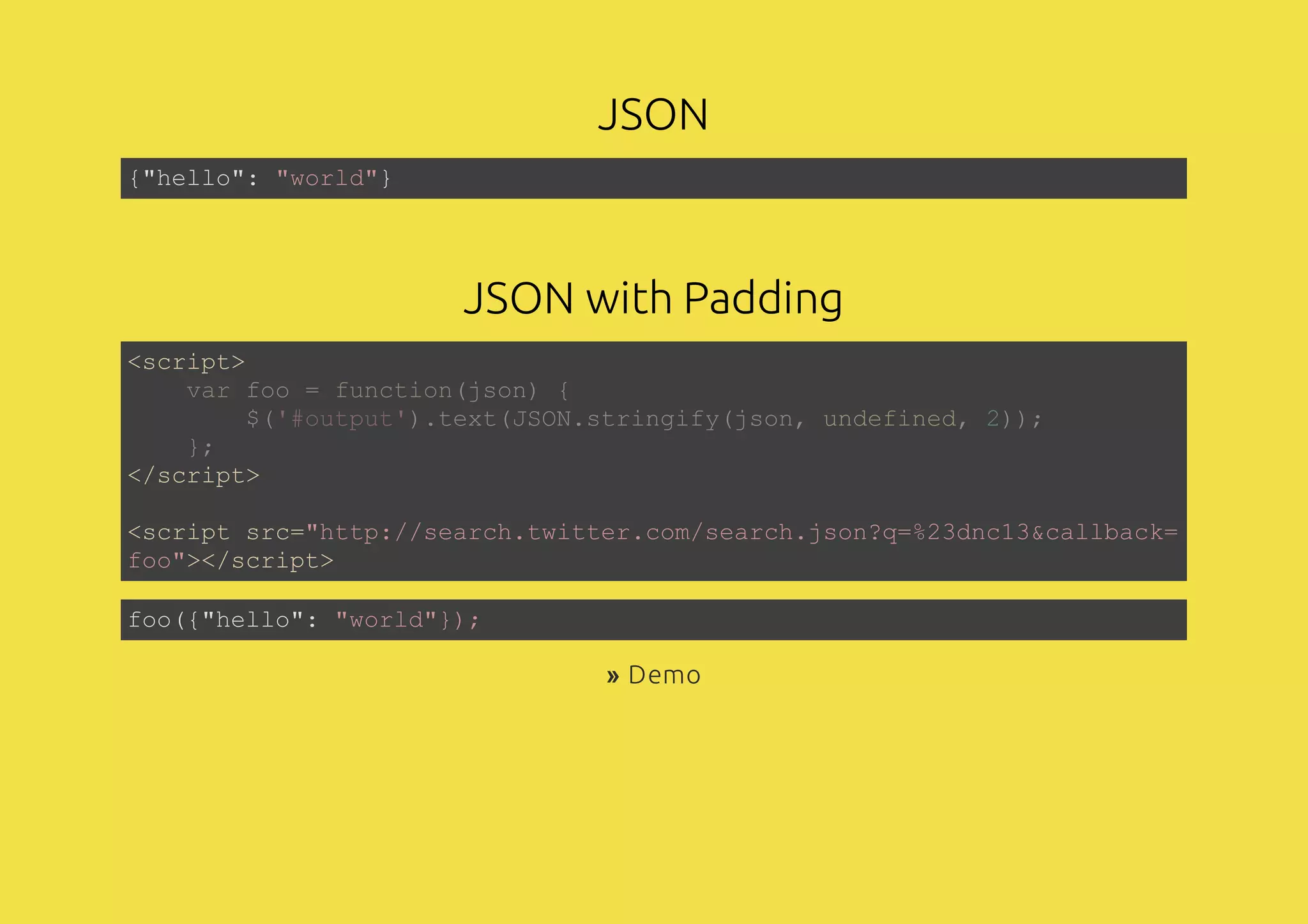
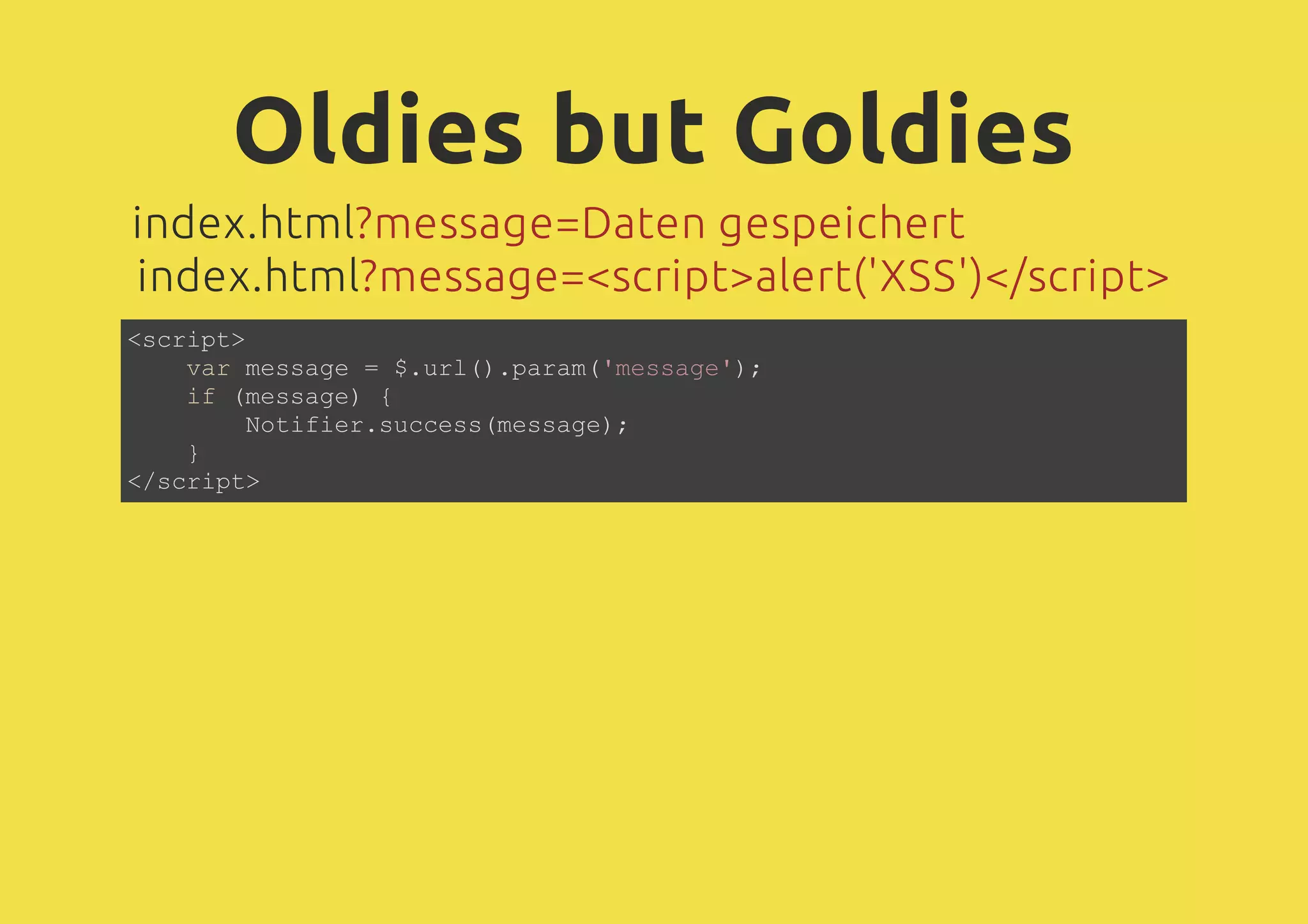
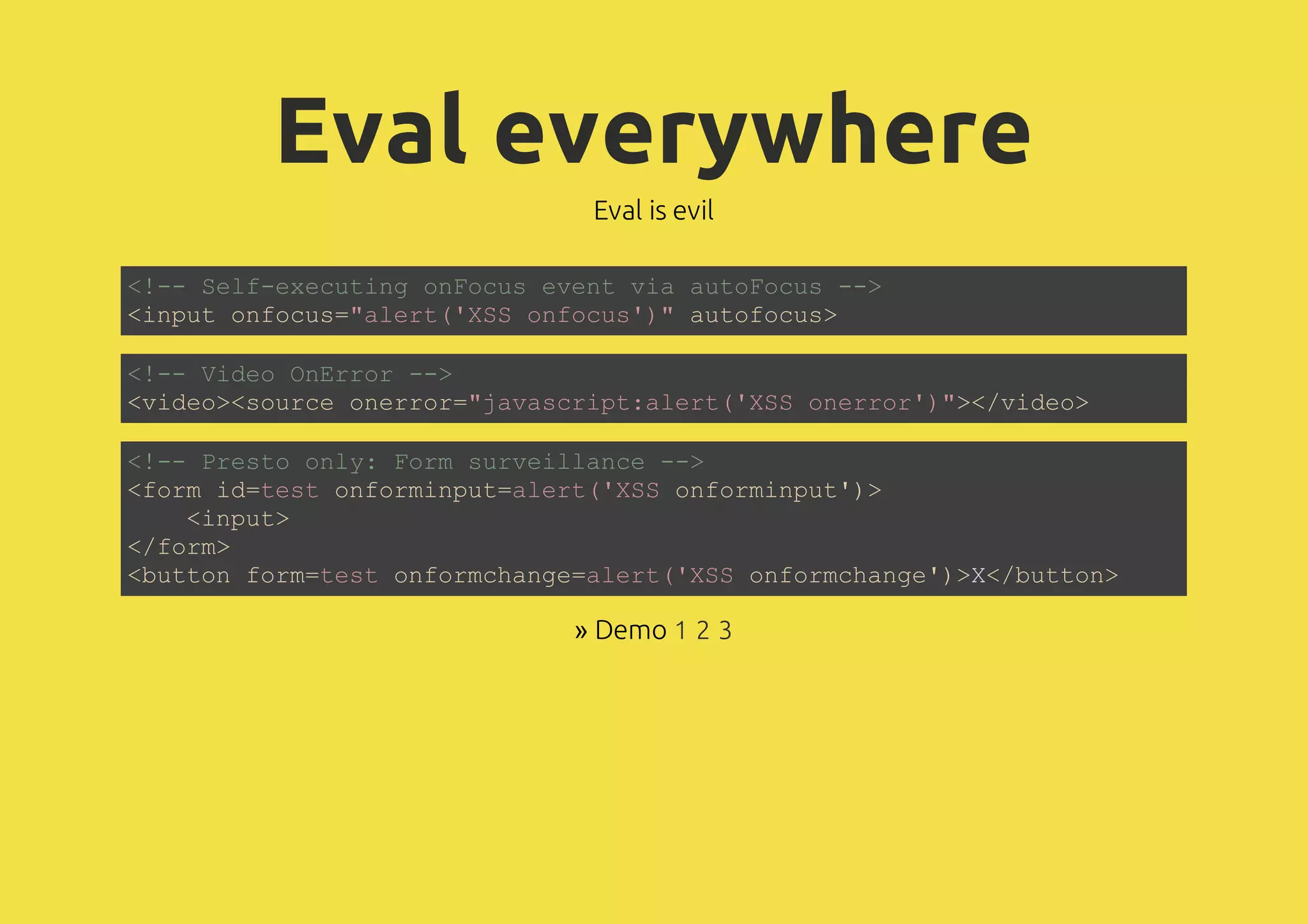
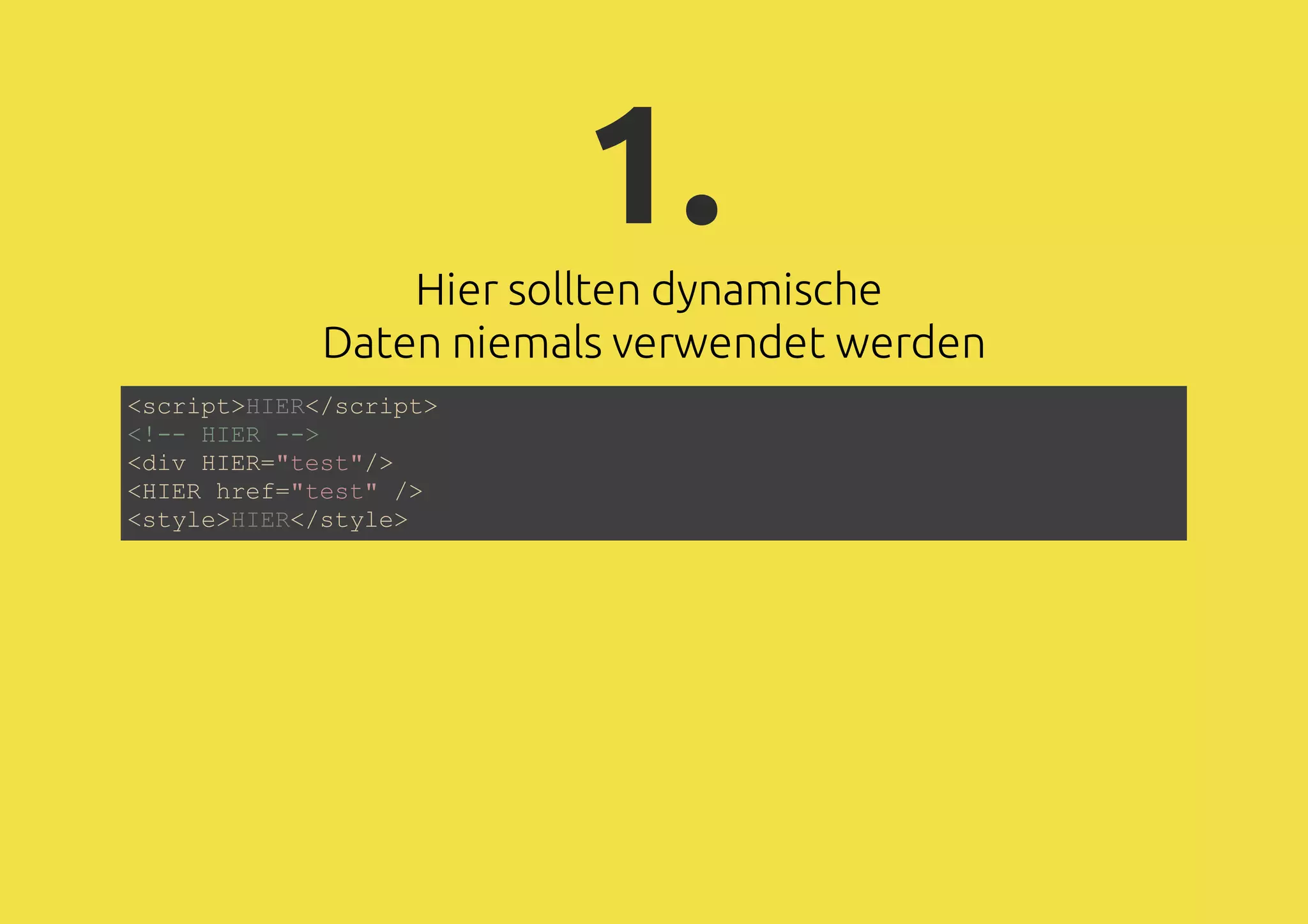
