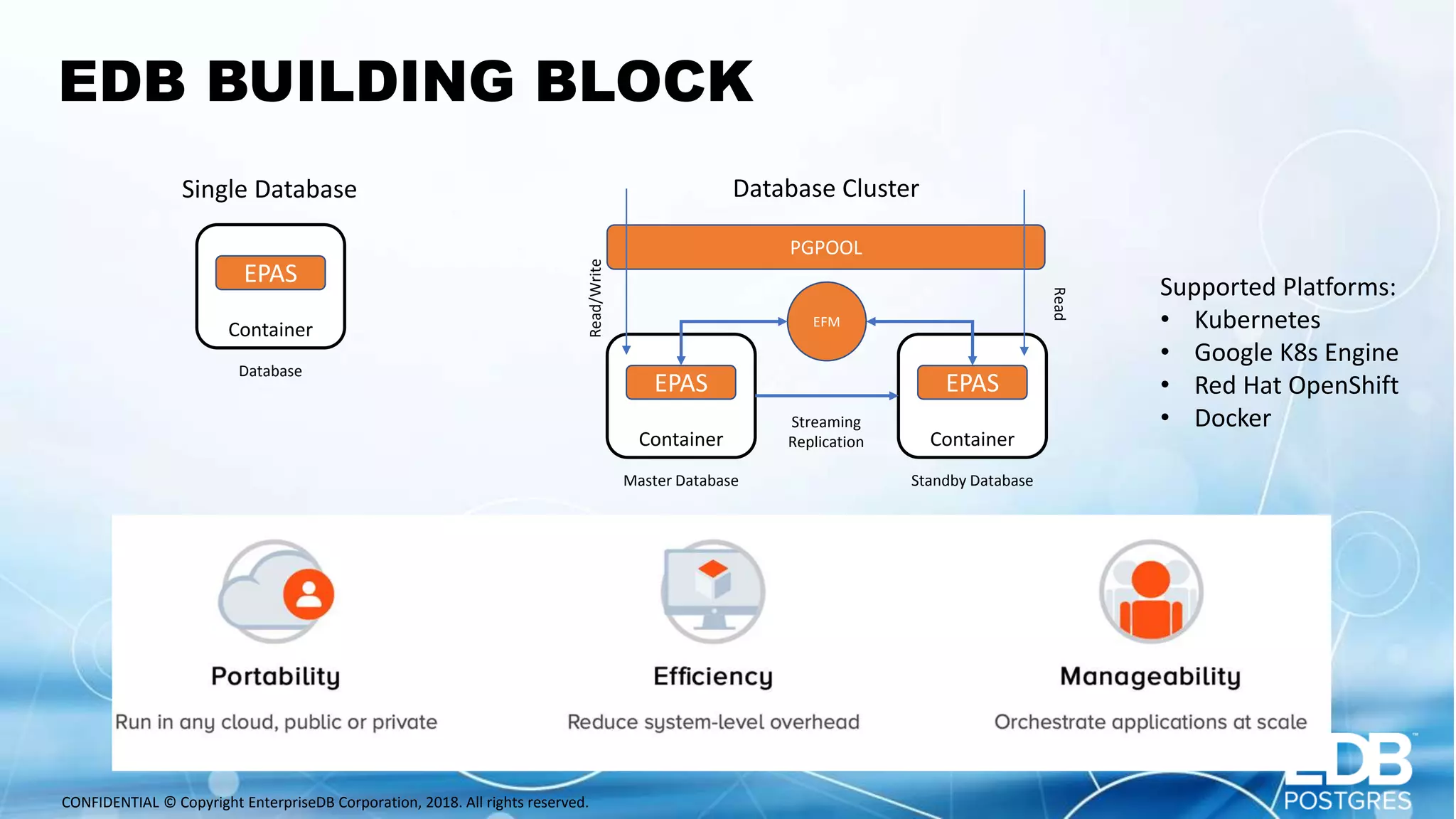
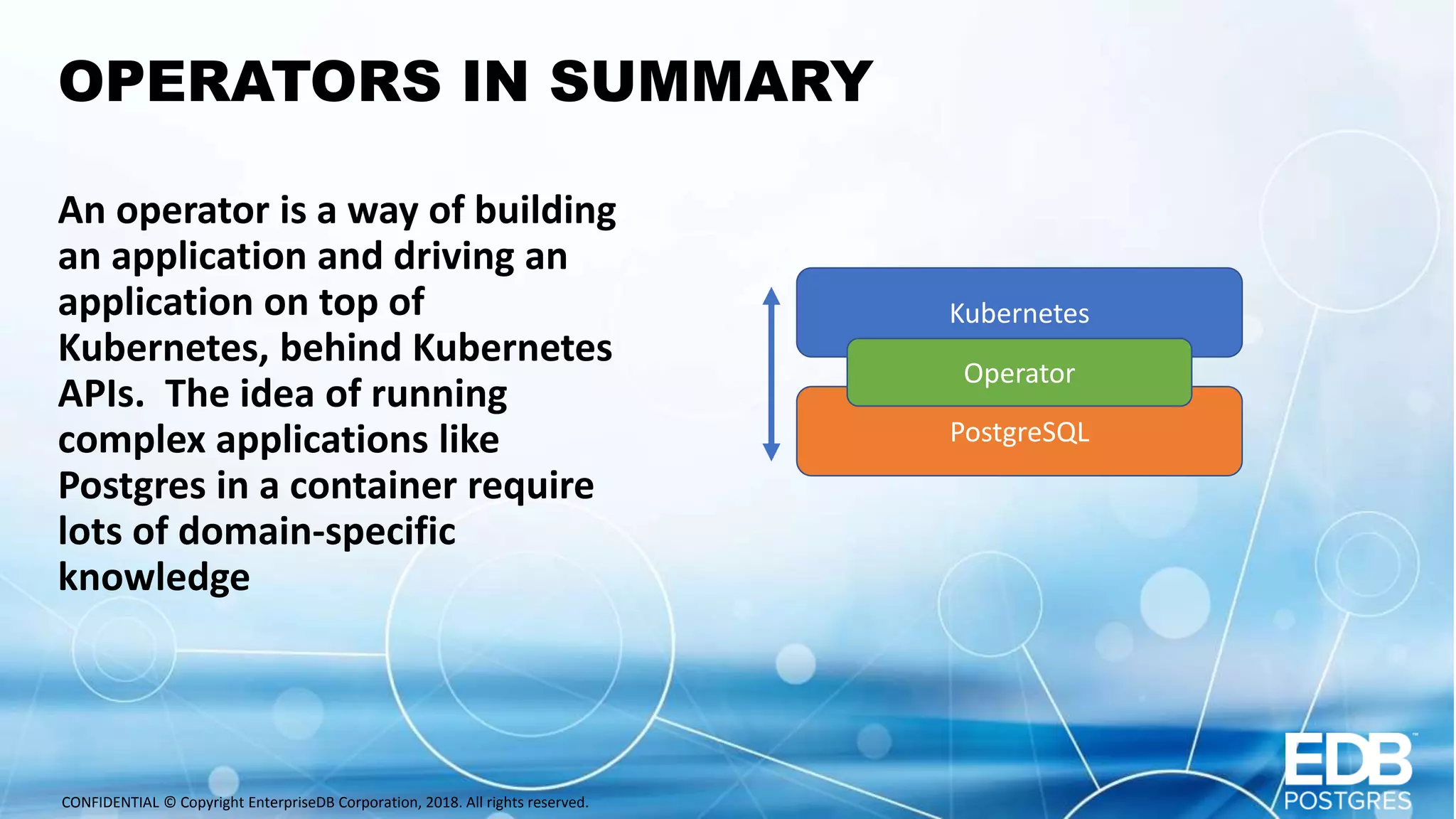
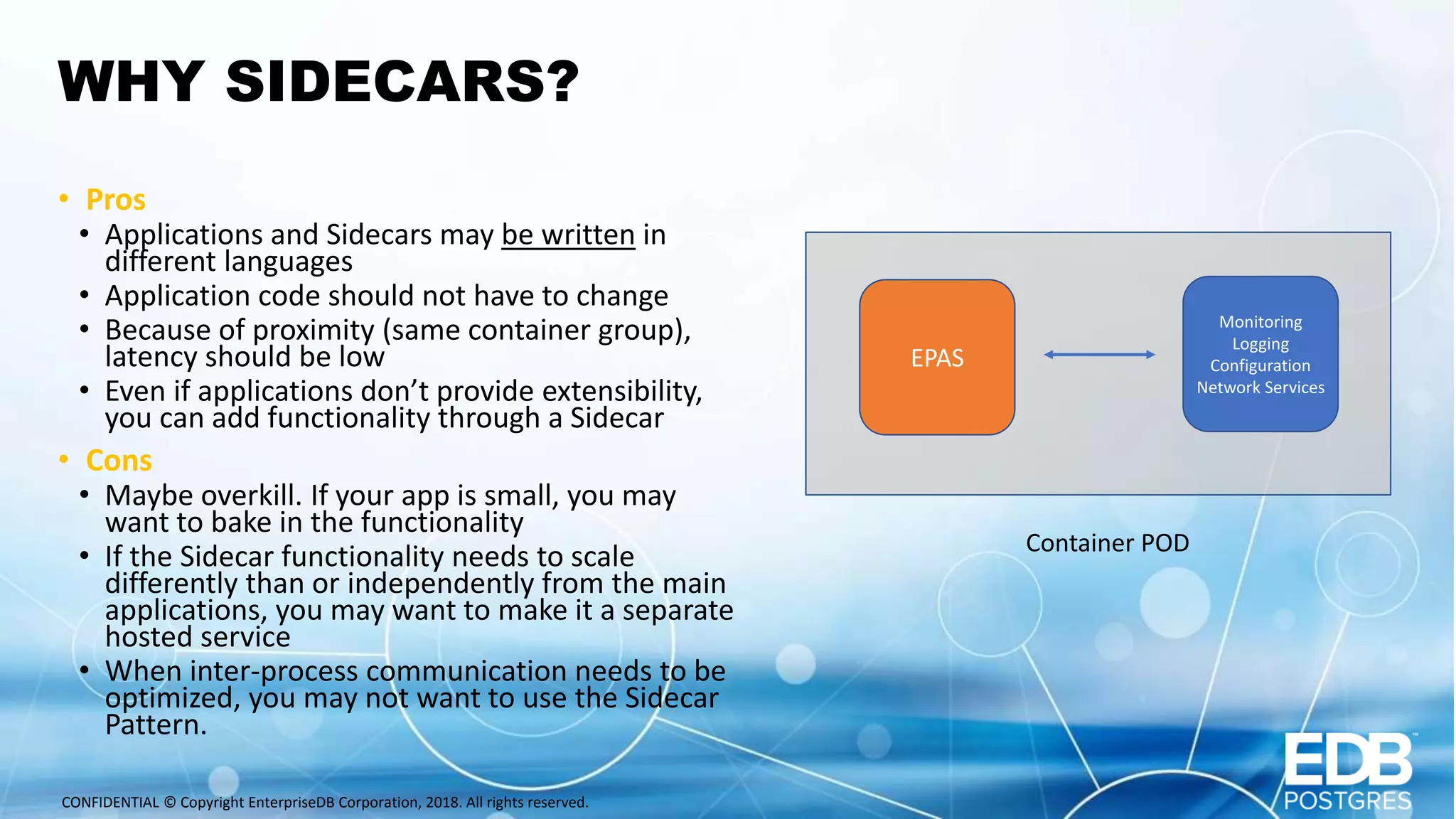
