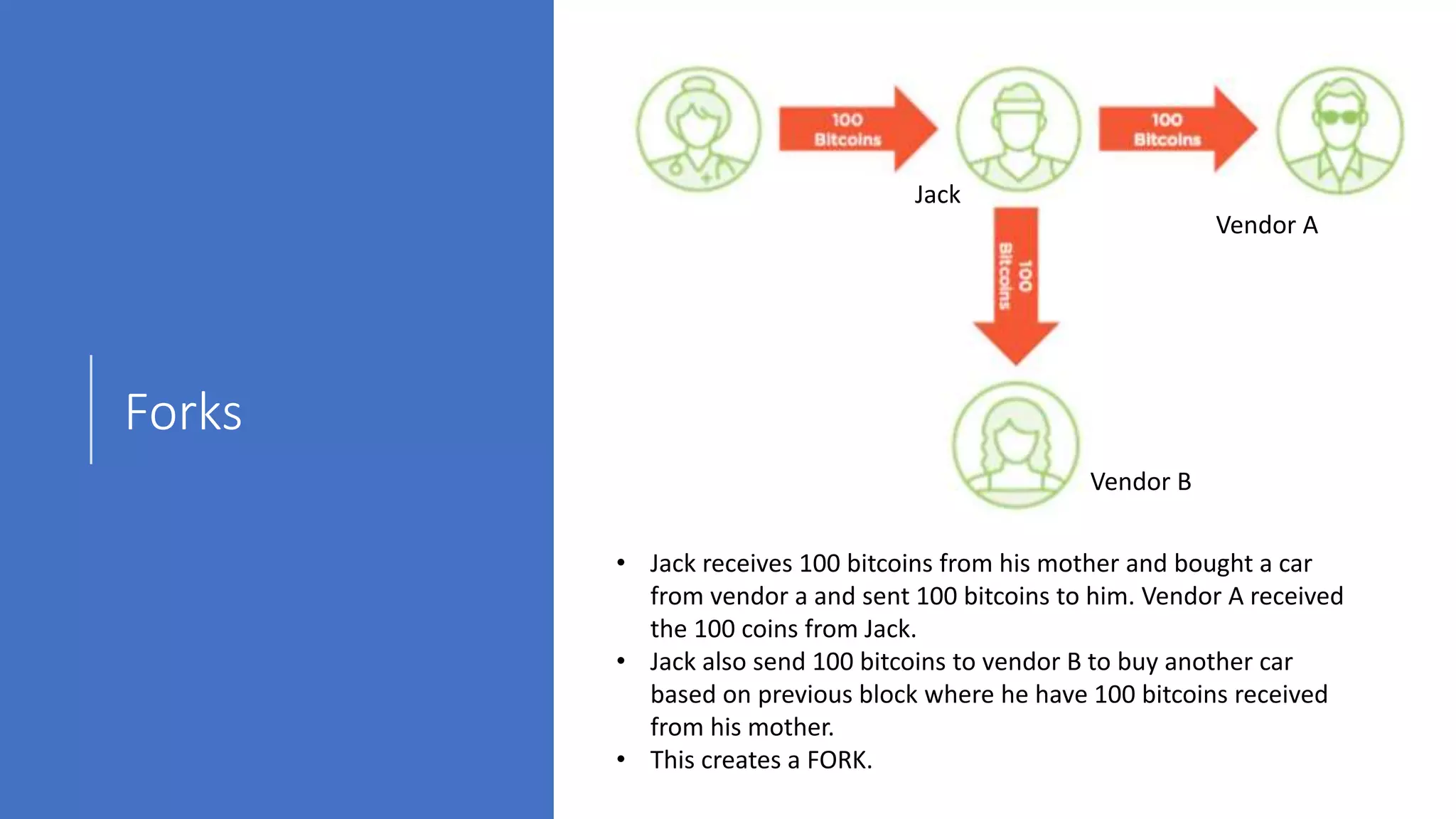
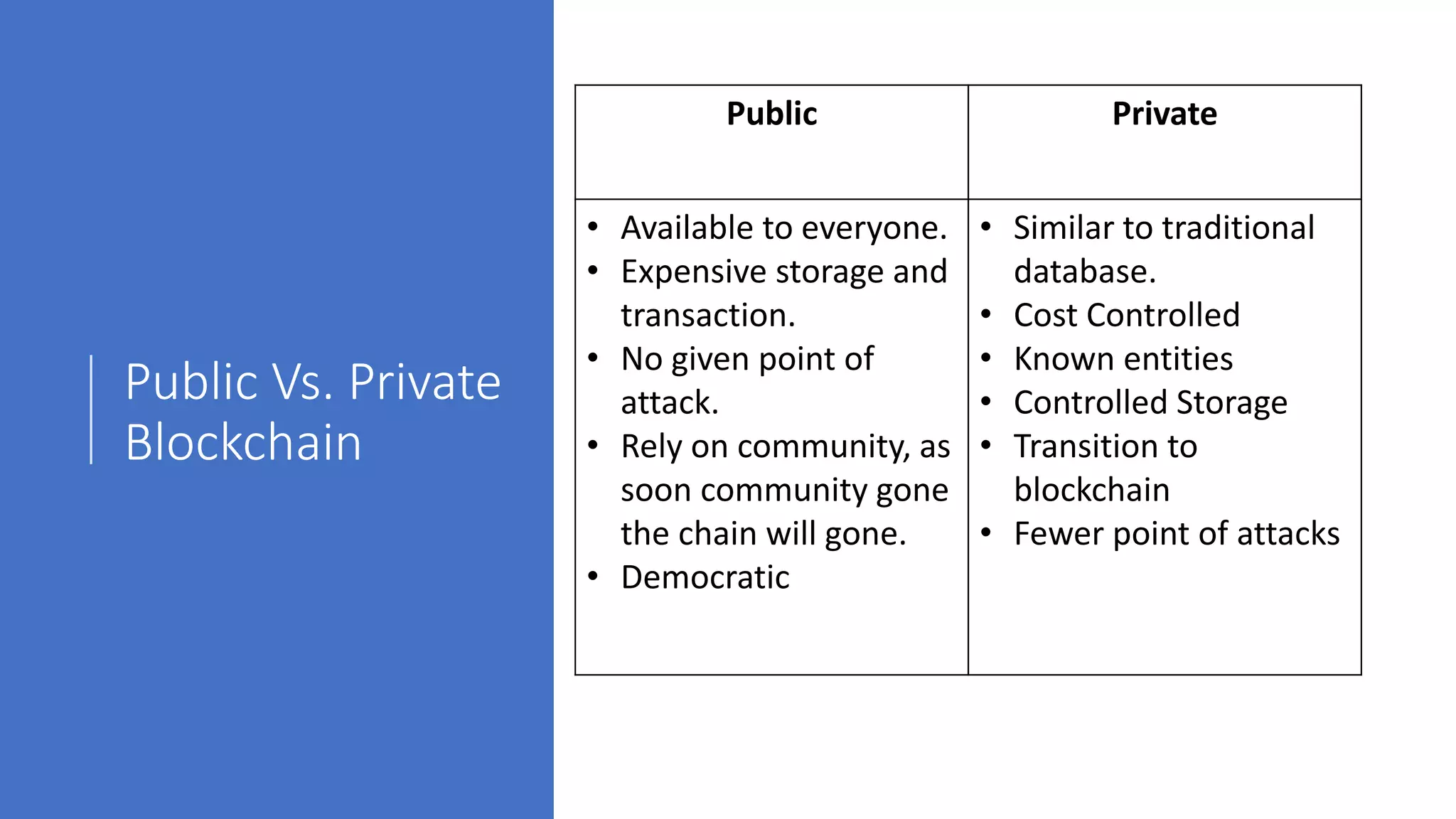
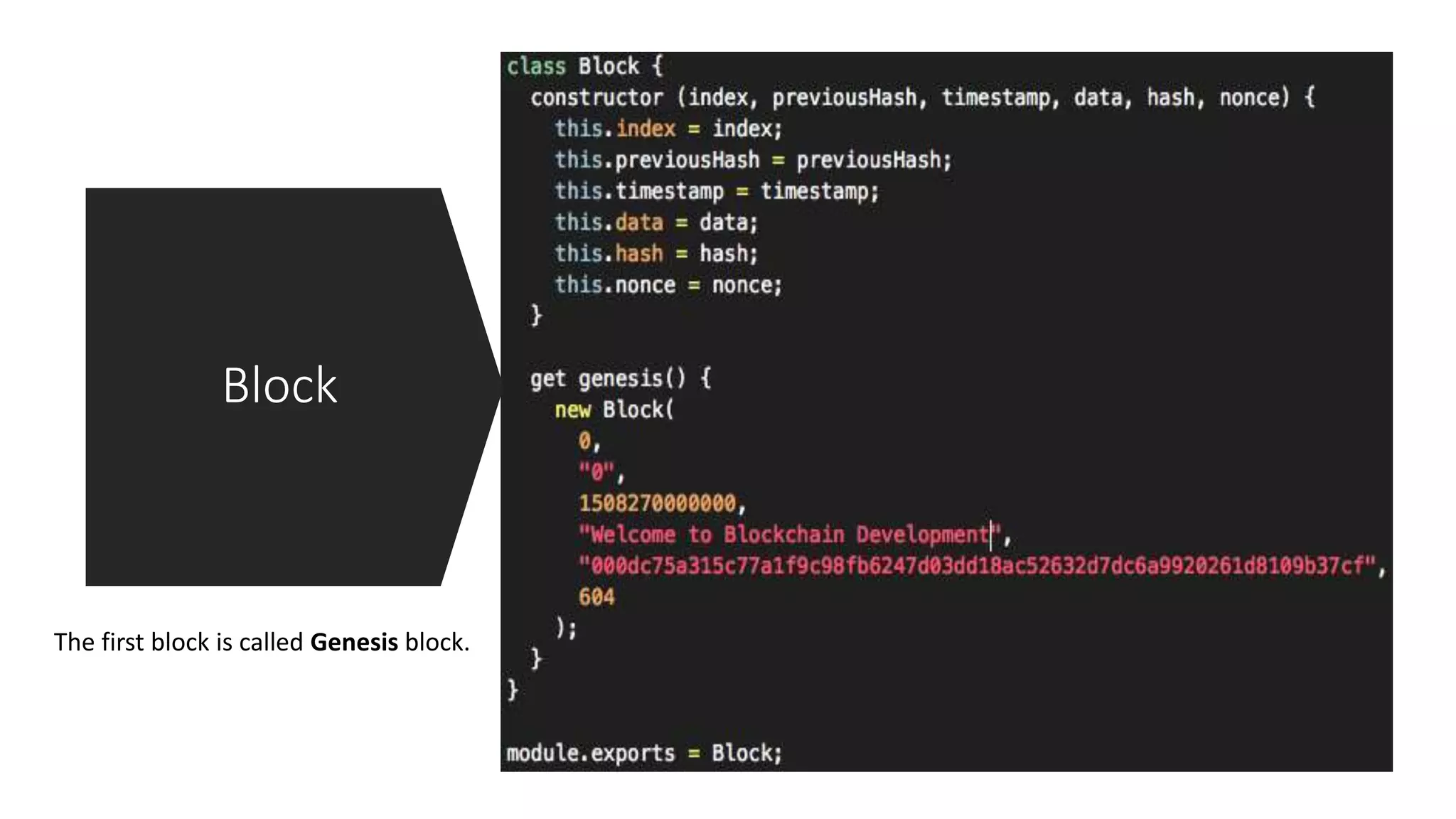
