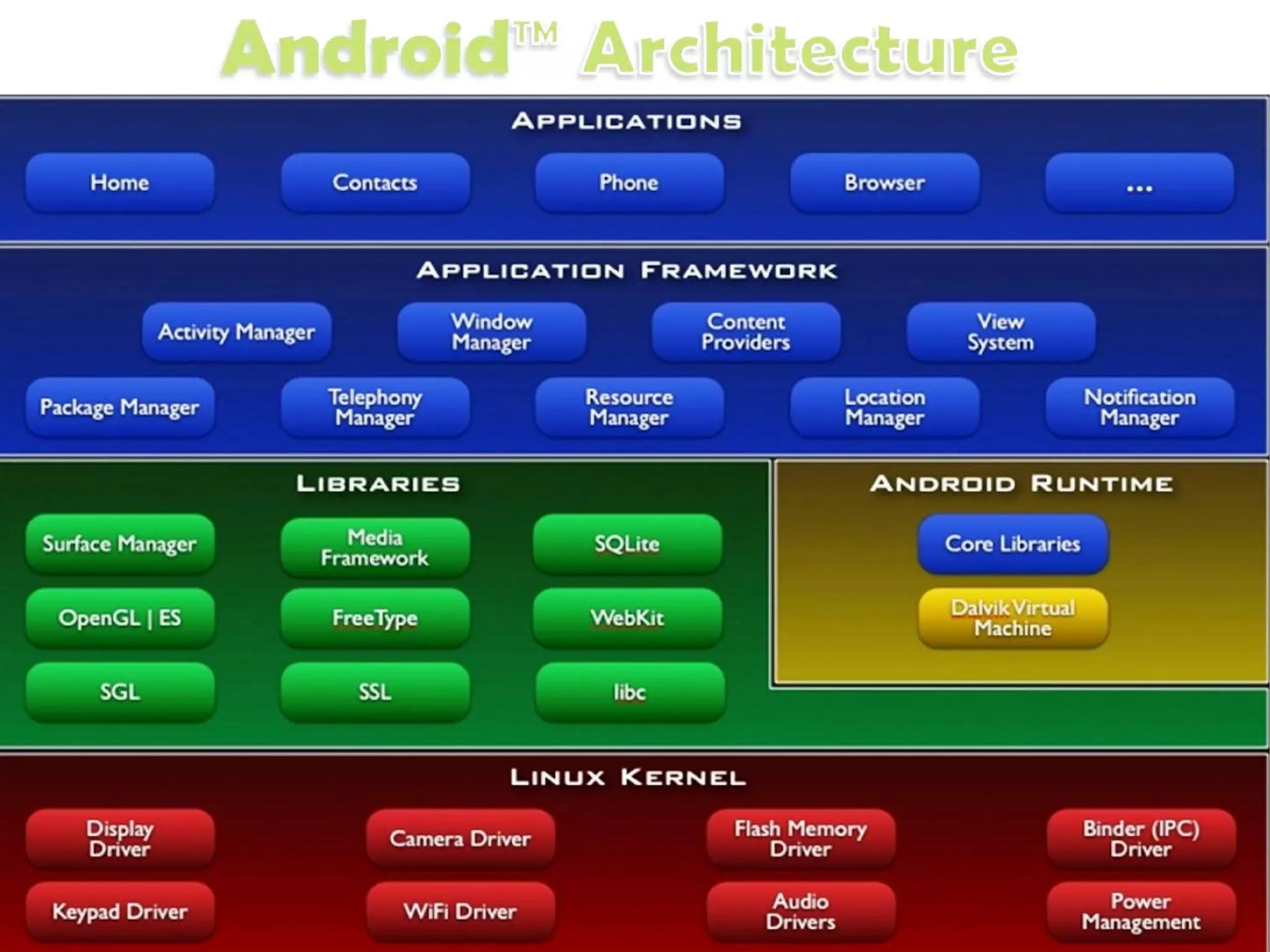
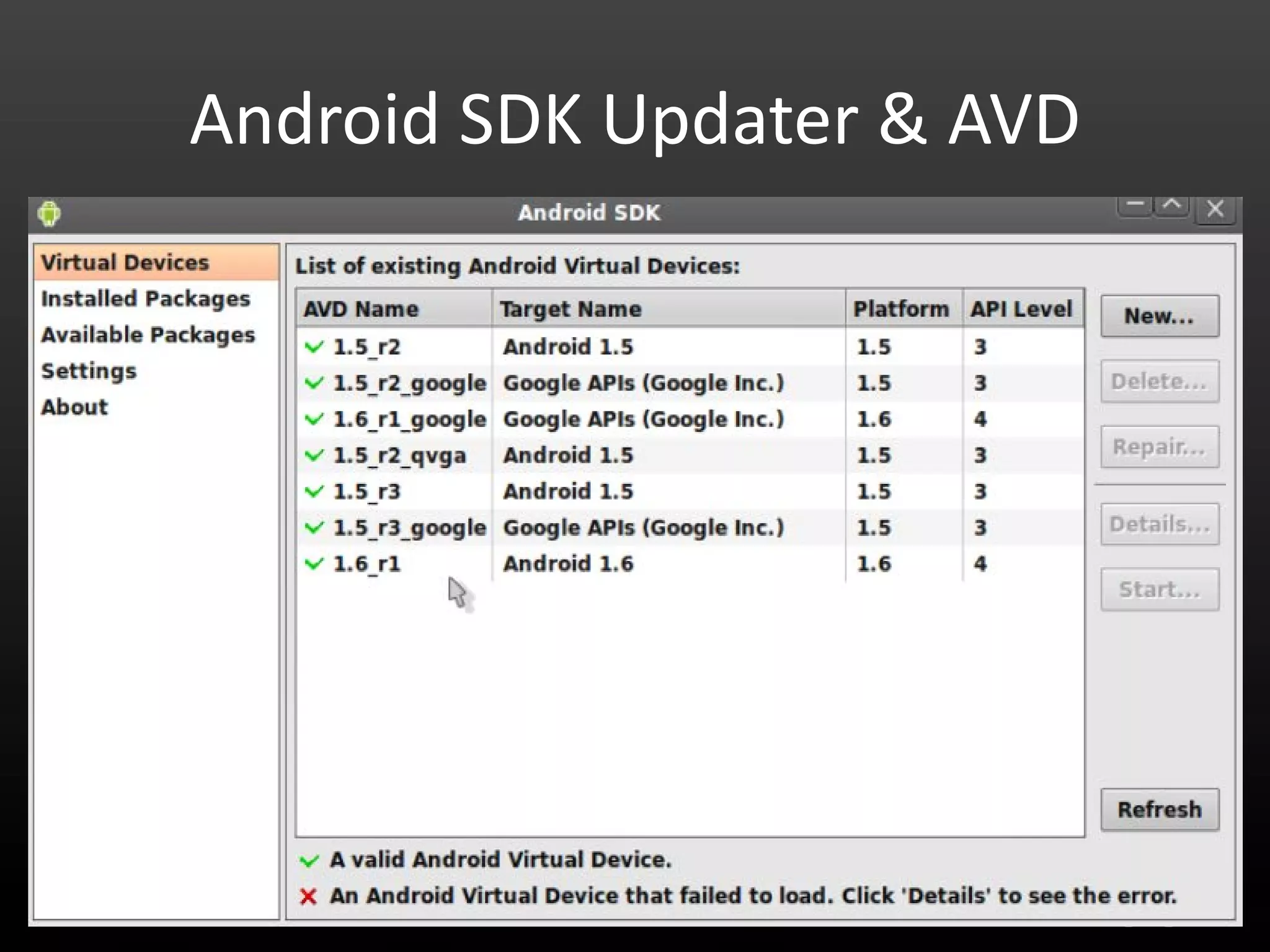
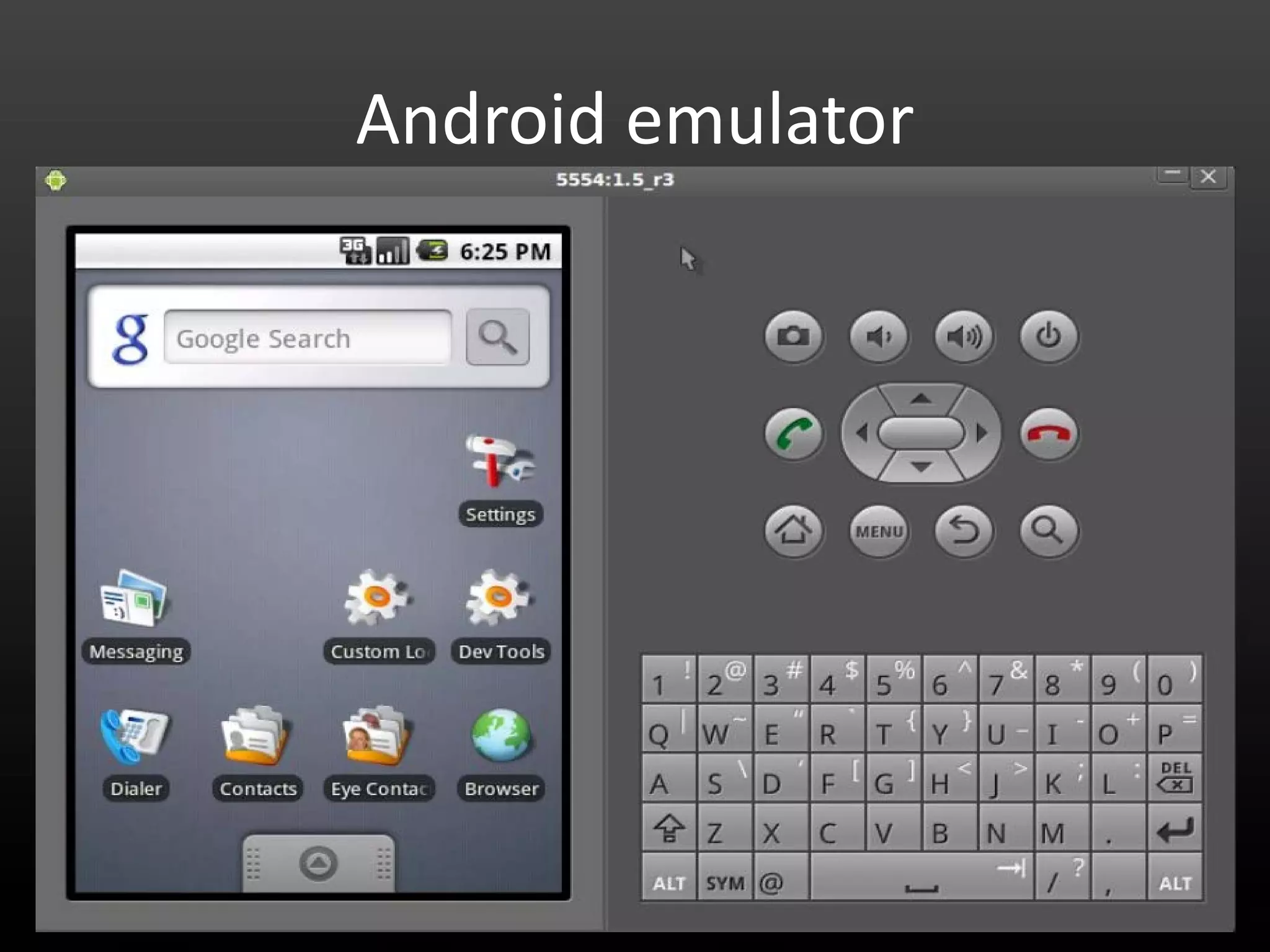
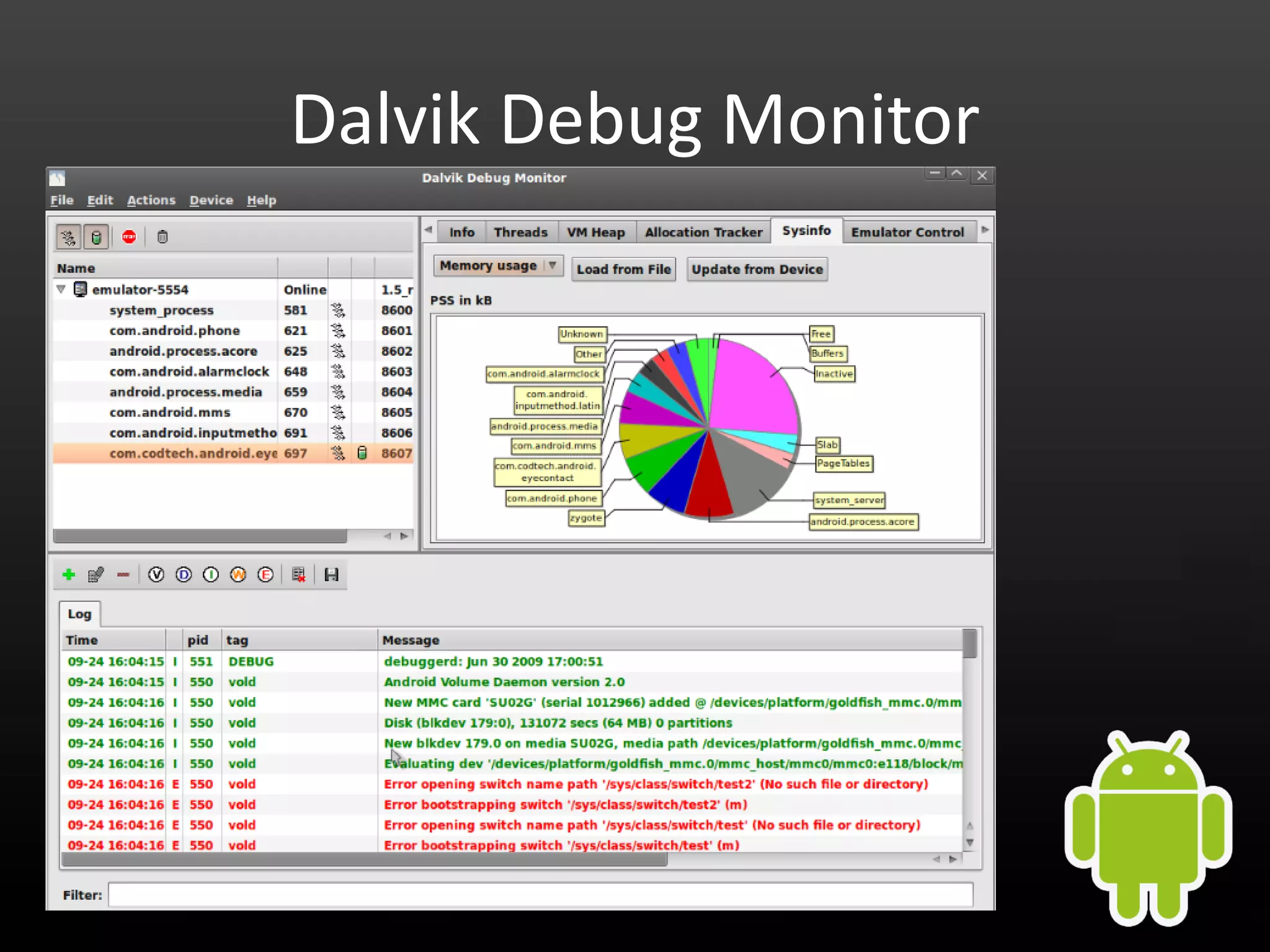
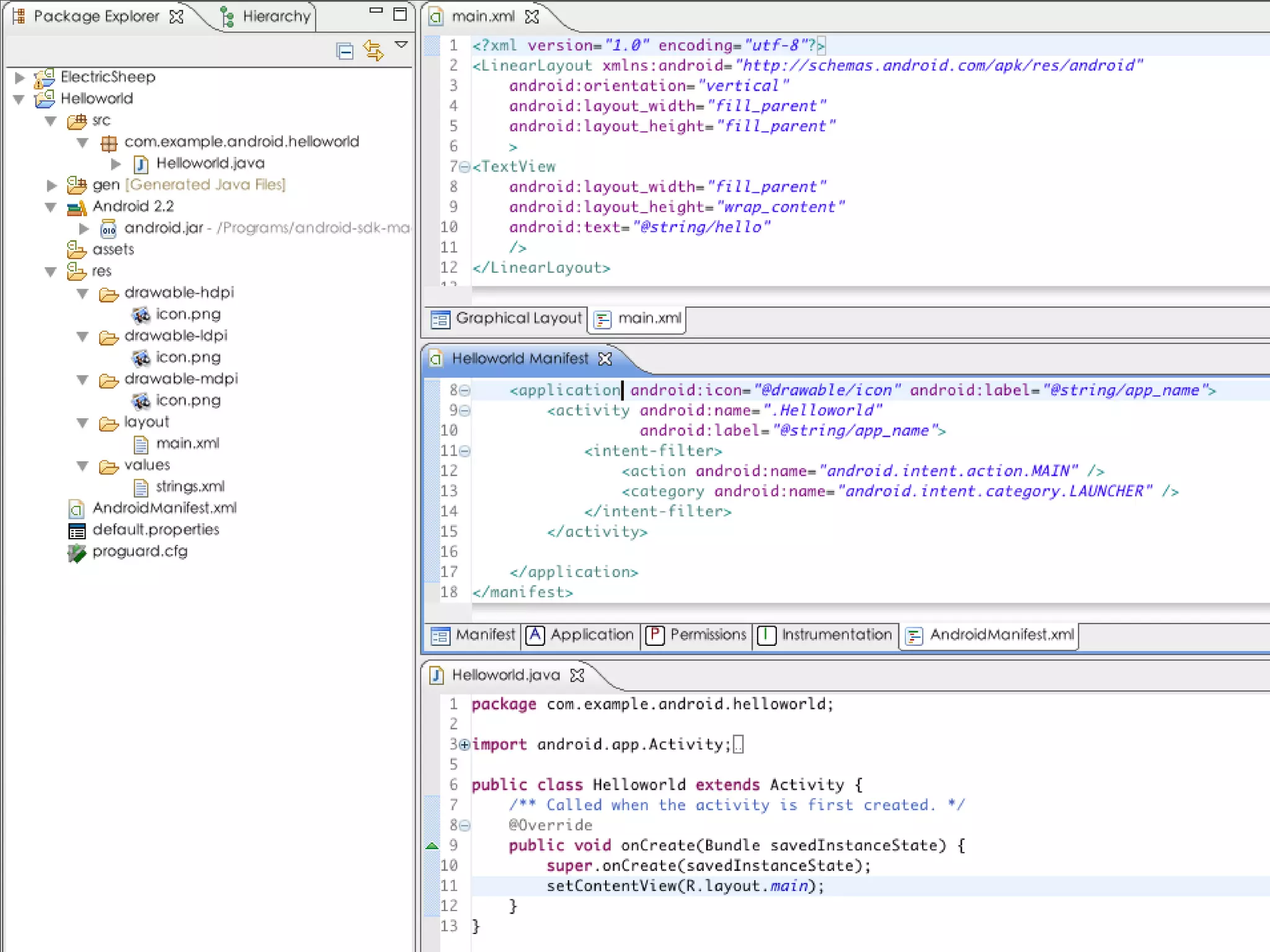