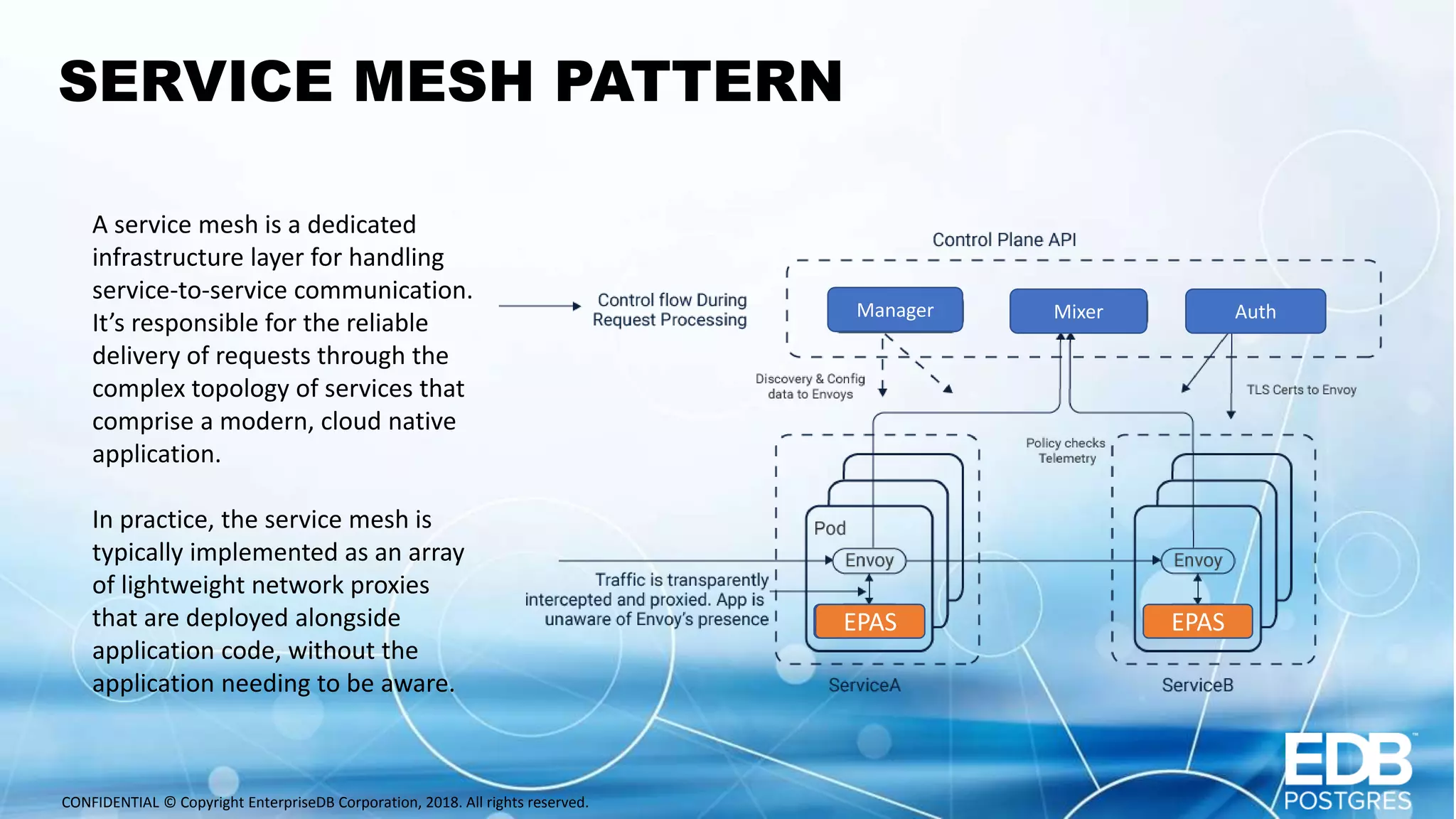
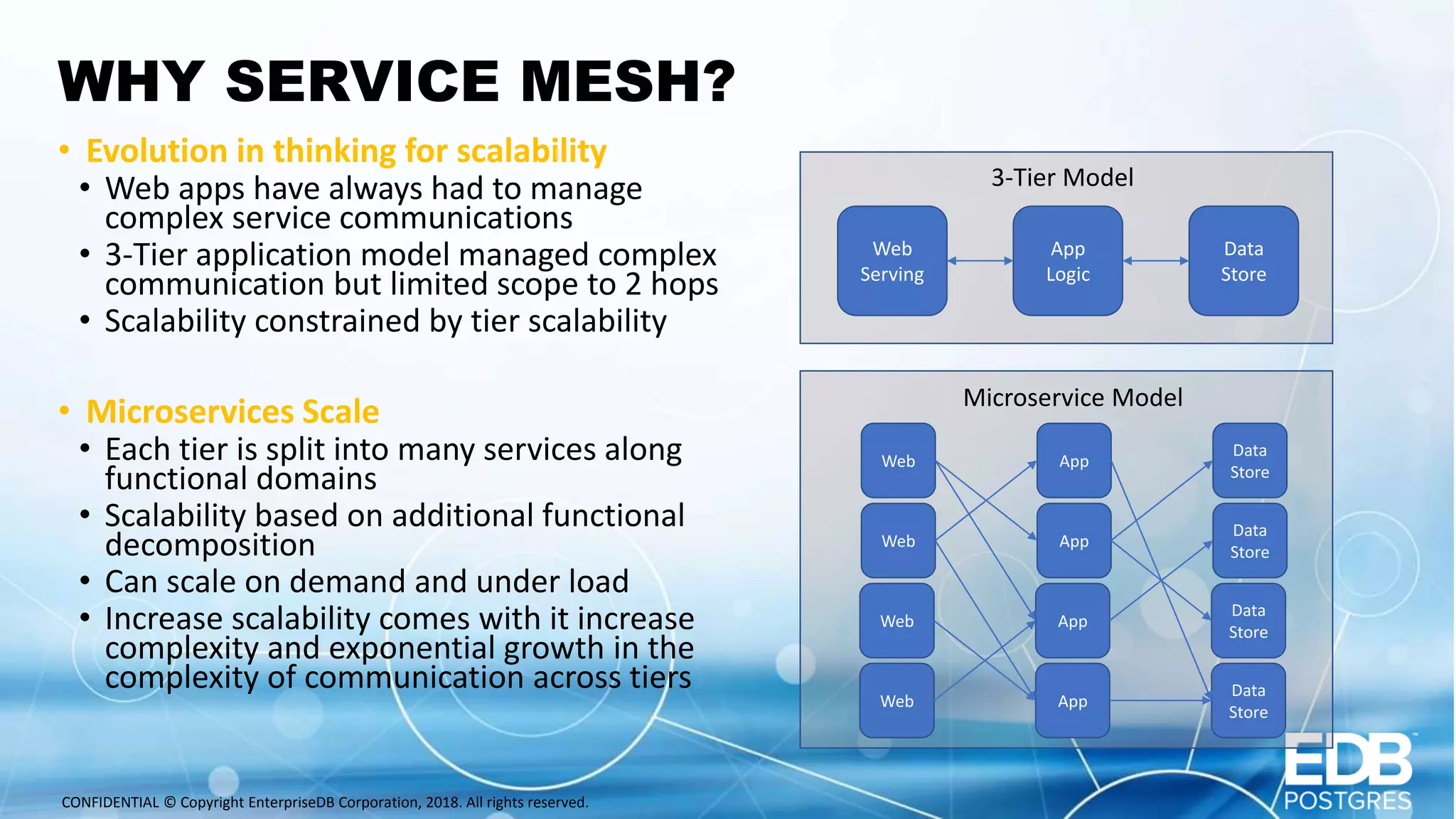
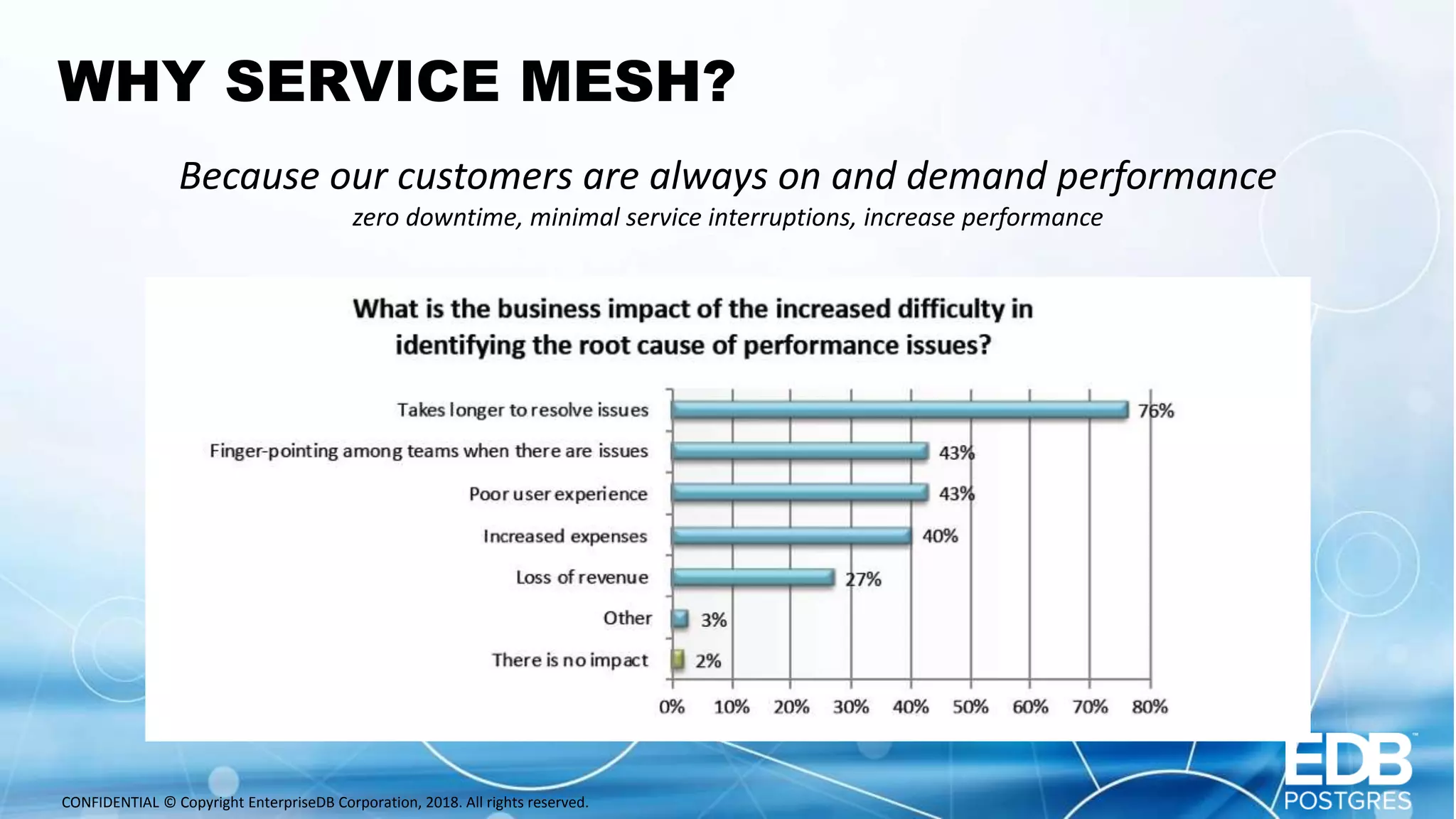