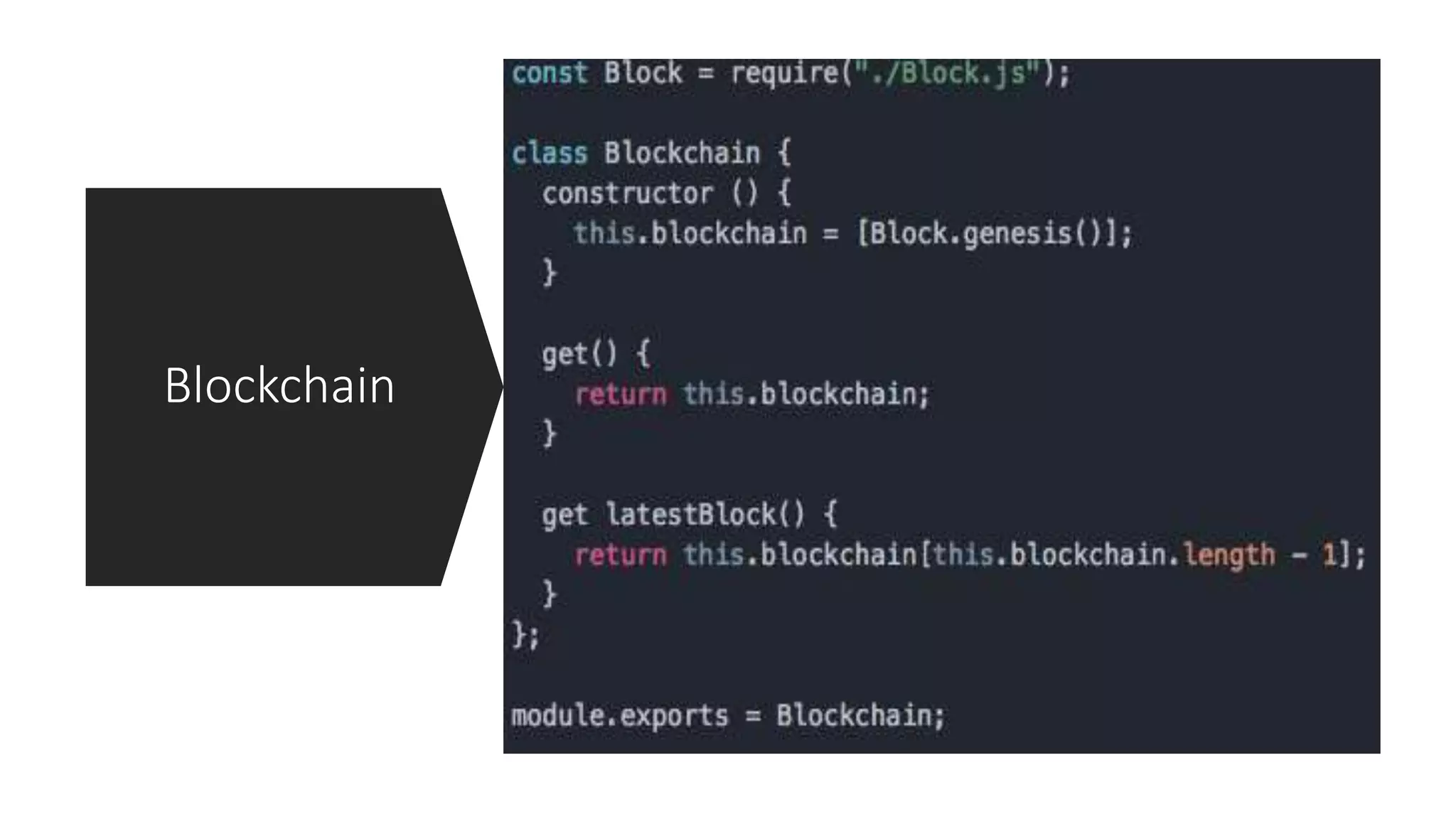
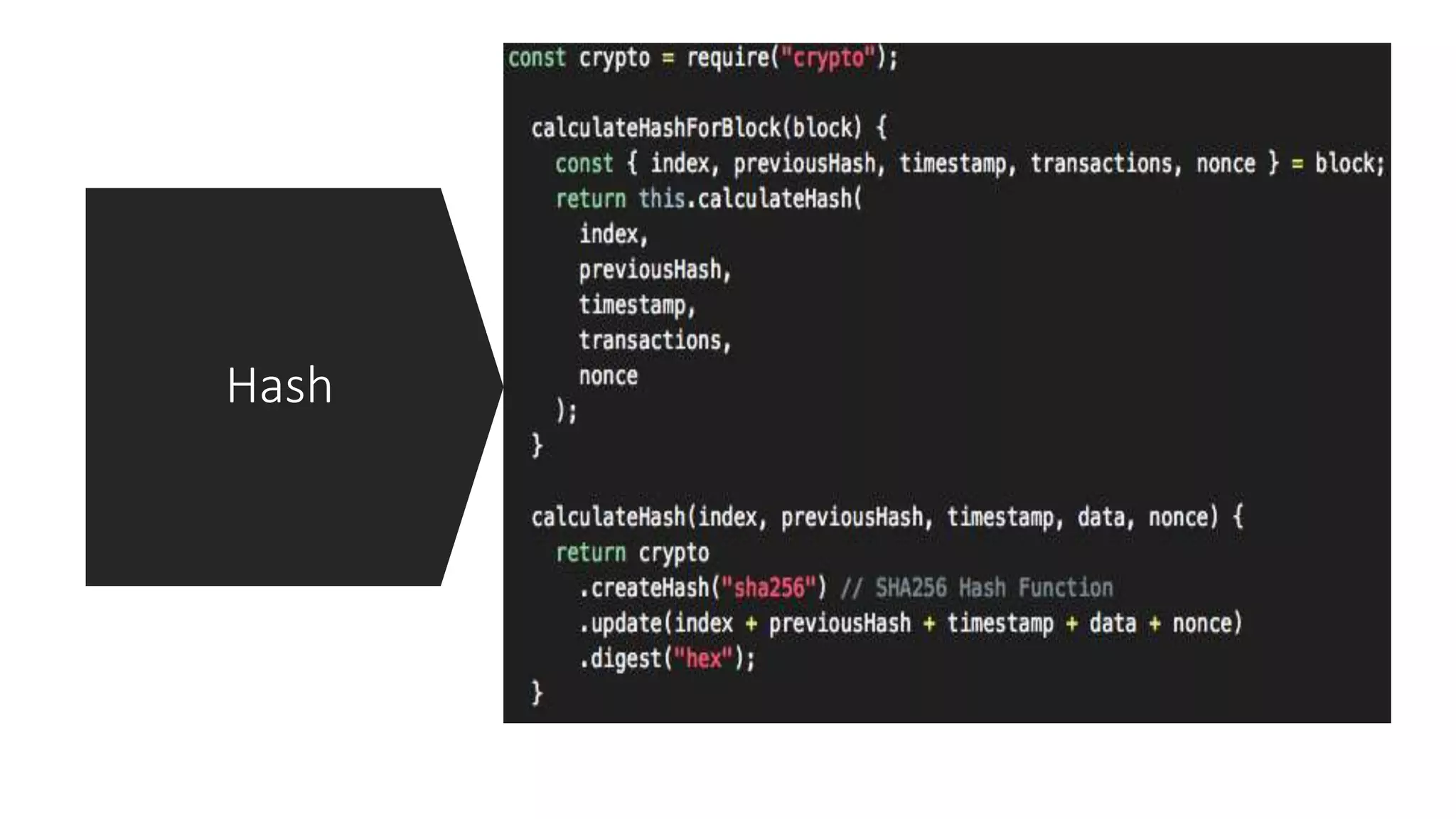
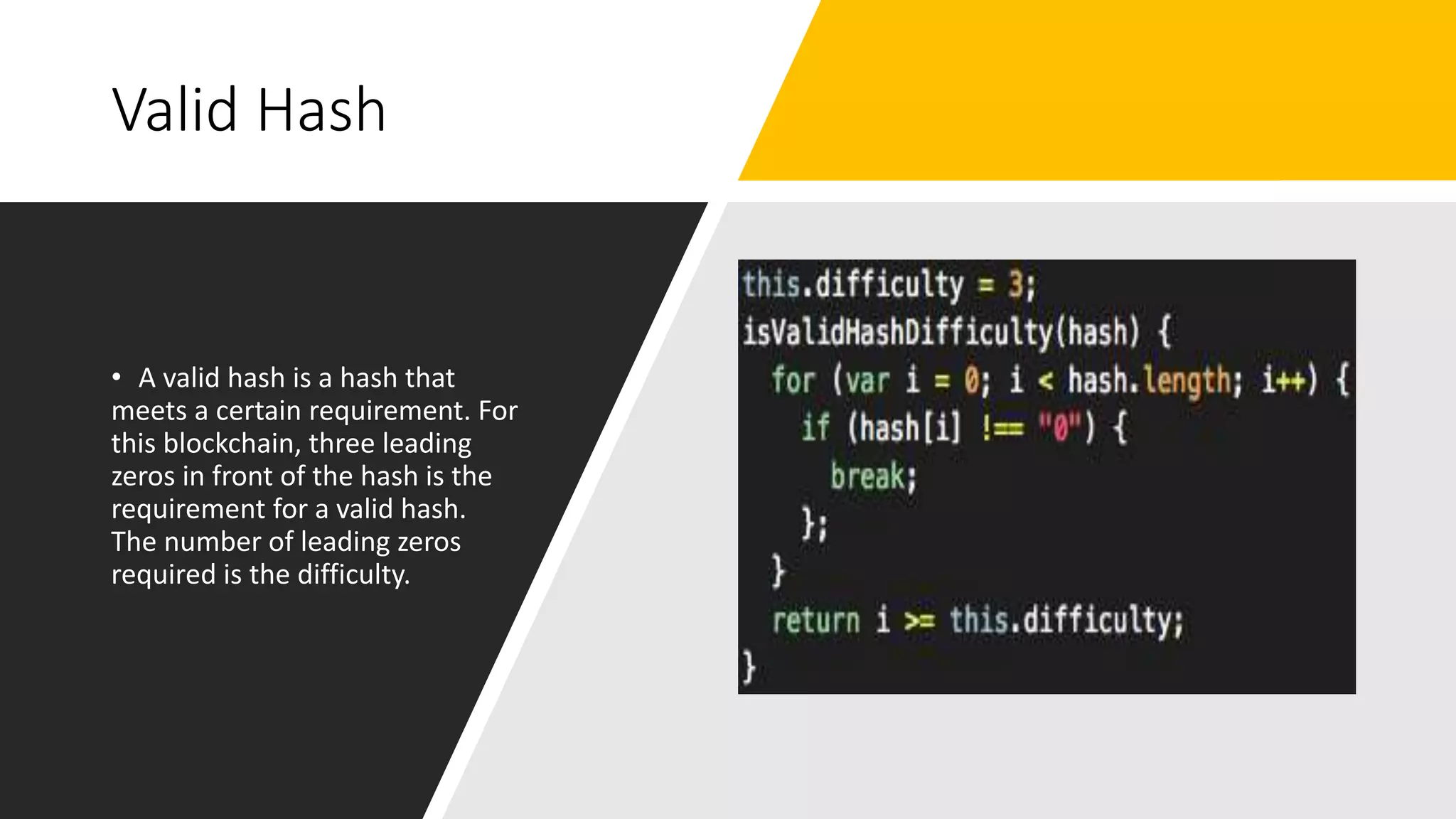
