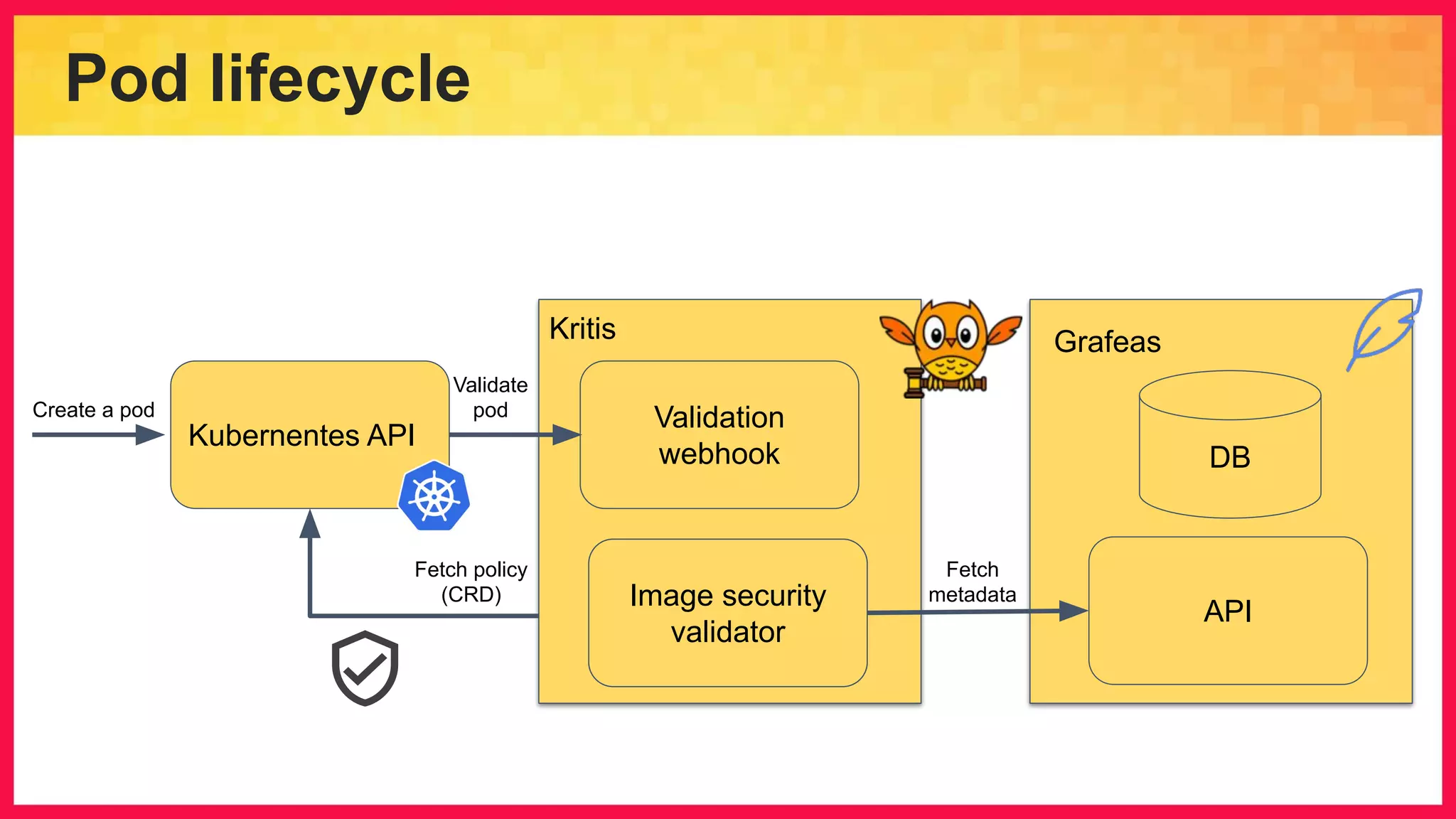
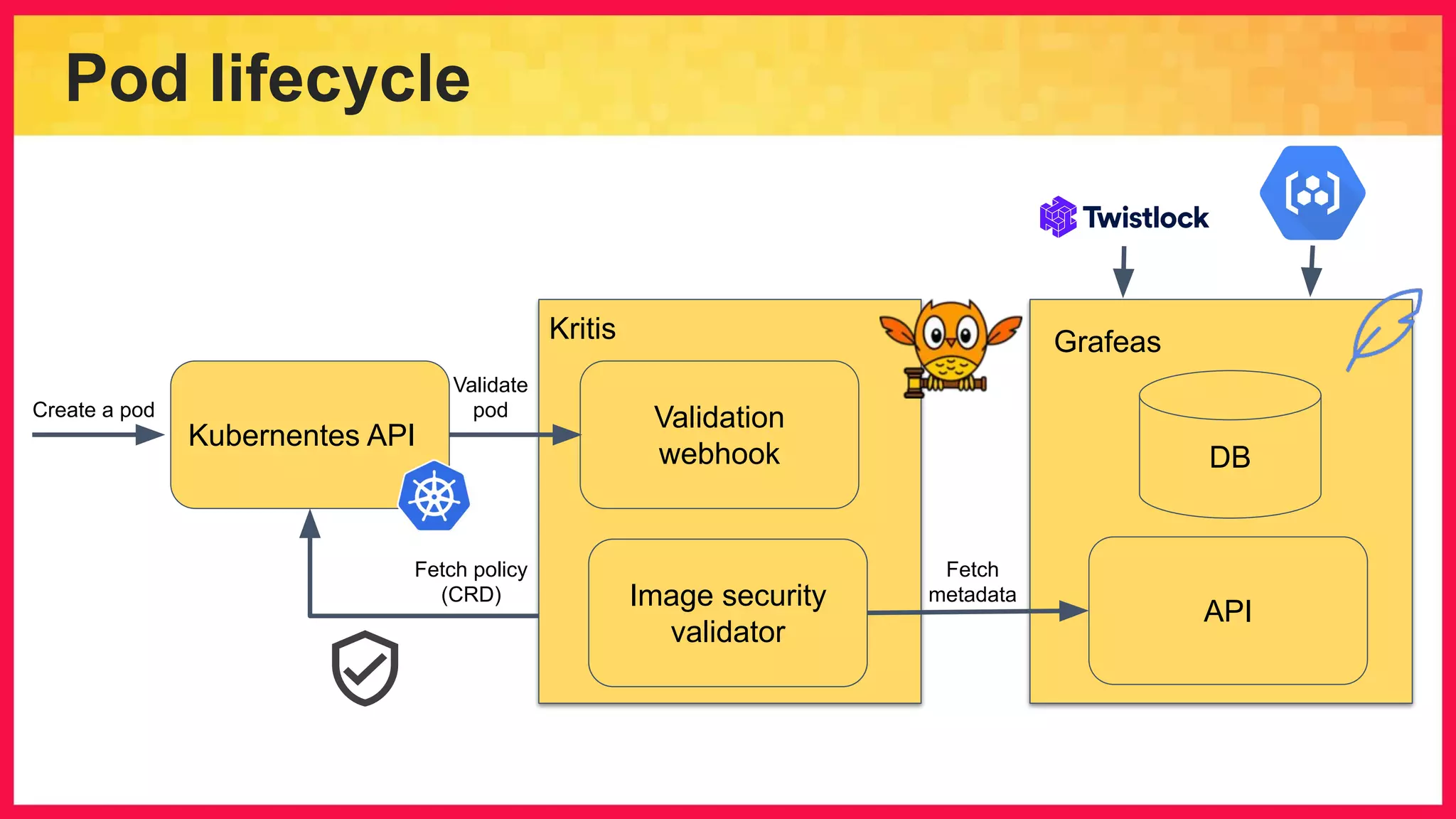
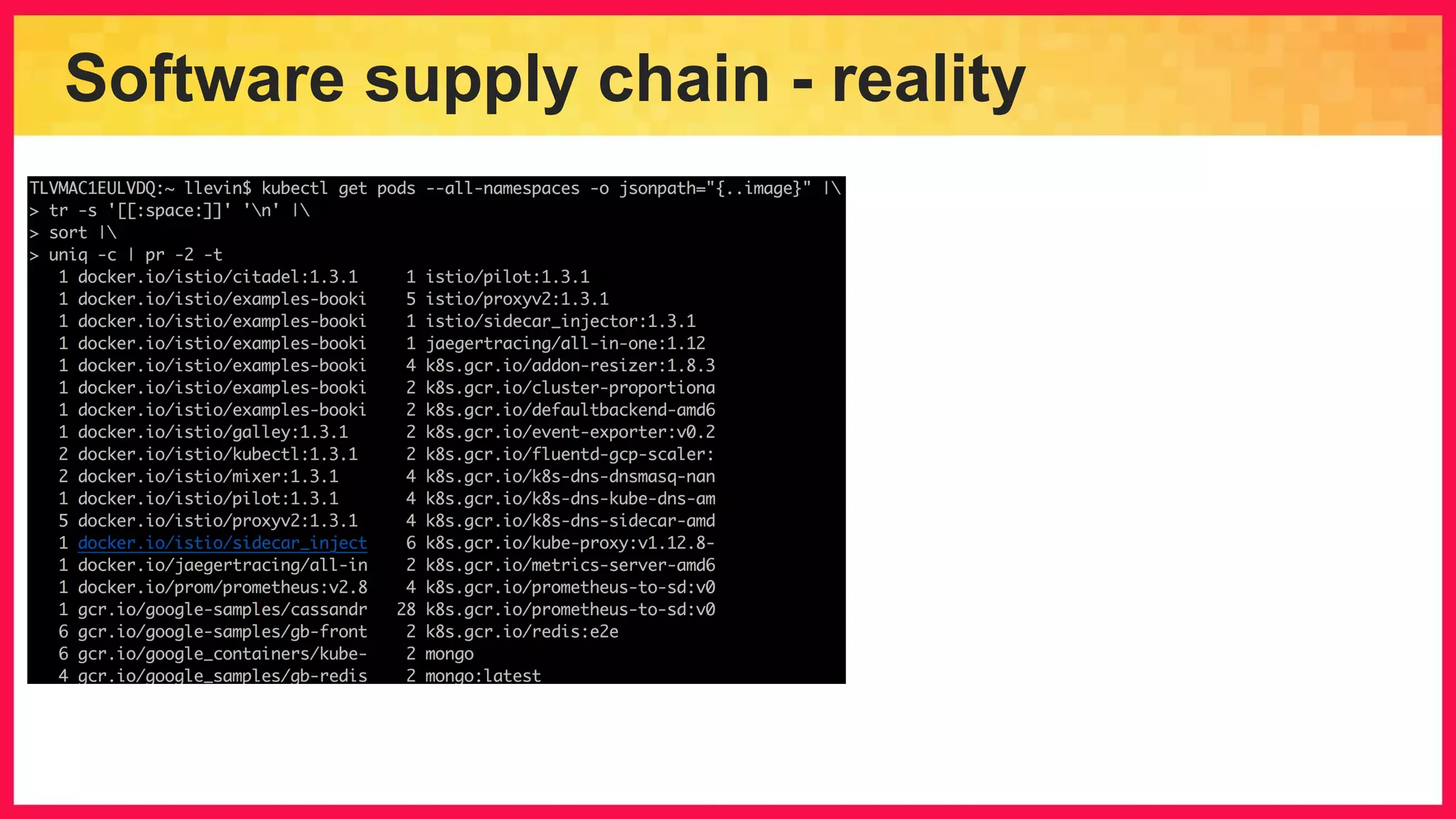
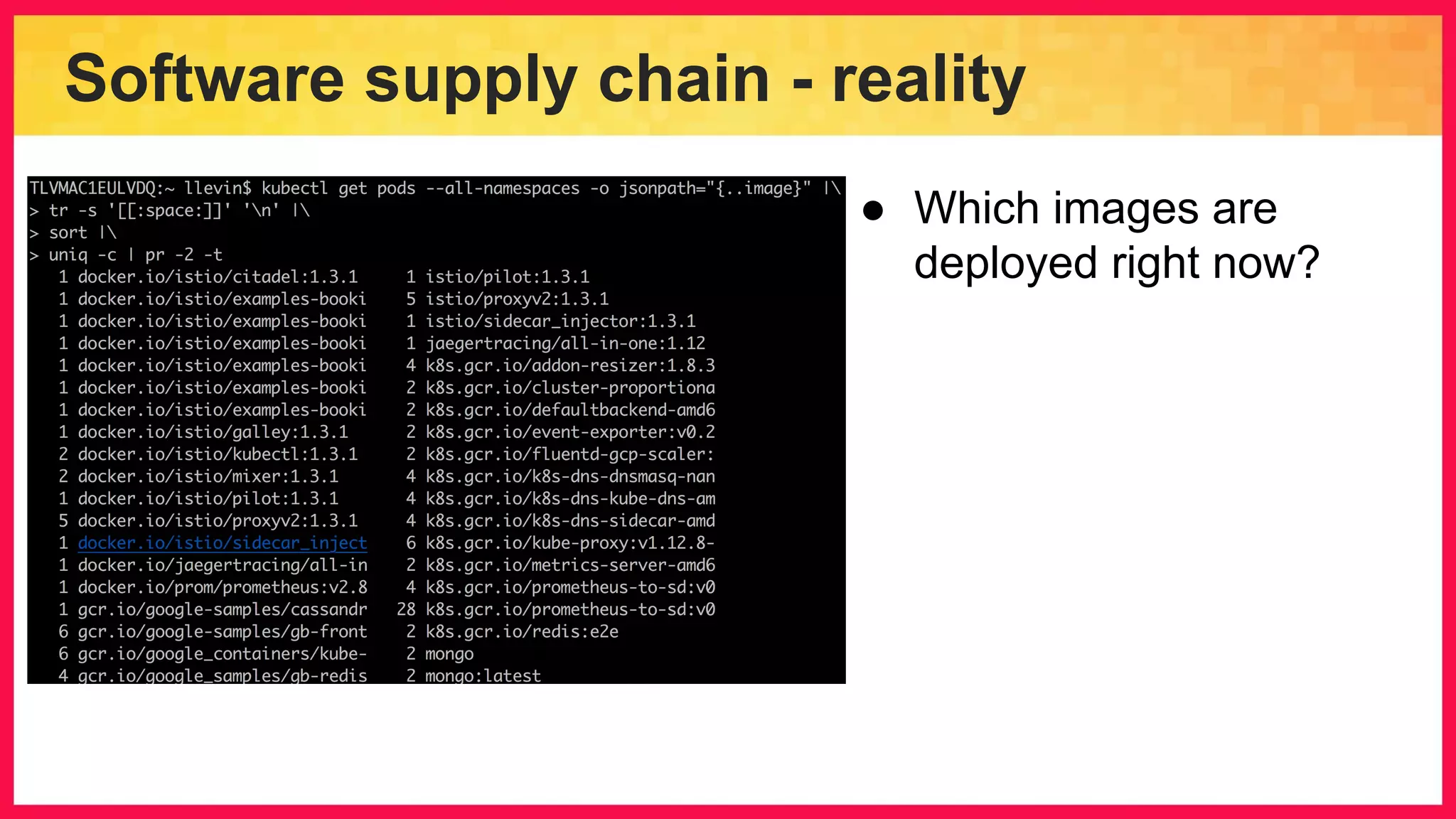