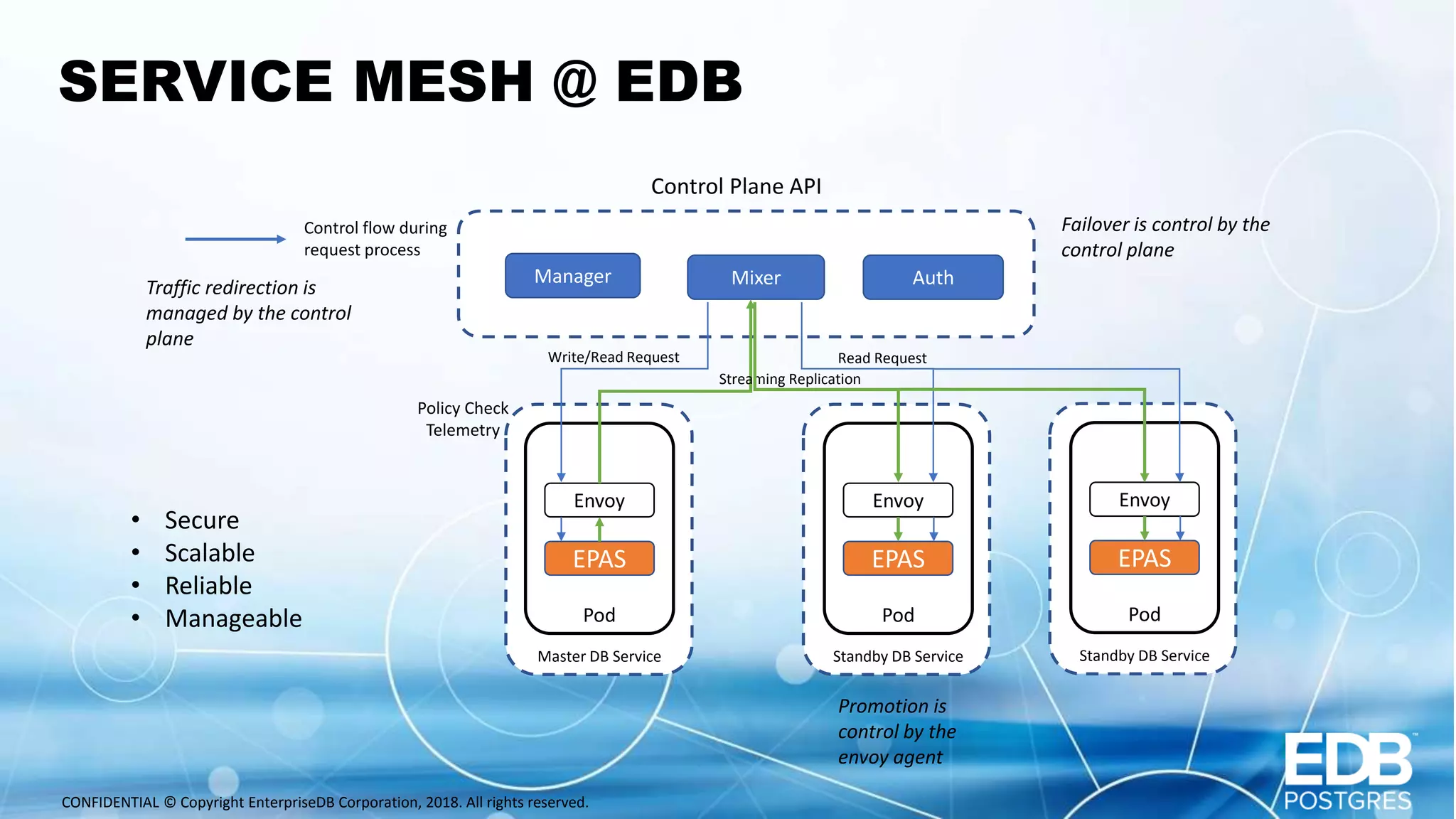
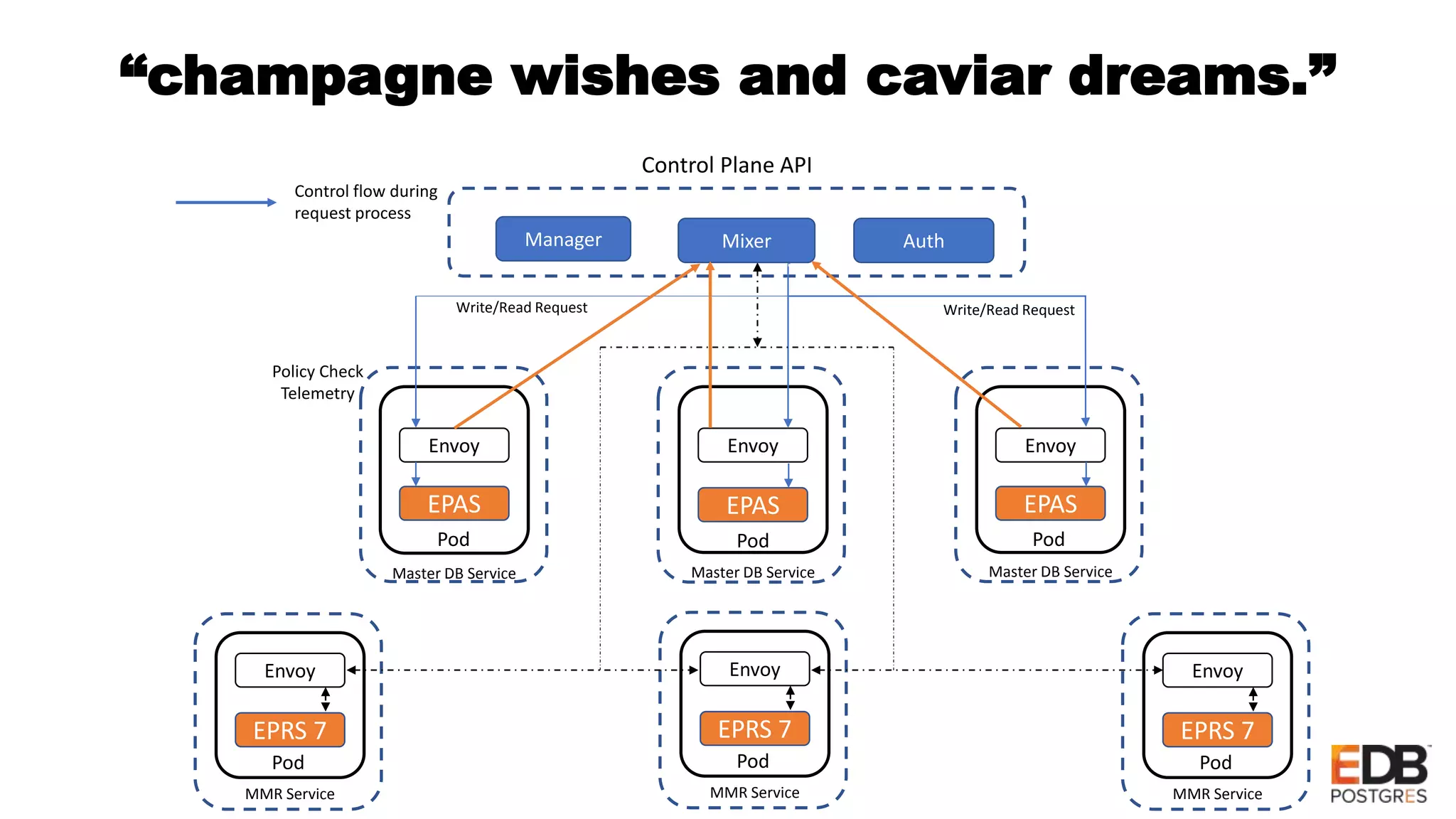
Oscar Herrera is the SVP of Global Services and Field CTO at EnterpriseDB. The document discusses database design patterns for Kubernetes including: - EPAS which provides a containerized PostgreSQL database with high availability. - Operators which extend Kubernetes capabilities by automating tasks like backups and resizing. - Sidecars which add functionality like monitoring and logging to database containers. - Service meshes which provide reliable communication between microservices through proxies. The patterns aim to abstract databases from applications and provide scalable, reliable database deployments in container and microservices environments.