The document discusses information security programming in Ruby, focusing on authentication, encryption, and secure communication practices. It outlines various implementation patterns, SSL configurations, and provides example code snippets for secure HTTP client usage and AWS KMS integration. The content also addresses challenges such as server authentication and weak connections, providing insights into common pitfalls and solutions in Ruby security programming.




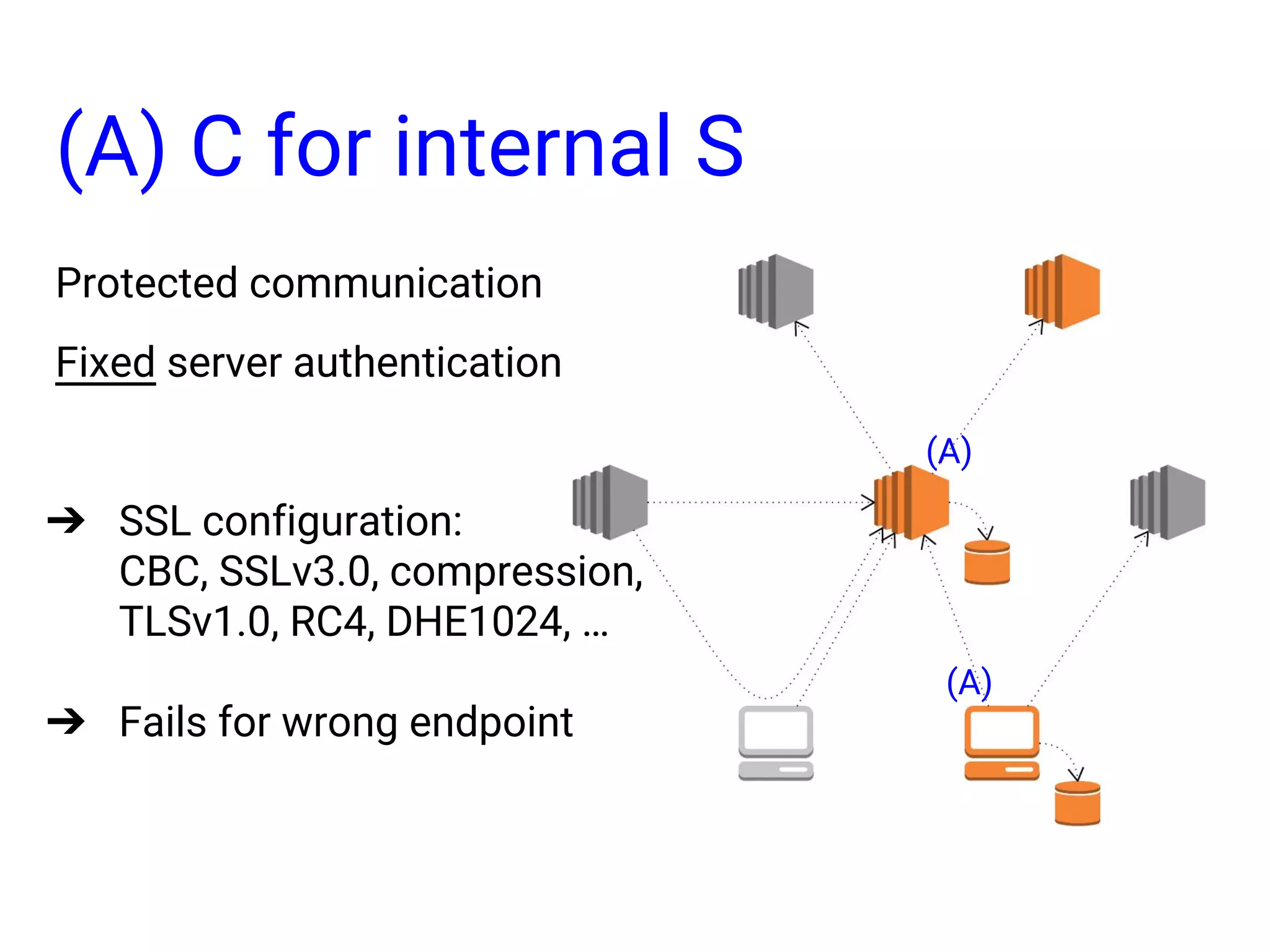
![(D) S for external C [F] Encryption in S [G] Encryption in C [E] authentication (C) S for