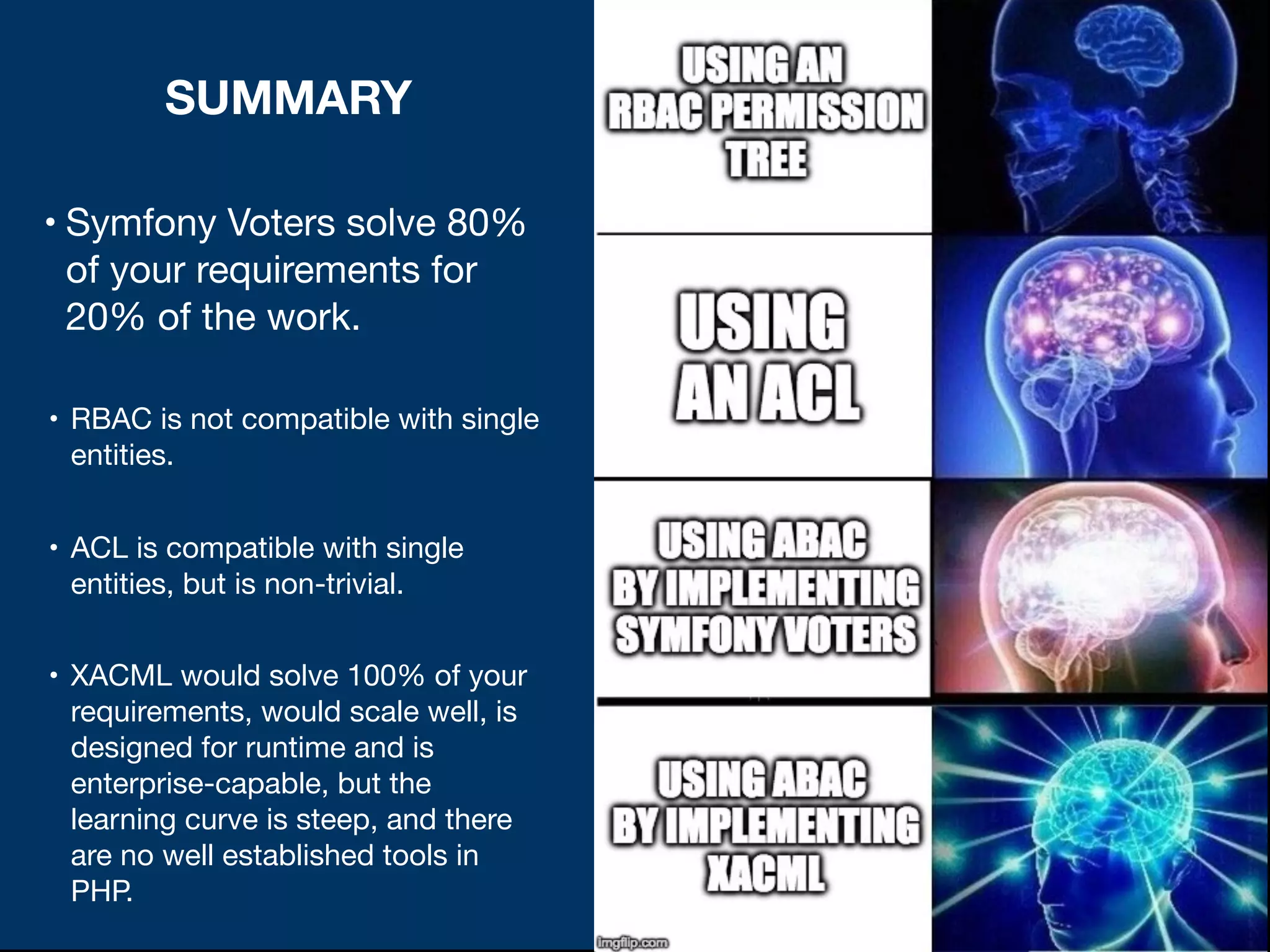
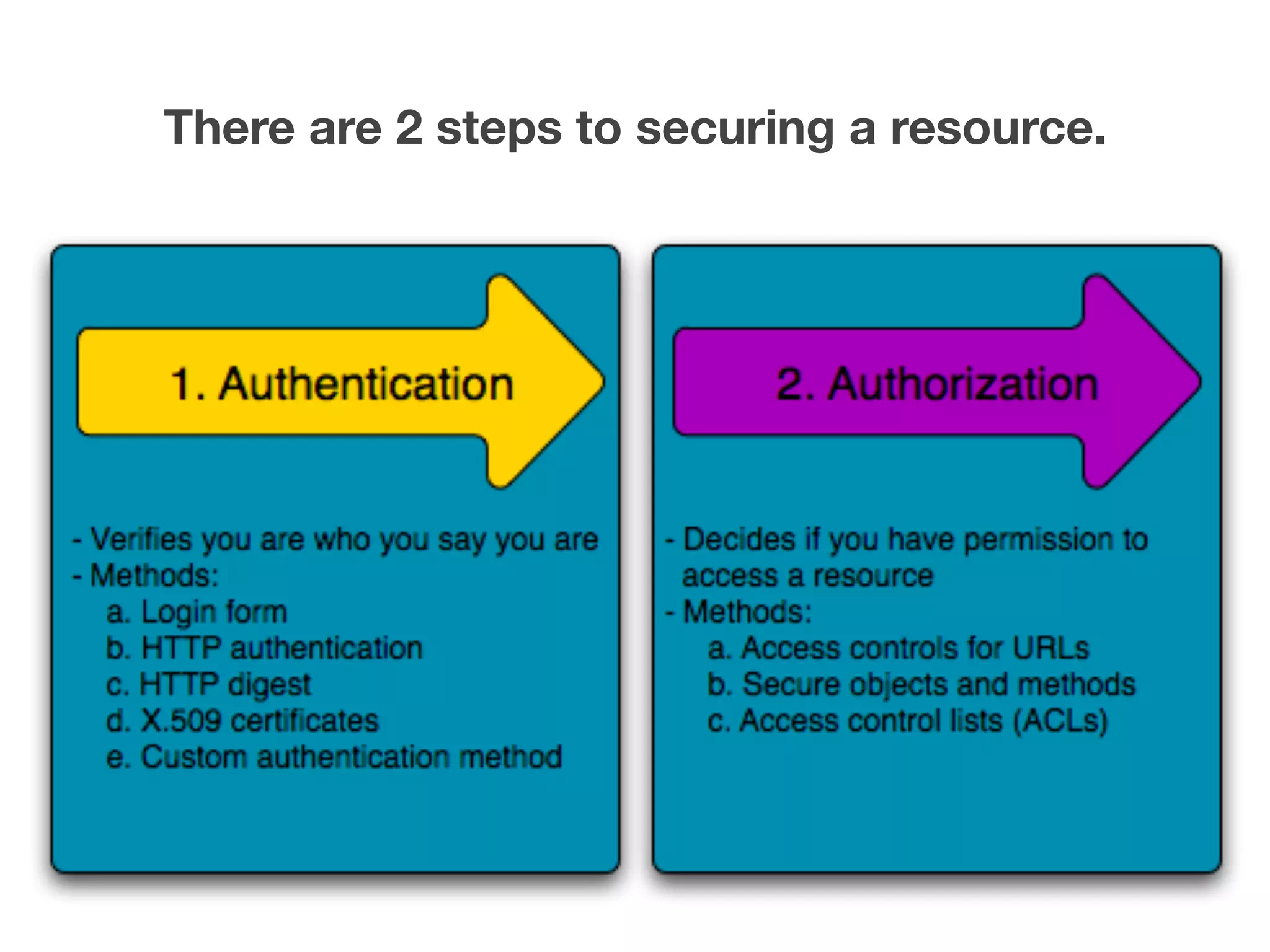
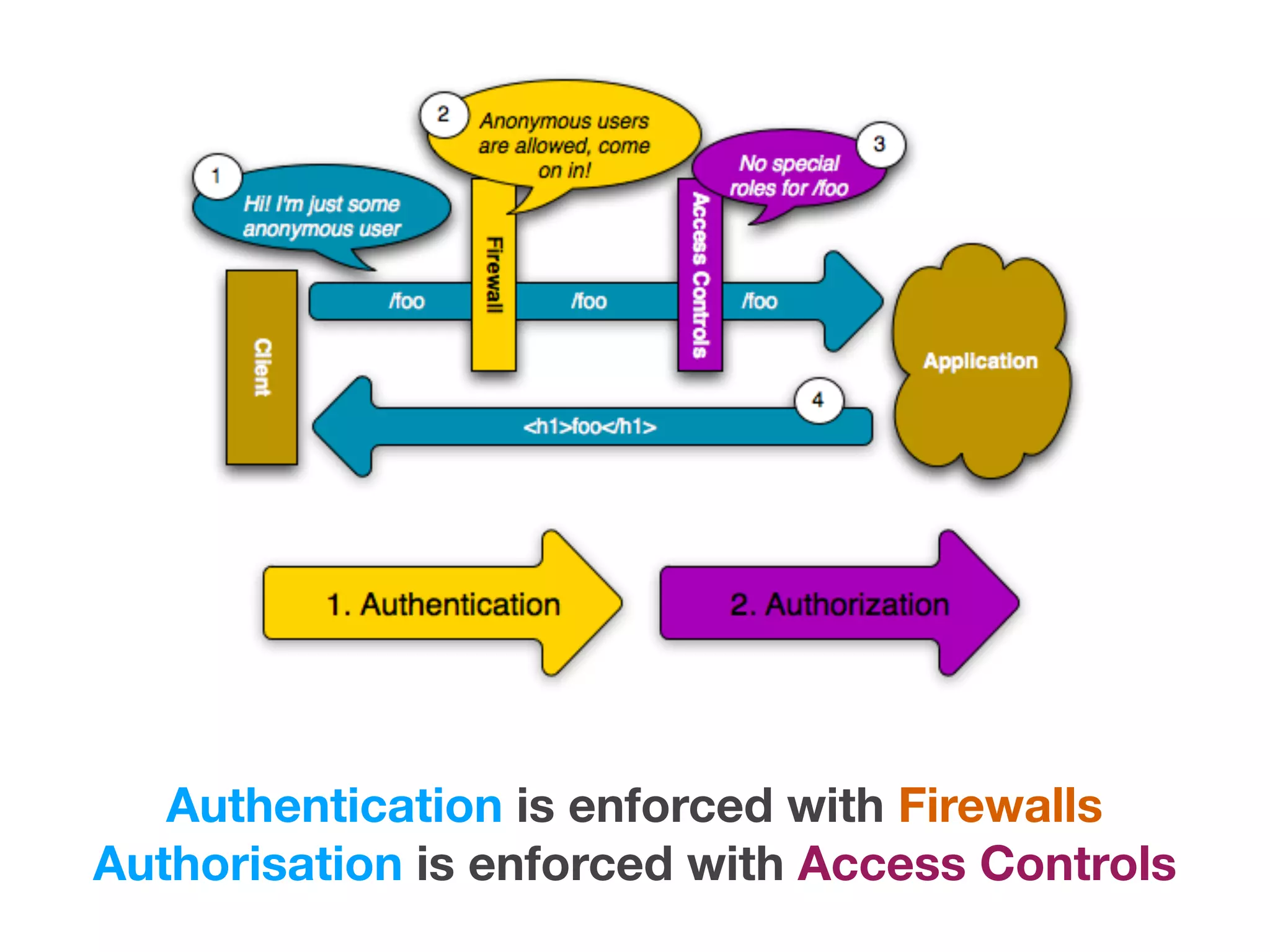
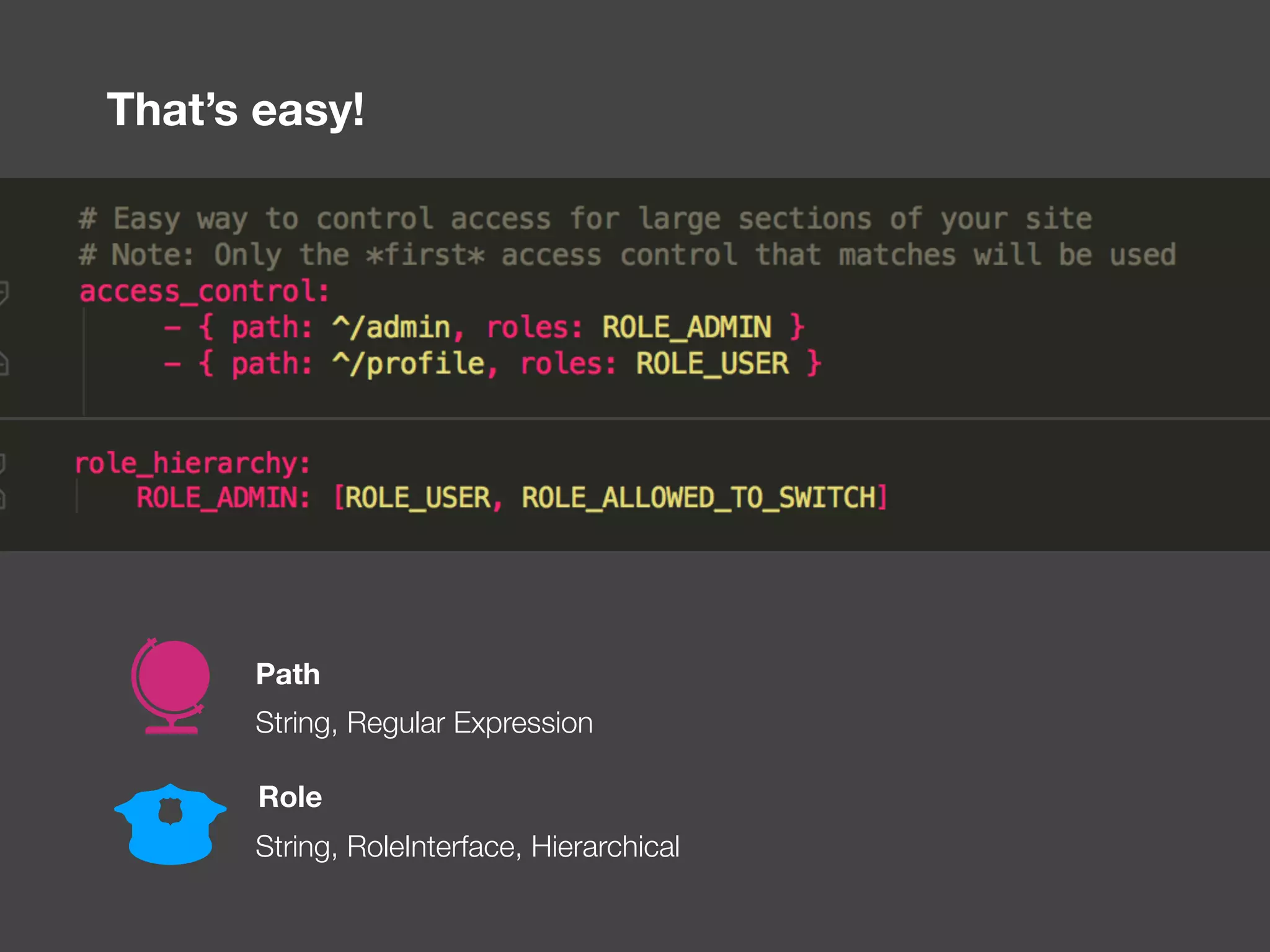
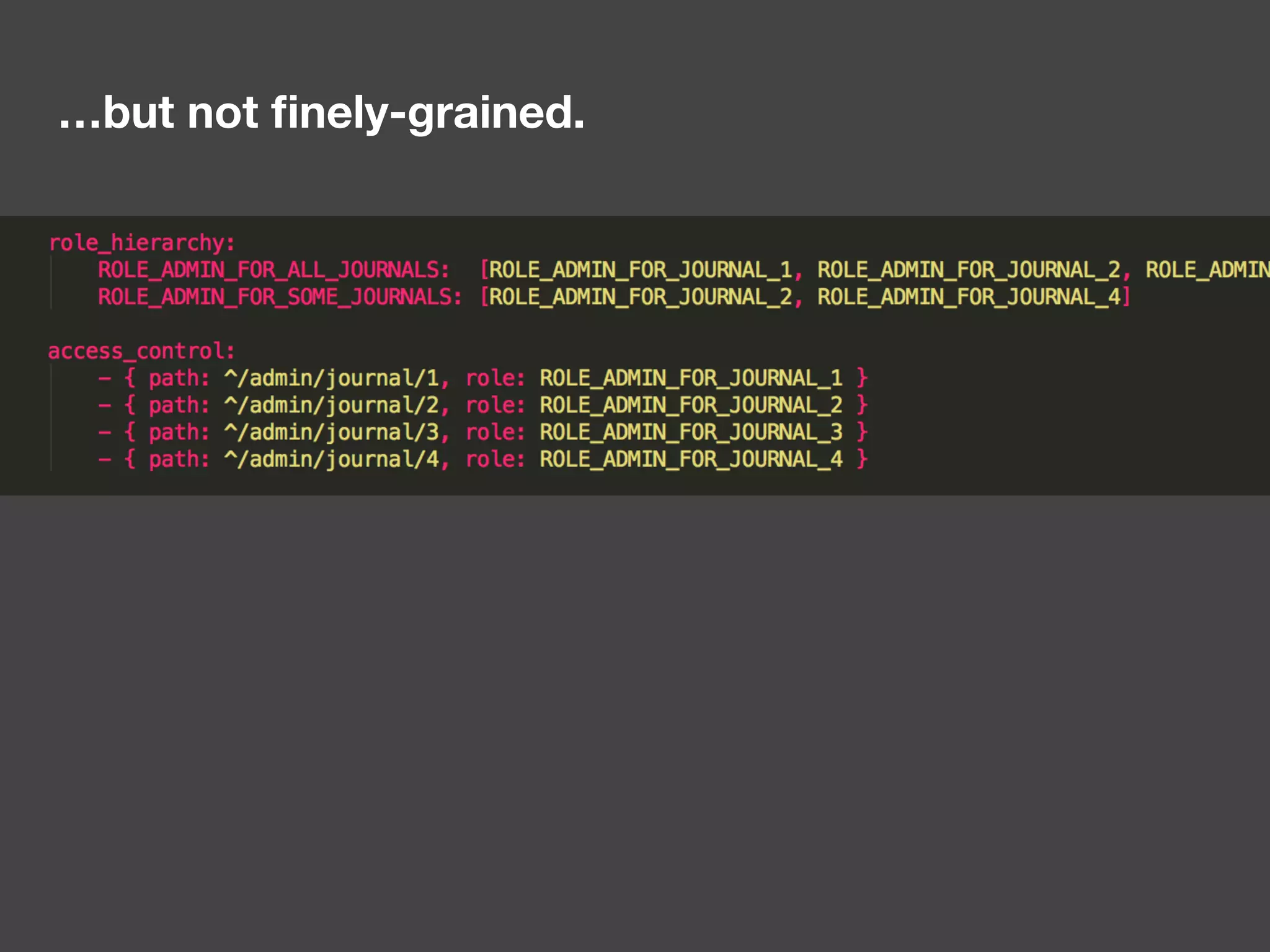
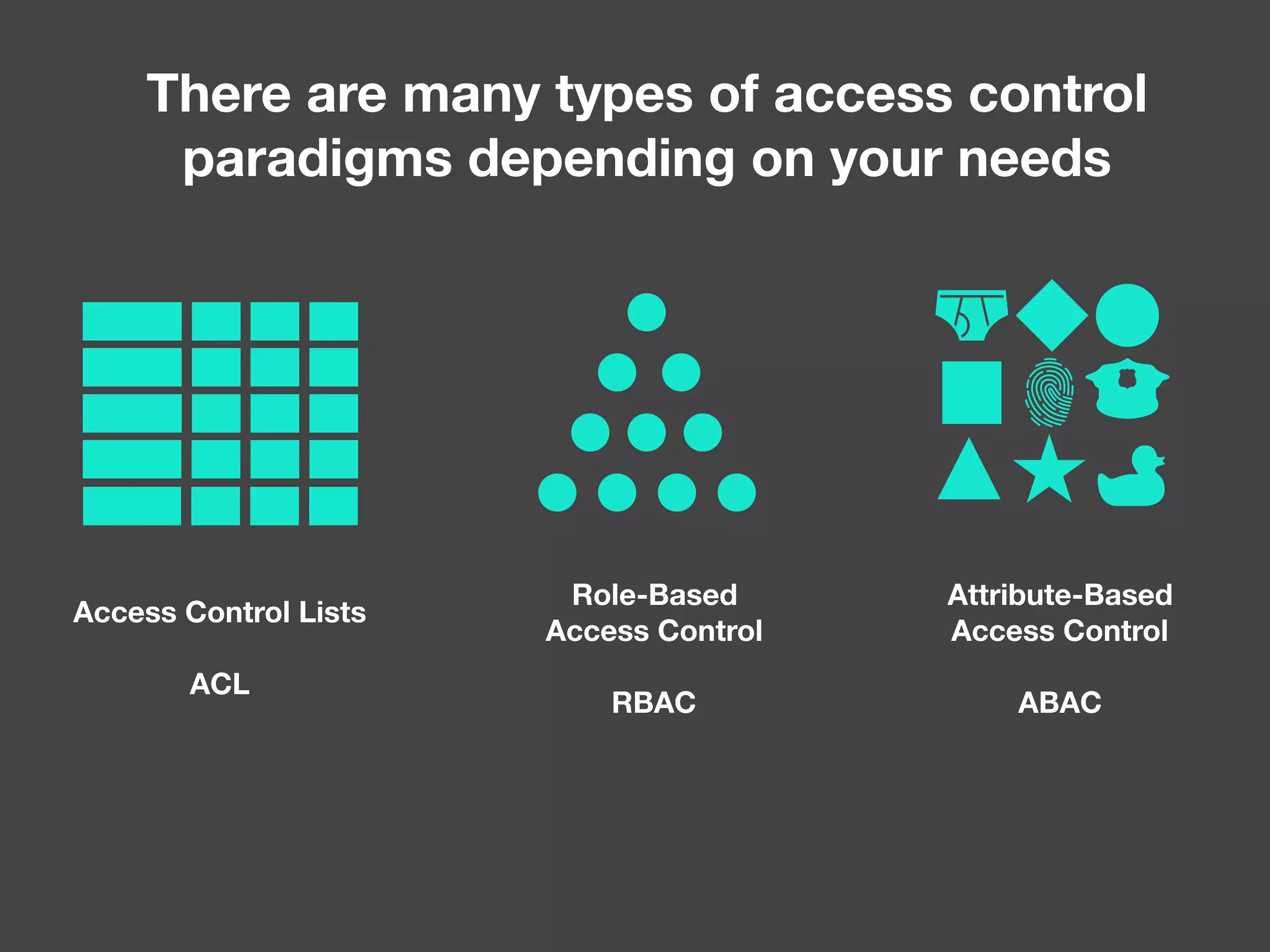
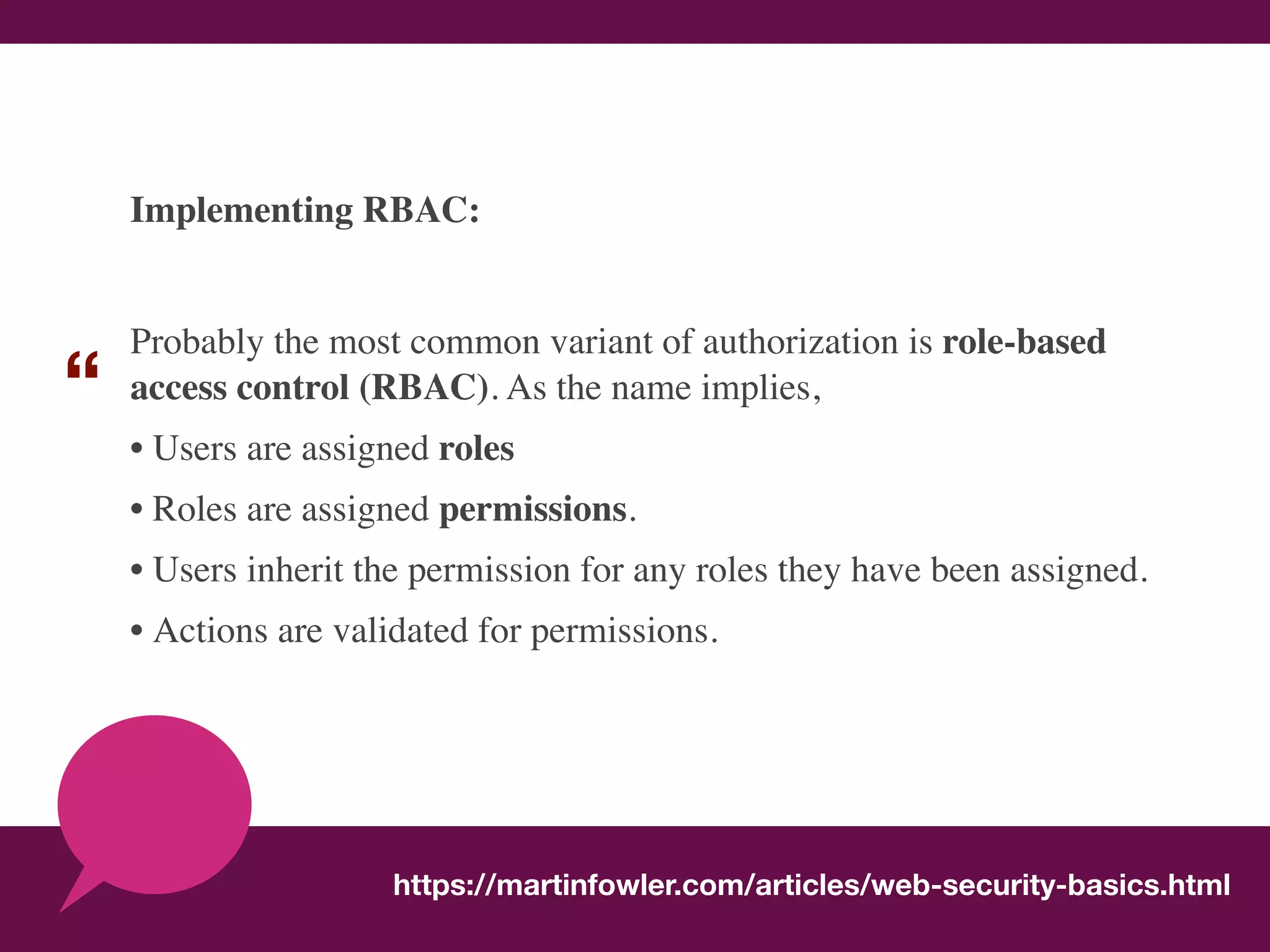
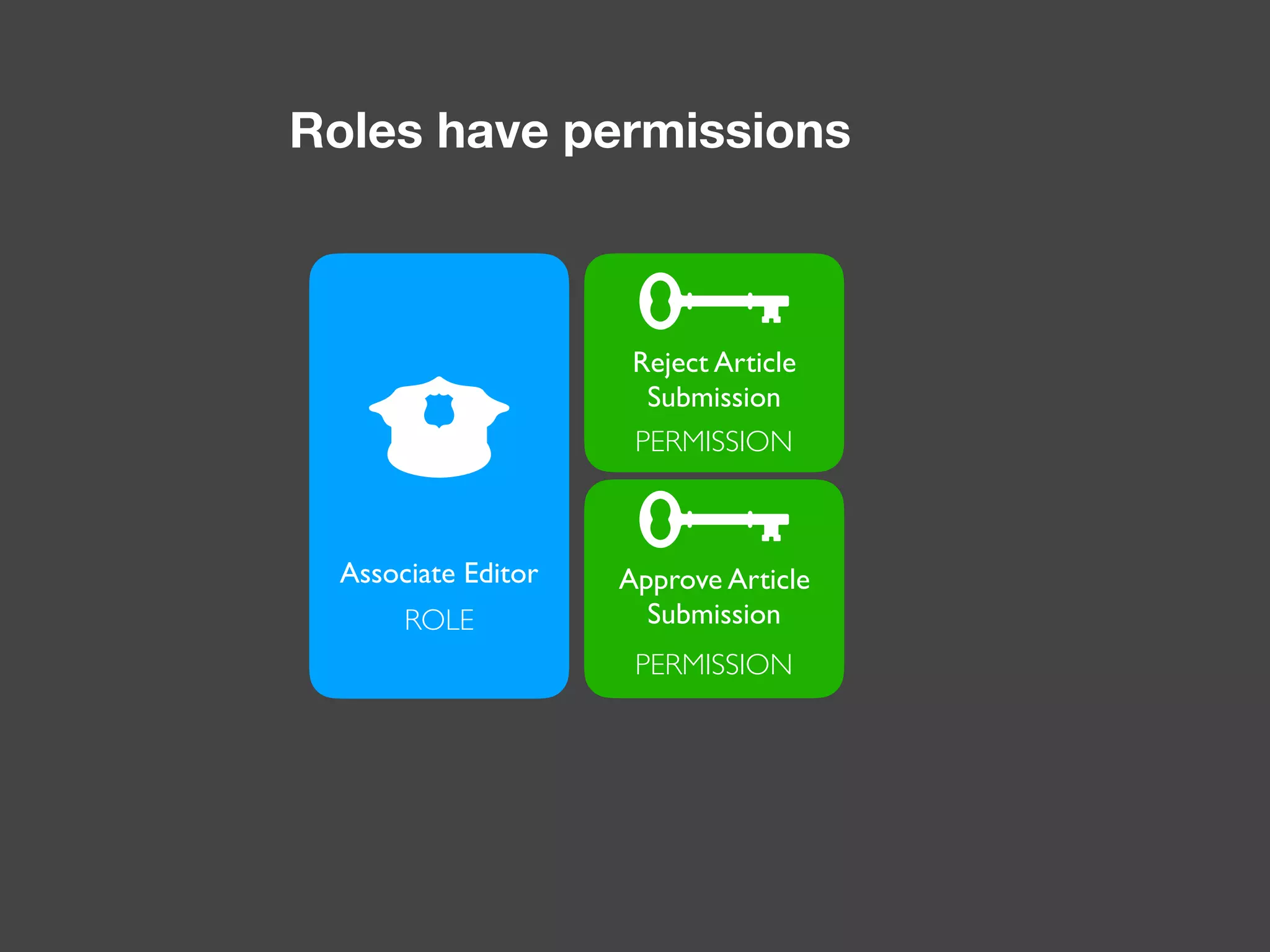
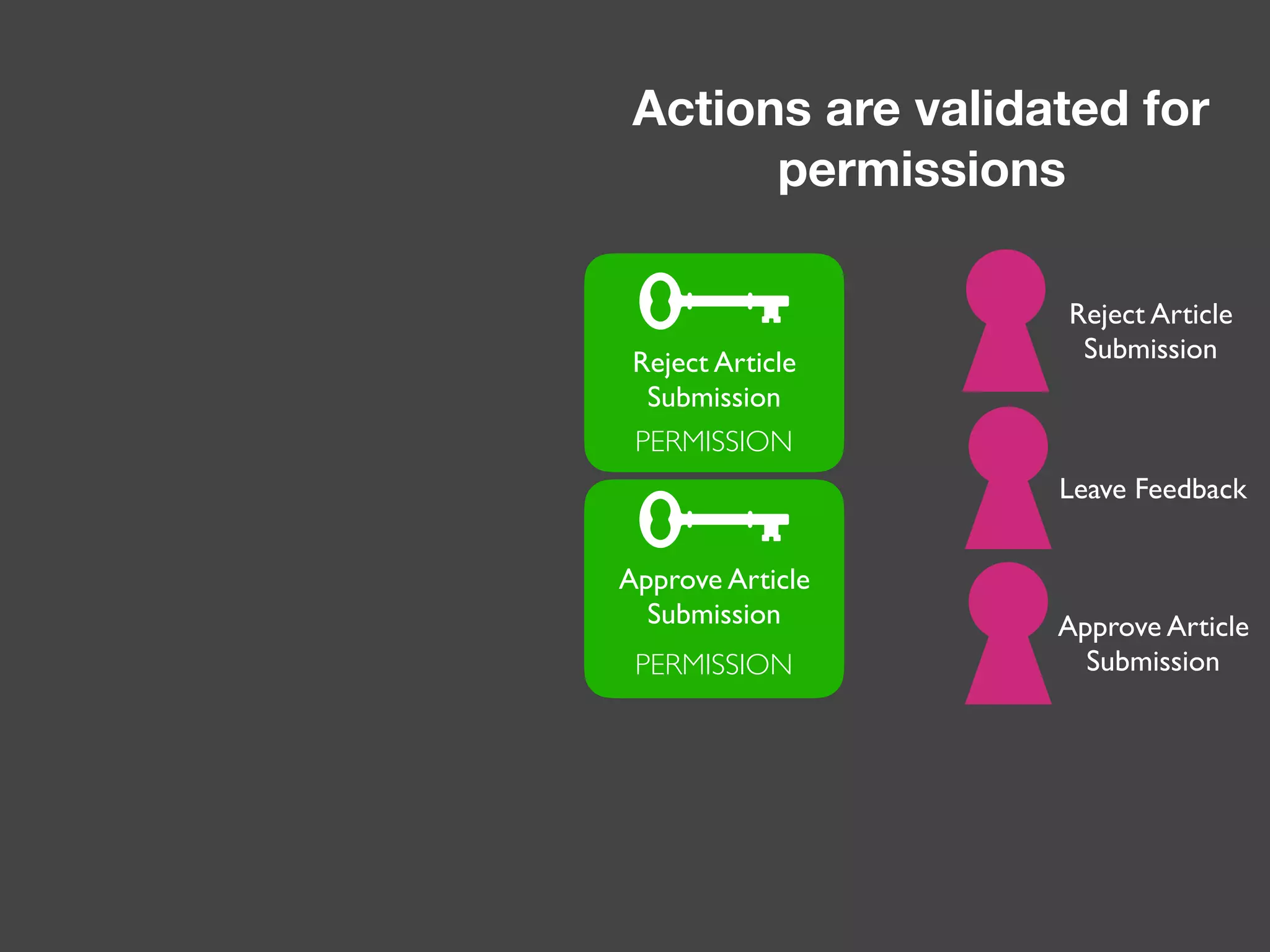
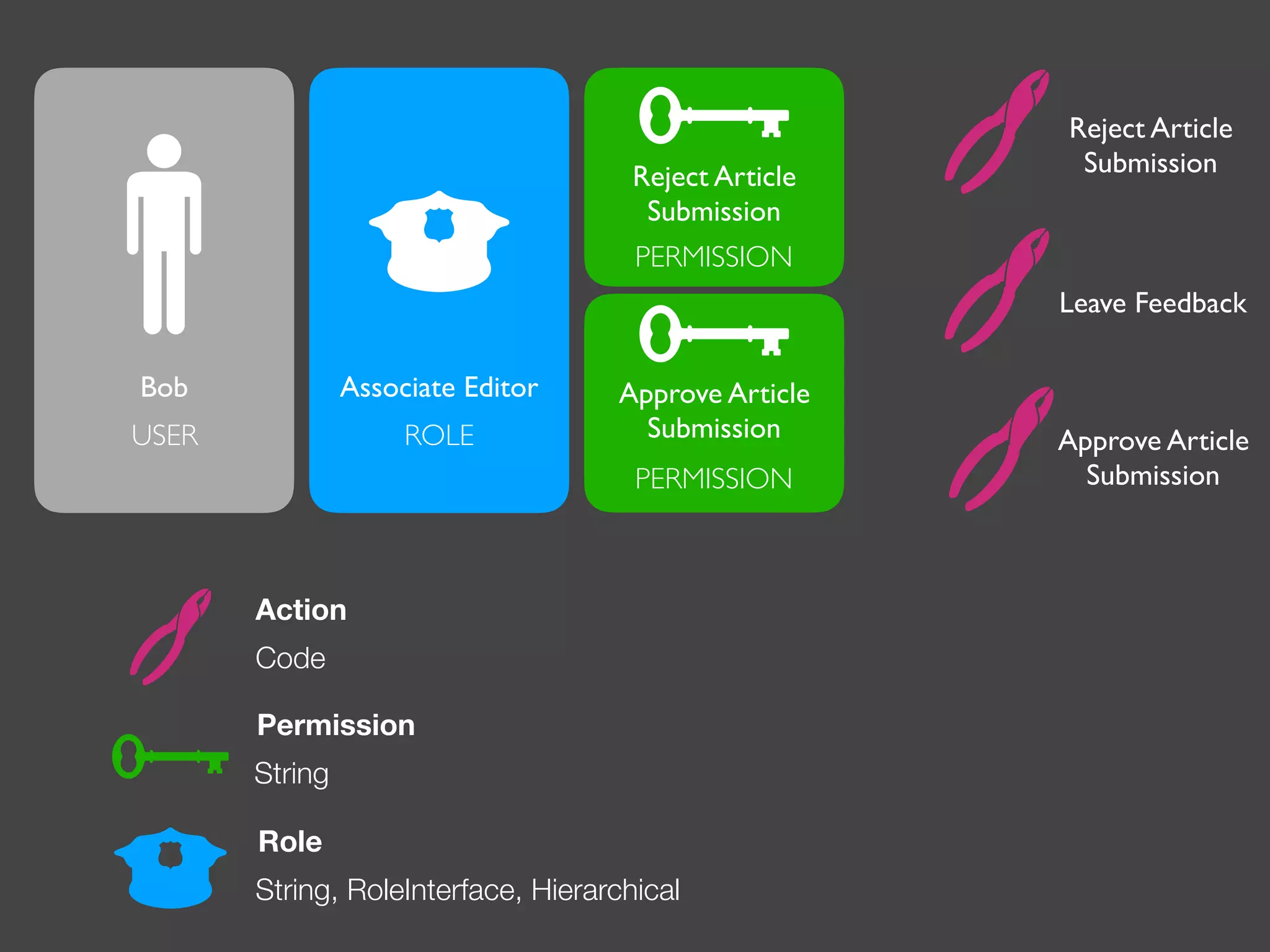
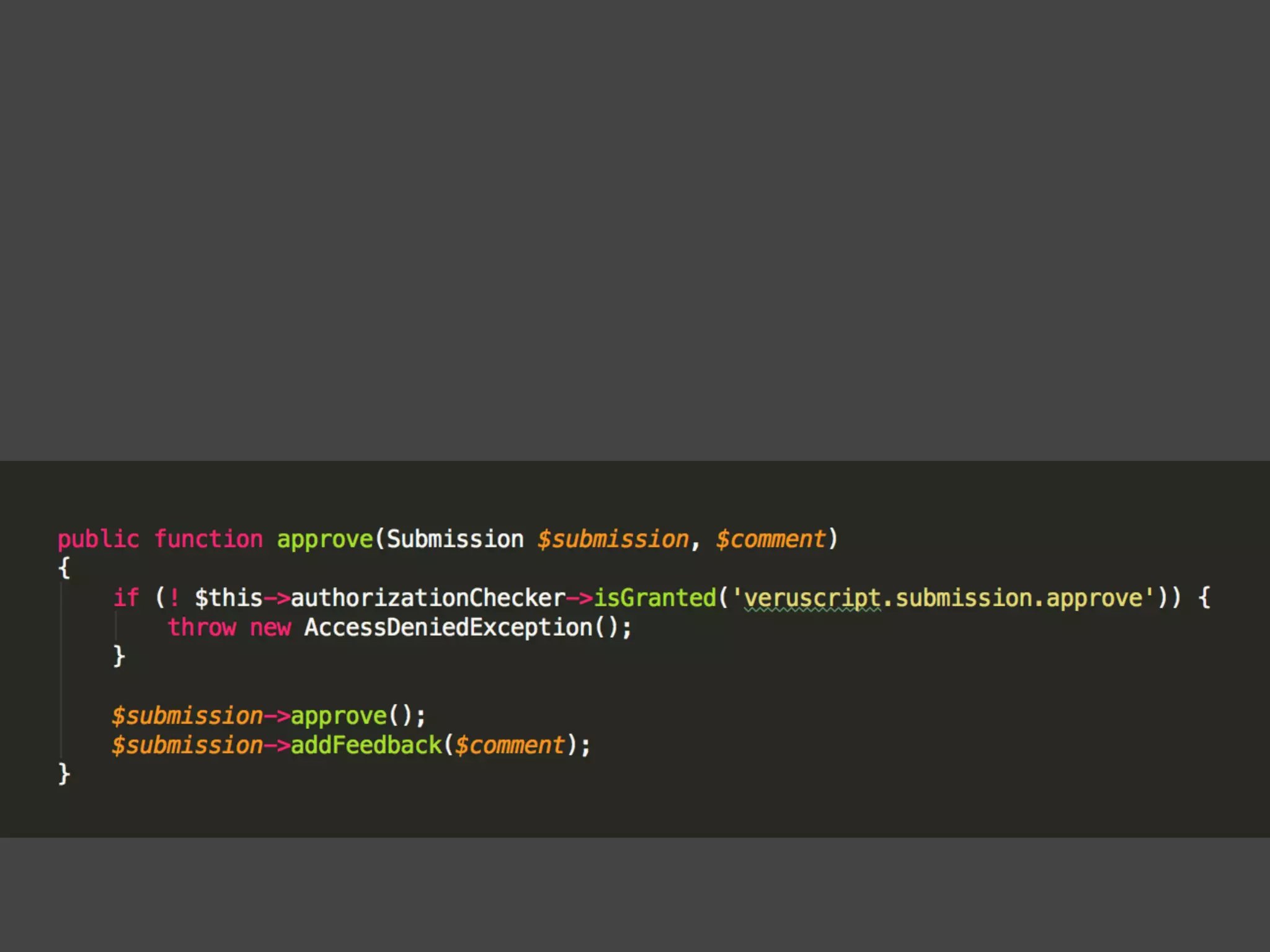
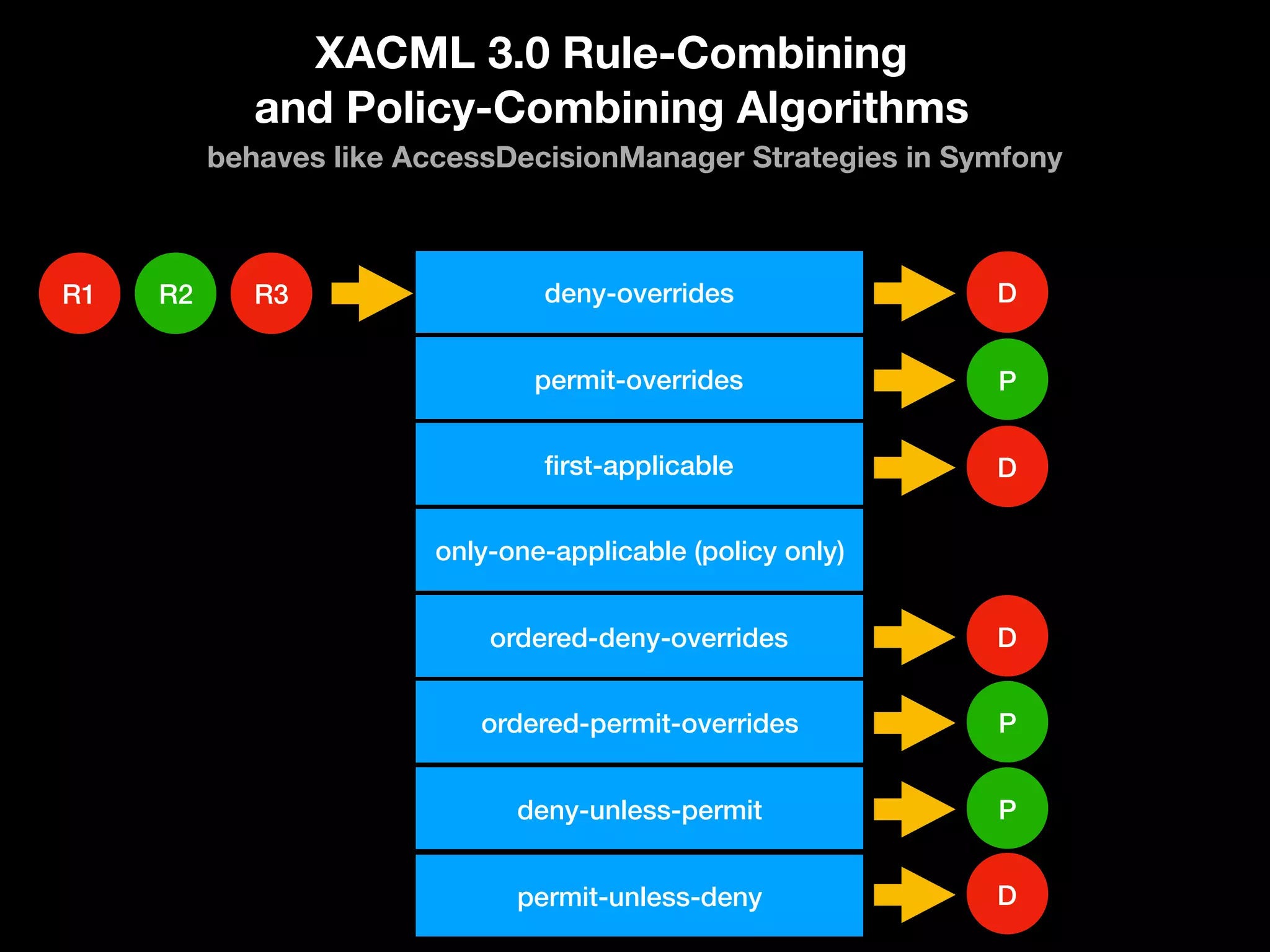
The document discusses various methods of authorization in Symfony and PHP applications, focusing on role-based access control (RBAC), access control lists (ACLs), and attribute-based access control (ABAC) using Symfony voters. It outlines the advantages and limitations of each approach, emphasizing that while XACML offers a comprehensive solution, Symfony voters are often sufficient for most use cases due to their ease of implementation. The document concludes by highlighting the importance of choosing the right access control method based on the specific needs and complexity of the application.






