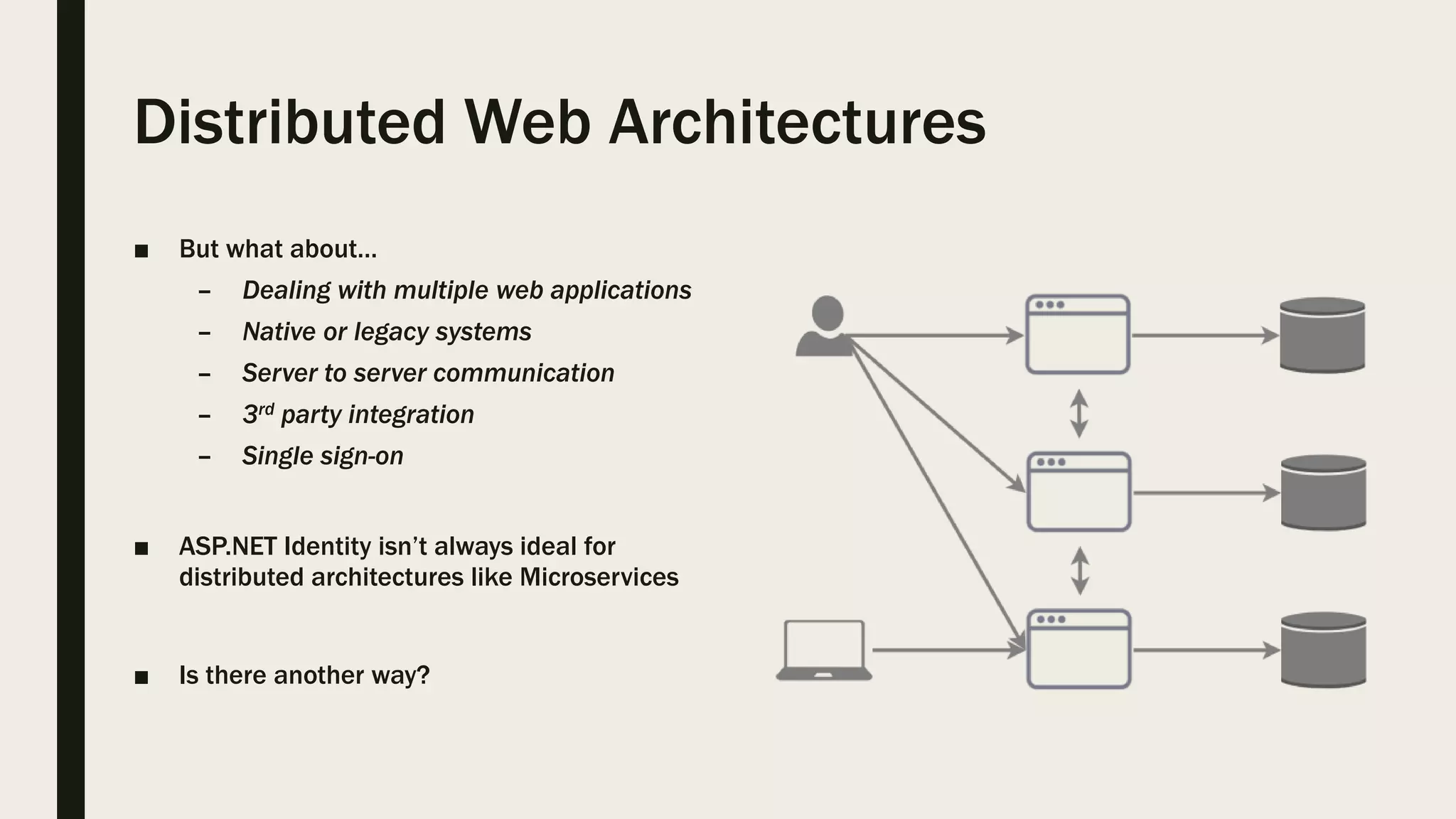
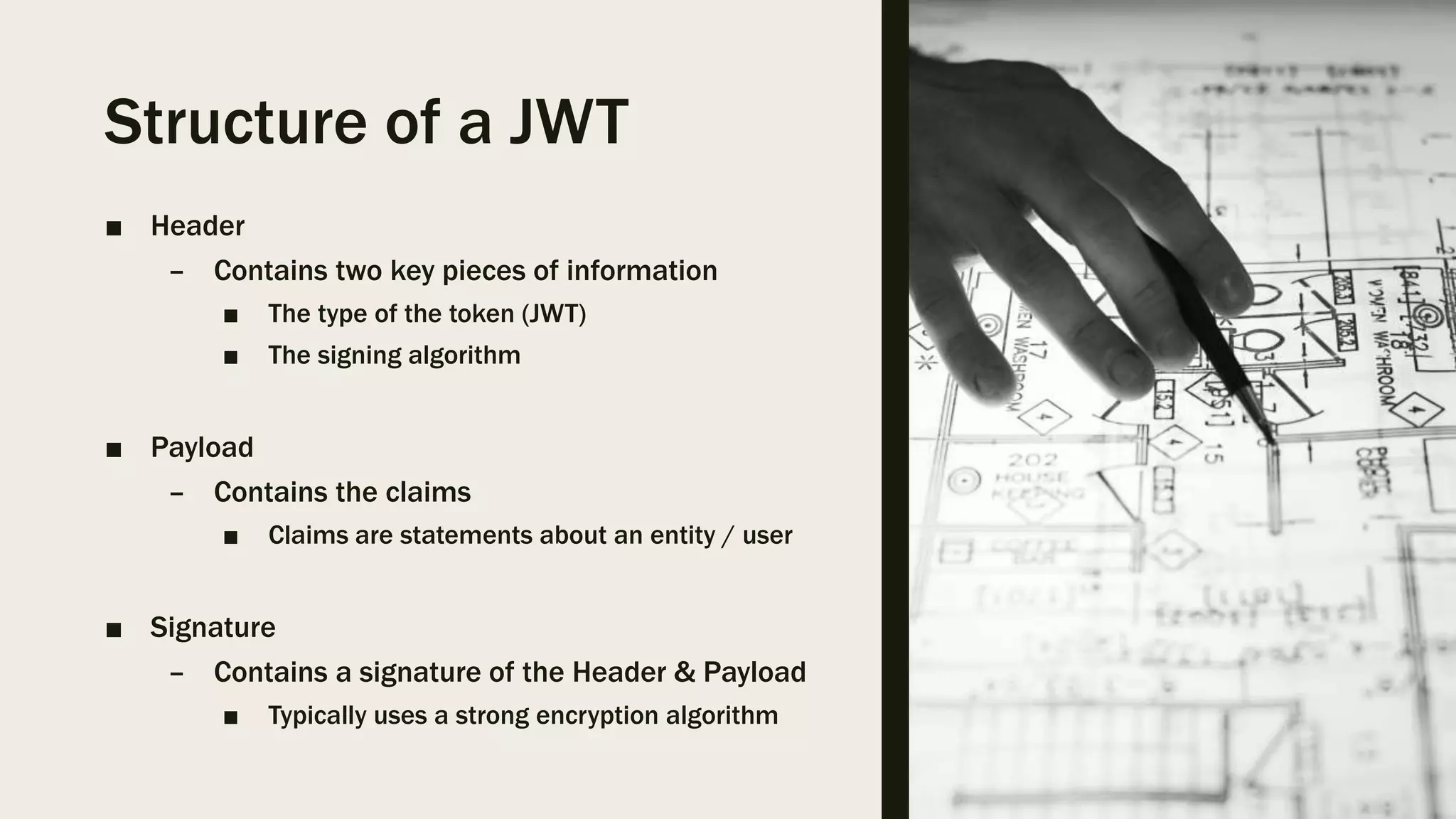