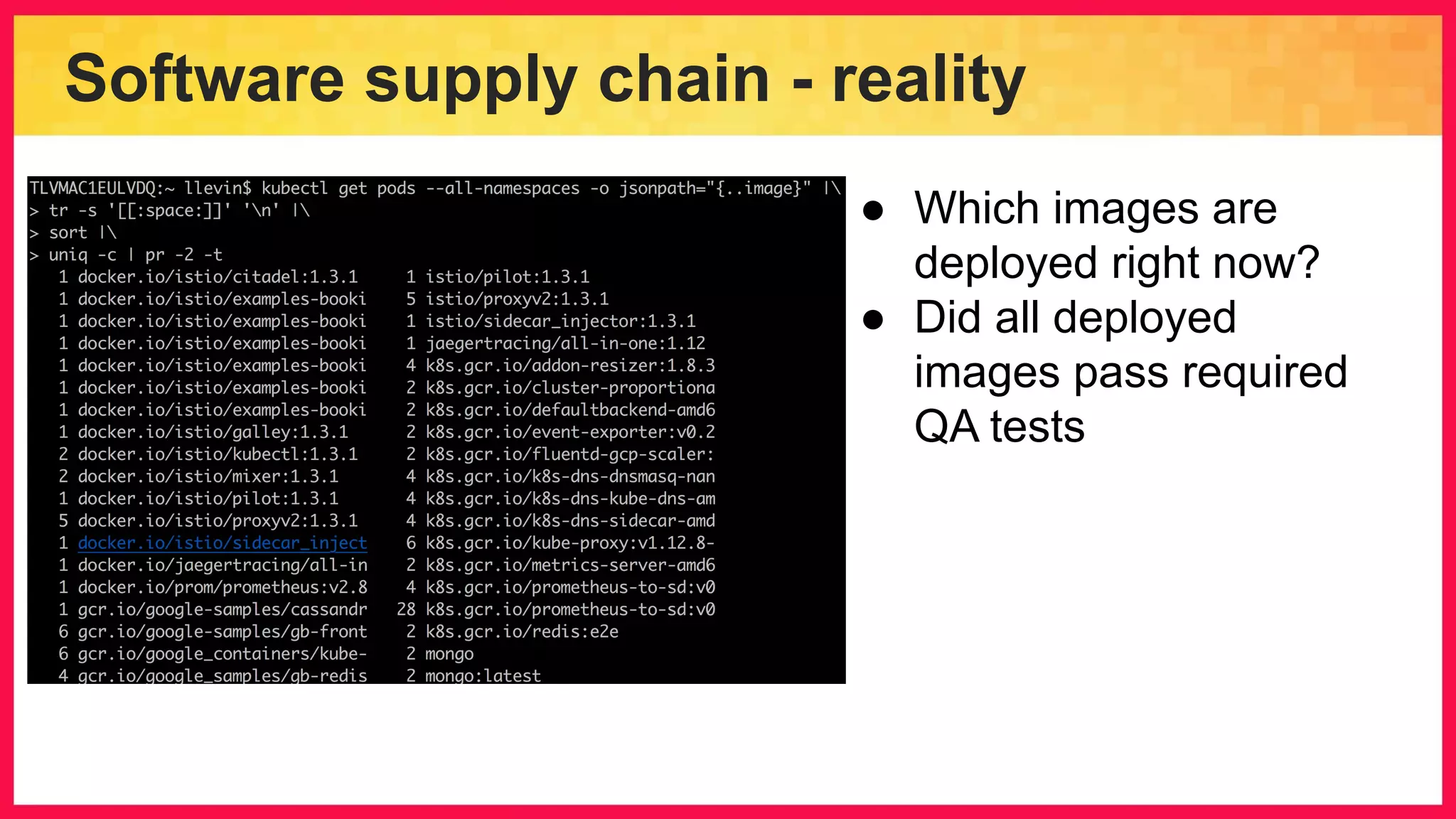
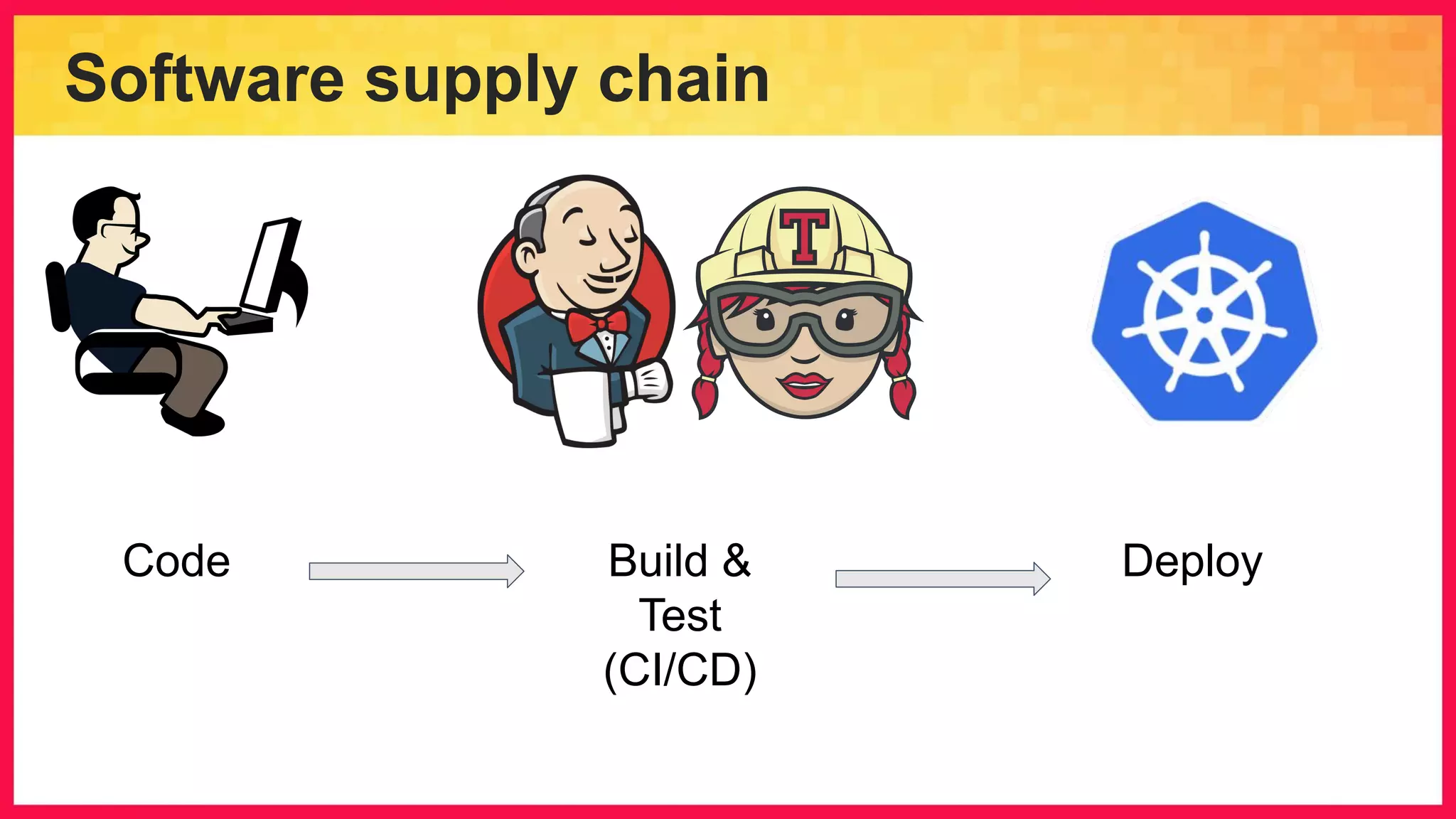
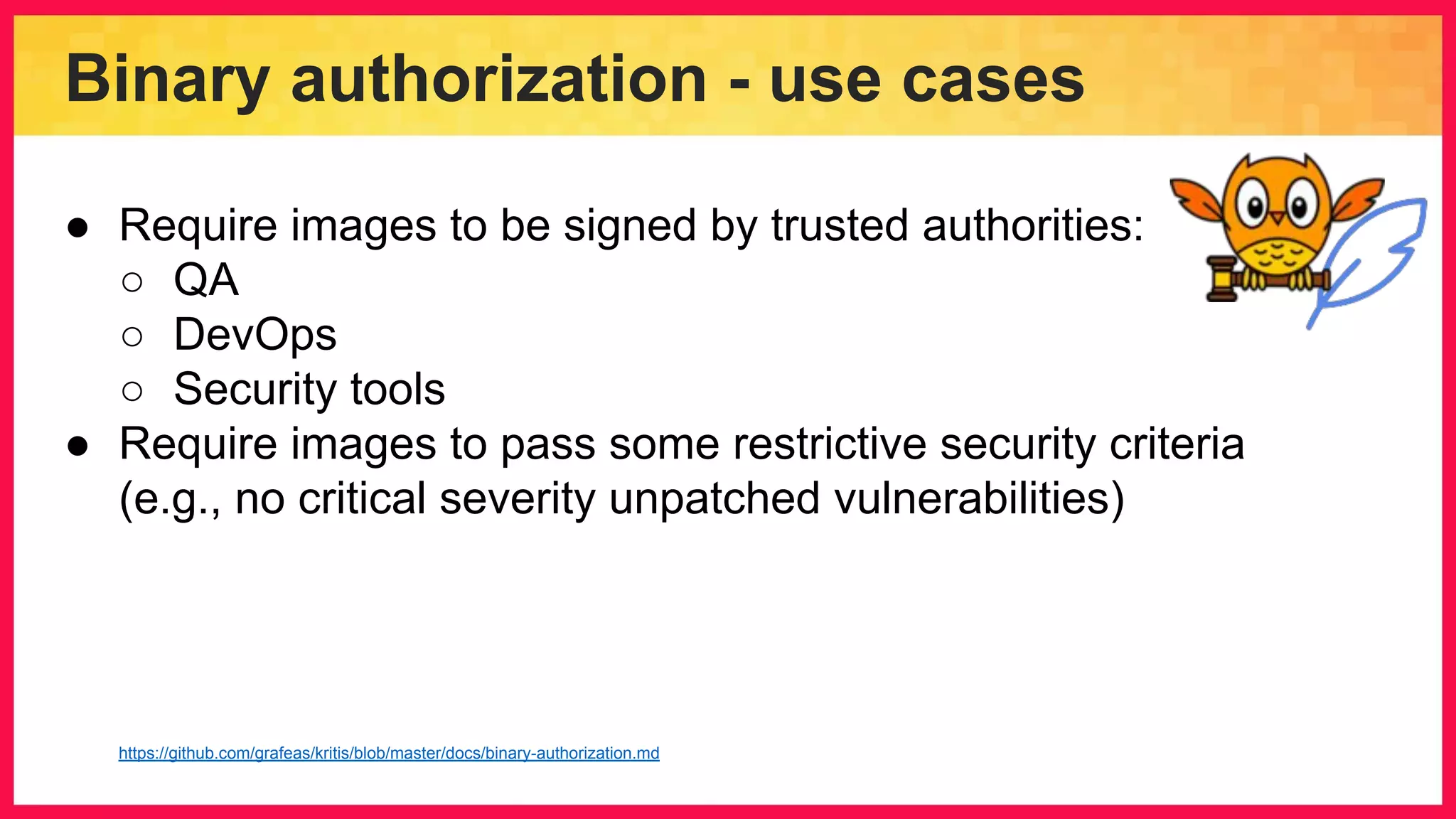
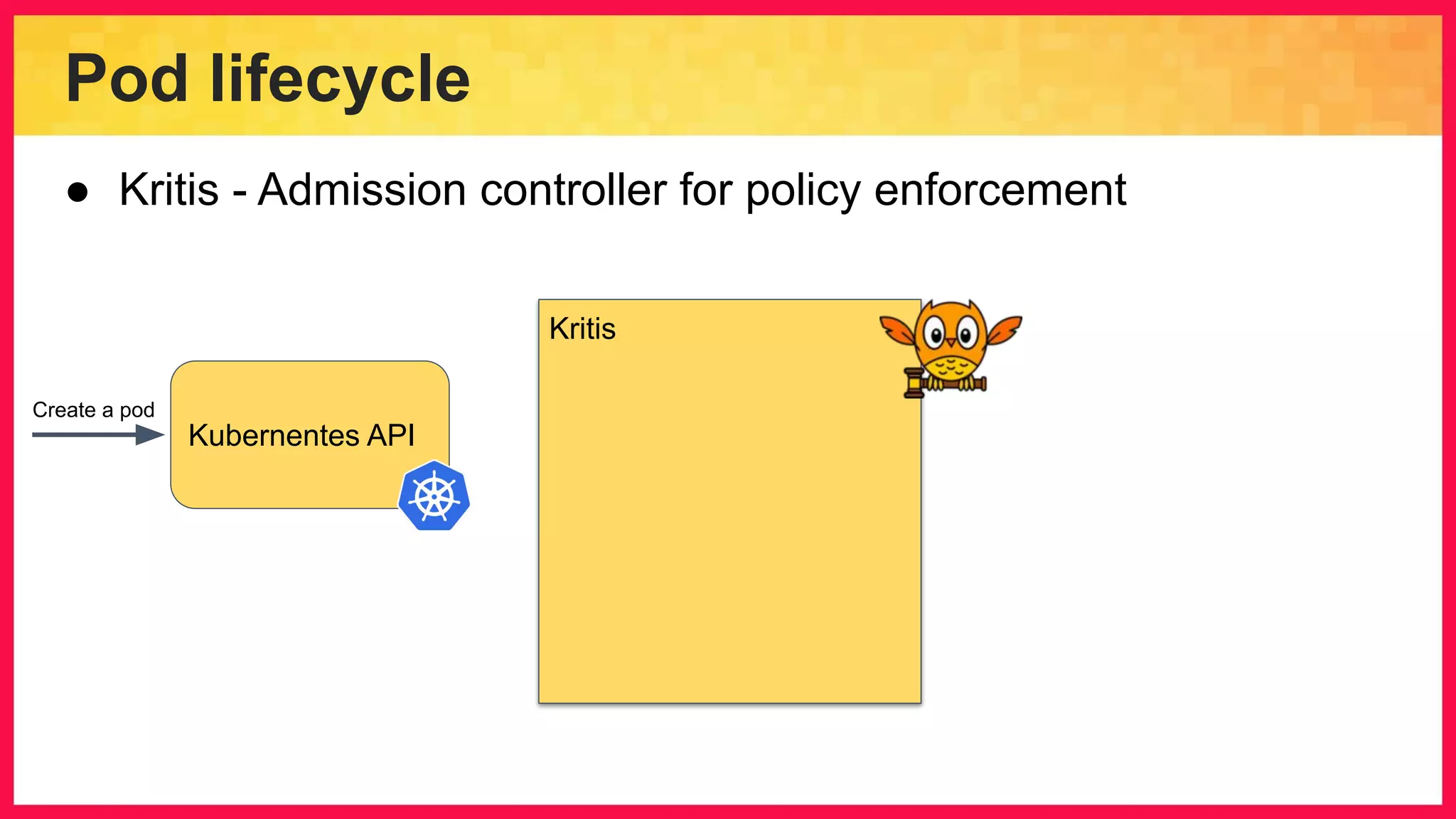
