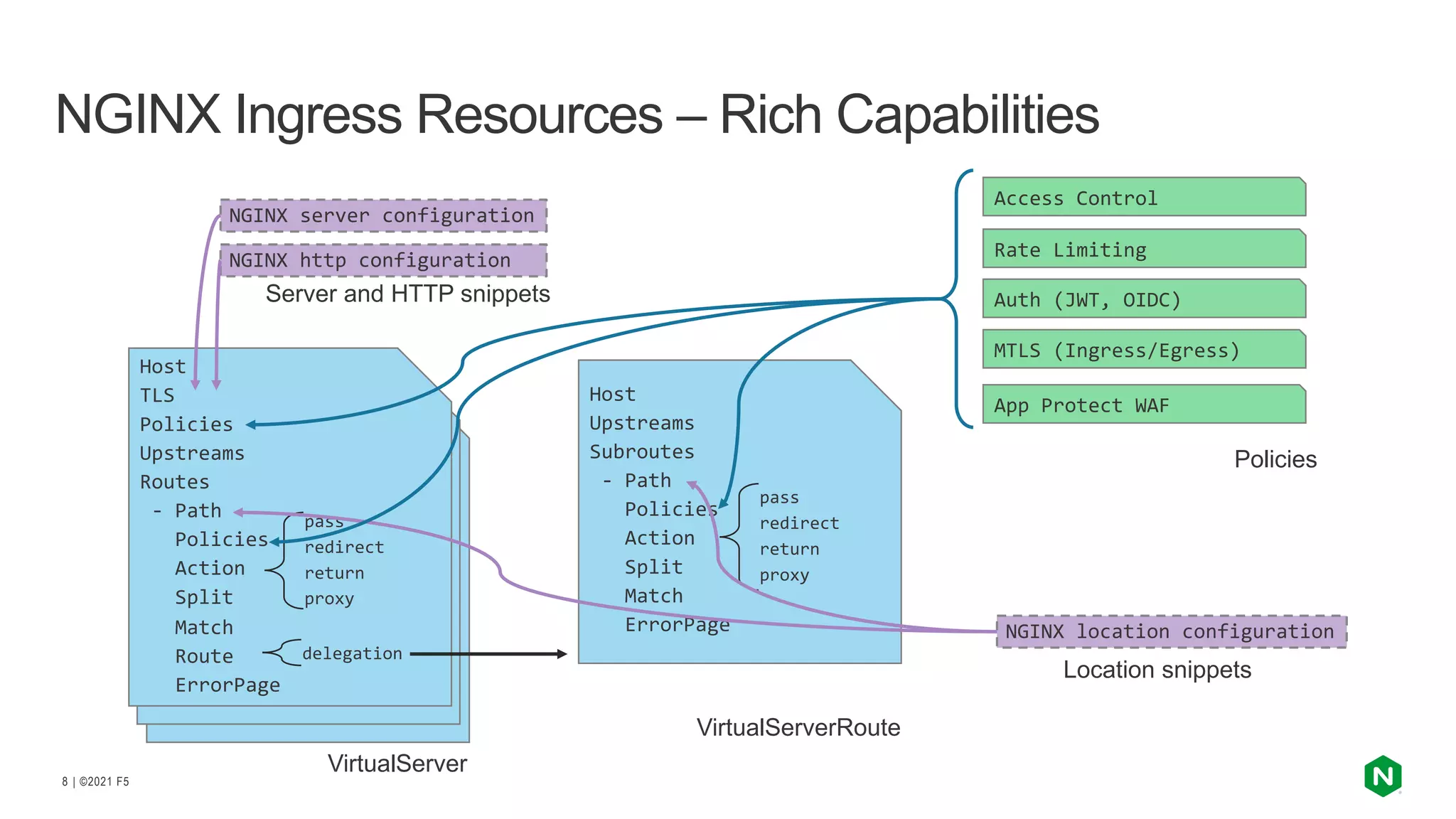
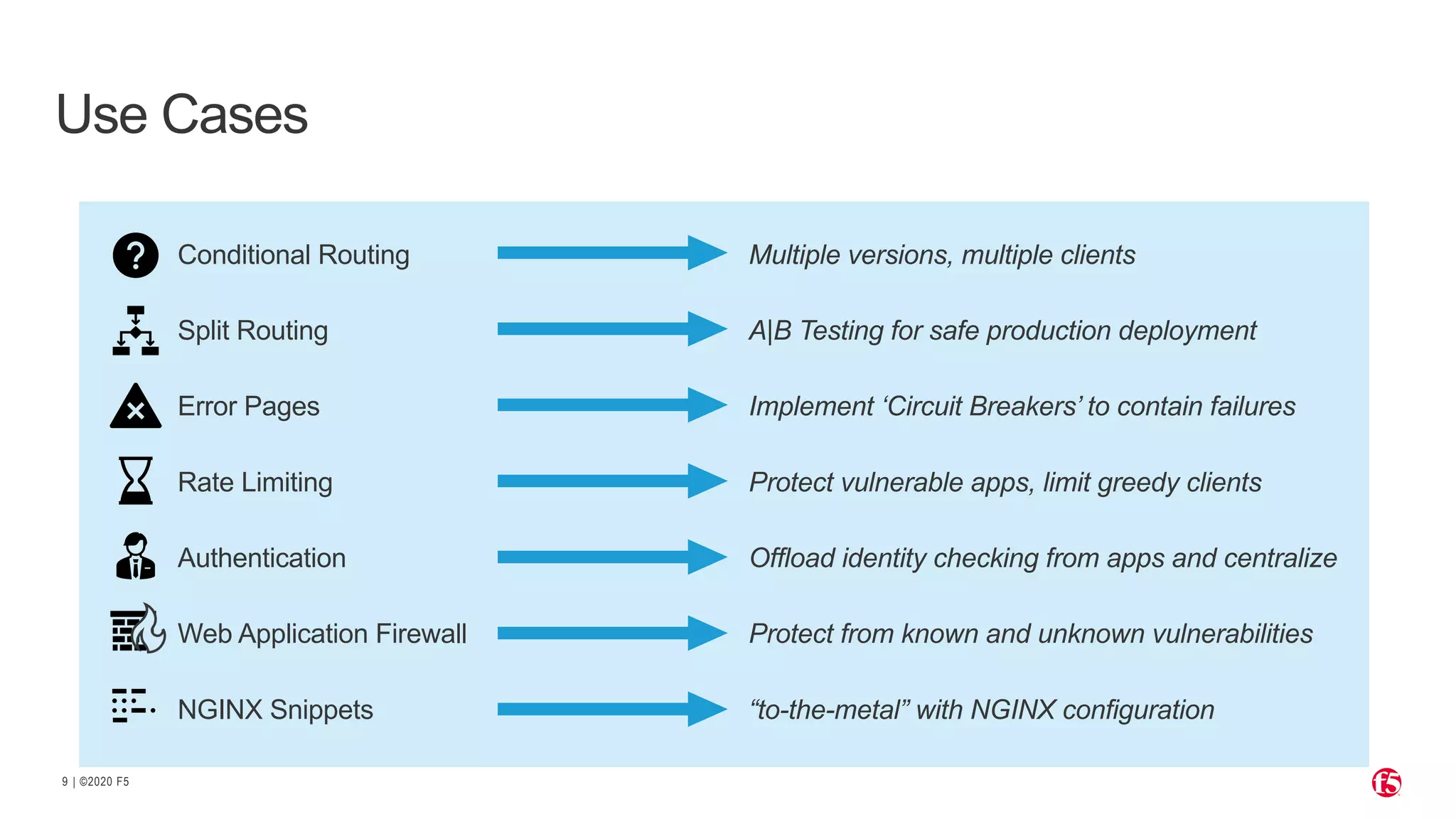
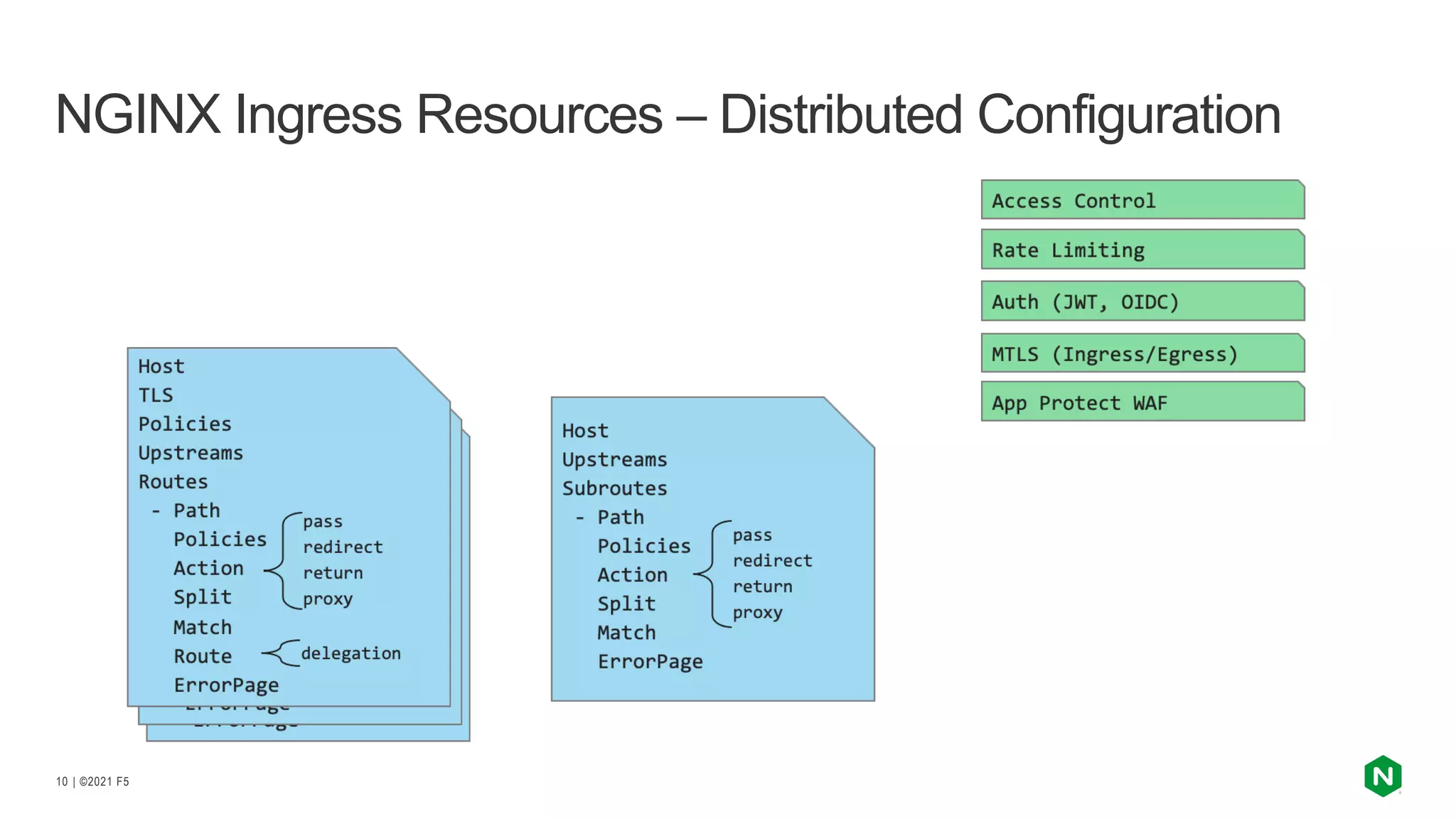
