Accessing Object Storage Service (OSS) resources over HTTP transmits data in plaintext. This method poses security risks, such as data theft and tampering, and may not meet data protection or compliance requirements. To mitigate these risks, you can configure an SSL Certificate to enable HTTPS access to OSS. HTTPS encrypts data during transmission, helps prevent network attacks, and improves your business security.
How it works
HTTPS access to OSS works by configuring a valid SSL Certificate for a specific endpoint in the correct location. The HTTPS protocol uses the SSL/TLS encryption mechanism for end-to-end encryption of HTTP datagrams. It also uses a certificate chain to verify the server identity. This process ensures data confidentiality, integrity, and authentication.
The location for SSL Certificate configuration depends on the type of endpoint you use. The configuration methods are as follows:
OSS bucket domain names
For example,
example.oss-cn-hangzhou.aliyuncs.com. Alibaba Cloud manages and maintains the SSL certificates for these domain names, which natively support HTTPS. No configuration is required. You can simply use thehttps://prefix to access them securely, which simplifies certificate management.Custom domain names
If you access OSS using a custom domain name, the location for SSL Certificate configuration depends on whether you enable CDN acceleration. This design ensures that the certificate configuration matches the traffic path.
CDN is not enabled: Traffic accesses OSS directly. You must configure certificate hosting for the bound custom domain name in the OSS console. For more information, see Configure certificate hosting in OSS to enable HTTPS access.
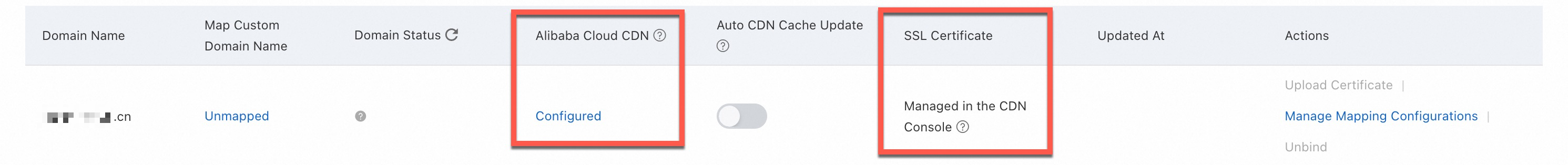
CDN is enabled: Traffic passes through CDN points of presence (POPs) before it is forwarded to OSS. You must configure an HTTPS certificate for the CDN-accelerated domain name in the CDN console. For more information, see Configure an HTTPS certificate in CDN to enable HTTPS access.
Configure certificate hosting in OSS to enable HTTPS access
Enable secure HTTPS access for a custom domain name that is bound to an OSS bucket. This encrypts data during transmission and provides identity authentication to ensure secure access.
Before you begin, make sure that you have bound a custom domain name to an OSS bucket. You must also have a valid SSL Certificate that matches the domain name in SSL Certificates Service. You can obtain a certificate by purchasing a new certificate, applying for a free certificate, or uploading a third-party certificate.
Step 1: Configure certificate hosting
Host an SSL Certificate in OSS to enable HTTPS encrypted access for a custom domain name.
Go to the Bucket List page. Click the destination bucket. In the navigation pane on the left, click .
In the Actions column for the destination custom domain name, click Certificate Hosting. Select a certificate from the Certificate Name drop-down list. If you cannot select the desired certificate, go to the SSL Certificate Management page and make sure that the certificate meets the following conditions:
The certificate is issued and valid.
The domain name bound to the certificate includes the domain name you are configuring.
Click Upload to finish configuring certificate hosting.
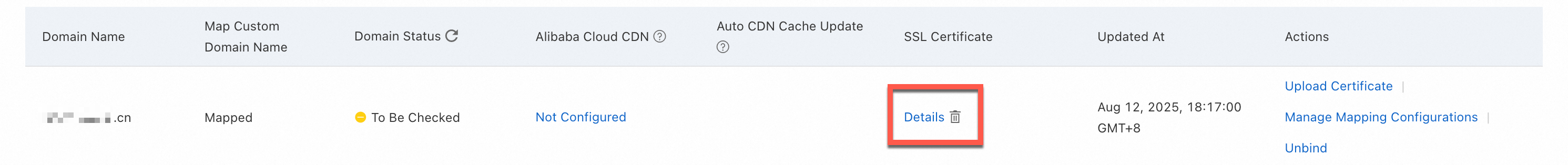
Step 2: Verify HTTPS access
After you configure certificate hosting, wait for the configuration to take effect. Then, you can access a resource from a browser to verify that HTTPS encryption is working correctly. This ensures that data transmission is secure.