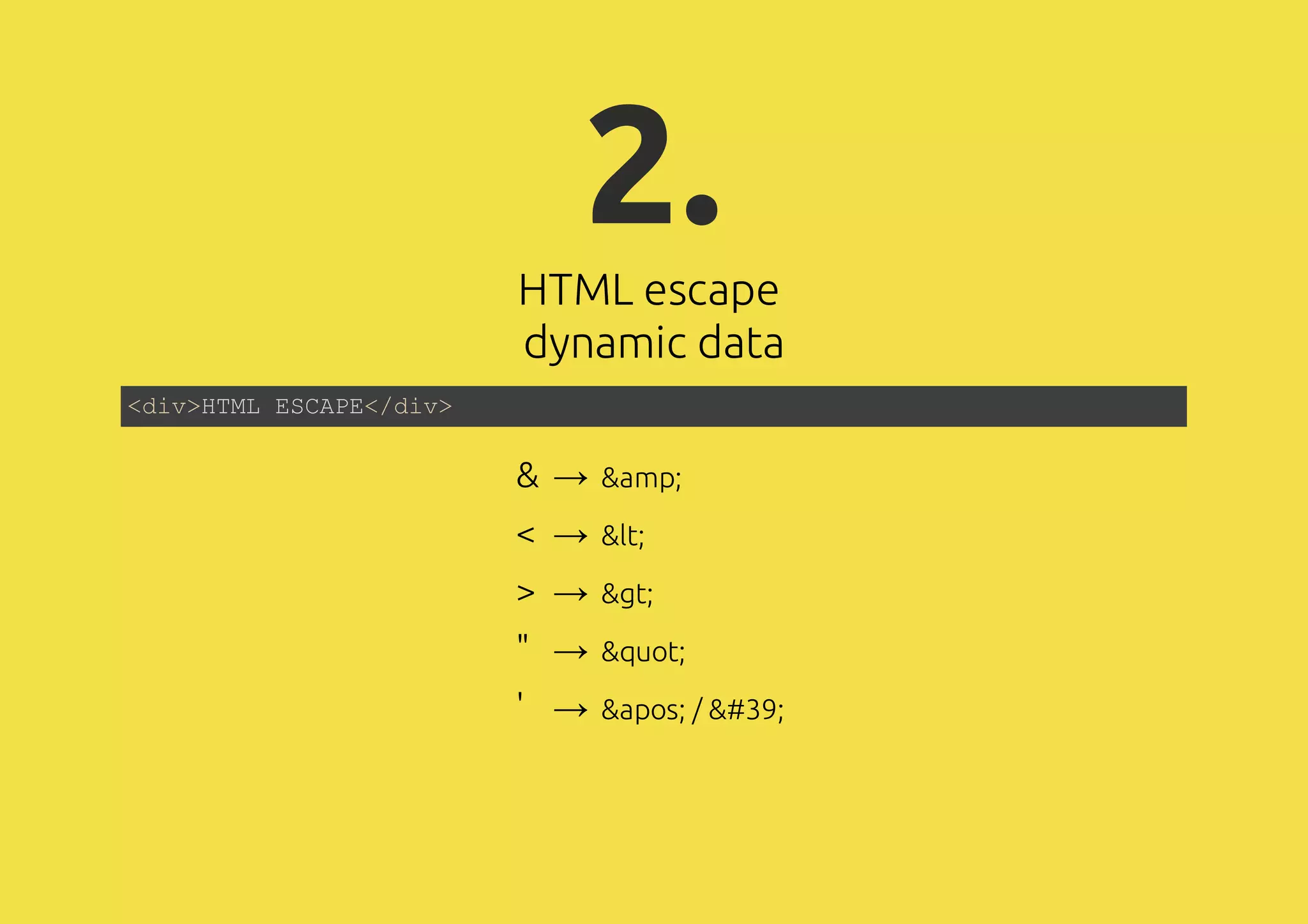
The document discusses web application security, focusing on various attack vectors such as XSS (Cross-Site Scripting) and methods to prevent them. It emphasizes the need for escaping dynamic data and the risks associated with using client-side storage for sensitive information. Additionally, it highlights the importance of security measures like prepared statements for SQL queries and the implications of CORS in communication.