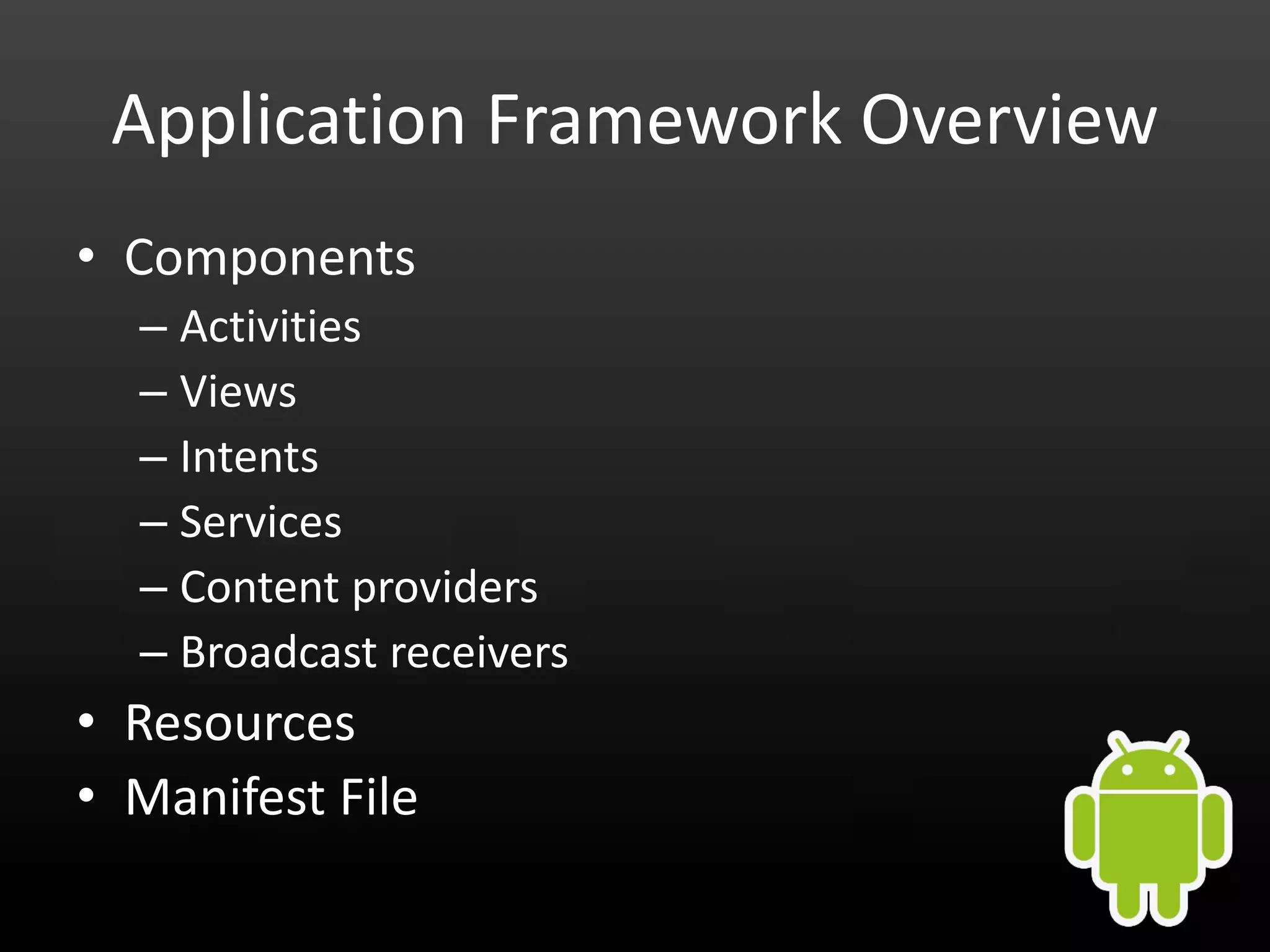
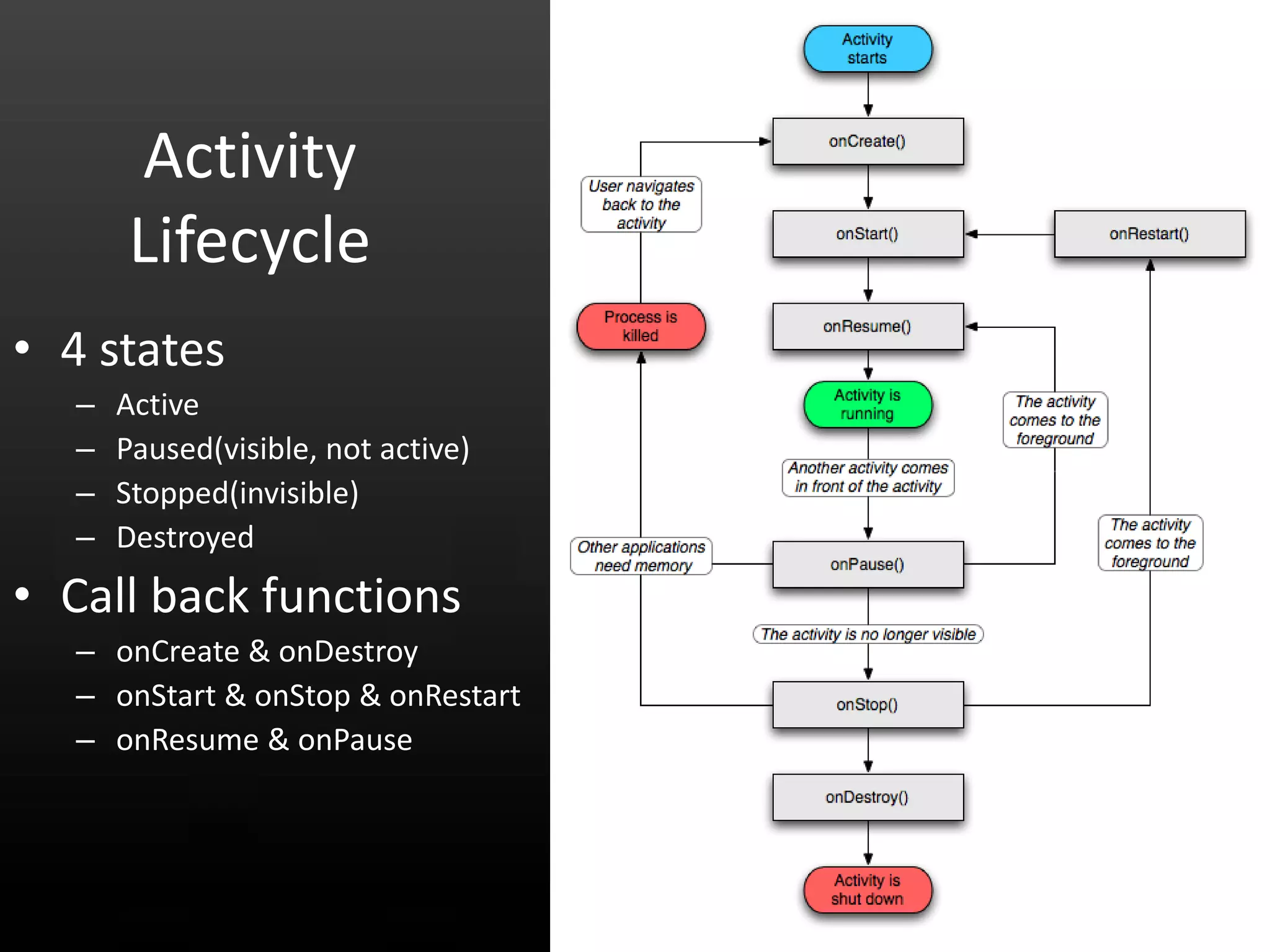
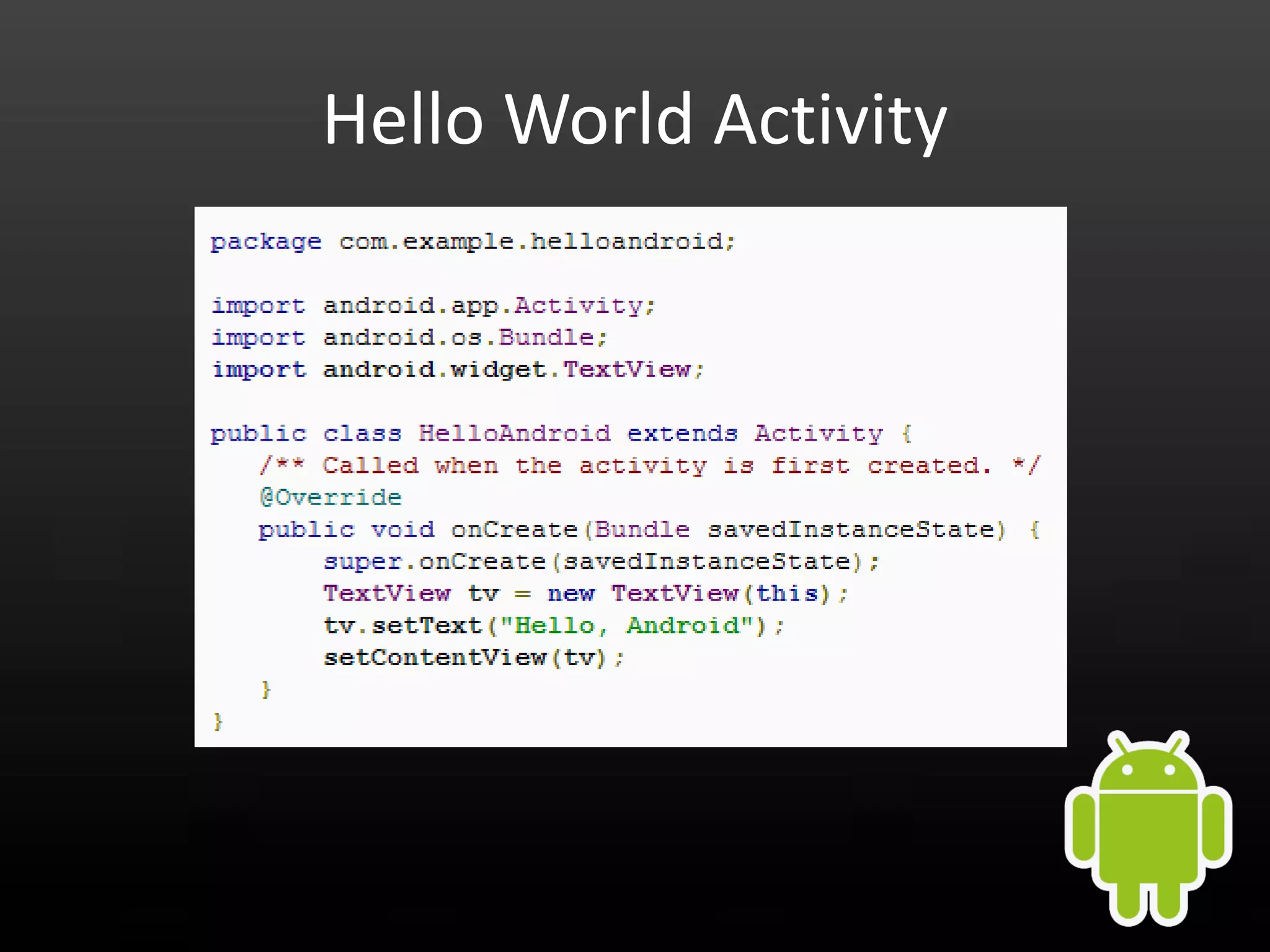
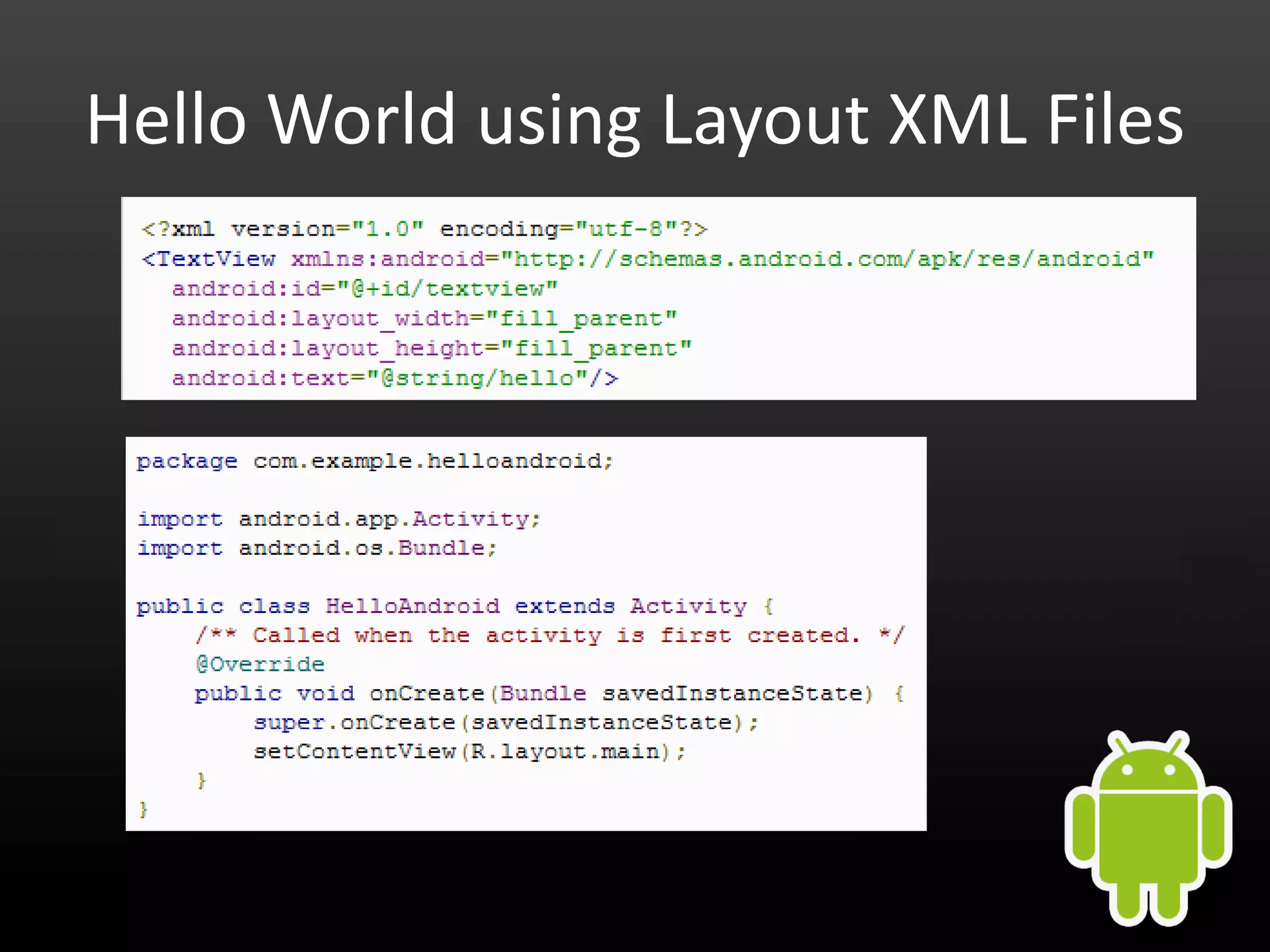
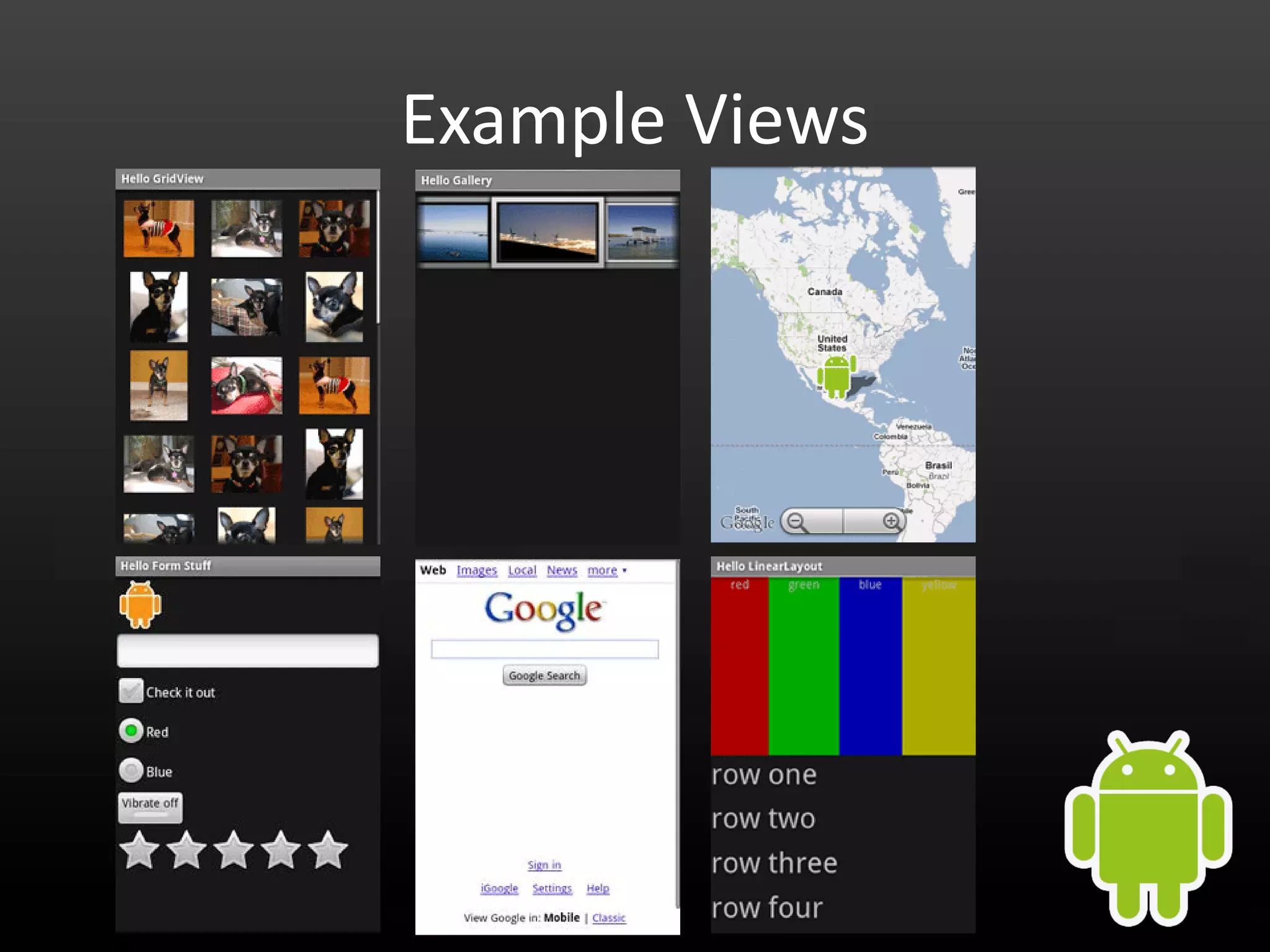
