The document discusses different approaches for anomaly-based network intrusion detection systems (NIDS), including machine learning, fuzzy logic, and genetic algorithm approaches. Specifically, it summarizes: 1) Fuzzy logic based NIDS that uses a strategy to automatically generate fuzzy rules from training data to define normal network behavior and detect anomalies. Experiments using the KDD Cup 99 dataset showed it achieved 90% accuracy. 2) The use of genetic algorithms for NIDS, which encode network data as chromosomes and use selection/evolution principles to optimize detection of intrusions based on fitness metrics like packet drop rates. 3) Research applying fuzzy logic and genetic algorithm techniques to detect packet dropping attacks by malicious nodes in mobile ad hoc

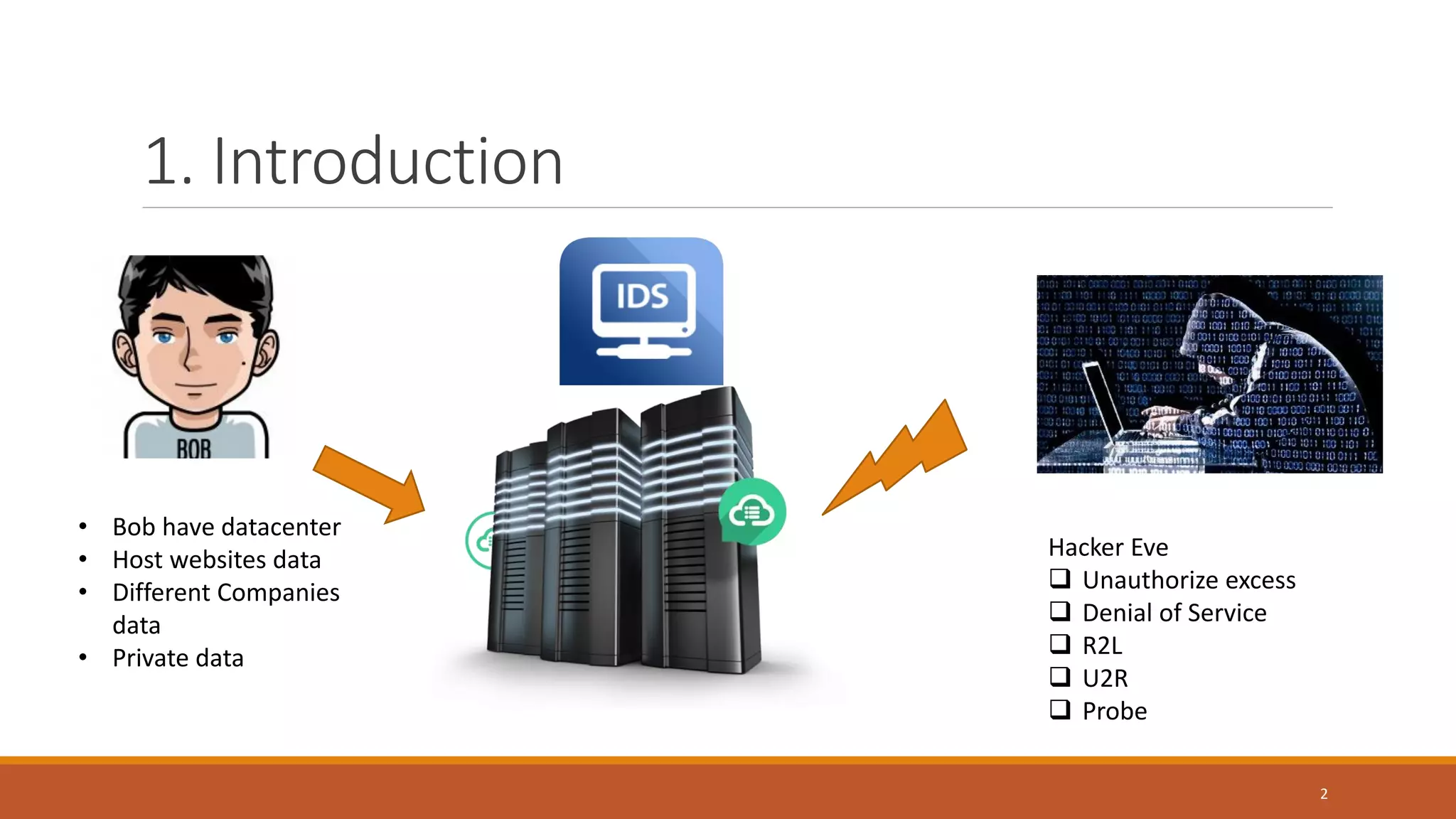
![Introduction.. [1] NIDS is tool used to detect security attack It is based on network traffic ❖Depending on type of analysis, IDS classified as ❖Misuse-based signature based ( defined patterns in data) ❖Anomaly based deviation from Normal behavior ✓ Ability to detect new attack ✓ Profiles for normal activity is customized as for system ✓ But it has high potential of False alarms 3](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-4-2048.jpg)
![3. Fuzzy Logic Based A-NIDS[2] Fuzzy logic : degree of truth rather than Boolean True/False(1/0) Process of Fuzzy logic include Fuzzify I/P values into fuzzy membership function Apply rules in the rulebase to compute O/P De-fuzzify the fuzzy O/P to crisp set 5](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-6-2048.jpg)
![3.1 KDD CUP DATASET DARPA 1998 network dataset(TCP Dump) 4.9 million single connection vectors Consist of 41 features Normal + Attack Contains 4 types of main attacks ( overall 38 attacks) 6 Fig: KDD cup dataset Features example.[2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-7-2048.jpg)
![3.2 Steps Involved in the Proposed A- NIDS[2] Classification of Training Data Strategy for generation of fuzzy rules Fuzzy decision module Finding an appropriate classification for a test input 7](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-8-2048.jpg)
