Secretes
ATCD is the database where master save data about nodes , so the secret will be created in ATCD encrypted , and he didn't put it in any Node until a pod need to use it. There is a resource to read it and it is a must to read before continue this article this is the link to the design of secretes read it and came back -> here
Files
the files also can be found in the DevOpsRepo in my github , if you already have it just pull it.
#app_055-cf.yml apiVersion: v1 kind: ConfigMap metadata: name: configs data: LANGUAGE: Polish #app_055-sec.yml apiVersion: v1 kind: Secret metadata: name: configs-sec data: API_KEY: MzMzLTQ0NC01NTUK #app_055.yml apiVersion: apps/v1 kind: Deployment metadata: name: envtest spec: selector: matchLabels: name: envtest replicas: 1 template: metadata: labels: name: envtest spec: containers: - name: envtest image: praqma/secrets-demo imagePullPolicy: Always ports: - containerPort: 3000 env: - name: LANGUAGE valueFrom: configMapKeyRef: name: configs key: LANGUAGE - name: API_KEY valueFrom: secretKeyRef: name: configs-sec key: API_KEY Lab
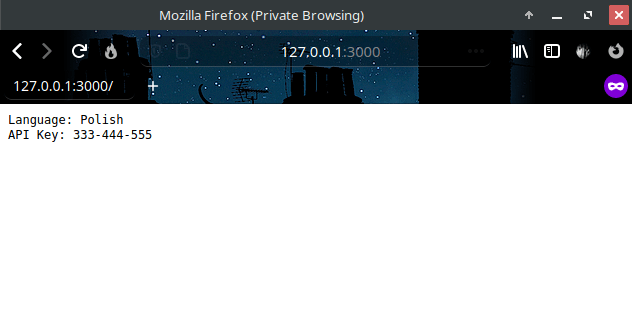
Will the ApiKey is a secret in fact , so we should put it in secret configs.
to convert our keys to an encryption we use this command on Linux
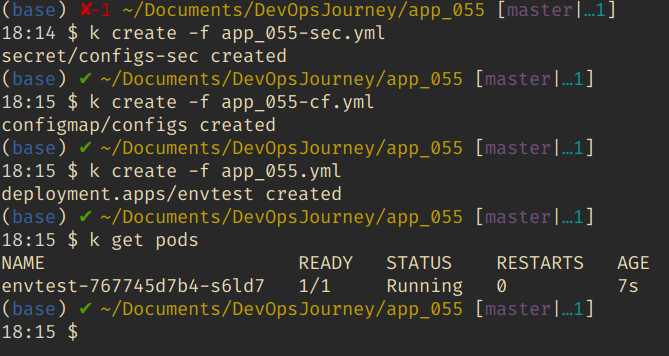
echo "333-444-555" | base64 //output : MzMzLTQ0NC01NTUK kubectl create -f app_055-sec.yml kubectl create -f app_055-cf.yml kubectl apply -f app_055.yml then port-forward to 3000
kubectl port-forward envtest-767745d7b4-s6ld7 3000 


Top comments (4)
The main issue i have with secrets right now, is that in order to save my k8 deployment I'd have to check the secrets into version control with the rest of my yaml files that describe my cluster. Even if they're base64 encoded, that's not really encrypted, obfuscated at best and you can always decode it with
base64 -dThanks for the tutorial otherwise. :)
you can git ignore it and push a template for it only.
Sure, but the secrets database has to live somewhere besides your local laptop. Especially if you're doing hundreds of services with a variety of API keys and password for various dev/qa/production environments.
I don't know how if kuberenetes have a way to do it.
Do you have a solution for it using kubernetes?