internal C (B) C for external S 7 Implementation Patterns (A) C for internal S (A) (A) (B) (B) (C) (D) [F] [G] [E] [E] Orange: Implementation target Gray: External system](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-6-2048.jpg)
![(D) S for external C [F] Encryption in S [G] Encryption in C [E] authentication (C) S for internal C (B) C for external S 7 Implementation Patterns (A) C for internal S (A) (A) (B) (B) (C) (D) [F] [G] [E] [E] Orange: Implementation target Gray: External system](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-7-2048.jpg)
![… in Ruby (A) C for internal S (B) C for external S (C) S for internal C (D) S for external C [E] authentication [F] Encryption in S [G] Encryption in C (A) (A) (B) (B) (C) [E] [F] [G] (D) [E] Blue: Acceptable Orange: Pitfalls Red: No way](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-8-2048.jpg)
![SSL configuration require 'httpclient' client = HTTPClient.new client.get('https://www.ruby-lang.org/en/').status % ruby a1.rb ok: "/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA" ok: "/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Domain Validation CA - SHA256 - G2" ok: "/OU=Domain Control Validated/CN=*.ruby-lang.org" Protocol version: TLSv1.2 Cipher: ["ECDHE-RSA-AES128-GCM-SHA256", "TLSv1/SSLv3", 128, 128] State: SSLOK : SSL negotiation finished successfully](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-10-2048.jpg)
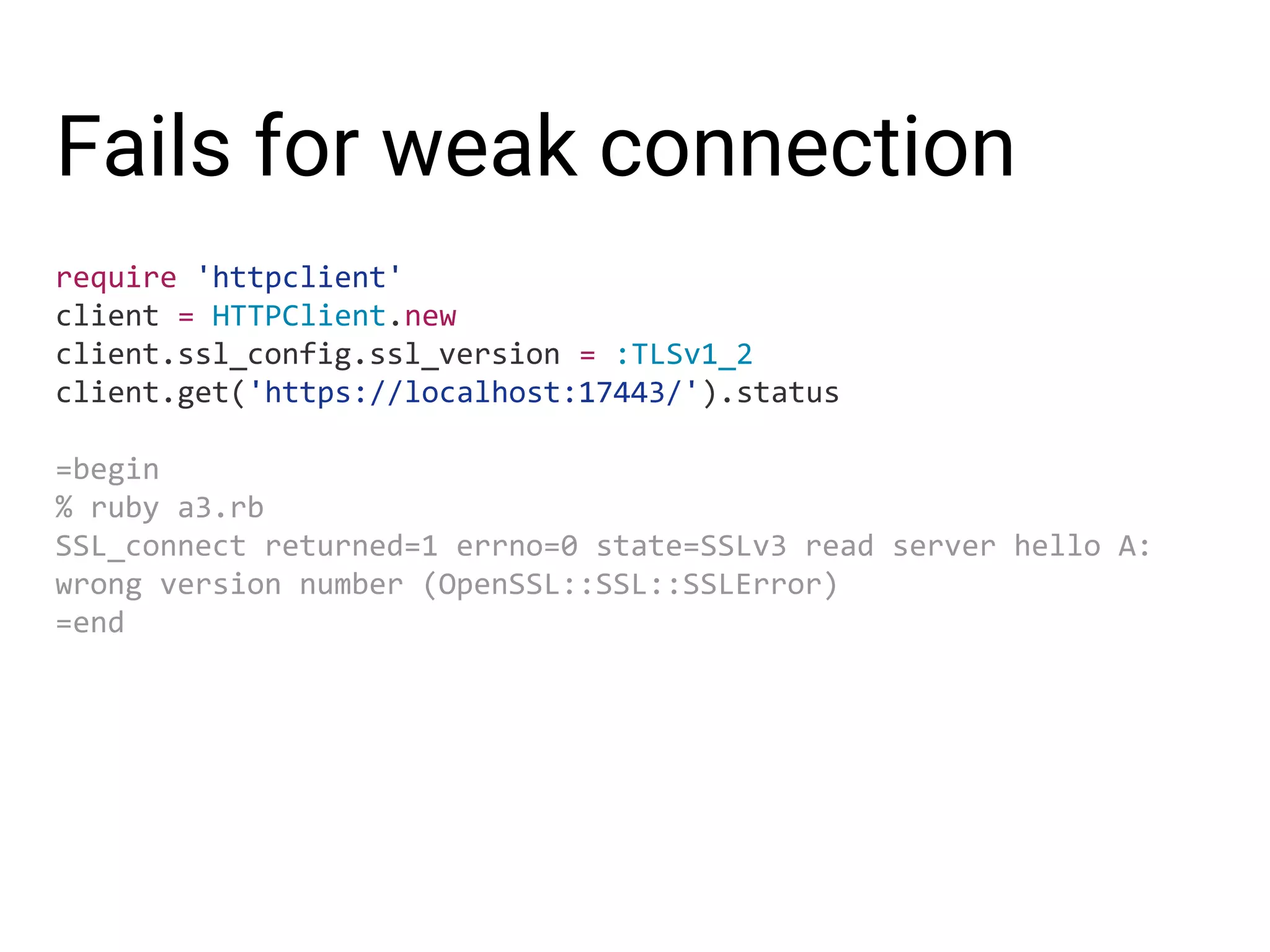
![Fails for wrong endpoint require 'httpclient' client = HTTPClient.new client.get('https://hyogo-9327.herokussl.com/en/').status % ruby -d a2.rb ok: "/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA" ok: "/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Domain Validation CA - SHA256 - G2" ok: "/OU=Domain Control Validated/CN=*.ruby-lang.org" Protocol