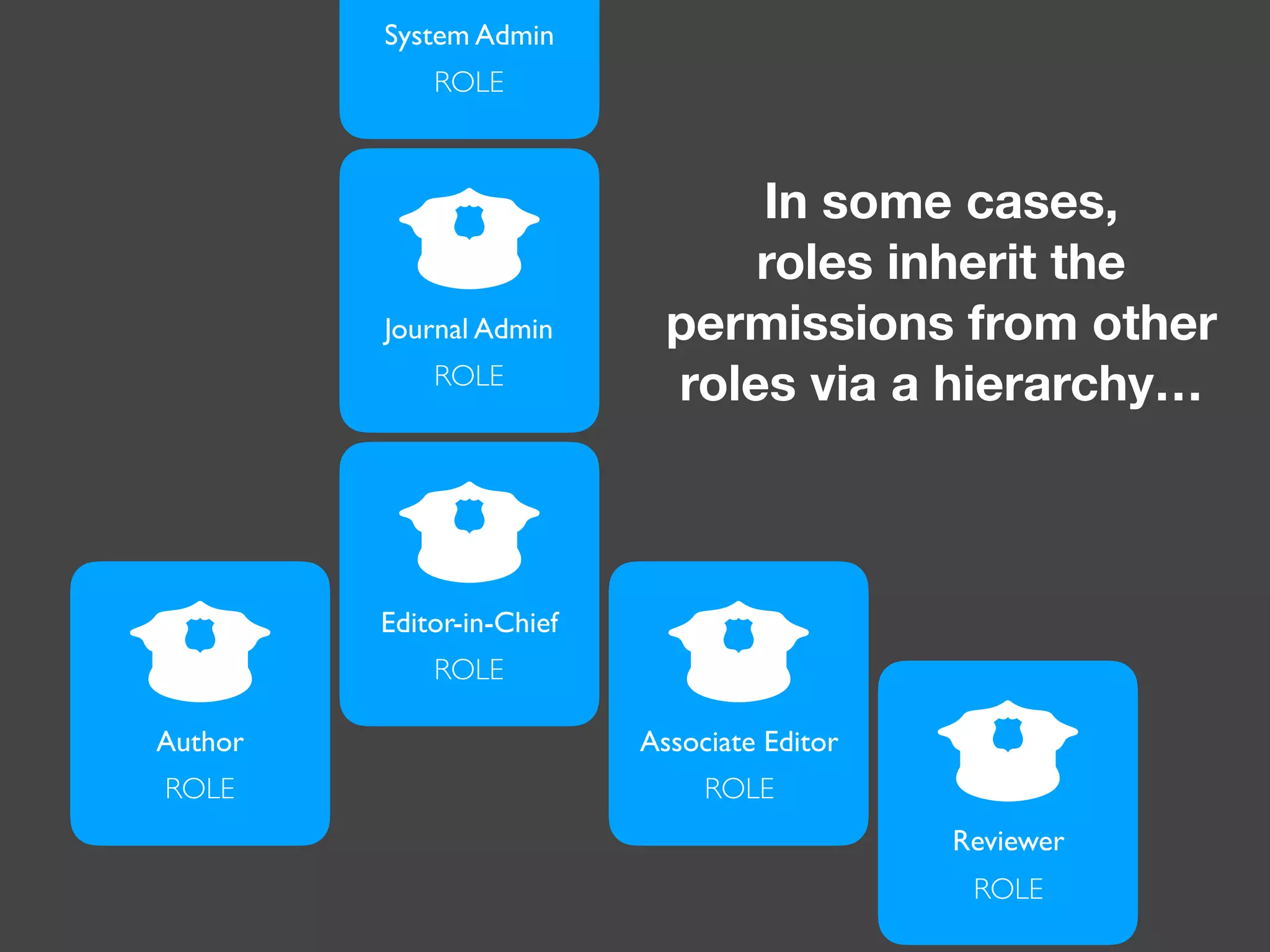
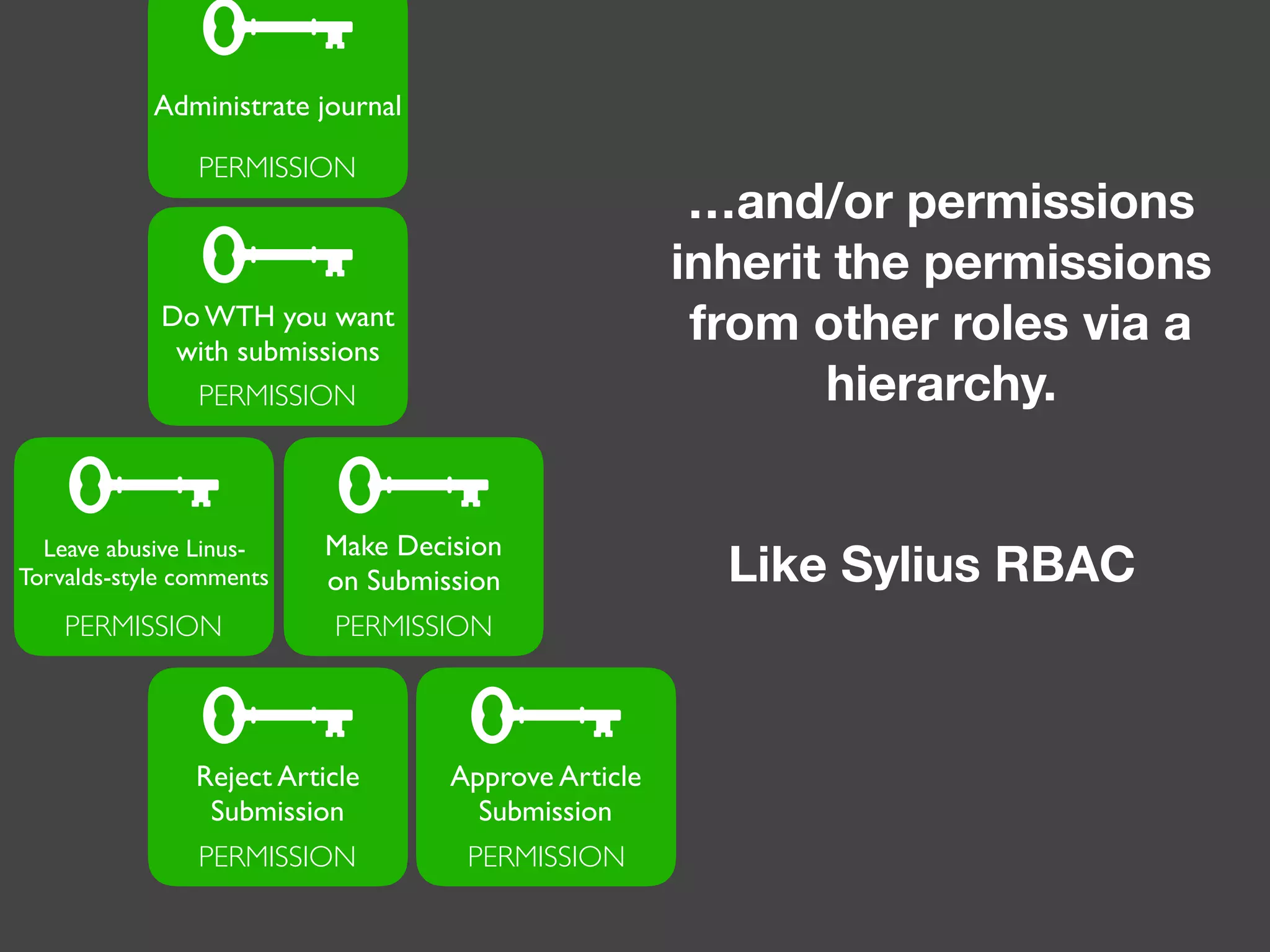
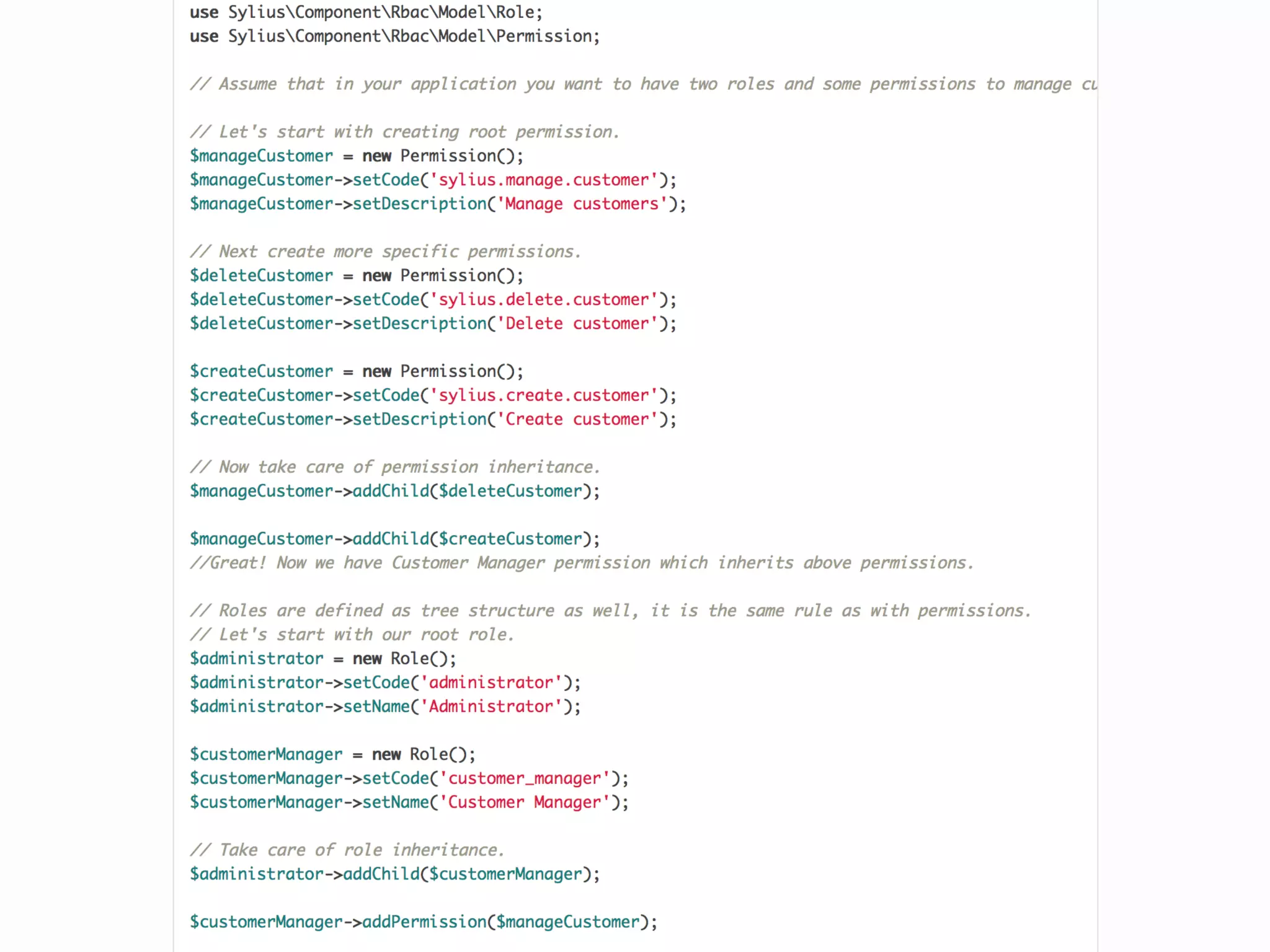
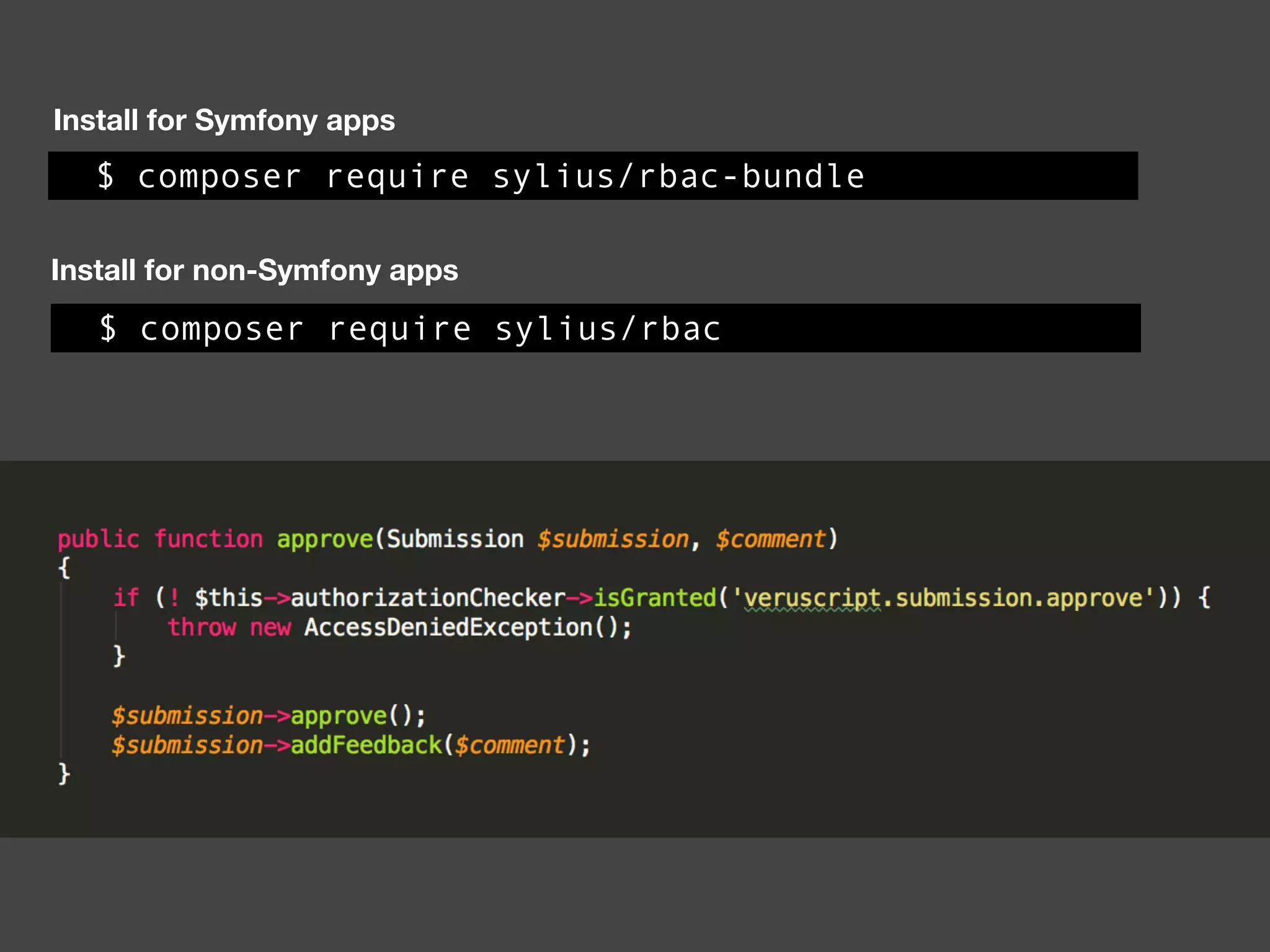



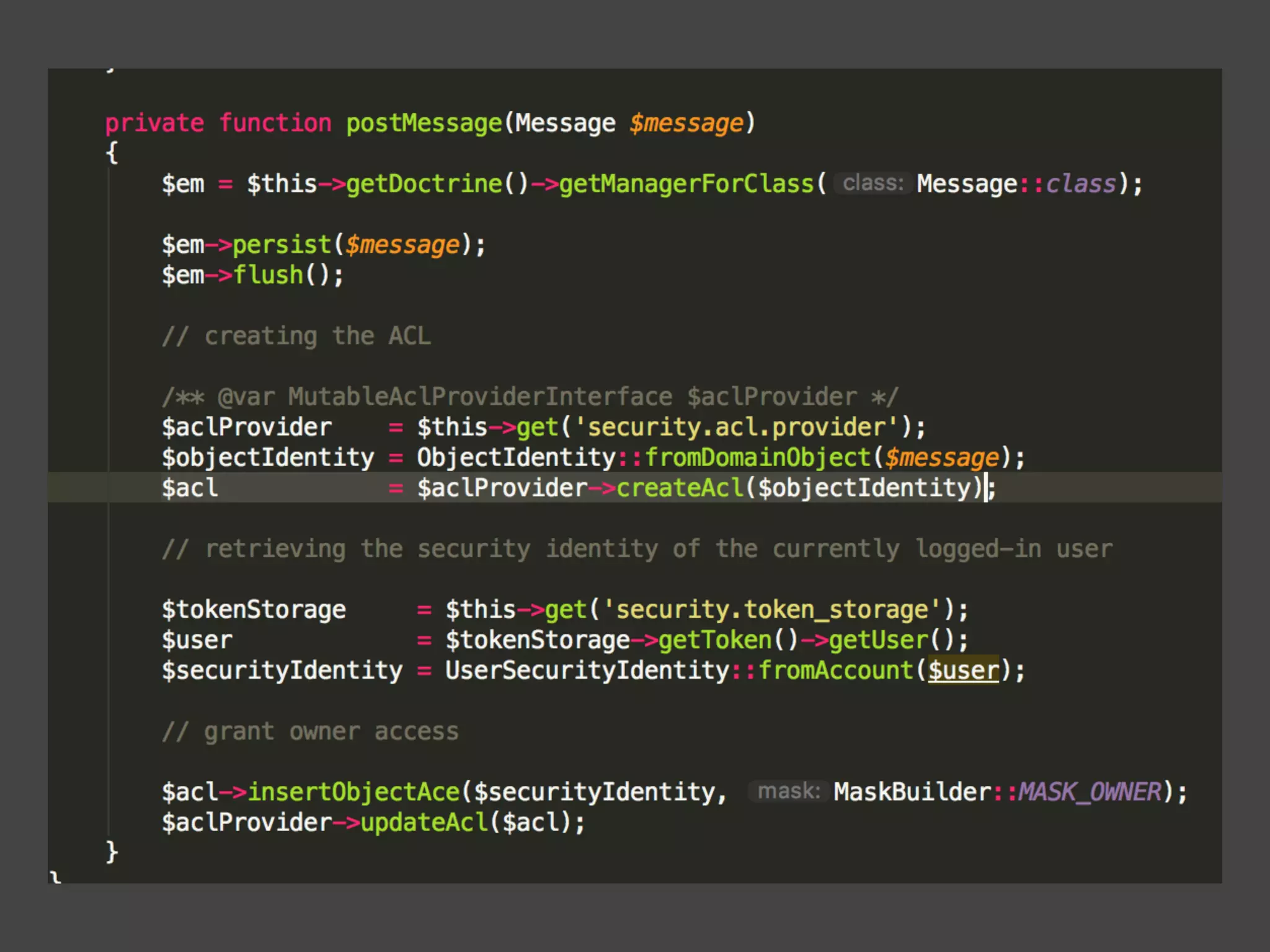
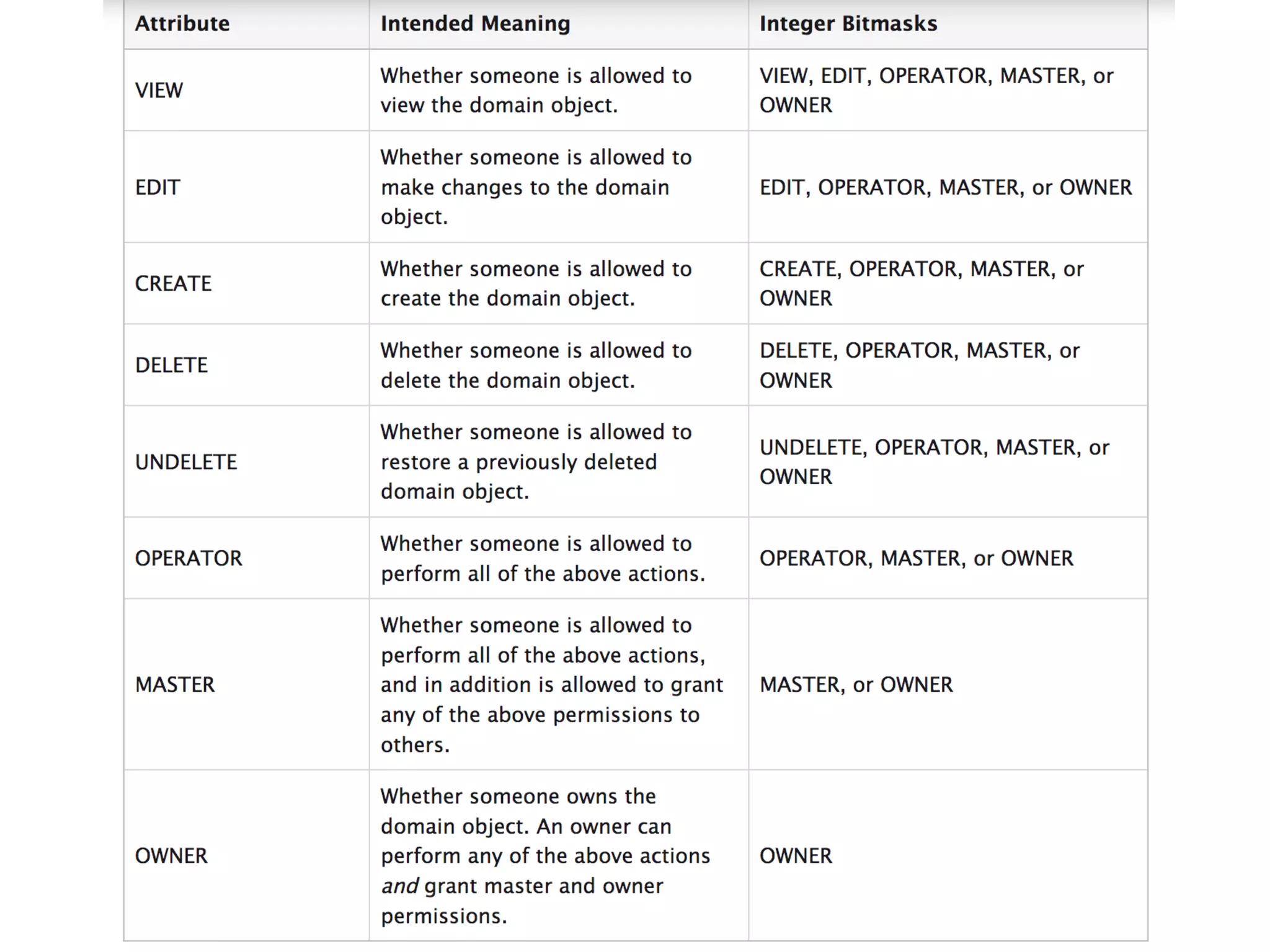
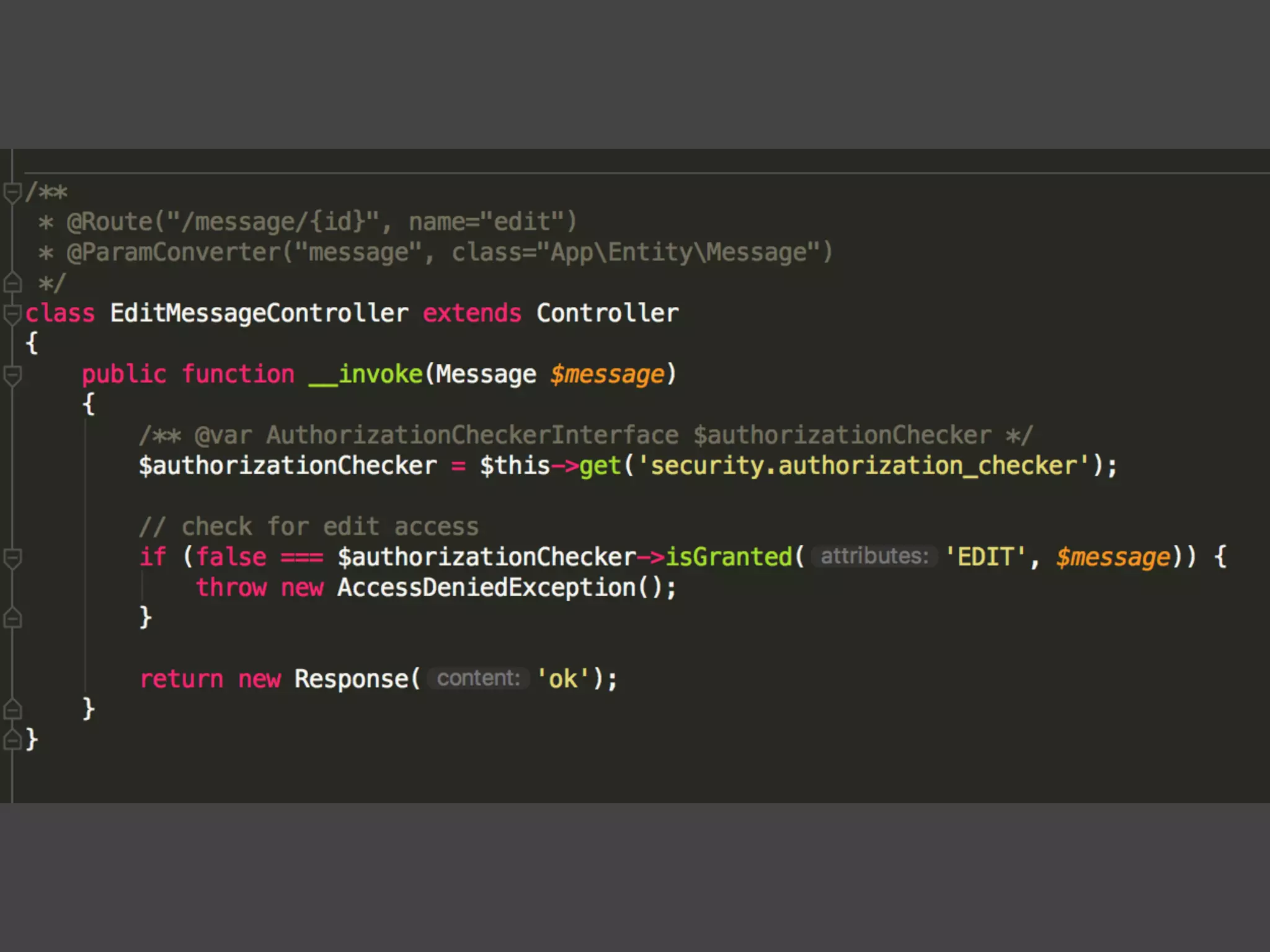
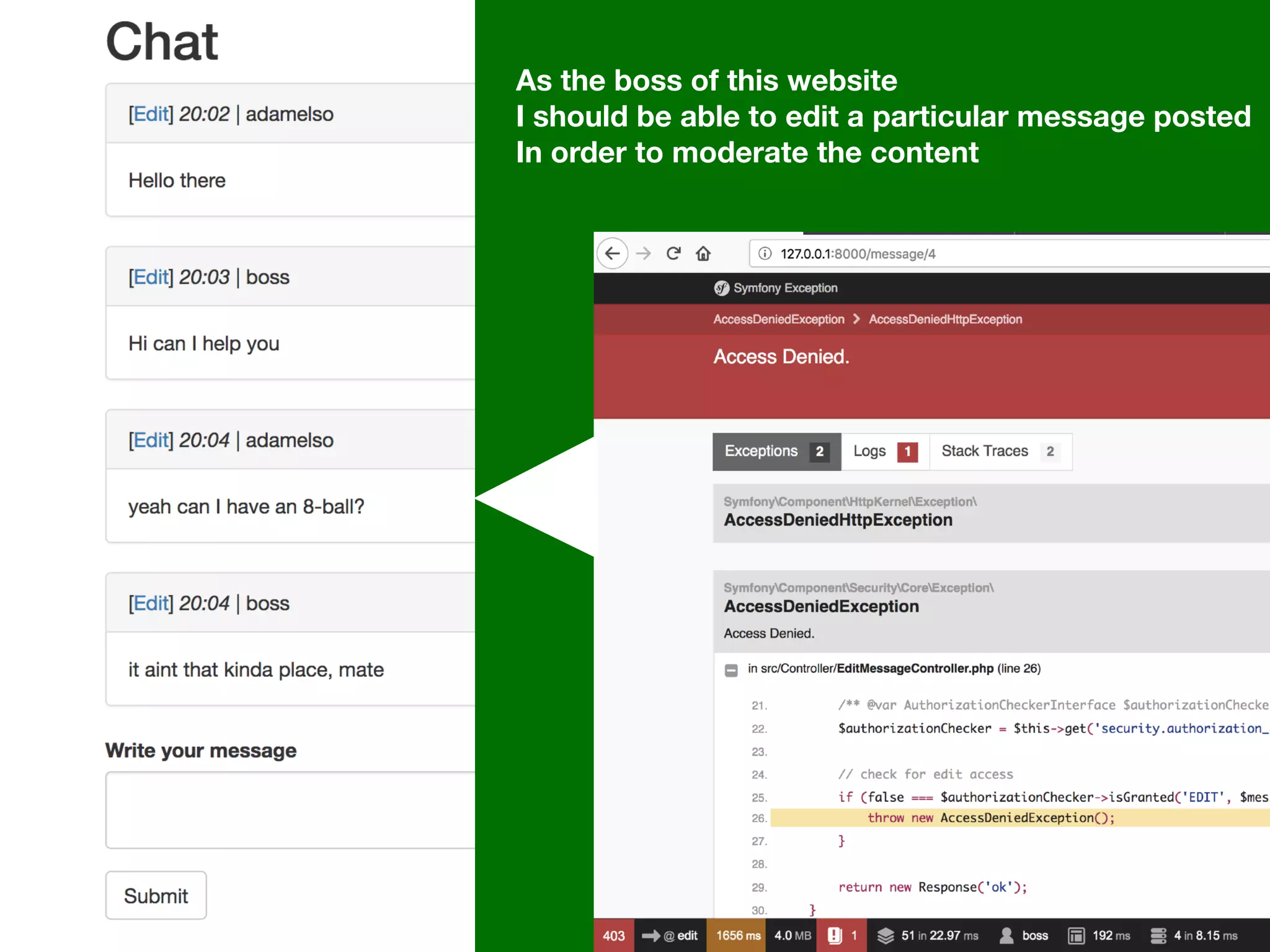
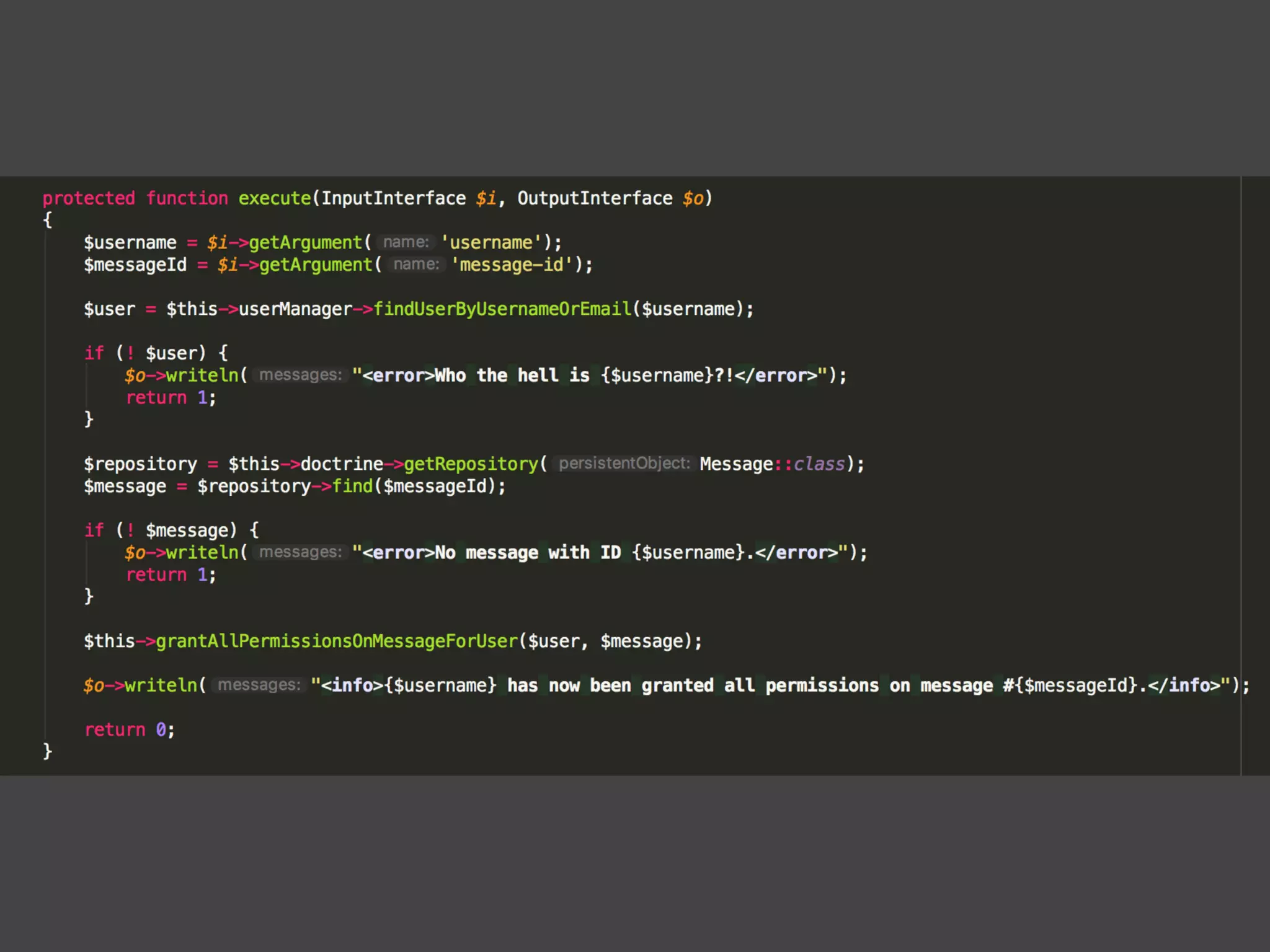
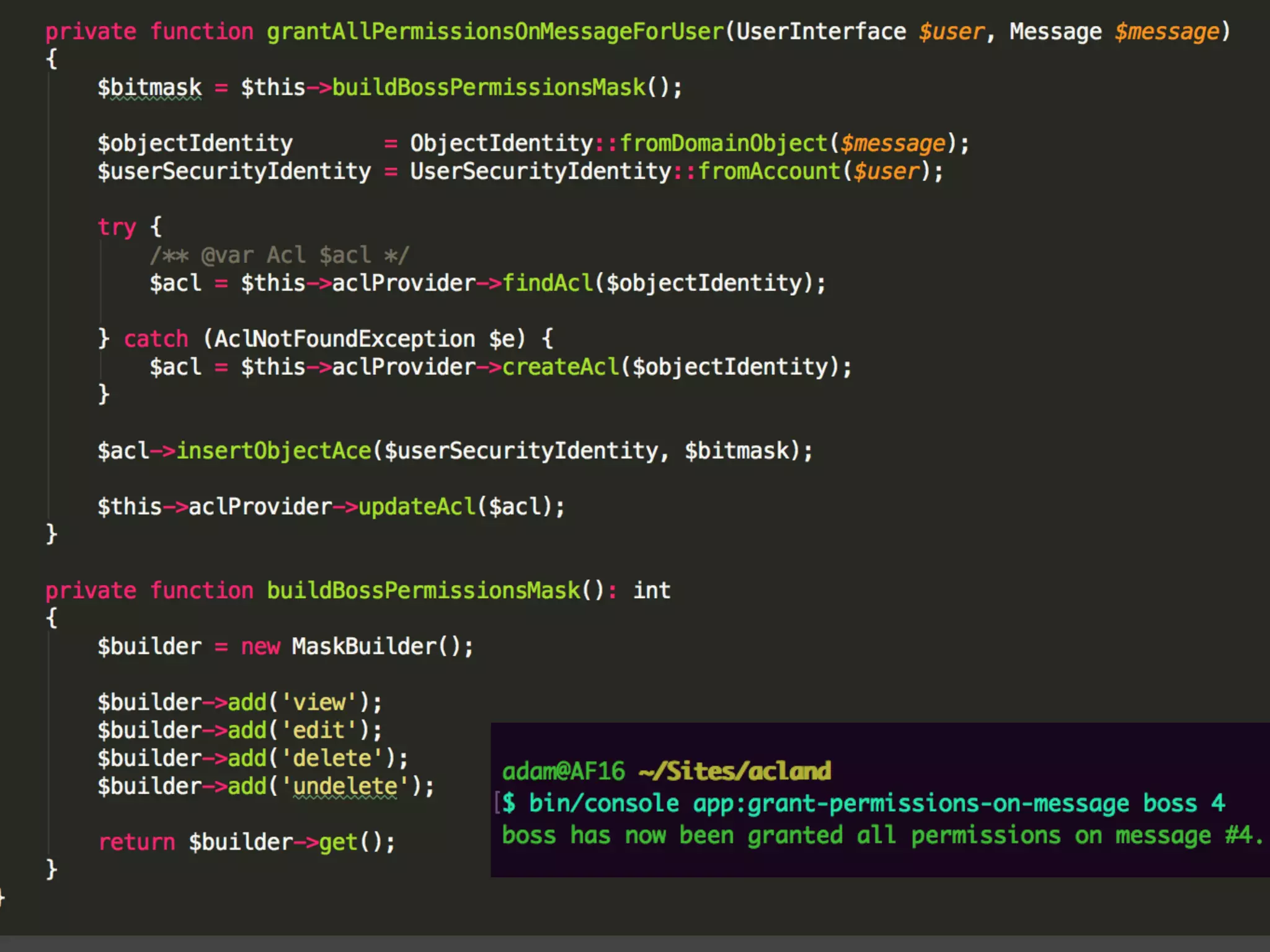
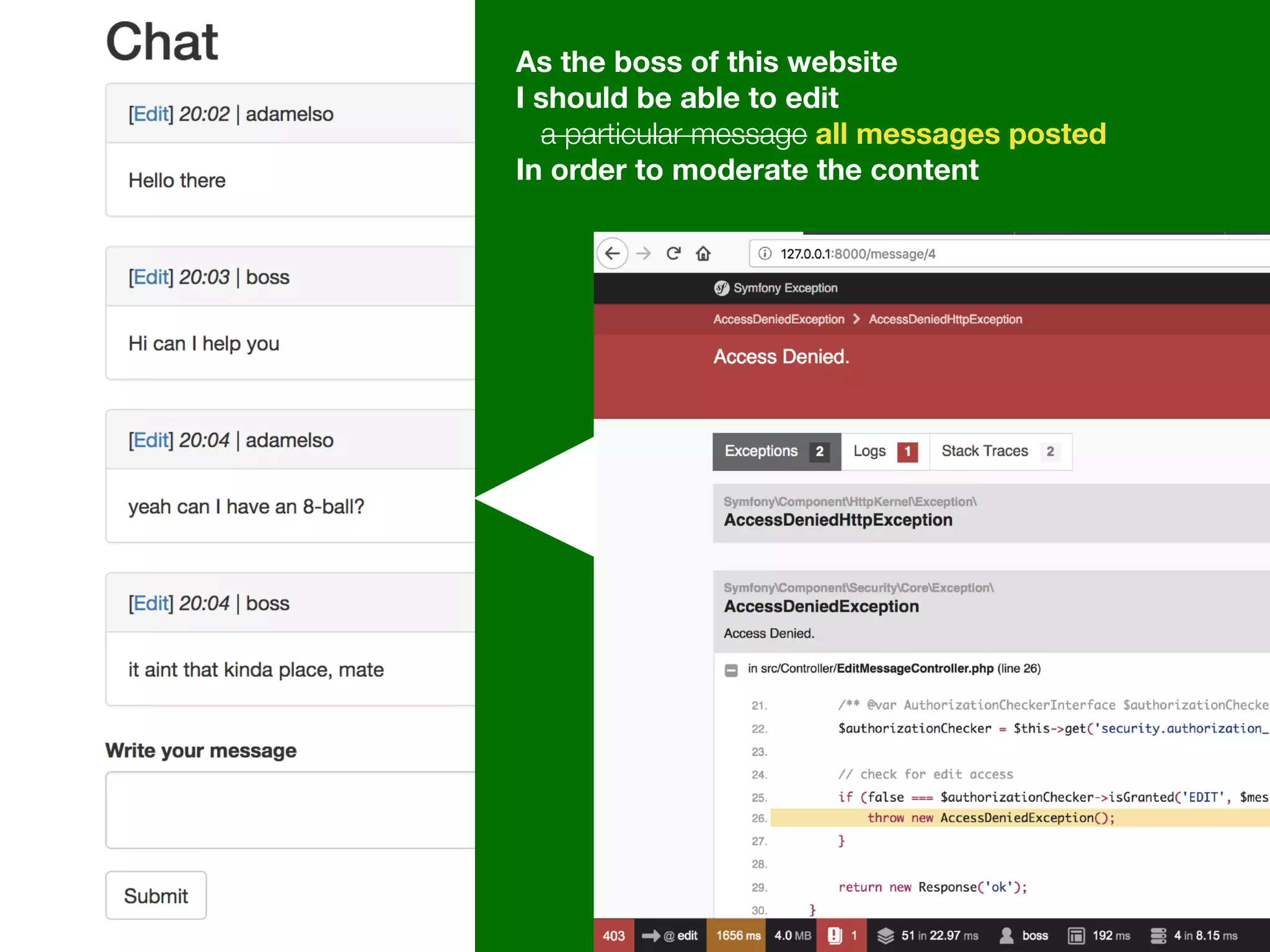
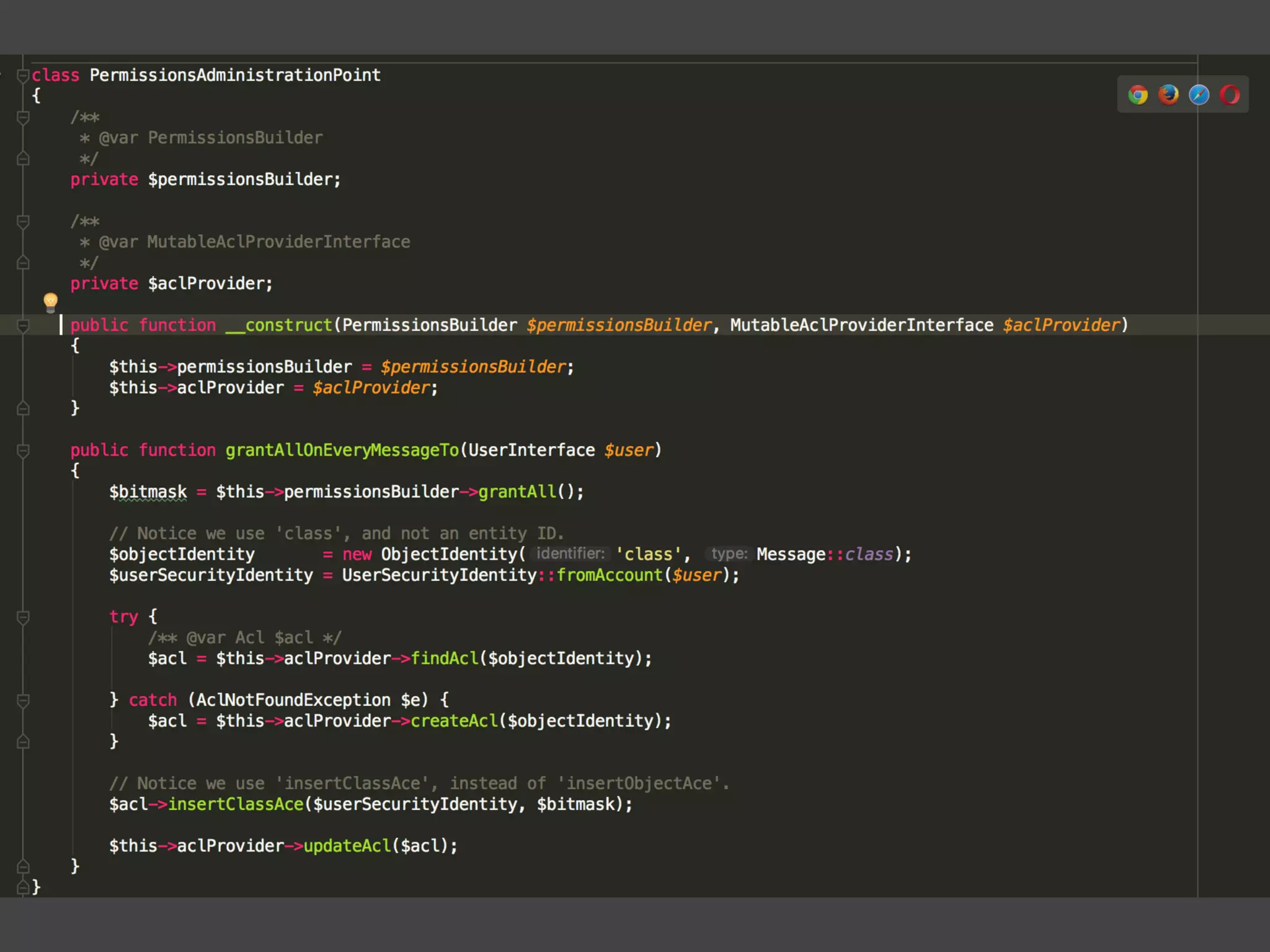
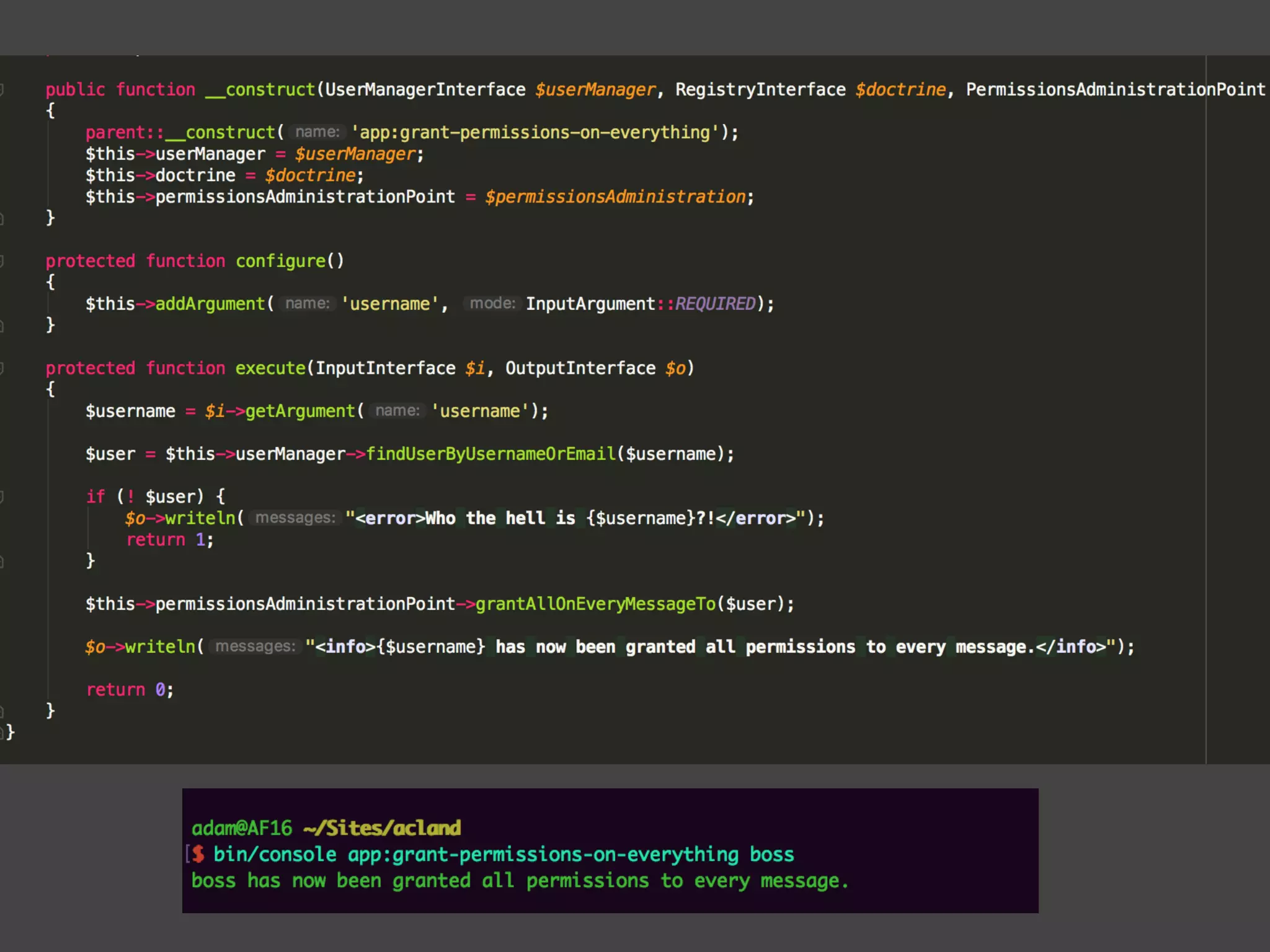
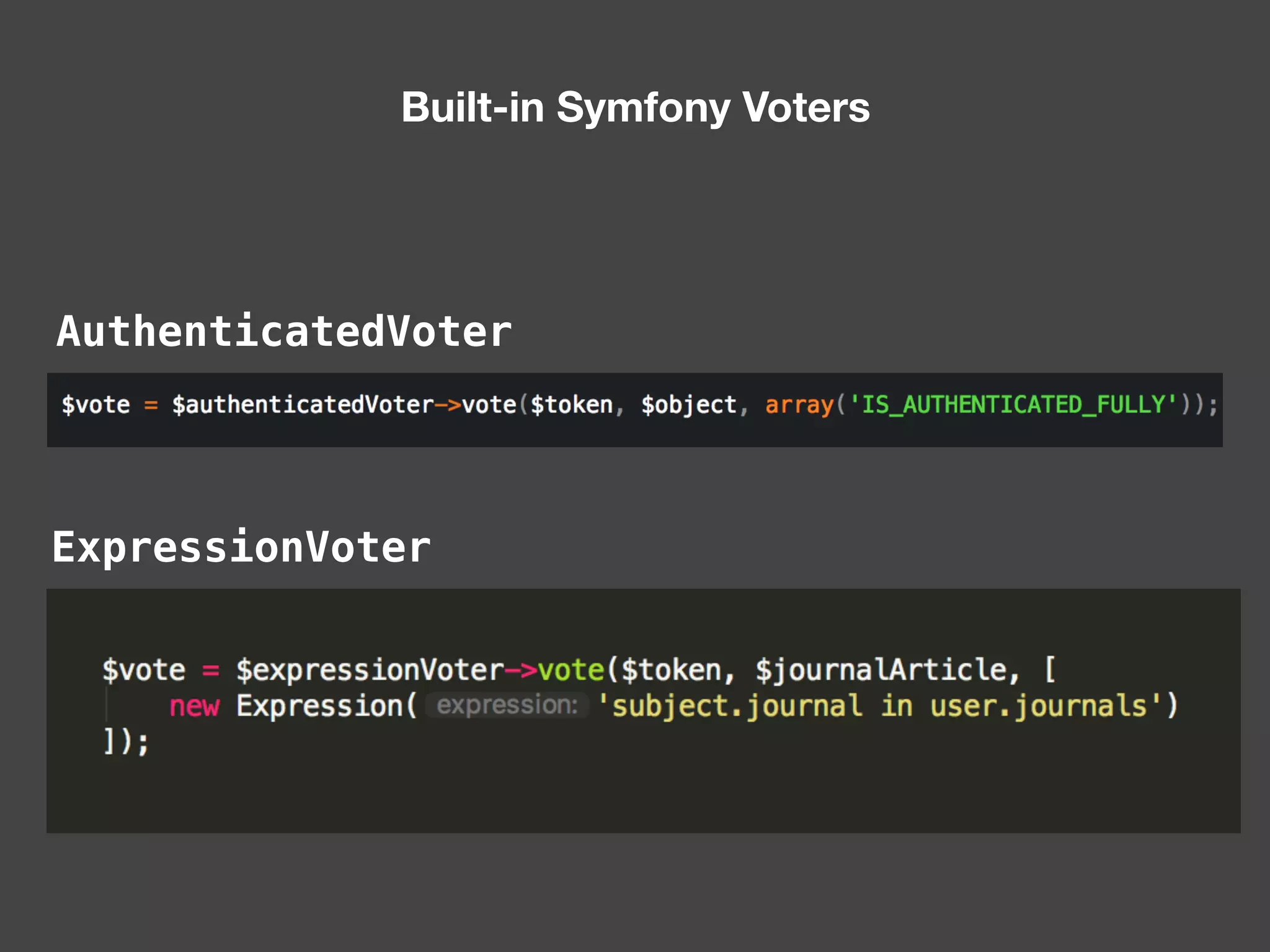
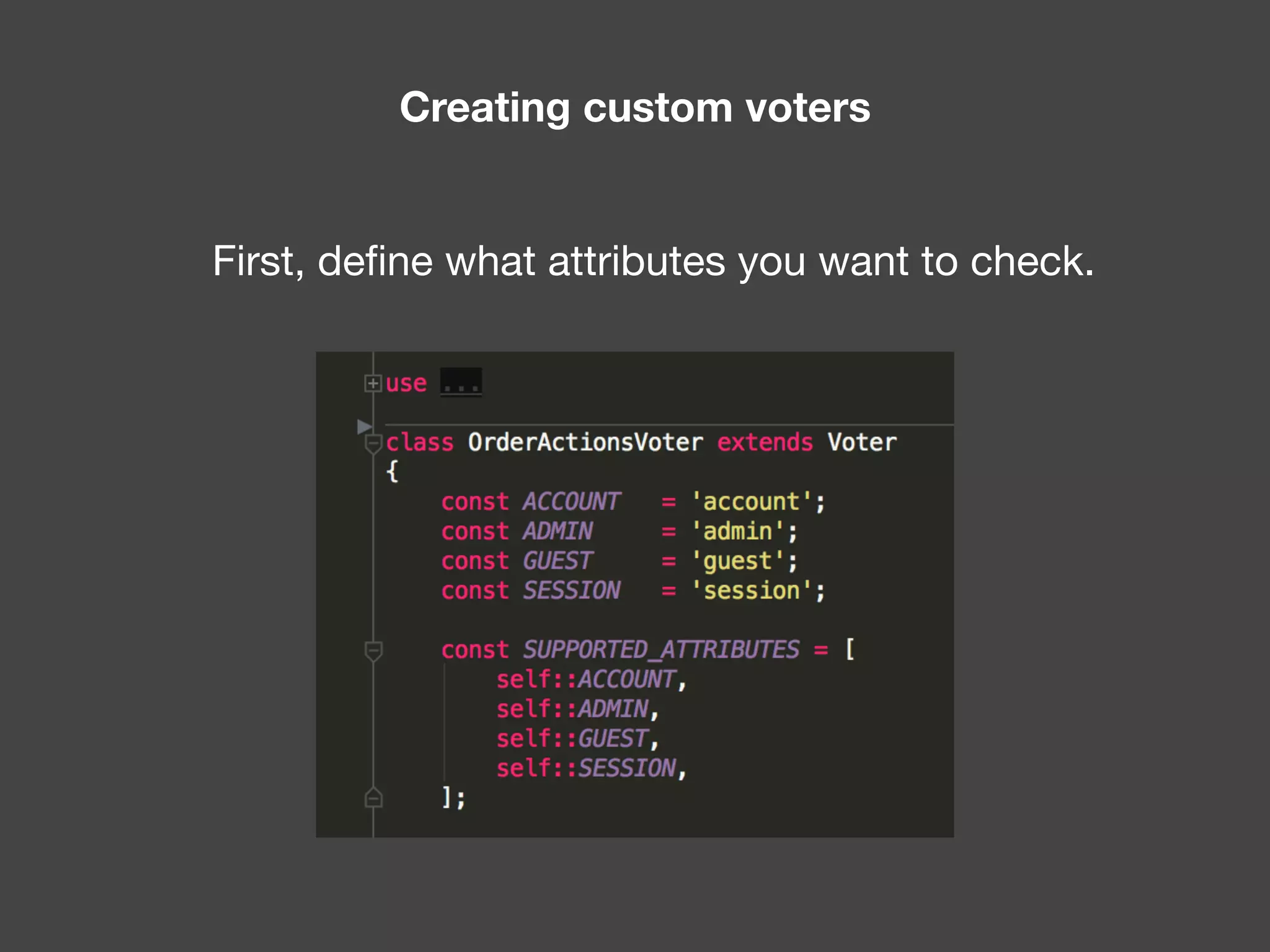
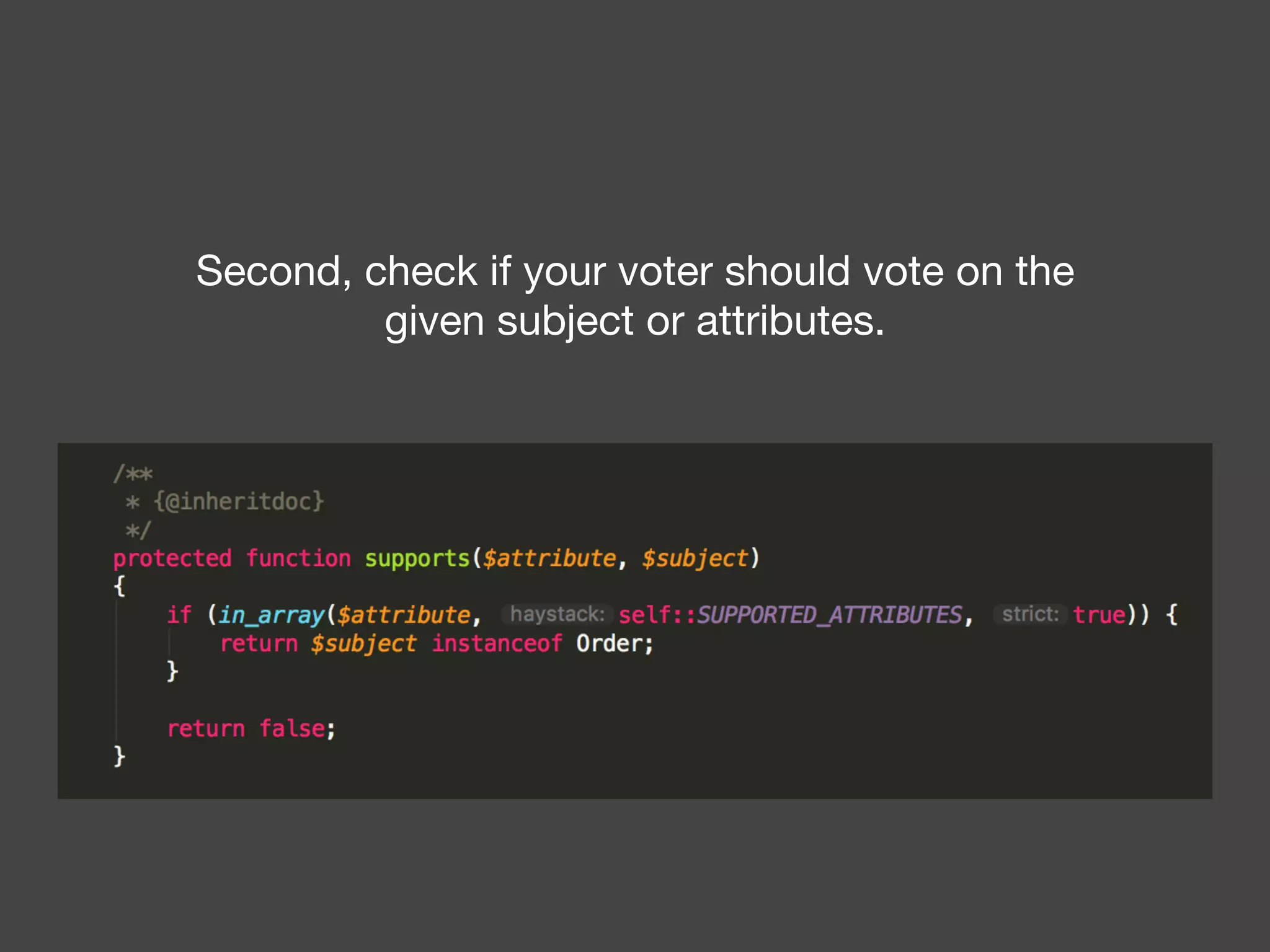
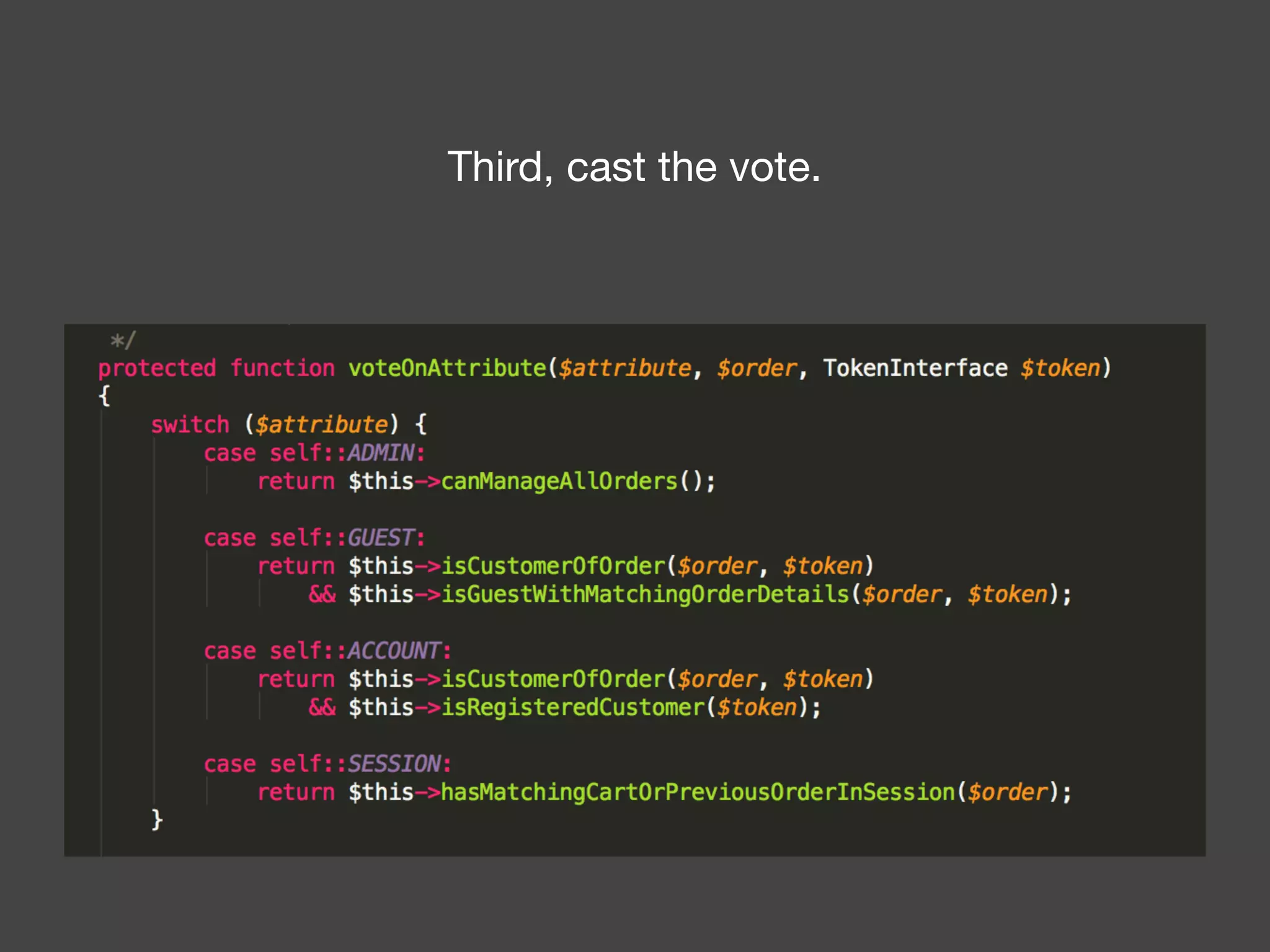
