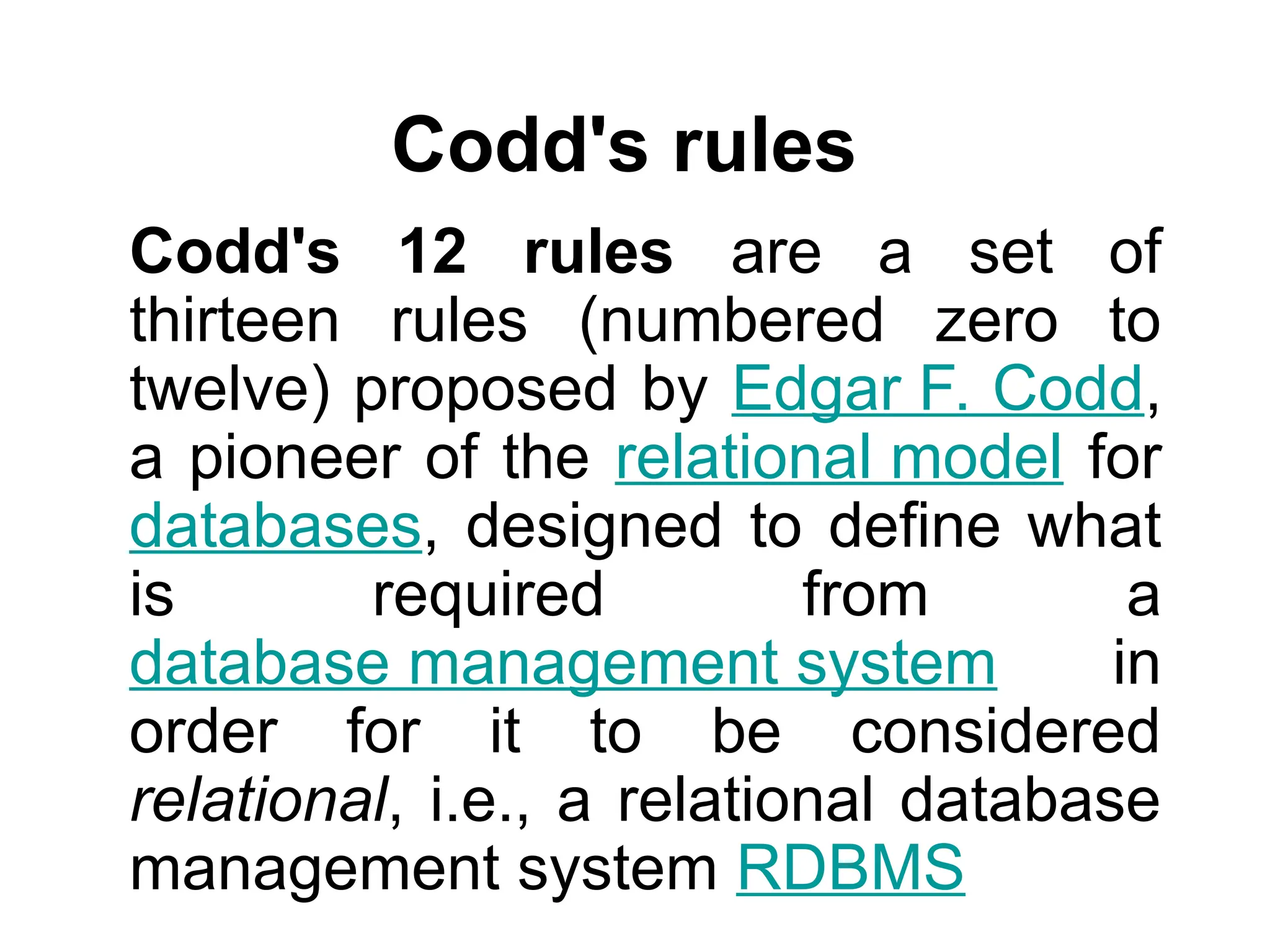
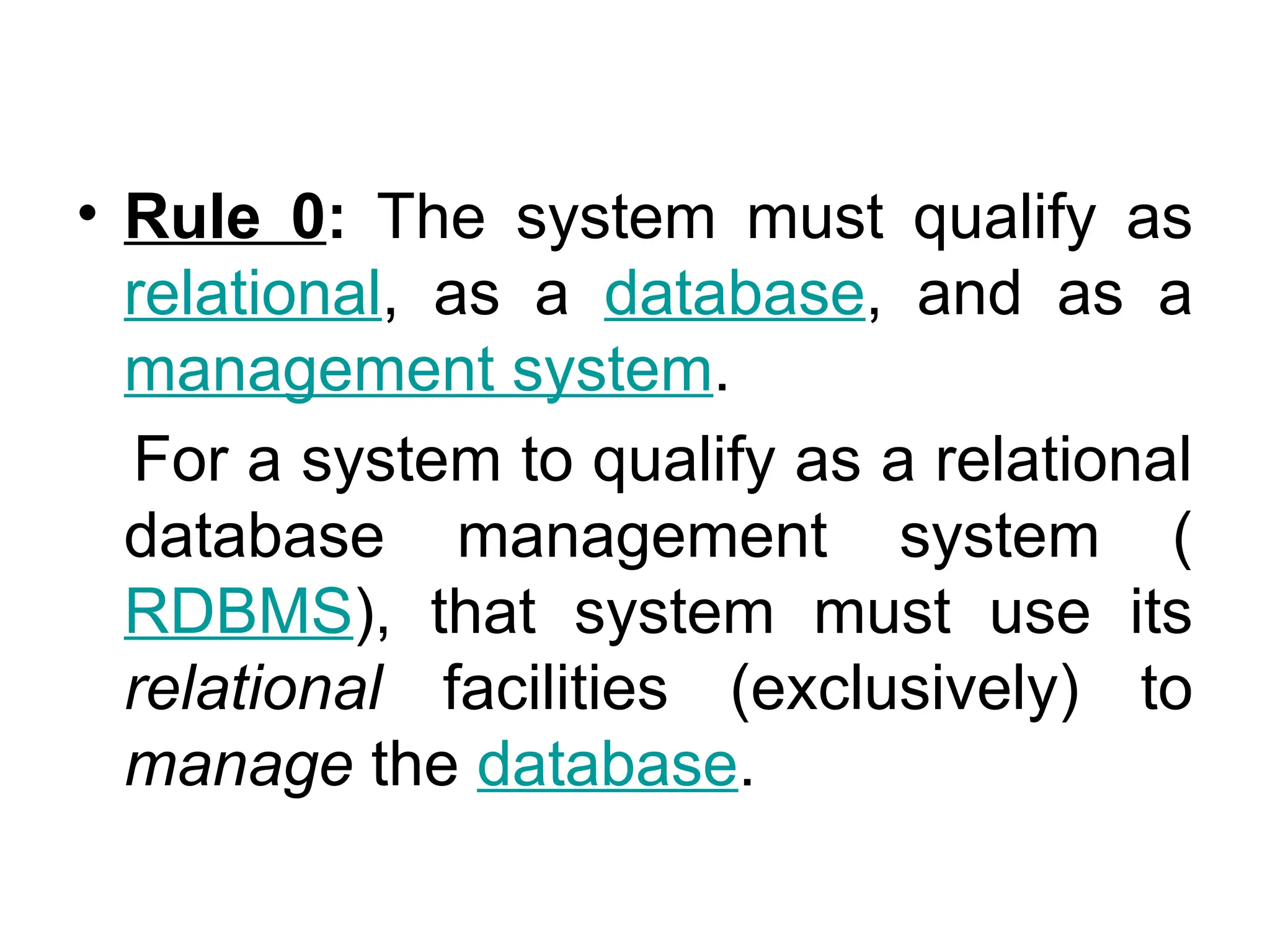
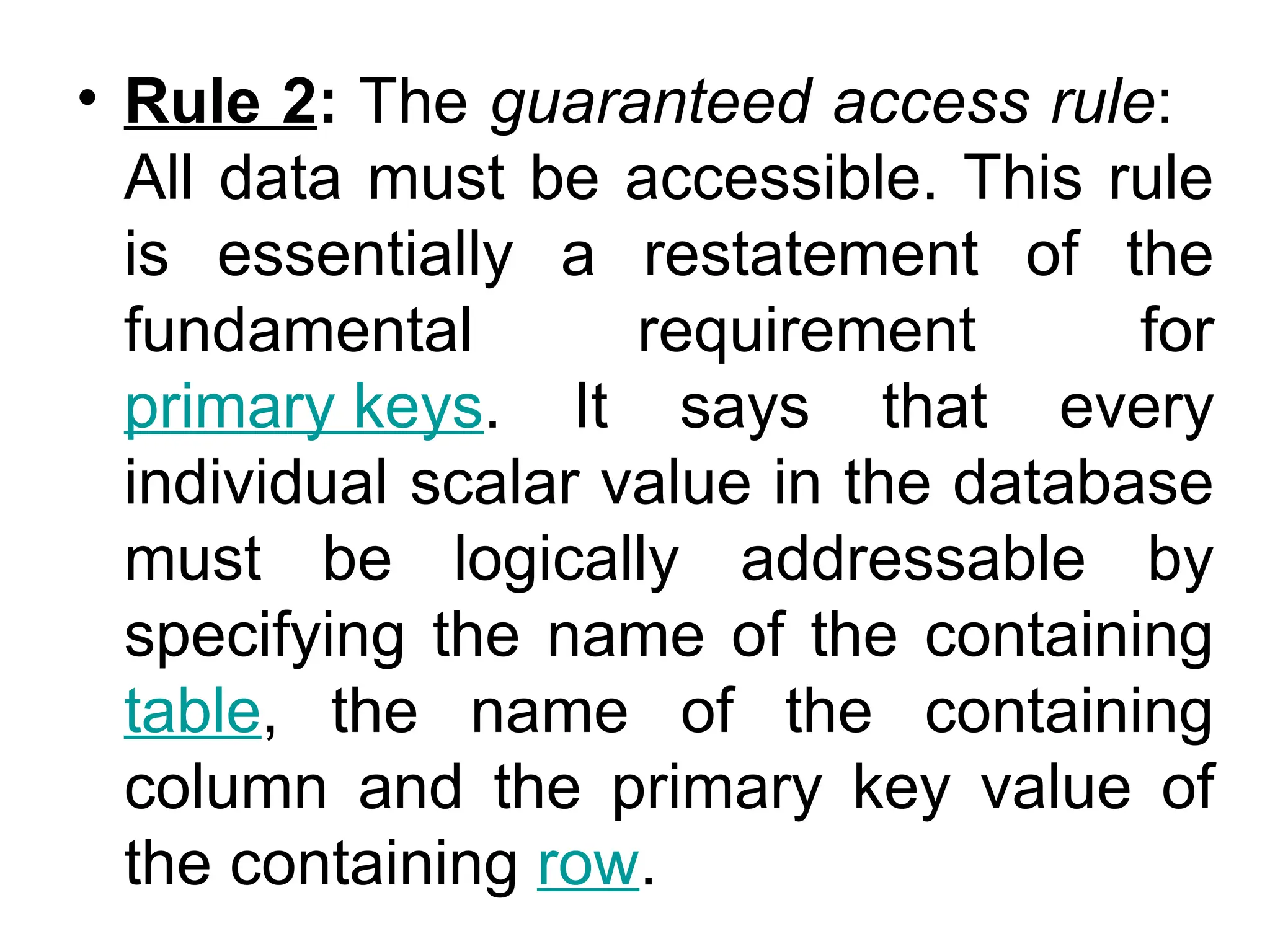