version: TLSv1.2 Cipher: ["ECDHE-RSA-AES128-GCM-SHA256", "TLSv1/SSLv3", 128, 128] State: SSLOK : SSL negotiation finished successfully Exception `OpenSSL::SSL::SSLError' - hostname "hyogo-9327. herokussl.com" does not match the server certificate](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-11-2048.jpg)
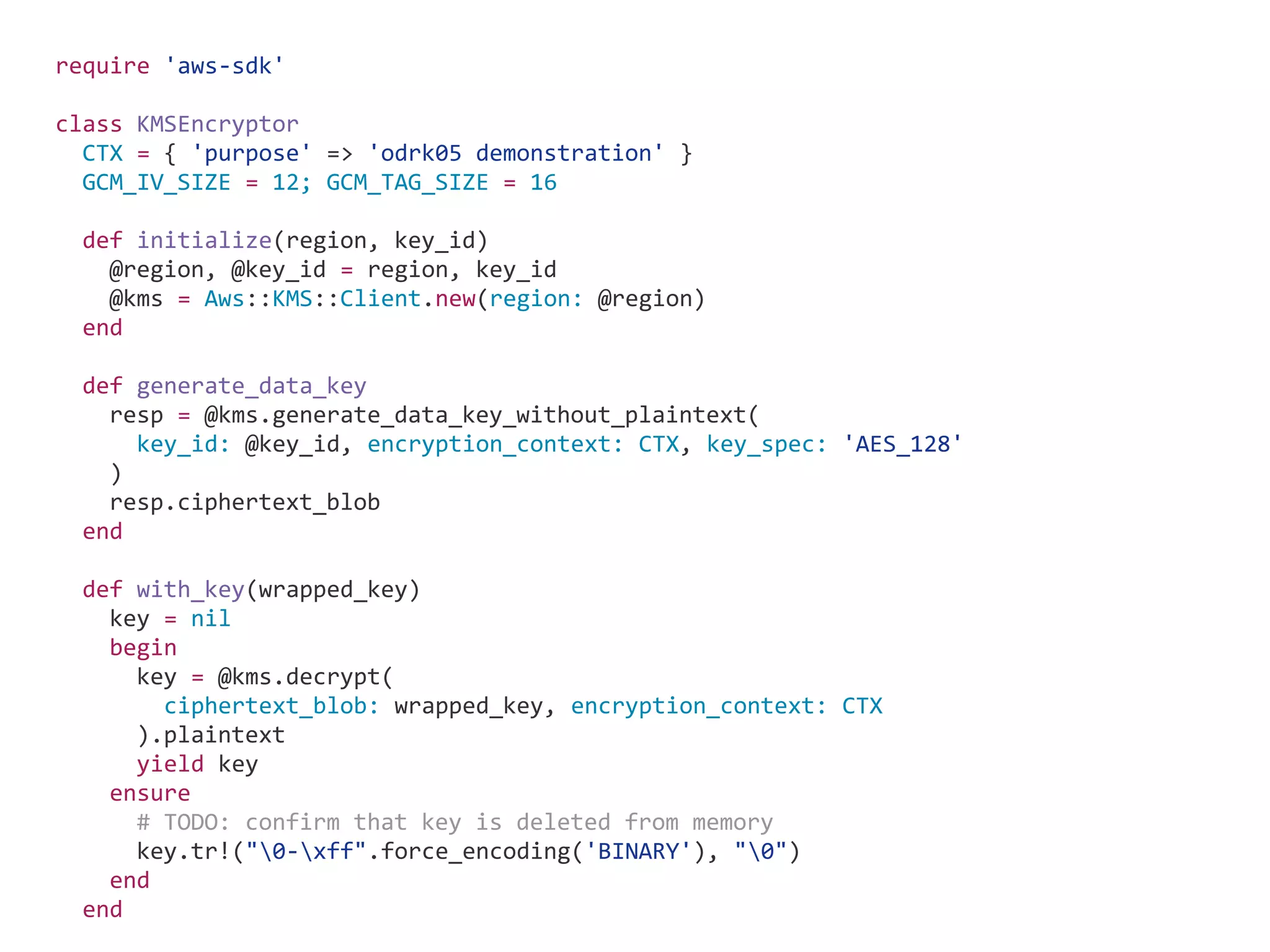
![WEBrick SSL server require 'webrick/https' require 'logger' logger = Logger.new(STDERR) server = WEBrick::HTTPServer.new( BindAddress: "localhost", Logger: logger, Port: 17443, DocumentRoot: '/dev/null', SSLEnable: true, SSLCACertificateFile: 