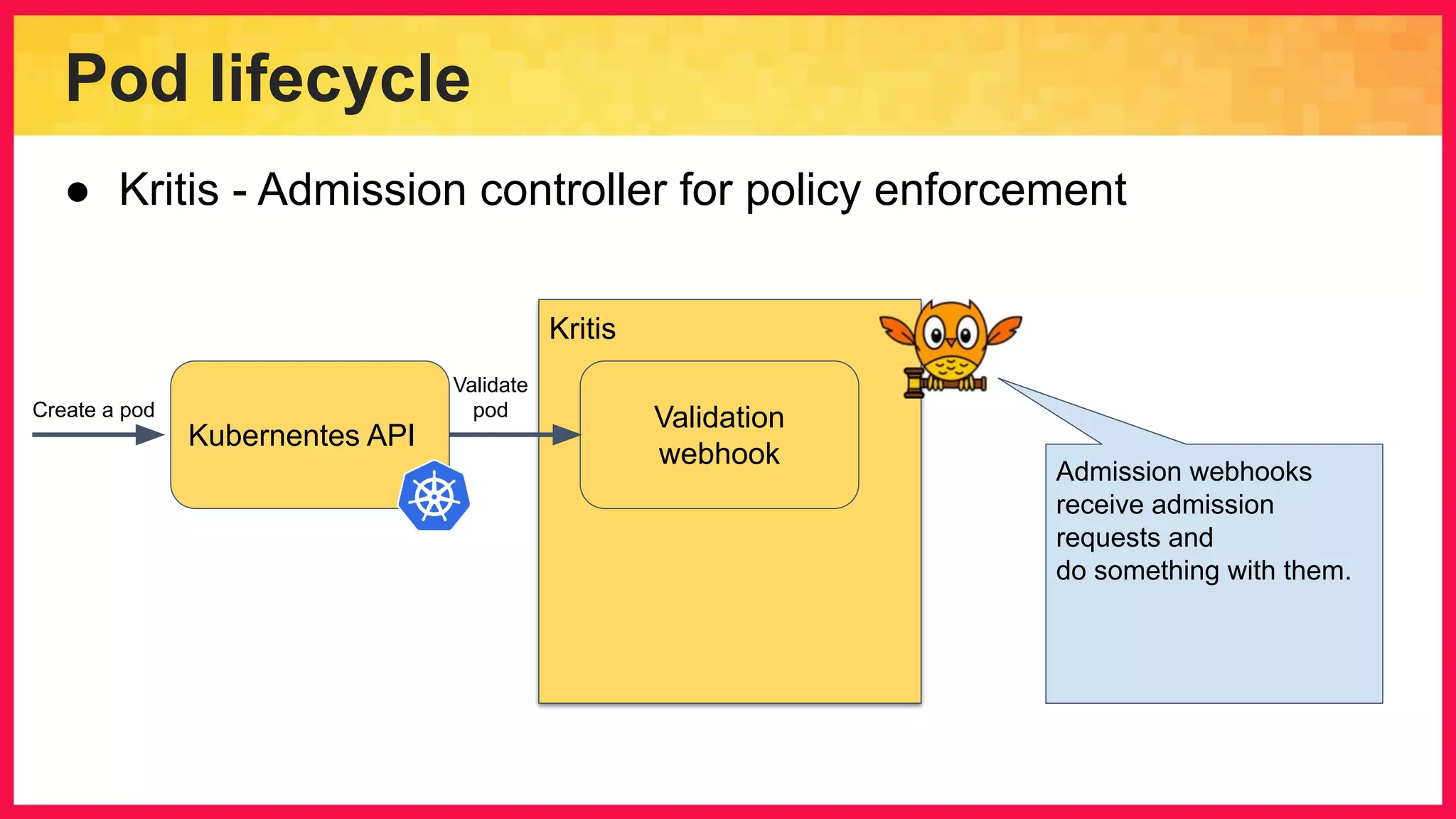
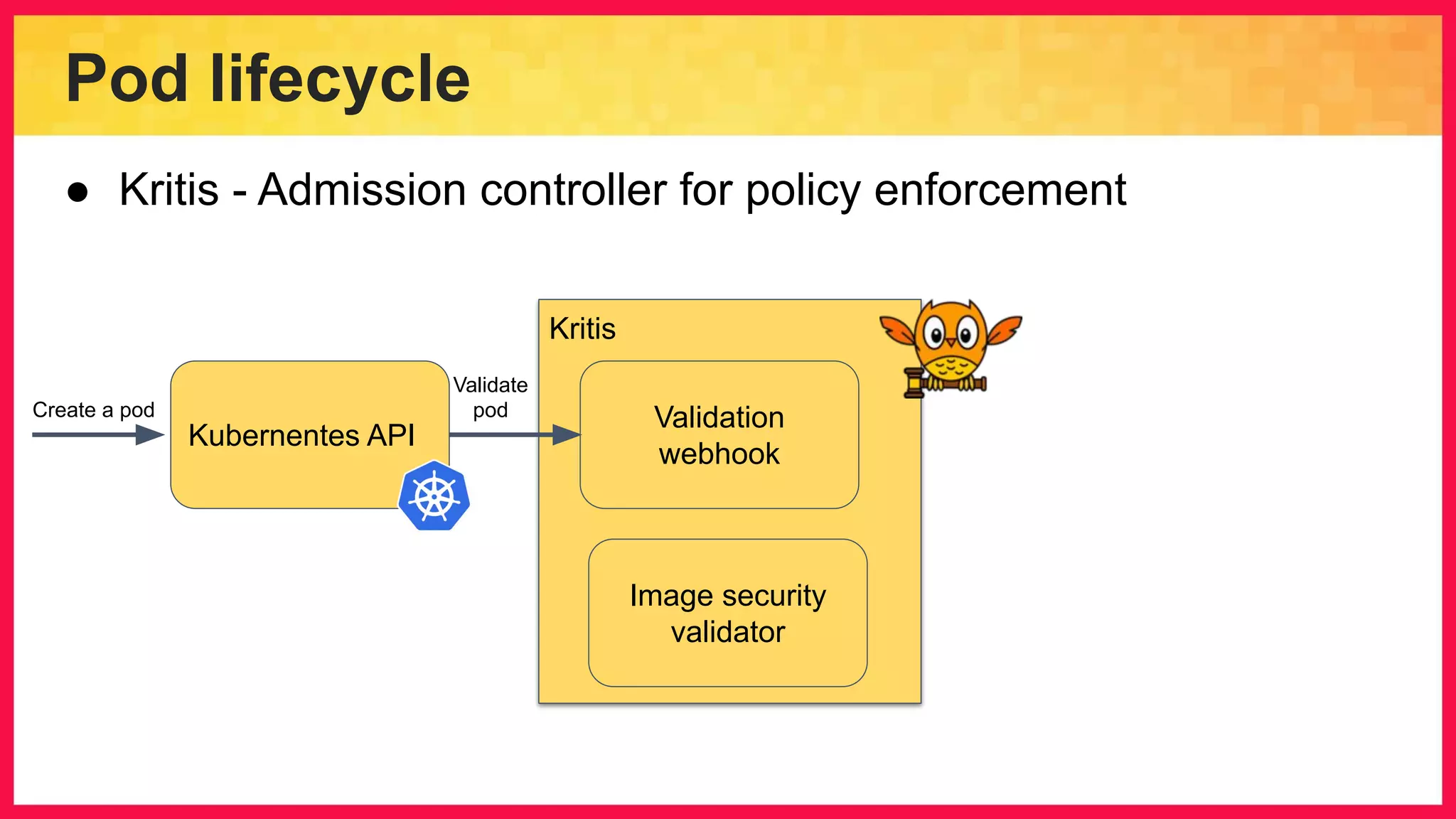
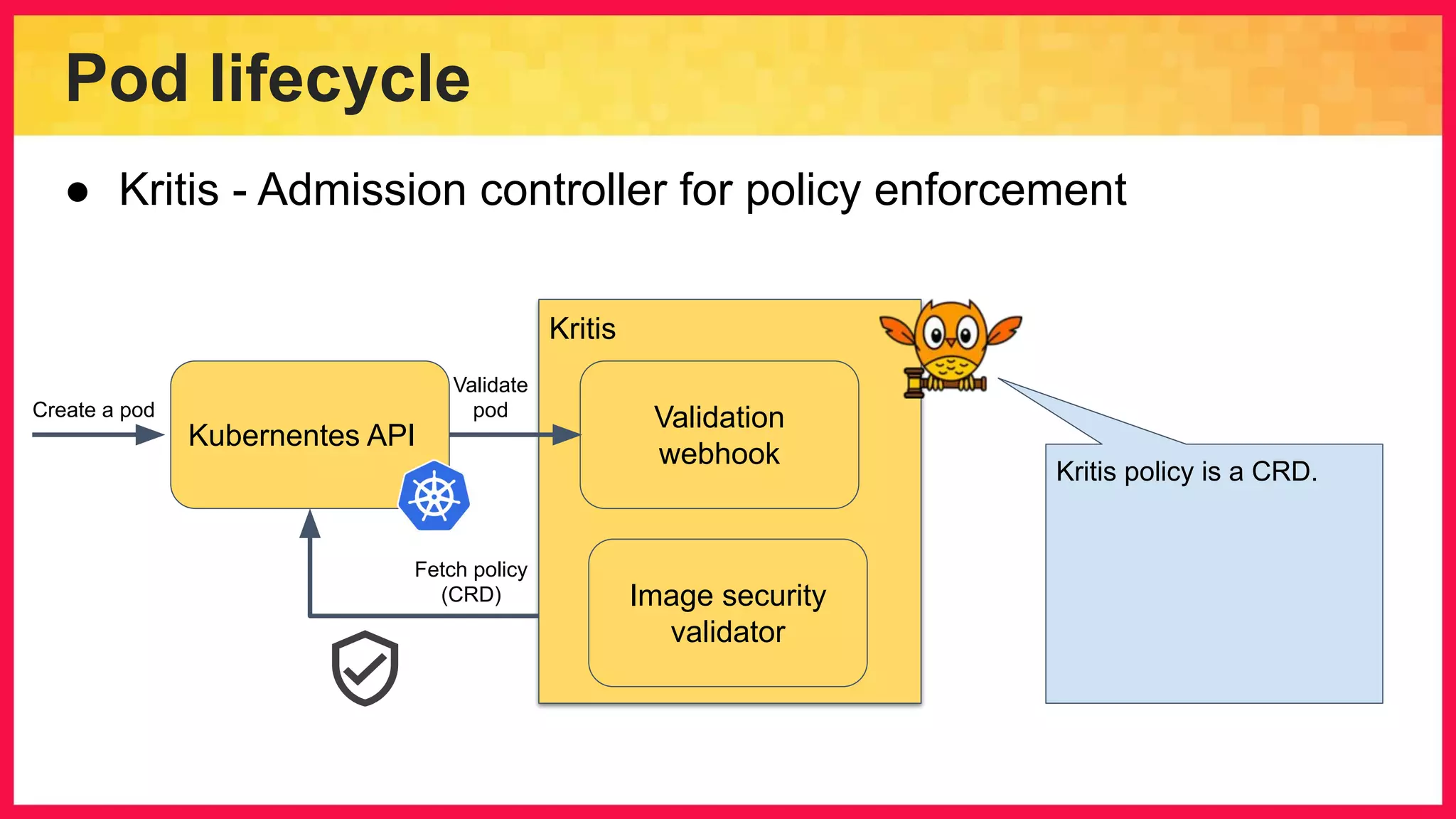
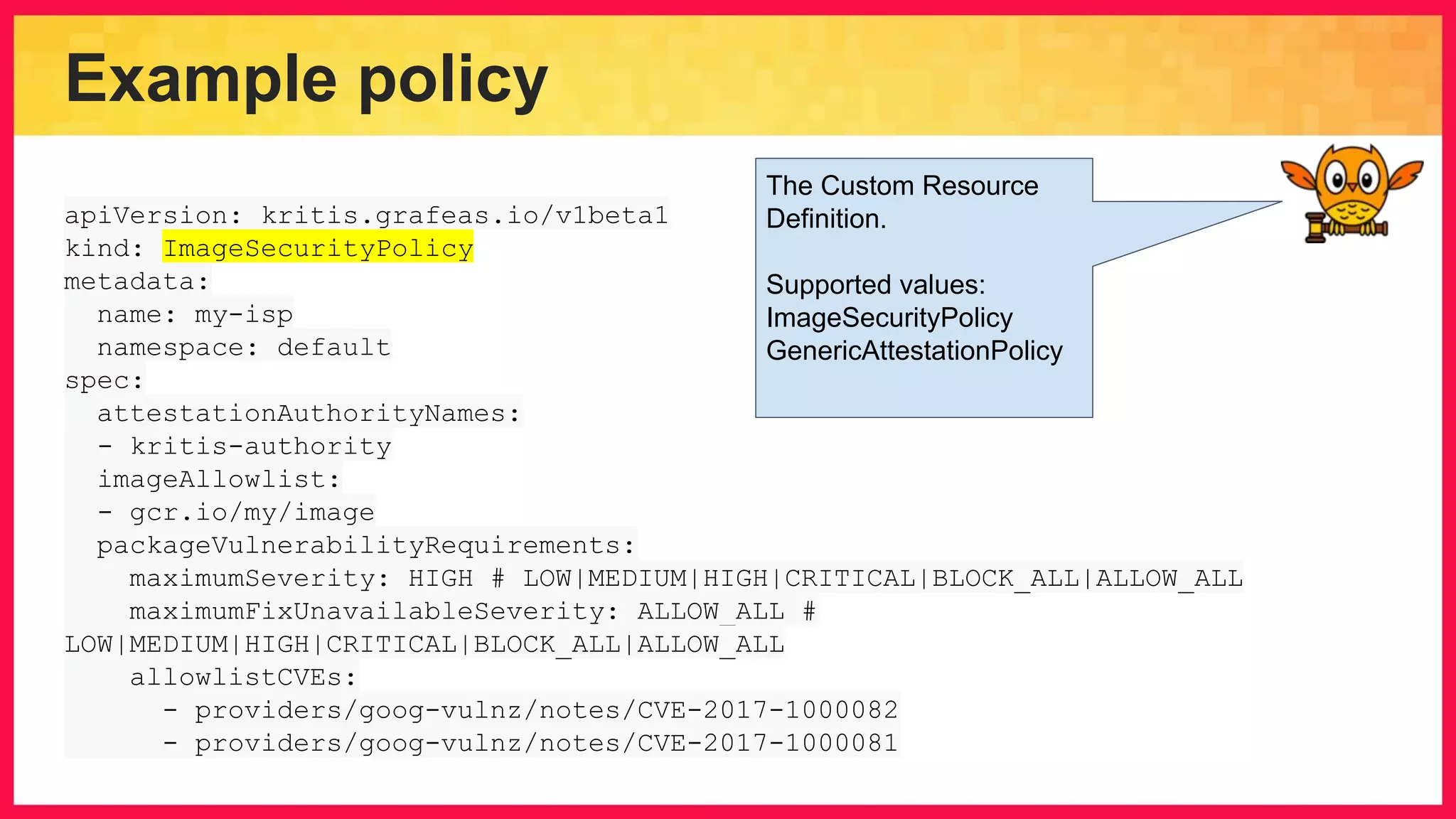
