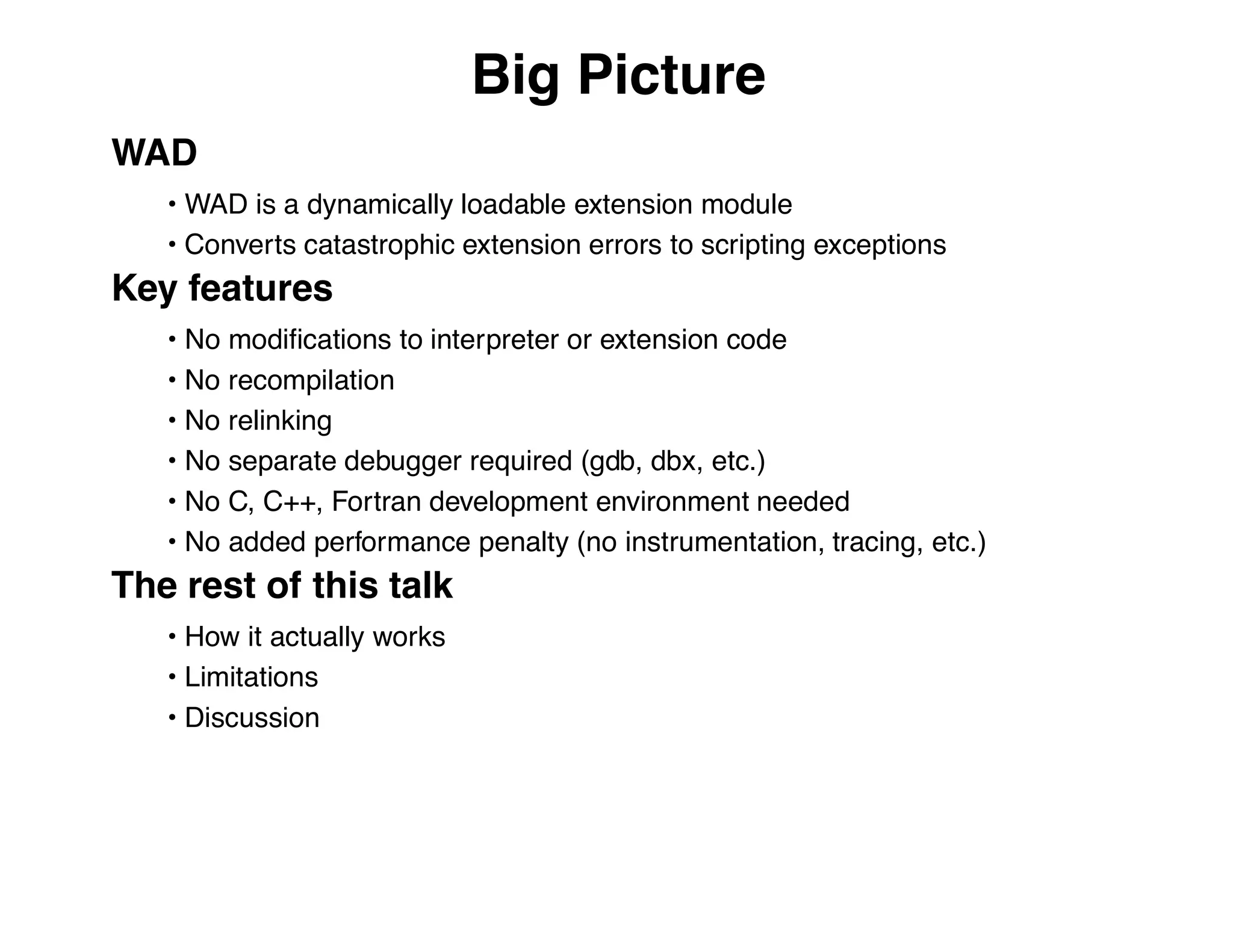
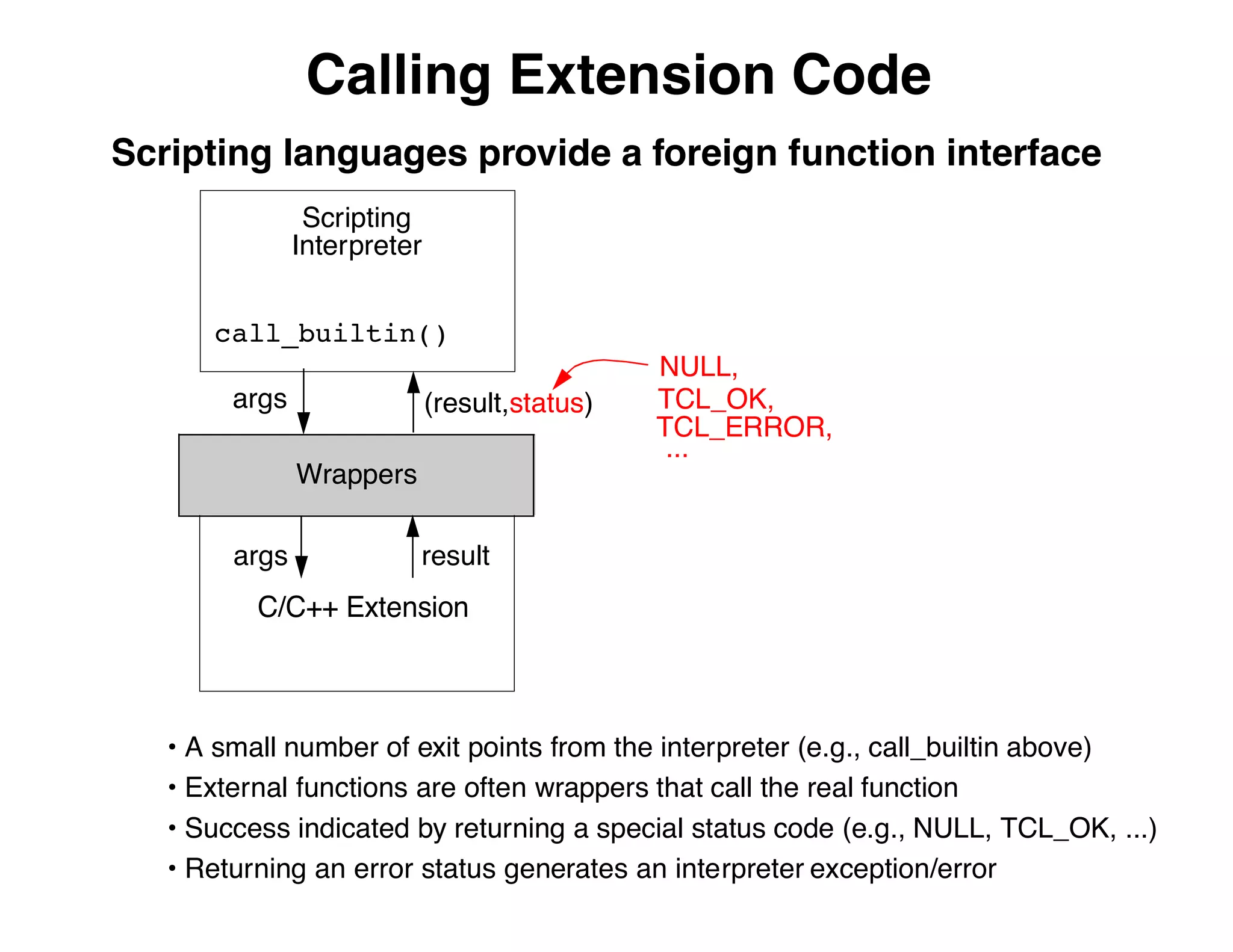
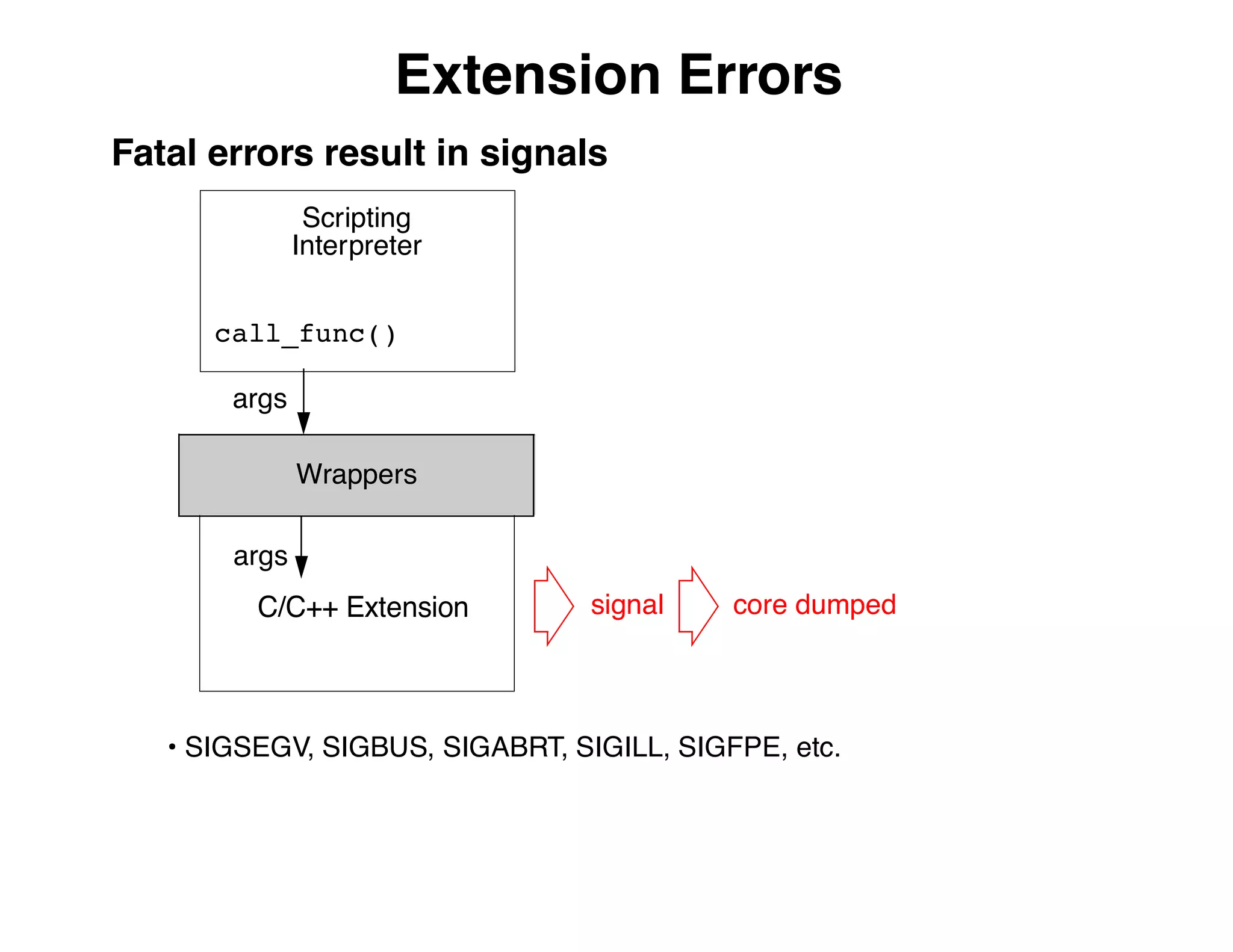
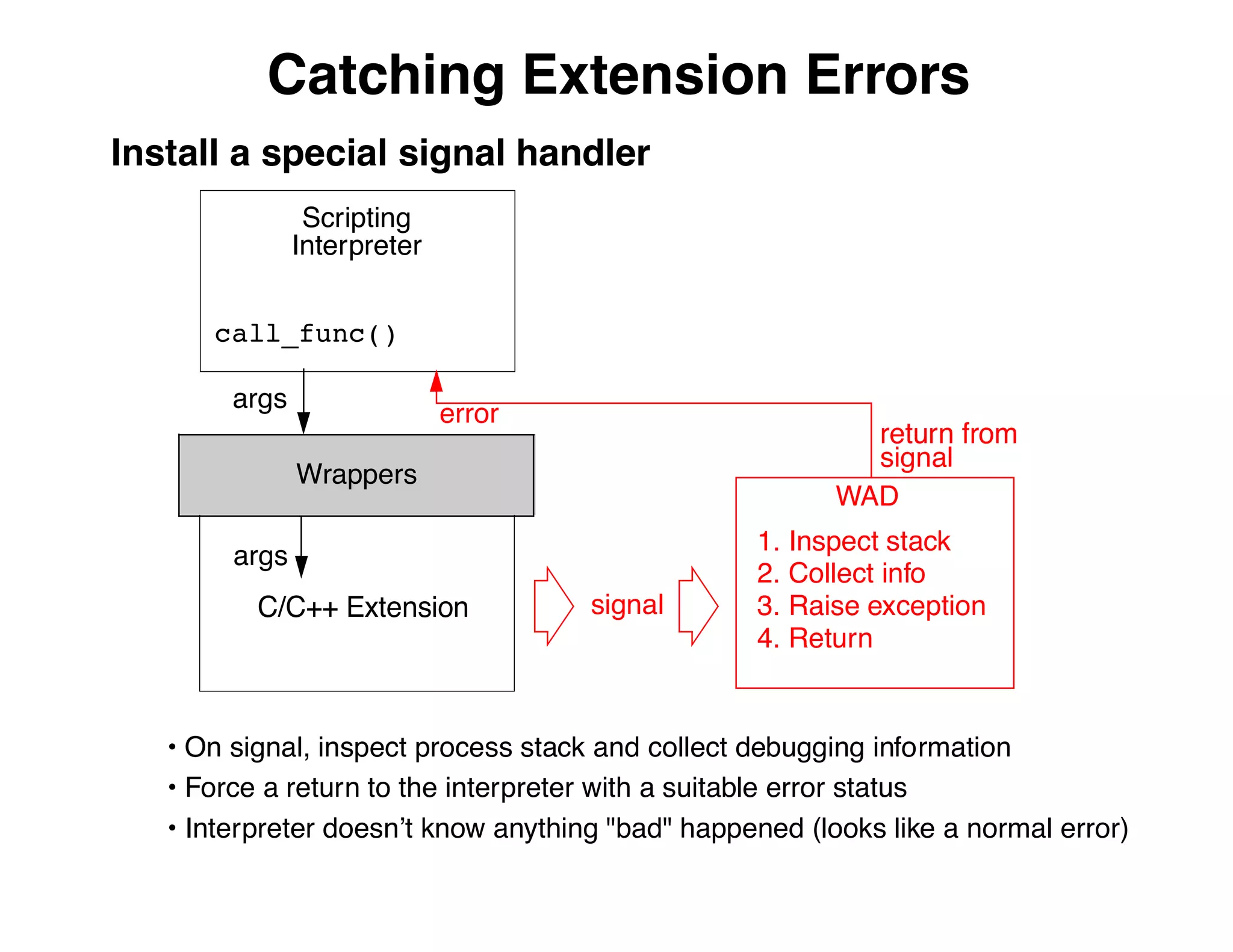
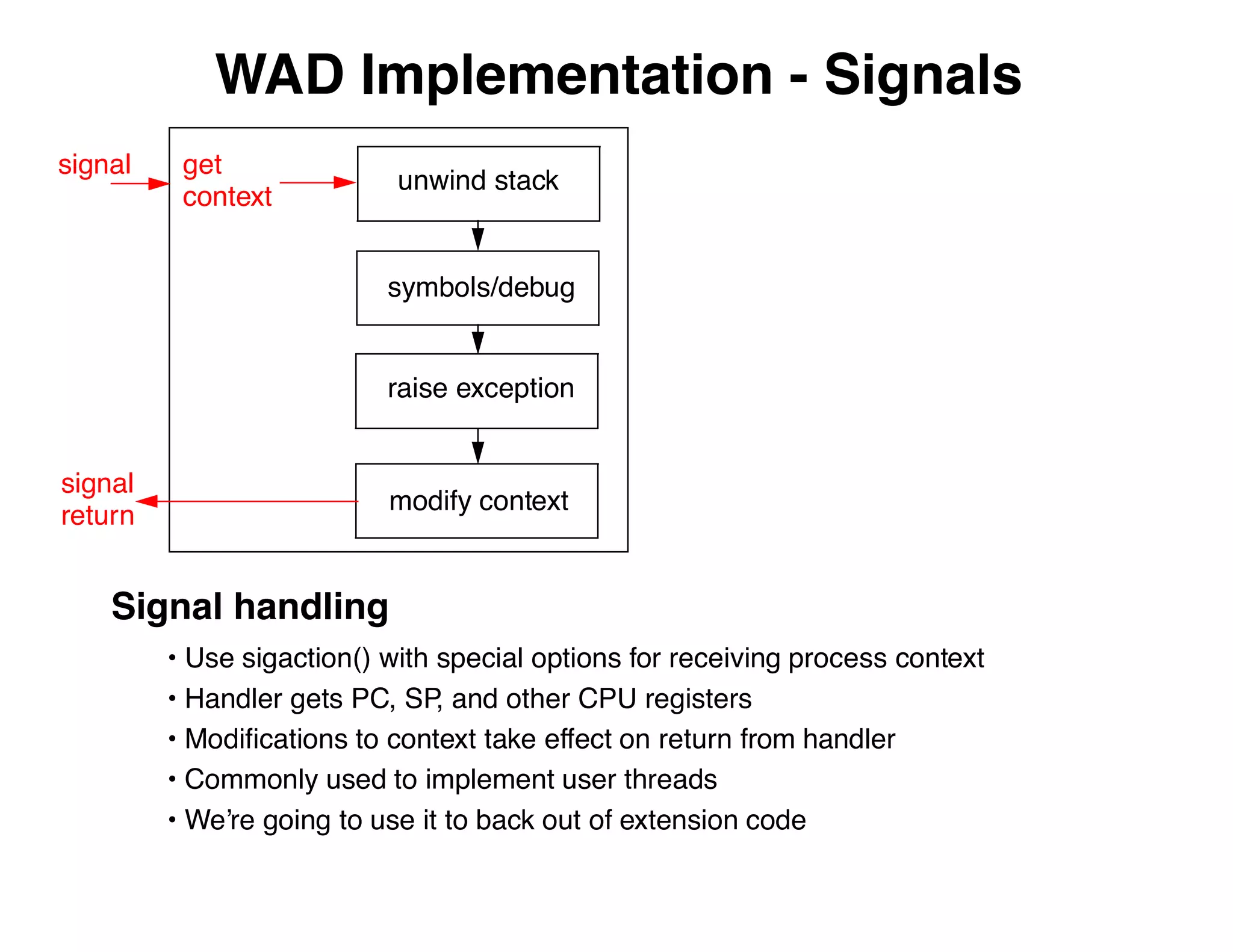
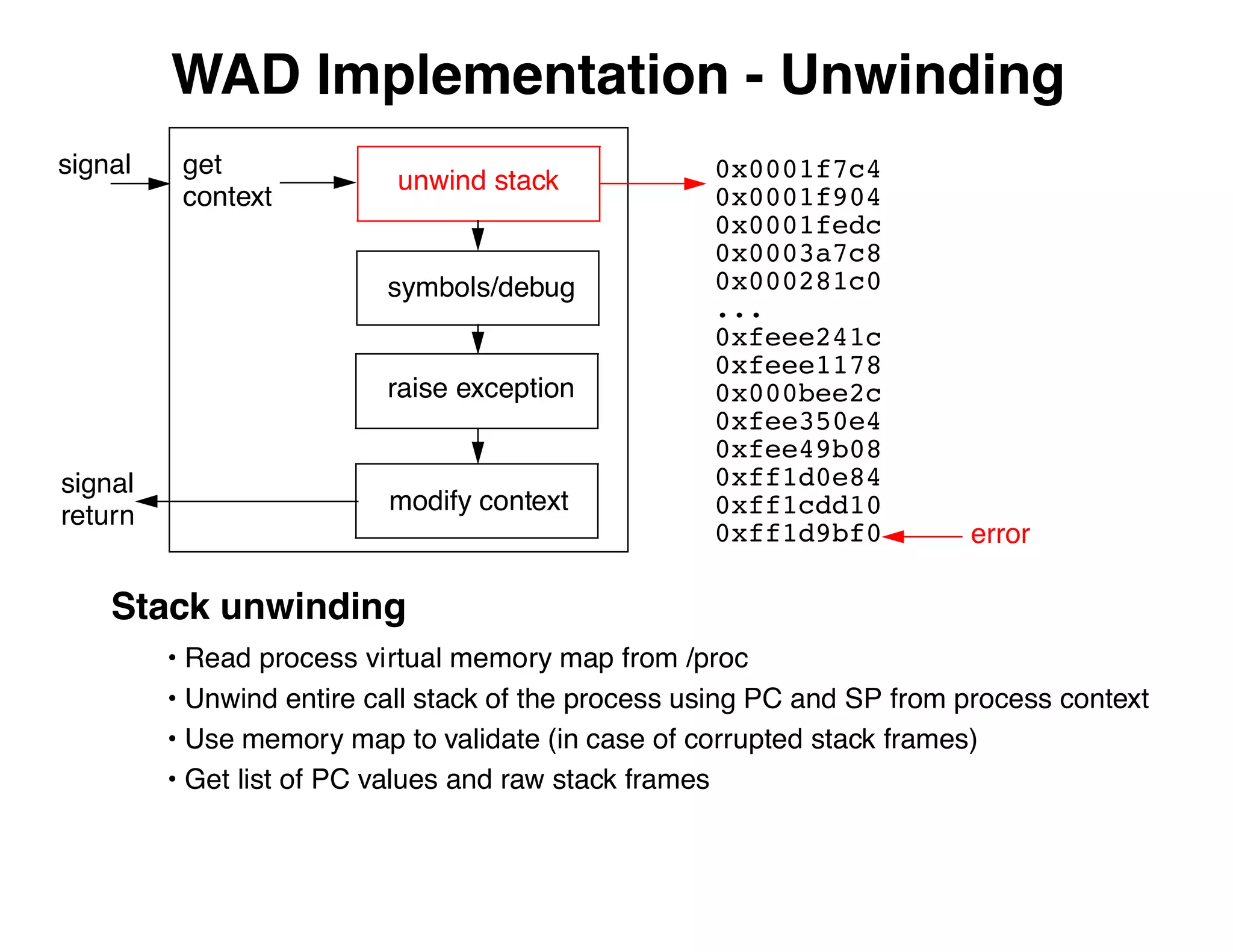