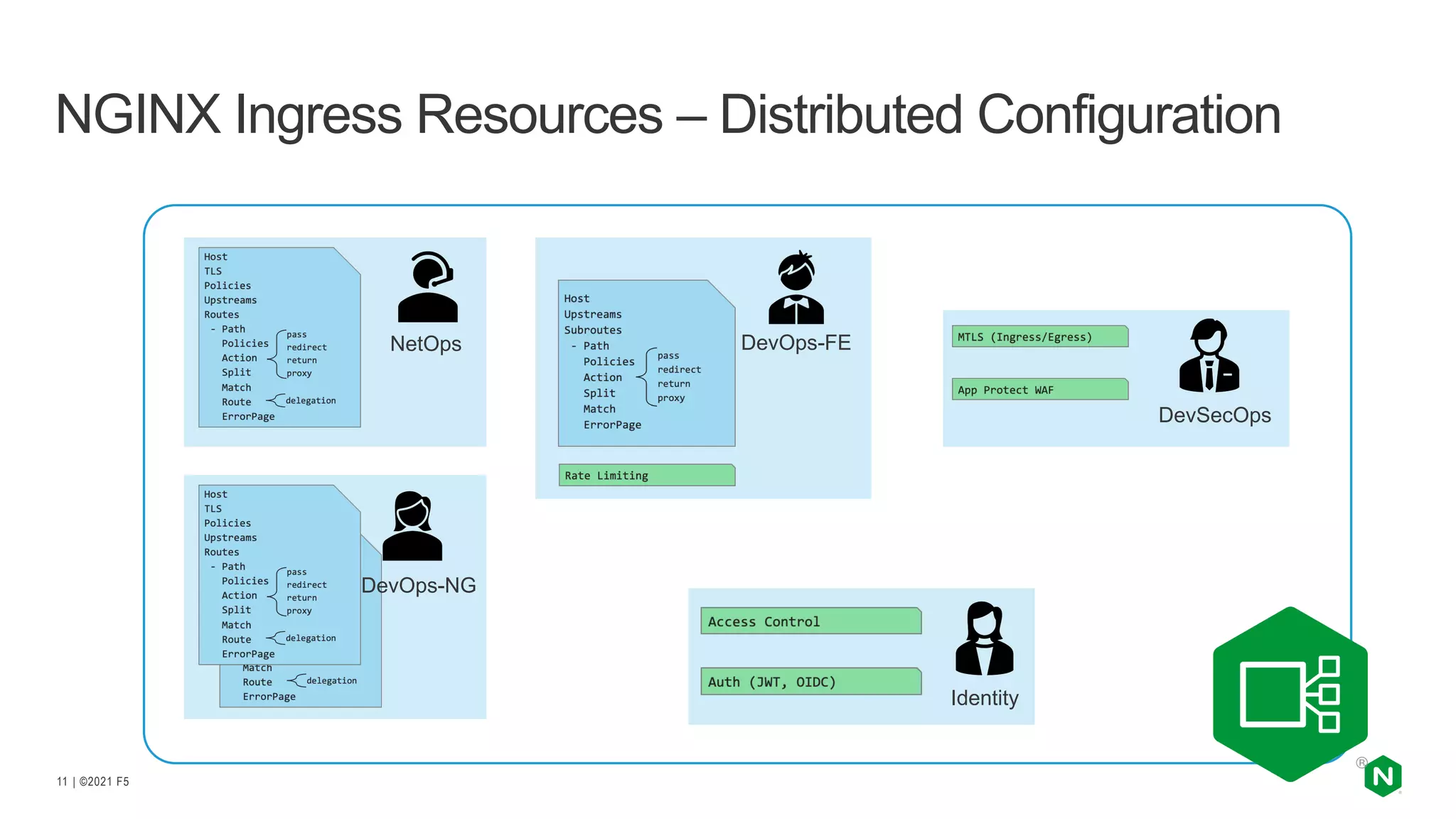
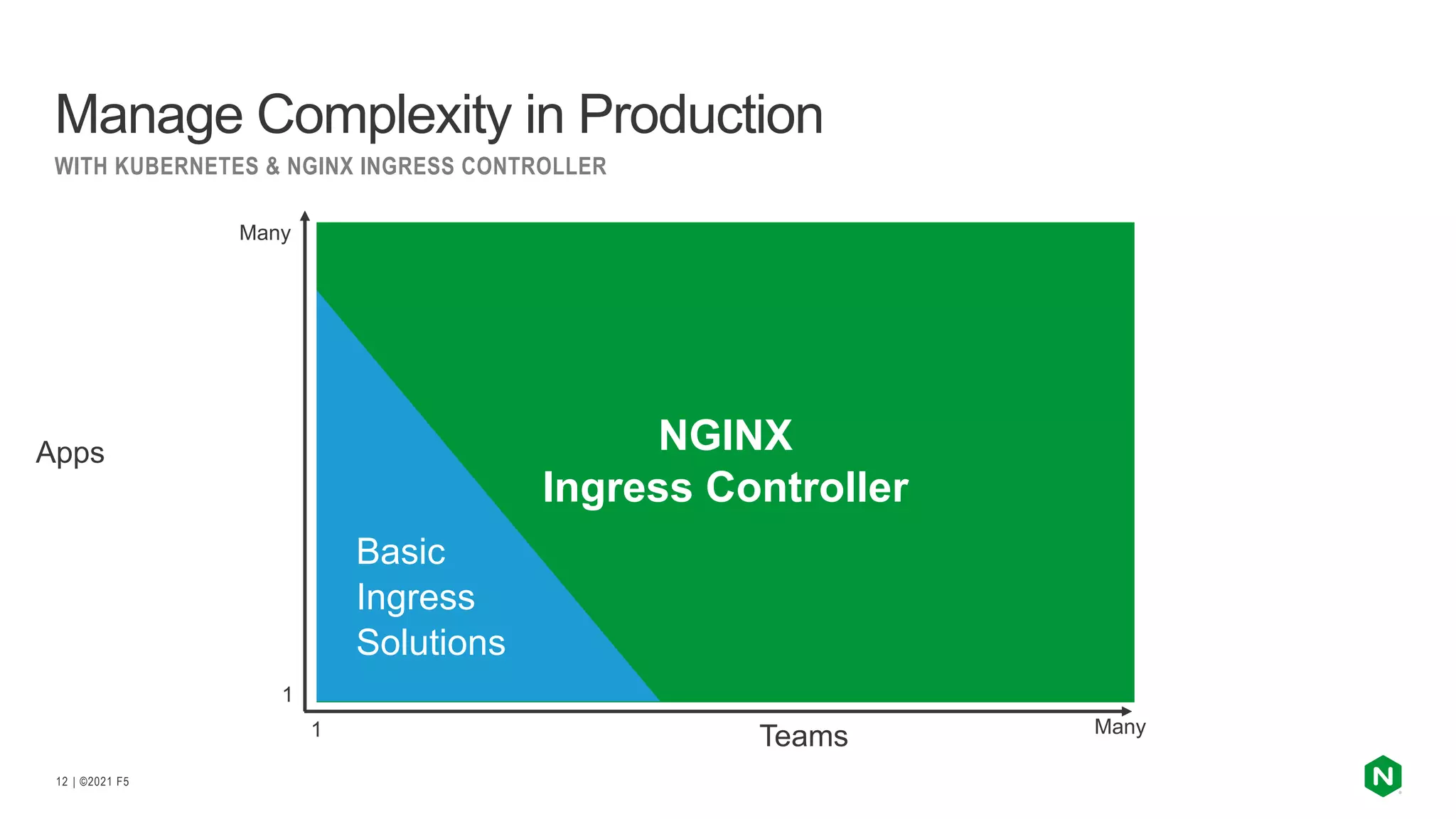
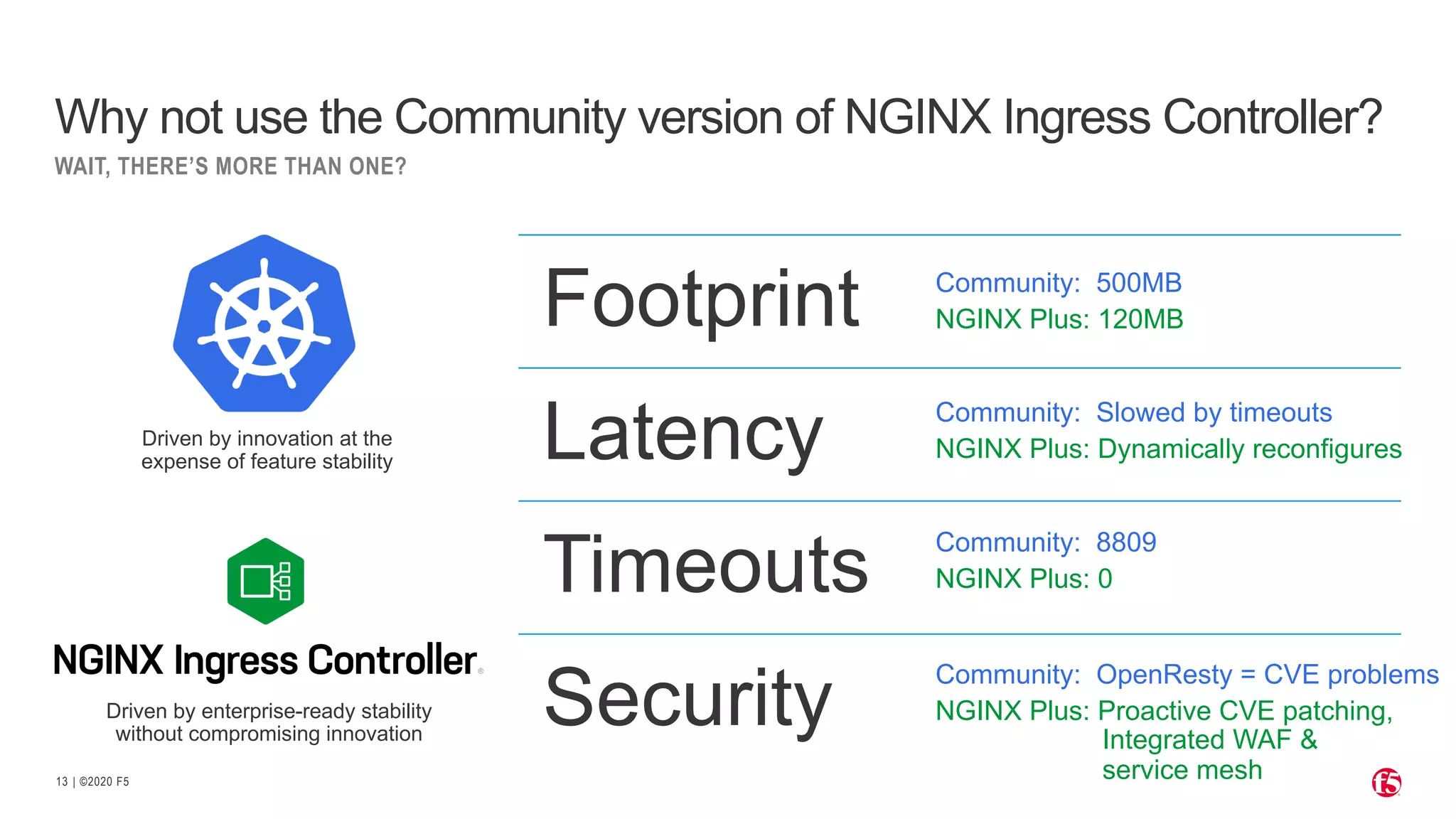