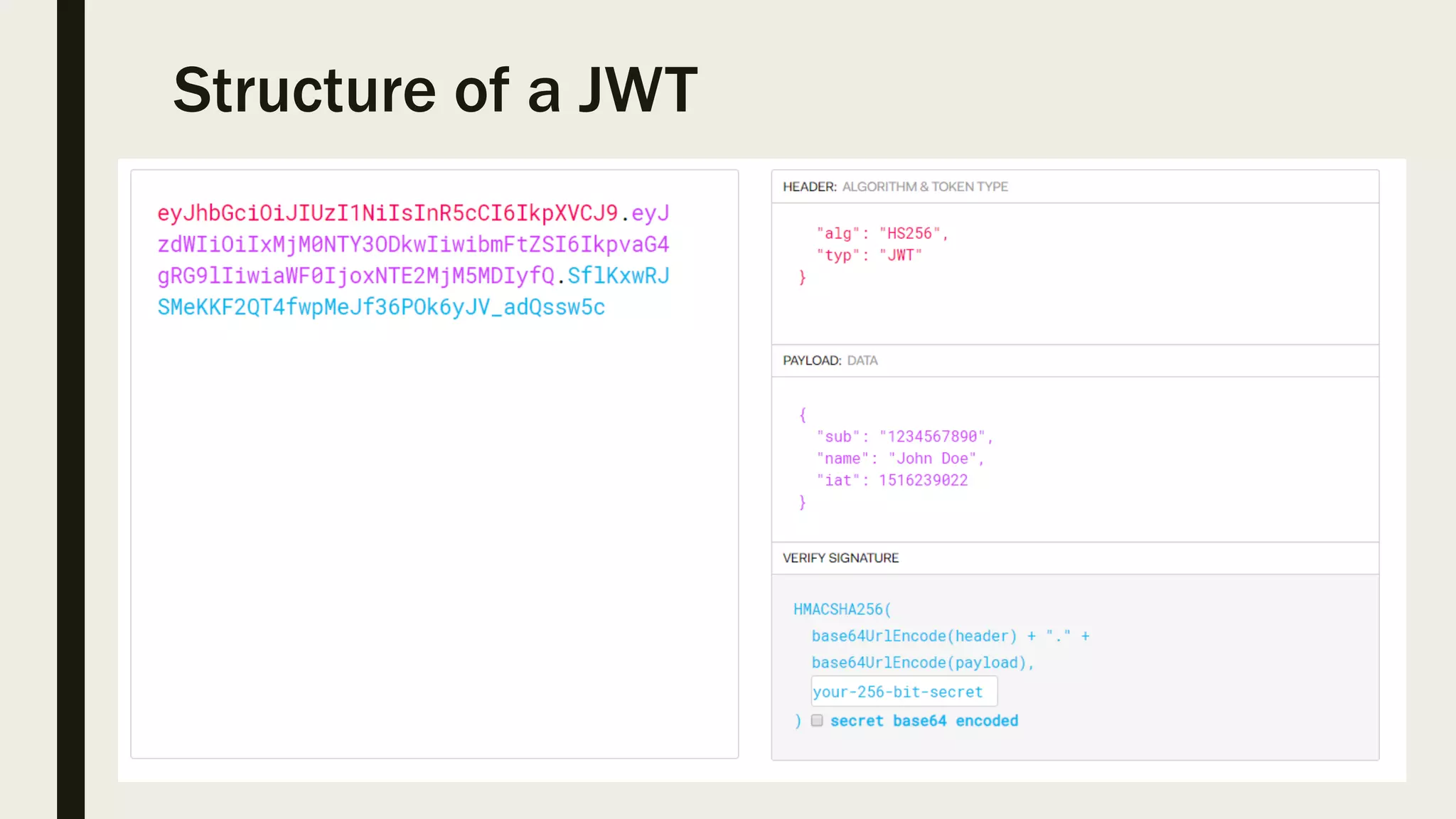
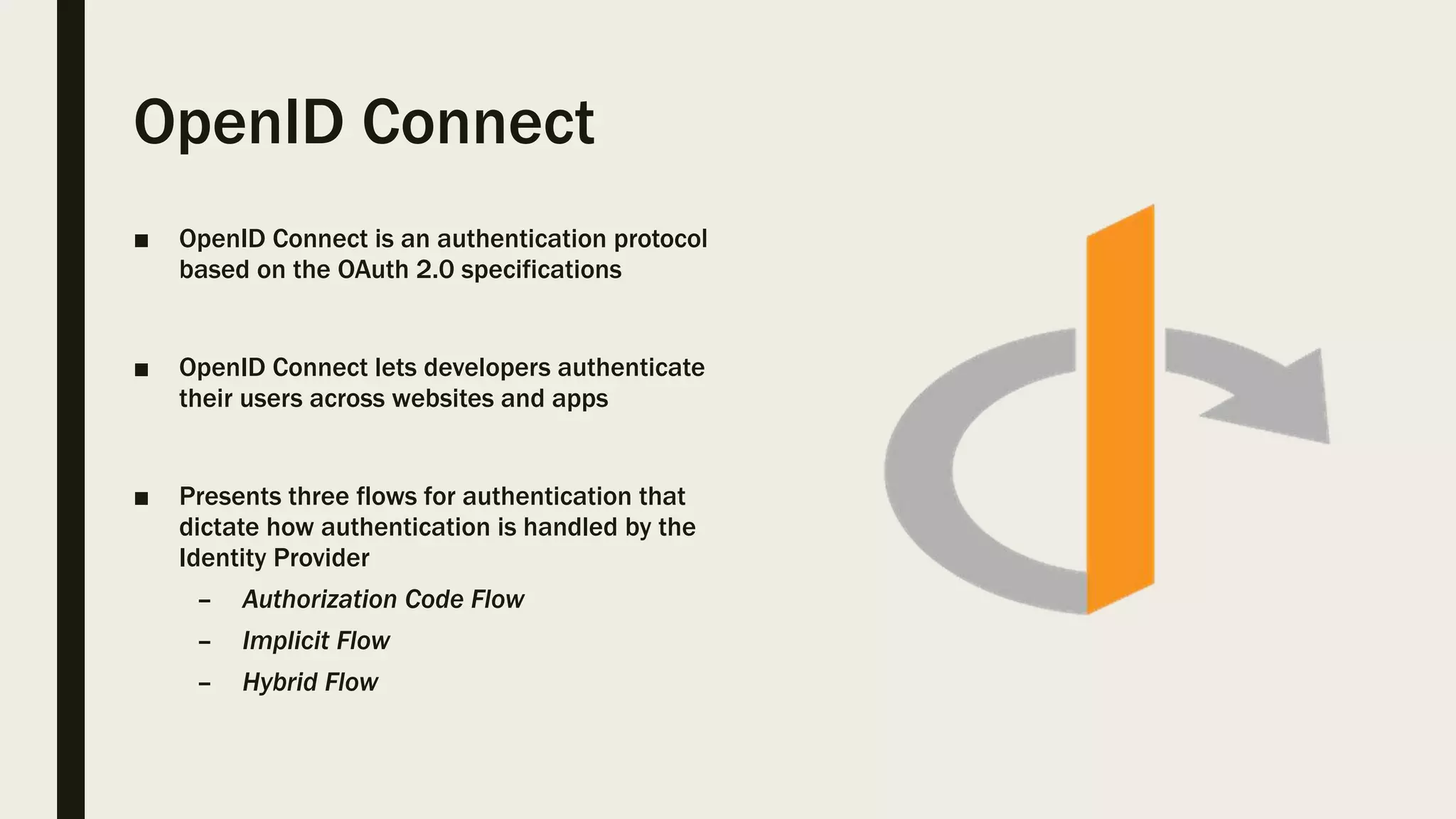
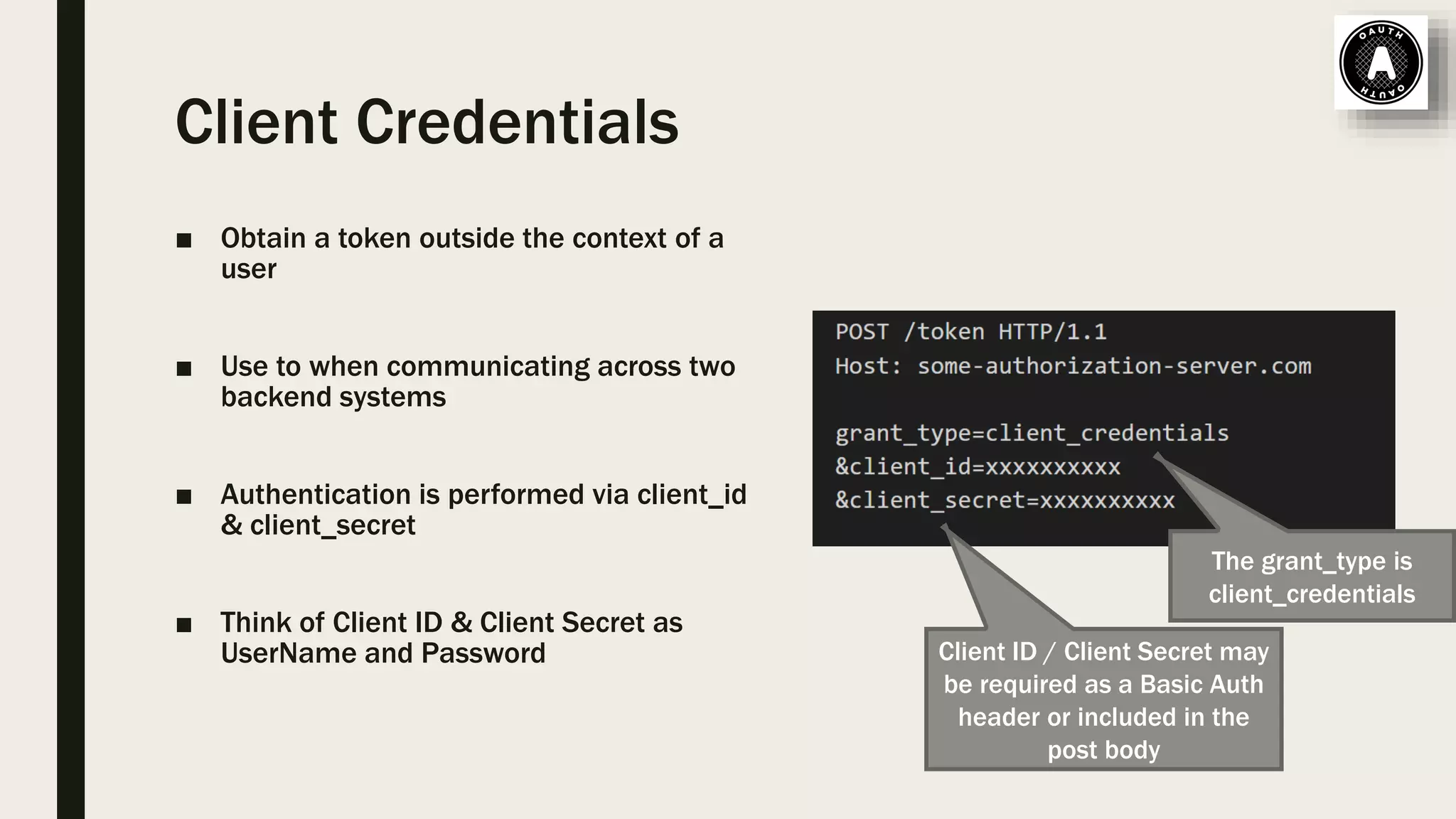
