The International Journal of Computer Networks & Communications (IJCNC) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of Computer Networks & Communications. The journal focuses on all technical and practical aspects of Computer Networks & data Communications. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on advanced networking concepts and establishing new collaborations in these areas.
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 DOI: 10.5121/ijcnc.2025.17306 89 A CLUSTER-BASED TRUSTED SECURE MULTIPATH ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Himanshu Bartwal 1 , Himani Sivaraman 1 , Jogendra Kumar 2 1 Department of Computer Science and Engineering, Jigyasa Univesity,Dehradun, Uttarakhand, India 2 Department of Computer Science and Engineering, GBPIET Pauri Garhwal Uttarakhand,India ABSTRACT Mobile Ad Hoc Network (MANET) is a self-organizing and flexible system. MANET systems manage sensitive data from many distinct applications in various domains. Its dynamic nature increases its vulnerability to numerous types of security threats. Many of the present approaches using indirect approaches provide false approximations of trust degrees. It is significantly required a good routing system that meets Quality of Service (QoS) standards and enhances network performance. In this paper purposed cluster-based trustworthy safe multipath routing (CTSMP-Routing) for mobile ad hoc networks (MANETs). Load balancing challenge is addressed by using a modified proportional topology optimization (MPTO) approach using geographical data related to network nodes. The Enhanced Seeker Search Optimization (ESSO) approach is used to compute trust degrees after the clustering phase considering numerous network constraints including node mobility, received signal strength, energy consumption, and cooperation rate. Assumed to be the service node, the node showing the highest degree of trust manages inter-cluster routing. We have developed a hybrid soft computing approach termed the multi-layer deep recurrent neural network (ML-DRNN) to enhance the optimal path-finding process. This method selects, among many routes between source and destination nodes, the best one quickly. The outcomes of this paper demonstrate that CTSMP-Routing provides effective protection against several attack paths within the MANET environment and displays better performance in regard to quality of service (QoS) requirements. KEYWORDS Mobile Ad-Hoc Networks (MANET), Modified Proportional Topology Optimization(MPTO), Enhanced Seeker Search Optimization(ESSO), Multi-Layer Deep Recurrent Neural Network (ML-DRNN) 1. INTRODUCTION All without depending on a permanent infrastructure, mobile ad hoc networks (MANETs) construct self-sustained wireless networks generated from mobile nodes [1]. These dynamically communicating nodes inside a MANET may use radio frequencies. MANETs provide a vital way for mobile users to interact with one another when either permanent infrastructure is not feasible or lacking [2]. The paths within a MANET often present difficulties including interference from outside sources, transmission issues, and node mobility by nature. Thanks in great part to the internet's explosive growth, MANETs have become somewhat popular recently [3]. These networks are unique in that they run free from any kind of supporting infrastructure. Furthermore easily integrated with current fixed infrastructure systems, they improve their communication capacity [4-5] MANET grew out of the explosion of affordable wireless networking devices and](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-1-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 90 desire for anytime, anywhere mobility. Here, several nodes are wirelessly linked and communication takes place between nodes inside each other's coverage zones. With this technology, mobile devices liberate themselves to go in any direction within the range of the radio connection, independent of permanent infrastructure [6]. The small transmission range emphasizes the need for every node's availability as it requires nodes to transmit messages across many hops [7]. Therefore, as it determines the best route between the data source and destination, the need for an effective routing protocol takes the front stage. In this sense, routing refers to provision for multipath connections to surrounding nodes dynamically established mostly via the mobile nodes acting as routers [8]. Nevertheless, this dynamic