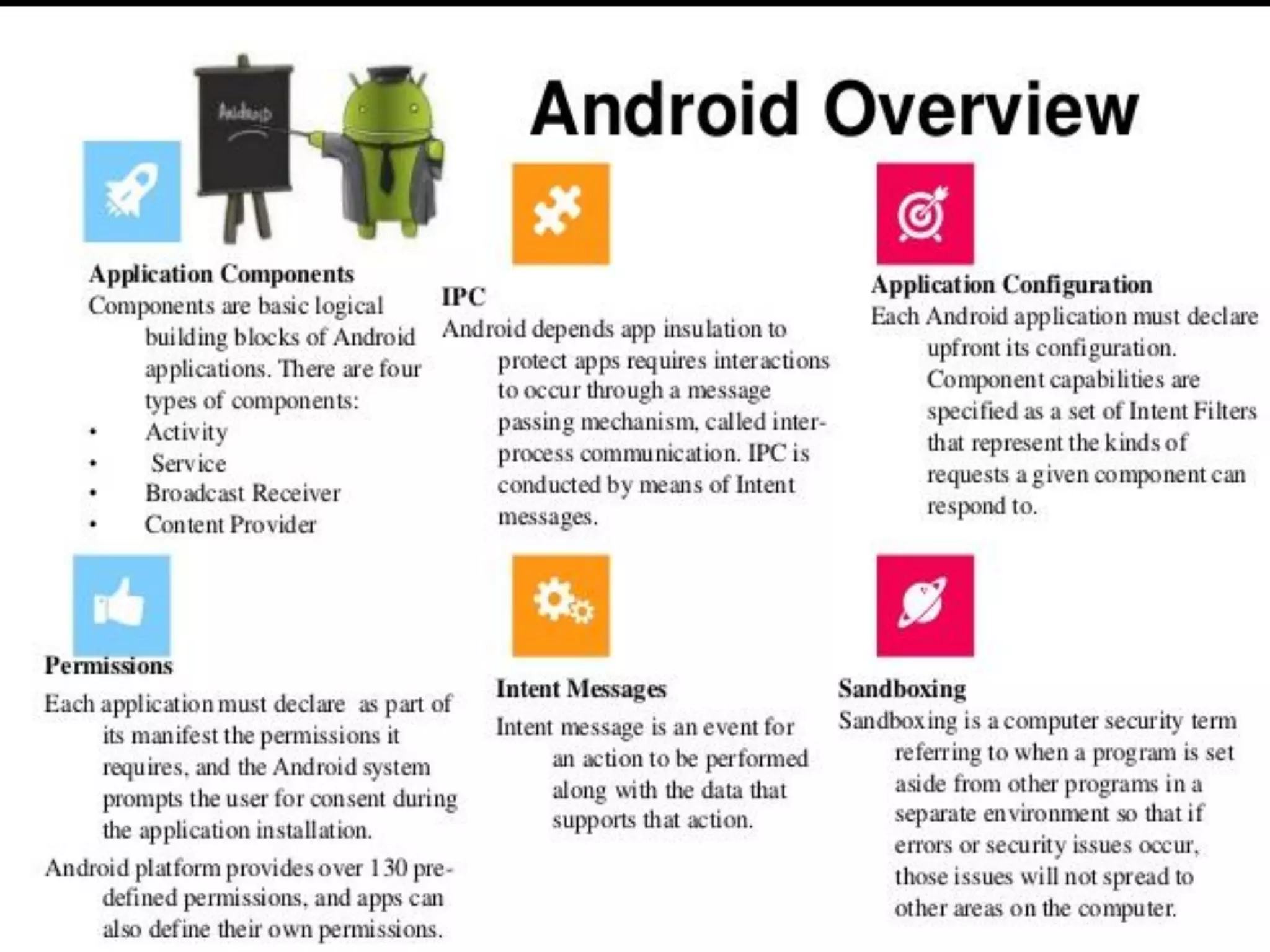
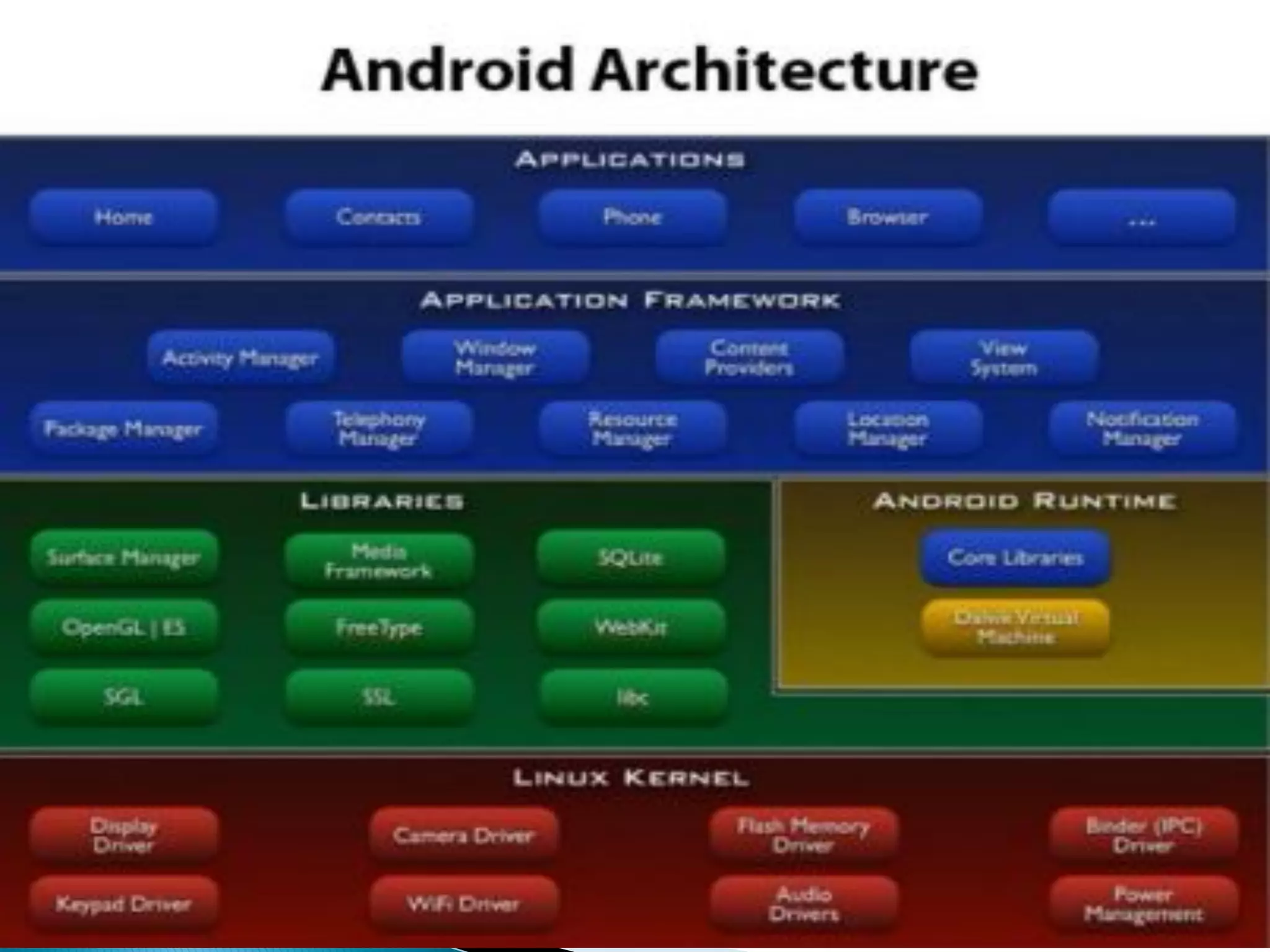
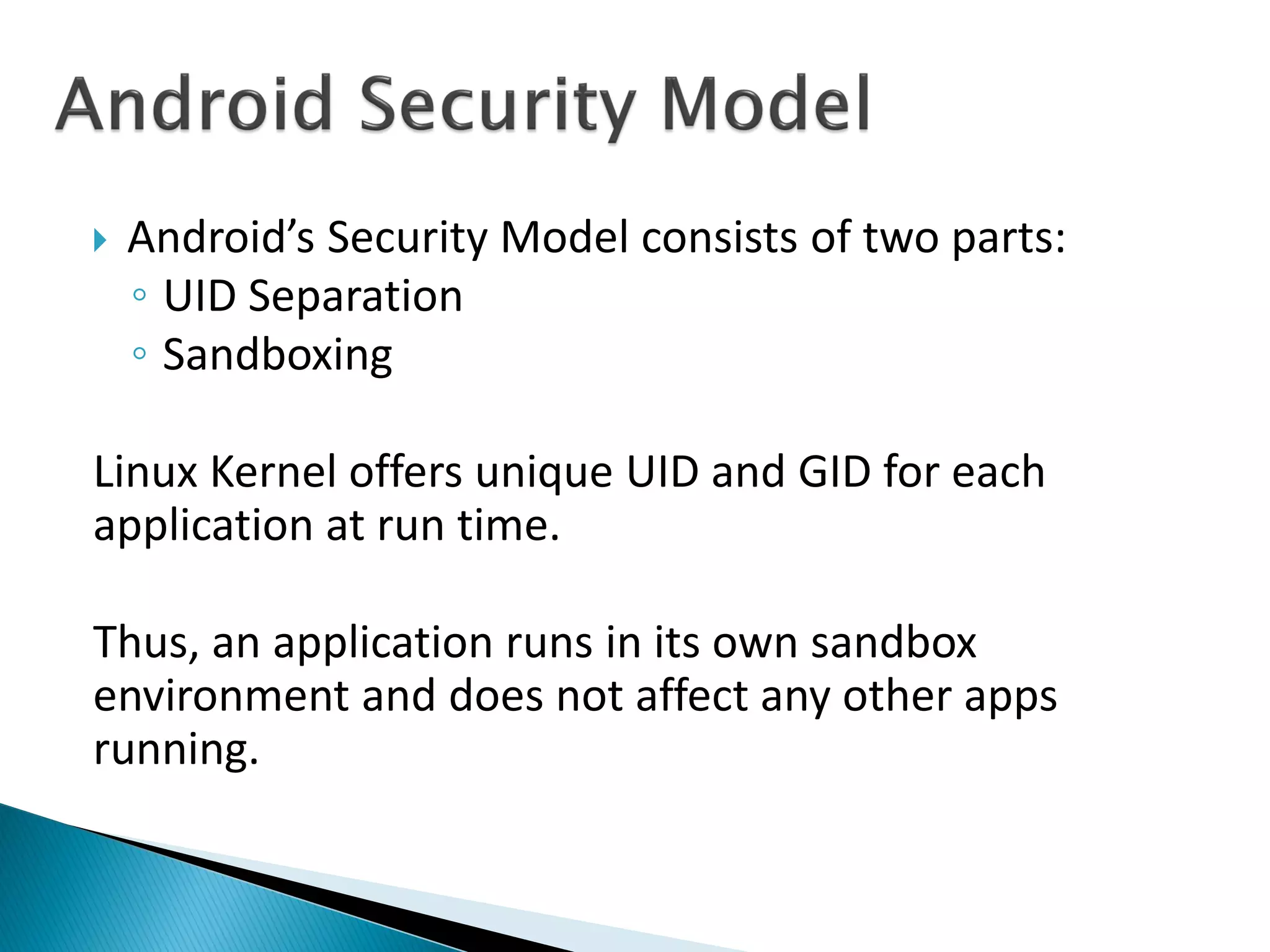