'ca-chain.cert', SSLCertificate: OpenSSL::X509::Certificate.new( File.read('server.cert')), SSLPrivateKey: OpenSSL::PKey::RSA.new( File.read('server.key')), ) basic_auth=WEBrick::HTTPAuth::BasicAuth.new( Logger: logger, Realm: 'auth', UserDB: WEBrick::HTTPAuth::Htpasswd.new( 'htpasswd') ) # => # => server.mount('/hello', WEBrick::HTTPServlet::ProcHandler.new( ->(req, res) { basic_auth.authenticate(req, res) res['content-type'] = 'text/plain' res.body = 'hello' }) ) trap(:INT) do server.shutdown end t = Thread.new { Thread.current.abort_on_exception = true server.start } while server.status != :Running sleep 0.1 raise unless t.alive? end puts $$ t.join](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-18-2048.jpg)
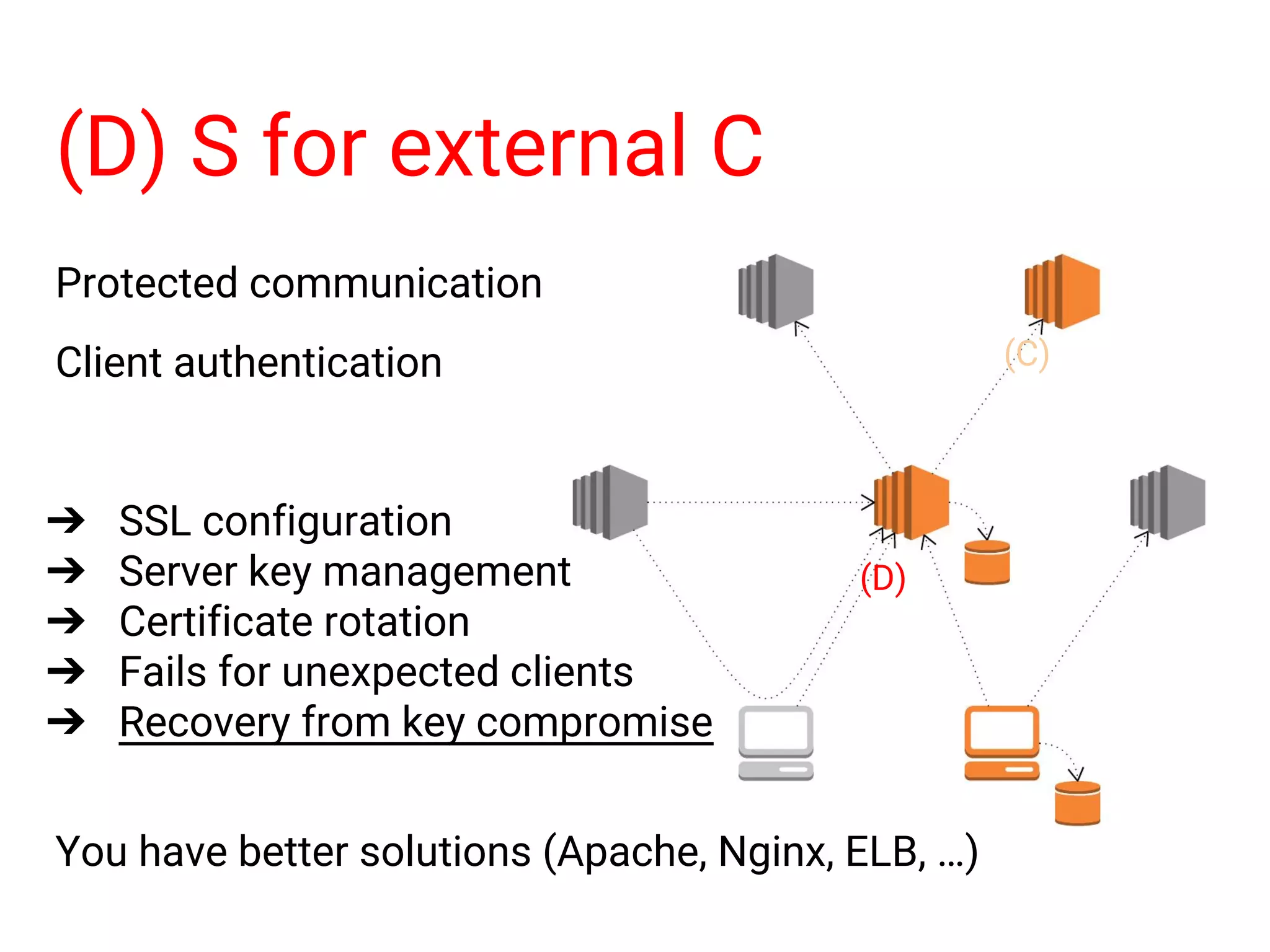
![Client authentication On unprotected network ➔ Cipher algorithm ➔ Tamper detection ➔ Constant time operation Use well-known library [E] authentication [E] [E]](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-20-2048.jpg)
![Data protection at rest ➔ Cipher algorithm ➔ Encryption key management ◆ Storage ◆ Usage authn / authz ◆ Usage auditing ◆ Rotation ➔ Tamper detection ➔ Processing throughput / latency [F] Encryption in S / [G] in C [F] [G]](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-21-2048.jpg)