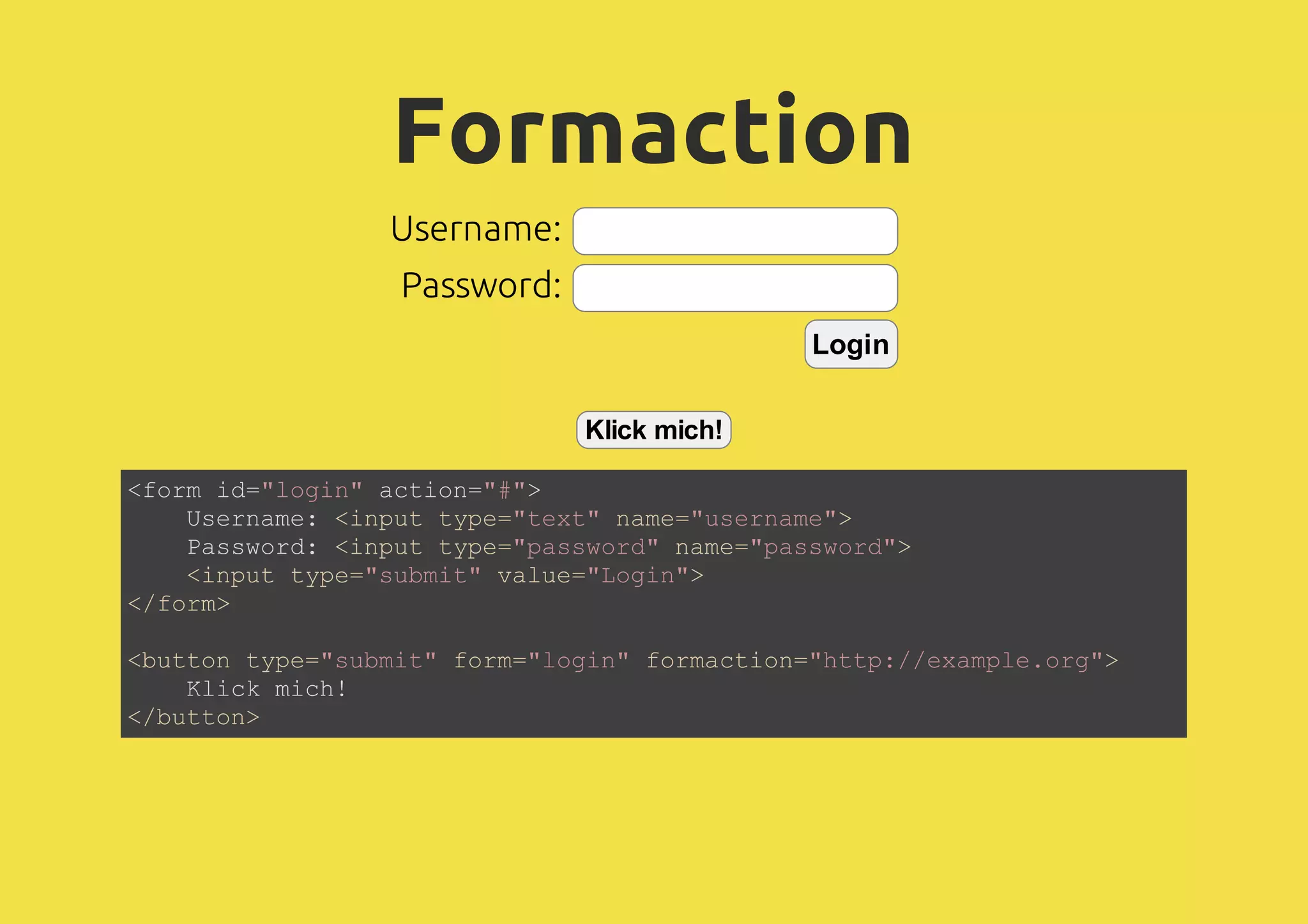
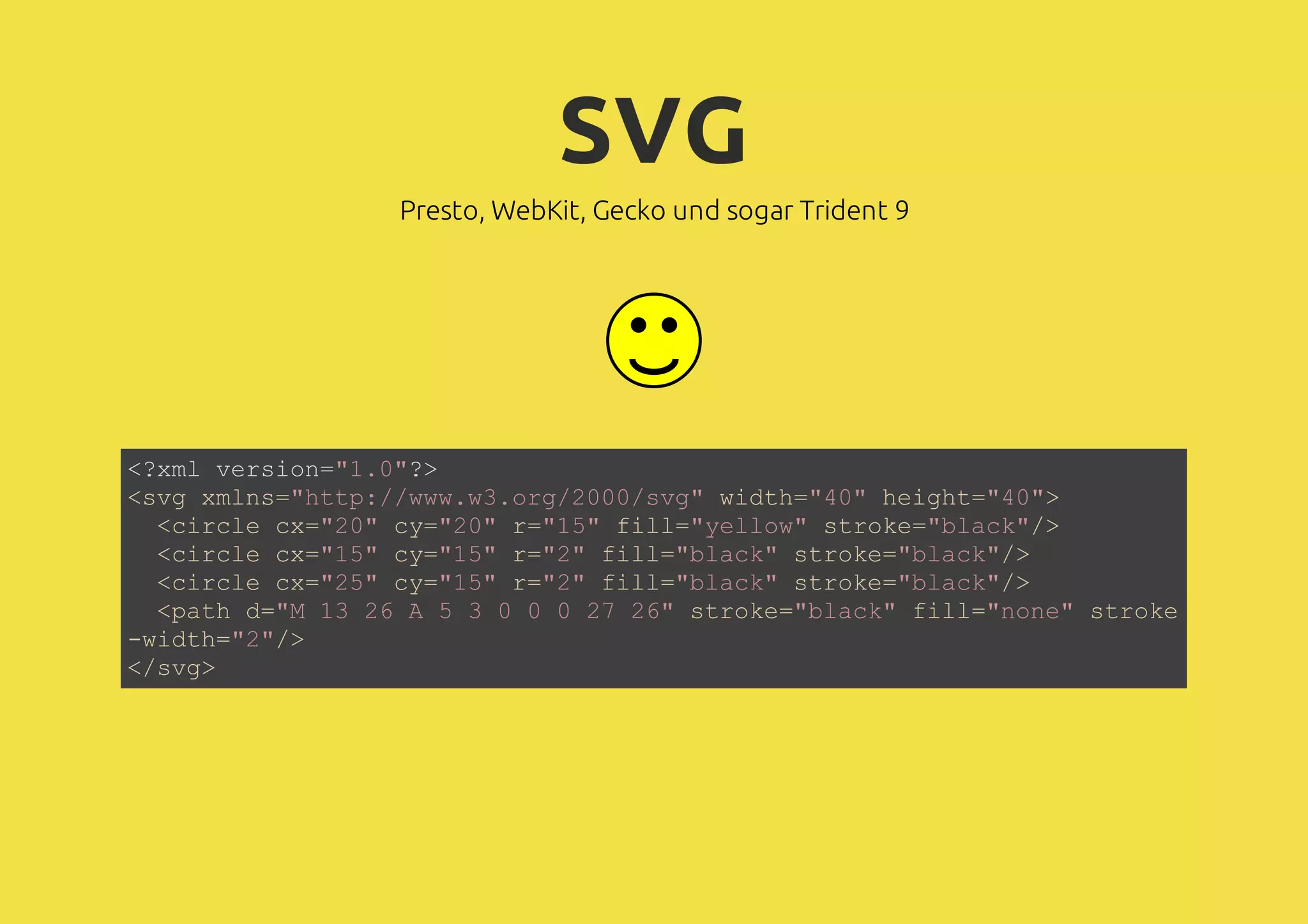
![SVG kann JavaScript enthalten! Test <?xml version="1.0"?> <svg xmlns="http://www.w3.org/2000/svg" width="200" height="50"> <defs><style> </style></defs> <circle cx="20" cy="20" r="15" fill="yellow" stroke="black"/> <circle cx="15" cy="15" r="2" fill="black" stroke="black"/> <circle cx="25" cy="15" r="2" fill="black" stroke="black"/> <path d="M 13 26 A 