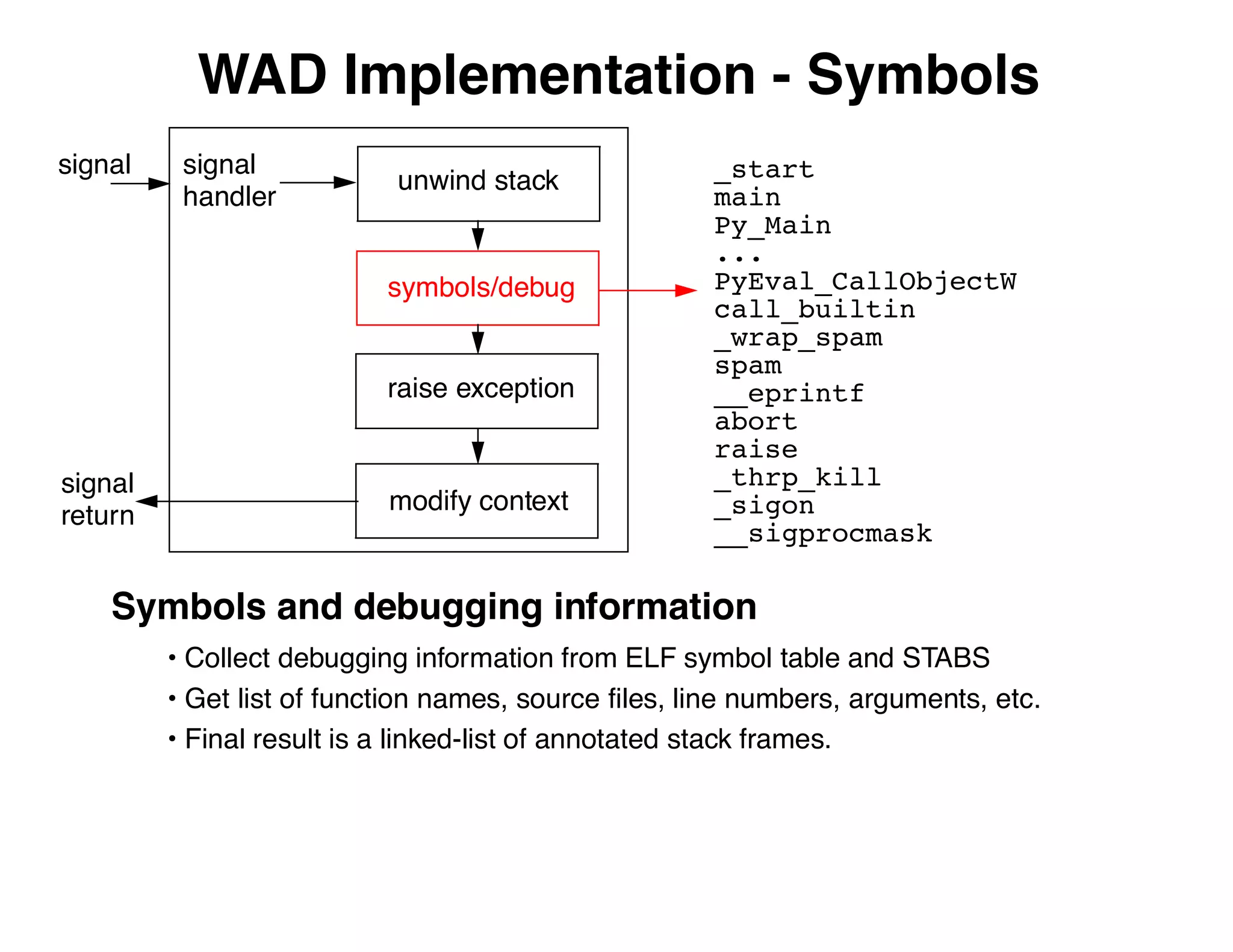
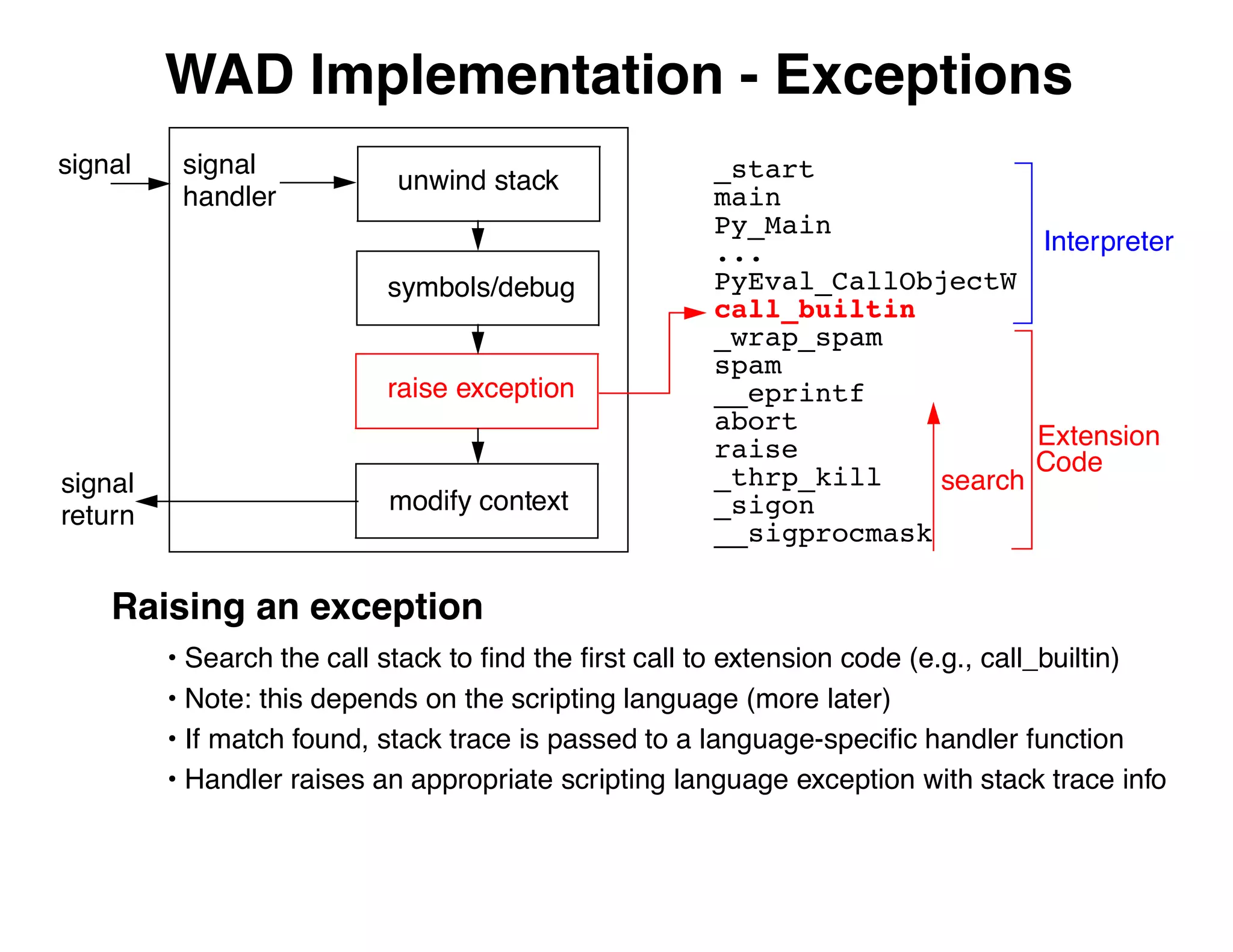
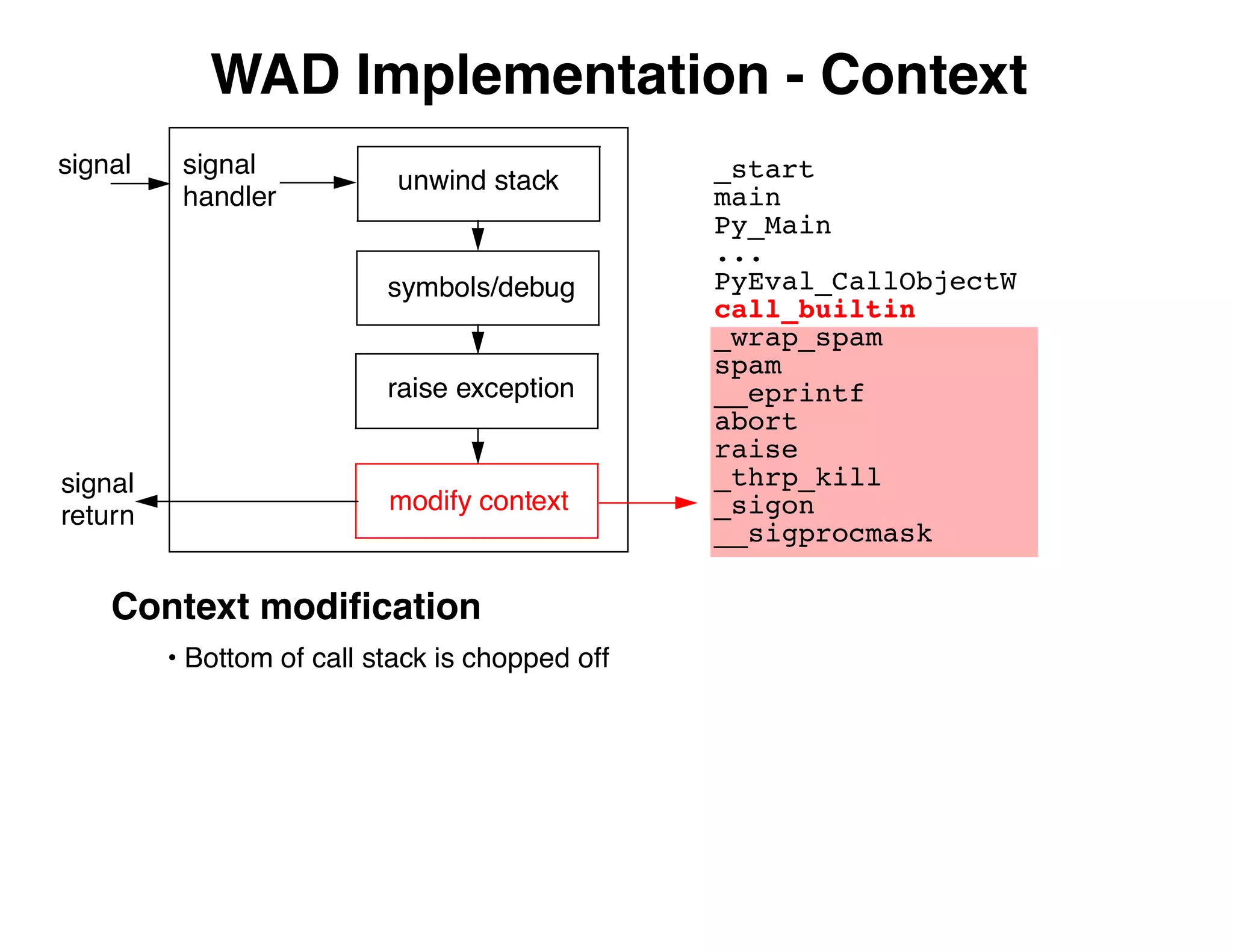
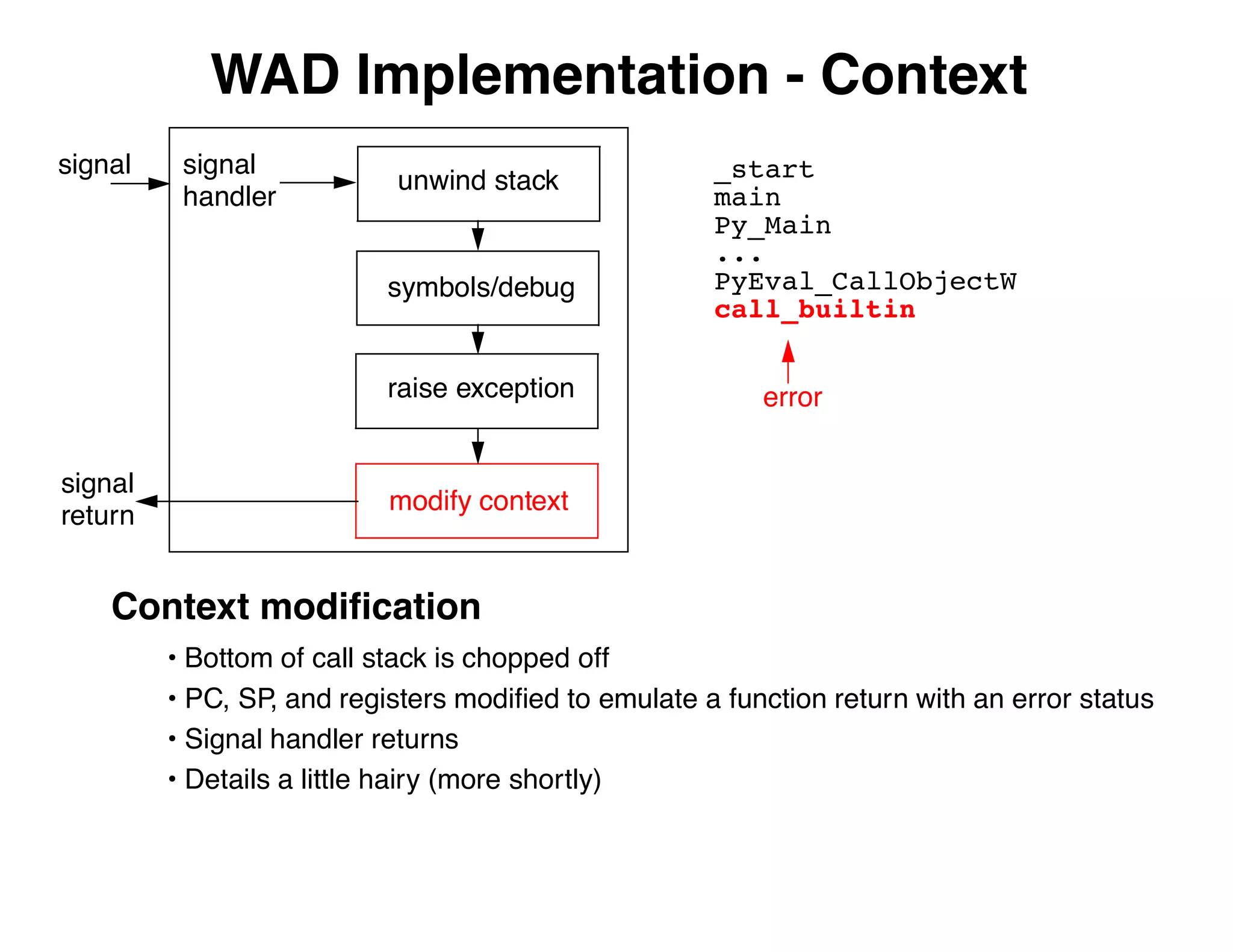
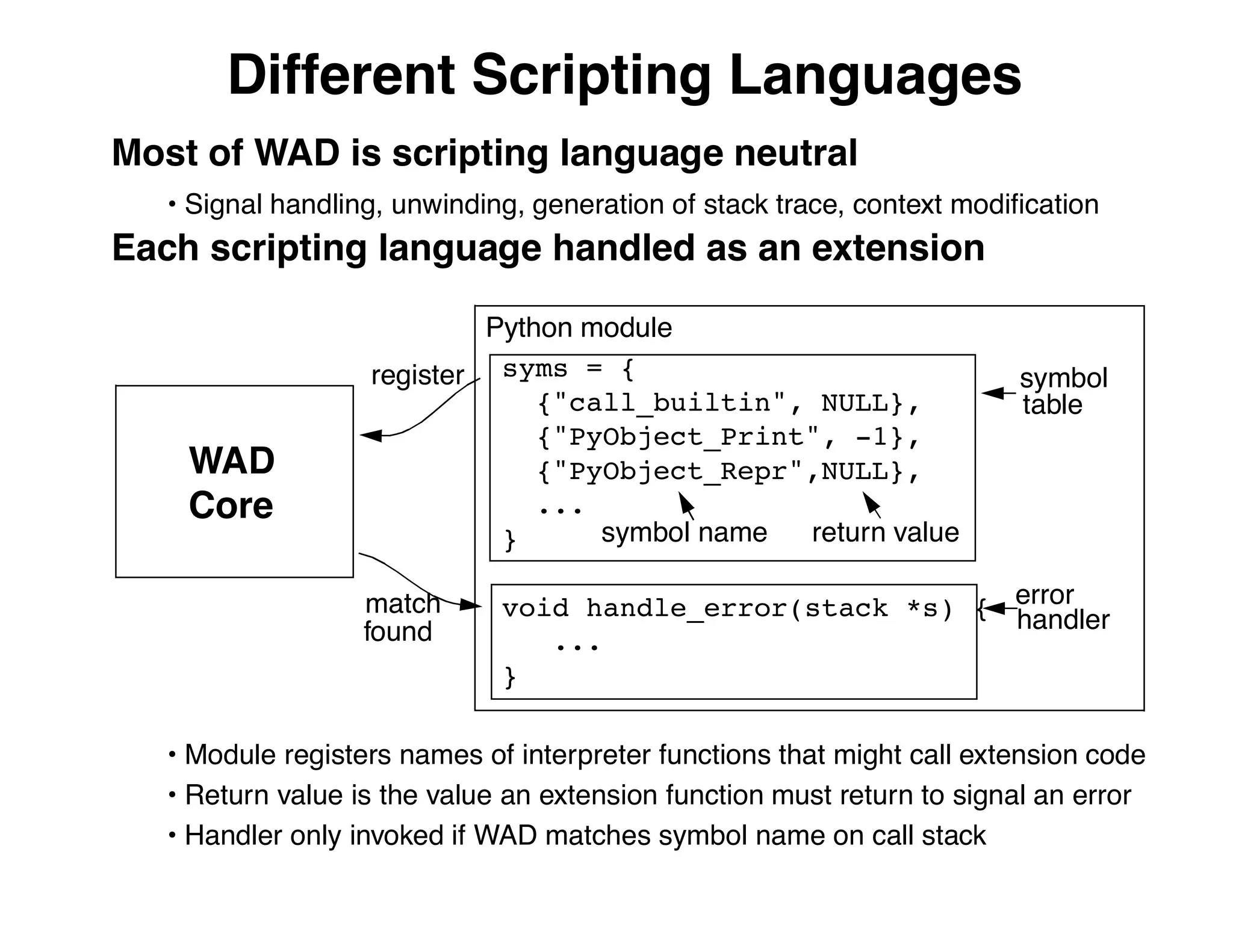
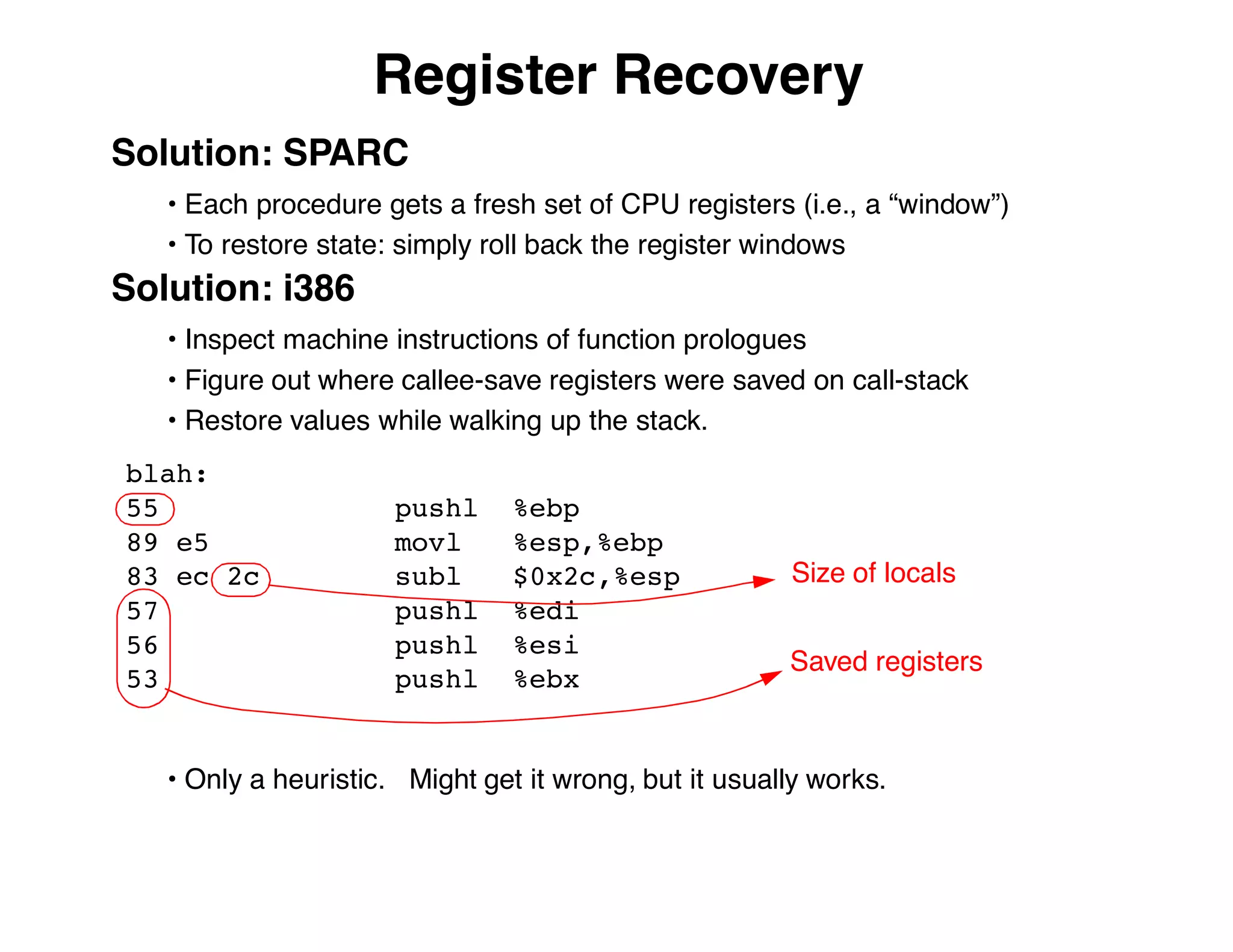
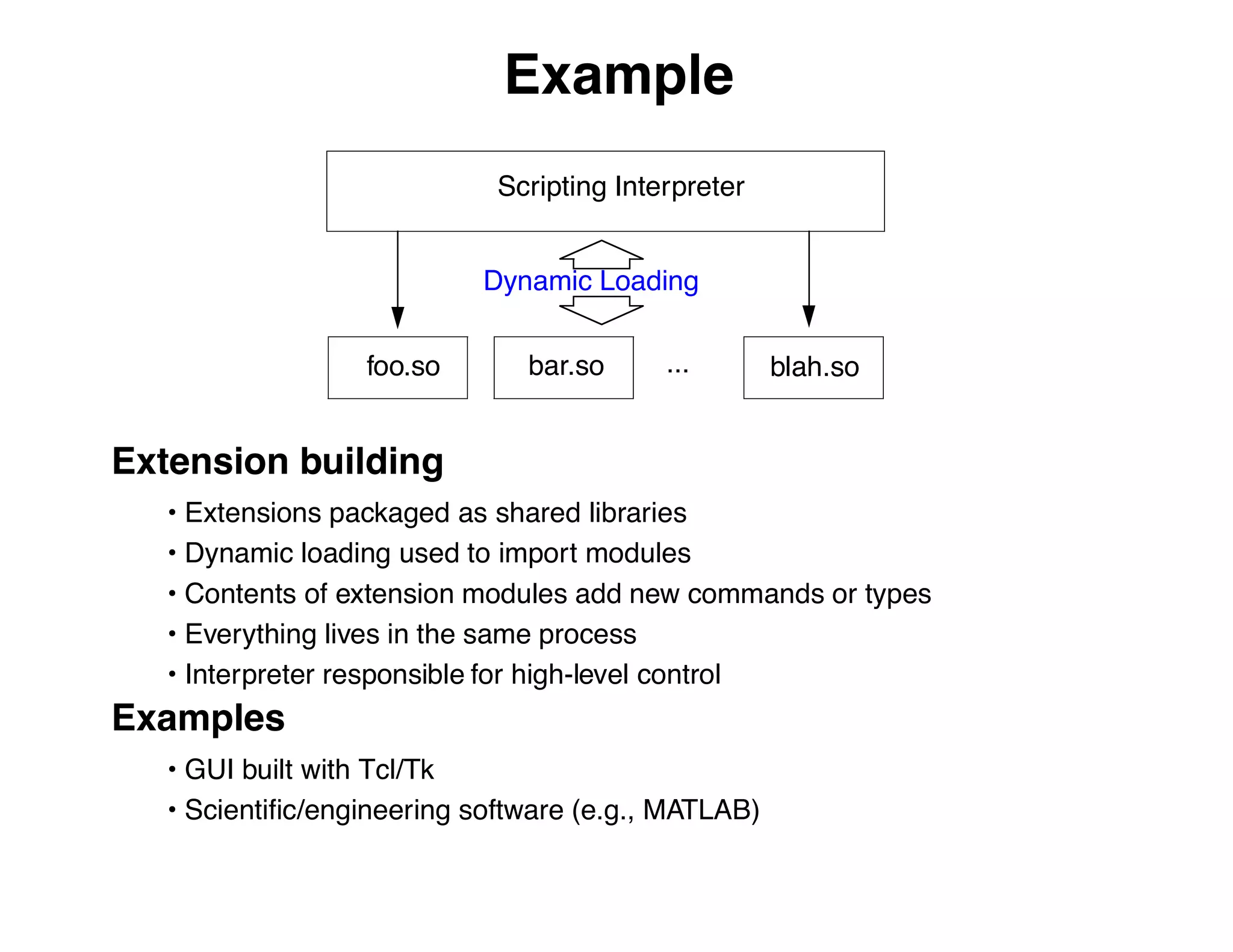