architecture, unique to wireless networks with nodes in motion, makes MANETs vulnerable to many security flaws [9]-[11]. Many routing strategies have been studied solve these issues with an eye on consistent data broadcast and greeting among nodes [12]. The demand- based AODV technique[13] has shown amazing performance among the current routing protocols [14-16] in several circumstances including varied mobility patterns, network density, and traffic loads. It does, however, have a problem wherein the number of control packages increases to maintain course planning to the goal. Moreover, studies have explored many guiding assaults started by evil nodes. In response to these concerns, methods using the trustworthiness of mobile nodes helping in routing or node authentication via certificate issuing have been investigated [17-18]. Precisely, recreating a new route from the foundation to the terminal may be a time-consuming procedure that increases control packets and consequent overhead when packet damage or route interruptions arise from assaults along the way. Maintaining the seamless running of MANETs provides a significant difficulty for security. Maintaining basic network services, data confidentiality, and integrity during transmission depends on addressing these security concerns [19]. MANETs' natural characteristics—open communication medium, changing topologies, absence of centralized monitoring—all of which contribute to a variety of security concerns [20] Therefore, the whole consistency of MANETs depends on the development of safer and more effective safe routing techniques. The rest of this paper is prearranged as follows. Section 2 offerings the appraisal of recent works linked to the secure routing for MANET. Segment 3 Network architecture of proposed CTSMP- Routing scheme. The thorough working procedure of planned CTSMP-Routing scheme is clarified in the Section 4. Simulation Parameters 5.The results and qualified analysis of planned and existing routing systems have debated in Section 6. Finally, the paper arranges in Section 6. 2. RELATED WORK Rajashanthi et al. [21] have introduced an inventive system designed to ensure secure and reliable data communication, hinging on QoS requirements and encryption techniques. Their approach combines multipath routing utilizing the AODV-BR protocol with optimal fuzzy logic. The development of these paths is guided by an adaptive grey wolf optimization method, aimed at identifying the most efficient route. To enhance data security, the system employs homomorphic encryption for data key management. Elmahdi et al. have [22] introduced an innovative approach to enhance the reliability and security of data transmission in MANETs, particularly in the face of potential black hole attacks. They achieved this by separating message distribution into many paths traveling toward the target using a modified AOMDV technique. For security reasons, a homomorphic encryption scheme was used to ensure data integrity and confidentiality. Tripathy et al. have [23] suggested an adaptive routing system fit for MANETs. This protocol demonstrates how dynamically changeable routing capabilities based on various metrics—](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-2-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 91 including diverse demand criteria and contextual features—can be attained. Among numerous aspects, these demand models include performance, security, and functional requirements. Under examination in this protocol are many contextual elements: the mobility of nodes or groups of nodes, trust values given to nodes, individual node resource restrictions, geographical context, and network node duties. Vatambeti [24] introduced the idea of grey wolf trust accumulation (GWTA). This approach greatly helps to identify prospective attacks by employing the fitness function of the GWTA model. Suspected attacked nodes are found and used for the final position of the network to greatly lower packet flow. Sirajuddin et al. [25] have developed a trust-based multipath routing protocol (TBSMR) to enhance the complete MANET presentation. TBSMS displays interesting strengths all aimed at increasing QoS by addressing numerous factors, including congestion management, packet loss reduction, malicious node identification, and safe data transmission facilitation. It considers numerous factors like node trust standards, congestion levels, and node attainable battery capacity all through the routing