![Alternatives to ACLs Using [ACLs] isn't trivial, and for simpler use cases, it may be overkill. If your permission logic could be described by just writing some code (e.g. to check if a Blog is owned by the current User), then consider using voters. A voter is passed the object being voted on, which you can use to make complex decisions and effectively implement your own ACL. Enforcing authorization (e.g. the isGranted() part) will look similar to what you see in this article, but your voter class will handle the logic behind the scenes, instead of the ACL system. “ https://symfony.com/doc/3.4/security/acl.html](https://image.slidesharecdn.com/abac-in-symfony-by-veruscript-180831213515/75/Attribute-Based-Access-Control-in-Symfony-42-2048.jpg)

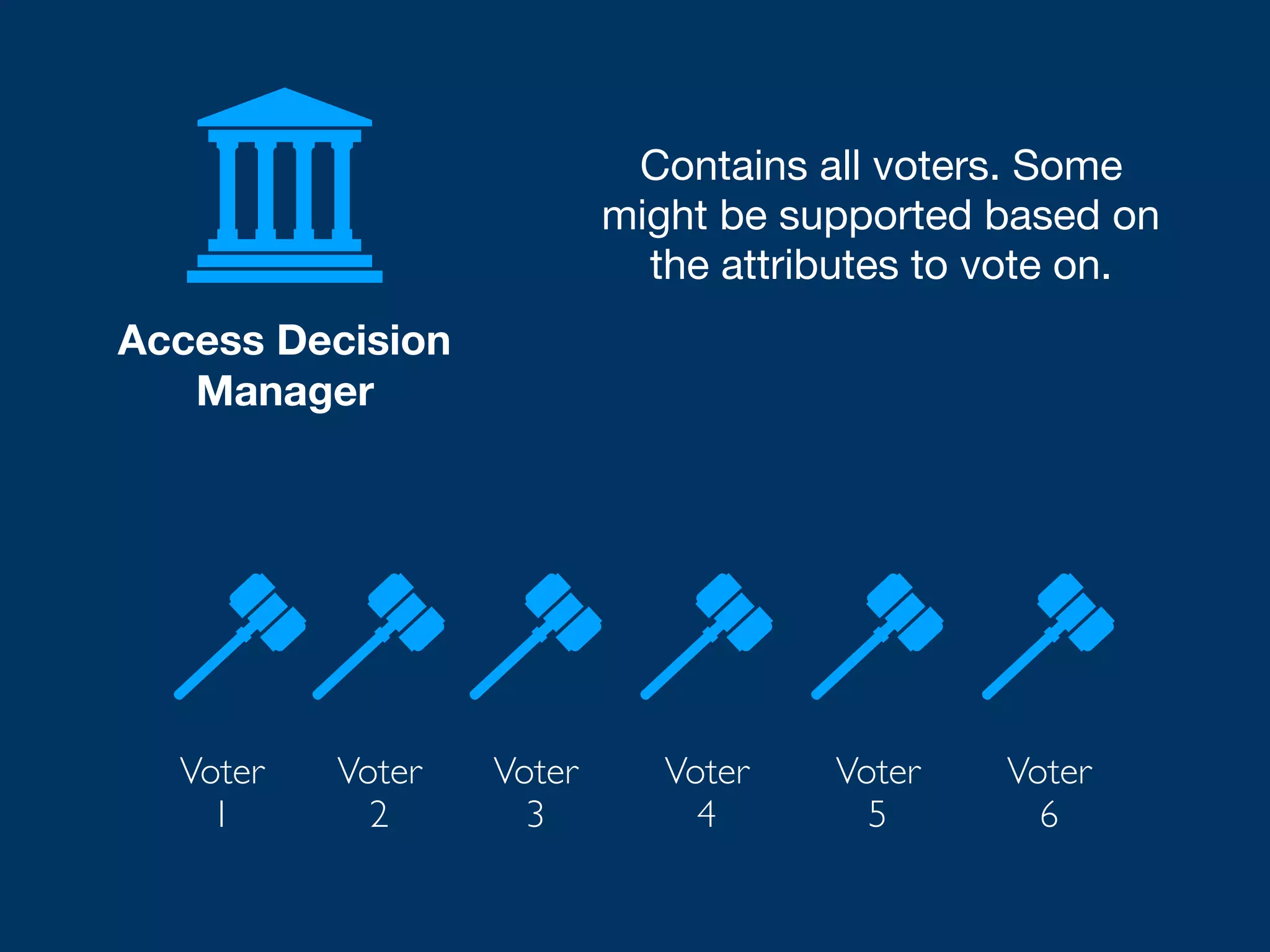



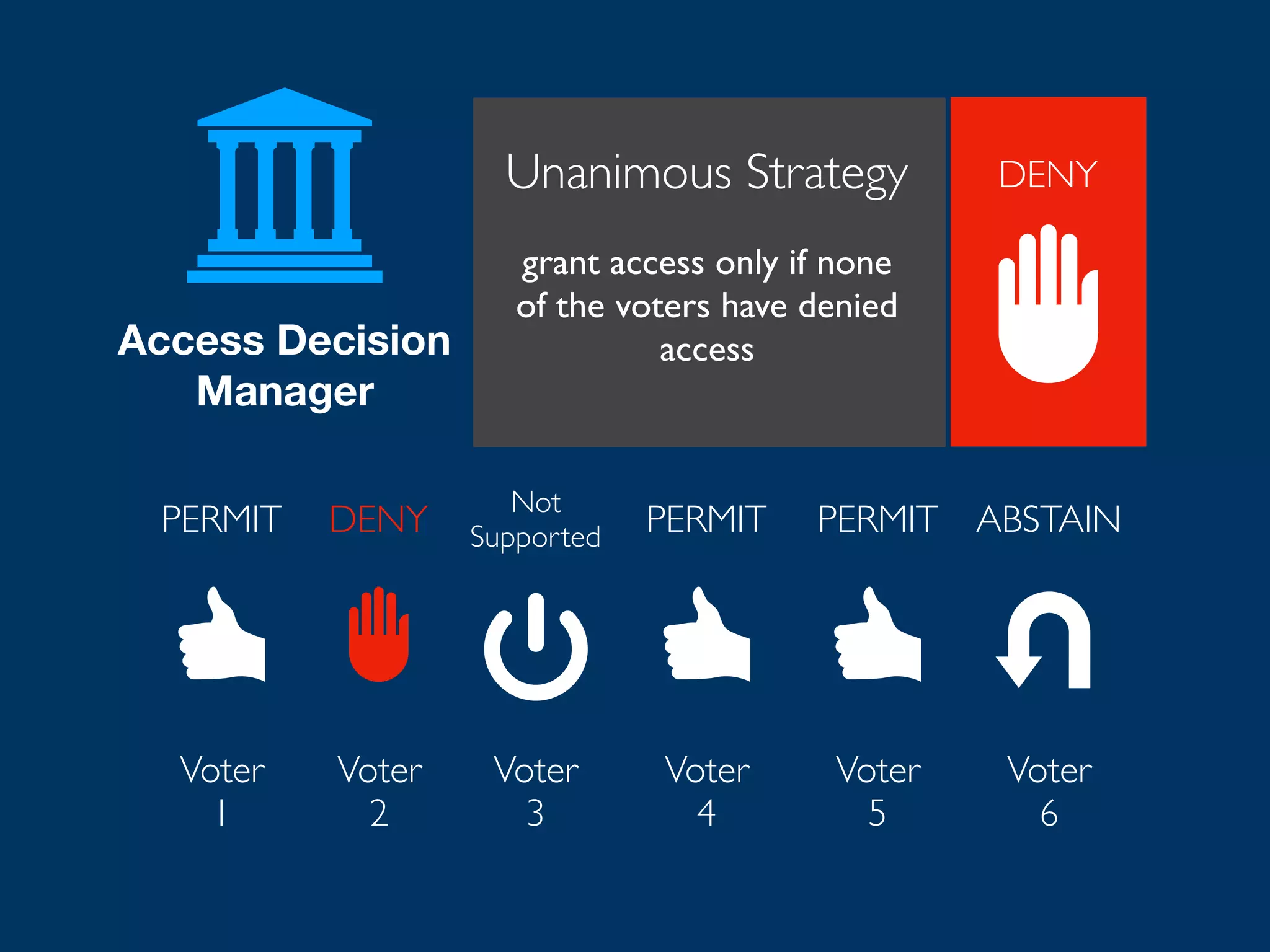
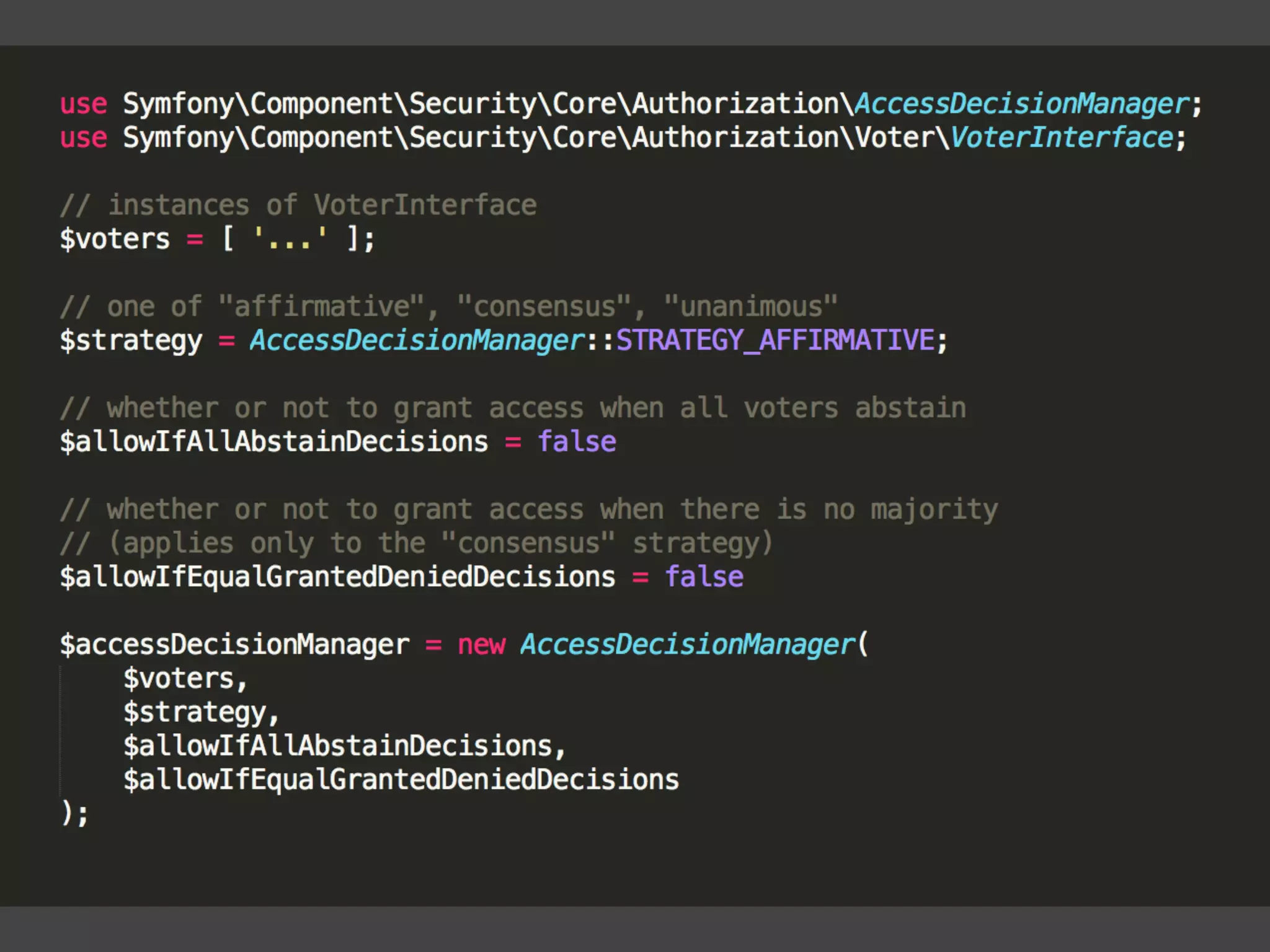
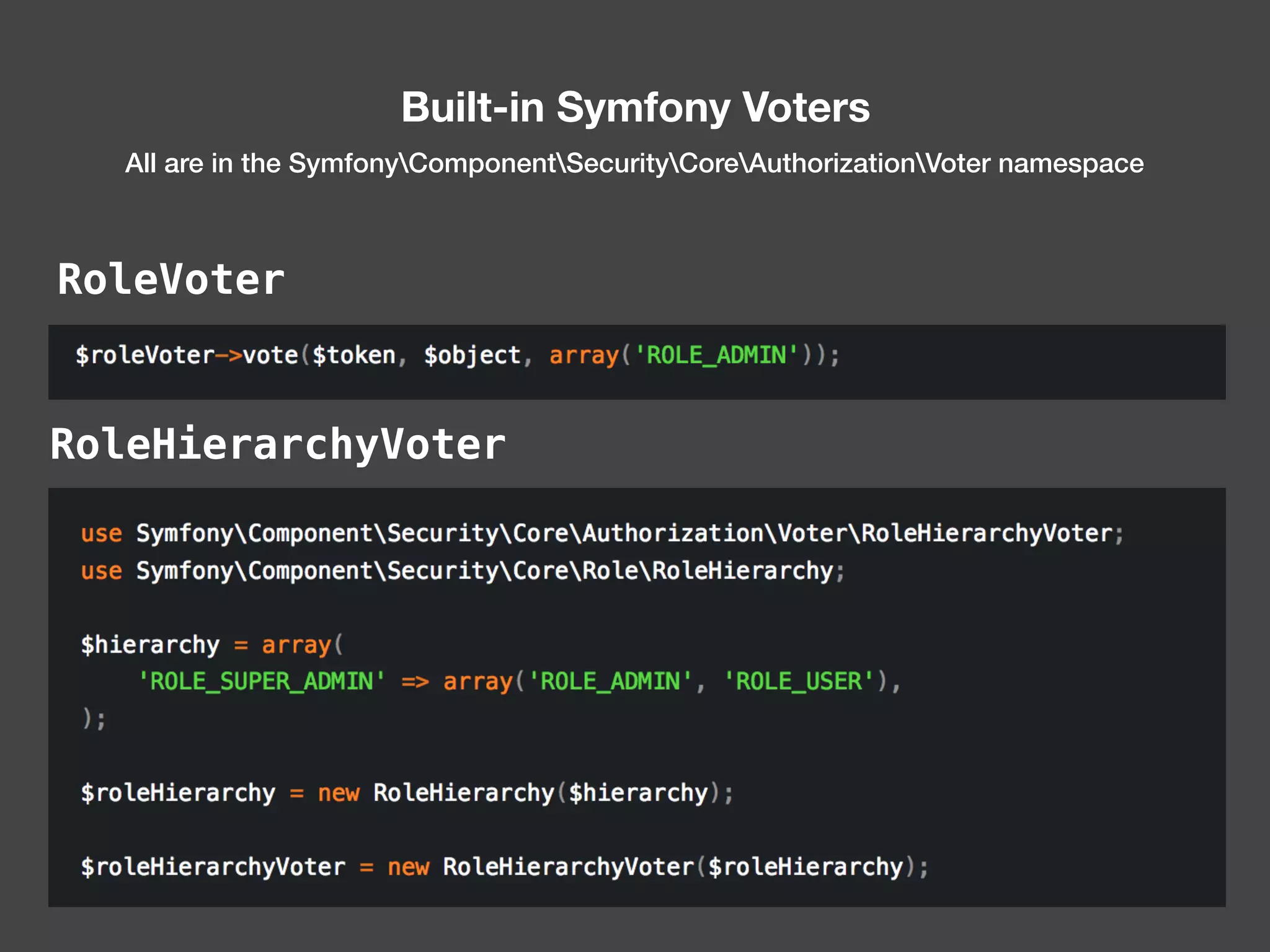