Go to the Bucket List page and click the name of the destination bucket.
In the Actions column of the object file you want to access, click Details.
Set Domain Name to Custom Domain Name. From the drop-down list, select the bound custom domain name. Then, click Copy File URL.
Access the URL in a browser to verify the HTTPS encrypted access. The browser's address bar should display a lock icon, which indicates that the connection is encrypted.

Configure an HTTPS certificate in CDN to enable HTTPS access
Enable secure HTTPS access for a custom domain name that has CDN acceleration enabled. This ensures secure data transmission while providing acceleration through CDN's global POPs.
Before you begin, make sure that you have configured CDN acceleration for an OSS bucket and are using the accelerated domain name as the endpoint. You must also have a valid SSL Certificate that matches the domain name in SSL Certificates Service. You can obtain a certificate by purchasing a new certificate or applying for a free certificate. You can also upload a third-party certificate or directly enter the third-party certificate content and private key in the following steps.
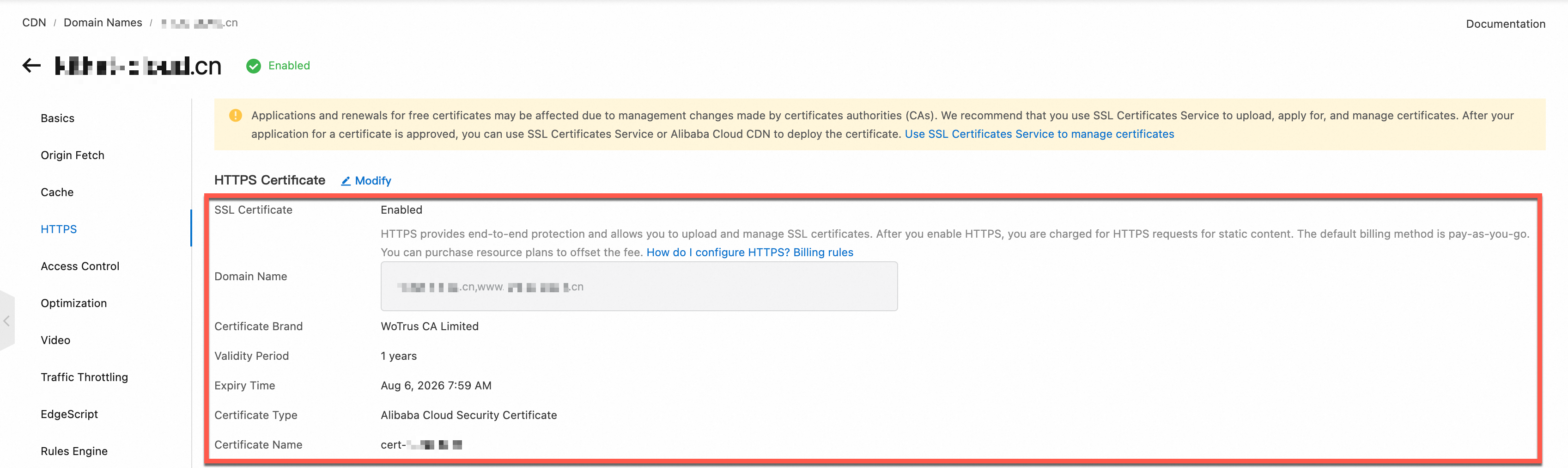
Step 1: Configure the CDN HTTPS certificate
Configure an SSL Certificate for the accelerated domain name in the CDN console to enable the HTTPS secure acceleration feature.