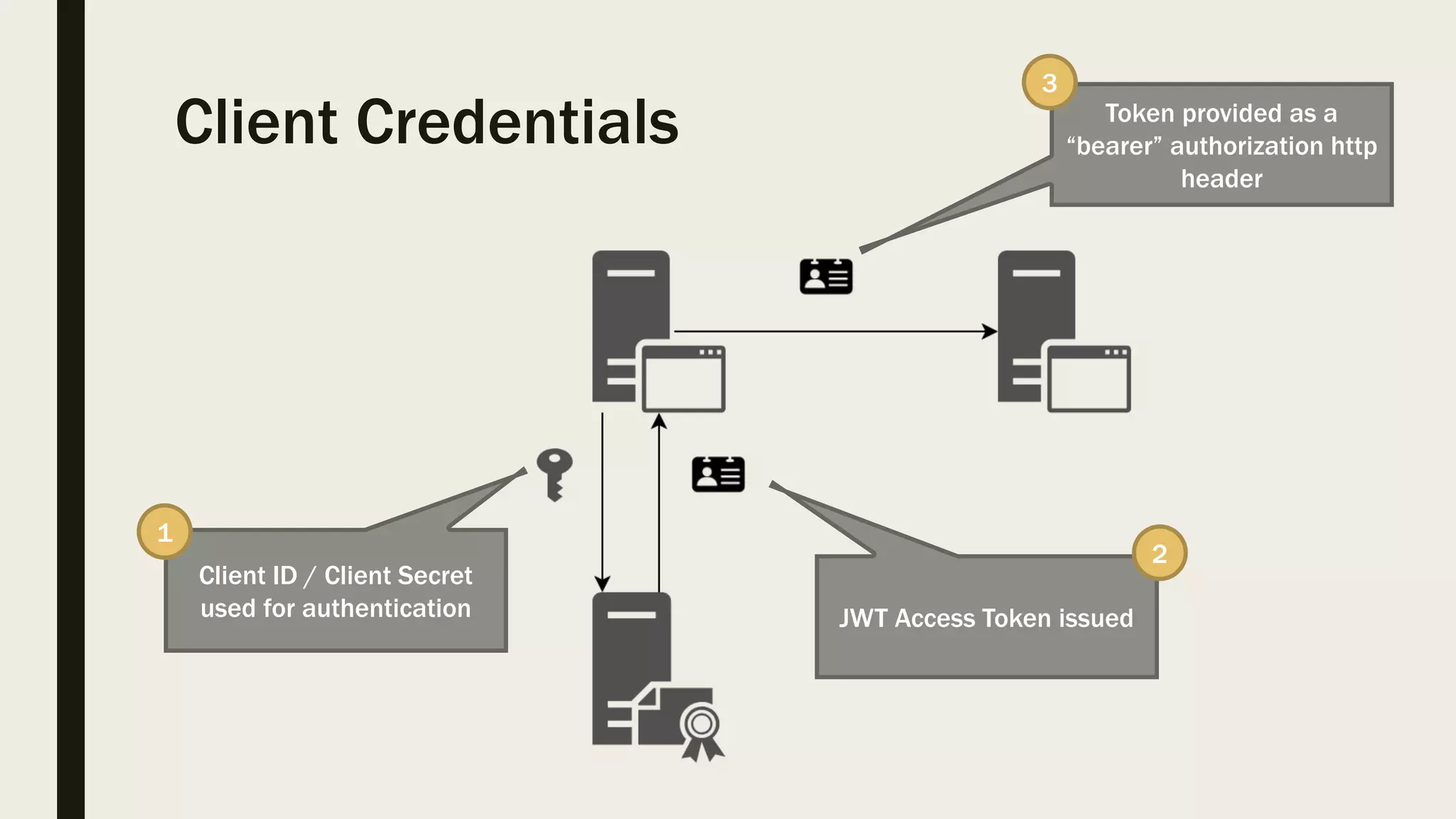
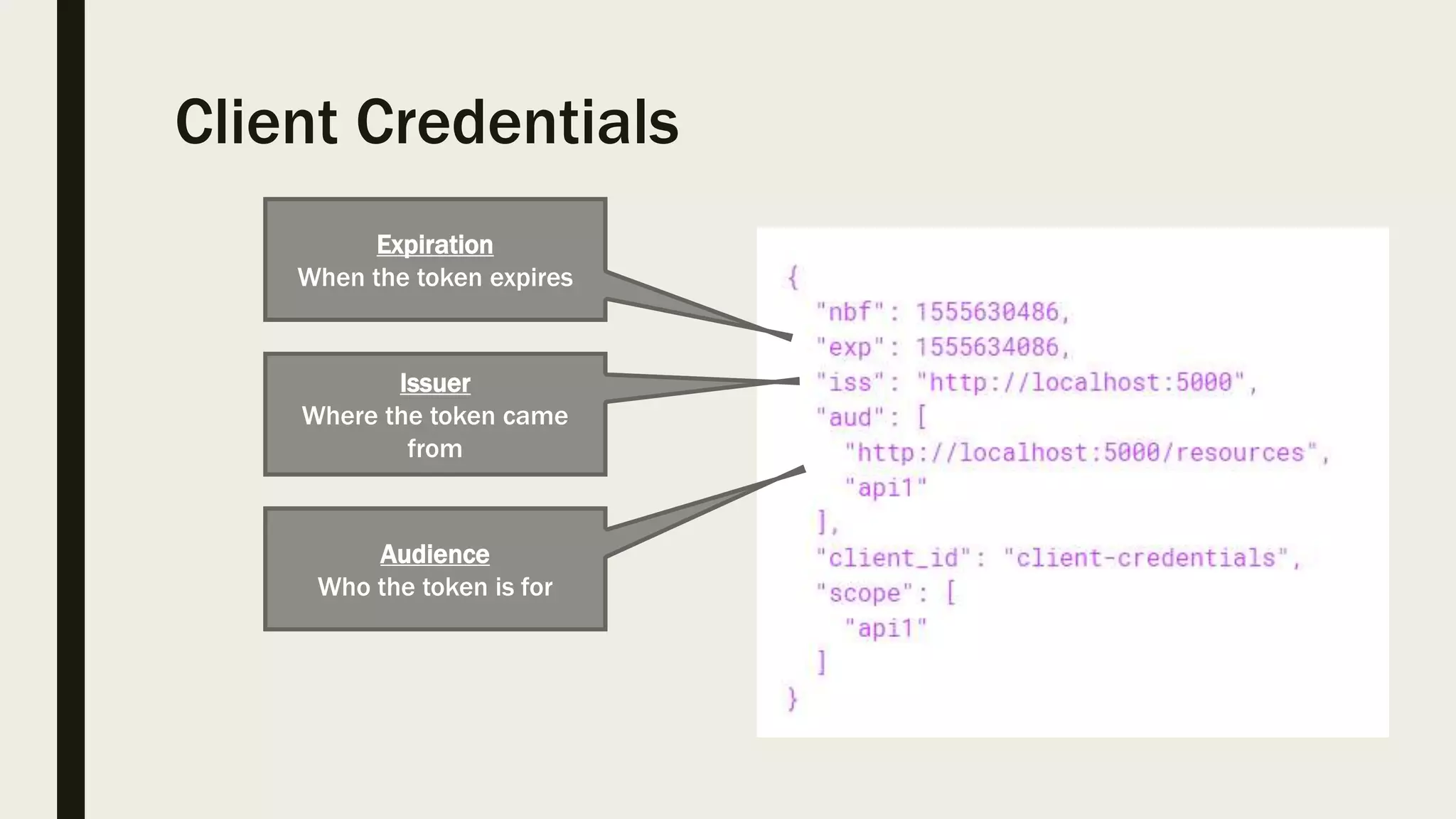
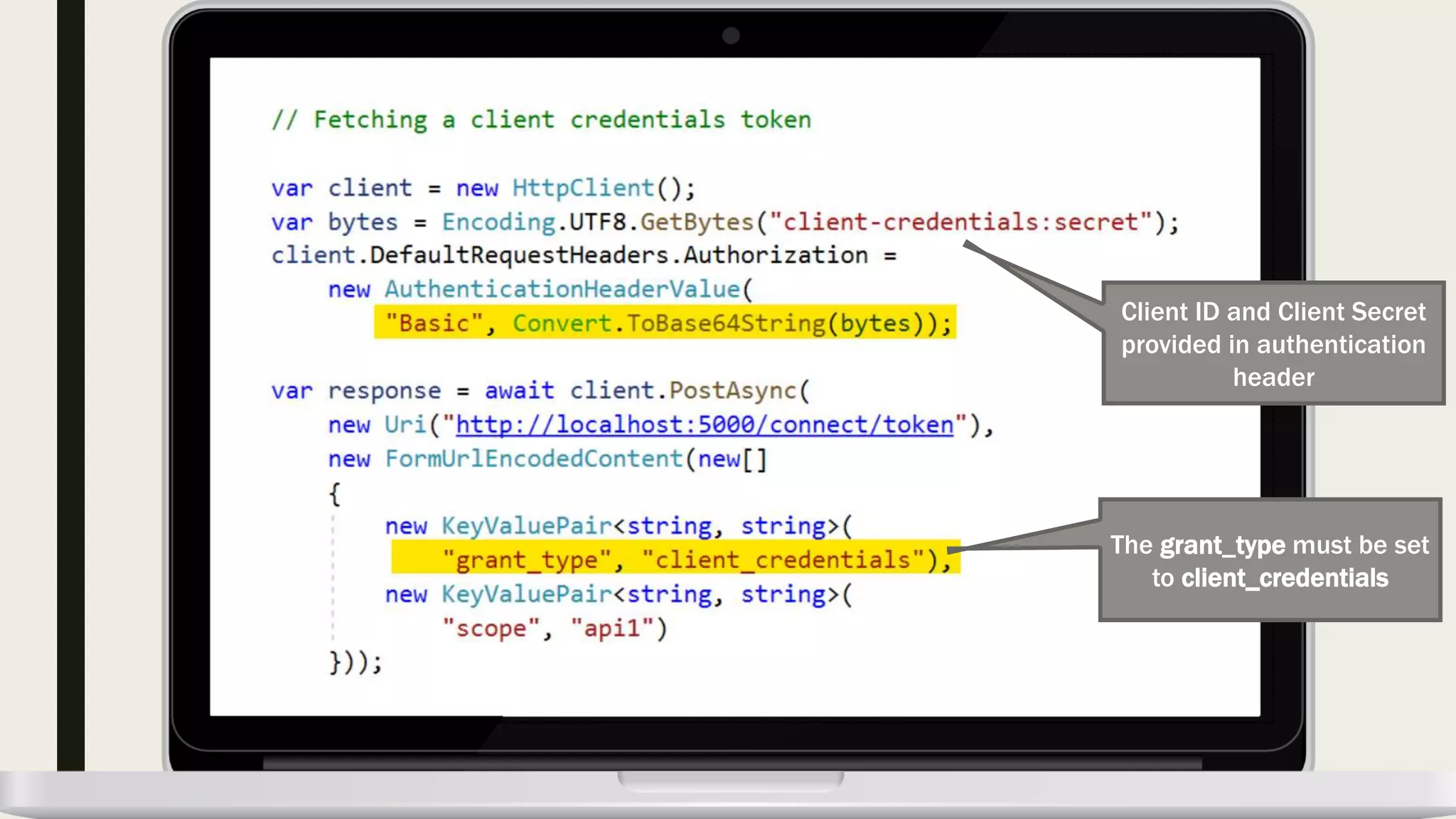