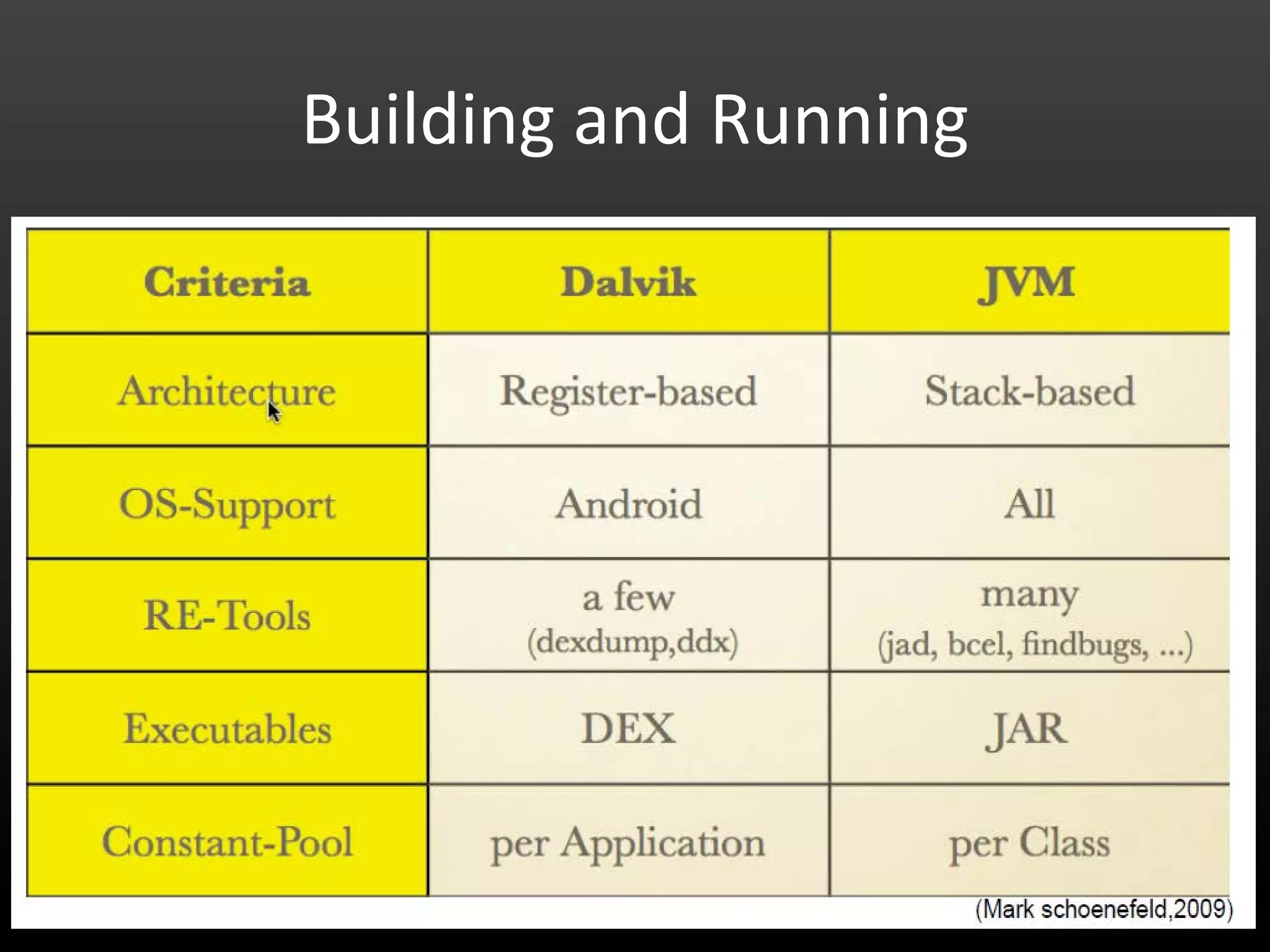
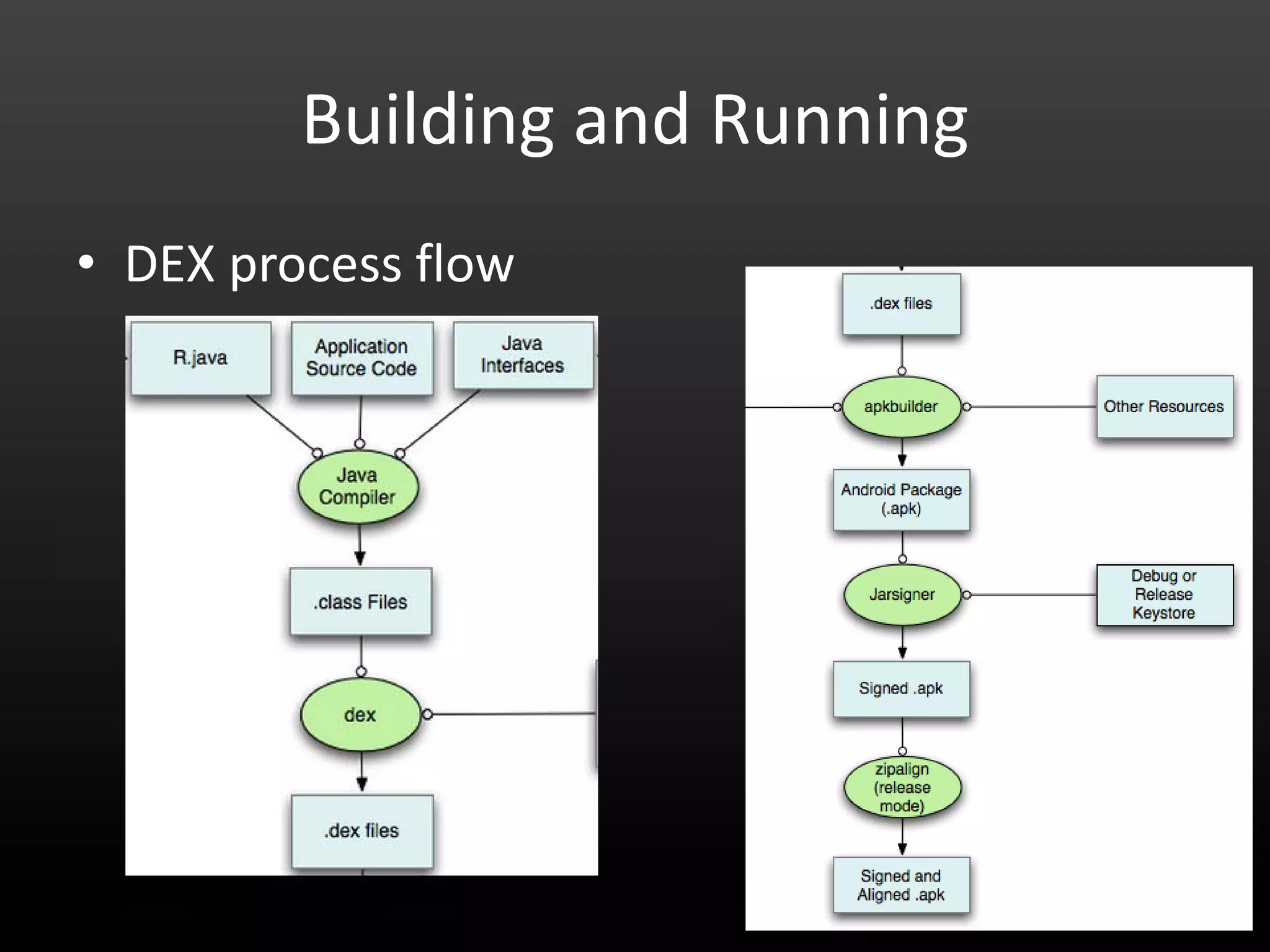
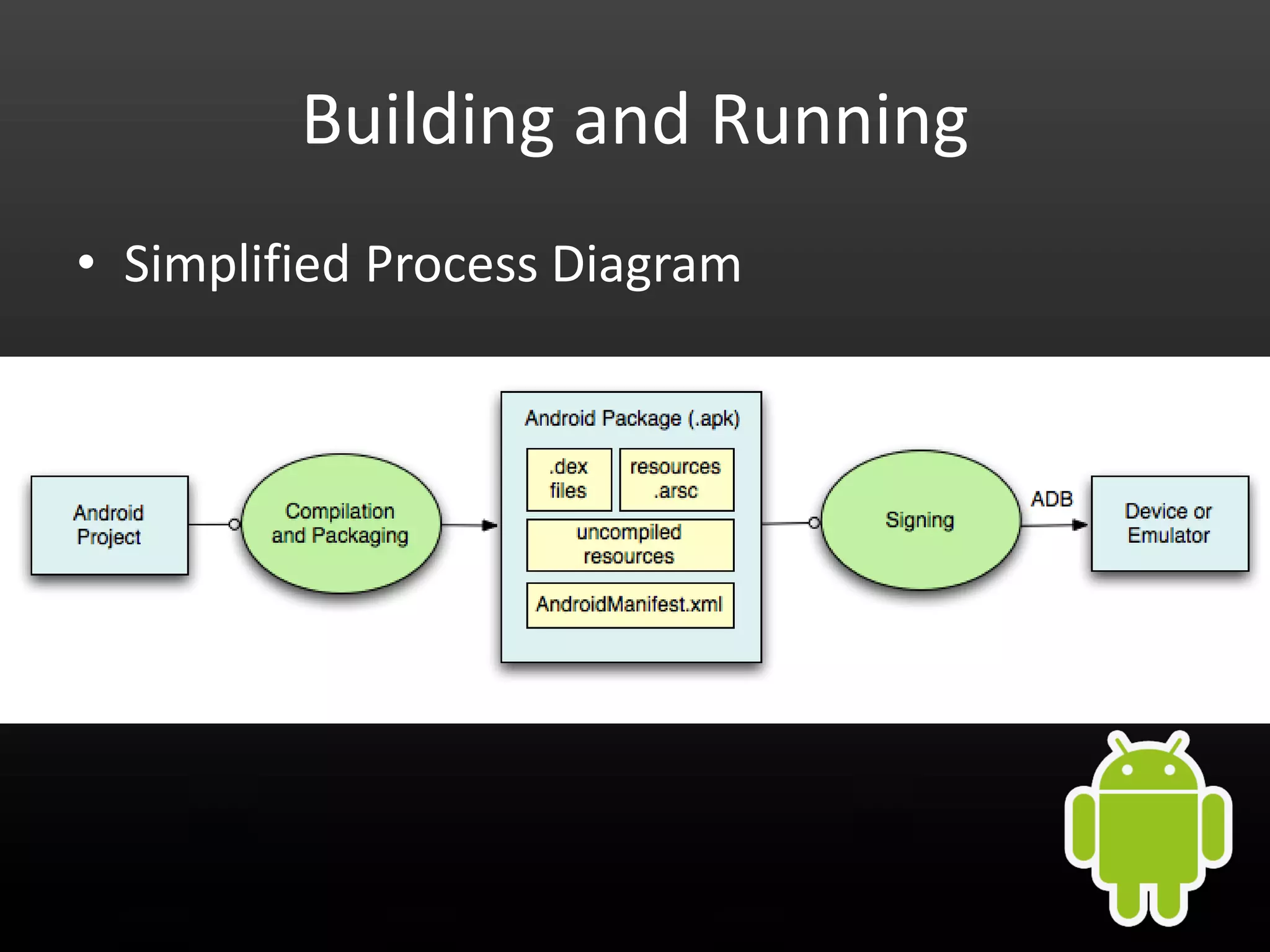
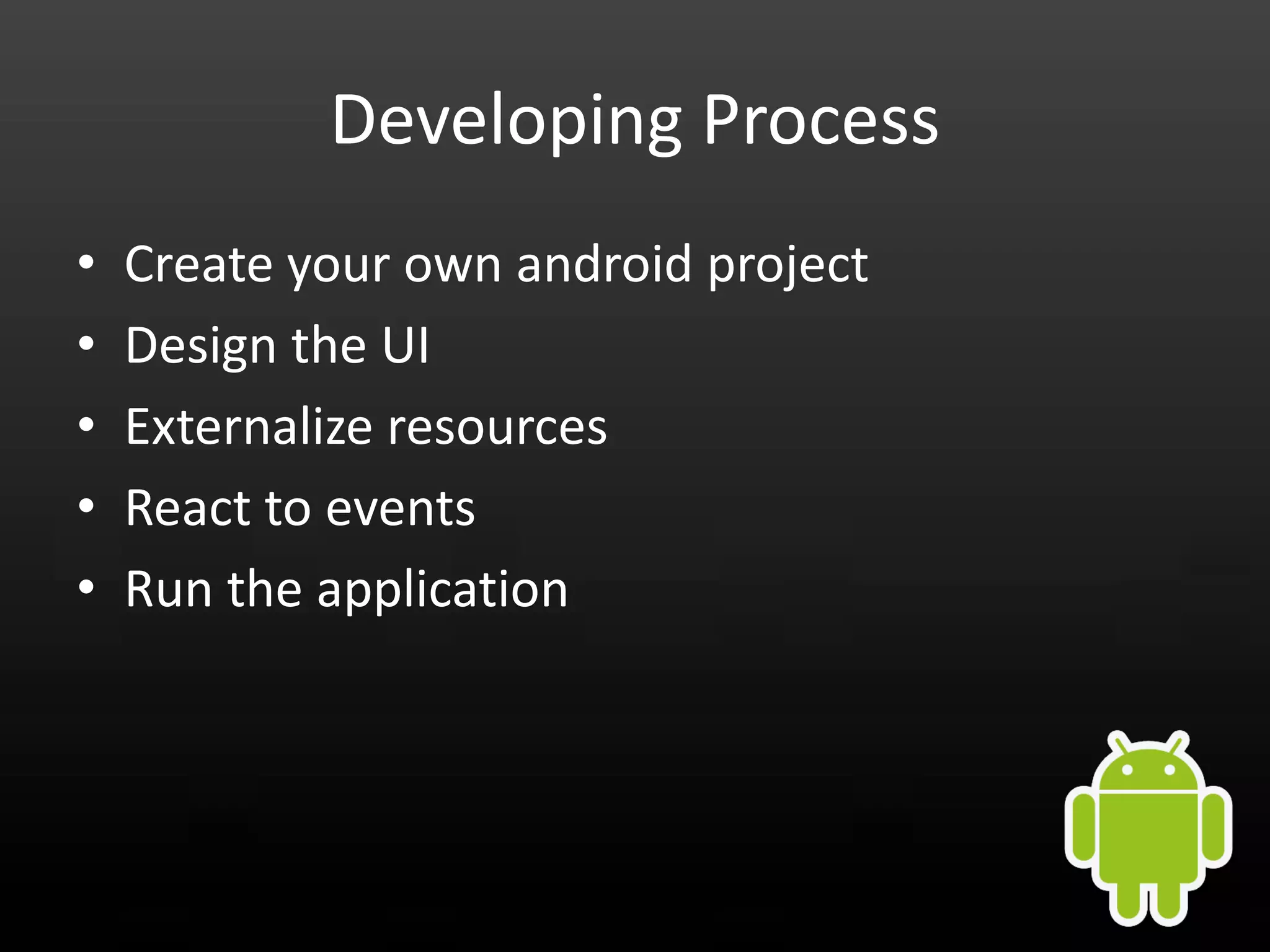
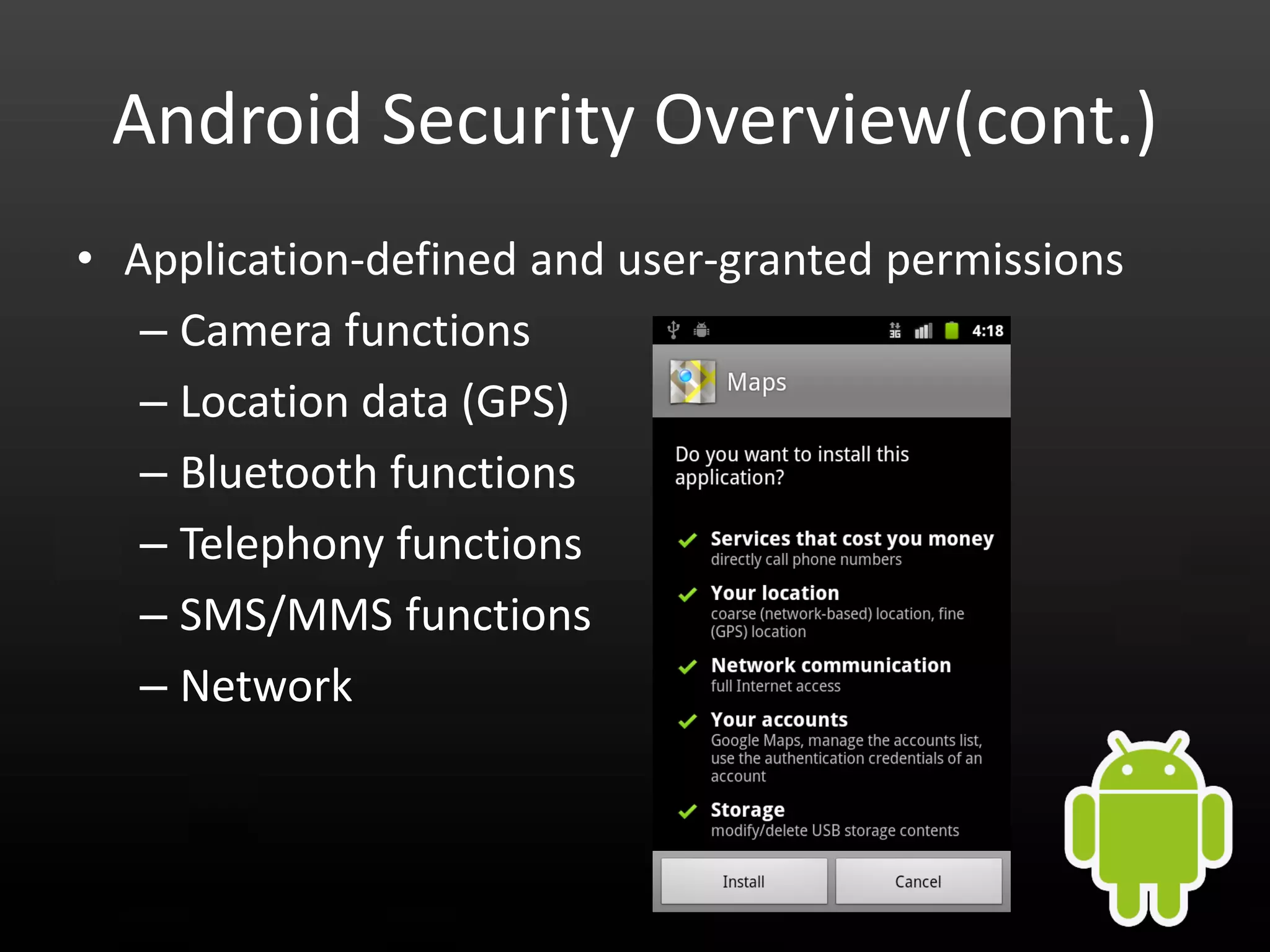