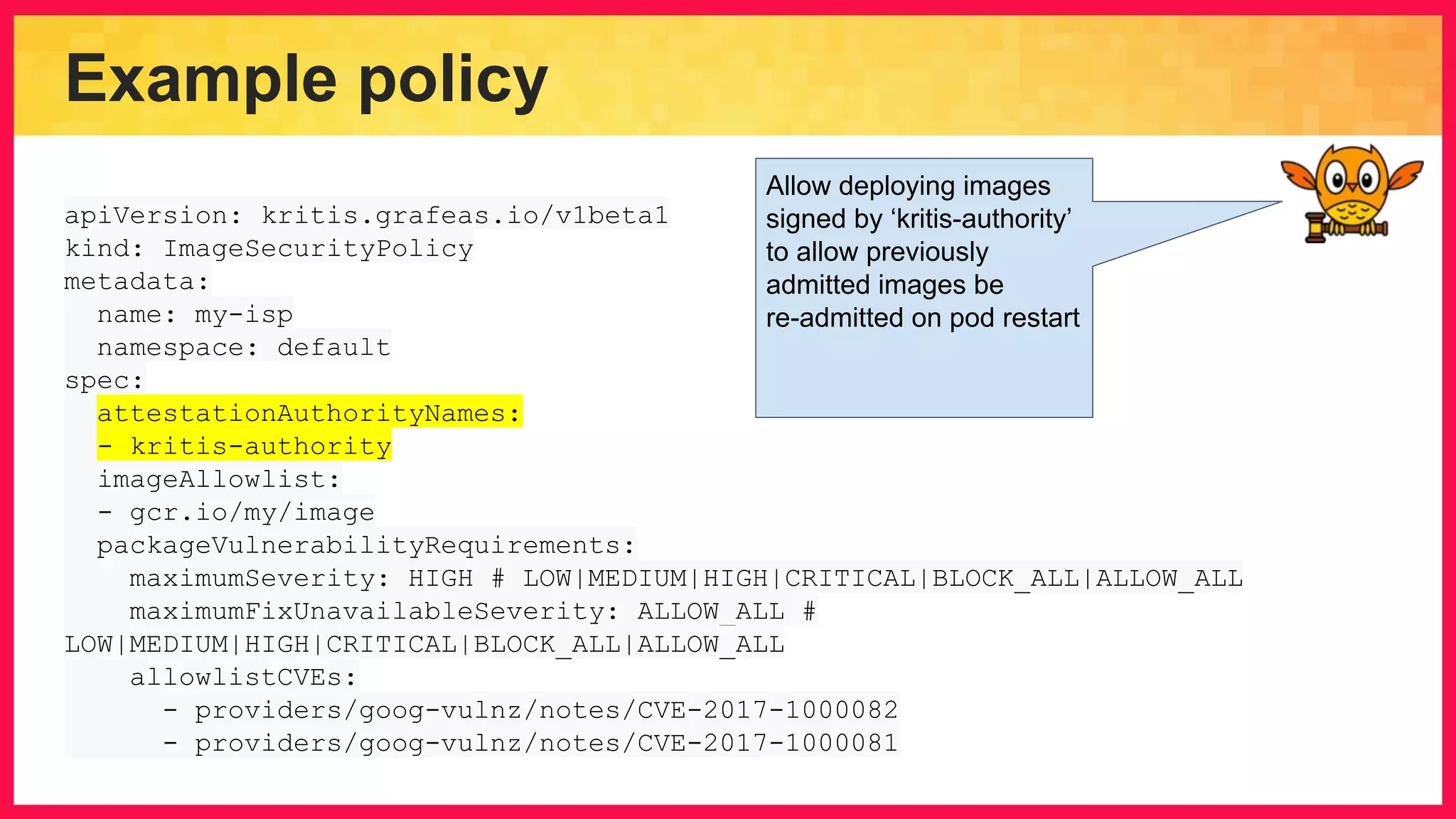
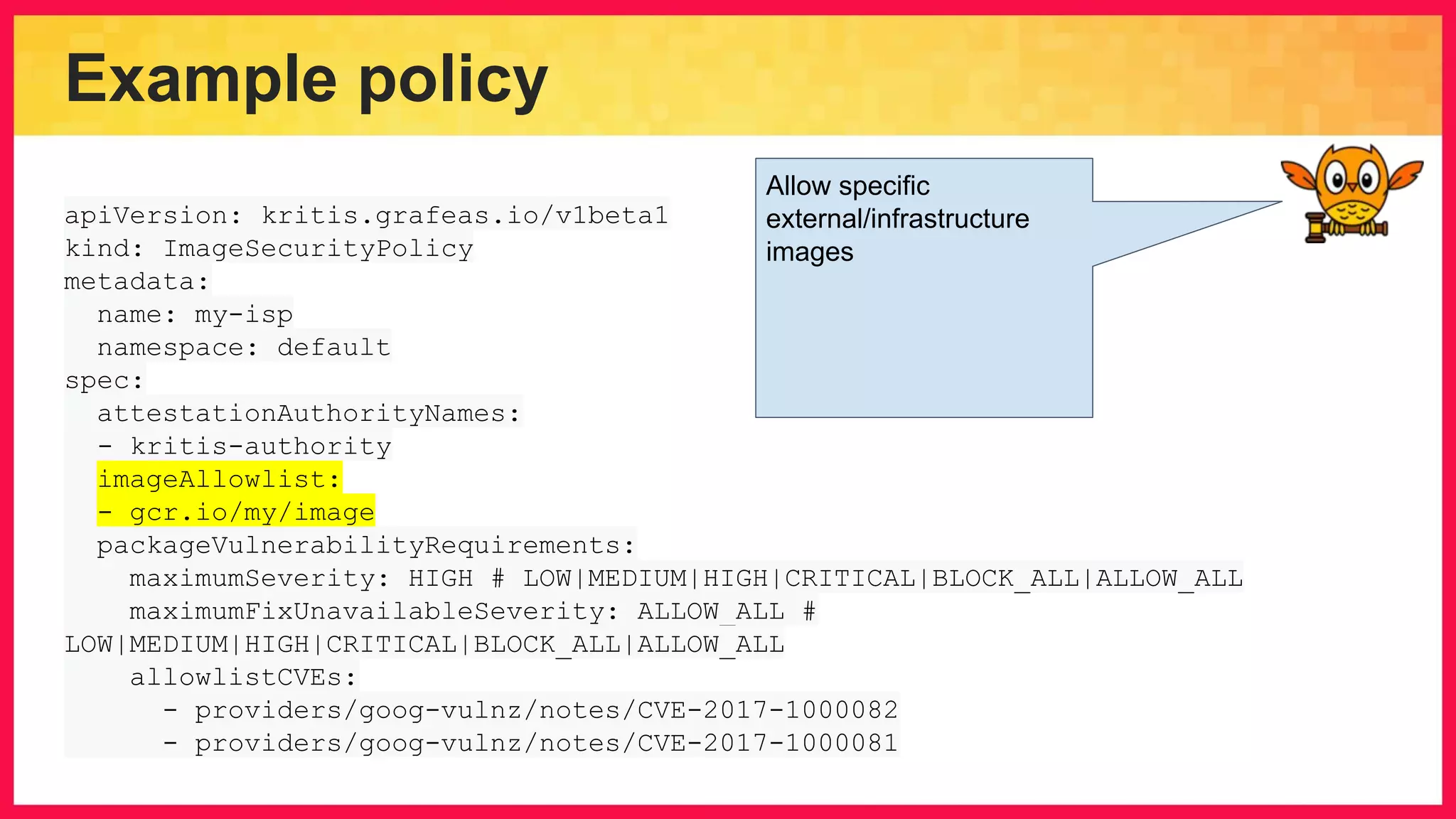
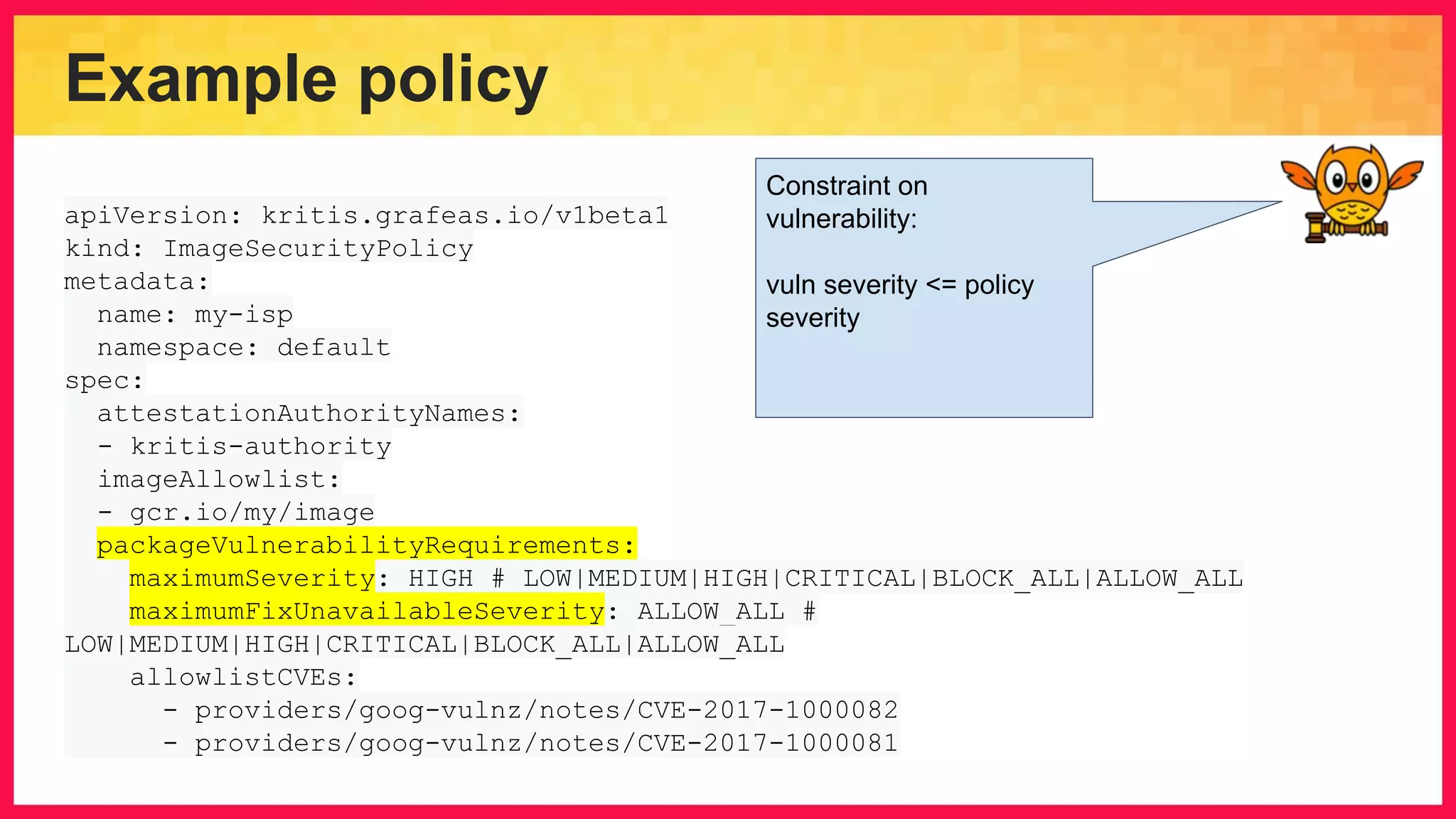
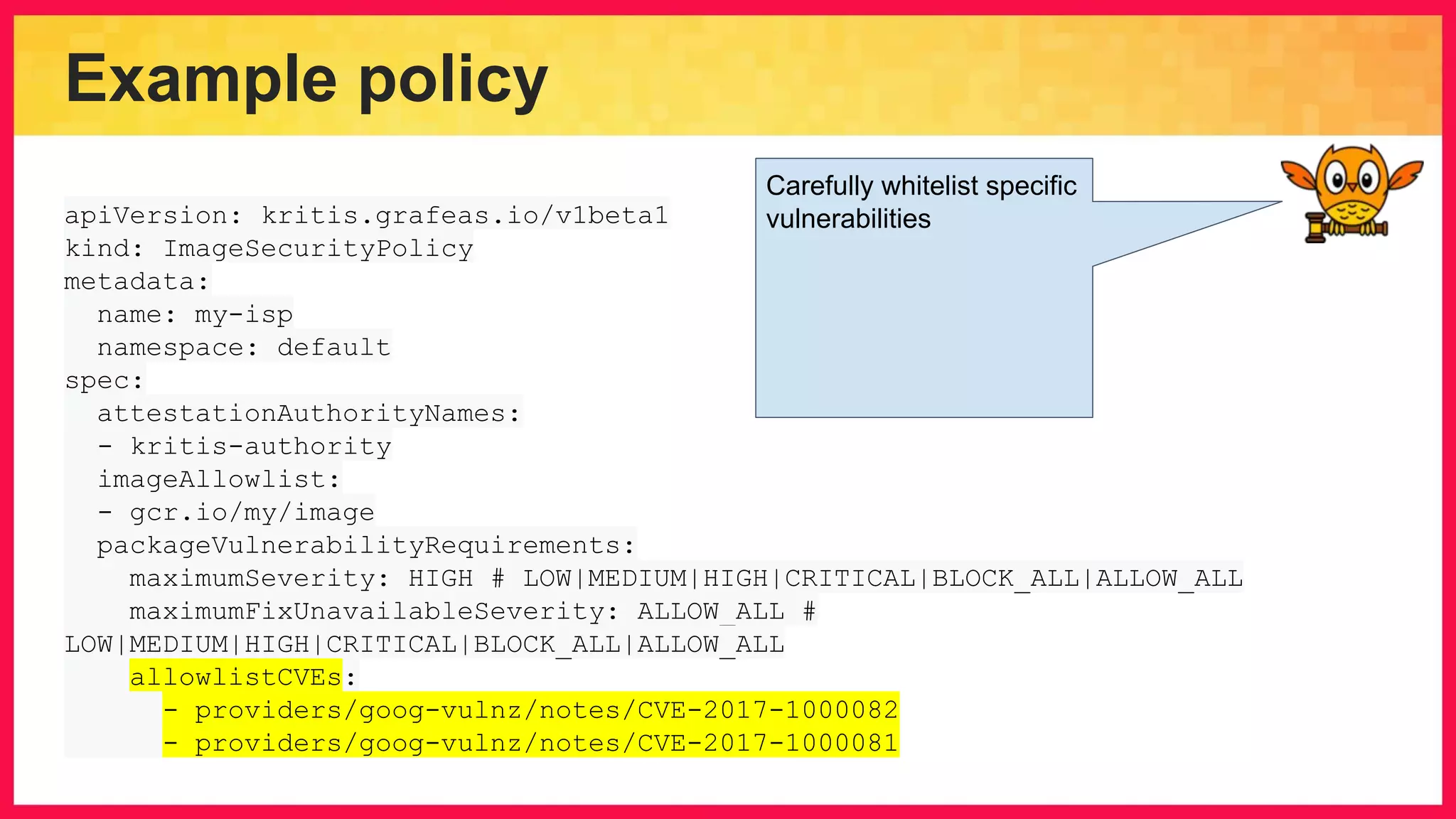