process. Simpson et al. [26] have offered a secure technique suited for the smart city scenario. Cooperative attacks need a coordinated effort across multiple IoT network nodes. Secure SEAL addresses challenges by building a fuzzy-based accountability scenario designed to lower security threats in smart cities. Benatia et al. [27] have developed an enhanced multipath quality-based routing system for urban settings (EMQS-UA). By selecting paths with superior link quality and more stable connections, this protocol ensures consistent data transmission; thus, in urban areas the focus should be on link excellence and consistency. Two key measurements—SNR and EMQS—UA combine. The SNR measurement increases the accuracy of the quality estimation process, therefore lowering the link quality degradation. This device is specifically suited to operate in urban settings where shadowing effects and background noise might seriously degrade connection quality. Combining these characteristics ensures that EMQS-UA is prepared to handle the challenges given by urban networking environments. Usha et al. [28] have shown an energy-efficient trust-aware routing ( NETAR) to increase trust levels across nodes in MANETs. NETAR employs a varied approach to develop trust among nodes by analyzing the trust rate of neighboring nodes, evaluating the available bandwidth, predicting energy usage, and recognizing probable hostile activities. Ran et al. [29] have introduced a multi-path QOS routing security algorithm by using blockchain, which enhances the traditional AODV protocol (AODV-MQS). This algorithm incorporates a chain of nodes within the network and preserves the states of all nodes by designating certain intermediate nodes along this chain. The Blockchain technology uses smart contracts to filter out nodes that adhere to QoS constraints. Through the application of smart contracts within the blockchain network, AODV-MQS identifies two distinct communication paths that are not significantly correlated. One path serves as the primary route, while the other acts as a standby route. It's important to note that this mechanism focuses primarily on un-trusted nodes within the network. Hemalatha et al. [30] have introduced an approach for establishing optimal, loop-free routes using the equilibrium optimizer (EO) in combination with fuzzy logic, ensuring the continuity of data transmission. EO with fuzzy logic during route exploration to determine the most efficient path for packet transmission. The selection of appropriate nodes for routing, they incorporates the Levy Flight distribution mechanism. In the route conservation phase, the system assesses the](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-3-2048.jpg)


![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 95 performance that determines the value Min p . Based on the improved SIMP technique, the substantial interruption scheme is written as follows: ] 1 , 0 [ , ) ( 0 h Min x h Min h p e e p e p e (2) For the minimization optimization problematic, an better density filter is compute as follows. h h B g g g h B g g h h p I I p , , 1 ~ (3) All g elements at h element distance are filtered densities measured h B from their respective centers Min R . The ) ( h p e derivative is the weighting g h I , factor between the elements h and g )) , ( , 0 ( , g h c R Max I Min g h (4) where h and g are the geometric center ) , ( g h c distance between the elements and the radius Min R of the filter. An additional optimization scheme was created for the density variable h g ra out h D p v p ~ ~ (5) In order for the compliance coefficient to drama a larger role in updating the density mutable in the inner loop, the obedience coefficient filter introduces a q. parameter. Based on a combination of matching factor and filtering techniques, it expresses: h h B g y g g h B g g h h D I I D , , 1 ~ (6) Correspondence coefficient is compute by Bickley threshold function, B g g g h h v D D D 1 (7) The residual volume of the material VRM is an significant midway variable for updating the density adjustable in the inner loop, which is printed as: B h h pro h Sa ra v p v v (8) The pro h p density adjustable found at each restatement of the inner cycle, h is the variable increase in element density out h p , and λ is the conformational inspiration coefficient. h and g represent the item relevance out h p . h D and g D , represents the relevance ratio and filtered relevance ratio, respectively, h D and h D ~ , y