JSON Web Tokens (JWT) Authentication
JWTs are short-lived, signed tokens used to securely authenticate and authorize connections from Courier SDKs to the Courier backend. They are the recommended authentication method in all cases. JWT generation requires a private key which is unique to your Courier workspace, and should only be accessed in secure environments such as your backend server. A typical production JWT generation flow might look like this: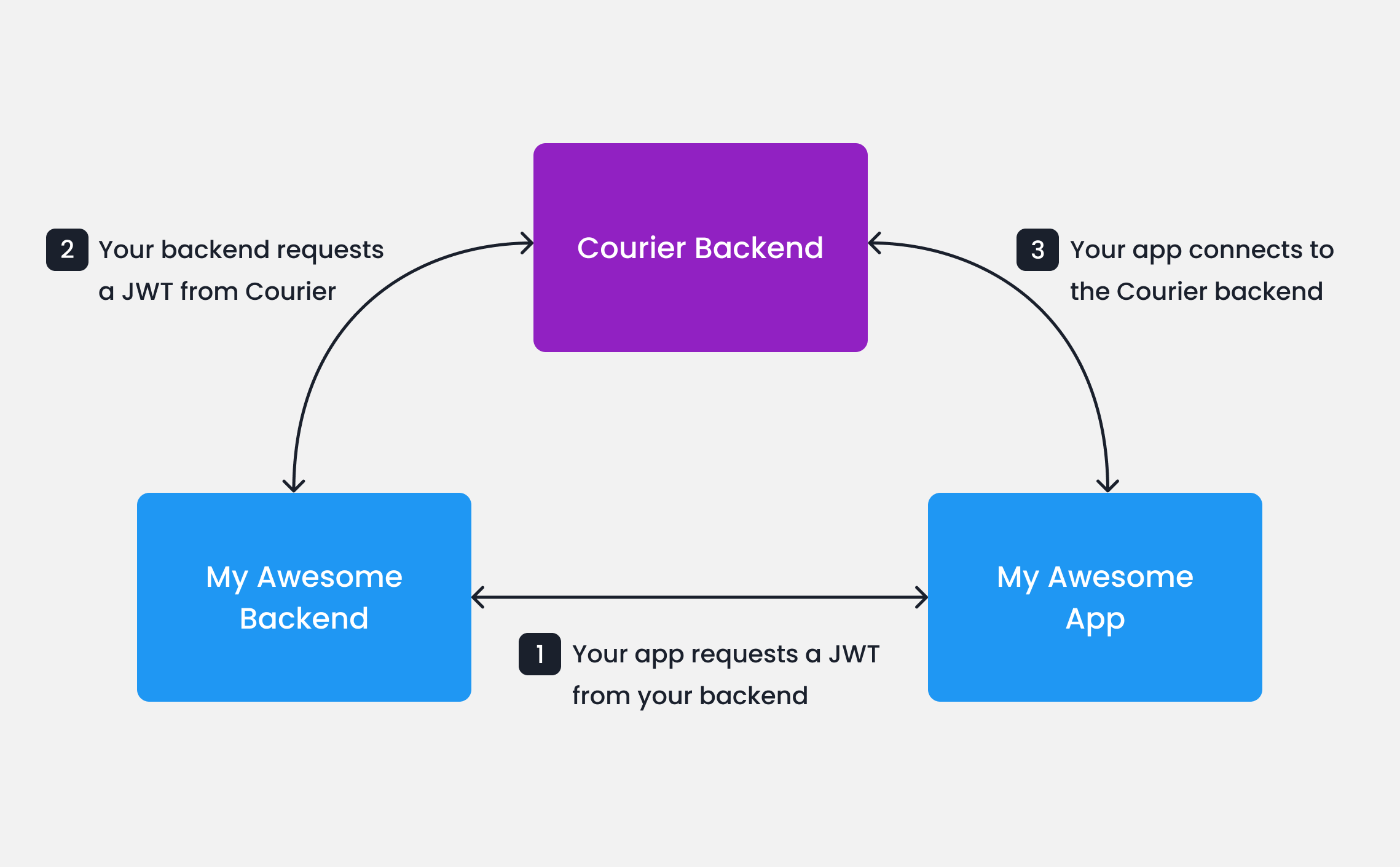
1
Your app calls your backend
When your app needs to authenticate a user, your app should make a request to your own backend (ex.
GET https://my-awesome-app.com/api/generate-courier-jwt).2
Your backend calls Courier
In your backend, use your Courier API Key to call the Courier Issue Token Endpoint and generate a JWT for the user.
3
Your backend returns the JWT to your app
Having received the JWT from Courier, your backend should return it to your app and pass it to the Courier SDK.
Testing JWTs in Development
To quickly get up and running with JWTs in development, you can use cURL to call the Courier Issue Token Endpoint directly.Client Key and HMAC Authentication (Deprecated)
HMAC authentication adds a hash-based code to the request to verify its authenticity. For requests to the Courier backend, the HMAC is a hash of theuserId and your Courier API Key. hmac.ts