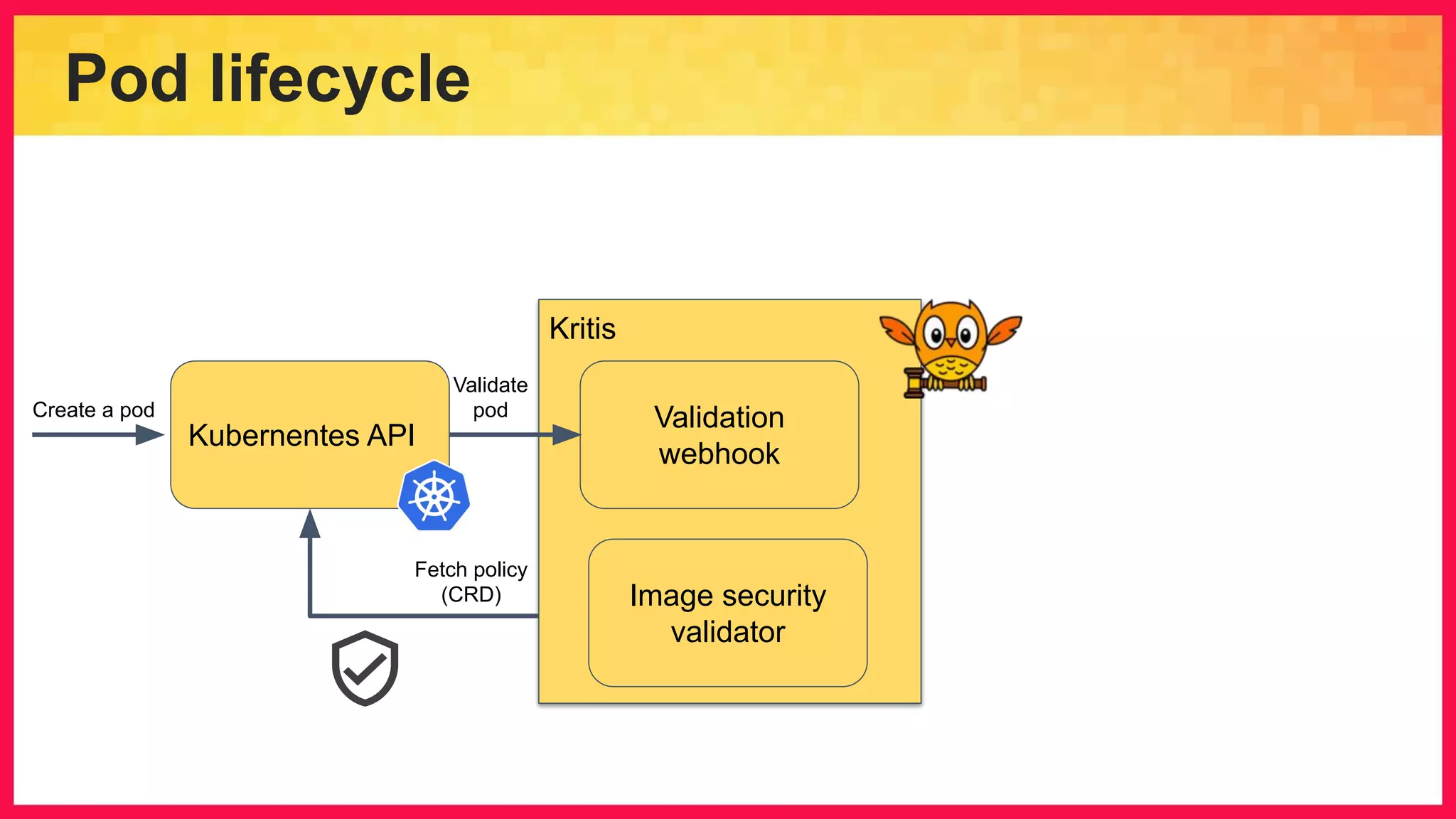
The document discusses the importance of binary authorization in Kubernetes to enhance security by ensuring that only trusted images are deployed in a cluster. It introduces the Kritis tool as an admission controller for policy enforcement, limiting image deployment based on security criteria and vulnerability assessments. Additionally, it covers the Grafeas metadata store for managing vulnerabilities and attestation authorities, along with examples of image security policies.