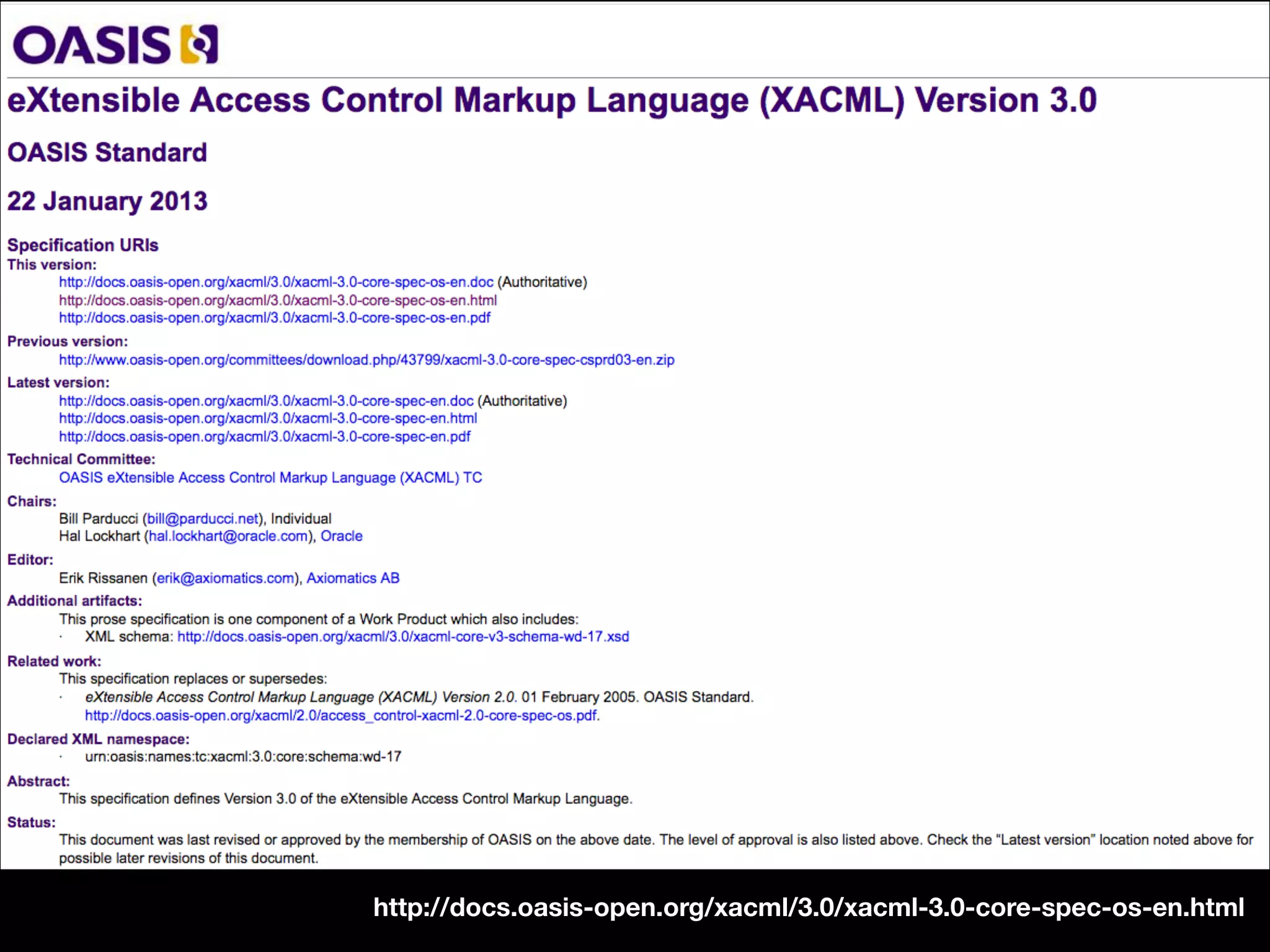
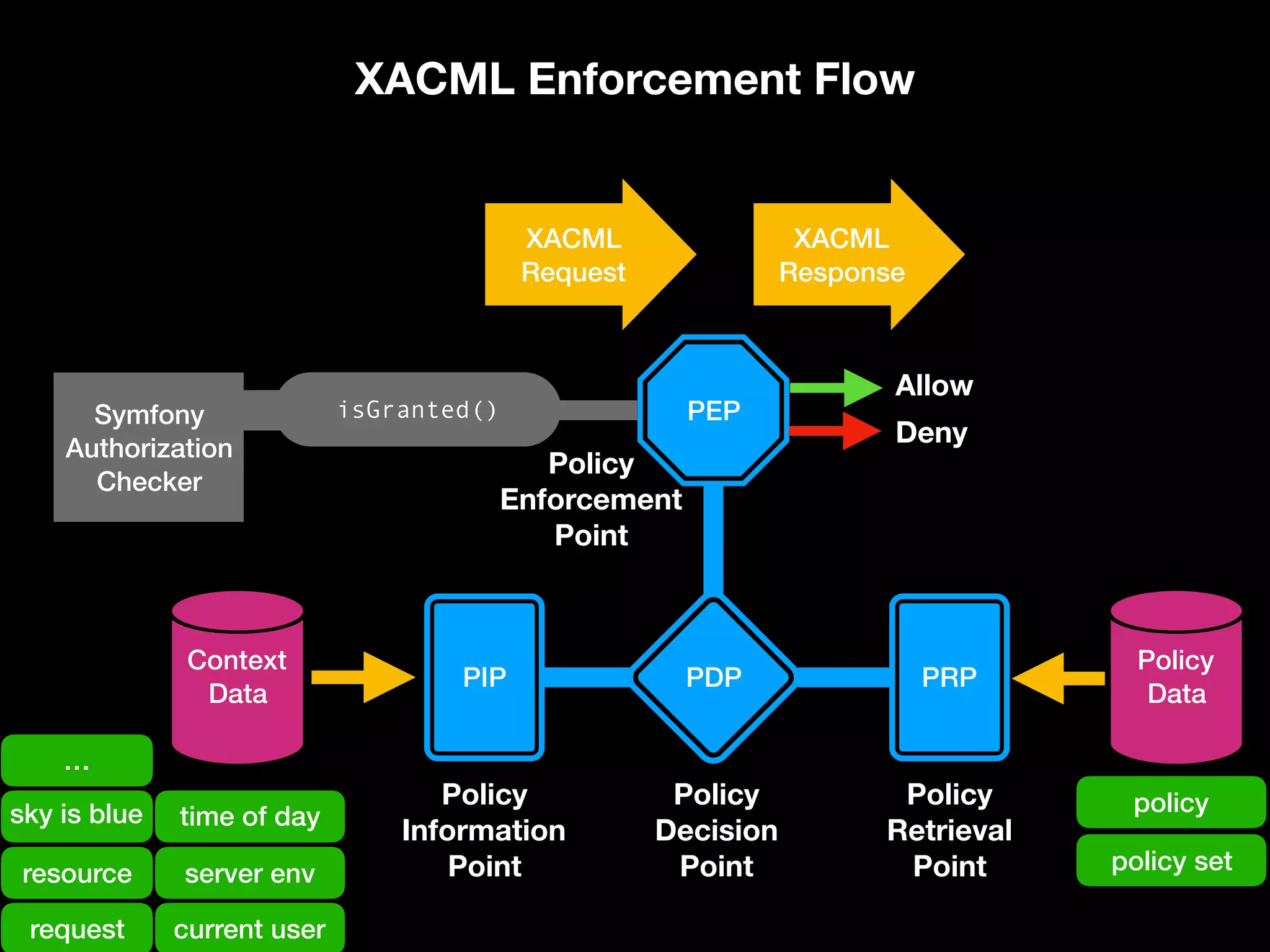
![[What is XACML?] XACML (eXtensible Access Control Markup Language) offers a standardized way to achieve externalized and dynamic authorization. This means that authorization decisions are made by an authorization service at run-time based on policies which determine what actions a user or service can perform on a given information asset and in a specific context. “ https://www.axiomatics.com/100-pure-xacml/](https://image.slidesharecdn.com/abac-in-symfony-by-veruscript-180831213515/75/Attribute-Based-Access-Control-in-Symfony-60-2048.jpg)
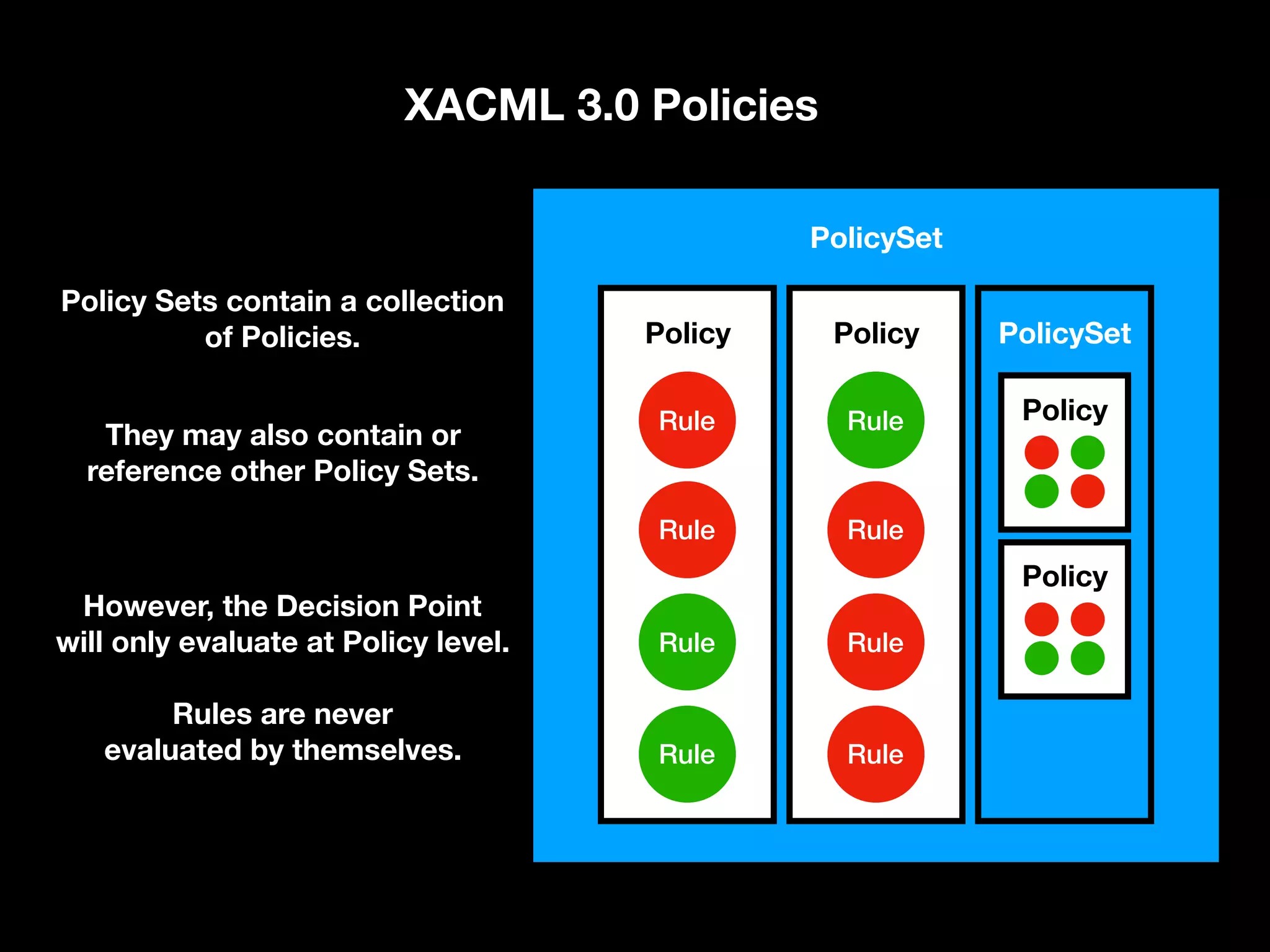
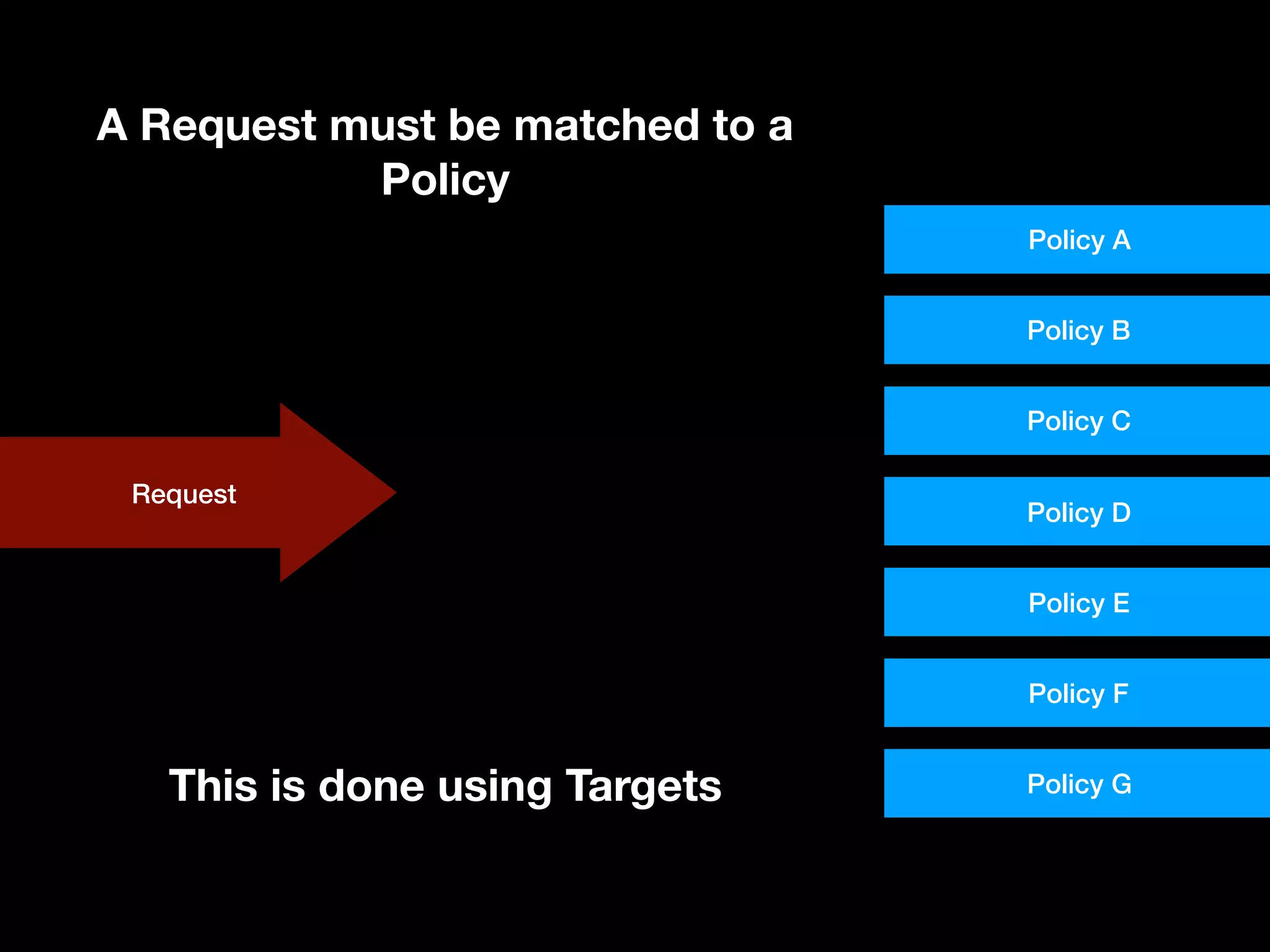
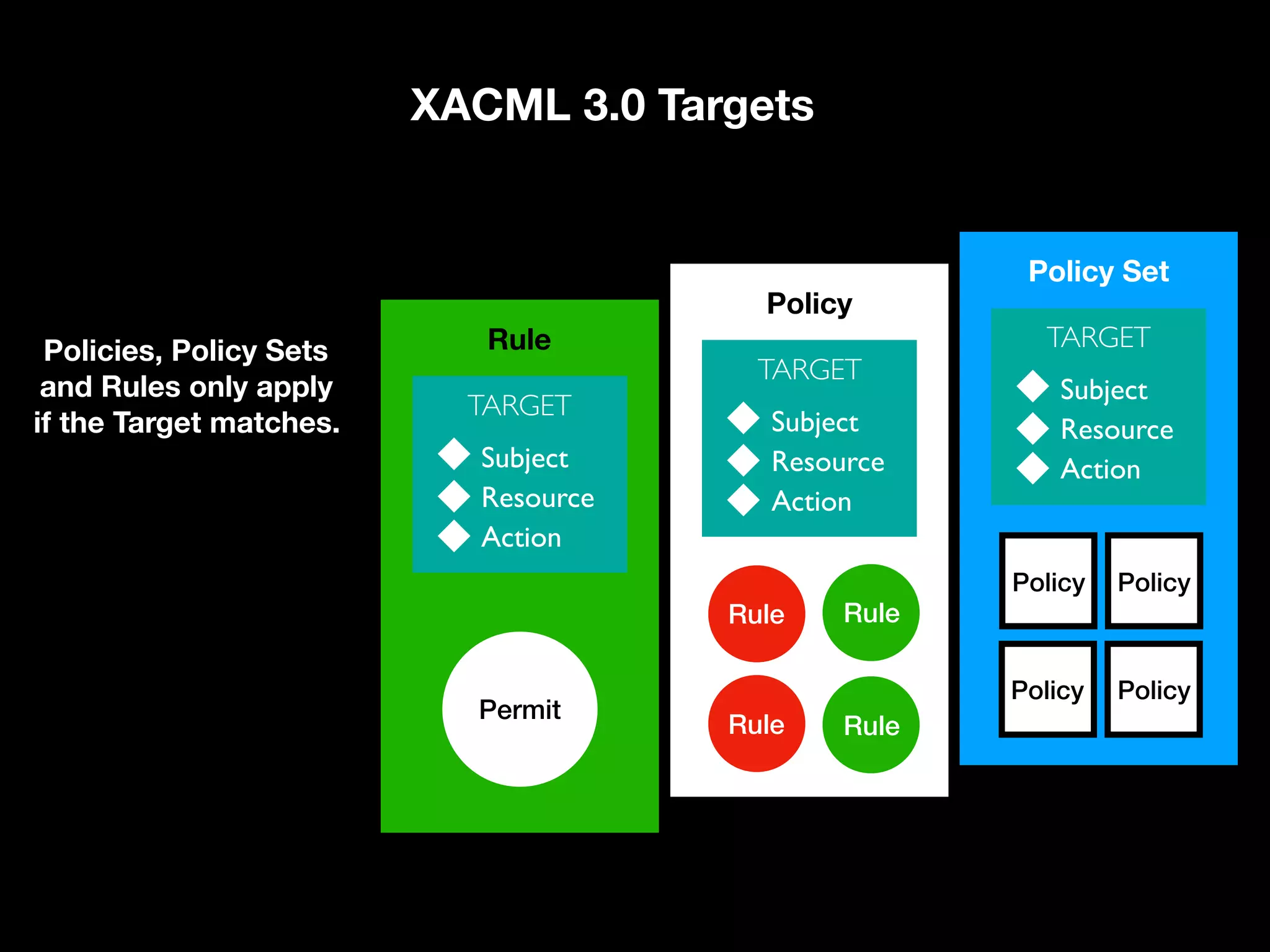
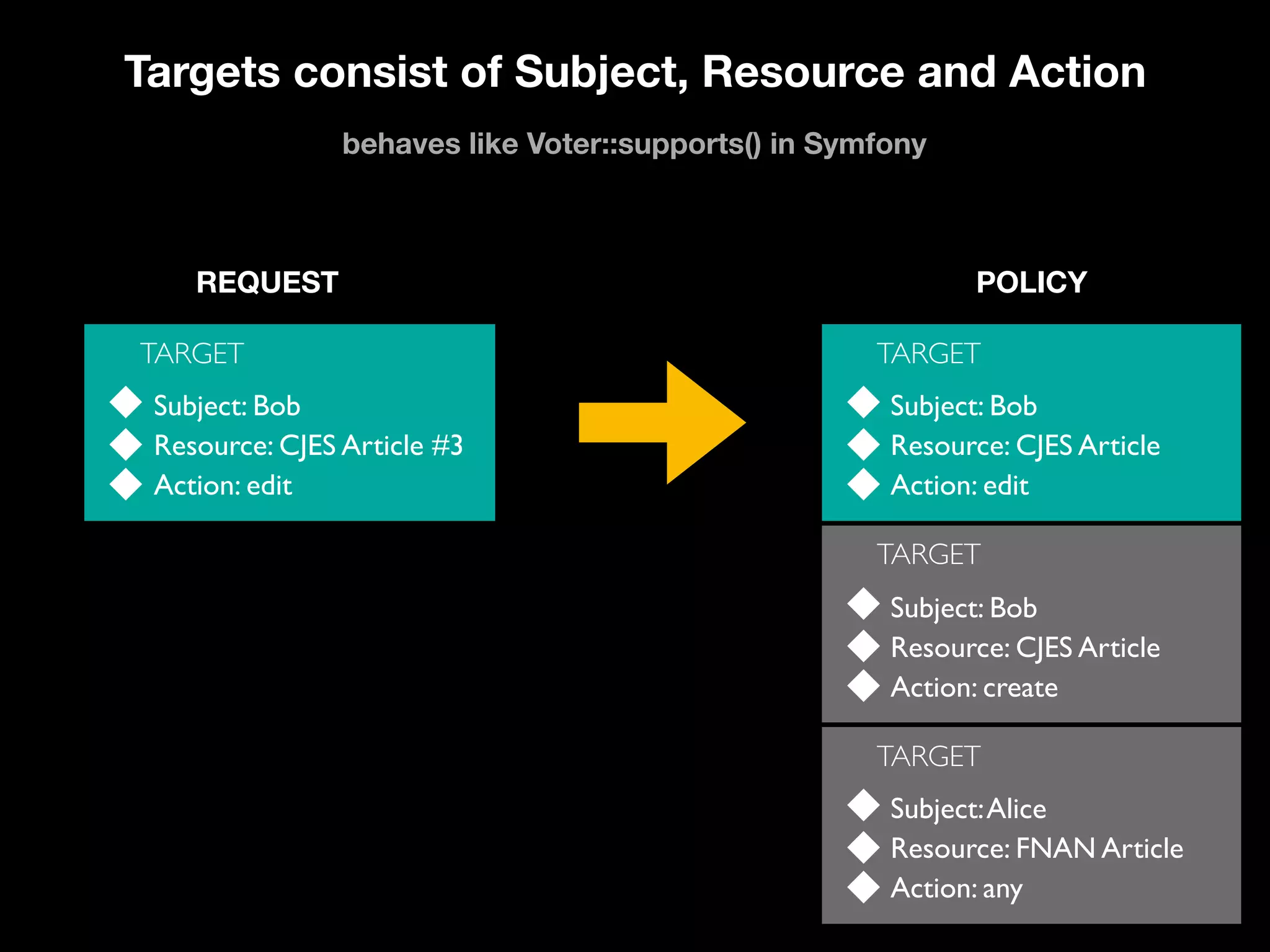