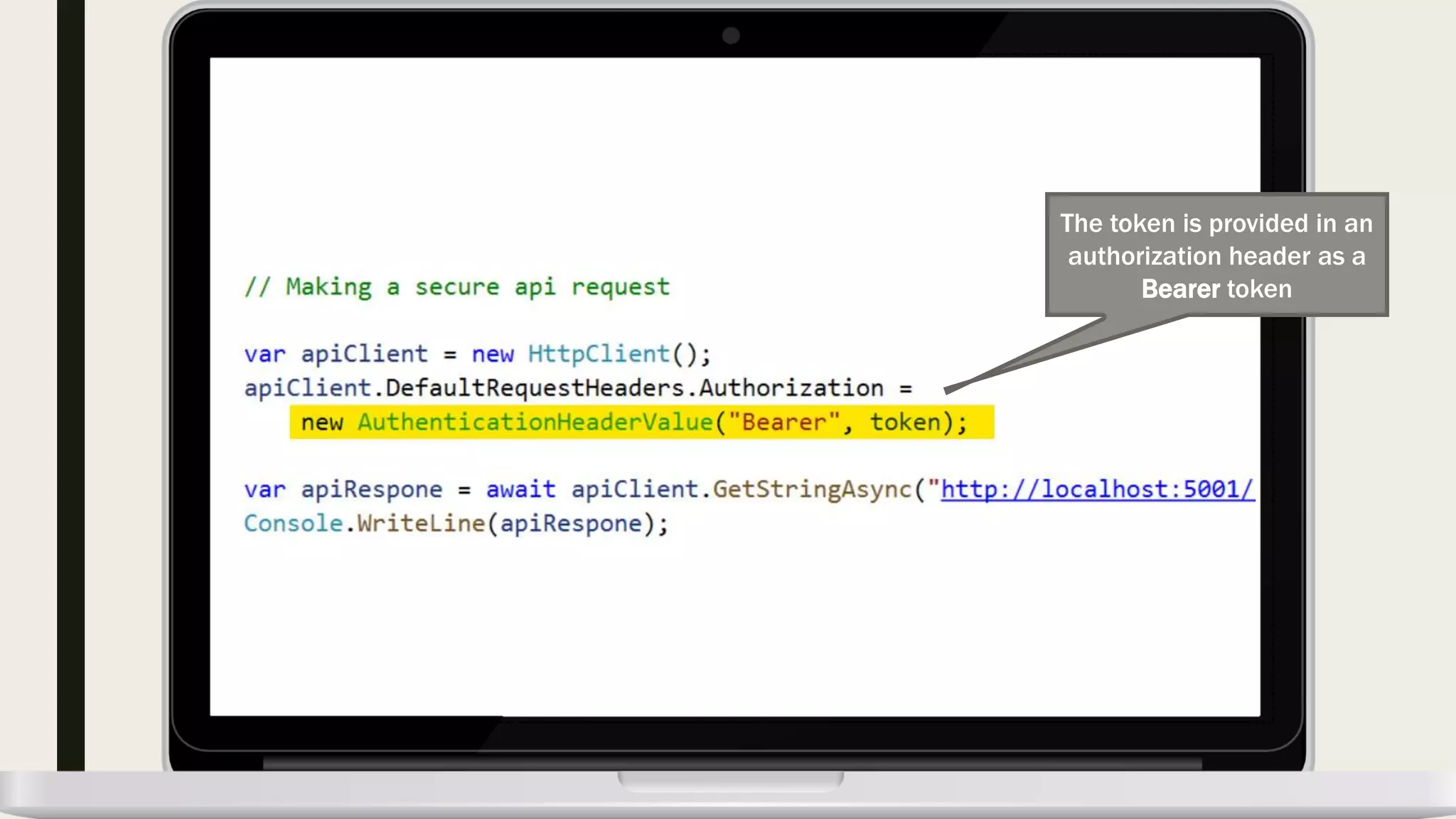
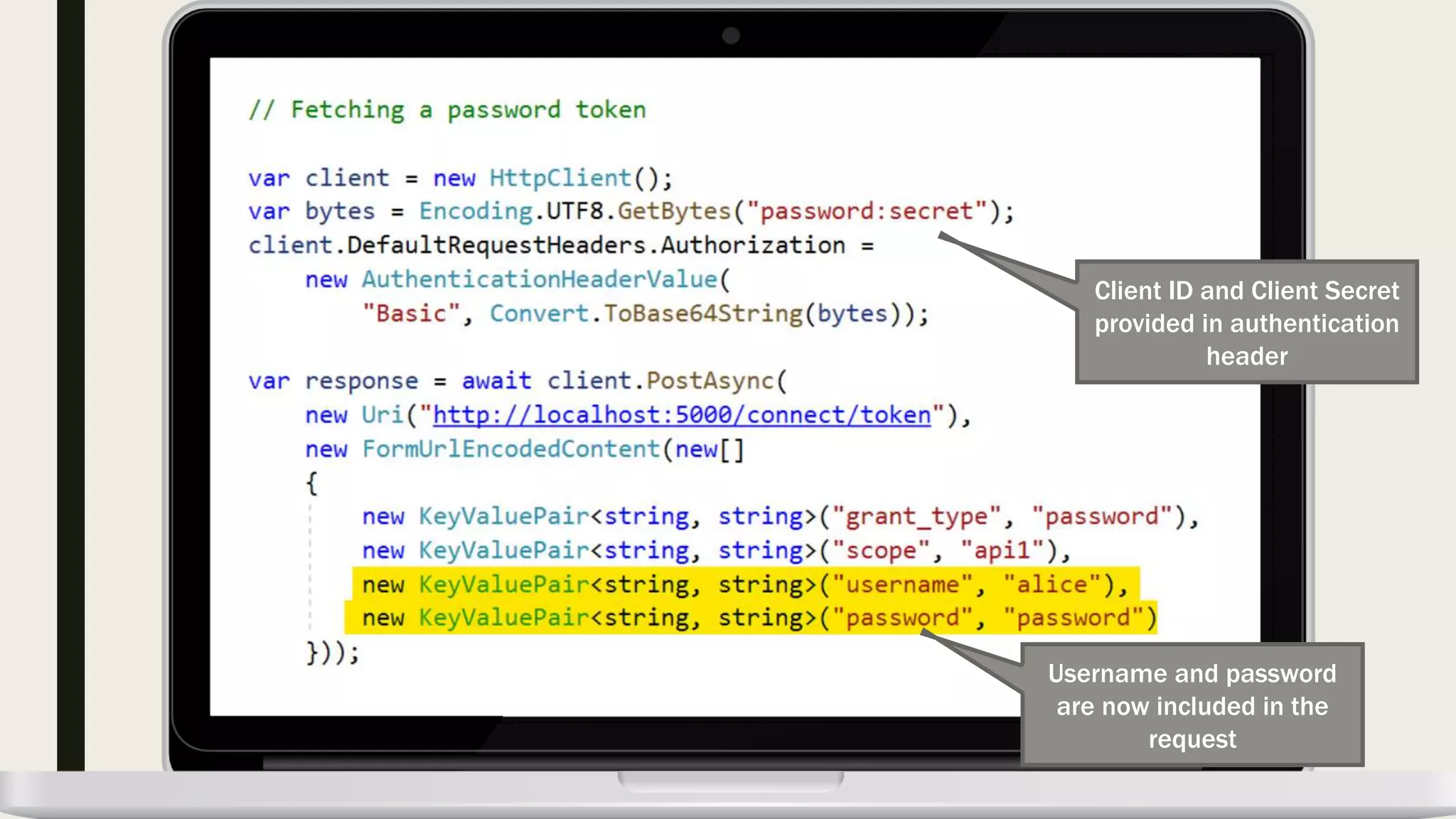