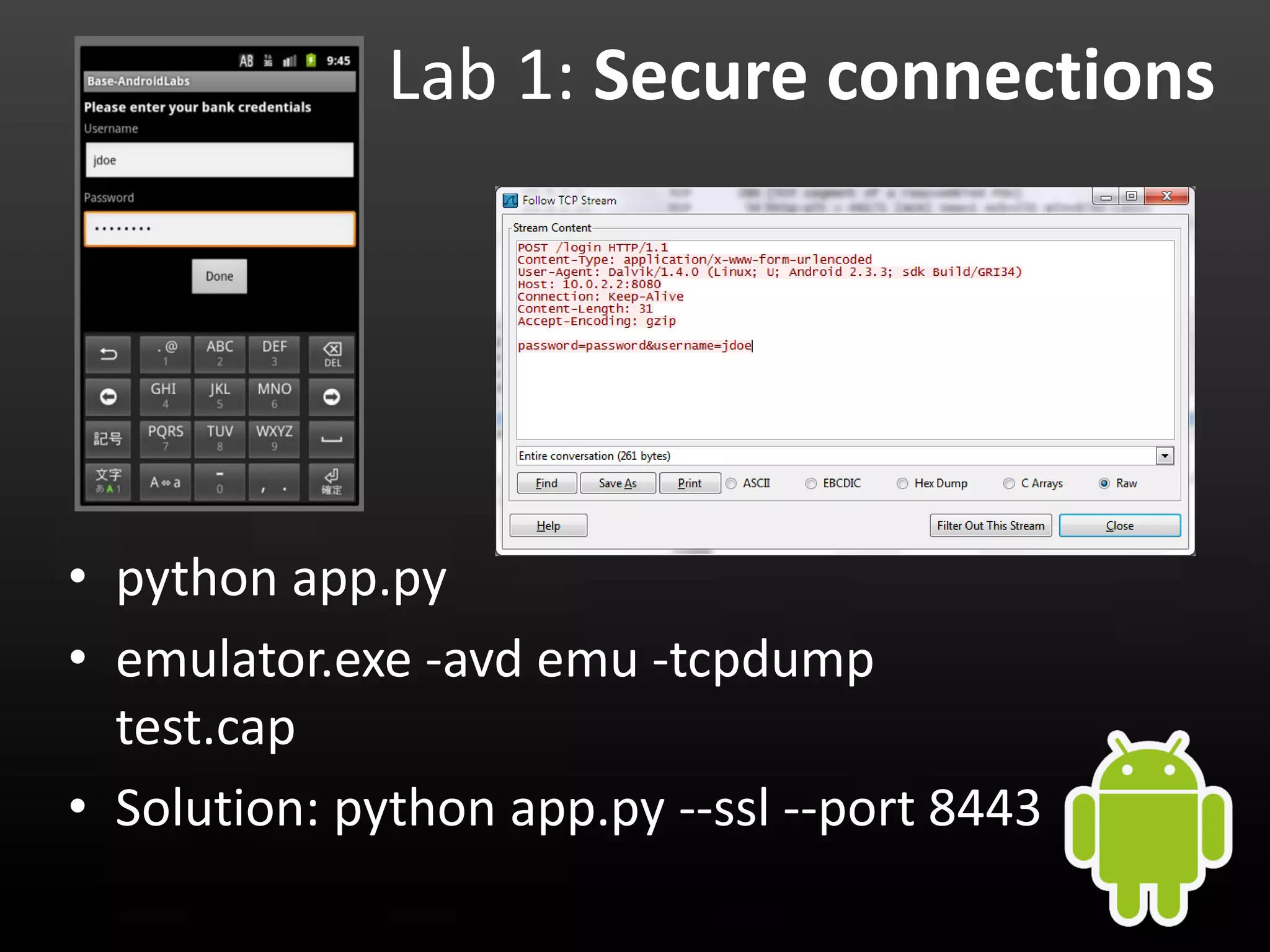
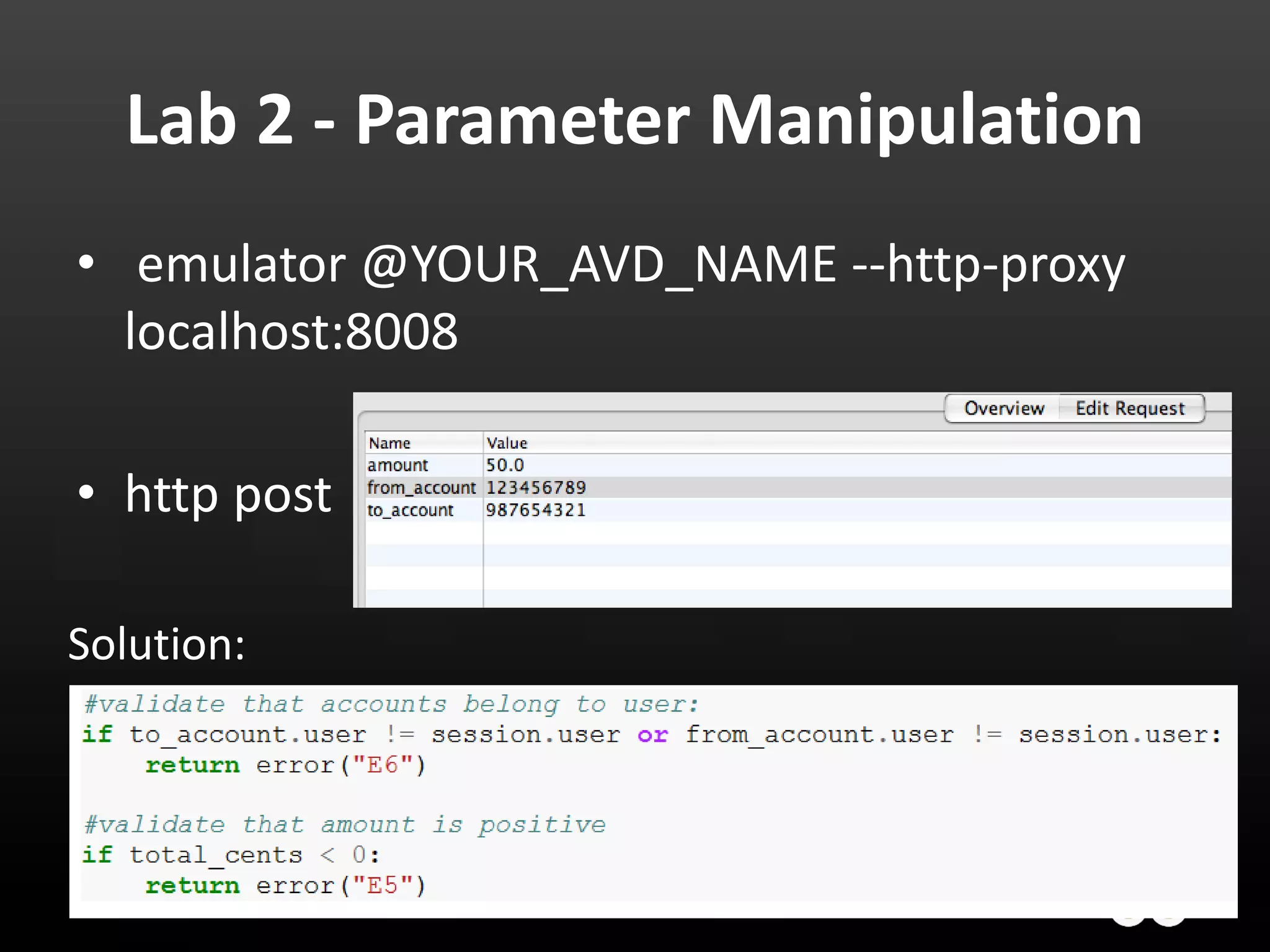
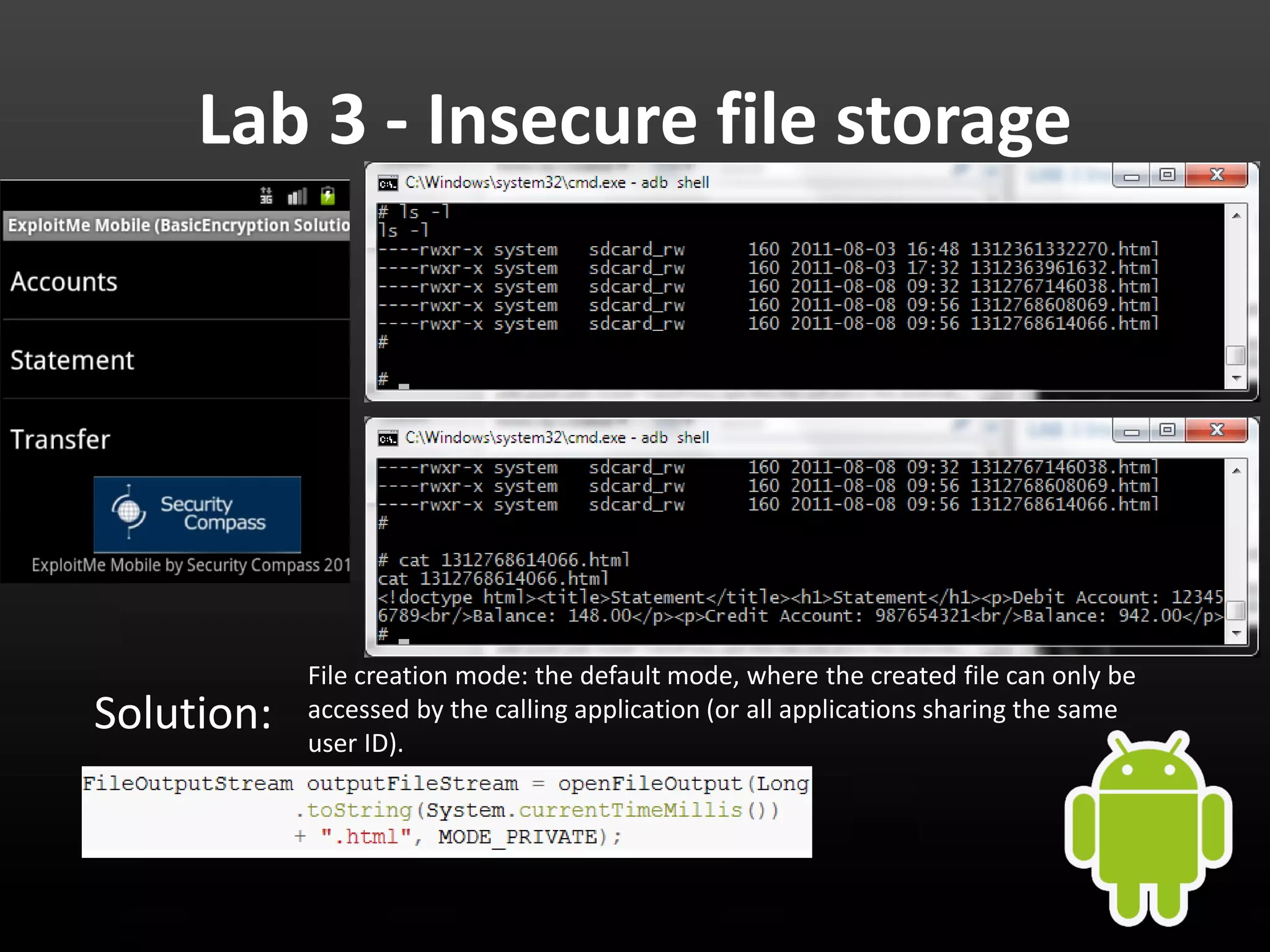
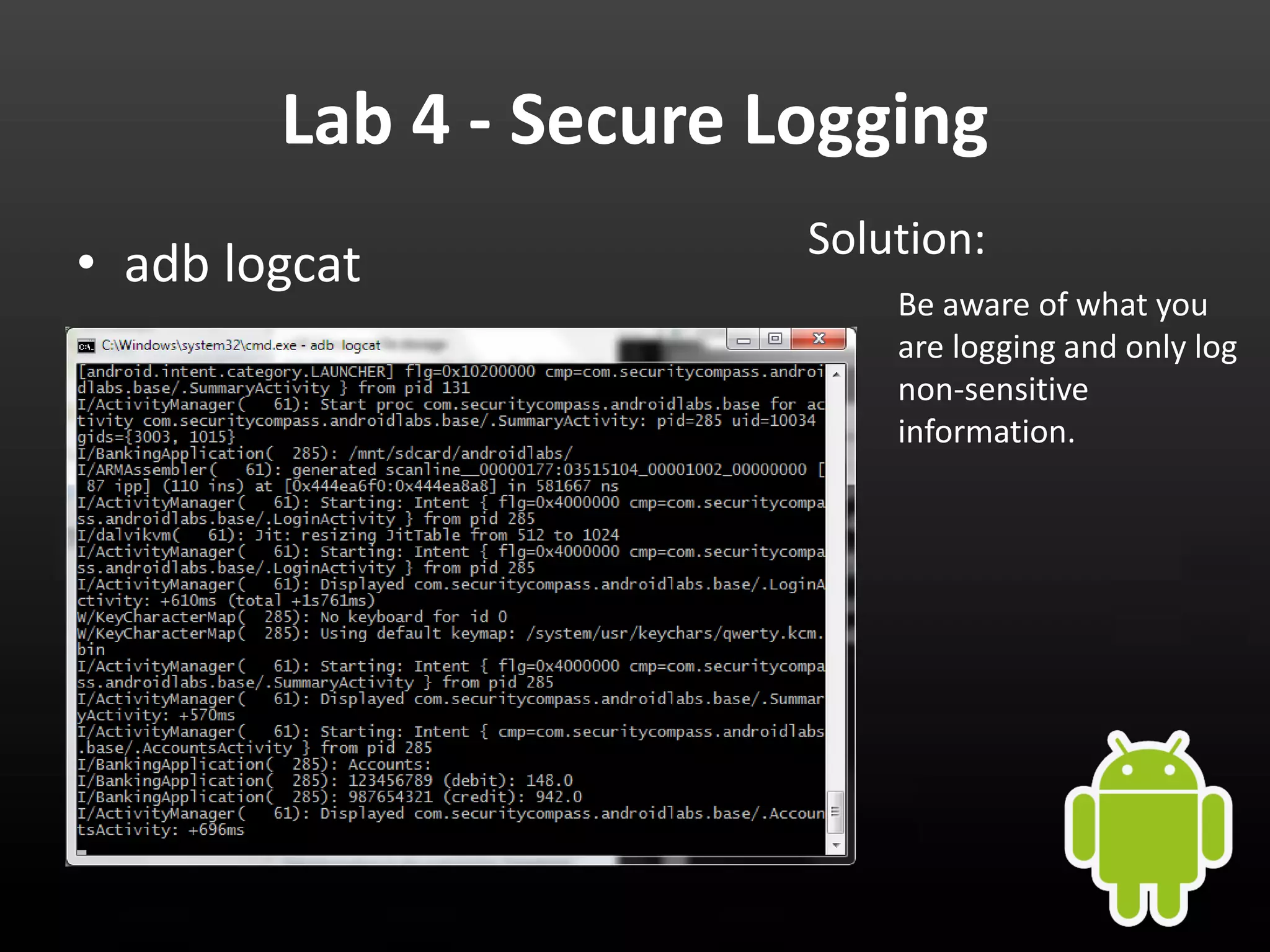
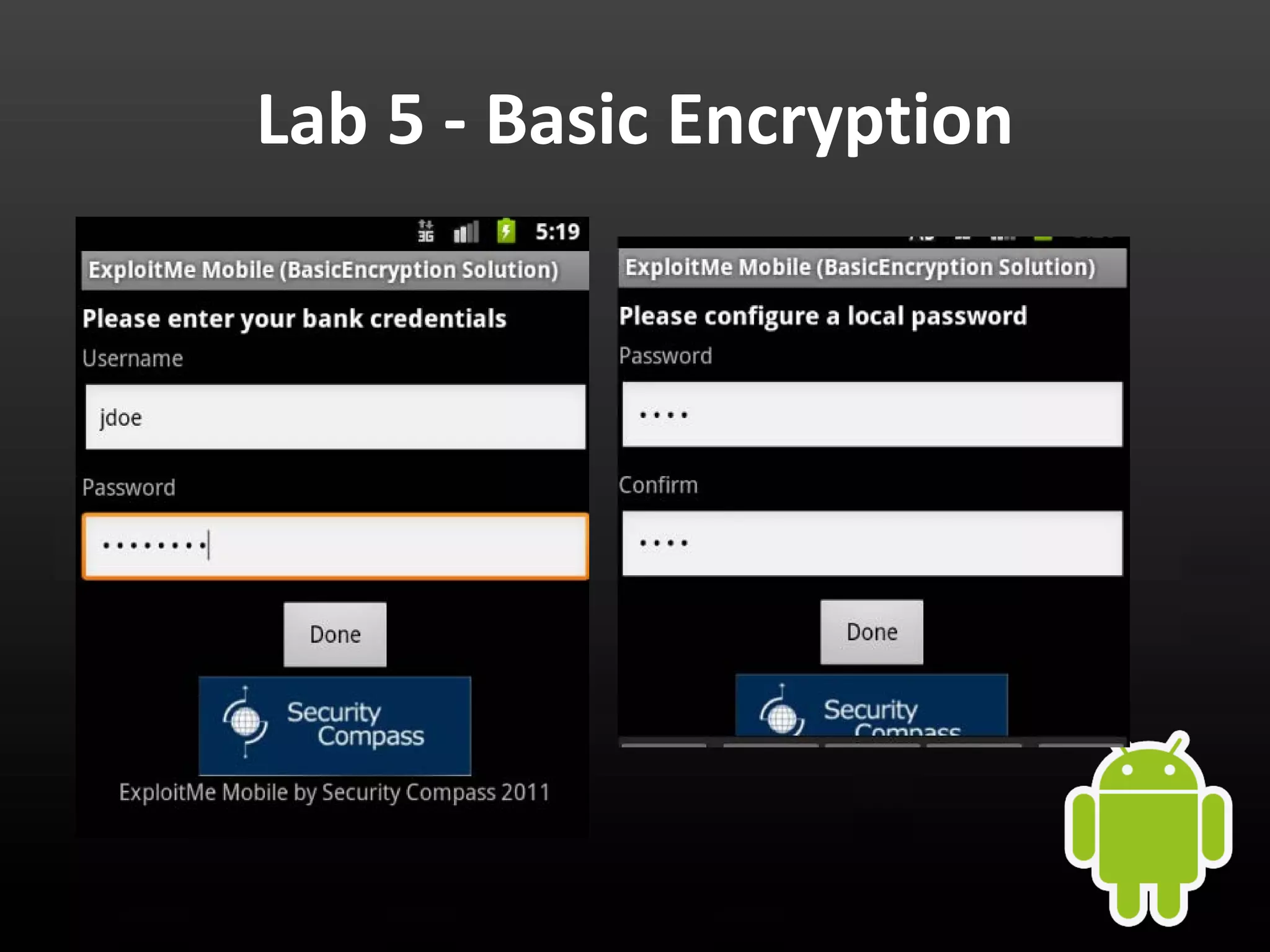