is the influence ratio of the relevance ratio.](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-7-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 96 out h pro h out h p p p (9) Based on the weighting factor, the variable density gain of component h is designed as a prejudiced average of the variable thickness gains of its neighboring element. Then, using the drinkable density mutable increment and the density mutable, a density variable optimization system can be describe as follows. out h pro h out h p p p ~ (10) where out h p ~ is the elemental clean density adjustable increment, which is assumed as follows. h h B g out g g h B g g h out h p I I p , , 1 ~ (11) where out g p is the variable compactness augmentation of component g adjacent to element h. According to the MPTO algorithm and MAX-MIN system, the control scheme for the values of density variable star is articulated as follows. Max out h Max Max out h Min out h out h Min pro h p p p p p p p p p p p , , , min (12) where Min p and Max p are the higher and lesser limitations of density variable star, individually. Here, 0 Min p and 1 Min p . The working step involved in the cluster creation using MPTO is explained in Algorithm 1. Algorithm 1 Cluster formation using MPTO Input : Number of mobile nodes, maximum iteration, threshold condition Output : Cluster formation 1. Setup FE and obedience analyses and sieving 2. Define the material interpolation ] 1 , 0 [ , ) ( 0 h Min x h Min h p e e p e p e 3. Until convergence 4. Check stop criteria, break if satisfied 5. Compute density filter by using h h B g g g h B g g h h p I I p , , 1 ~ 6 Compute correspondence coefficient B g g g h h v D D D 1 7. Apply filter 8. Update density 9. Find the density variable optimization out h pro h out h p p p ](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-8-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 97 10. Perform clean density adjustable increment, h h B g out g g h B g g h out h p I I p , , 1 ~ 11. End if 12. Update the final value 13. End 3.2. Enhanced Seeker Search Optimization (ESSO) Enhanced seeker search optimization (ESSO) approach, trust degrees dependent on these design constraints are calculated. This optimization technique identifies the most reliable and trustworthy nodes in the network based on the already provided criteria. ESSO maximizes the choice of these nodes by weighing their conformity with these limitations. The ESSO technique computes a most highly trusted node that is chosen to be the service node. This node acts as a focal point for inter-cluster routing and is responsible for the routing of data between clusters and ensuring secure and efficient communication within the MANET. The egoistic direction ) ( , s F e h , altruistic direction ) ( , s F m h , and pre-emptive direction ) ( , s F X h of the h-th individual in any dimension can be obtained as follows. ) ( ) ( , , s p x s F h best h e h (13) ) ( ) ( , , s p j s F h best h m h (14) ) ( ) ( ) ( 2 1 , s p s p s F h h X h (15) The chaser uses a random weighted average technique to obtain the search orientation. )) ( ) ( ) ( ( ) ( , 2 , 1 , s F s F s F sign s F m h e h X h h (16) where: 1 s , 2 s ∈ {s, s − 1, s − 2}, ) ( 1 s ph and ) ( 2 s ph are the best advantages of )} ( ), 1 ( ), 2 ( { s p s p s p h h h separately; best h j , is the optimal position in the region where the h- th exploration factor is positioned; best h x , is the optimum neighborhood from the h-th exploration factor to the current locality; 1 and 2 are random numbers in [0,1]. ω is the weight of inertia. 2 2 2 ) ( E (17) where α and δ are the parameters of the membership function and the probability that the output variable exceeds [−3δ, 3δ] is less than 0.0111. Under normal conditions, an individual's optimal level Max = 1.0 t h H s H t Min Max h Max h ,... 2 , 1 , (18) C g Rand h g h ,... 2 , 1 ), 1 , ( , (19)](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-9-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 98 Here h H is the count of the arrangement ) (s ph of the existing those arranged from high to low by meaning value. And the purpose rand ) 1 , ( h is the real amount in any divider [ 1 , h ]. ) ln( ) ( hg hg hg s (20) where, hg is a restriction of the Gaussian circulation meaning, which is distinct as follows. ) ( Max Min hg p p ABS p (21) Here, ω is the inertial weight. As the evolutionary algebra upsurges, ω decreases linearly from 0.9 to 0.1. Min p and Max p are are the minimum and maximum values of the function, respectively. After receiving the scout track and the person's scout step dimension, the location update is specified as follows C g t h s F s s p s p hg hg hg hg ,.... 