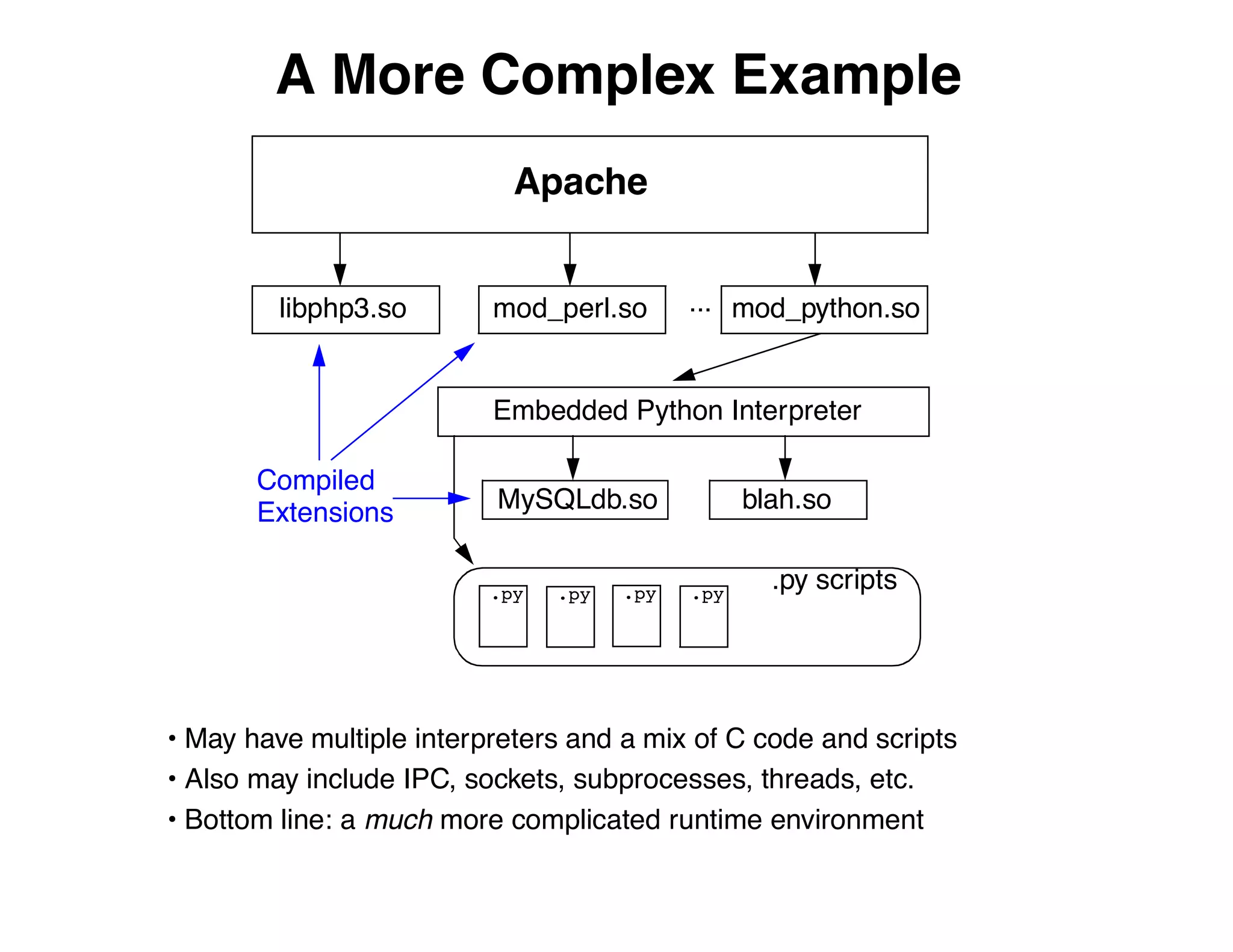
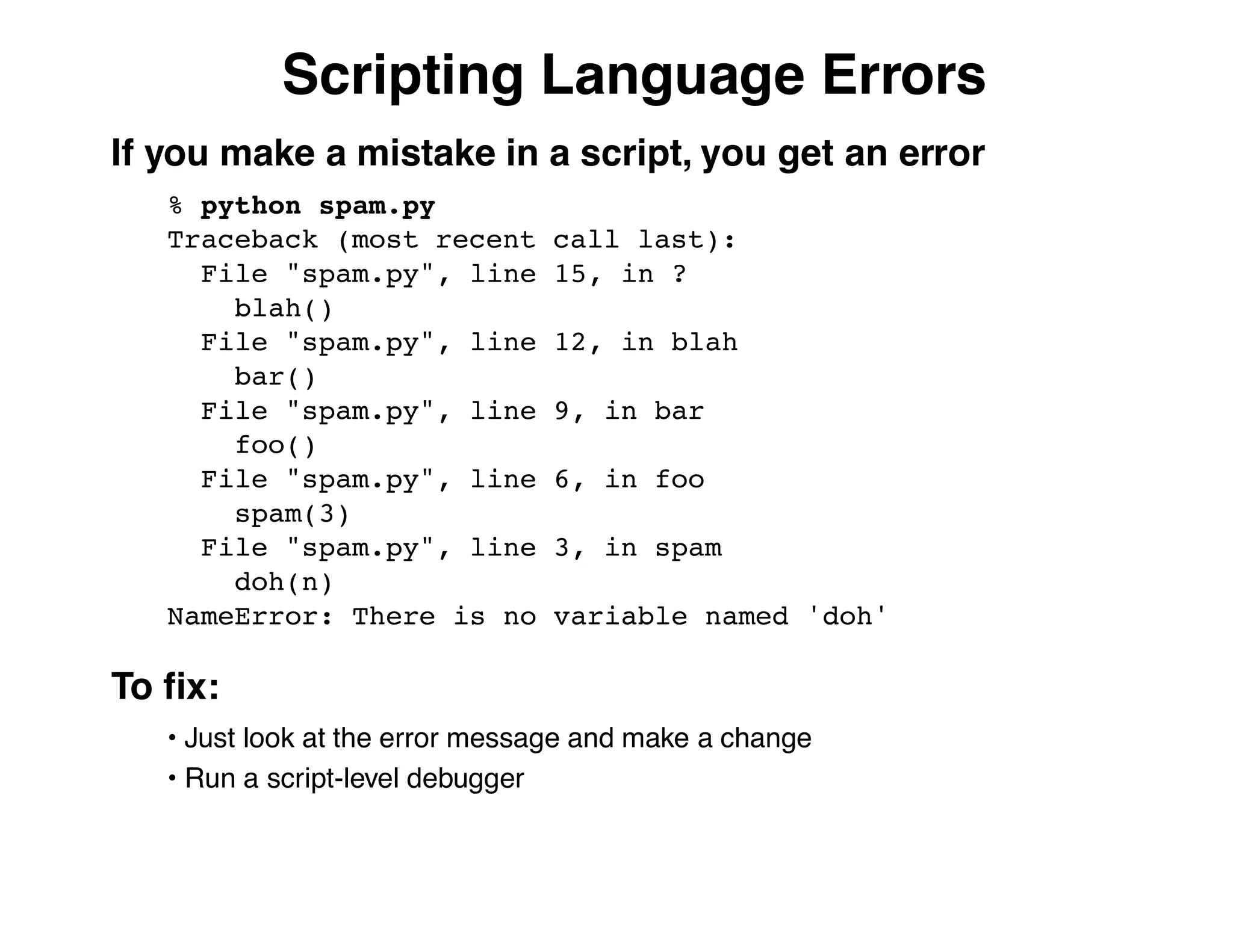
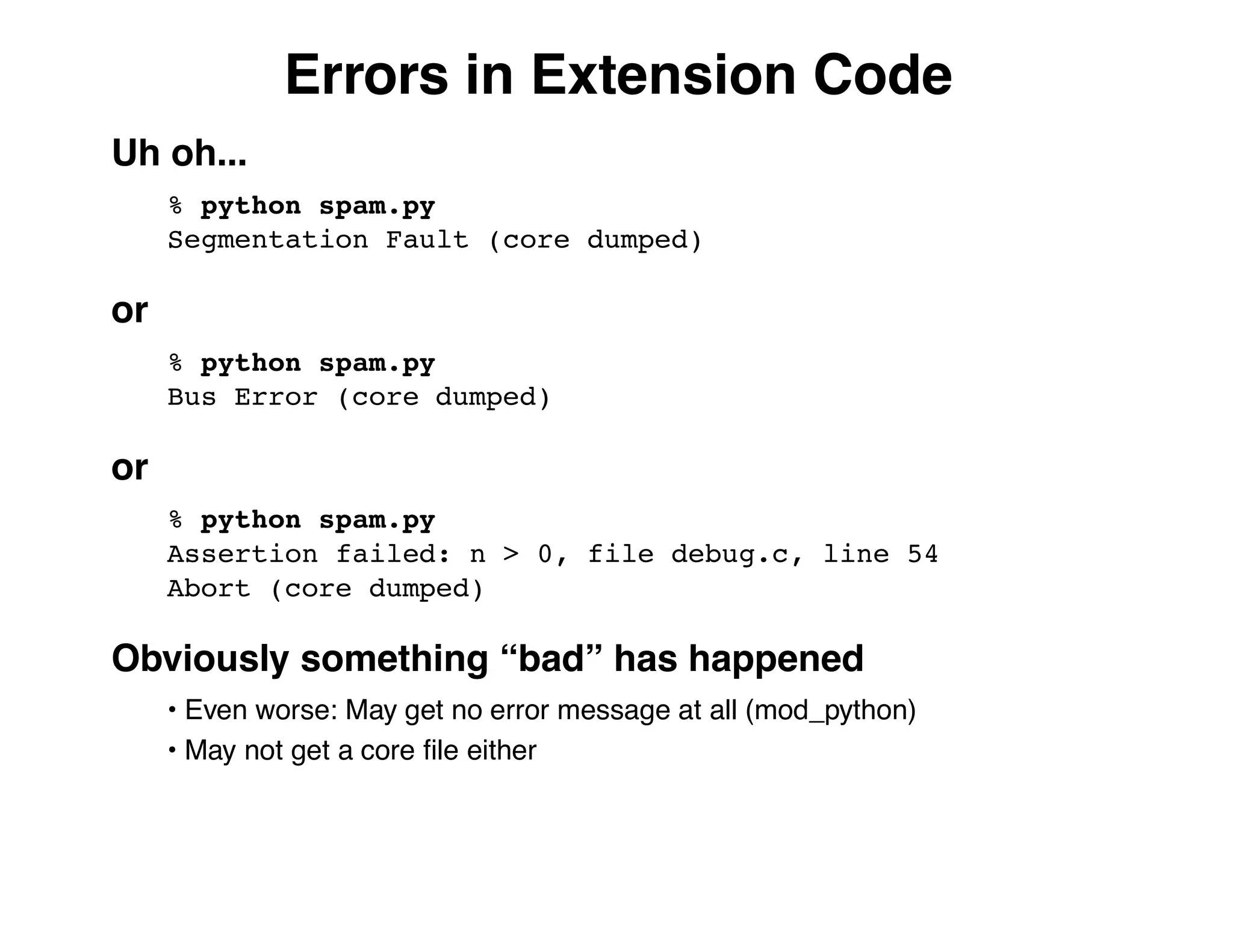
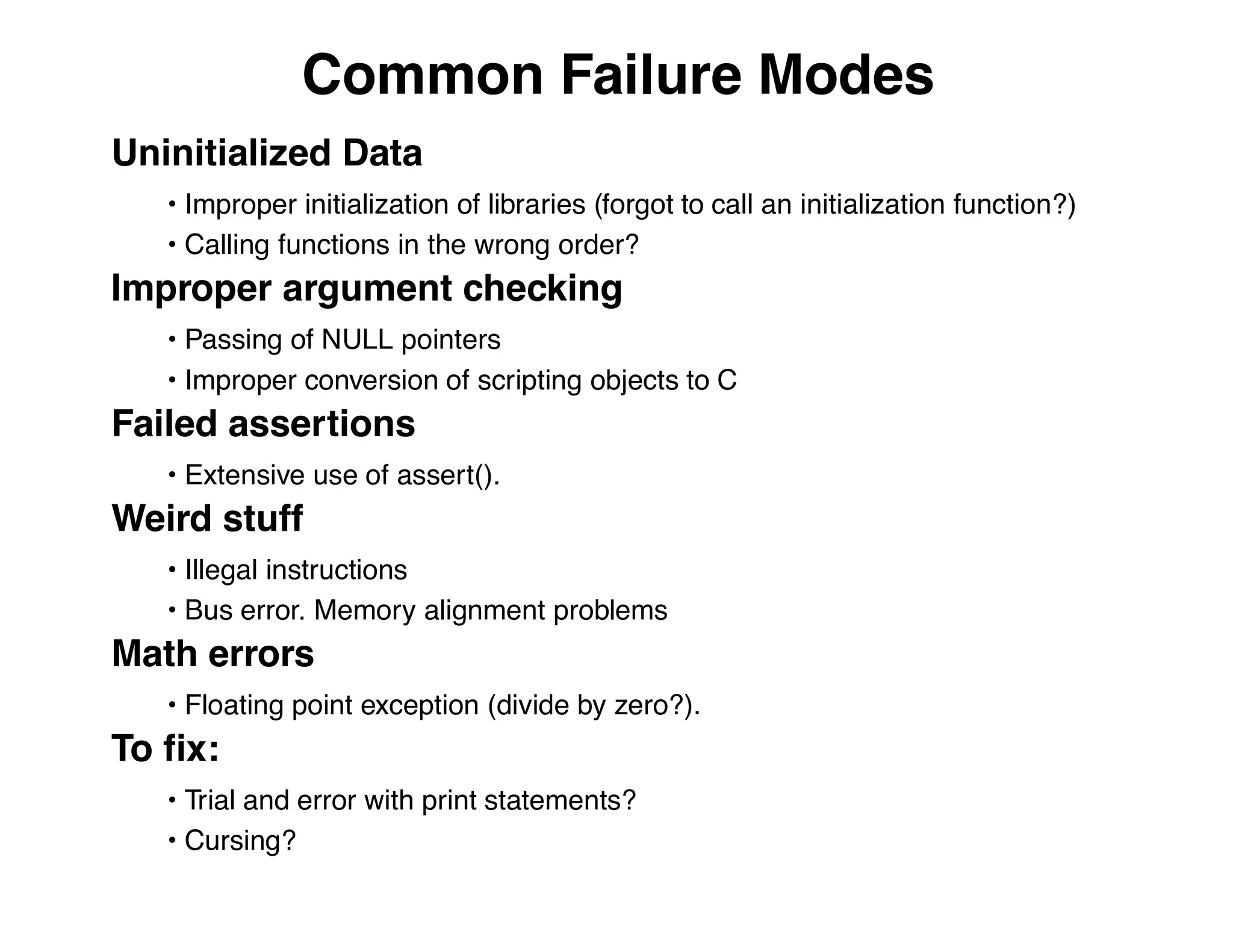
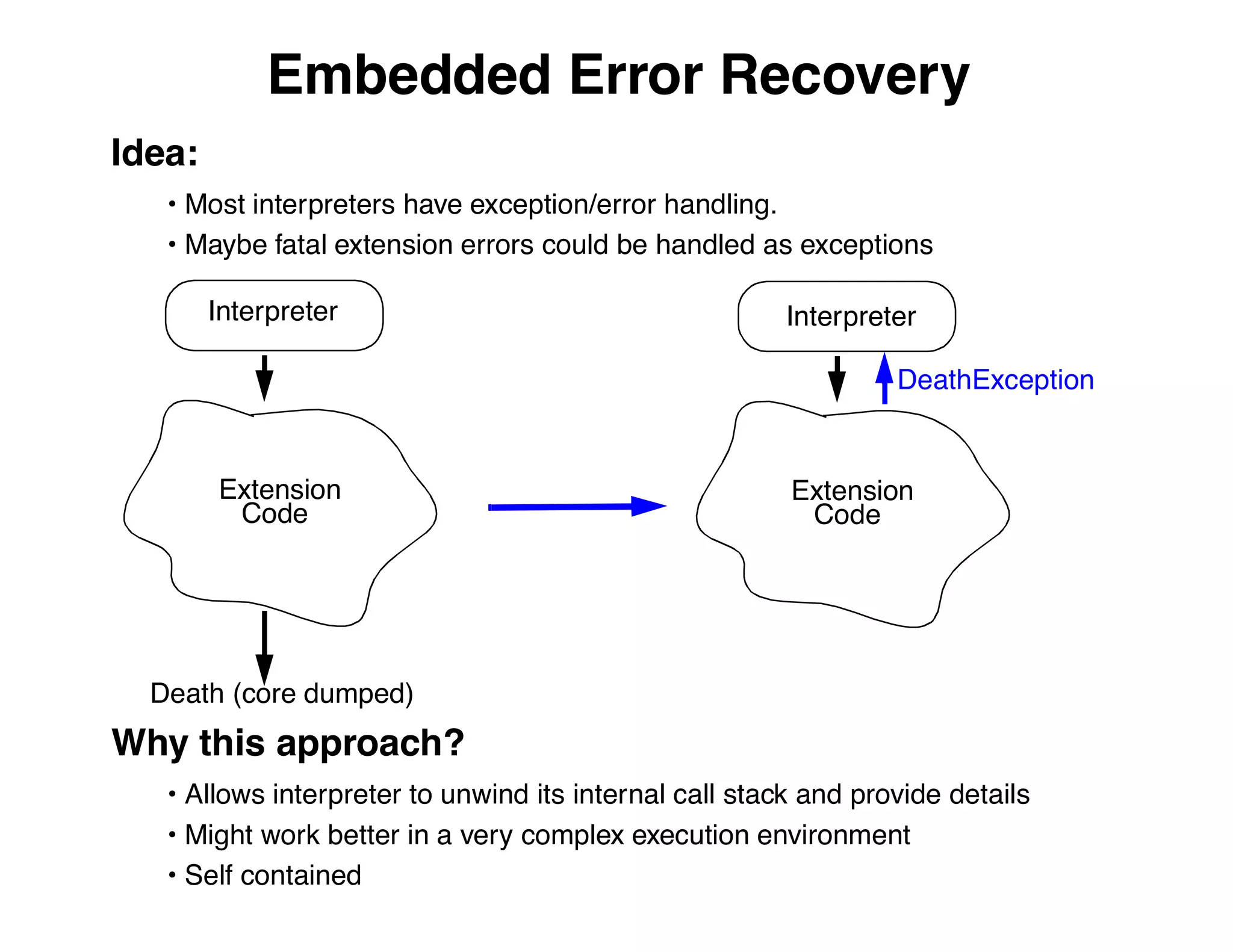