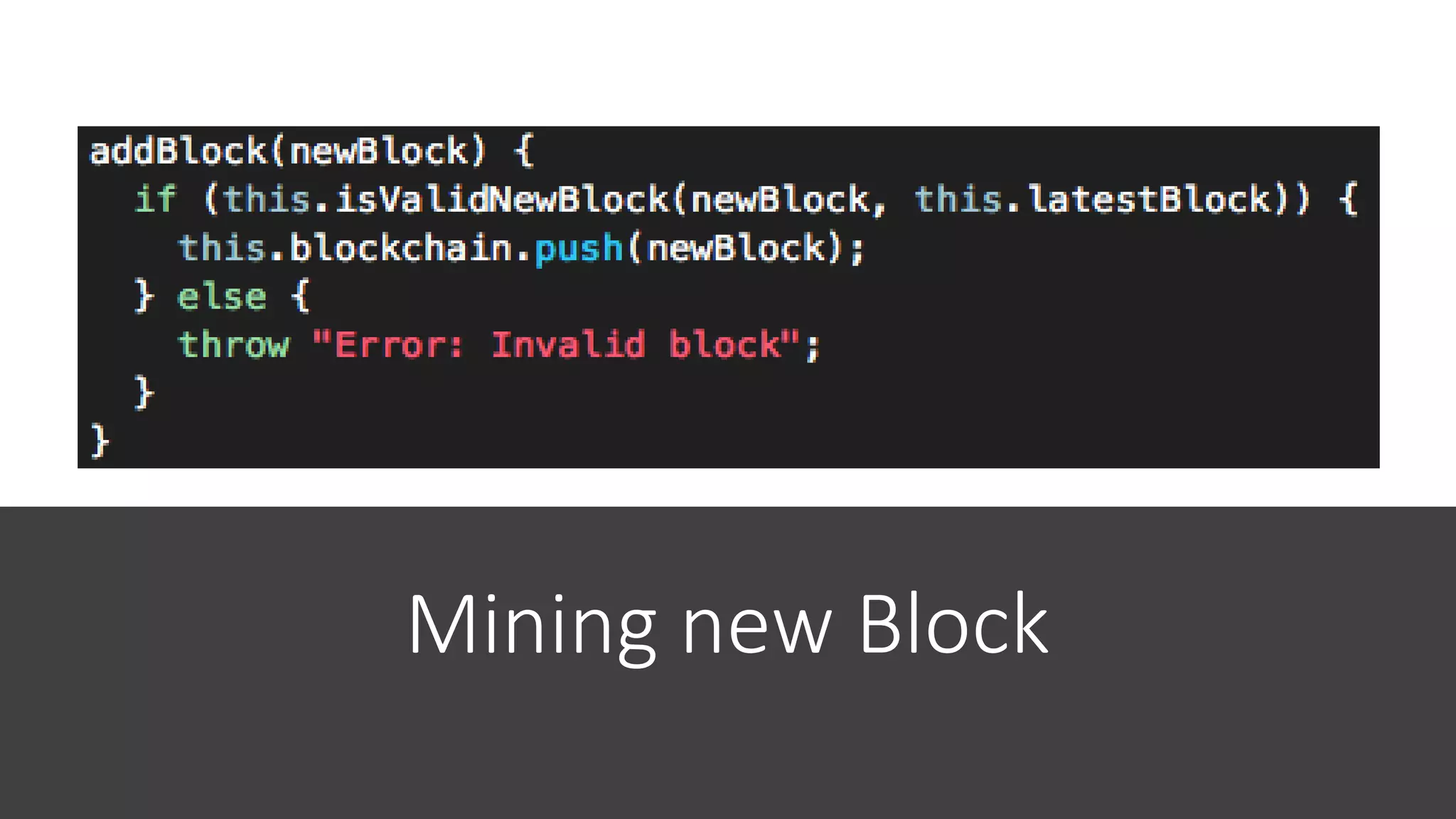
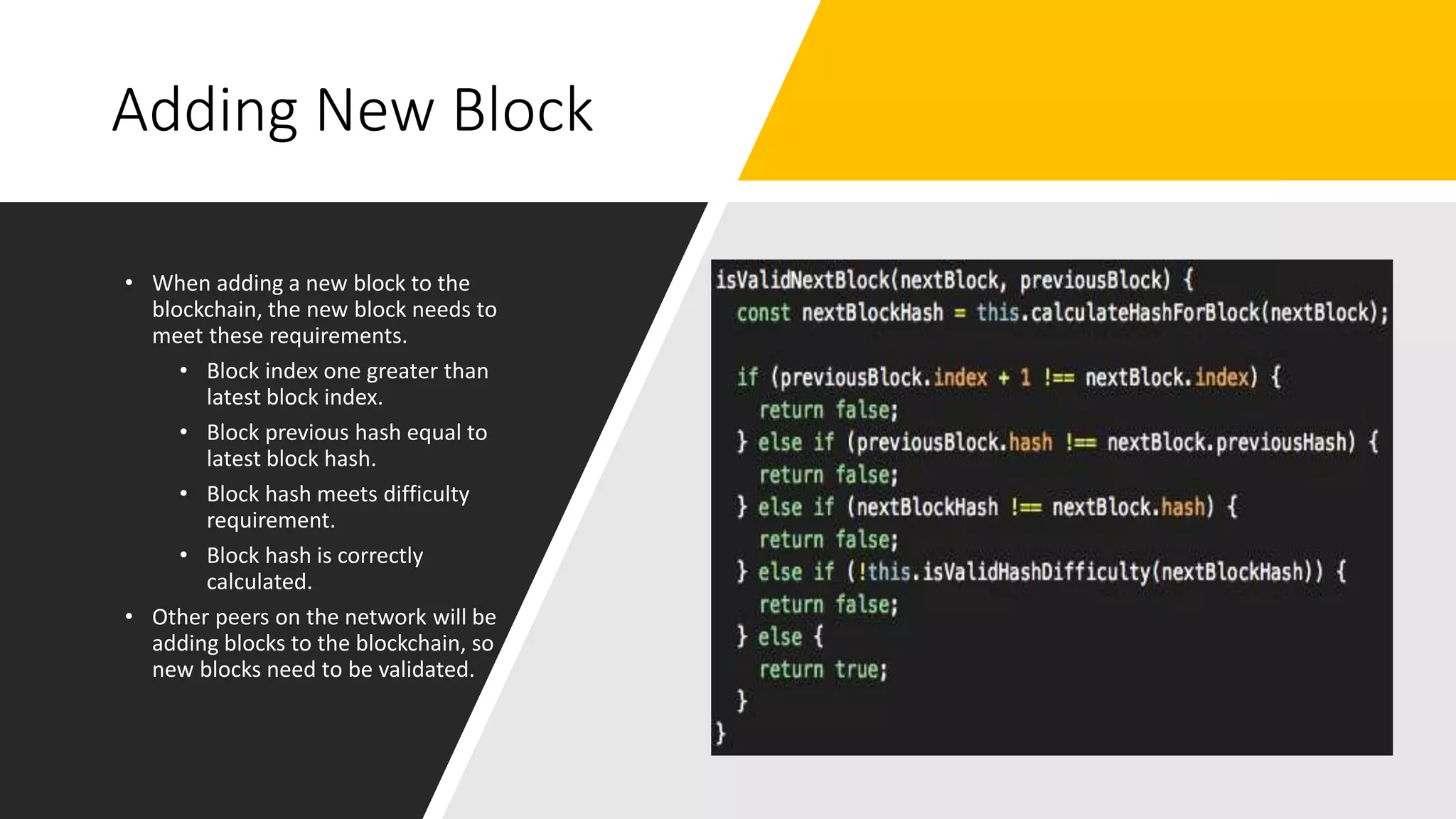
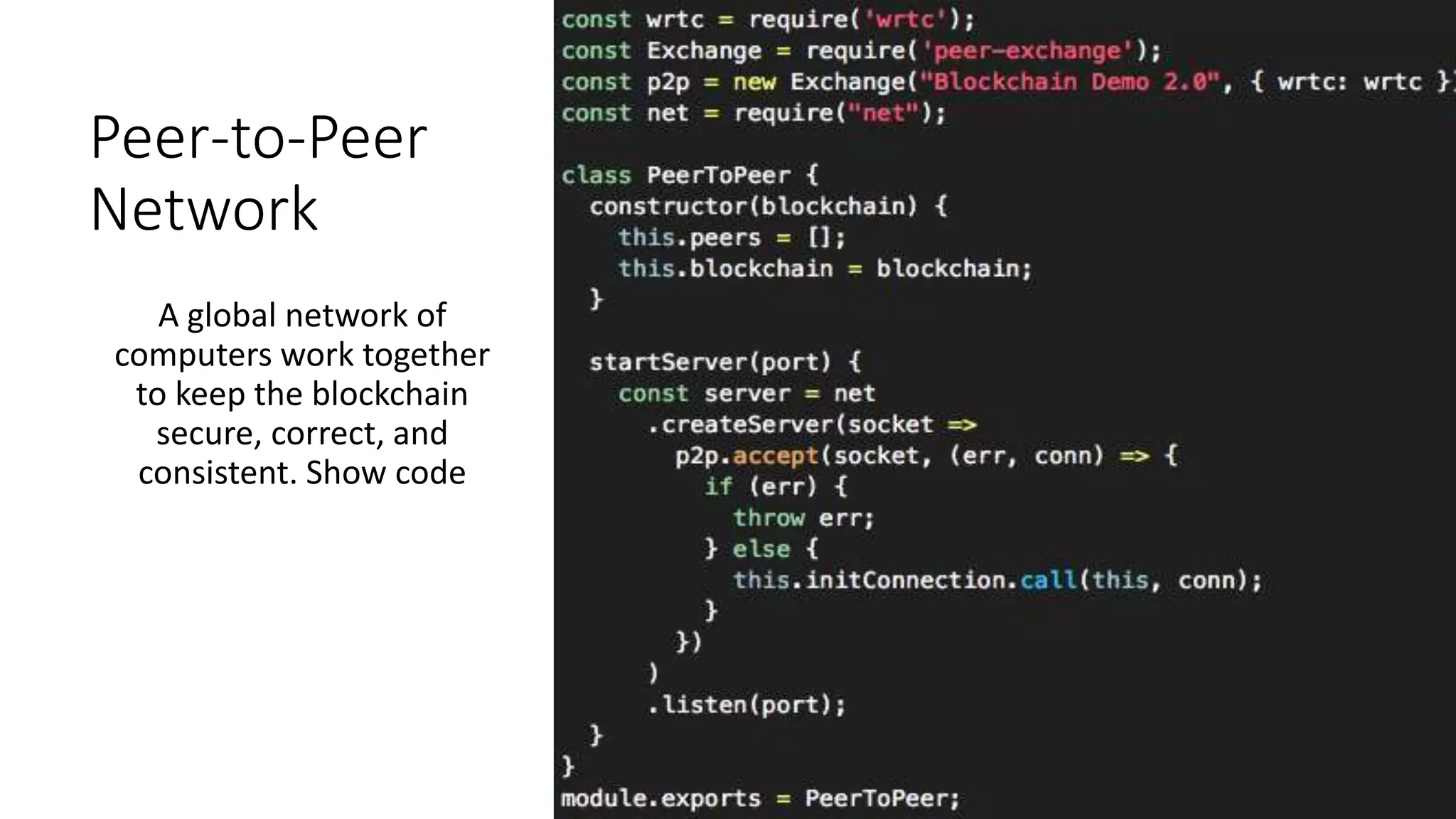