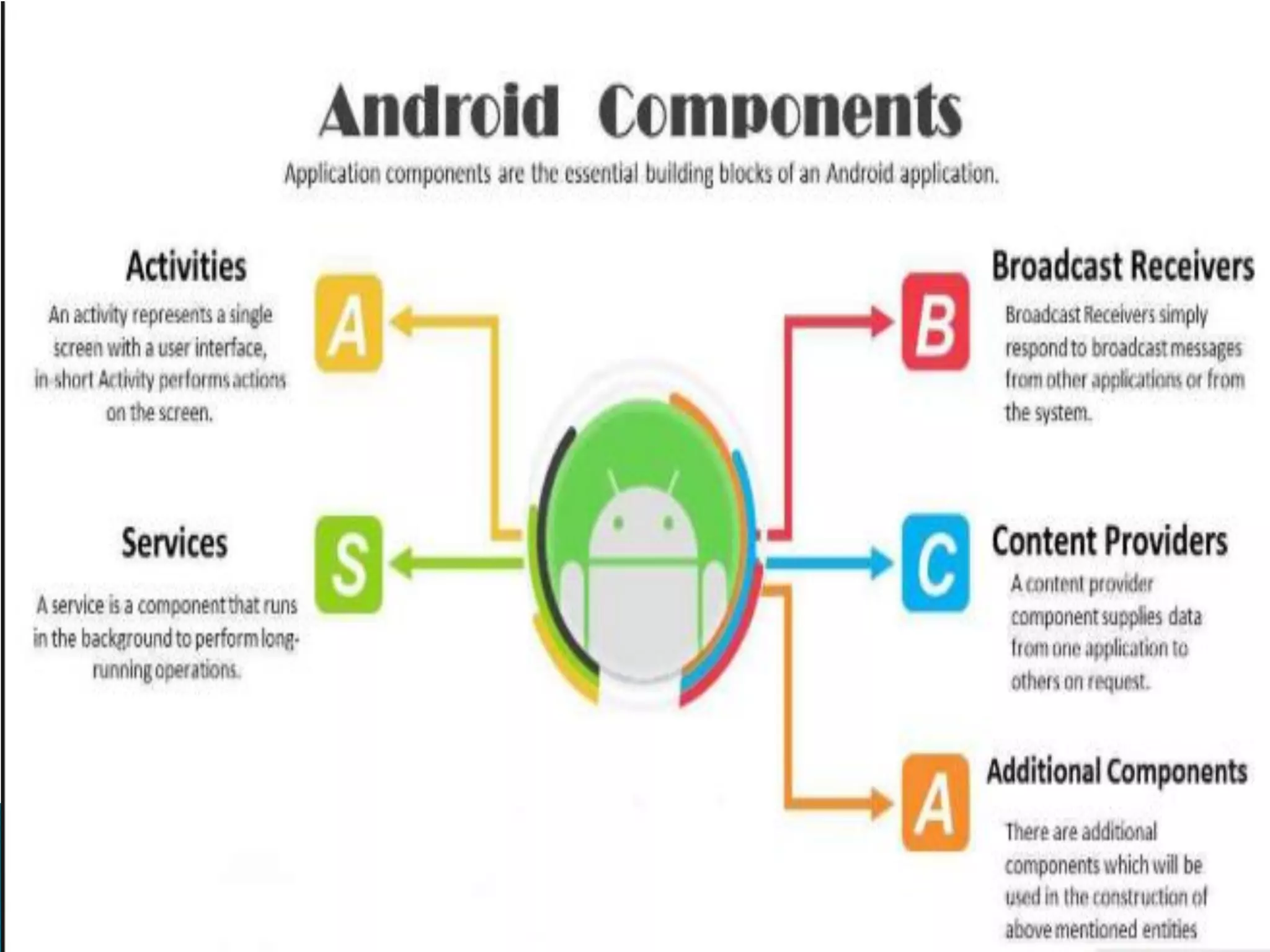
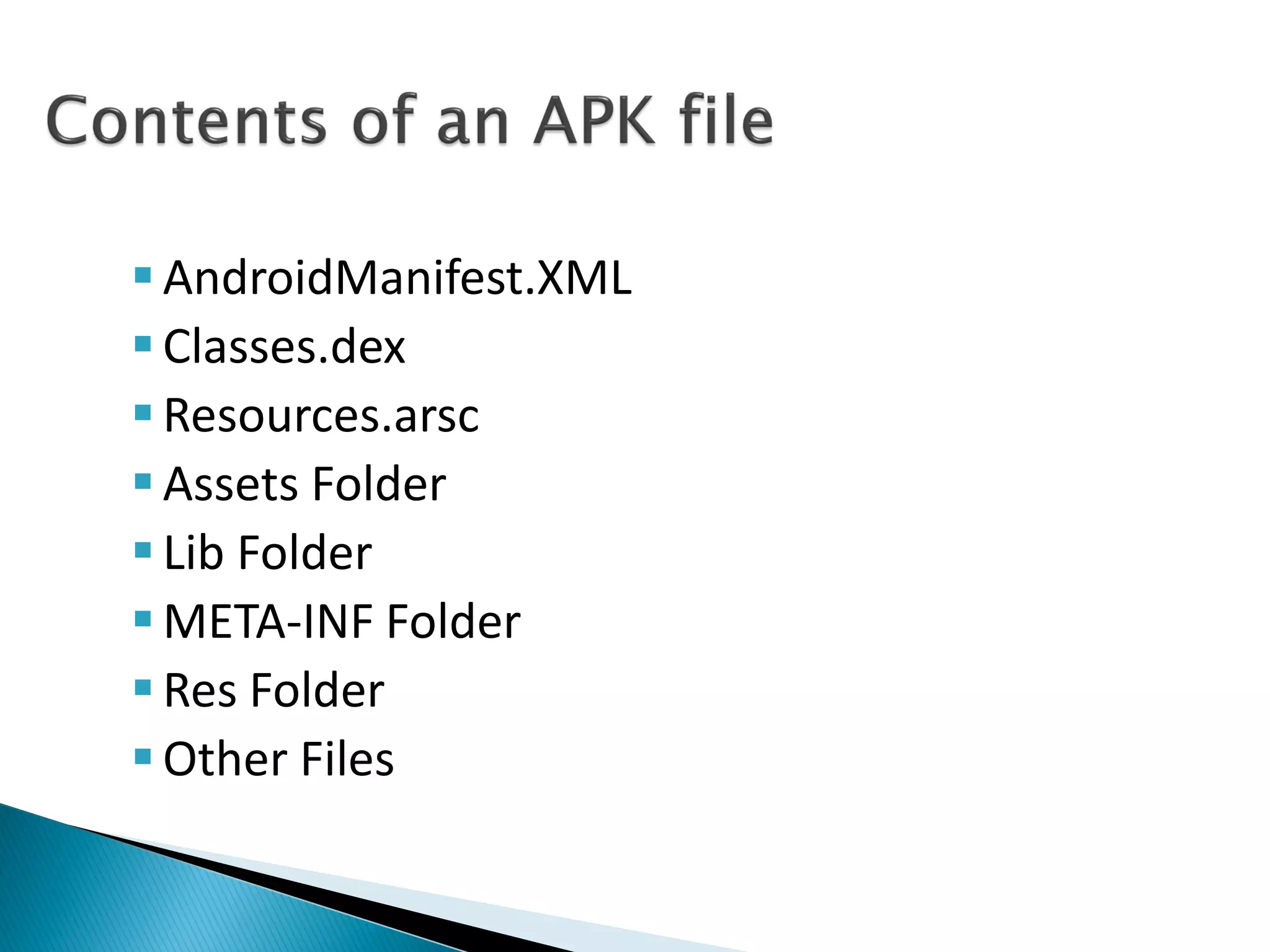
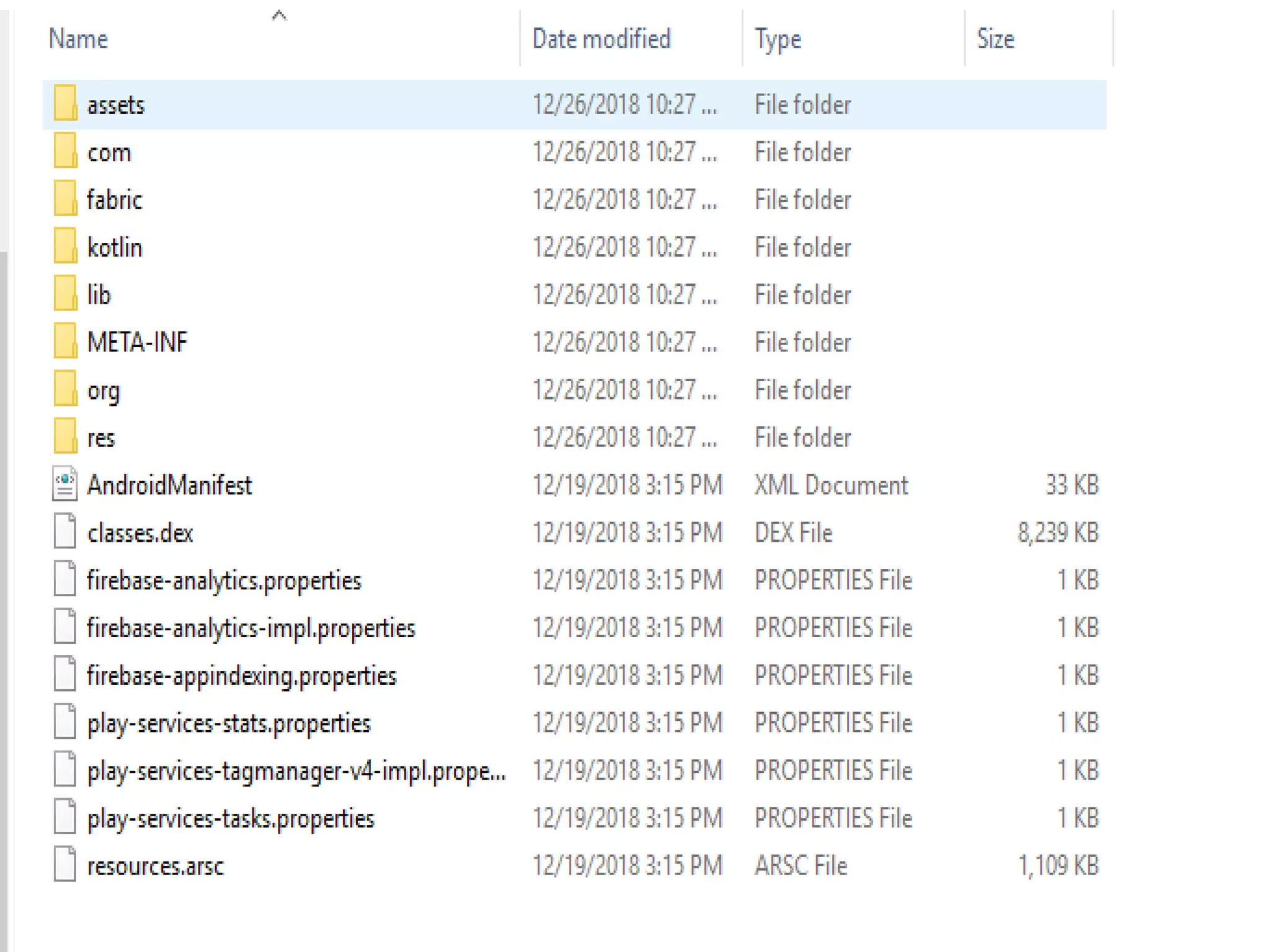
