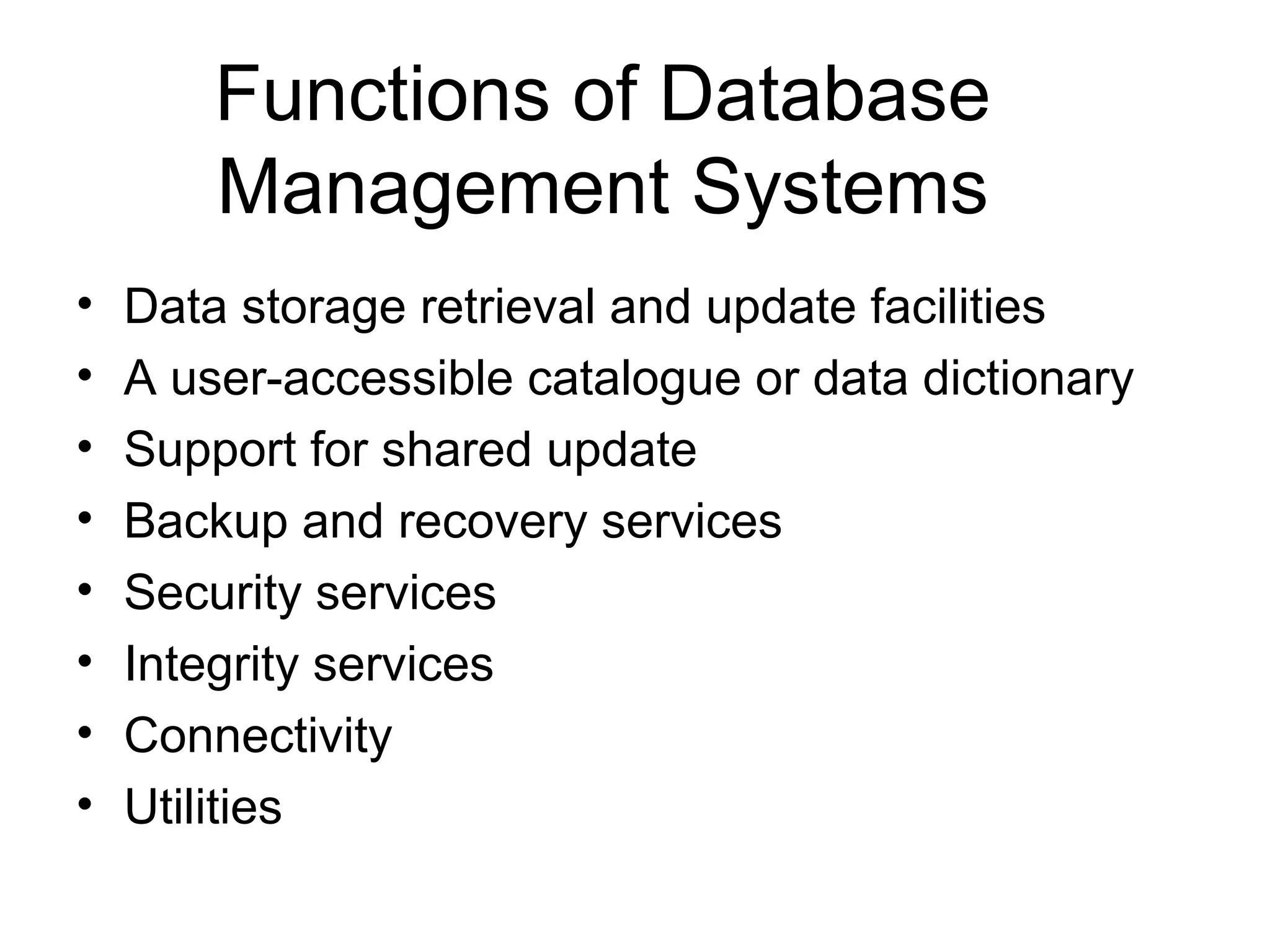
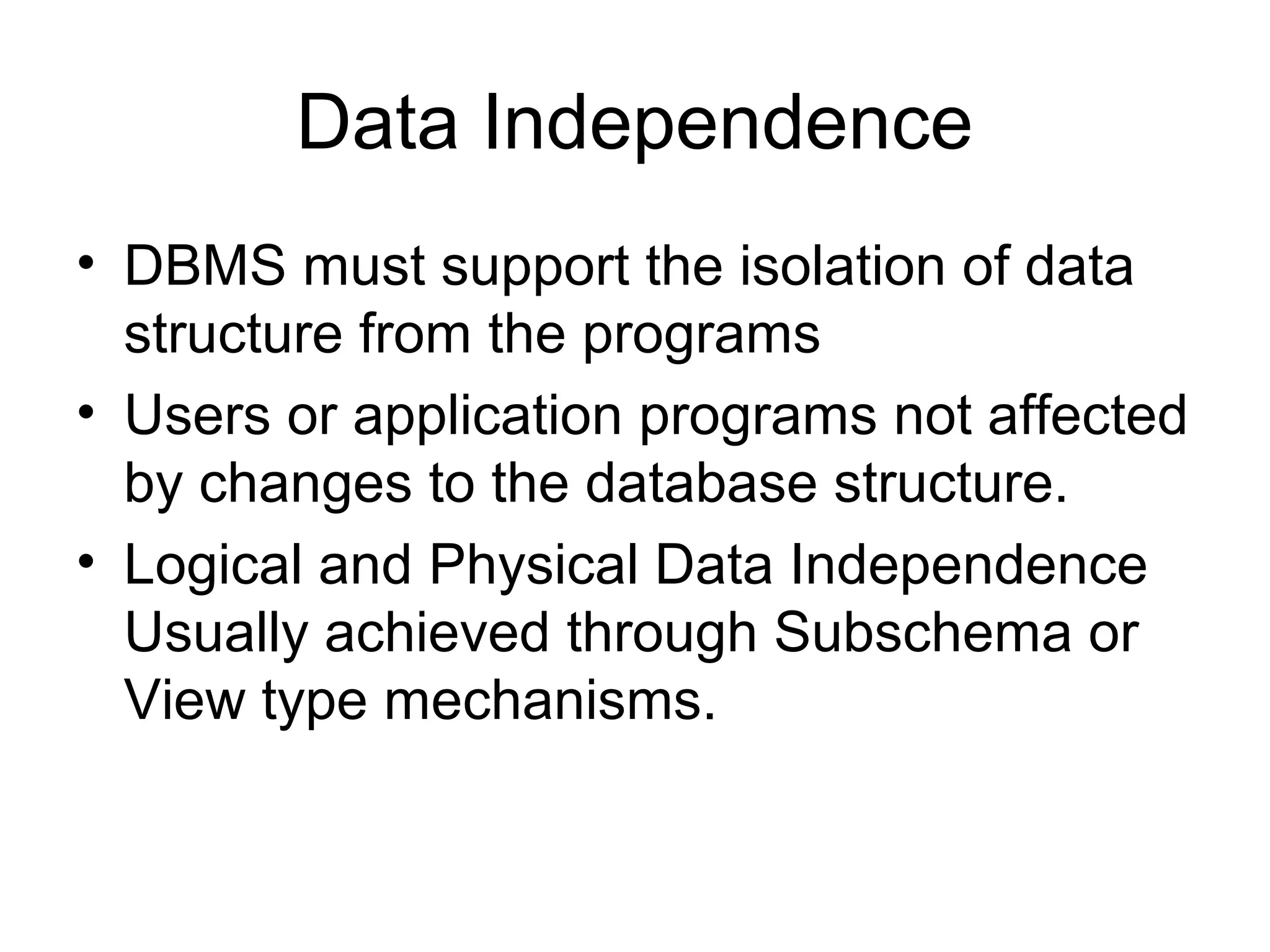
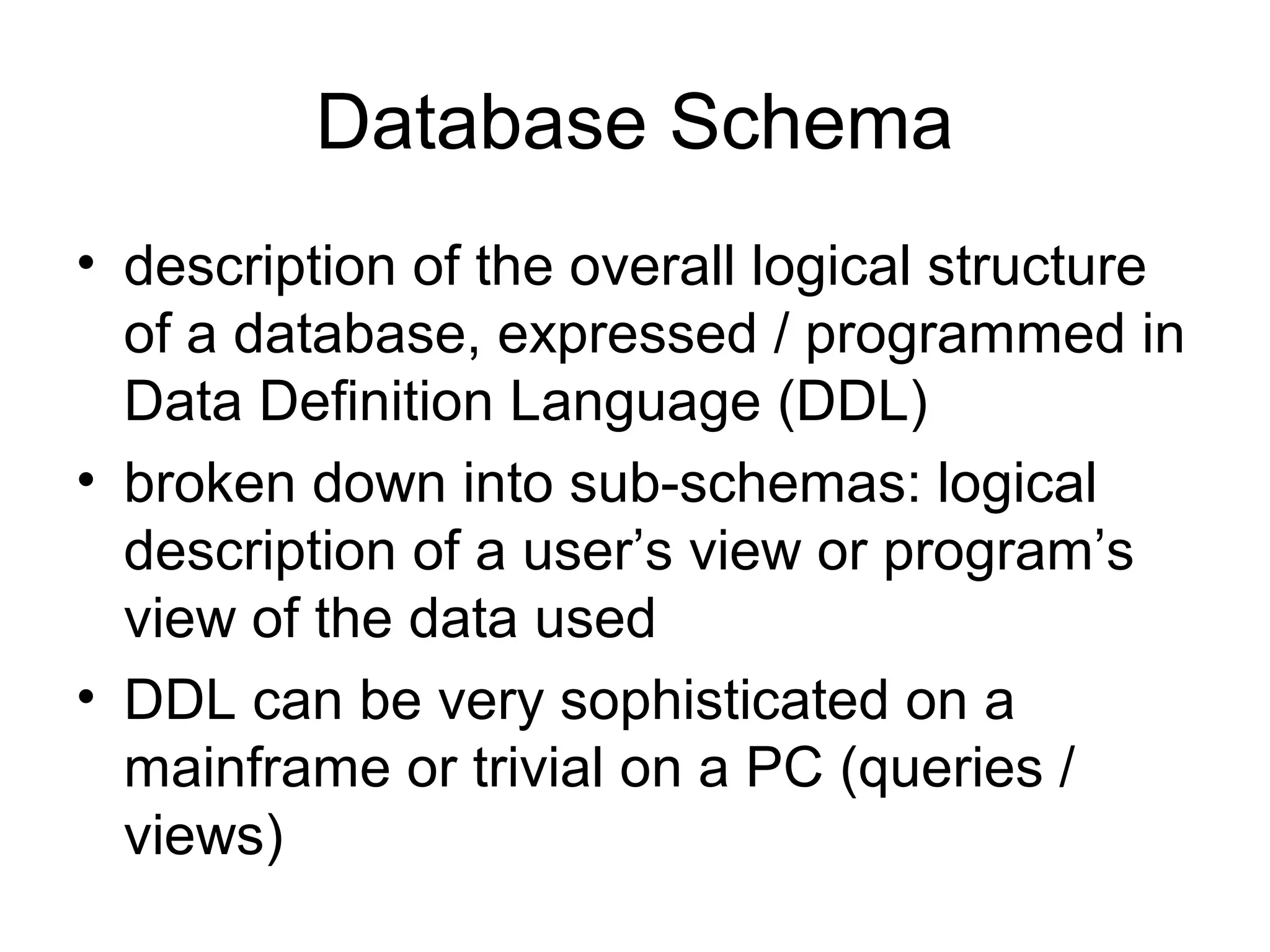
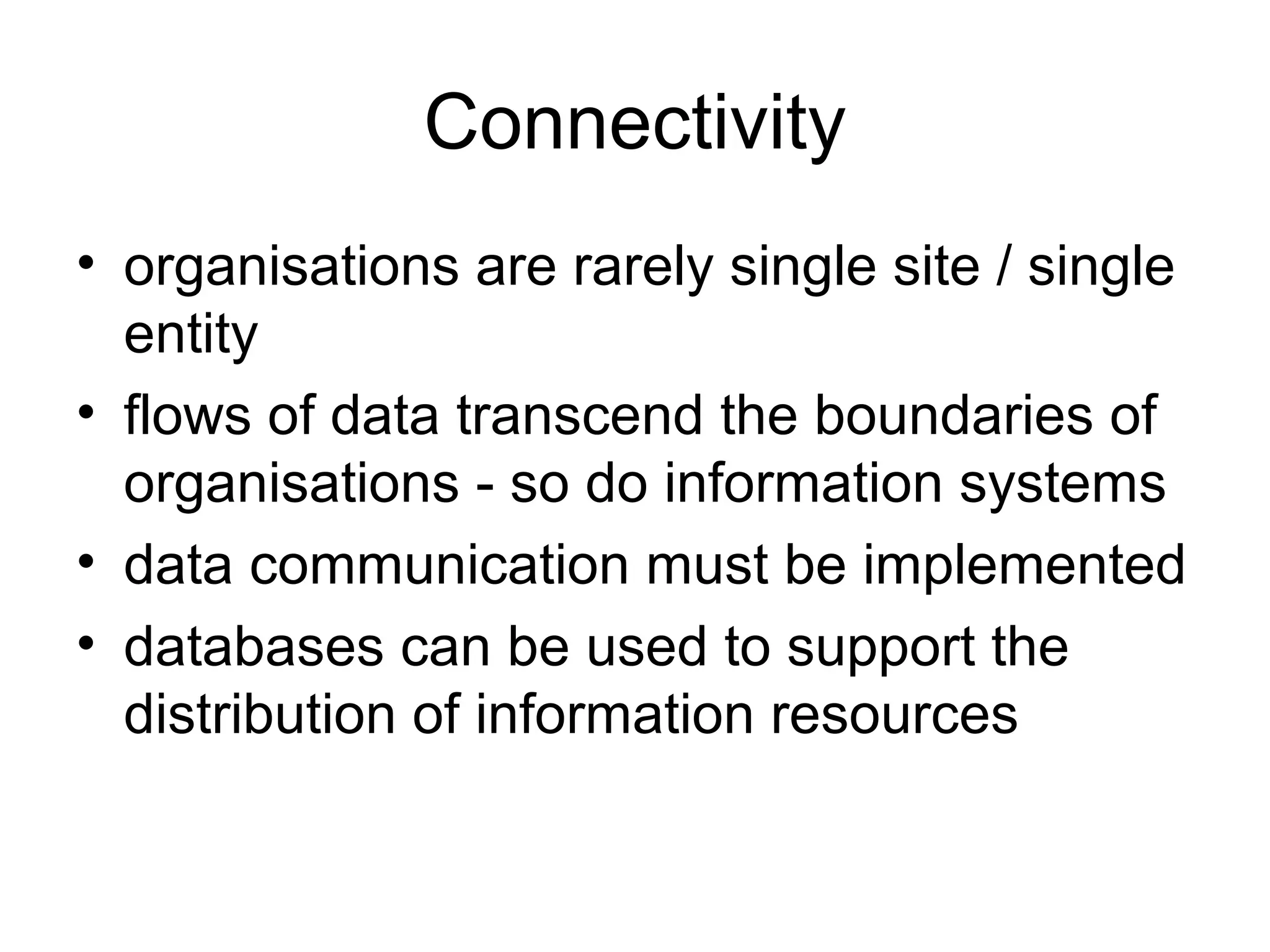
The document outlines several key functions of database management systems including data storage and retrieval, data dictionary, transaction processing with commit and rollback, concurrency control through locking, recovery through backups and journals, security, data integrity, data independence, and connectivity between distributed databases. Database utilities are also described for compacting, indexing, importing/exporting data, and enforcing database standards.