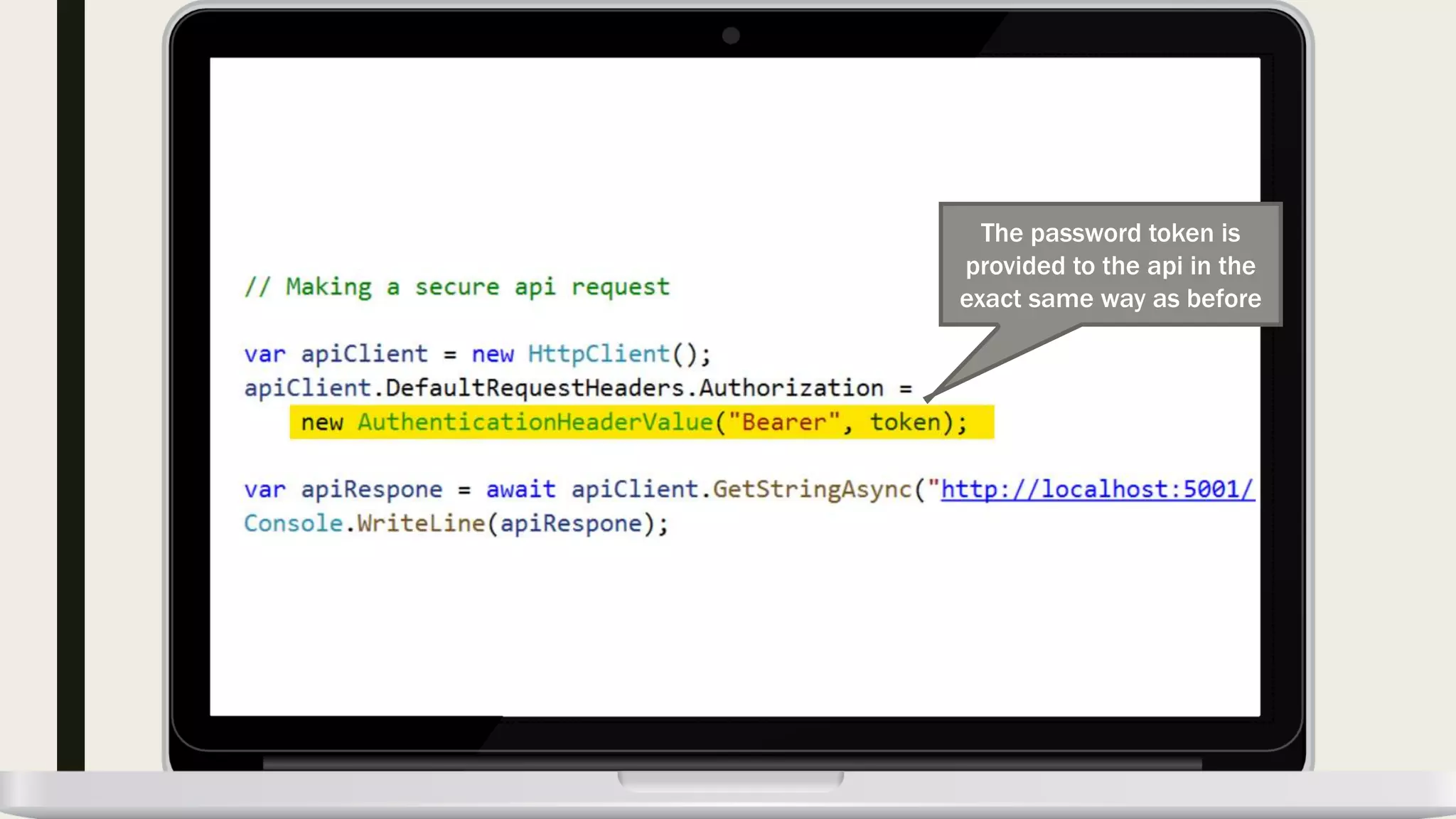
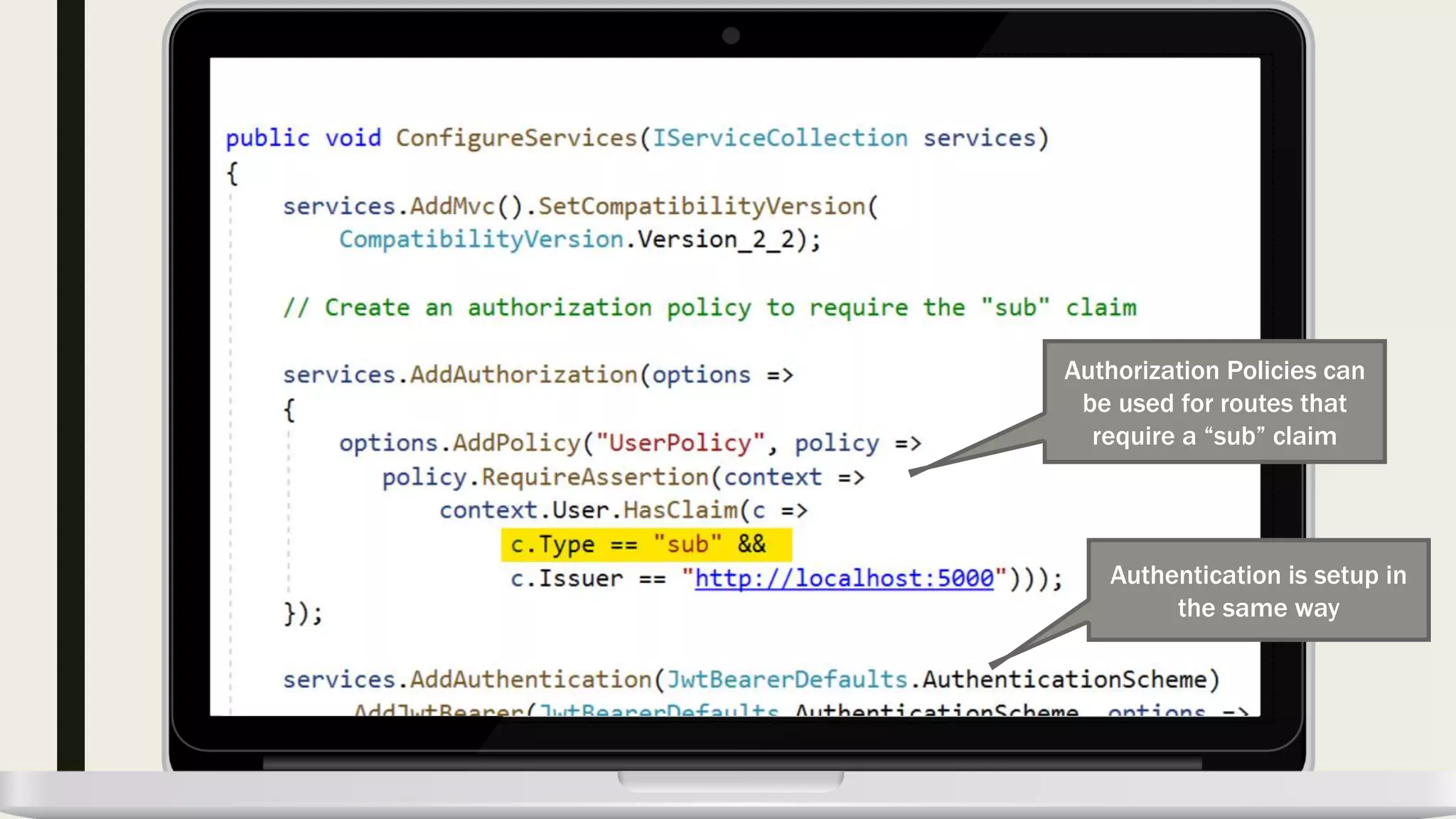