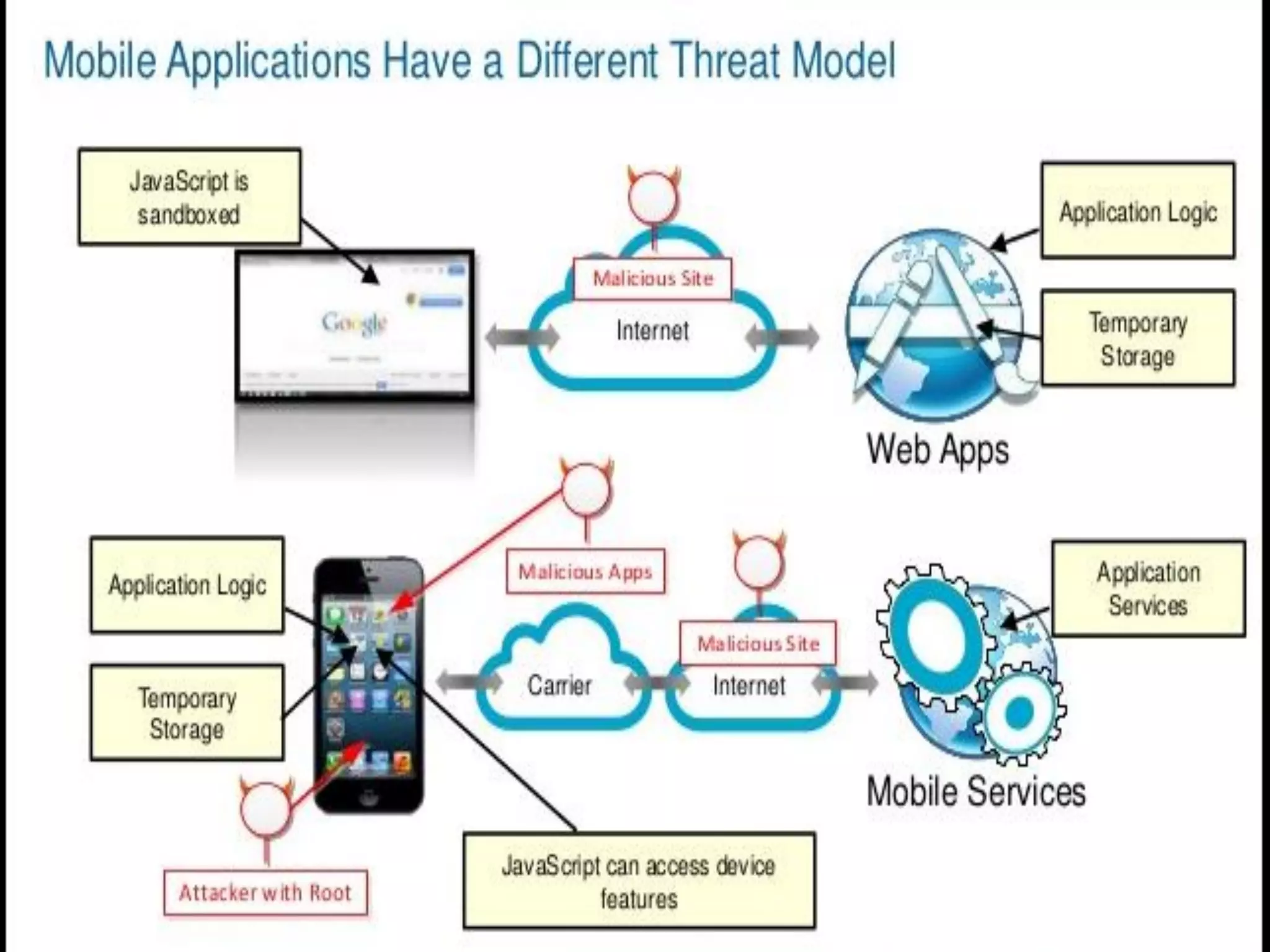
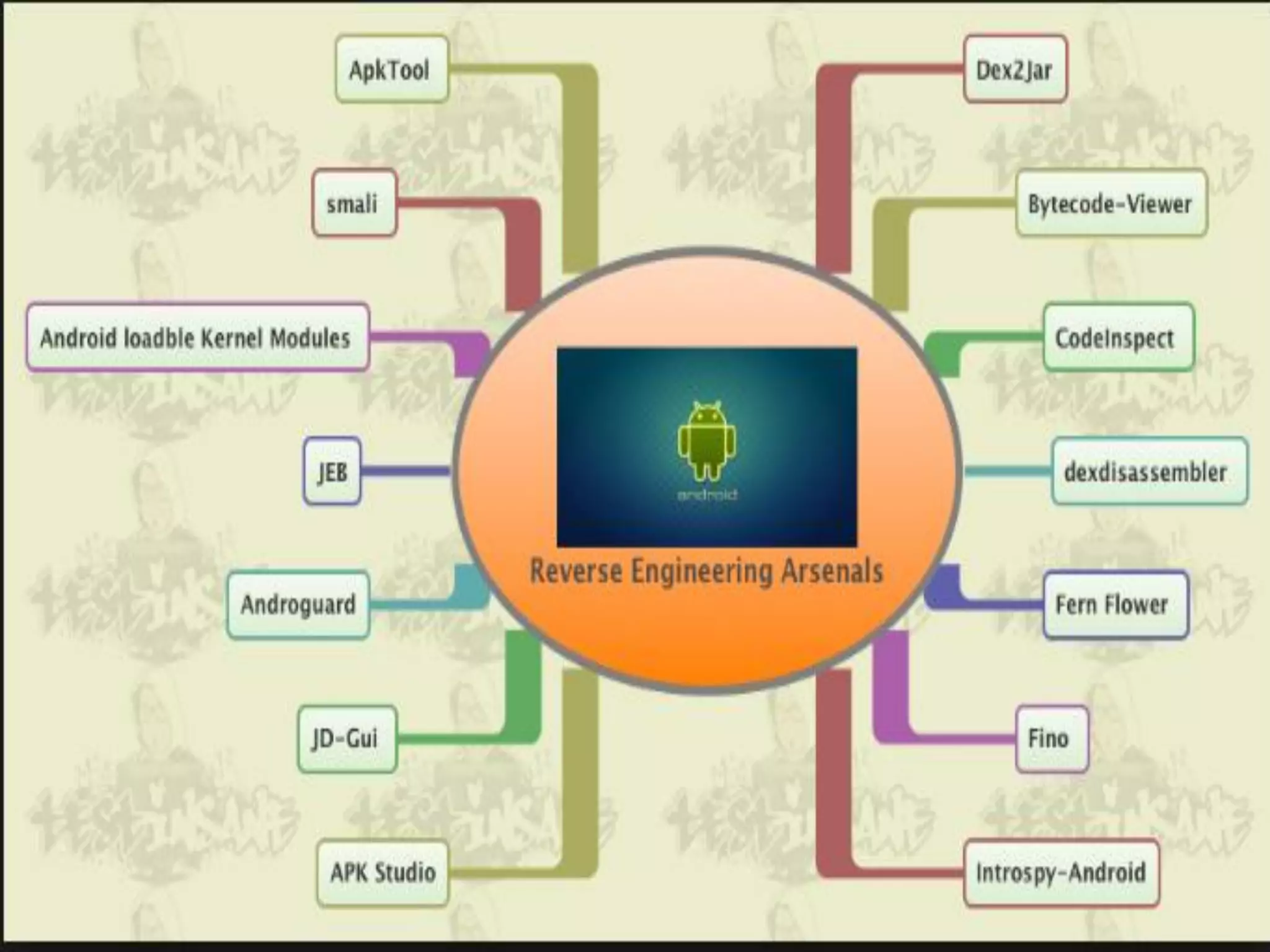
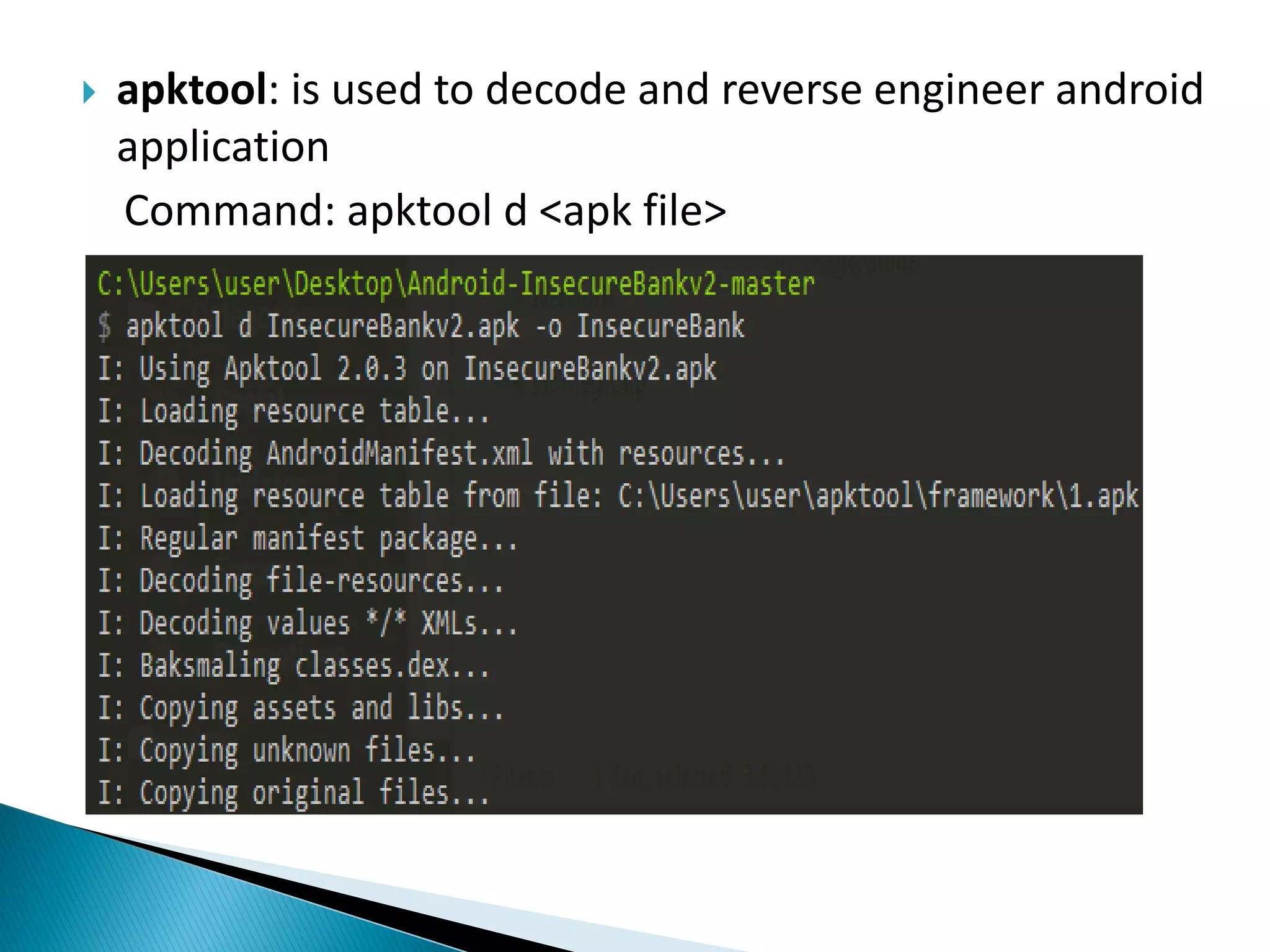