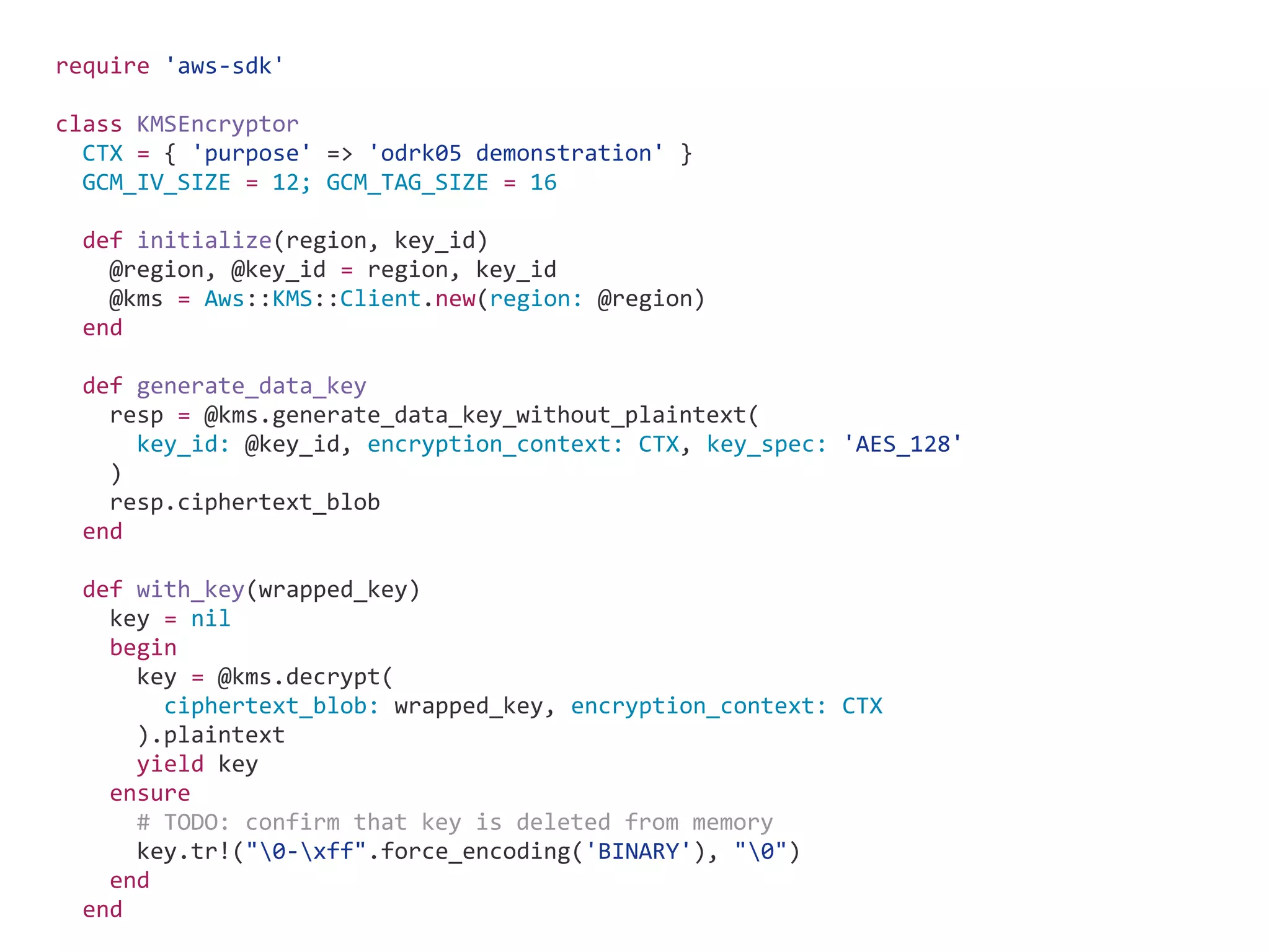
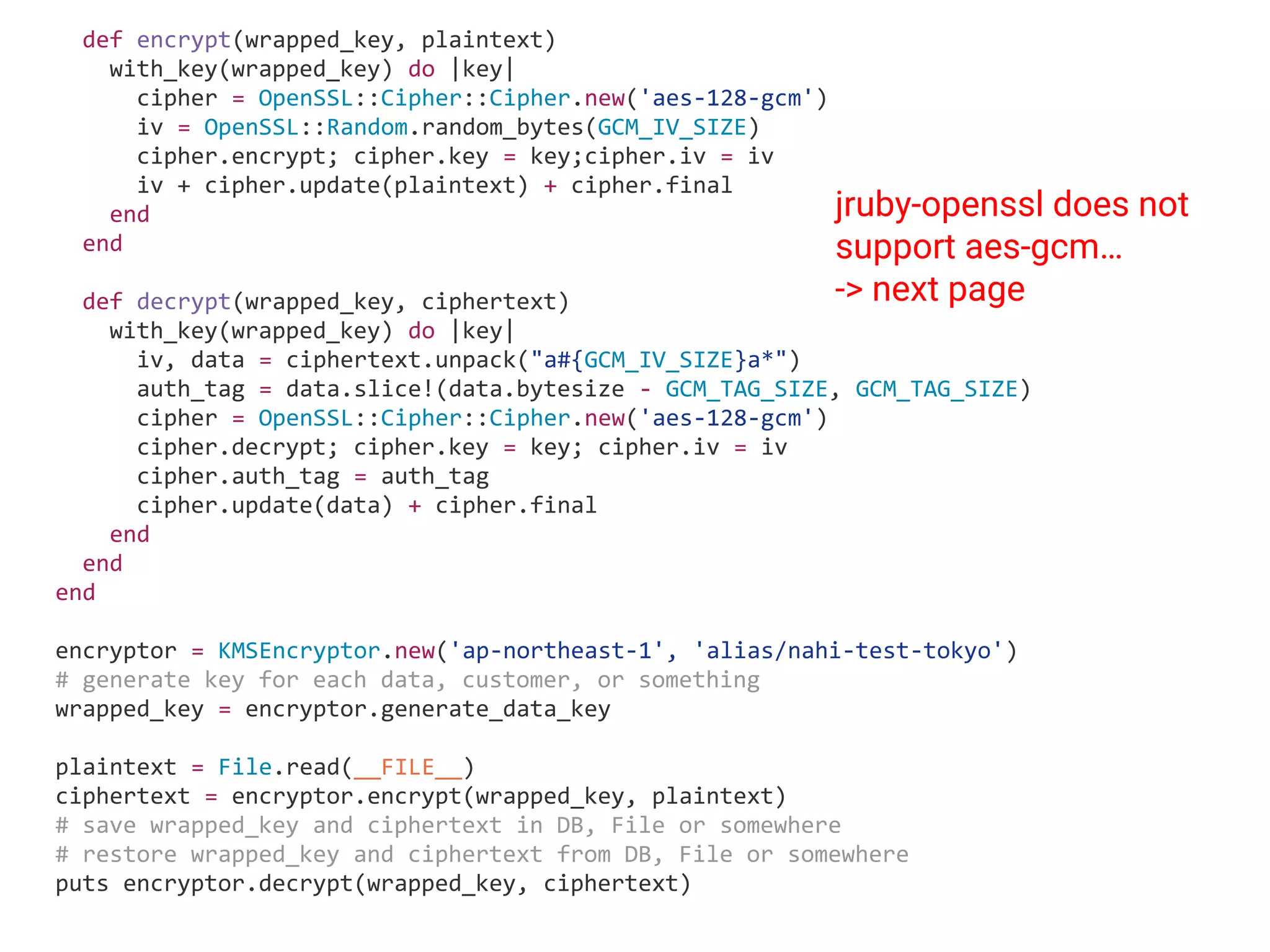
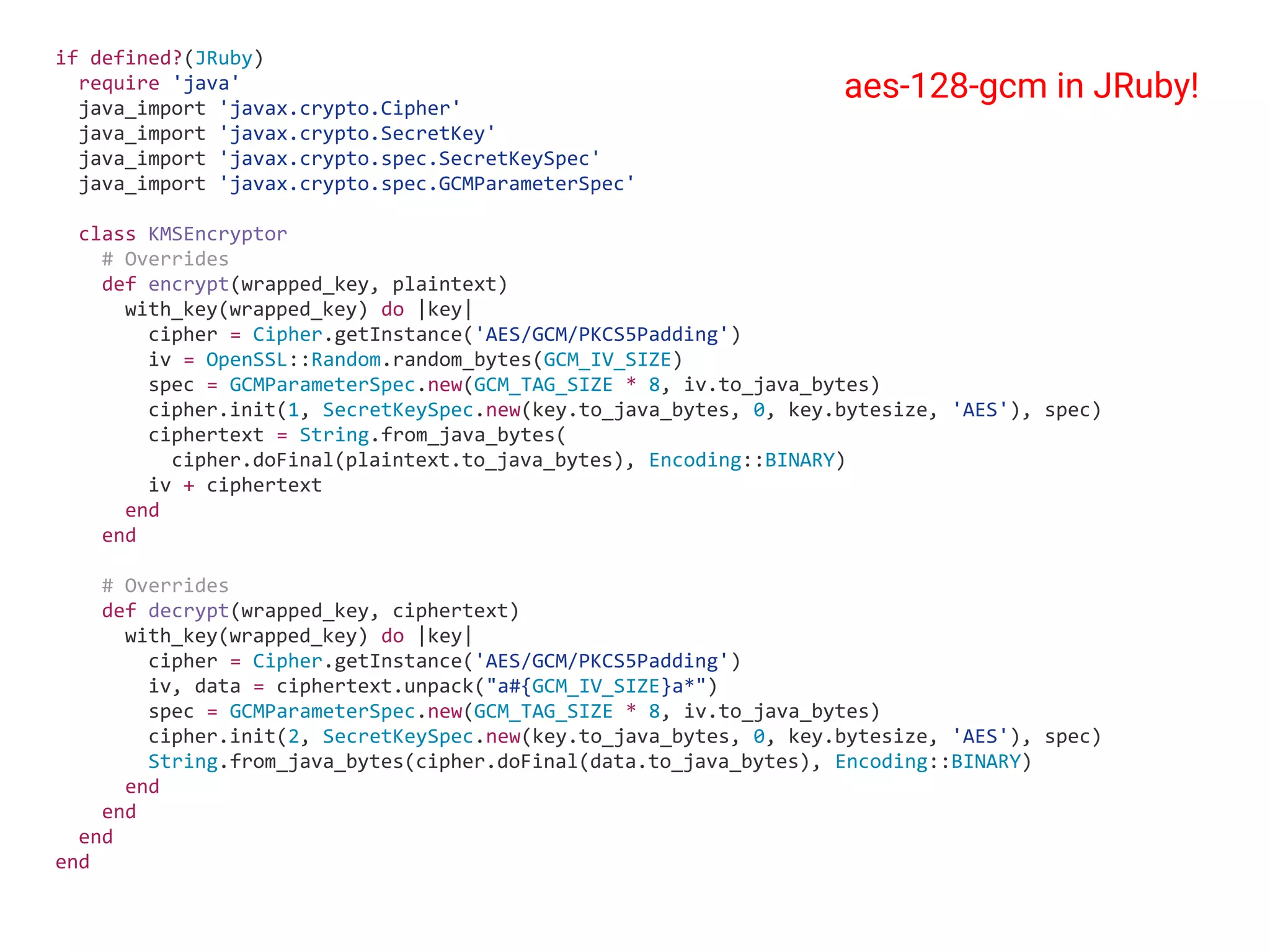
![… in Ruby (A) C for internal S (B) C for external S (C) S for internal C (D) S for external C [E] authentication [F] Encryption in S [G] Encryption in C (A) (A) (B) (B) (C) [E] [F] [G] (D) [E] Blue: Acceptable Orange: Pitfalls Red: No way](https://image.slidesharecdn.com/informationsecurityprogramminginruby-151108063547-lva1-app6892/75/Information-security-programming-in-ruby-25-2048.jpg)