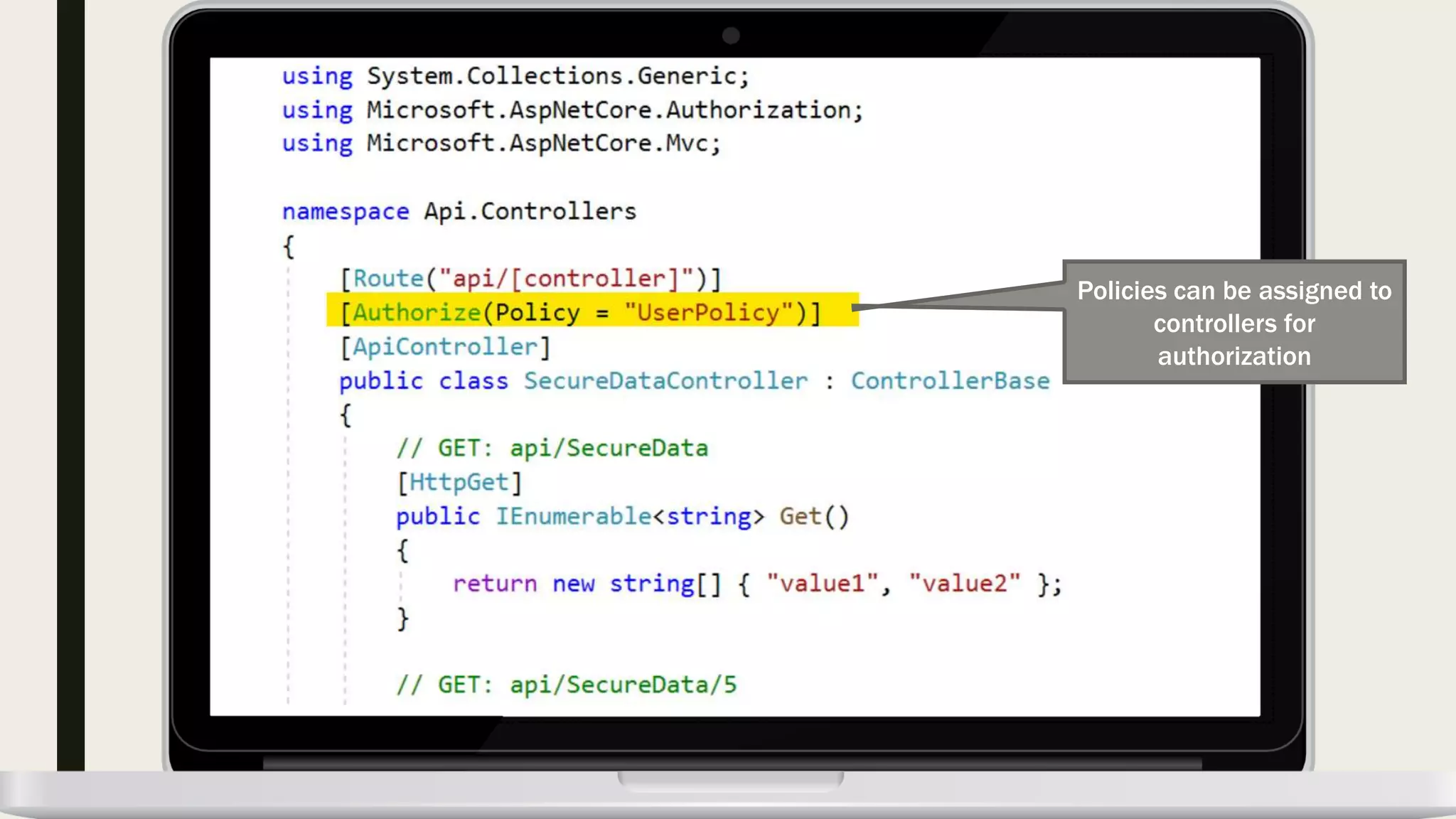
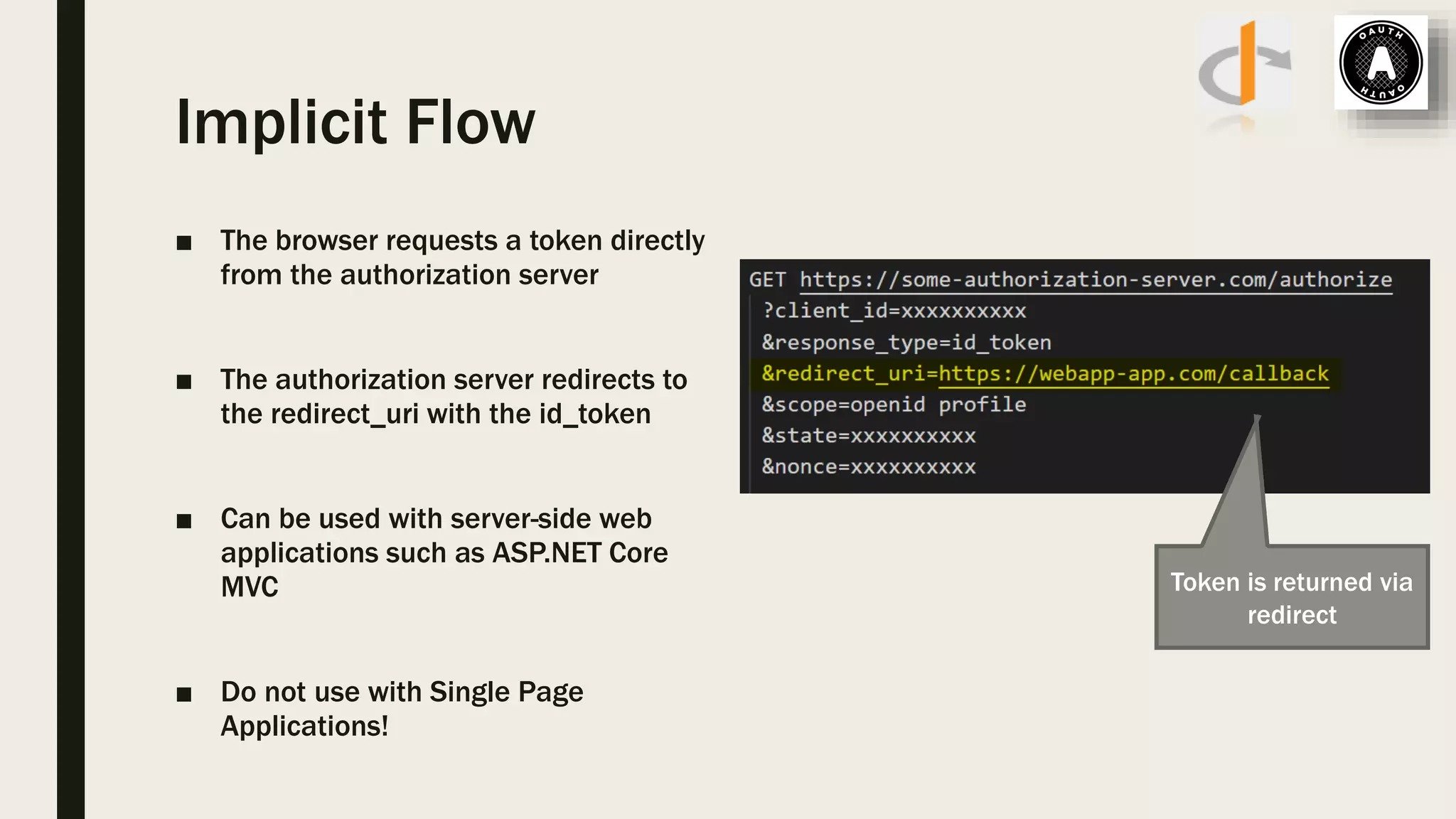
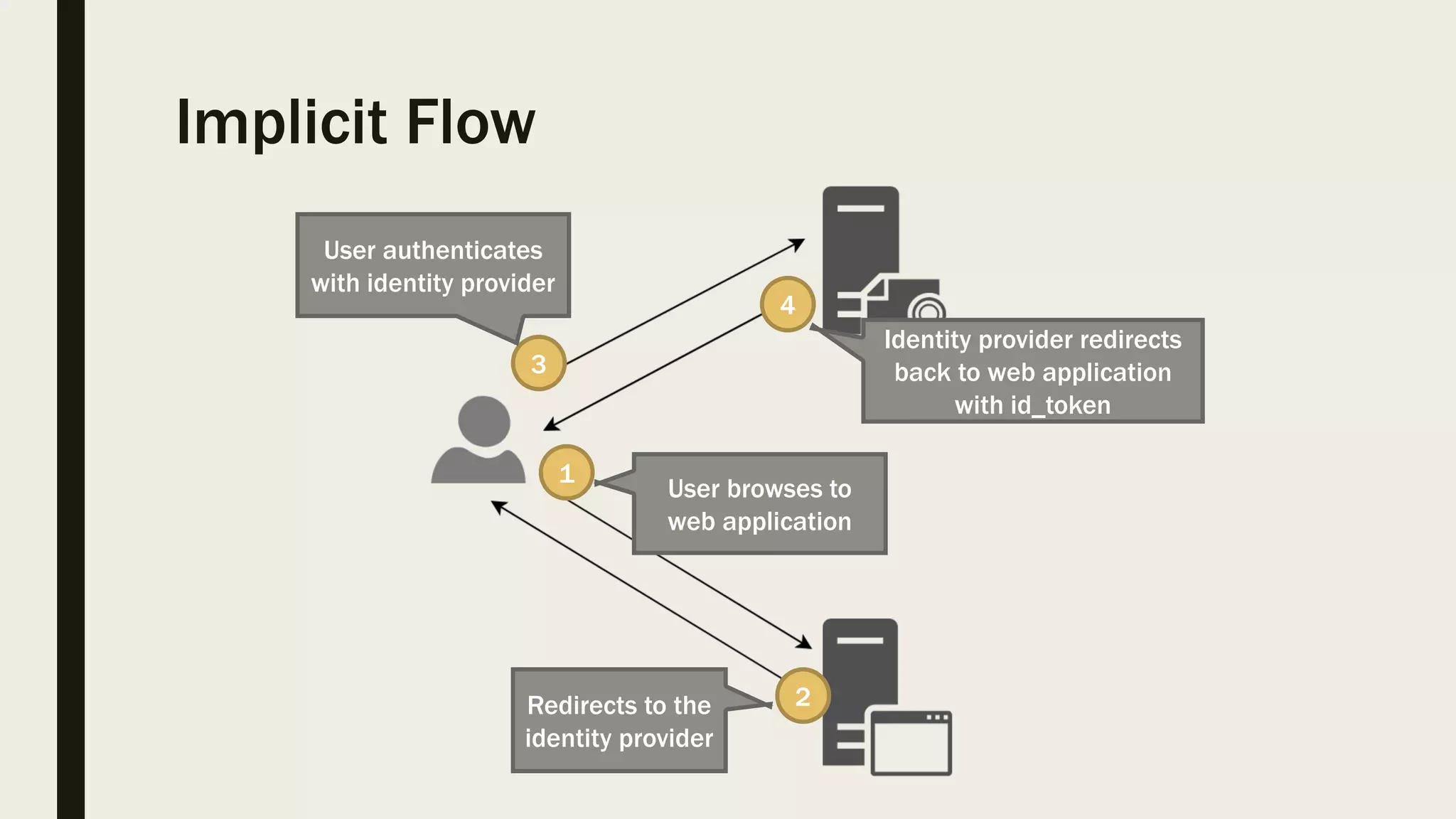