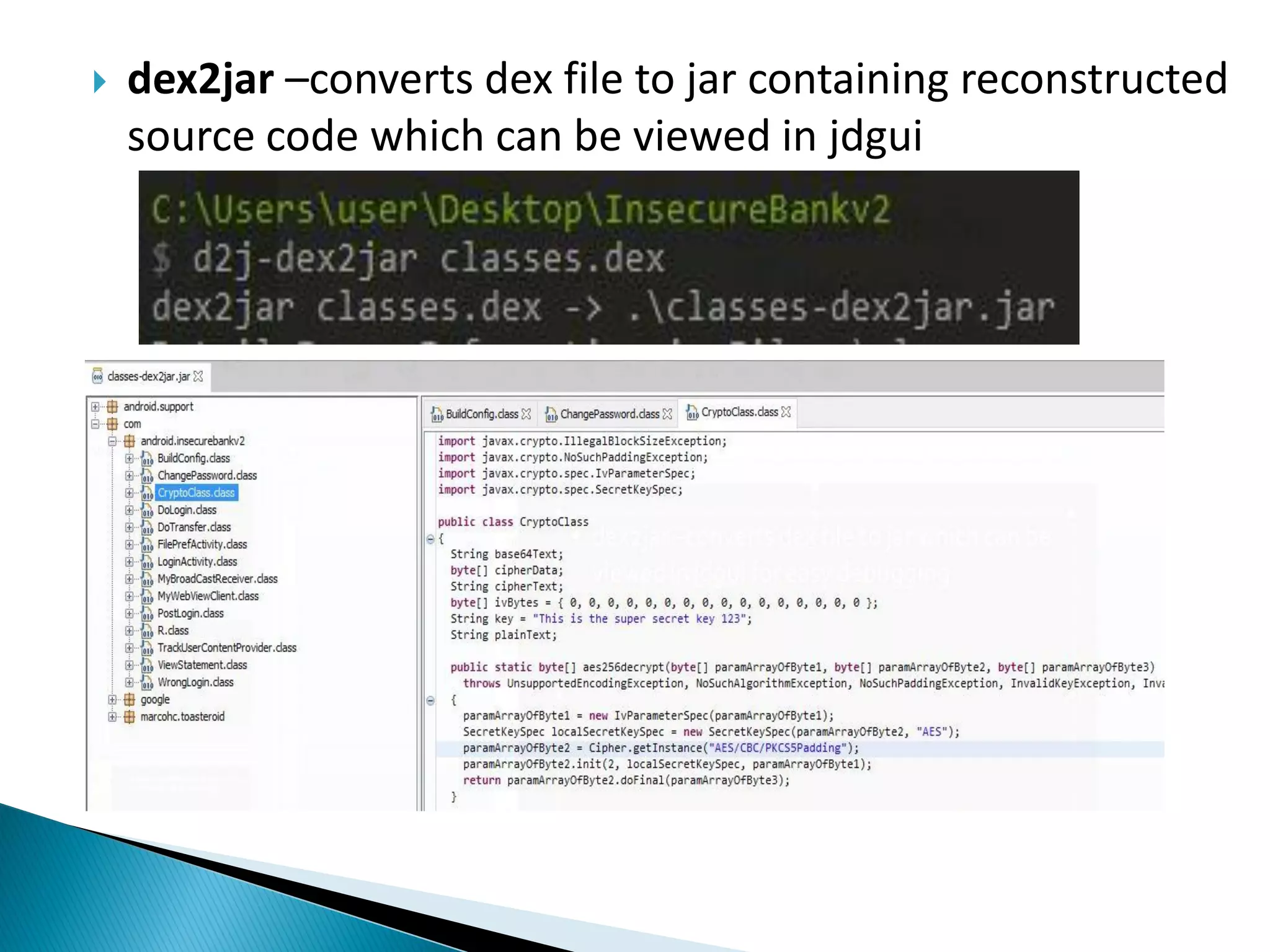
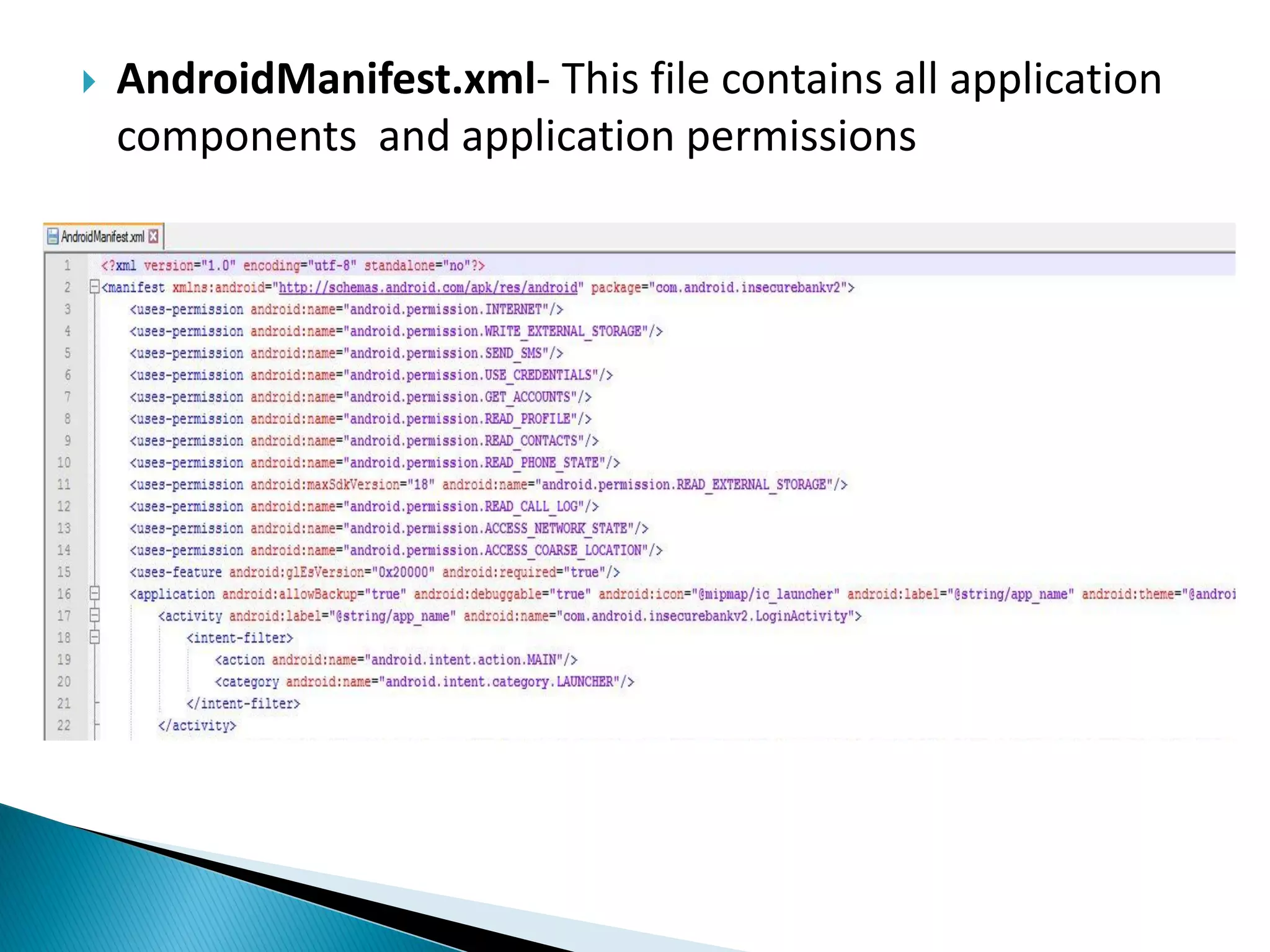
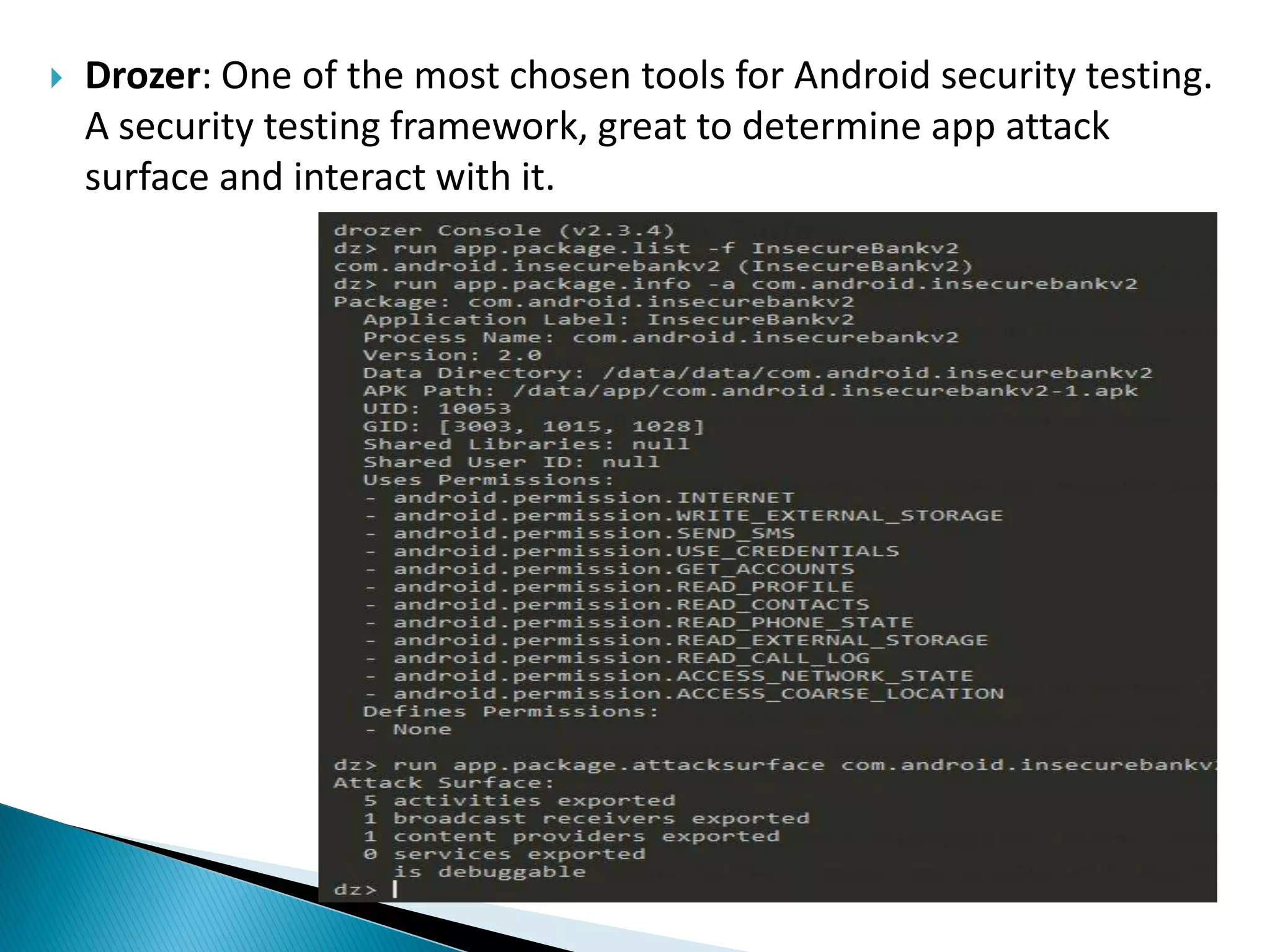
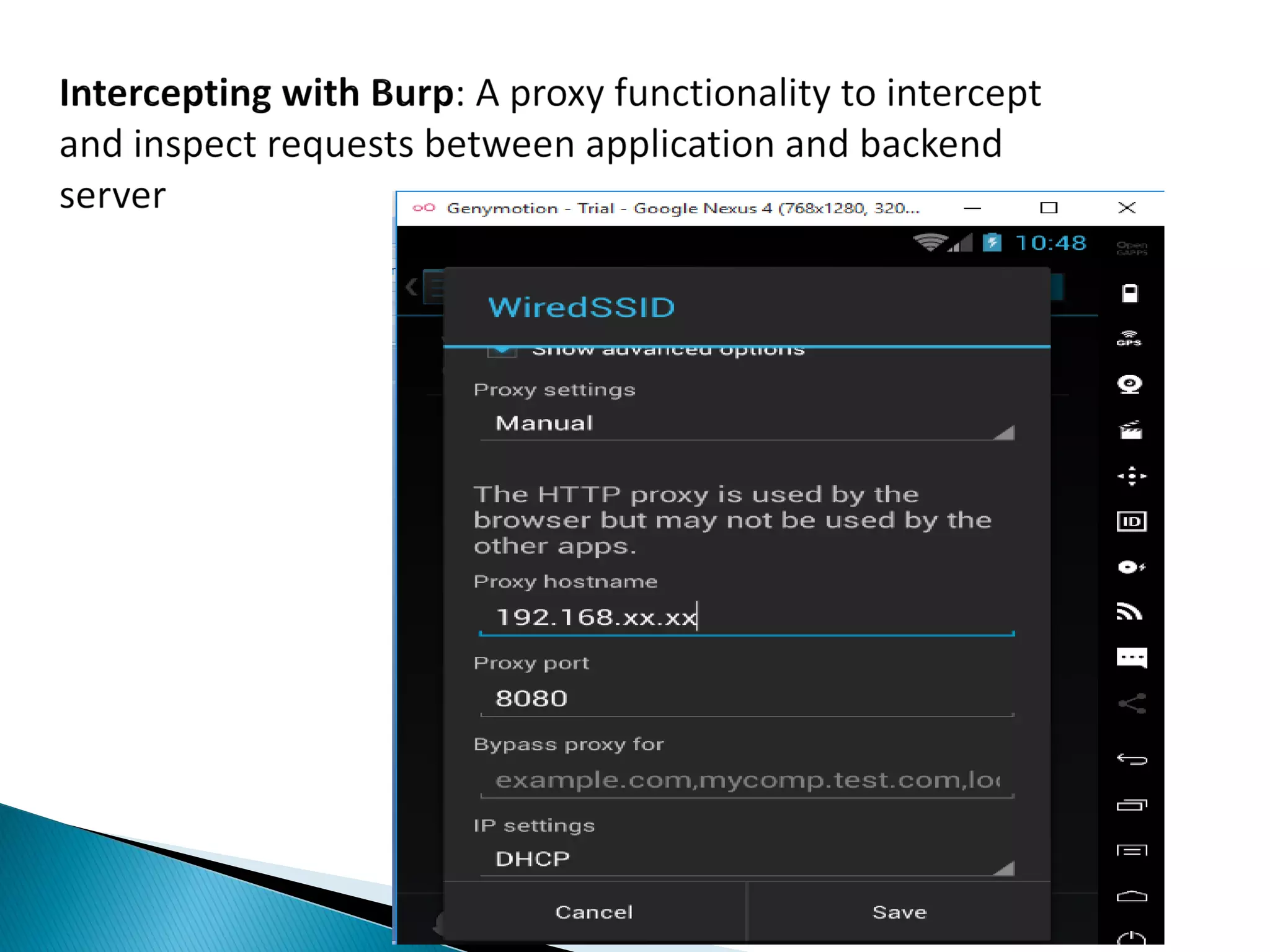