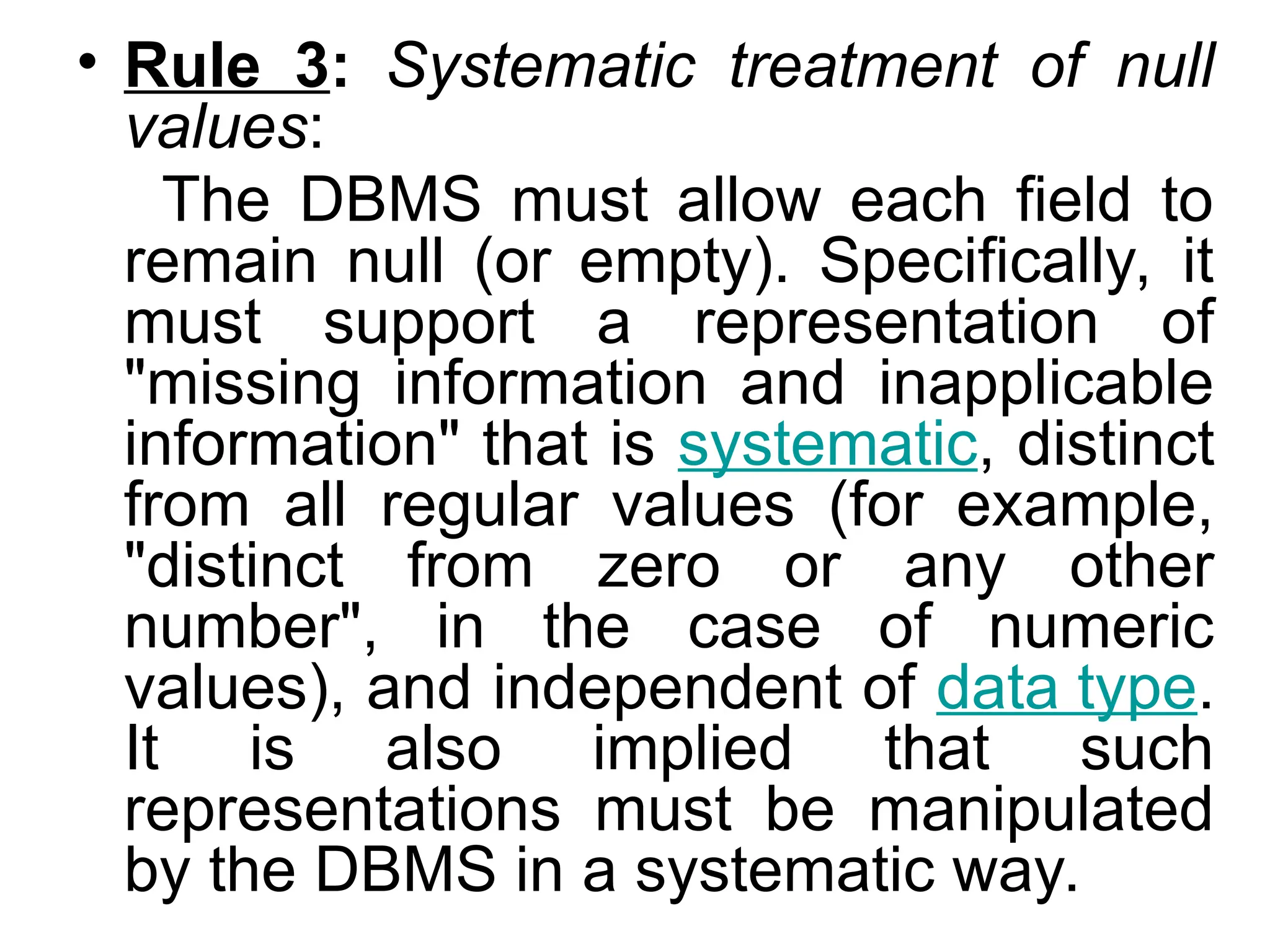
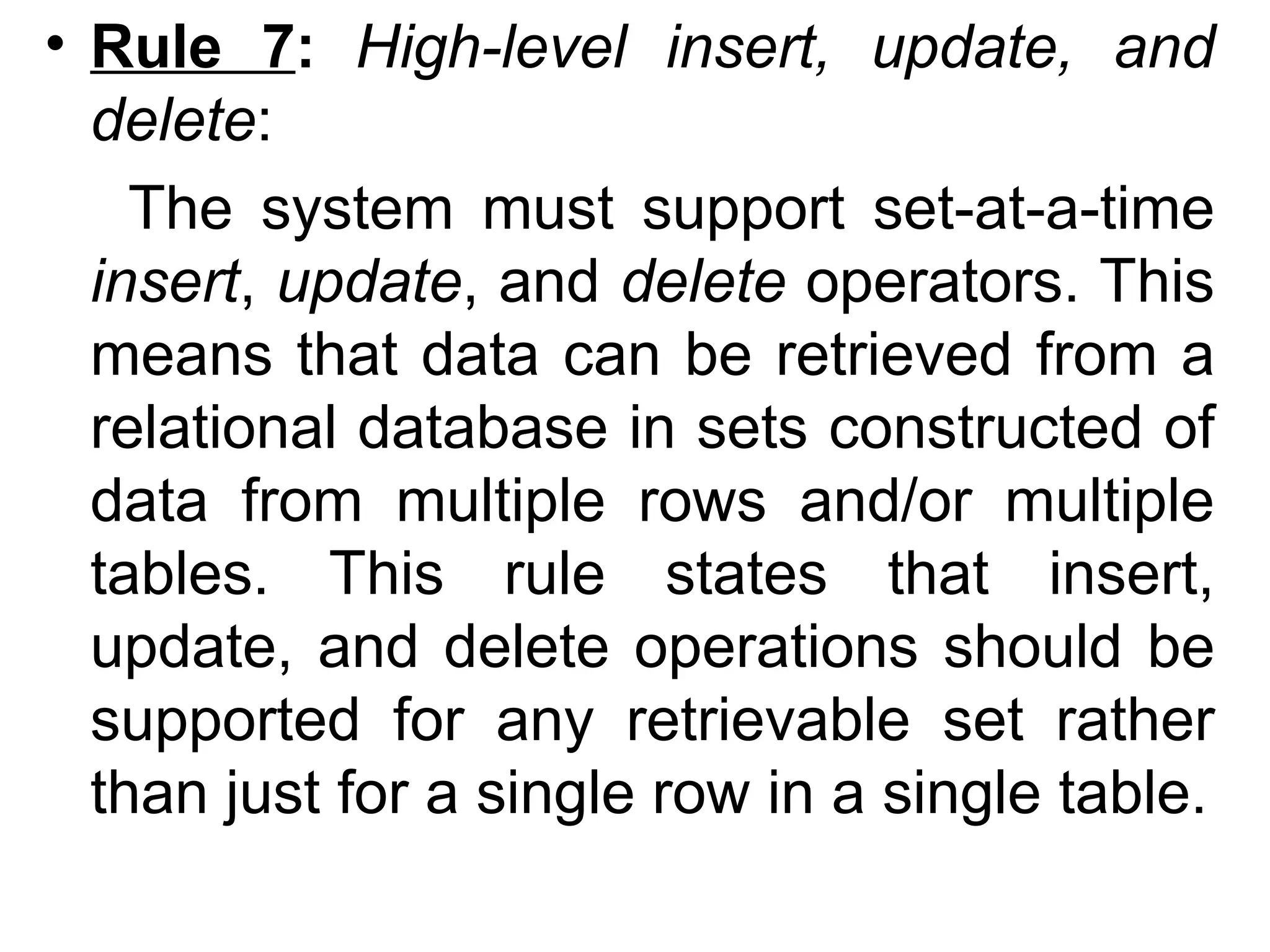
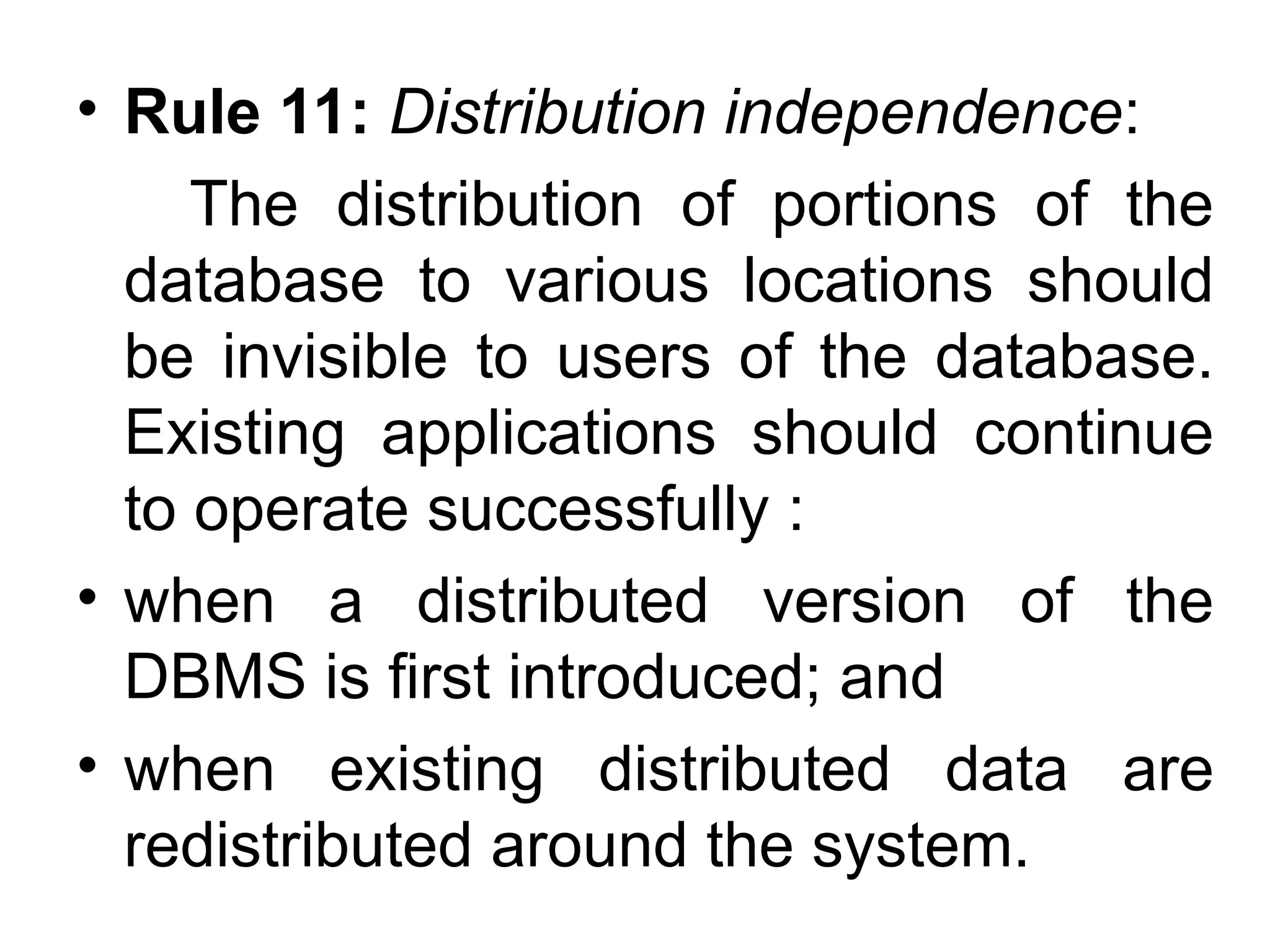