5 3 0 0 0 27 26" stroke="black" fill="none" stroke -width="2" transform="rotate(180, 20, 28)"/> <text x="11" y="50" id="display">Test</text> <script> </script> </svg> <![CDATA[ text { font-size:6pt; } ]]> alert(document.cookie); document.getElementById('display').textContent = document.cookie;](https://image.slidesharecdn.com/2013-05-03-html5javascriptsecurityjohanneshoppe-130506155212-phpapp01/75/2013-05-03-HTML5-JavaScript-Security-7-2048.jpg)





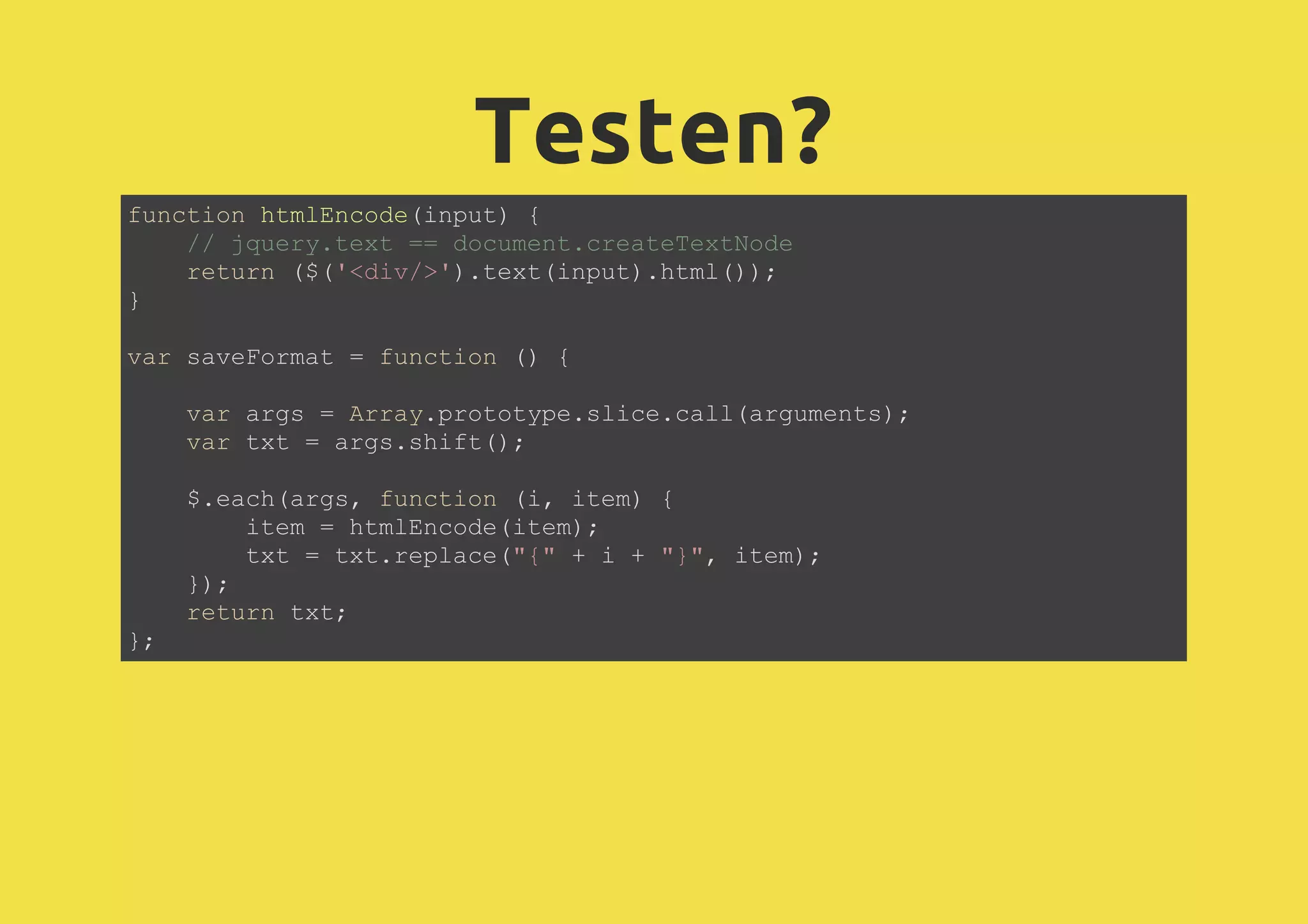
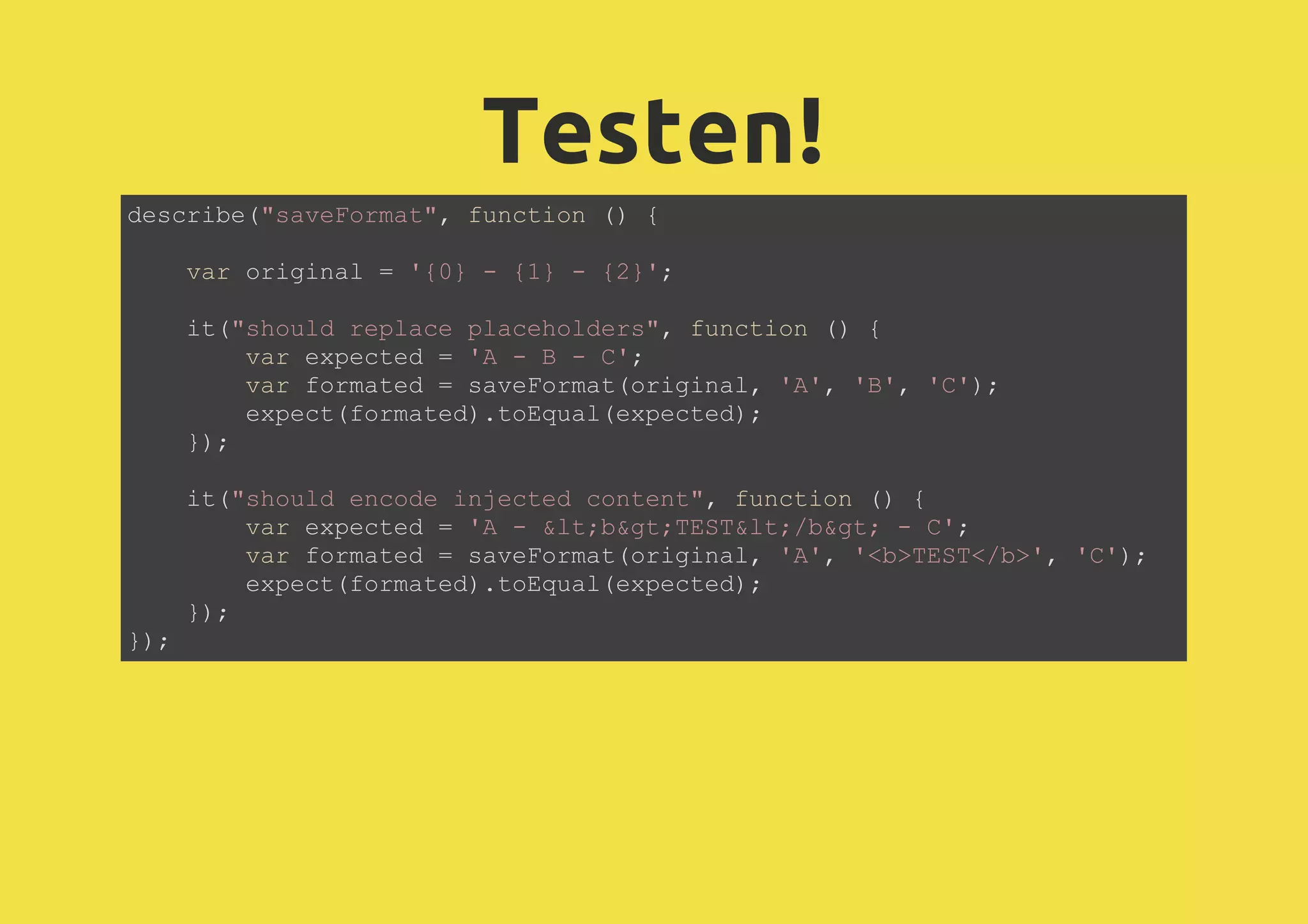






![WebSQL SQL Injection: Prepared Statement: executeSql("SELECT foo FROM bar WHERE value=" + value); executeSql("SELECT foo FROM bar WHERE value=?", [value]);](https://image.slidesharecdn.com/2013-05-03-html5javascriptsecurityjohanneshoppe-130506155212-phpapp01/75/2013-05-03-HTML5-JavaScript-Security-31-2048.jpg)

![Mashups! define(['jquery', 'knockout', 'knockout.mapping', 'domReady!'], function ($, ko, mapping) { var url ='http://search.twitter.com/search.json?q=%23xss&callback=?'; $.getJSON(url).done(function (data) { var viewModel = mapping.fromJS(data); ko.applyBindings(viewModel, $('#tweets').get(0)); }); });](https://image.slidesharecdn.com/2013-05-03-html5javascriptsecurityjohanneshoppe-130506155212-phpapp01/75/2013-05-03-HTML5-JavaScript-Security-33-2048.jpg)