2 , 1 ; ,.... 2 , 1 ) ( ) ( ) ( ) 1 ( (22) where h denotes the h-th searcher separate, g denotes the discrete dimension; ) (s Fhg and ) (s hg respectively represents the seekers’ search track and examination step size at time s, ) (s phg and ) 1 ( s phg correspondingly characterize the hunters’ site at time s and (s + 1). The continuous brink x∈ [0,1] is set as the likelihood of seeker h p being seized by a triple black hole system. For each seeker h p , a accidental number l ∈ [0,1] is produced in each restatement. If l ≤ x, h p is detained by a triple black hole scheme; otherwise, it is efficient in the outdated way. 2 1 3 1 1 2 3 1 1 3 , 2 / ) ) ( ( ) ( , 2 / ) ) ( ( ) 1 ( x L RR p s jbest x L x RR s jbest x L RR p s jbest s p Max Min hg (23) where h characterizes the h-th separate, g characterizes the discrete length; ) (s jbest is the global optimal solution of group t in the entire populace; Min Max p p / is the upper/lower limit of the seeker exploration region, the continuous verge 1 x , 2 x ∈ [0,1], and 1 x < 2 x , 3 R is a random number [−1,1]. The constant threshold xx∈ [0,1] is a random value K∈ [0,1] for each dimension of each seeker. ) 1 ( ) ( ) 1 ( 4 R s p s p hg hg (24) where: ψ is the meddling degree, and 4 R is the haphazard number [−1,1].the seekers’ location is reset so that they are haphazardly distributed everywhere ) (s jbest , to hypothetically jump out of local optimality, distinct as follows. ) 1 ( | 01 . 0 | ) ( ) 1 ( | s f s f s f j j j (25)](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-10-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 99 m hg R s jbest s jbest s p )) ( ) 1 ( ( ) 1 ( ' (26) where: ) 1 ( / ) ( s f s f j j are the meaning values conforming to the global ideal of the s/s−1 cohort correspondingly, and m R is the accidental number [−1,1]. ) 1 ( ' s jbest is the current optimal explanation of group t + 1. The working process of trust degree computation and service node selection using ESSO is explained in Algorithm 2. Algorithm 2 Trust degree computation and service node selection using ESSO Input : Number of clusters, Number of constraints, maximum iteration Output : Trust degree/service node 1. Population initialization. Generate an initial species group. 2. Define random prejudiced average to obtain the exploration orientation )) ( ) ( ) ( ( ) ( , 2 , 1 , s F s F s F sign s F m h e h X h h 3. If s =1 4. While the stopping condition is not satisfied. 5. Generate the search direction 6 Totalling the triple black hole system 7. end if 8. The elastic collision variation; Define Gaussian distribution function is 2 2 2 ) ( E 9. Compute location update C g t h s F s s p s p hg hg hg hg ,.... 2 , 1 ; ,.... 2 , 1 ) ( ) ( ) ( ) 1 ( 10. Compute potentially jump out of local optimality ) 1 ( | 01 . 0 | ) ( ) 1 ( | s f s f s f j j j 11. Calculate the fitness and judge the optimal solution. 12. End if 13. S=S+1 14. If Max S s ,then jump to 3; 15. Else stop 16. Find the best output values 3.3. Multi-Layer Deep Recurrent Neural Network (ML-DRNN) An Optimal path finder is used to select the most suitable route for data transmission between the source and destination nodes in a MANET. The ML-DRNN excels in analyzing and predicting the optimal path from among multiple available options in the dynamic MANET environment. The ML-DRNN is trained on historical data, enabling it to learn the behavior of the MANET over time. It considers many network-specific criteria, node mobility, connection quality, interference, and other elements. The ML-DRNN has major benefits mostly related to its recurrent character, which enables the memory of previous states and use that knowledge to project future network circumstances. The ML-DRNN's main goal is to choose, among the many paths accessible between the source and destination nodes, the most best one for data transmission. Analyzing present network circumstances, using previous trends and real-time data helps one to choose the best path. The ML-DRNN's real-time decision-making capabilities, capacity to identify complicated patterns, and flexibility to changing network circumstances help to transmit data](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-11-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 100 effectively and lower resource usage. Applied