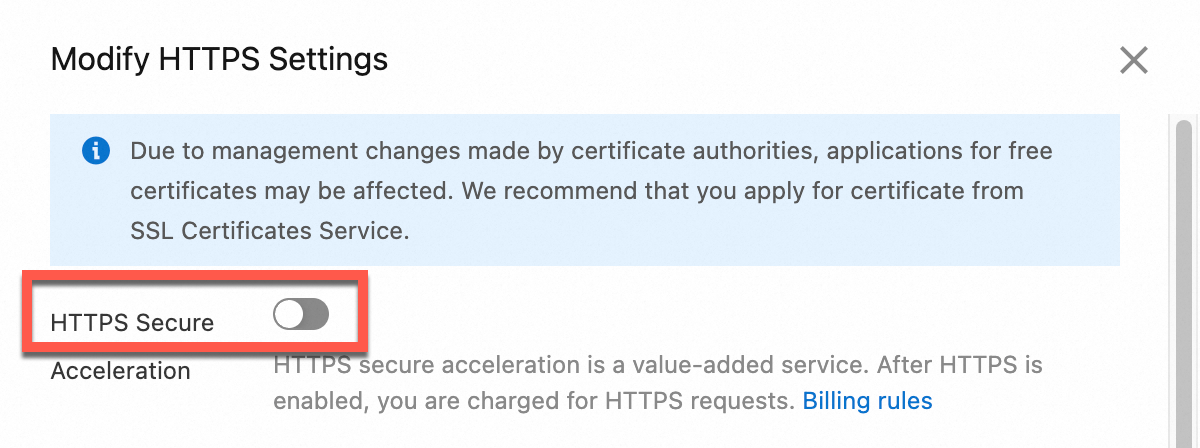
Go to the CDN console. Click the destination accelerated domain name. Click HTTPS Settings. Next to HTTPS Certificate, click Modify.
Select HTTPS Secure Acceleration. Read the billing reminder and click OK.
From the Certificate Source drop-down list, select an SSL Certificate or enter third-party certificate information.
SSL Certificates Service: From the Certificate Name drop-down list, select a certificate. If you cannot select the destination certificate, go to the SSL Certificate Management page and make sure the certificate meets the following conditions:
The certificate is issued and valid.
The domain name bound to the certificate includes the domain name you are configuring.
Custom Upload (Certificate + Private Key): Enter the Certificate Name, Certificate (Public Key), and Private Key.
Click OK to complete the HTTPS certificate configuration.
Step 2: Verify CDN HTTPS access
It takes about 1 minute for the HTTPS configuration of the CDN-accelerated domain name to take effect. After the configuration takes effect, you can access an OSS resource over HTTPS from a browser to verify the configuration. For example, you can access https://example.com/dest.jpg, where example.com is the CDN-accelerated domain name. If the access is successful, the browser's address bar displays a lock icon. This indicates that data transmission is encrypted.

Going live
HTTPS configurations in a production environment must consider security, reliability, and performance. You should use appropriate configuration policies and risk prevention measures to ensure stable and continuous business operations.
Best practices
Force HTTPS access: Configure an access control policy
In a production environment, you should force all clients to use HTTPS for access. This prevents data from being stolen or tampered with during transmission and meets data protection compliance requirements.
For OSS custom domain names, configure a bucket policy to deny all HTTP requests.
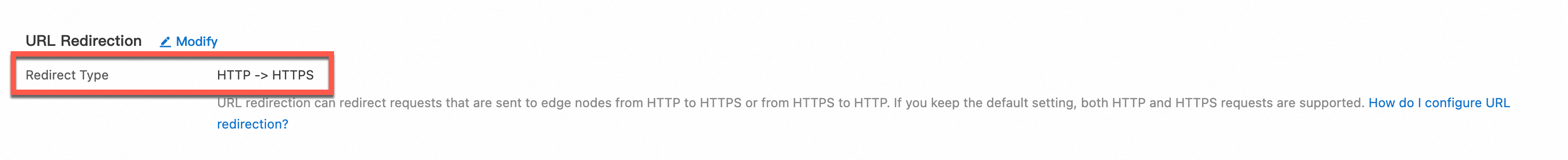
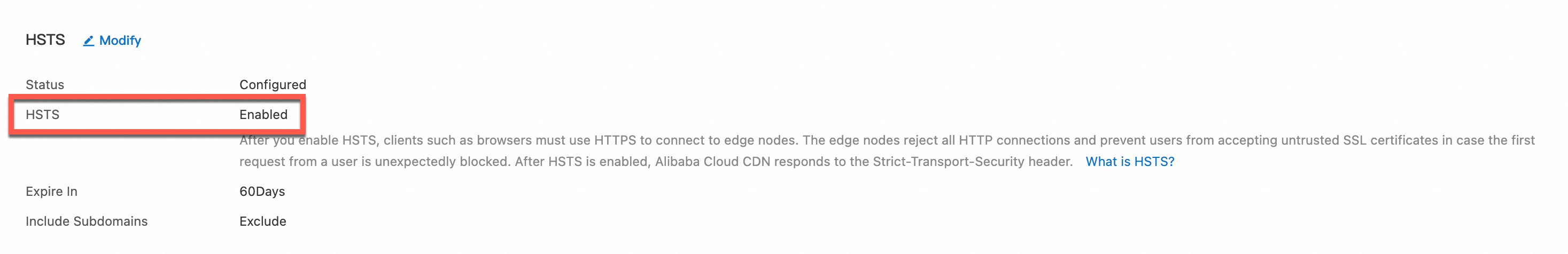
For CDN-accelerated domain names, configure a force redirect or enable HTTP Strict Transport Security (HSTS) to force clients to use HTTPS for access. This improves overall security.