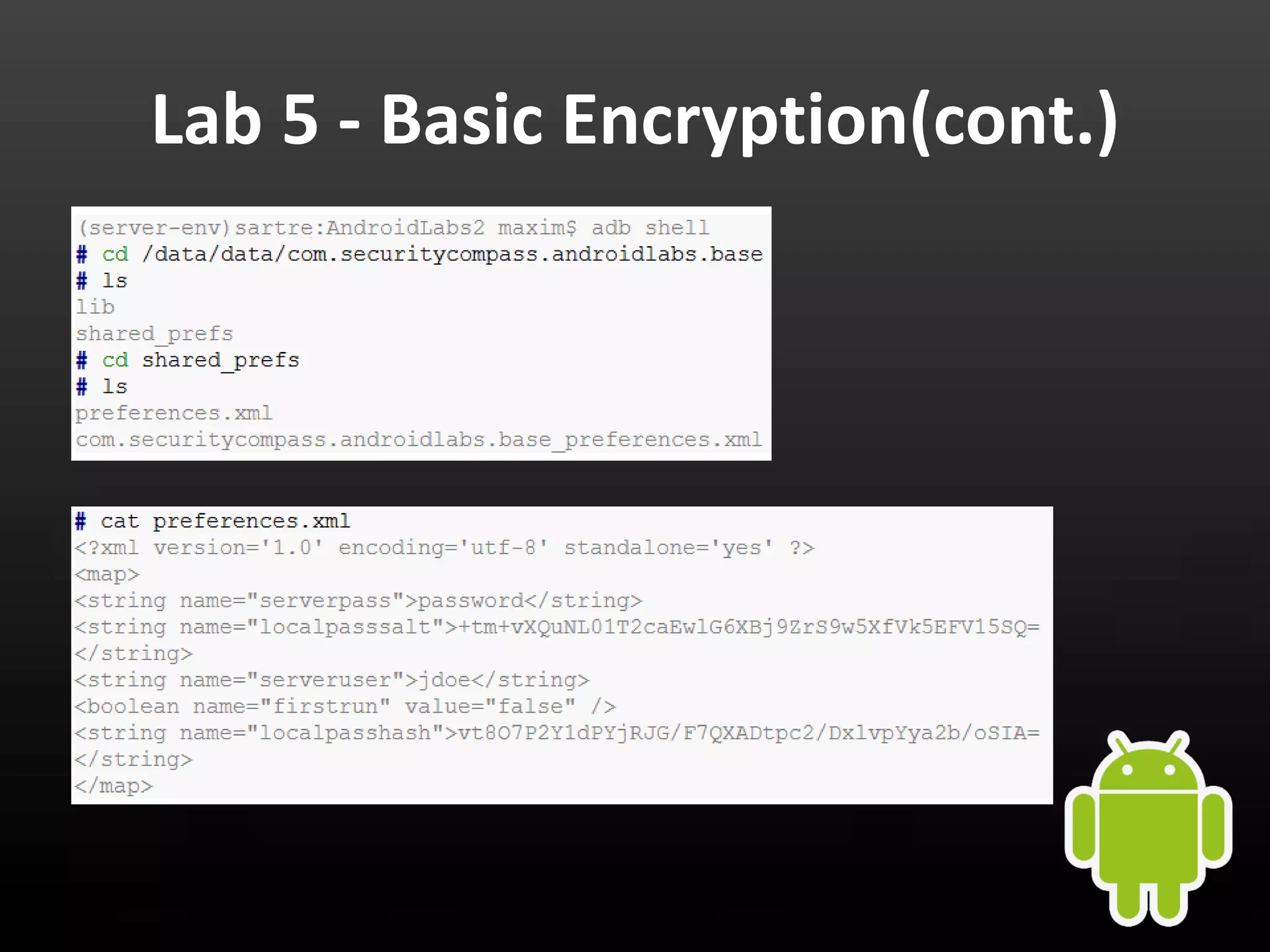
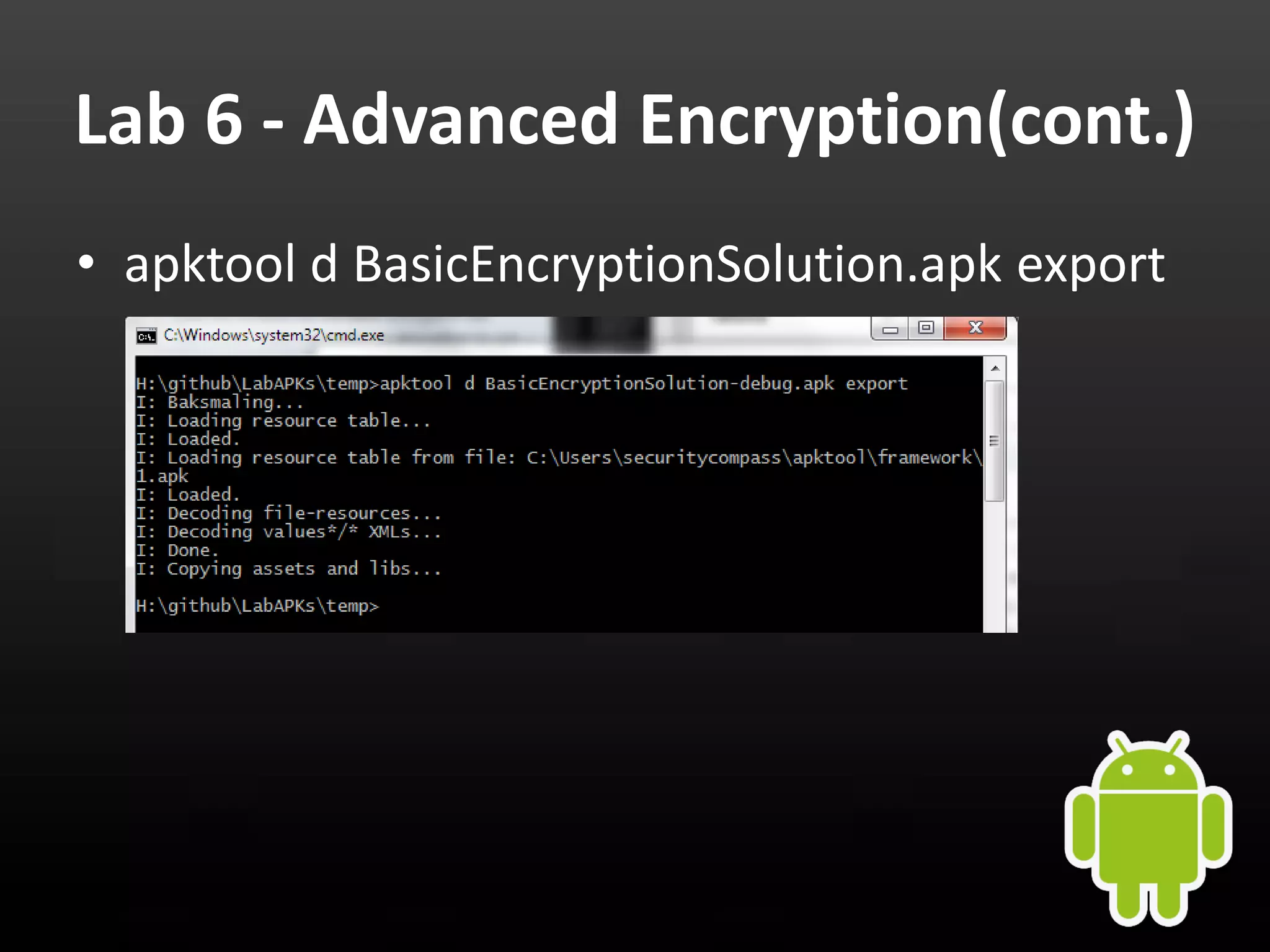
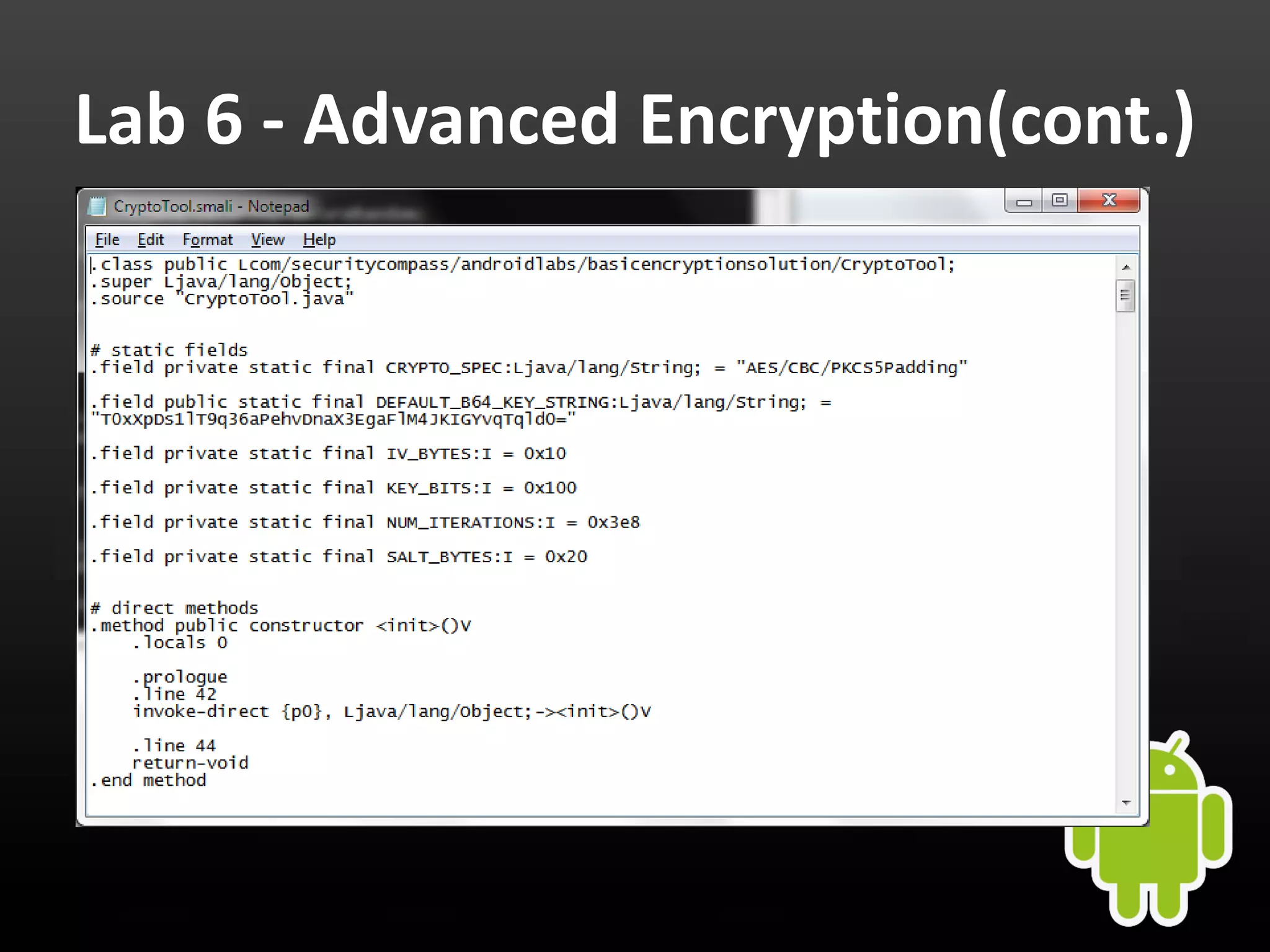
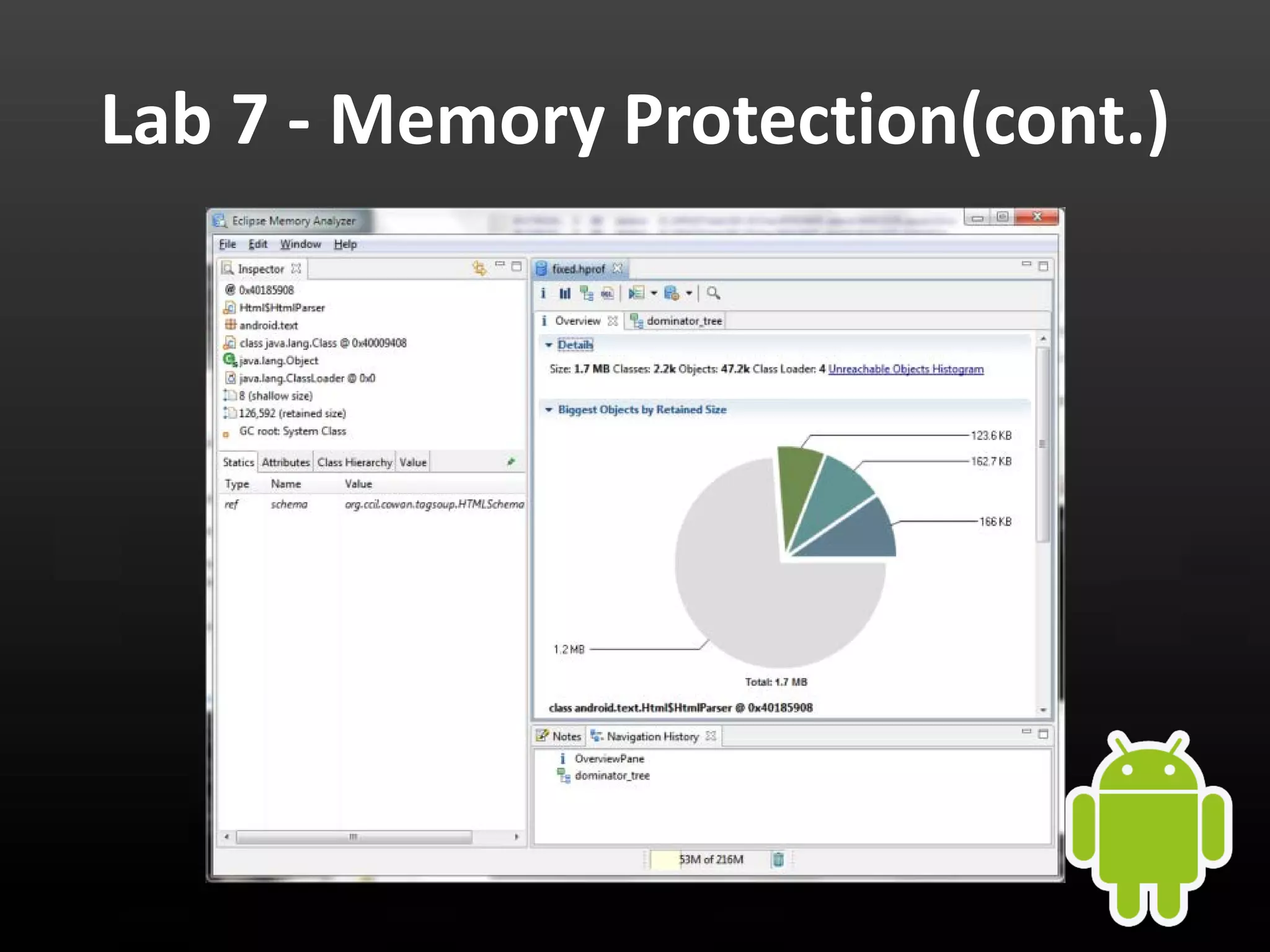
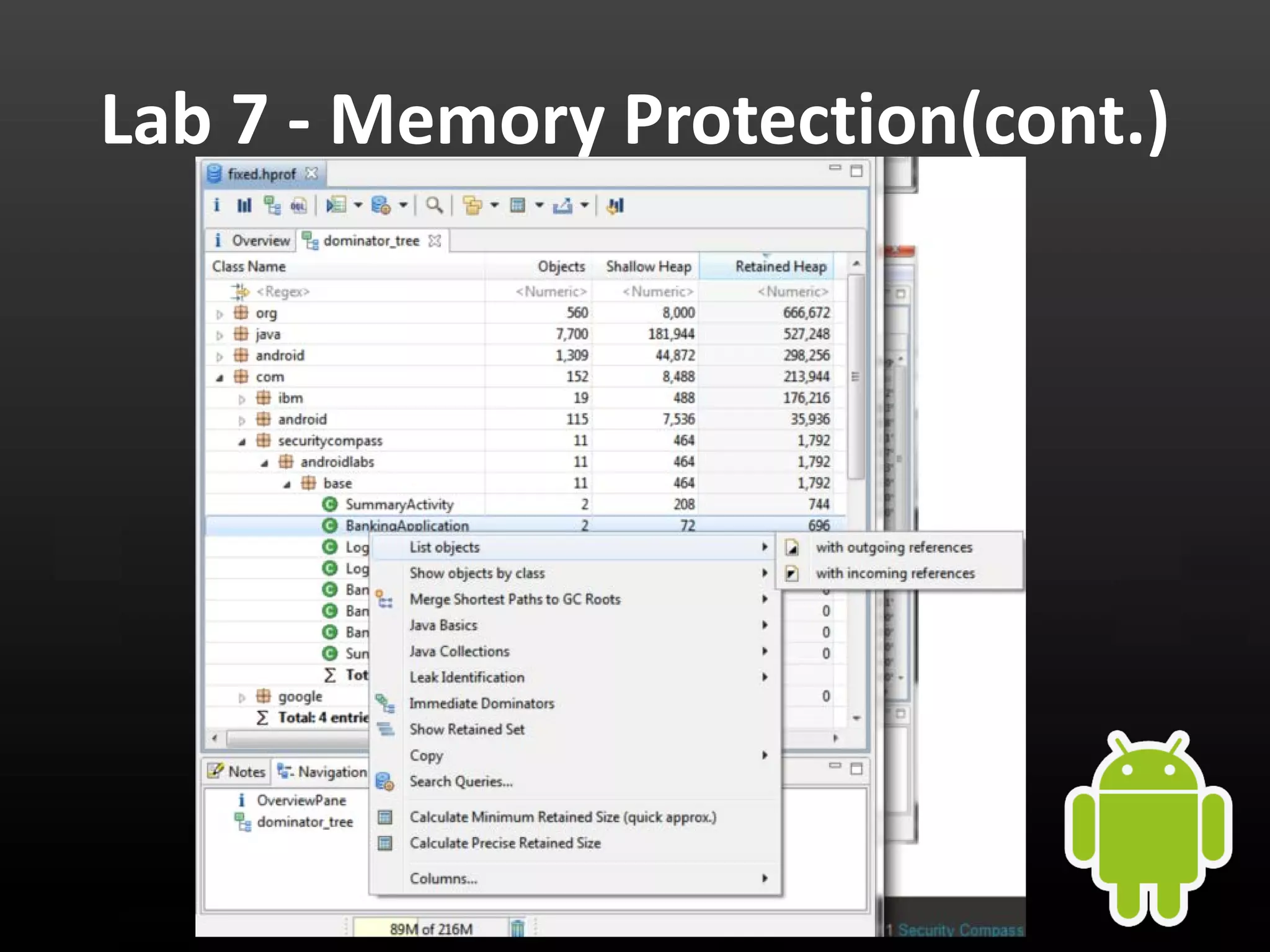