as previously detailed, the Stockwell transform is a time-frequency based signal transform. We define the continuous T-transform of the q(s) time series as follows. Fs h E F s j s q F T 2 ) . ( ) ( ) , ( (27) F=Frequency: s, =time Function Modulation Gaussian E F F j s : 2 | | ) , ( 2 3 2 One defines the unconnected T-transform of a gesture as follows. B ag h E b a z b a Q b g T 2 ] , [ ] [ ] , [ (28) where Q[a+ne]: Discrete Fourier Transmute of the indication loosened by b. B aK g B K E K q B a Q 2 1 0 ] [ 1 ] [ (29) b a g E b a Z 2 2 2 ] [ (30) Stockwell transform is applied to the vectorized representation of each amino acid sequence, resulting in a complex T-matrix that is A-valued and B-valued. B A AB A A A B B T T T T T T T T T T T T Mat T L L L L L L L L 3 2 1 2 23 22 21 1 13 12 11 Four different System features [SF] are calculated from the T-matrix of the encoded protein arrangement.: ) .... , , , ( 3 2 1 1 MAX B MAX MAX MAX c c c c STD SF ) .... , , , ( 3 2 1 2 MAX A MAX MAX MAX r r r r STD SF ) .... , , , ( 3 2 1 3 MAX B MAX MAX MAX c c c c Energy SF ) _ ( 4 contour phase STD SF h c : column wise supreme of absolute value of S-matrix. h r : row wise extreme of absolute value of T-matrix. STD: average deviation. Each amino acid sequence X can be characterized as, ] ... ... ..... ... ... ], 1 [ ], 0 [ [ 16 13 9 8 5 4 1 X X X X X X X sSNE sSNE X ](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-12-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 101 vectors Feature reduced sSNE sSNE ] 1 [ ] 0 [ ] 1 [ ... 4 1 vector transform stockwell X X ] 2 [ ... 8 5 vector transform stockwell X X ] 3 [ ... 12 9 vector transform stockwell X X ] 4 [ ... 16 13 vector transform stockwell X X The traditional recurrent network faces the gradient disappearing problem because the long-term dependences of the arrangements are masked by the short-term dependences. )) , ( ( 1 s s i s i p z F i (31) where F() is the nonlinear beginning function, s p the current input and s i and 1 s i are hidden unit states are s and s − 1, respectively. Closed loop units protect hidden level memory with reset s r and s w forget gates. The purpose of the GRU part is to reconstruct a new reminiscence s i ~ , which in attitude should characteristic of the current input and a non-linear alteration of the preceding memory. Adjust the top combination of forward and present inputs. 1 ) 1 ( ~ : s s s s s i w i w i state Hidden (32) ]) , [ ( : 1 ) ( ) ( s s s w s i p p Z w get Forget (33) ]) , [ ( tan ~ : 1 s s s s i R p Z i i memory New (34) ]) , [ ( : Re 1 s s R s i p Z r gate set (35) p E p 1 1 ) ( (36) where is the component wise operator. The working process of optimal path finder using ML- DRNN is explained in Algorithm 3. Algorithm 3 Optimal path finder using ML-DRNN Input : Number of paths, Number of attacks, attacks characteristics, threshold condition Output : Optimal paths among multiple paths 1. Initialize the random population 2. Define continuous T-transform of the ) (s q time series Fs h E F s j s q F T 2 ) . ( ) ( ) , ( 3. If i=0 , j=1 4. While Do 5. Compute DFT of the signal loosened by b B aK g B K E K q B a Q 2 1 0 ] [ 1 ] [ 6 Define the updation process using )) , ( ( 1 s s i s i p z F i 7 Compute the threshold for optimal combination of forward and current](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-13-2048.jpg)
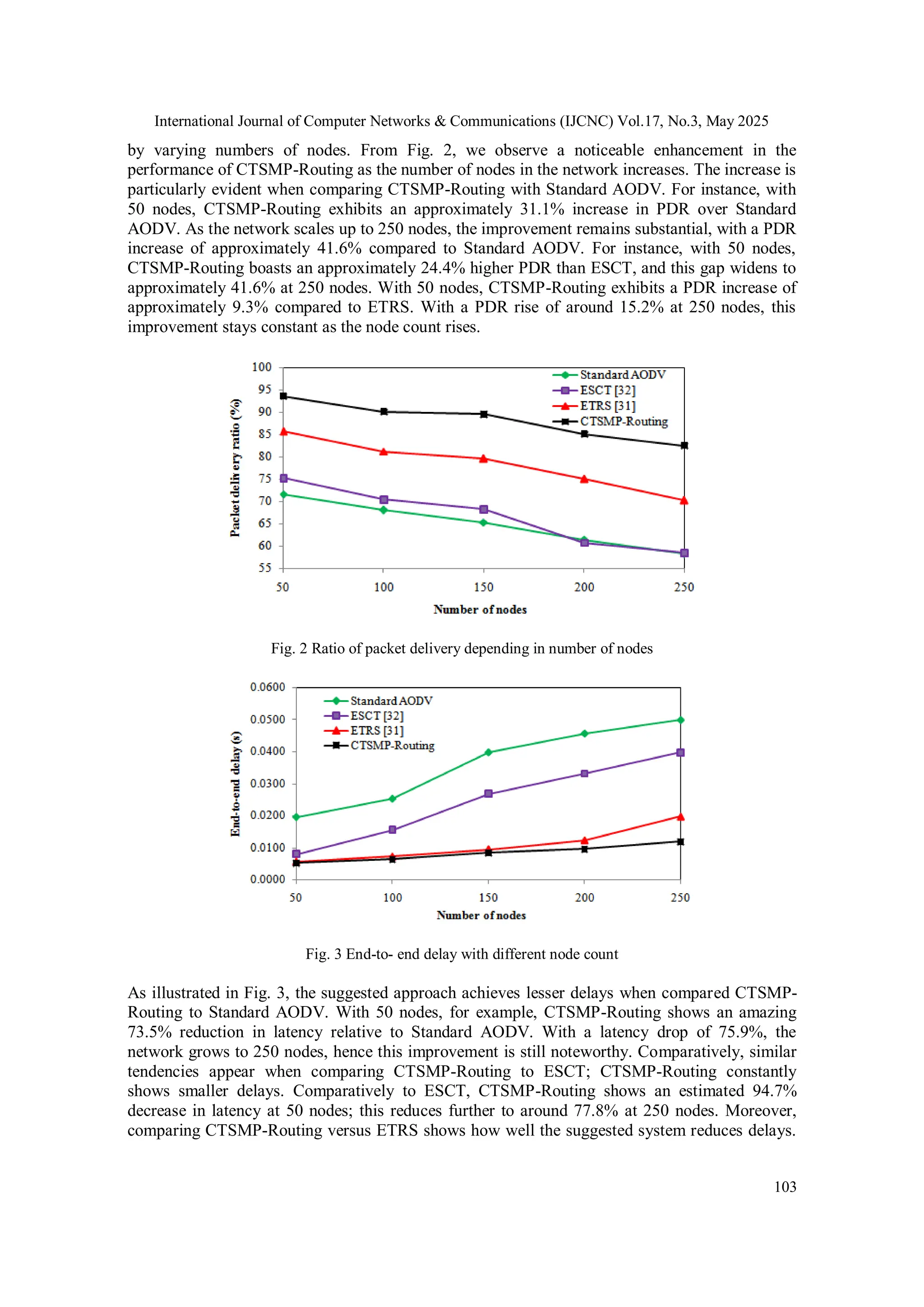
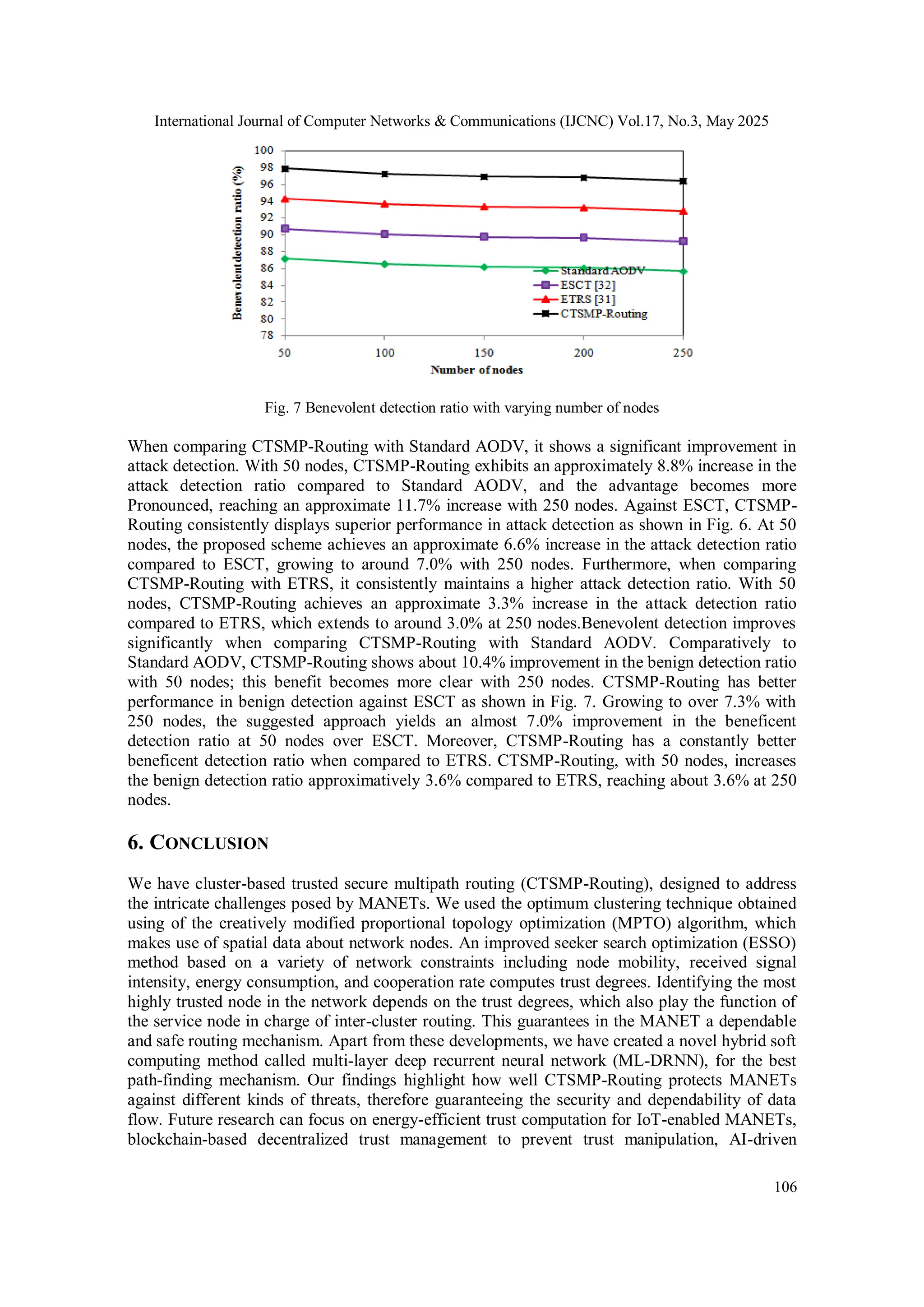
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 102 inputs. p E p 1 1 ) ( 8. End if 9. Update the final output value 10. End 4. SIMULATION PARAMETERS In this section, we delve into the outcomes and comparative analysis of the proposed CTSMP- Routing scheme alongside established routing schemes for MANETs under various simulation scenarios. To perform this evaluation, we have fully implemented the entire CTSMP-Routing scheme within the network simulator (NS3) tool [31]. The comparison encompasses the assessment of the CTSMP-Routing scheme against existing schemes, which include the standard AODV protocol, the evolutionary self-cooperative trust (ESCT) scheme [32], and the efficient trust-based routing scheme (ETRS) [33-34]. The evaluation is extensive and encompasses the analysis of diverse QoS metrics, including but not limited to packet delivery ratio, end-to-end delay, throughput, packet drop ratio, attack detection ratio, and benevolent detection ratio. 