Automatic renewal: Manage the certificate lifecycle
SSL Certificates have a fixed validity period. An expired certificate can cause service interruptions and business losses. You should set up an alert monitoring mechanism for certificate expiration. You should renew certificates 30 days in advance to ensure enough time for testing and deployment. For Alibaba Cloud SSL Certificates, you can enable certificate hosting to reduce manual intervention. For third-party certificates, you should establish a regular update process and assign responsibilities to ensure business continuity.
Performance optimization: Enable HTTP/2 and compressed transmission
Modern browsers and CDNs widely support the HTTP/2 protocol. Compared with HTTP/1.1, HTTP/2 offers technical advantages such as multiplexing, header compression, and server push. These can significantly improve page load speeds. In the CDN configuration, you can enable the HTTP/2 protocol and Gzip compression. This optimizes transmission efficiency, reduces bandwidth consumption, and improves user experience while ensuring security.
Risk prevention
Certificate failure contingency: Establish a backup certificate mechanism
You should prepare a backup SSL Certificate to handle unexpected situations, such as a primary certificate failure, accidental deletion, or a certification authority (CA) failure. For critical business systems, you should use certificates from multiple CAs as backups. If the primary certificate fails, you can quickly switch to a backup. This practice minimizes the risk of service interruption and ensures business continuity.
Access downgrade policy: Fall back to HTTP in emergencies
Although HTTPS is a security best practice, you should have an emergency fallback plan to HTTP access for situations where serious certificate configuration issues cannot be fixed quickly. You should establish a standard emergency procedure and an operations manual. This plan should allow you to temporarily revert to HTTP access during troubleshooting. At the same time, you should enhance monitoring and logging to promptly detect issues and quickly restore normal operations.
OSS root certificate upgrade
A root certificate is the foundation of the SSL/TLS trust chain. It is used to verify the trustworthiness of a server certificate. Browsers and operating systems have built-in root certificate libraries. A server certificate is considered trustworthy only when it is issued by a trusted root certificate.
Background
To ensure the continued reliability of the network security environment, Mozilla implemented a new root certificate trust policy in early 2023. According to this policy, all root certificates used for server authentication that were issued more than 15 years ago will no longer be trusted by Mozilla. As a result of this policy, GlobalSign issued a root certificate upgrade notice. The notice states that the GlobalSign Root R1 root certificate will become invalid on April 15, 2025. For more information, see Mozilla's notice on updating the root certificate trust policy and GlobalSign's root certificate upgrade notice.
OSS response strategy
In response to the change in the root certificate trust policy, Alibaba Cloud Object Storage Service (OSS) has adopted the following strategies to ensure a smooth transition and continued service availability. For more information, see Alibaba Cloud Object Storage Service HTTPS Root Certificate Upgrade Announcement.
Certificate update plan
Starting from July 1, 2024, new certificates issued by OSS will use GlobalSign Root R3. This ensures compatibility with the latest security standards and prevents access interruptions caused by changes in the root certificate trust policy.
Cross-certificate compatibility solution
To ensure broad compatibility during the transition period, existing OSS certificates use a cross-certificate mechanism for a smooth migration from GlobalSign Root R1 to GlobalSign Root R3. The cross-certificate based on GlobalSign Root R1 is valid until January 28, 2028. Because certificate applications must be submitted 13 months before expiration, you must complete all related root certificate update preparations before December 28, 2026.
Future planning and recommendations
For long-term development, although GlobalSign Root R3 is the current solution, it will no longer be trusted by Mozilla as of April 15, 2027, and will expire on March 18, 2029. Therefore, we strongly recommend that you promptly upgrade the root certificates on your clients. You should also make sure that the root certificate list includes multiple authoritative root certificates, such as GlobalSign R1, R3, R6, and R46, to meet future certificate rotation needs.