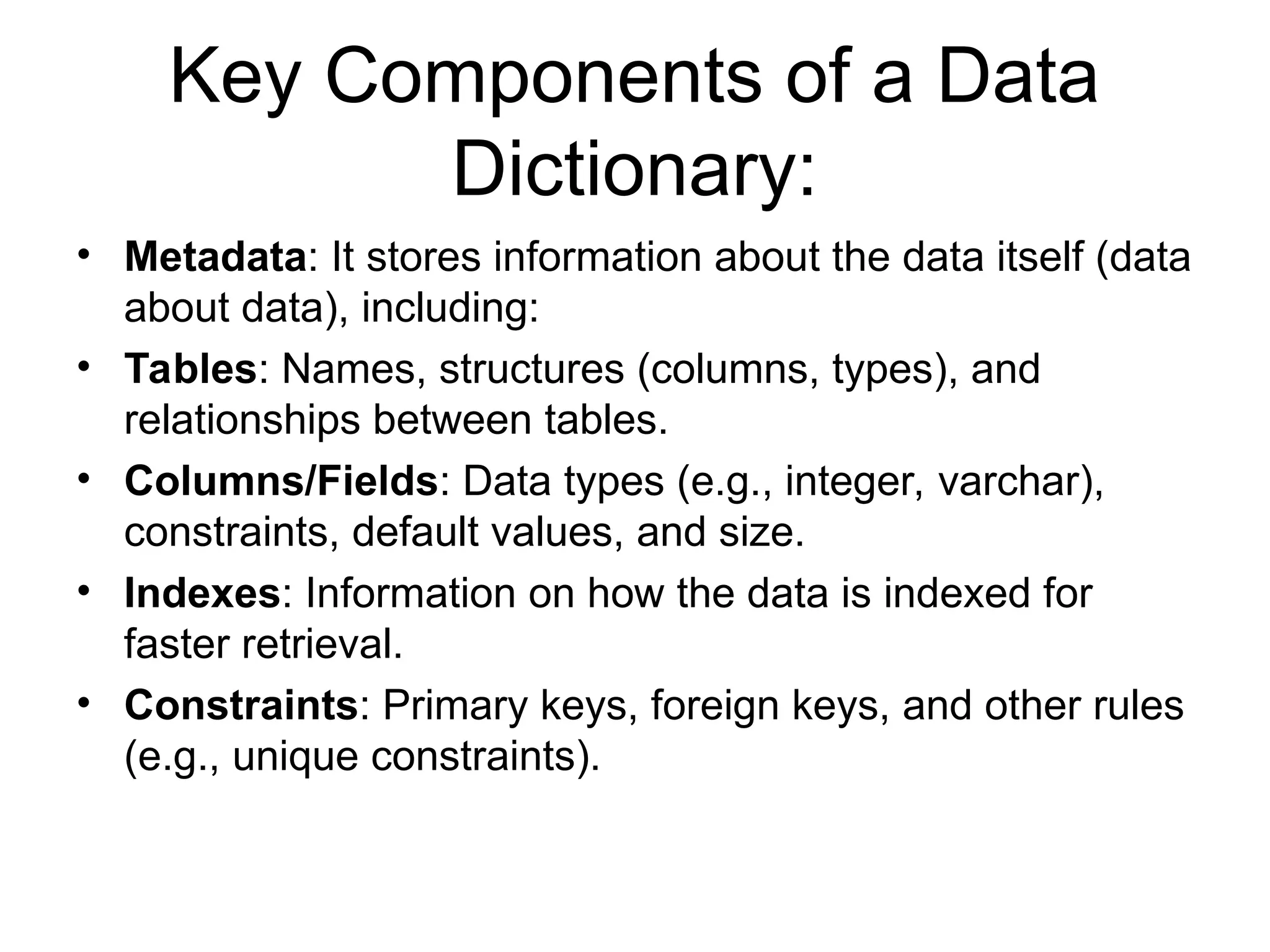
Codd's 12 rules define the essential requirements for a relational database management system (RDBMS), including data representation, access, and independence from physical and logical changes. The rules emphasize proper handling of null values, support for an online catalog, mechanisms for data integrity, and the enforcement of relational constraints even with low-level access. Additionally, a data dictionary serves as a central repository of metadata about the database structure, enabling effective management and understanding of the data.