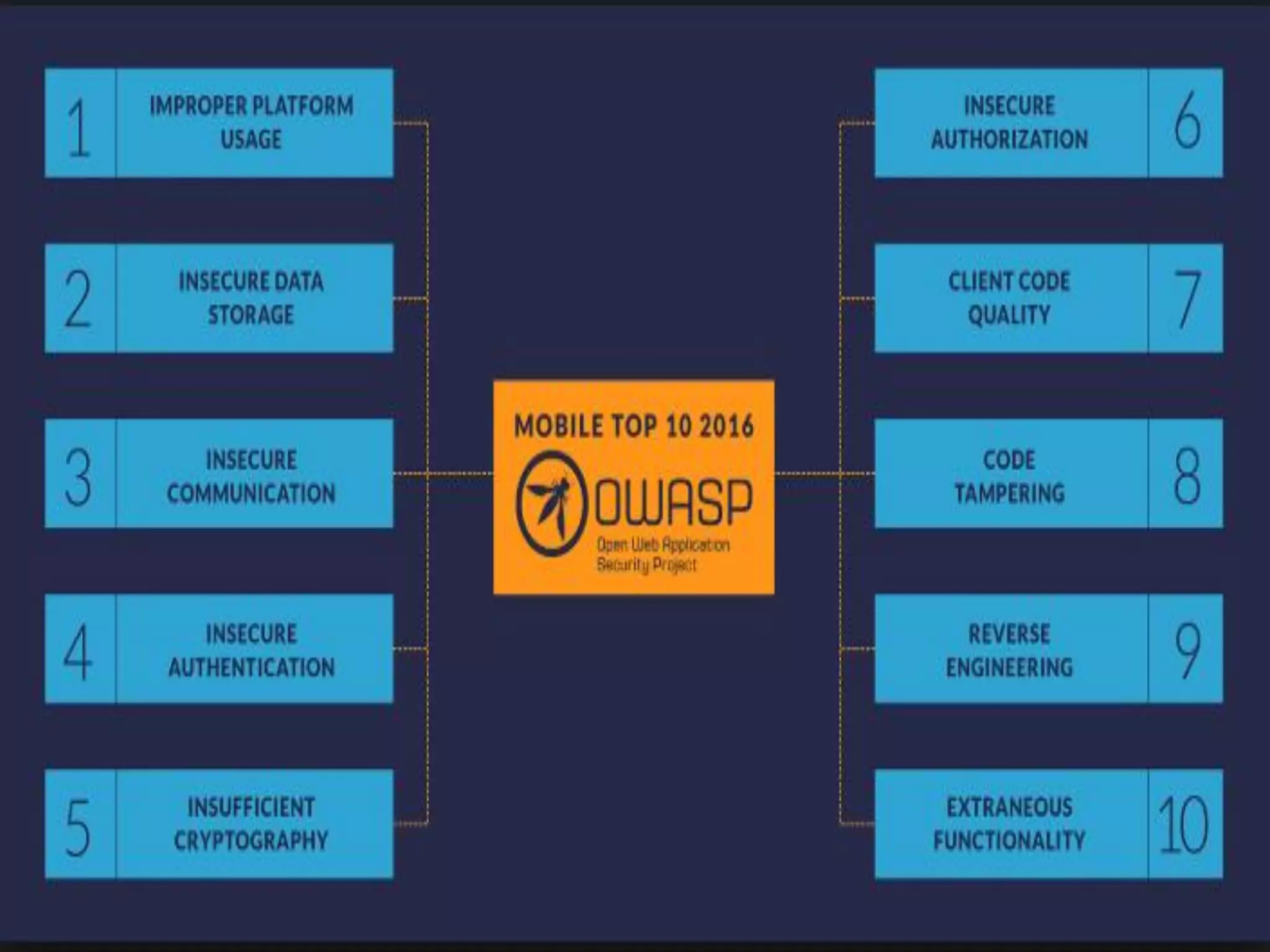
Minali Arora is a cyber security professional with 6 years of experience in application and network pentesting, bash scripting, and red teaming. She is also a part-time bug bounty hunter and blogger. The document discusses Android security architecture, testing methodologies, common vulnerabilities, and security tips for developers. It covers topics such as Android security model, application components, static and dynamic testing tools, and the OWASP top 10.