4.1. Simulation_Setup A specific MANET scenario is designed, featuring randomly positioned nodes following a random waypoint mobility pattern. Within this context, certain nodes are deliberately designated as misbehaving nodes, tasked with the unauthorized action of discarding any data packets not belonging to them. Table 1 provides a comprehensive overview of the simulation parameters Table 1 Simulation parameters Parameter Value Network size 1500×1500 Number of mobile nodes 50, 100, 150, 200 and 250 Node mobility (mps) 5, 10, 15,20 and 25 Number of attacks 2, 4, 6, 8 and 10 Attack types Selfish and black hole Data rate 2 Mbps MAC protocol IEEE 802.11 Transmission range 250m Mobility model CBR (UDP) Packet length 512 bytes Packet arrival rate 4 packets/s Default simulation time 2000s 5. RESULTS AND DISCUSSION FOR COMPARISON WITH VARYING NUMBER OF NODES Table 2 presents a comparative analysis that examines the performance of the proposed CTSMP- Routing scheme in contrast to existing routing schemes across different scenarios characterized](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-14-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 107 adaptive routing mechanisms for dynamic decision-making, and cross-layer security approaches to defend against multi-layer attacks. Addressing these aspects will further refine MANET security, optimize routing efficiency, and contribute to the evolution of secure and intelligent network communication. CONFLICTS OF INTEREST The authors declare no conflict of interest. REFERENCES [1] Ali, H., & Khan, M. (2022). Intelligent intrusion detection in MANETs using fuzzy logic and machine learning. IEEE Access, 10, pp. 17893–17906. DOI: 10.1109/ACCESS.2022.3147893 [2] Benatia, S.E., Smail, O., Meftah, B., Rebbah, M. and Cousin, B., 2021. A reliable multipath routing protocol based on link quality and stability for MANETs in urban areas. Simulation Modelling Practice and Theory, 113, p.102397. [3] Borkar, G.M. and Mahajan, A.R., 2017. A secure and trust based on-demand multipath routing scheme for self-organized mobile ad-hoc networks. Wireless Networks, 23(8), pp.2455-2472. [4] Cai, R.J., Li, X.J. and Chong, P.H.J., 2018. An evolutionary self-cooperative trust scheme against routing disruptions in MANETs. IEEE transactions on Mobile Computing, 18(1), pp.42-55. [5] Chen, Y., & Wu, H. (2025). AI-driven QoS-aware MANET protocols: A deep learning-based approach for QoS prediction and adaptive routing. IEEE Transactions on Wireless Communications, 74(2), pp. 235–249. DOI: 10.1109/TWC.2025.3412345 [6] Devi, V.S. and Hegde, N.P., 2018. Multipath security aware routing protocol for MANET based on trust enhanced cluster mechanism for lossless multimedia data transfer. Wireless Personal Communications, 100, pp.923-940. [7] Dhurandher, S.K., Obaidat, M.S., Verma, K., Gupta, P. and Dhurandher, P., 2010. Faces: friend- based ad hoc routing using challenges to establish security in MANETs systems. IEEE Systems Journal, 5(2), pp.176-188. [8] Elmahdi, E., Yoo, S.M. and Sharshembiev, K., 2020. Secure and reliable data forwarding using homomorphic encryption against blackhole attacks in mobile ad hoc networks. Journal of Information Security and Applications, 51, p.102425. [9] El-Sayed, H., & Omar, M. (2025). QoS-aware multipath routing using reinforcement learning in MANETs. IEEE Internet of Things Journal, 12(5), pp. 1075–1089. DOI: 10.1109/JIOT.2025.3578901 [10] Ghosh, A., & Roy, P. (2023). Hybrid trust management for secure routing in MANETs using blockchain and AI. Computer Networks, 225, 109876, pp. 1–18. DOI: 10.1016/j.comnet.2023.109876 [11] Gundeboyina Srinivasalu and Hanumanthappa Umadevi,"Cluster Based Routing Using Energy and Distance Aware Multi-Objective Golden Eagle Optimization in Wireless Sensor Network ", International Journal of Computer Networks & Communications (IJCNC) Vol.14, No.3, May 2022, PP 37-53, DOI: 10.5121/ijcnc.2022.14303 [12] Hammamouche, A., Omar, M., Djebari, N. and Tari, A., 2018. Lightweight reputation-based approach against simple and cooperative black-hole attacks for MANET. Journal of information security and applications, 43, pp.12-20. [13] Hemalatha, R., Umamaheswari, R. and Jothi, S., 2021. LF distribution and equilibrium optimizer based fuzzy logic for multipath routing in MANET. Wireless Personal Communications, 120(2), pp.1837-1861. [14] Hurley-Smith, D., Wetherall, J. and Adekunle, A., 2017. SUPERMAN: security using pre-existing routing for mobile ad hoc networks. IEEE Transactions on Mobile Computing, 16(10), pp.2927- 2940. [15] Kala