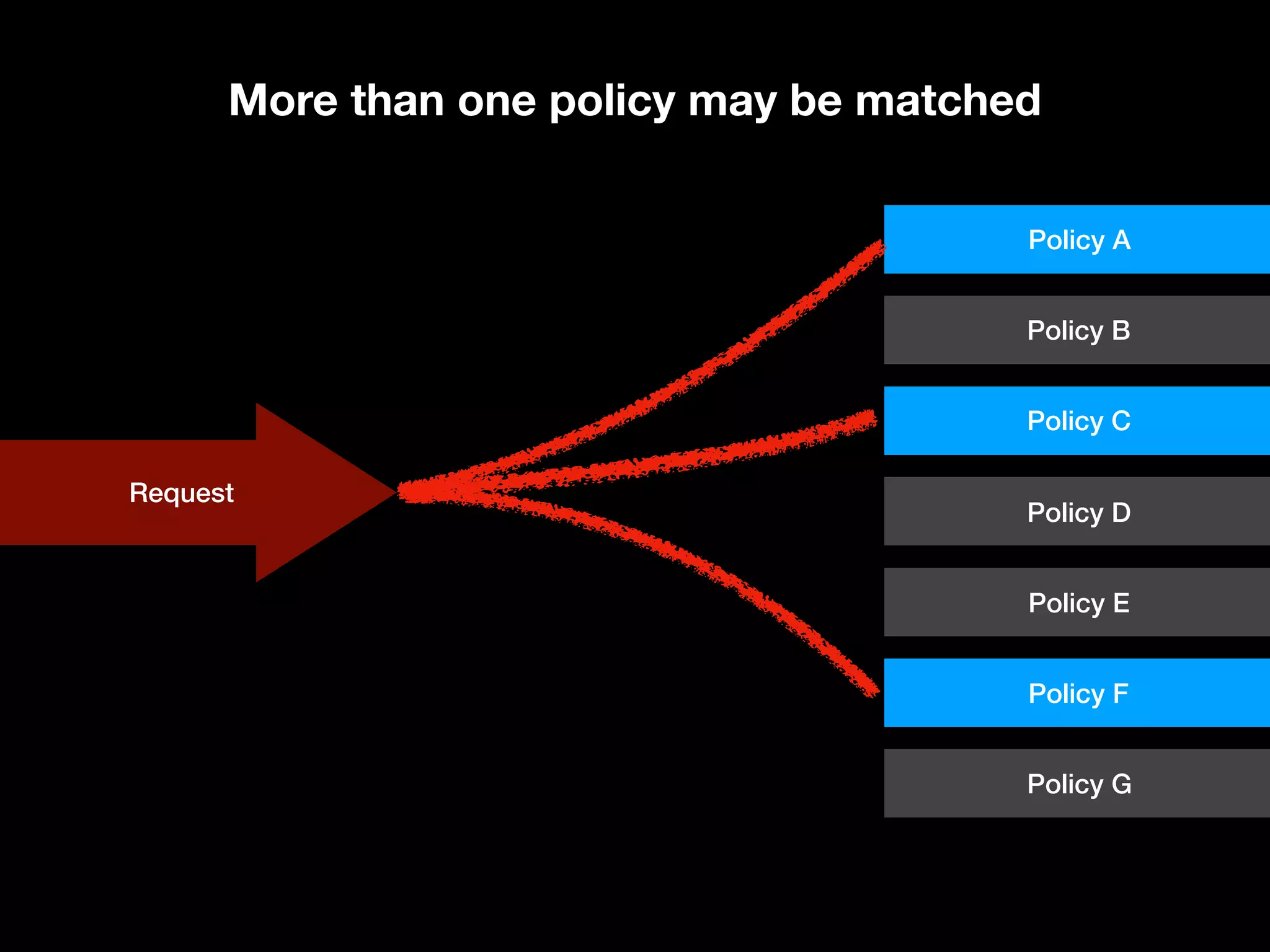
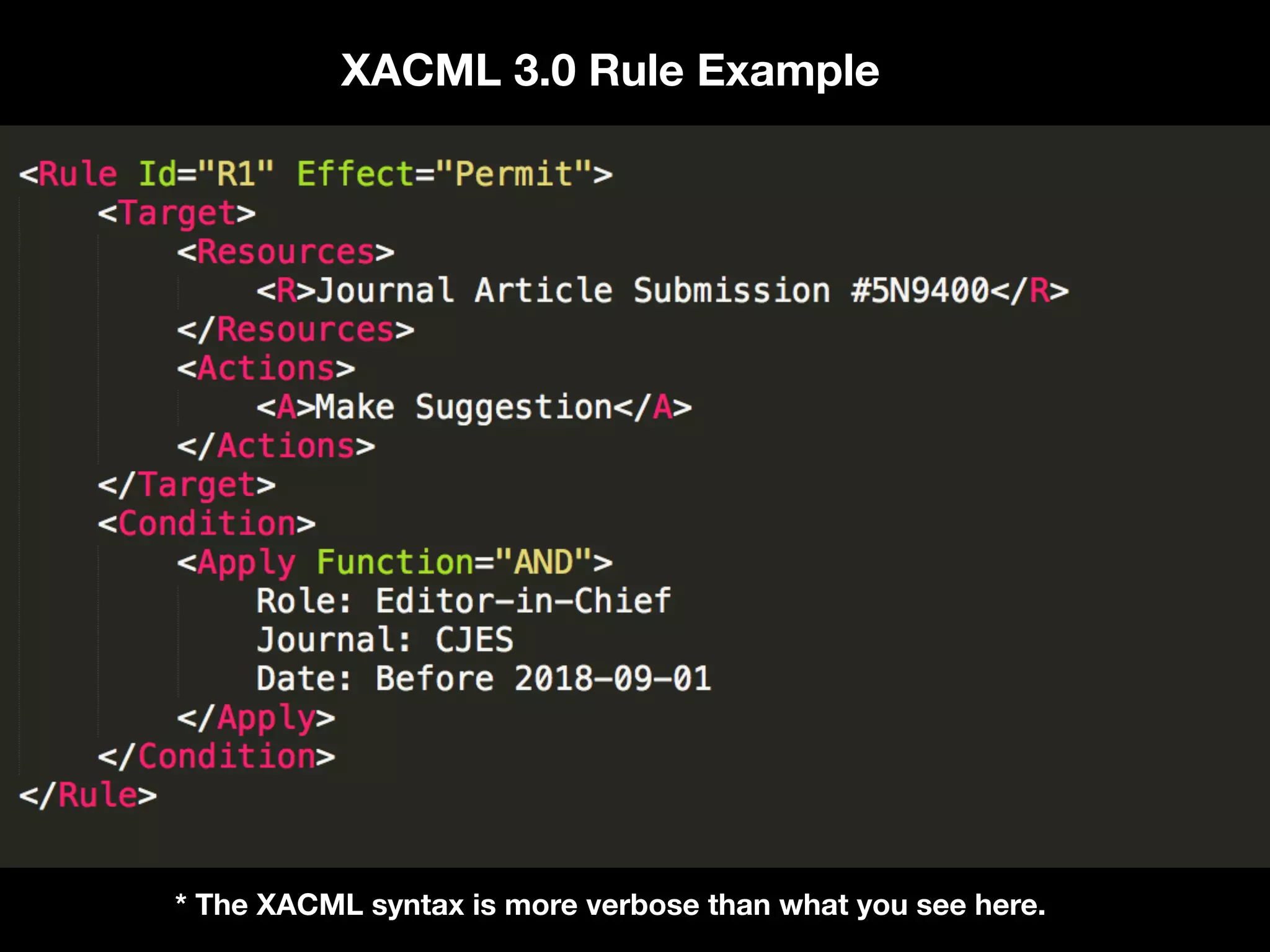
![Targets and Rules Part of what [the] XACML PDP [Policy Decision Point] needs to do is find a policy that applies to a given request. To do this, XACML provides another feature called a Target. A Target is basically a set of simplified conditions for the Subject, Resource and Action that must be met for a PolicySet, Policy or Rule to apply to a given request. If all the conditions of a Target are met, then its associated PolicySet, Policy, or Rule applies to the request. In addition to being a way to check applicability, Target information also provides a way to index policies, which is useful if you need to store many policies and then quickly sift through them to find which ones apply. “ https://www.axiomatics.com/100-pure-xacml/](https://image.slidesharecdn.com/abac-in-symfony-by-veruscript-180831213515/75/Attribute-Based-Access-Control-in-Symfony-65-2048.jpg)

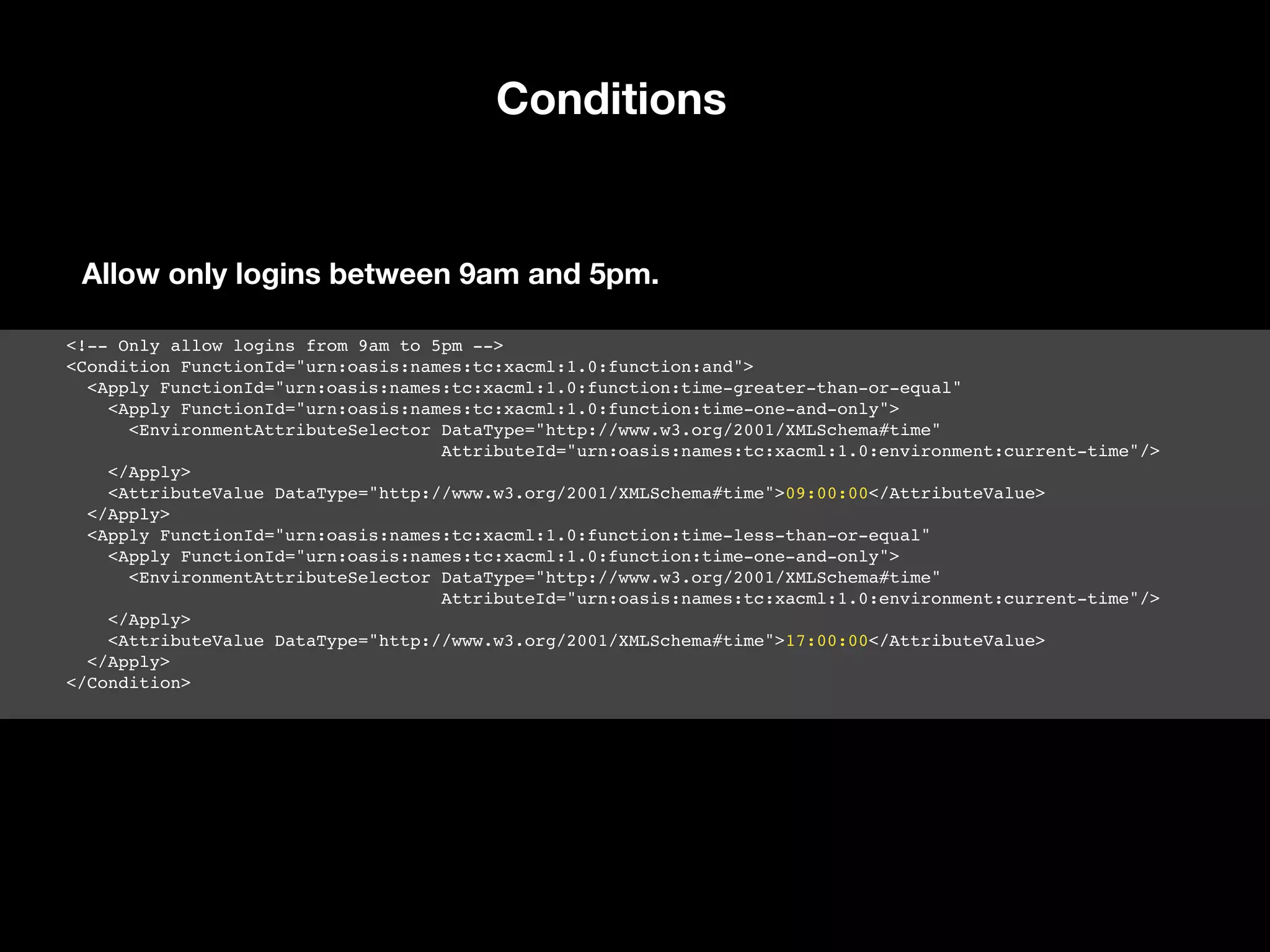
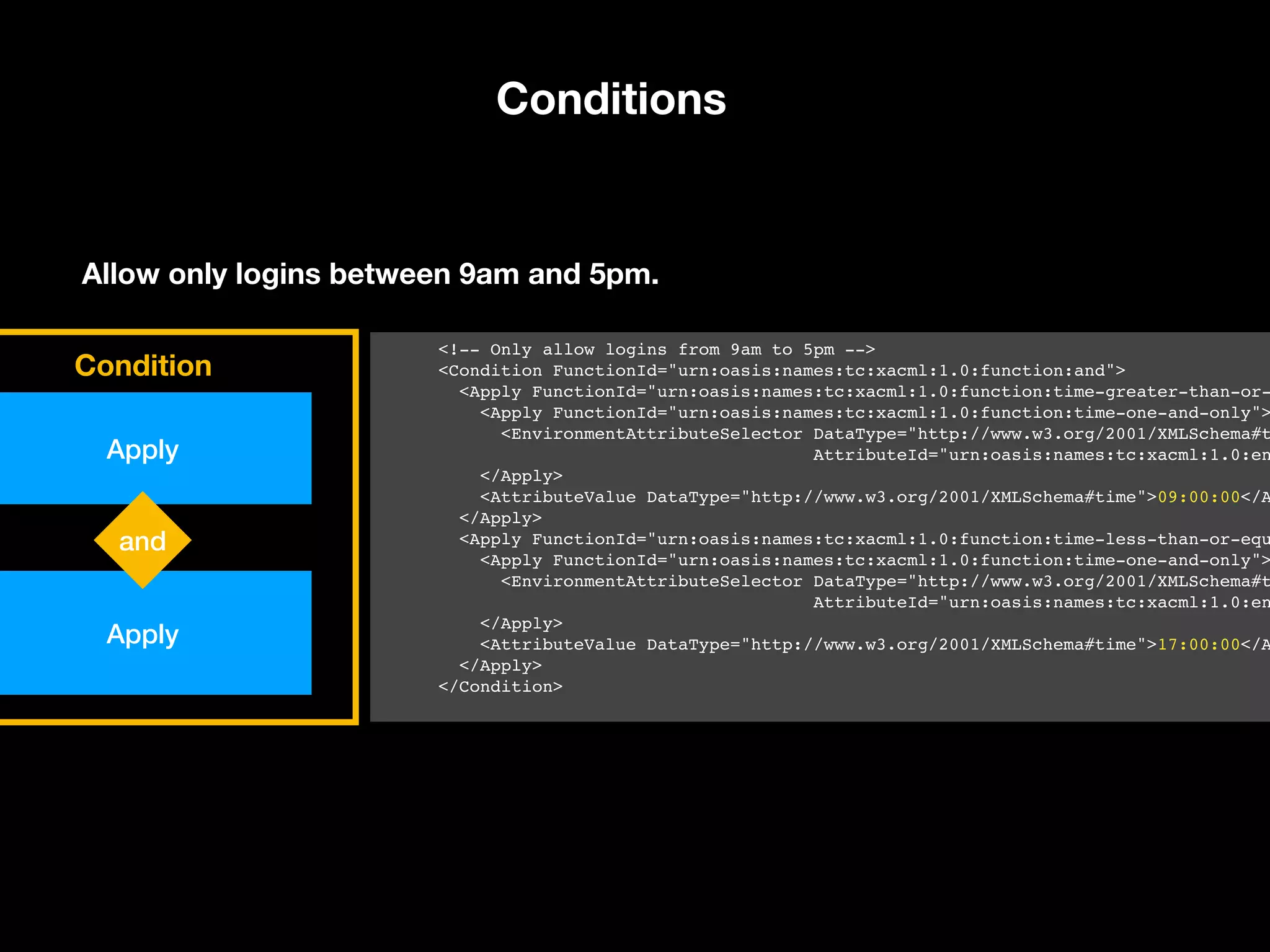
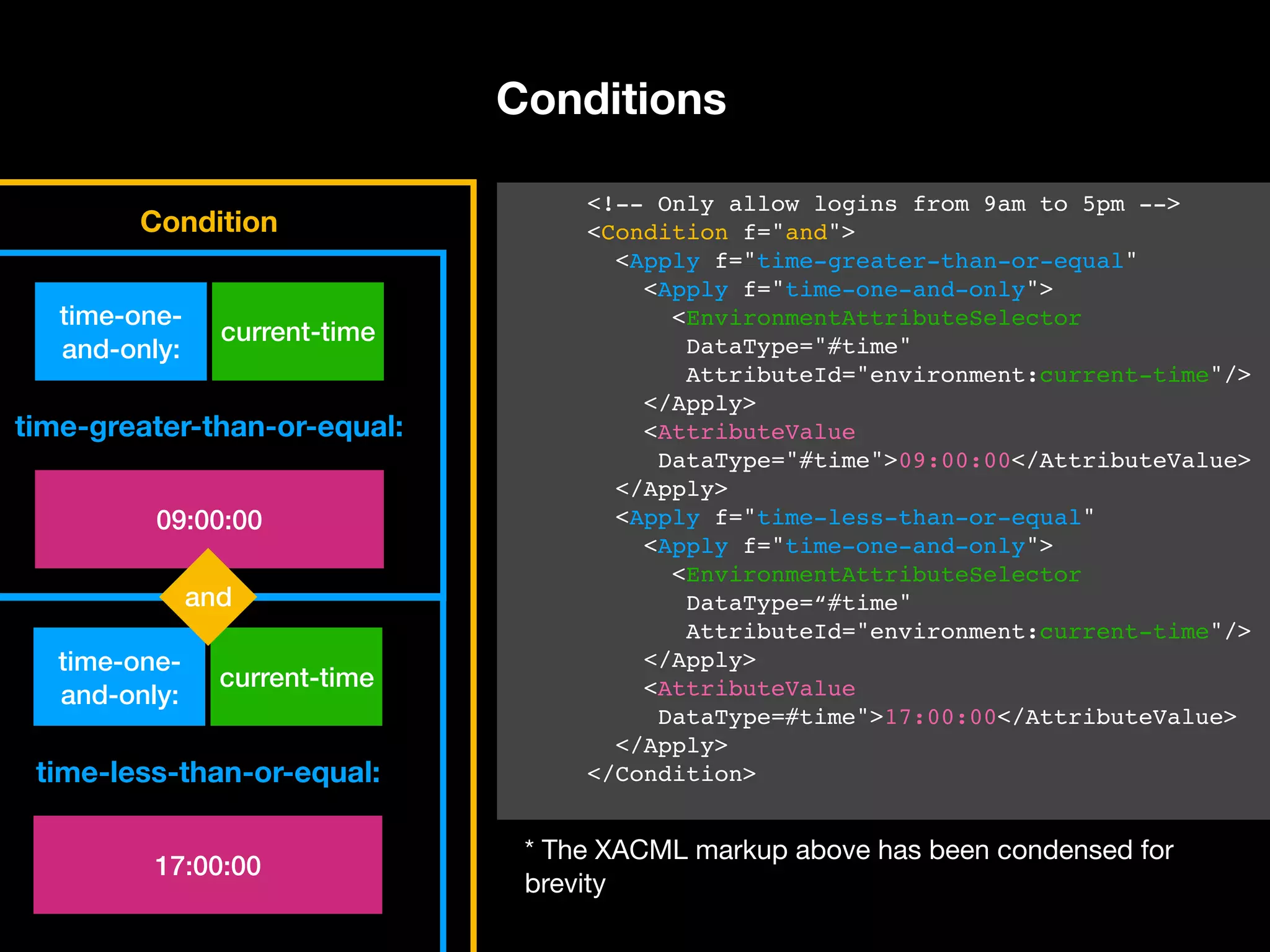
![current-time time-one- and-only: time-less-than-or-equal: 17:00:00 Conditions $timeGreaterThanOrEq = function($x, $y): bool { return $x >= $y; } $timeLessThanOrEq = function($x, $y): bool { return $x <= $y; } $timeOneAndOnly = function($x): DateTimeInterface { return new DateTimeImmutable($x); } $condition = Functionaltrue([ $timeGreaterThanOrEq( $timeOneAndOnly($env->getCurrentTime()), ’09:00:00’ ), $timeLessThanOrEq( $timeOneAndOnly($env->getCurrentTime()), ’17:00:00’ ), ]); Condition current-time time-one- and-only: time-greater-than-or-equal: 09:00:00 and](https://image.slidesharecdn.com/abac-in-symfony-by-veruscript-180831213515/75/Attribute-Based-Access-Control-in-Symfony-77-2048.jpg)
![What’s a XACML Obligation? The XACML standard defines the concept of obligations which are elements which can be returned along with a XACML decision (either of Permit or Deny) in order to enrich that decision. Obligations are triggered on either Permit or Deny. The Policy Enforcement Point [PEP] must implement and enforce obligations. If it fails to do so, it must deny access to the requested resource (in the case of a Permit). “ https://www.webfarmr.eu/2015/02/tgif-xacml-whats-a-xacml-obligation/](https://image.slidesharecdn.com/abac-in-symfony-by-veruscript-180831213515/75/Attribute-Based-Access-Control-in-Symfony-78-2048.jpg)