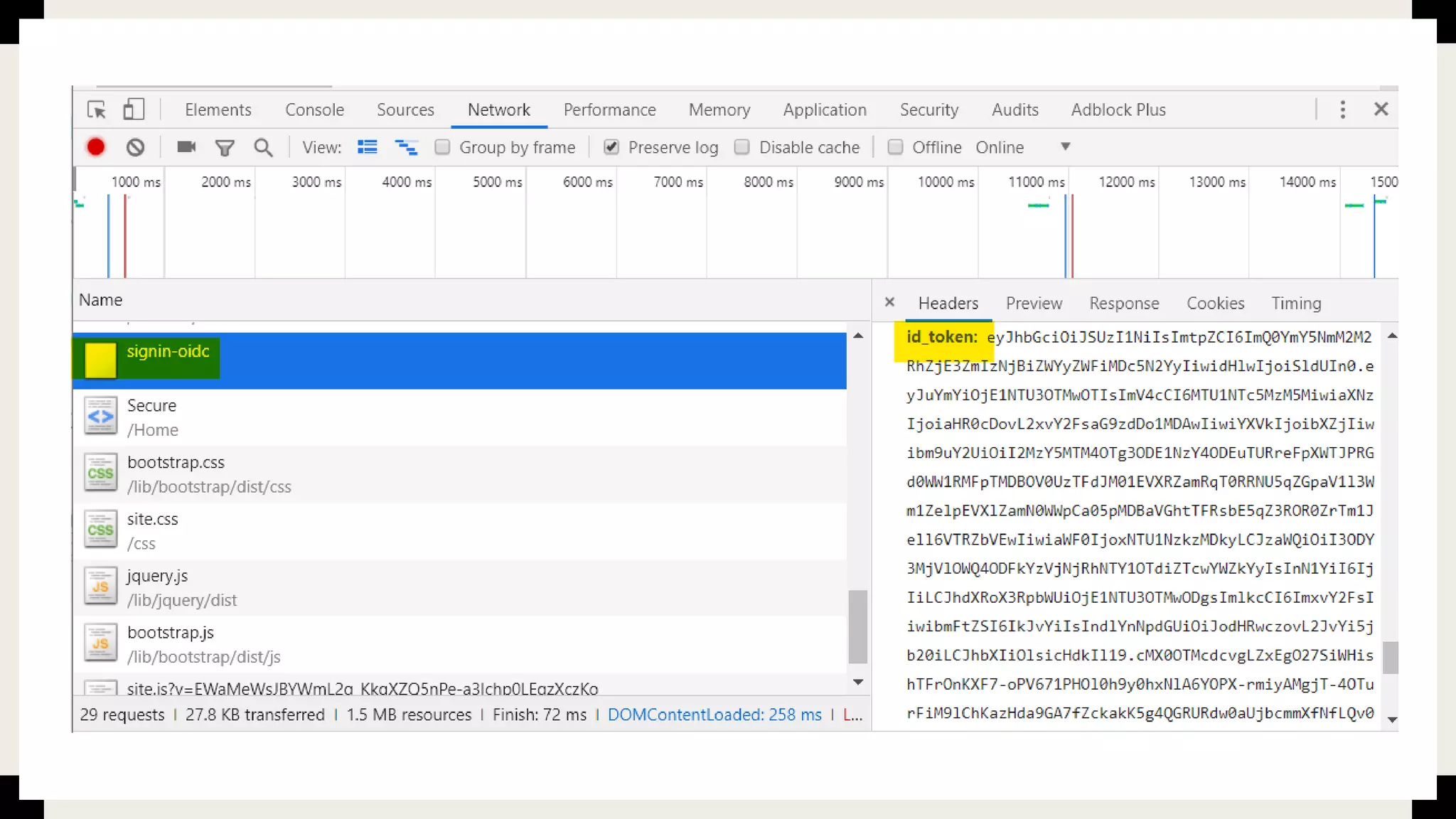
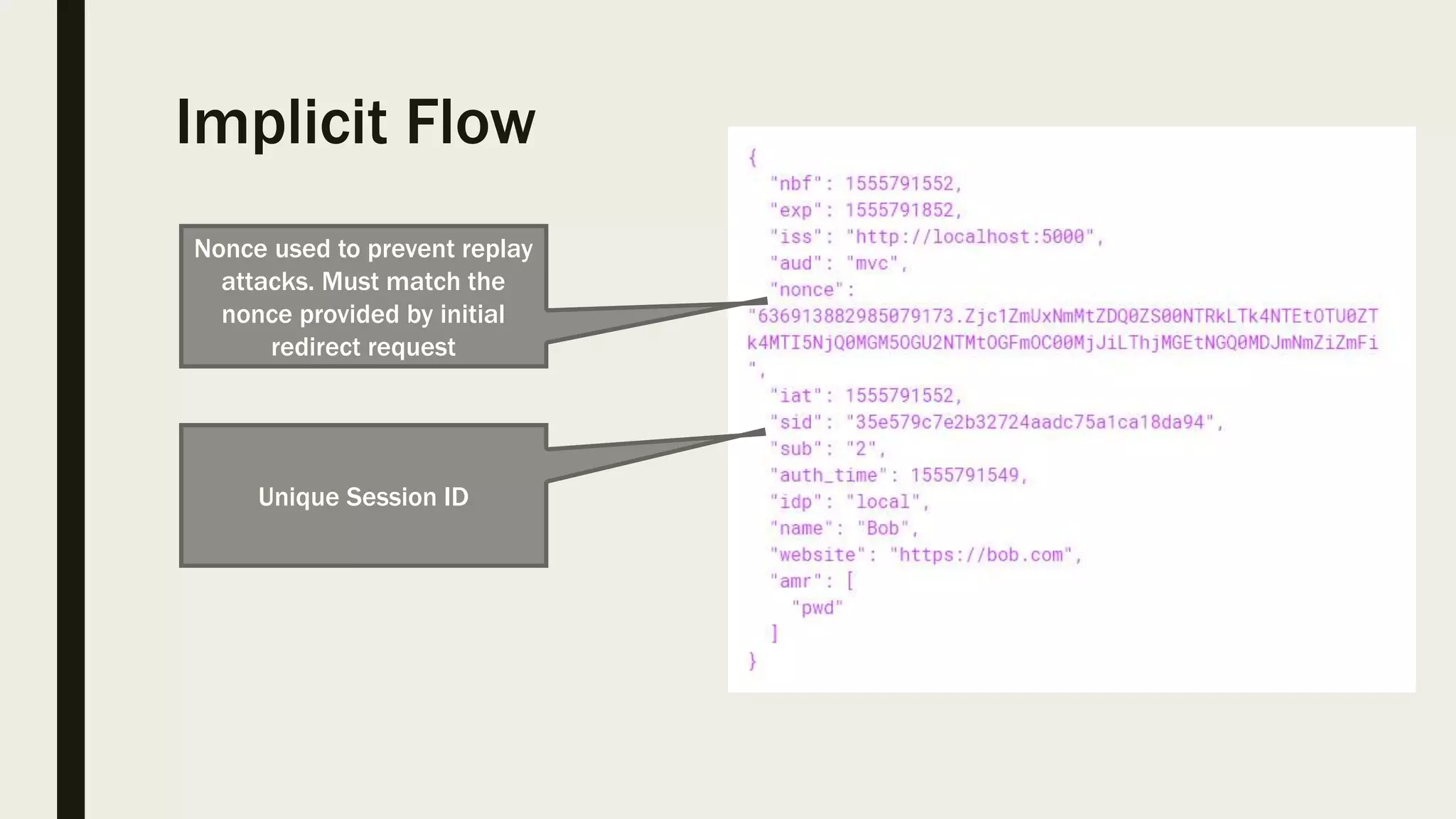
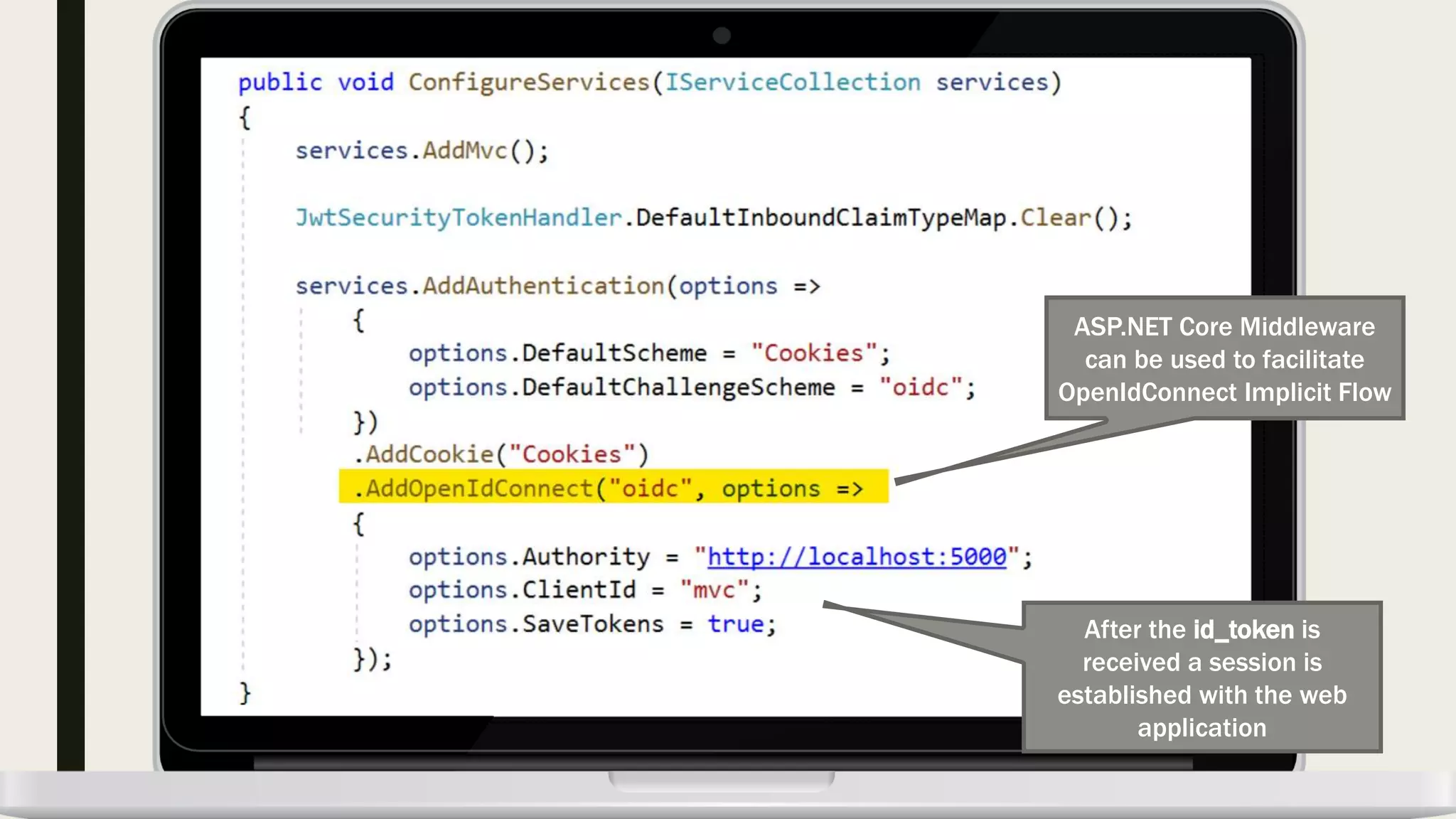