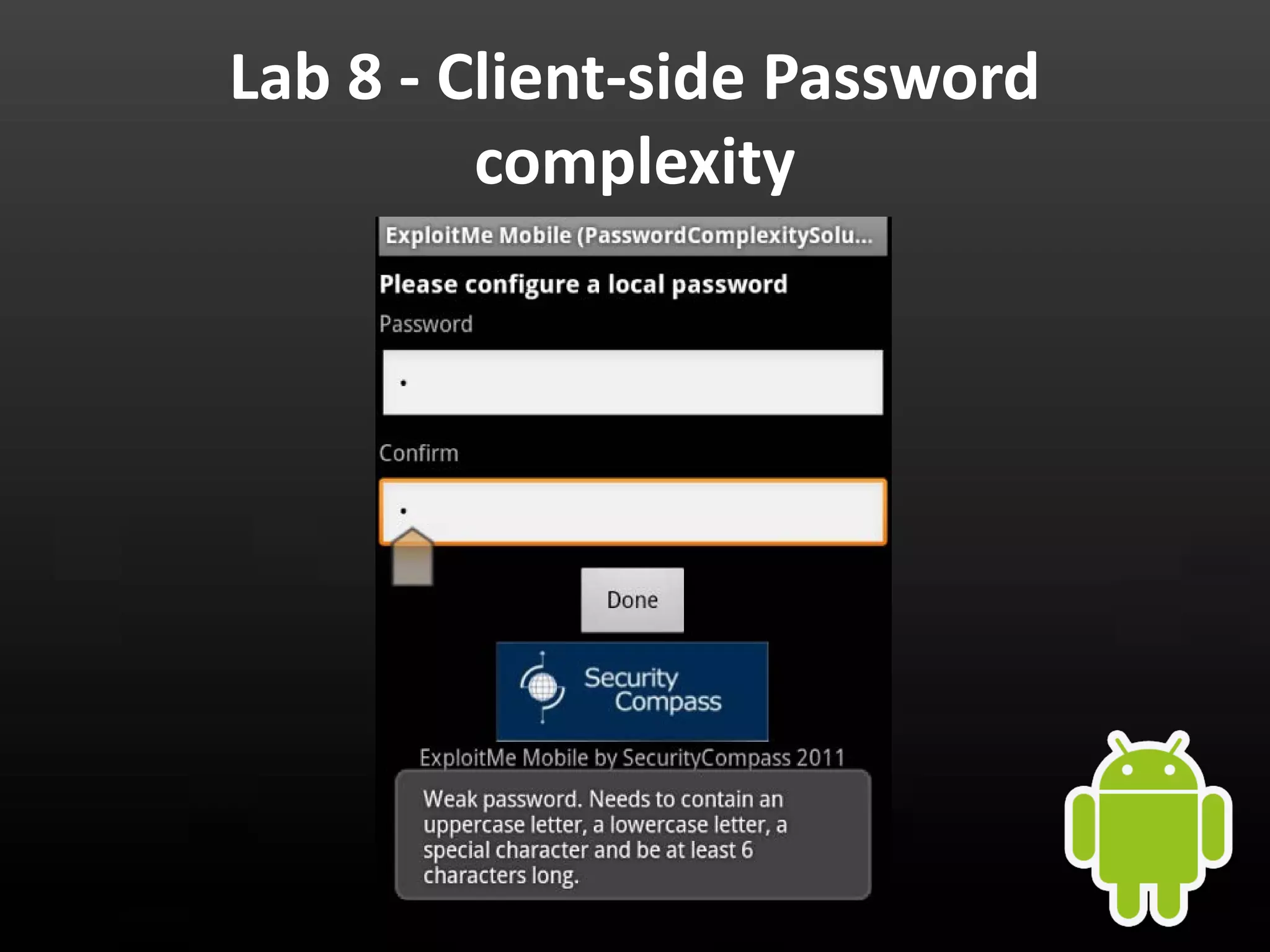
This document provides an introduction to Android development and security. It begins with a brief history of Android and overview of its architecture. It then discusses the Android development environment and process, including key tools and frameworks. It also outlines Android security features like application sandboxing, permissions, and encryption. Finally, it introduces a series of Android security labs that demonstrate exploits like parameter manipulation, insecure storage, and memory attacks. The goal is to provide hands-on examples of common Android vulnerabilities.