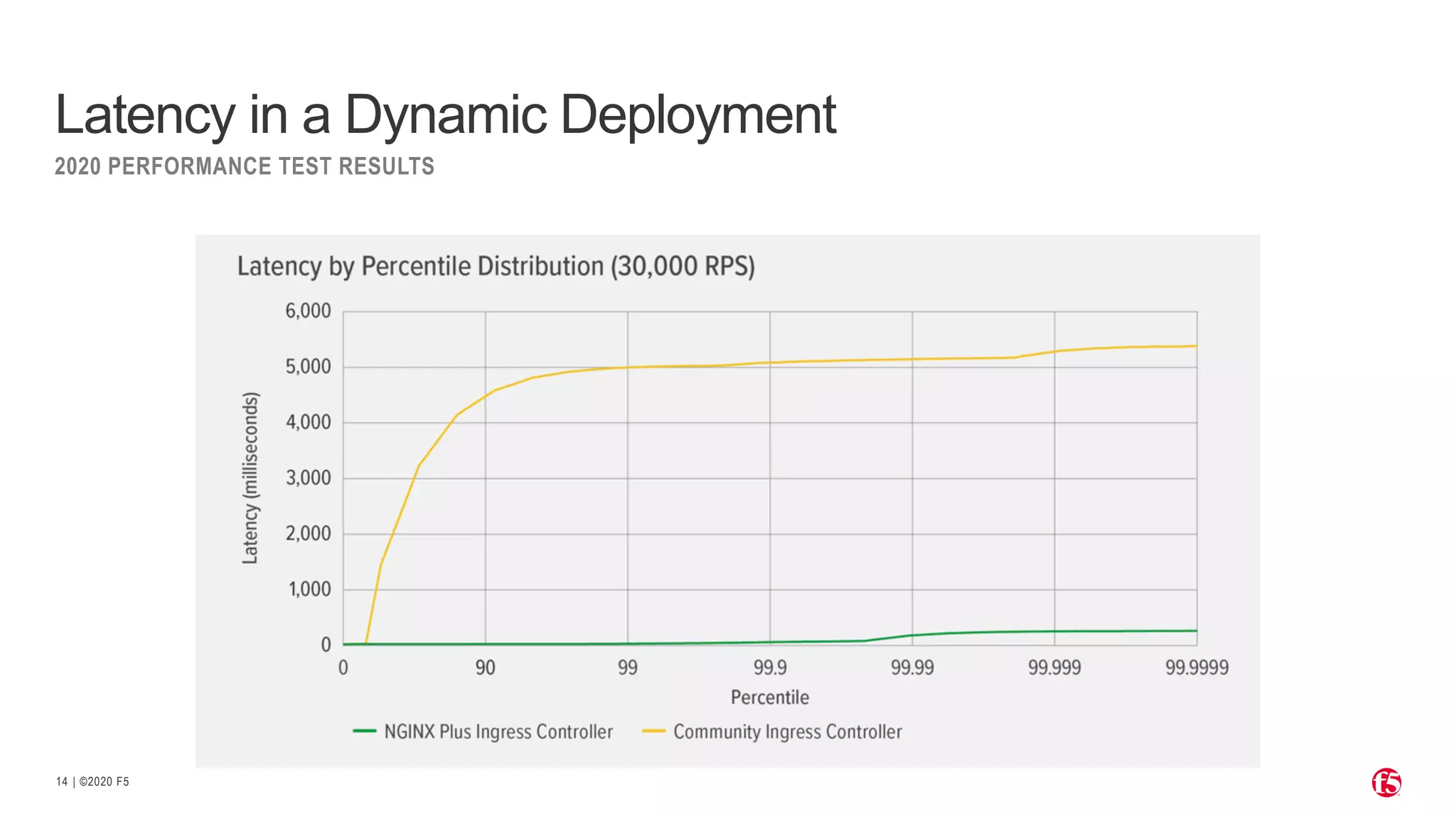
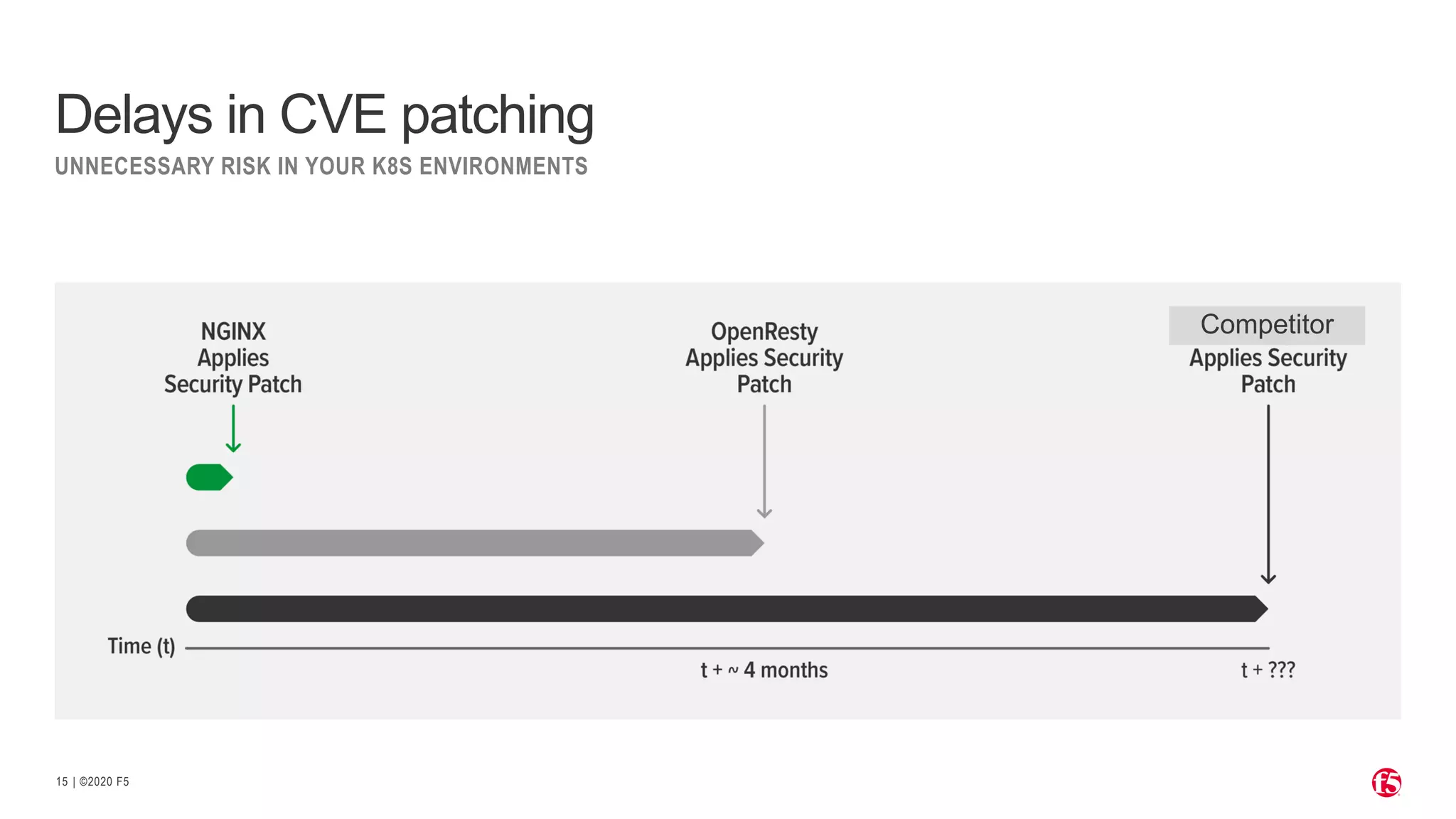
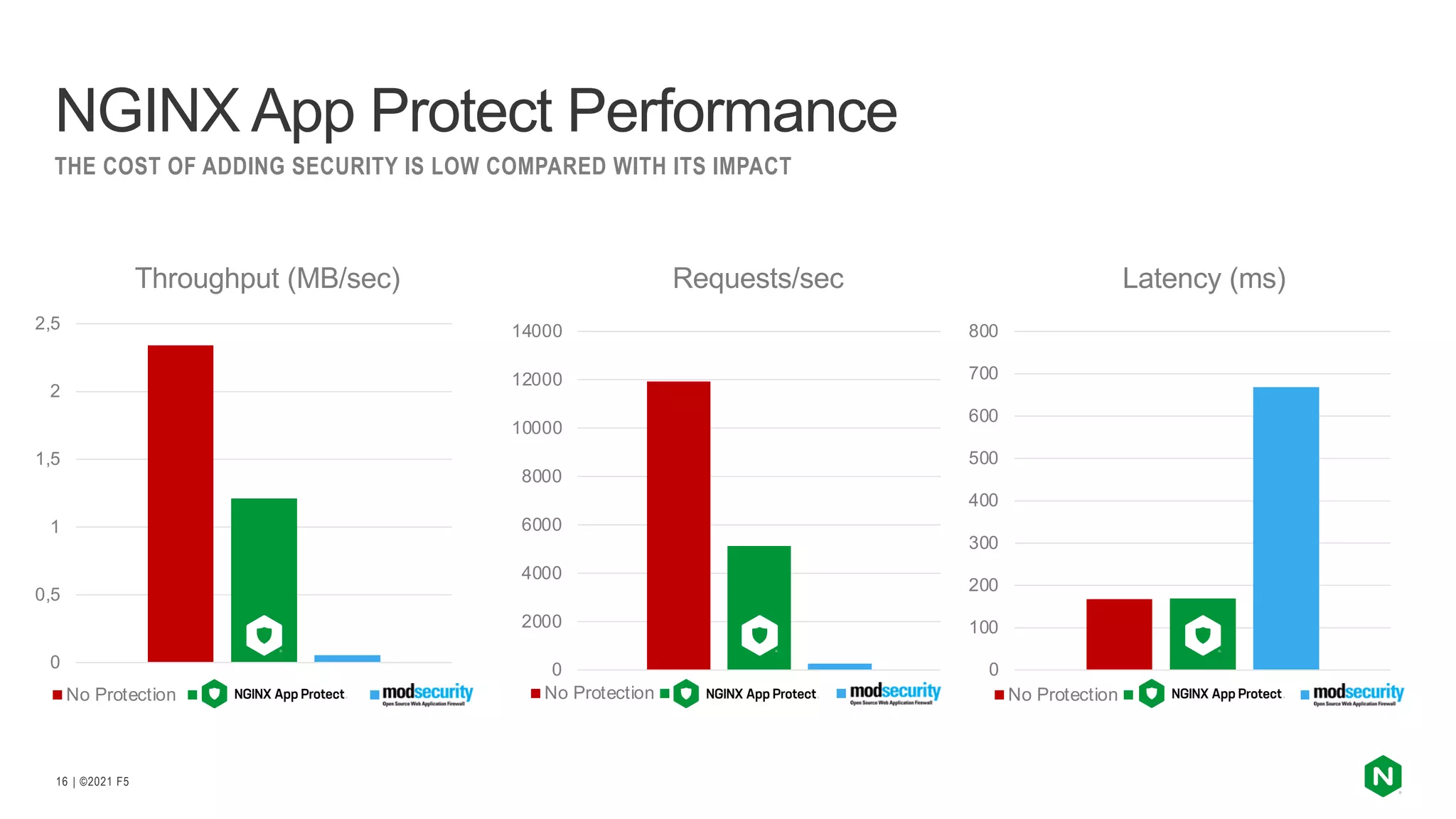