![8 Fig: Overall steps of proposed intrusion detection in [2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-9-2048.jpg)
![3.2.1 Classification of Training Data Continuous attributes of KDD dataset (Continuous in Nature) Hence, 34 attributes from Input data set Divide dataset D in to 5 subset (Class label) --[2] Class Label define several attack ◦ 4 Major attack dat ◦ Denial of Service, Remote to Local,U2R and Probe ◦ 1 Normal data These data set used to develop Fuzzy Rules automatically 9](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-10-2048.jpg)
![10 Fig: Overall steps of proposed intrusion detection in [2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-11-2048.jpg)
![3.2.2 Strategy For Generation of Fuzzy Rules Mining method to identify better set of rules due to huge input data Definite rule obtained from single length frequent items used for learning of fuzzy system. It has 4 steps 1. Mining of Single Length Frequent Items [2]: Frequent items(attributes) for Attack & Normal classes discovered Find 1 Length item for each attribute by finding frequency of continuous variable present in each attribute 11](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-12-2048.jpg)
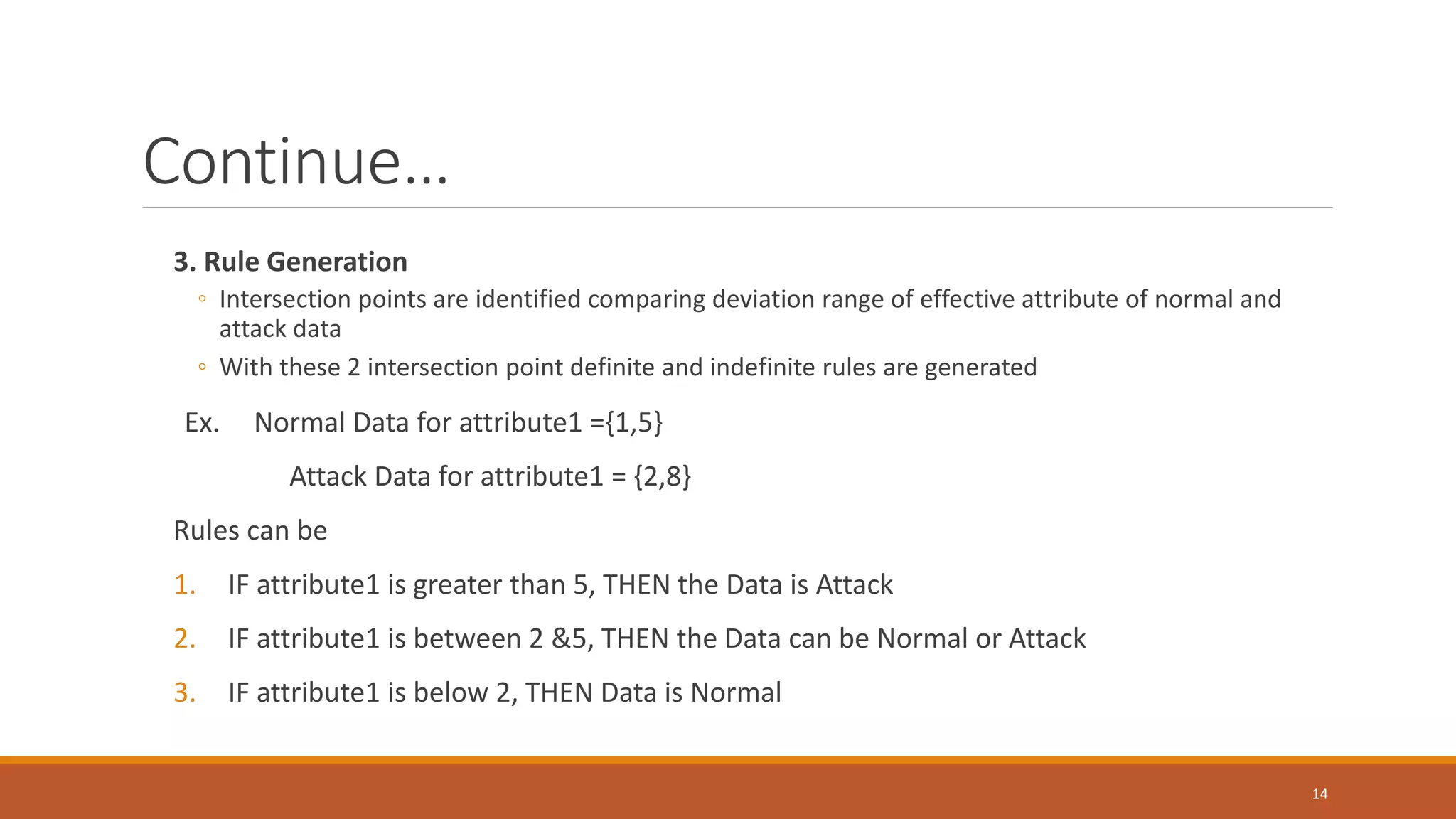
![Continue.. 2. Identification of suitable attributes for rule generation[2] Used Deviation Method Mined l-length frequent items from each attribute are stored in a vector so that 34 vectors are obtained for each class ----[2] 12 Where i=1(refer to Normal) & =2(refer to attack) Vector contains frequent items, frequency > minimum support ---[2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-13-2048.jpg)
![Continue.. For each attribute, Deviation range of frequent item is identified based on frequency range(max, min) 13 --[2] ➢ One to one comparison is performed between respective vector of each class to identify effective attribute ➢ Attributes that not contain identical {max, min} range for both class is chosen as effective attribute --[2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-14-2048.jpg)