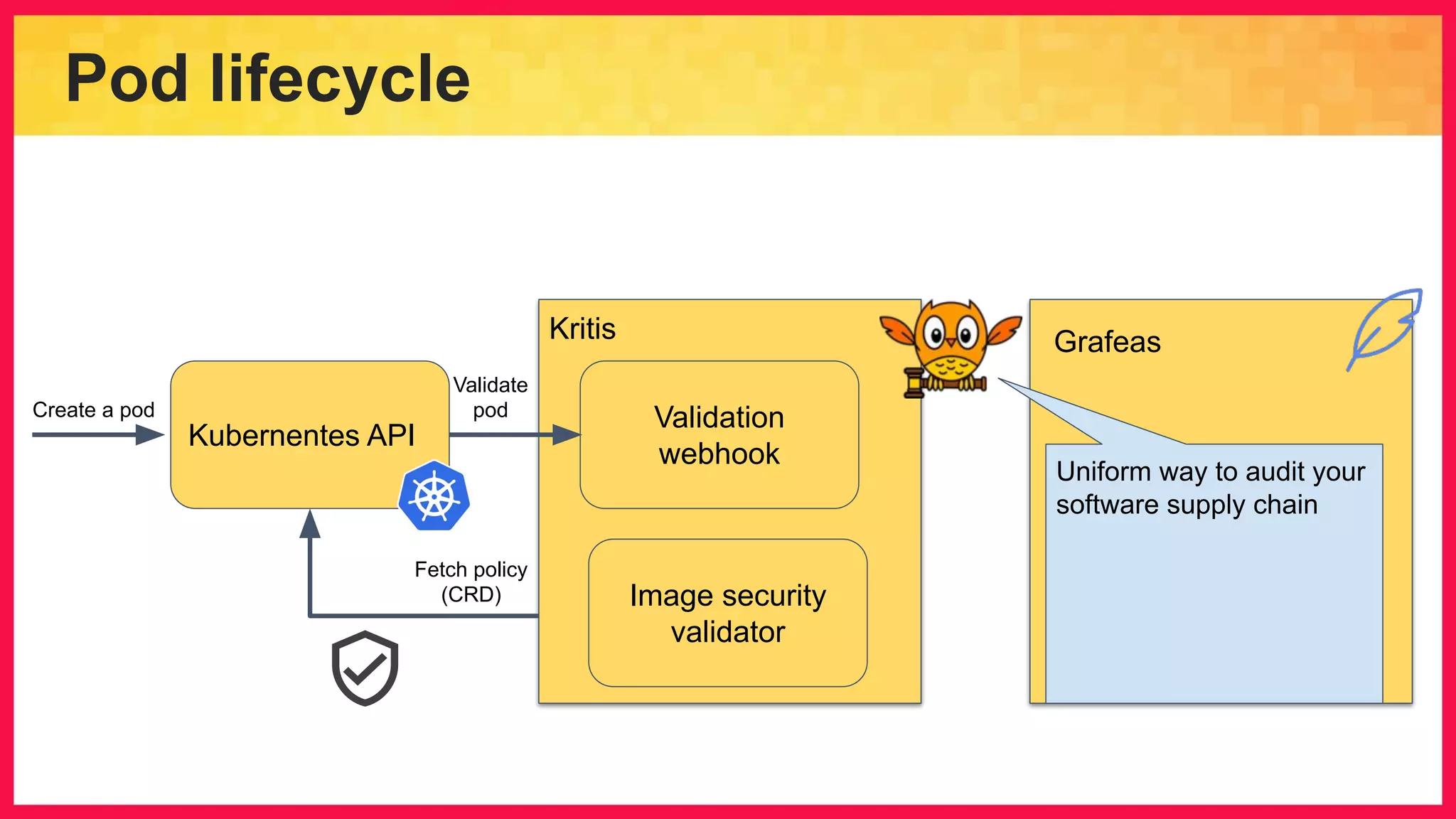
![Grafeas metadata store ● Notes - High level piece of metadata { "name" : "projects/provider_example/notes/test" , "shortDescription" : "A brief description of the note" , "longDescription" : "A longer description of the note" , "kind": "VULNERABILITY" , "vulnerability" : { "details": [ { "package": "libexempi3", "cpeUri": "cpe:/o:debian:debian_linux:7" , "minAffectedVersion" : { "name": "2.5.7", "revision": "1", "kind": "NORMAL" }, }] } }](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-39-2048.jpg)
![Grafeas metadata store { "name" : "projects/provider_example/notes/test" , "shortDescription" : "A brief description of the note" , "longDescription" : "A longer description of the note" , "kind": "VULNERABILITY" , "vulnerability" : { "details": [ { "package": "libexempi3", "cpeUri": "cpe:/o:debian:debian_linux:7" , "minAffectedVersion" : { "name": "2.5.7", "revision": "1", "kind": "NORMAL" }, }] } } ● Notes - High level piece of metadata - Vulnerability: CVE description](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-40-2048.jpg)
![Grafeas metadata store { "name" : "projects/provider_example/notes/test" , "shortDescription" : "A brief description of the note" , "longDescription" : "A longer description of the note" , "kind": "VULNERABILITY" , "vulnerability" : { "details": [ { "package": "libexempi3", "cpeUri": "cpe:/o:debian:debian_linux:7" , "minAffectedVersion" : { "name": "2.5.7", "revision": "1", "kind": "NORMAL" }, }] } } ● Notes - High level piece of metadata - Vulnerability: CVE description & details](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-41-2048.jpg)
![Grafeas metadata store { "name" : "projects/provider_example/notes/test" , "shortDescription" : "A brief description of the note" , "longDescription" : "A longer description of the note" , "kind": "VULNERABILITY" , "vulnerability" : { "details": [ { "package": "libexempi3", "cpeUri": "cpe:/o:debian:debian_linux:7" , "minAffectedVersion" : { "name": "2.5.7", "revision": "1", "kind": "NORMAL" }, }] } } ● Notes - High level piece of metadata - Vulnerability: CVE description & details](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-42-2048.jpg)

![Grafeas metadata store { "name" : "projects/provider_example/notes/test" , "shortDescription" : "A brief description of the note" , "longDescription" : "A longer description of the note" , "kind": "VULNERABILITY" , "vulnerability" : { "details": [ { "package": "libexempi3", "cpeUri": "cpe:/o:debian:debian_linux:7" , "minAffectedVersion" : { "name": "2.5.7", "revision": "1", "kind": "NORMAL" }, }] } } ● Notes - High level piece of metadata - Vulnerability: CVE description & details - Attestation: attestation authority - Deployment - Build history - And more!](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-44-2048.jpg)
![Grafeas metadata store ● Notes ● Occurrences - Instantiation of a note { "name": "projects/occurrence_example/occurrences/test", "resource": { "uri": "https://gcr.io/project/image@sha256:foo", }, "noteName": "projects/provider_example/notes/test", "kind": "VULNERABILITY", "vulnerability": { "packageIssue": [ { "affectedLocation": { "cpeUri": "7", "package": "a", "version": { "name": "v1.1.1", "kind": "NORMAL", "revision": "r" } }, "fixedLocation": { "cpeUri": "cpe:/o:debian:debian_linux:7", "package": "a", "version": { "name": "namestring", "kind": "NORMAL", "revision": "1" } } } ] } }](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-45-2048.jpg)
![Grafeas metadata store { "name": "projects/occurrence_example/occurrences/test", "resource": { "uri": "https://gcr.io/project/image@sha256:foo", }, "noteName": "projects/provider_example/notes/test", "kind": "VULNERABILITY", "vulnerability": { "packageIssue": [ { "affectedLocation": { "cpeUri": "7", "package": "a", "version": { "name": "v1.1.1", "kind": "NORMAL", "revision": "r" } }, "fixedLocation": { "cpeUri": "cpe:/o:debian:debian_linux:7", "package": "a", "version": { "name": "namestring", "kind": "NORMAL", "revision": "1" } } } ] } } ● Notes ● Occurrences - Instantiation of a note](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-46-2048.jpg)
![Grafeas metadata store { "name": "projects/occurrence_example/occurrences/test", "resource": { "uri": "https://gcr.io/project/image@sha256:foo", }, "noteName": "projects/provider_example/notes/test", "kind": "VULNERABILITY", "vulnerability": { "packageIssue": [ { "affectedLocation": { "cpeUri": "7", "package": "a", "version": { "name": "v1.1.1", "kind": "NORMAL", "revision": "r" } }, "fixedLocation": { "cpeUri": "cpe:/o:debian:debian_linux:7", "package": "a", "version": { "name": "namestring", "kind": "NORMAL", "revision": "1" } } } ] } } ● Notes ● Occurrences - Instantiation of a note](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-47-2048.jpg)
![Grafeas metadata store { "name": "projects/occurrence_example/occurrences/test", "resource": { "uri": "https://gcr.io/project/image@sha256:foo", }, "noteName": "projects/provider_example/notes/test", "kind": "VULNERABILITY", "vulnerability": { "packageIssue": [ { "affectedLocation": { "cpeUri": "7", "package": "a", "version": { "name": "v1.1.1", "kind": "NORMAL", "revision": "r" } }, "fixedLocation": { "cpeUri": "cpe:/o:debian:debian_linux:7", "package": "a", "version": { "name": "namestring", "kind": "NORMAL", "revision": "1" } } } ] } } ● Notes ● Occurrences - Instantiation of a note - Package where vulnerability was found](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-48-2048.jpg)
![Grafeas metadata store { "name": "projects/occurrence_example/occurrences/test", "resource": { "uri": "https://gcr.io/project/image@sha256:foo", }, "noteName": "projects/provider_example/notes/test", "kind": "VULNERABILITY", "vulnerability": { "packageIssue": [ { "affectedLocation": { "cpeUri": "7", "package": "a", "version": { "name": "v1.1.1", "kind": "NORMAL", "revision": "r" } }, "fixedLocation": { "cpeUri": "cpe:/o:debian:debian_linux:7", "package": "a", "version": { "name": "namestring", "kind": "NORMAL", "revision": "1" } } } ] } } ● Notes ● Occurrences - Instantiation of a note - Package where vulnerability was found - Remediation](https://image.slidesharecdn.com/kubecon-2019-grafeas-kritis-191216200251/75/Binary-Authorization-in-Kubernetes-49-2048.jpg)