Venugopal and T G Basavaraju," Congestion and Energy Aware Multi-pathload Balancing Routing for LLNS", International Journal of Computer Networks & Communications (IJCNC) Vol.15, No.3, May 2023,PP 71-92, DOI: 10.5121/ijcnc.2023.15305 [16] Kasthuribai, P.T. and Sundararajan, M., 2018. Secured and QoS based energy-aware multipath routing in MANET. Wireless Personal Communications, 101, pp.2349-2364.](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-19-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.3, May 2025 108 [17] Kumar, R., & Sharma, V. (2024). A trust-based secure routing protocol for MANETs using fuzzy logic. International Journal of Computer Networks & Communications (IJCNC), 16(2), pp. 45–60. DOI: 10.5121/ijcnc.2024.16203 [18] Mahamune, A.A. and Chandane, M.M., 2021. An efficient trust-based routing scheme against malicious communication in MANET. International Journal of Wireless Information Networks, 28(3), pp.344-361. [19] Muneeswari, B. and Manikandan, M.S.K., 2019. Defending against false data attacks in 3D grid- based MANET using soft computing approaches. Soft Computing, 23, pp.8579-8595. [20] Nguyen, T., & Park, J. (2024). Soft computing approaches for MANET security: A hybrid neural network-based trust model. Expert Systems with Applications, 237, 120345, pp. 1–20. DOI: 10.1016/j.eswa.2024.120345 [21] Paramasivan, B., Prakash, M.J.V. and Kaliappan, M., 2015. Development of a secure routing protocol using game theory model in mobile ad hoc networks. Journal of Communications and Networks, 17(1), pp.75-83. [22] Patel, D., & Mehta, S. (2023). QoS-aware multipath routing for MANETs using AI-based decision- making. International Journal of Computer Networks & Communications (IJCNC), 15(4), pp. 78– 92. DOI: 10.5121/ijcnc.2023.15405 [23] Radwan S.Abujassar," Enhancing Traffic Routing Inside a Network through IoT Technology & Network Clustering by Selecting Smart Leader Nodes", International Journal of Computer Networks & Communications (IJCNC) Vol.16, No.2, March 2024, PP 1-24, DOI: 10.5121/ijcnc.2024.16201 [24] Rahman, M., & Patel, S. (2022). Fuzzy logic-based trust evaluation system to improve routing reliability in MANETs. Future Generation Computer Systems, 134, pp. 567–580. DOI: 10.1016/j.future.2022.02.045 [25] Rajashanthi, M. and Valarmathi, K., 2020. A secure trusted multipath routing and optimal fuzzy logic for enhancing QoS in MANETs. Wireless Personal Communications, 112, pp.75-90. [26] Rajendran, N., Jawahar, P.K. and Priyadarshini, R., 2019. Cross centric intrusion detection system for secure routing over black hole attacks in MANETs. Computer Communications, 148, pp.129- 135. [27] Ran, C., Yan, S., Huang, L. and Zhang, L., 2021. An improved AODV routing security algorithm based on blockchain technology in ad hoc network. EURASIP Journal on Wireless Communications and Networking, 2021(1), pp.1-16. [28] Robinson, Y.H., Krishnan, R.S., Julie, E.G., Kumar, R. and Thong, P.H., 2019. Neighbor knowledge-based rebroadcast algorithm for minimizing the routing overhead in mobile ad-hoc networks. Ad Hoc Networks, 93, p.101896. [29] Sharma, P., & Singh, R. (2023). A dynamic trust-based secure routing protocol to detect and mitigate insider attacks in MANETs. Ad Hoc Networks, 145, 103123, pp. 1–15. DOI: 10.1016/j.adhoc.2023.103123 [30] Simpson, S.V. and Nagarajan, G., 2021. A fuzzy based co-operative blackmailing attack detection scheme for edge computing nodes in MANET-IOT environment. Future Generation Computer Systems, 125, pp.544-563. [31] Sirajuddin, M., Rupa, C., Iwendi, C. and Biamba, C., 2021. TBSMR: A trust-based secure multipath routing protocol for enhancing the QoS of the mobile ad hoc network. Security and Communication Networks, 2021, pp.1-9. [32] Tripathy, B.K., Jena, S.K., Bera, P. and Das, S., 2020. An adaptive secure and efficient routing protocol for mobile ad hoc networks. Wireless Personal Communications, 114, pp.1339-1370. [33] Vatambeti, R., 2020. A novel wolf based trust accumulation approach for preventing the malicious activities in mobile ad hoc network. Wireless Personal Communications, 113, pp.2141-2166. [34] Zhang, L., & Wei, X. (2024). An adaptive QoS-aware routing algorithm optimizing delay and throughput in MANETs. IEEE Transactions on Communications, 72(3), pp. 459–472. DOI: 10.1109/TCOMM.2024.3309875](https://image.slidesharecdn.com/17325cnc06-250709125411-3f60be2d/75/A-Cluster-Based-Trusted-Secure-Multipath-Routing-Protocol-for-Mobile-Ad-Hoc-Networks-20-2048.jpg)