![17 Fig: Overall steps of proposed intrusion detection in [2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-18-2048.jpg)
![3.2.3 Fuzzy Decision Module Finding suitable class label (attack or normal) of the test data using fuzzy logic system 18 Fig: Fuzzy decision Module [2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-19-2048.jpg)
![3.3 Experimentation ➢Experiment was done on 10% of available KDD Cup data set ➢Paper has shown result based on the MATLAB computation ➢Where TP= True Positive, TN= True Negative, FP= False Positive, FN=False Negative ➢Achieved 90 % of accuracy for all types of attacks 21 ----[2]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-22-2048.jpg)
![4.Genetic Algorithm [4] ➢Based on laws of selection and evolution ➢Problem is converted into the Chromosome ➢Identify dataset called population(collection of chromosome) ➢Dataset are individually encoded using bits, characters or integers which form chromosome 22](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-23-2048.jpg)

![24 Fig: Genetic Algorithm Flow[4]](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-25-2048.jpg)
![5. Fuzzy IDS for Mobile Ad hoc Network[3] ➢Communication by via wireless links makes mobile ad hoc networks more vulnerable ➢IDS for packet dropping attack through Malicious node Fuzzy Based Parameter extraction ◦ Data packet forwarded ratio ◦ Average data packet Dropped rate ➢Result ➢Calculated for different speed of mobile nodes ➢Fix malicious node 3 ➢True positive rate and false positive rate 25](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-26-2048.jpg)
![6. GA based Intrusion Detection in MANET[4] ➢IDS for packet dropping attack through Malicious node ➢Number of nodes of MANET is initial population ➢Members of initial population are encoded and called as chromosome ➢Each chromosomes are evaluated based on ➢Packet drop(PD) ➢Request Forwarding Rate(RFR) ➢Request Receive Rate(RRR) ➢Experiment result ➢Different numbers of malicious nodes(up to 10) ➢It talks number of detected node 26](https://image.slidesharecdn.com/anamolydetectionbasedonfuzzylogicandga-170825092016/75/Network-Anomaly-detection-based-on-fuzzy-logic-and-Genetic-Algorithm-27-2048.jpg)