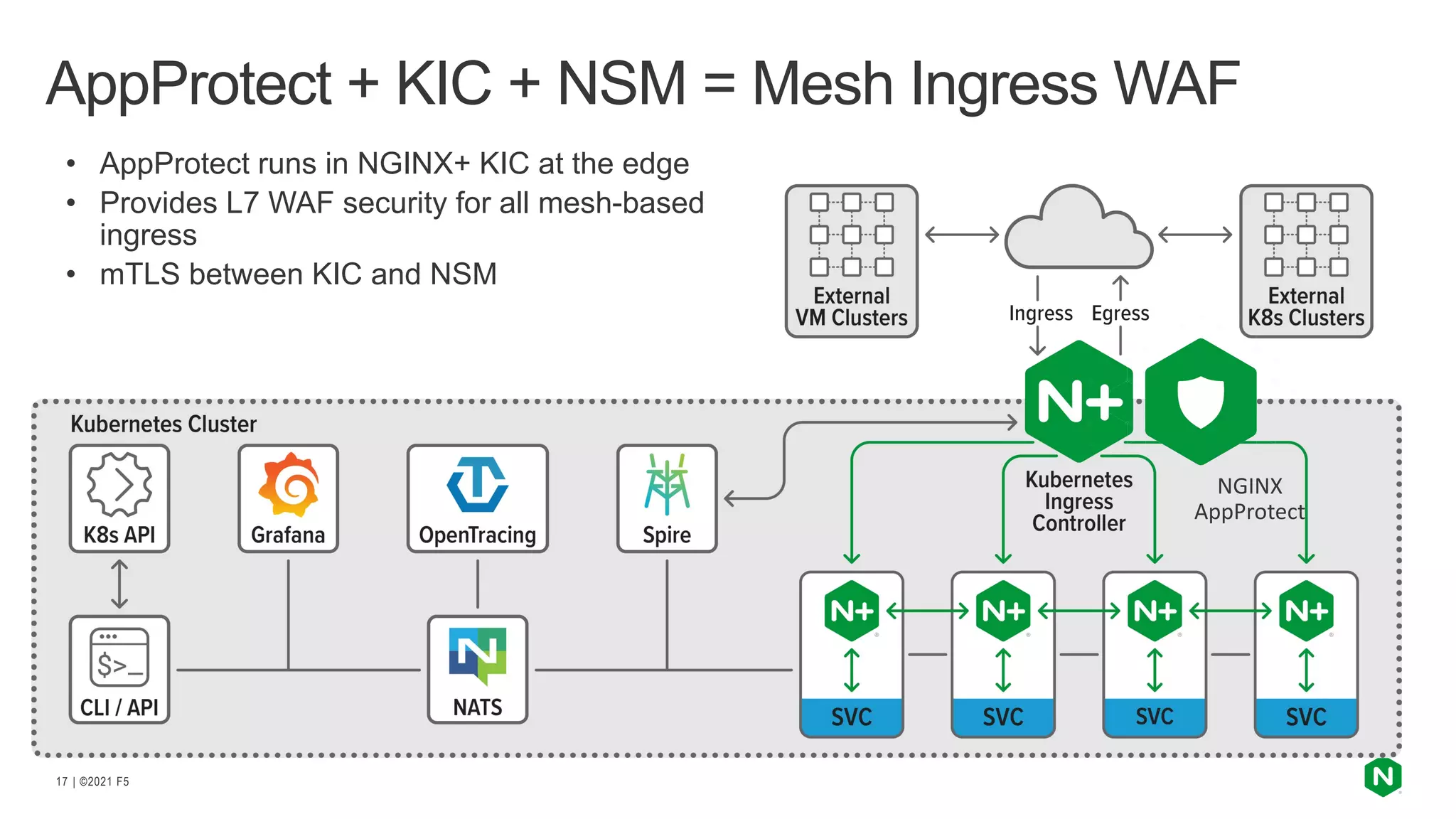
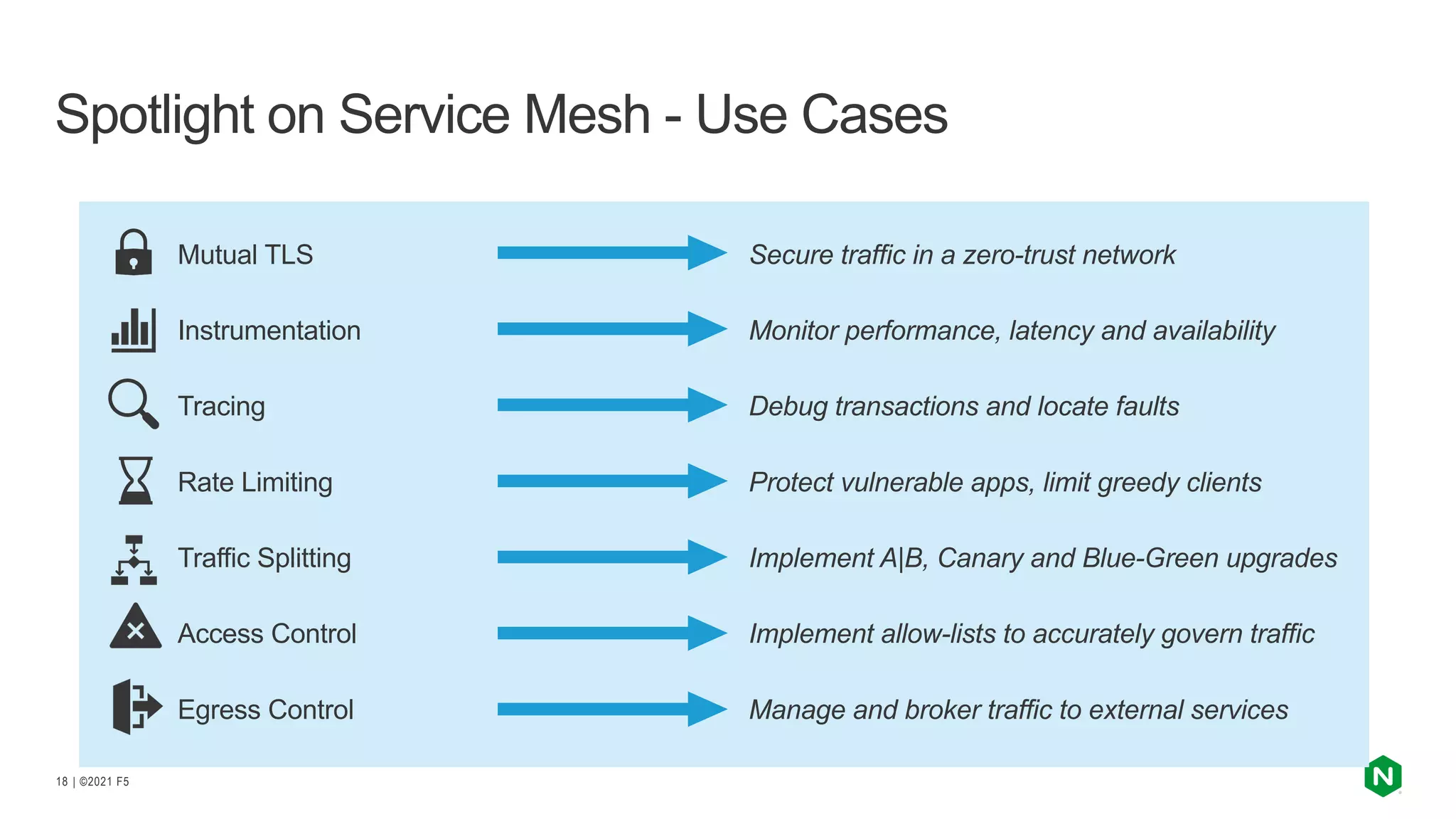
The document discusses the challenges and solutions associated with Kubernetes load balancer services, specifically focusing on the NGINX Ingress Controller (KIC) in cloud-native environments. It highlights features, including the need for enhanced security, flexibility, and dynamic configuration, while comparing community versus enterprise versions of NGINX for performance and latency. Additionally, it includes use cases for mutual TLS, traffic management, and application protection to illustrate the benefits of using NGINX in Kubernetes environments.