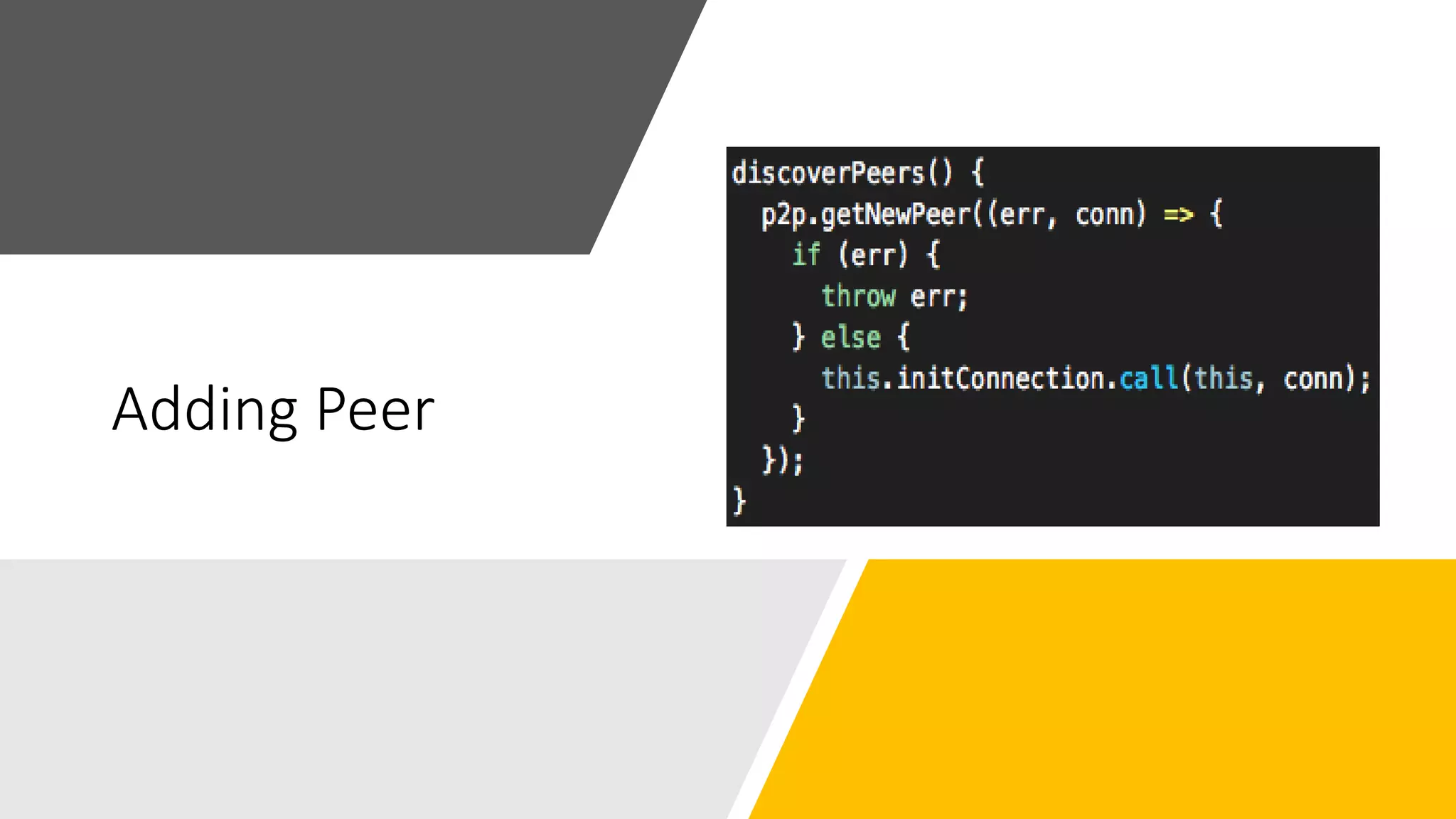
The document discusses blockchain concepts and provides a coding demonstration. It describes key blockchain characteristics like decentralization and immutability. It explains how hashing, Merkle trees, blocks and chains of blocks work to securely store transaction data. Forks that can occur when transactions conflict are also covered. The document differentiates between public and private blockchains. It then demonstrates coding a basic blockchain implementation, including functions for mining blocks and adding them to the peer-to-peer network.