User response
For most users, no action is required. Modern operating systems (such as Windows 7+, macOS 10.12.1+, and major Linux distributions from the last 5 years) and browsers (such as Chrome, Firefox, and Safari) automatically update their built-in root certificate libraries. They will automatically trust the new root certificates.
You only need to follow the steps below for troubleshooting and updates if you encounter certificate errors when you access OSS over HTTPS on legacy operating systems, embedded devices, or outdated custom clients.
Step 1: Check for the 'GlobalSign Root CA - R3' root certificate
Windows
Press Win+R, enter
certmgr.msc, and press Enter to open Certificate Manager.In the navigation pane on the left, expand .
In the list on the right, find the certificate where Issued To is GlobalSign and Friendly Name is GlobalSign Root CA - R3.
Linux
Using Ubuntu as an example, open a terminal and run the following command to check if the system certificate directory contains GlobalSign-related certificates.
ls /etc/ssl/certs/ | grep GlobalSignmacOS
Open Finder, search for Keychain Access, and double-click it to open.
Click System Roots. Enter GlobalSign in the search box in the upper-right corner. Double-click a certificate to view its details.
Step 2: Install the missing root certificate
If your check confirms that the root certificate is missing from the system, select the appropriate installation method for your operating system.
Billing
After you enable the HTTPS feature in CDN, you are billed separately for the number of HTTPS requests for static content. For more information, see Billing of HTTPS requests for static content.
FAQ
How do I update a certificate that is replaced or has expired?
The procedure for updating a certificate is the same as for the initial configuration. You can select the appropriate update path based on the domain name type.
OSS custom domain name: Go to the Bucket List page. In the certificate hosting section of the destination bucket's domain name management, select the new certificate.
CDN-accelerated domain name: Go to the CDN console. In the HTTPS settings for the destination accelerated domain name, select or upload the new certificate.
After I configure an SSL Certificate, why does my browser still show an 'insecure' or 'certificate error' message?
If a security warning still appears after the configuration is complete, you can troubleshoot the issue as follows.
Check the configuration location: Confirm whether CDN acceleration is enabled for the endpoint. If it is, you must configure HTTPS for the accelerated domain name in the CDN console. Certificate hosting in the OSS console will not take effect.
Clear the browser cache: The browser may have cached the old certificate status. You can try clearing the browser cache and then accessing the URL again.
Wait for the configuration to take effect: It takes some time for the CDN HTTPS configuration or OSS certificate hosting configuration to take effect.
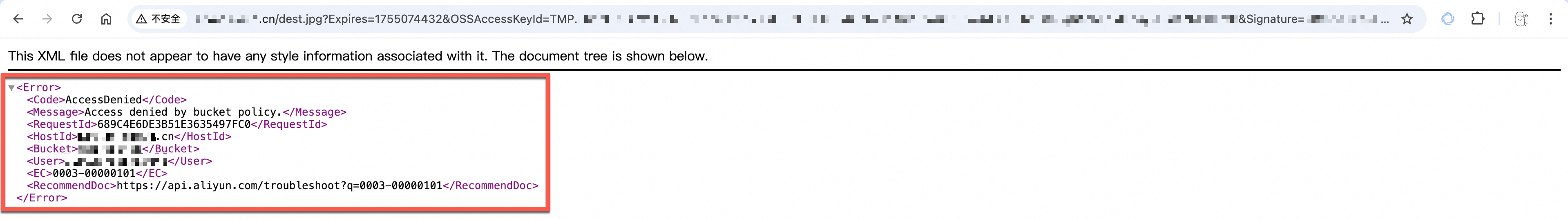
Check the certificate chain integrity: A certificate file issued by an intermediate CA contains multiple certificates. You must concatenate the server certificate and the intermediate certificate into a complete certificate chain before uploading. The CA usually provides instructions for concatenation. You should carefully review the relevant documentation.
How do I handle certificate exceptions when accessing OSS over HTTPS?
You can use the corresponding method based on the type of certificate exception.