The document describes an embedded error recovery and debugging mechanism for scripting language extensions. It discusses how errors can occur both in script code and extension code built as shared libraries. Debugging errors in extension code is challenging as typical debuggers and tracebacks do not work. The document then presents the Wrapped Application Debugger (WAD) which allows debugging of extension code as if it were part of the script by capturing signals and integrating with the GNU Debugger (GDB).


![WAD Demo % python >>> import debug >>> debug.seg_crash() Segmentation fault (core dumped) % % python >>> import debug >>> import libwadpy WAD Enabled >>> debug.seg_crash() Traceback (most recent call last): File "<stdin>", line 1, in ? SegFault: [ C stack trace ] #2 0x000281c0 in call_builtin(func=0x1cbaf0,arg=0x18f114,kw=0x0) in 'ceval.c', line 2650 #1 0xfeee26b8 in _wrap_seg_crash(self=0x0,args=0x18f114) in 'pydebug.c', line 510 #0 0xfeee1258 in seg_crash(0x1,0xfeef2d48,0x19a9f8,0x0,0x7365675f,0x5f5f6469) in 'debug.c', line 18 /u0/beazley/Projects/WAD/WAD/Test/debug.c, line 18 int seg_crash() { int *a = 0; => *a = 3; return 1; }](https://image.slidesharecdn.com/usenixwad-100925135153-phpapp01/75/An-Embedded-Error-Recovery-and-Debugging-Mechanism-for-Scripting-Language-Extensions-14-2048.jpg)