Certificate not configured: The browser displays "Your connection is not private" with the error message:
NET::ERR_SSL_PROTOCOL_ERROR. This may be because the certificate is not configured or is configured in the wrong location. For example, CDN acceleration is enabled, but certificate hosting is configured in the OSS console. You can reconfigure HTTPS access using the correct method.Certificate expired: The browser displays "Your connection is not private" with the error message:
NET::ERR_CERT_DATE_INVALID. The certificate bound to the domain name has expired. You can view the expiration date in the browser. You can purchase or apply for a new certificate, and then update it according to the configuration procedure.Certificate mismatch: The browser displays "Your connection is not private" with the error message:
NET::ERR_CERT_COMMON_NAME_INVALID. The domain name in the access URL is not within the scope of the domain names bound to the certificate. For example, the endpoint iscdn.example.com, but the domain name bound to the certificate isoss.example.com. You must configure the correct certificate for the endpoint.
Why can't I find the destination certificate in the drop-down list when selecting a certificate?
You may not be able to find the destination certificate in the drop-down list for the following reasons:
Certificate and domain name mismatch: The system only lists certificates that match the domain name being configured. For example, when you configure a certificate for the domain name
oss.example.com, you cannot select a certificate issued tocdn.example.com.Certificate is not under the current account: Confirm whether the certificate is under the current Alibaba Cloud account. If not, you must upload the certificate on the SSL Certificate Management page.
Wildcard certificate level mismatch: A wildcard certificate only supports domain names at the same level. For example,
*.example.comcan matchwww.example.comandoss.example.com, but it cannot matchcdn.oss.example.com.
When I configure an HTTPS certificate in CDN, a message indicates that the certificate format is incorrect. How do I convert the format?
CDN HTTPS configuration only supports certificates in PEM format. Different CAs have different requirements for uploading certificate content. If the certificate is not in PEM format, see Certificate formats. You can follow the instructions in the document to convert the format before uploading.
How do I update a certificate using the command line or an API?
CDN-accelerated domain name: You can use the Cloud Assistant CLI to set the CDN domain name certificate. For more information, see Cloud Assistant CLI integration example and SetDomainServerCertificate API.
OSS custom domain name: You can use ossutil to bind a certificate to a custom domain name. For more information, see put-cname command.
How do I disable HTTPS access?
OSS custom domain name
When you no longer need HTTPS encrypted access, you can delete the HTTPS certificate as follows.
Go to the Bucket List page. Click the destination bucket. In the navigation pane on the left, click .
Click the delete icon next to Certificate Details for the destination domain name, and then click OK.
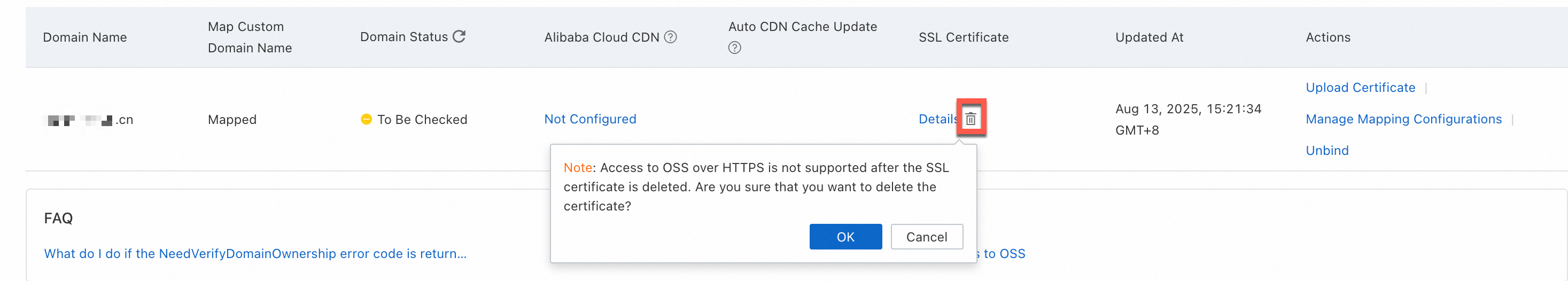
CDN-accelerated domain name
When you no longer need HTTPS encrypted access, you can disable this feature as follows.
ImportantTo avoid access interruptions, you must restore the redirect type to the default setting and disable the HSTS feature before you disable HTTPS.
Go to the CDN console. Click the destination accelerated domain name. Click HTTPS Settings. Next to HTTPS Certificate, click Modify.
As shown in the following figure, disable HTTPS Secure Acceleration, and then click OK.