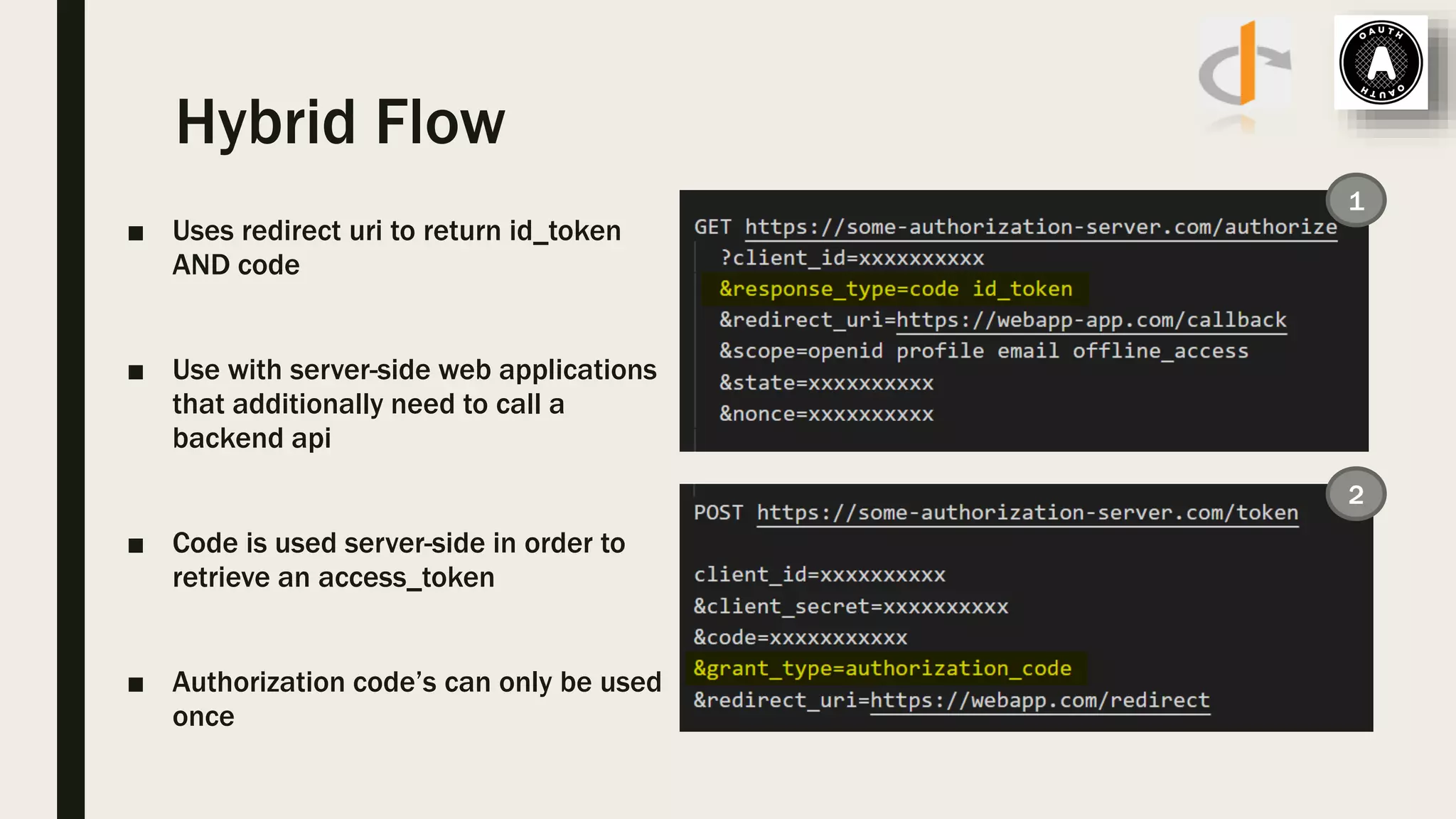
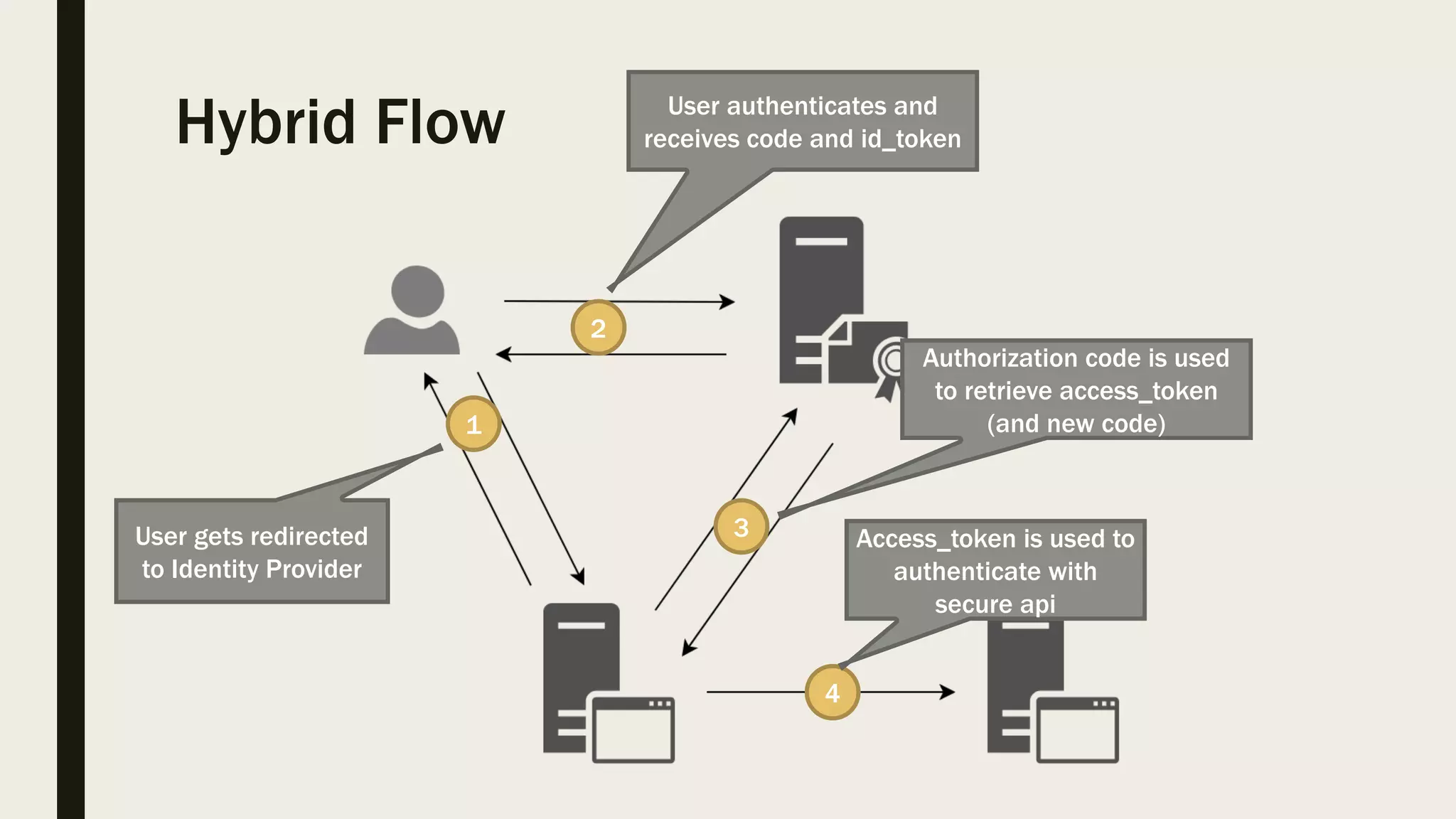
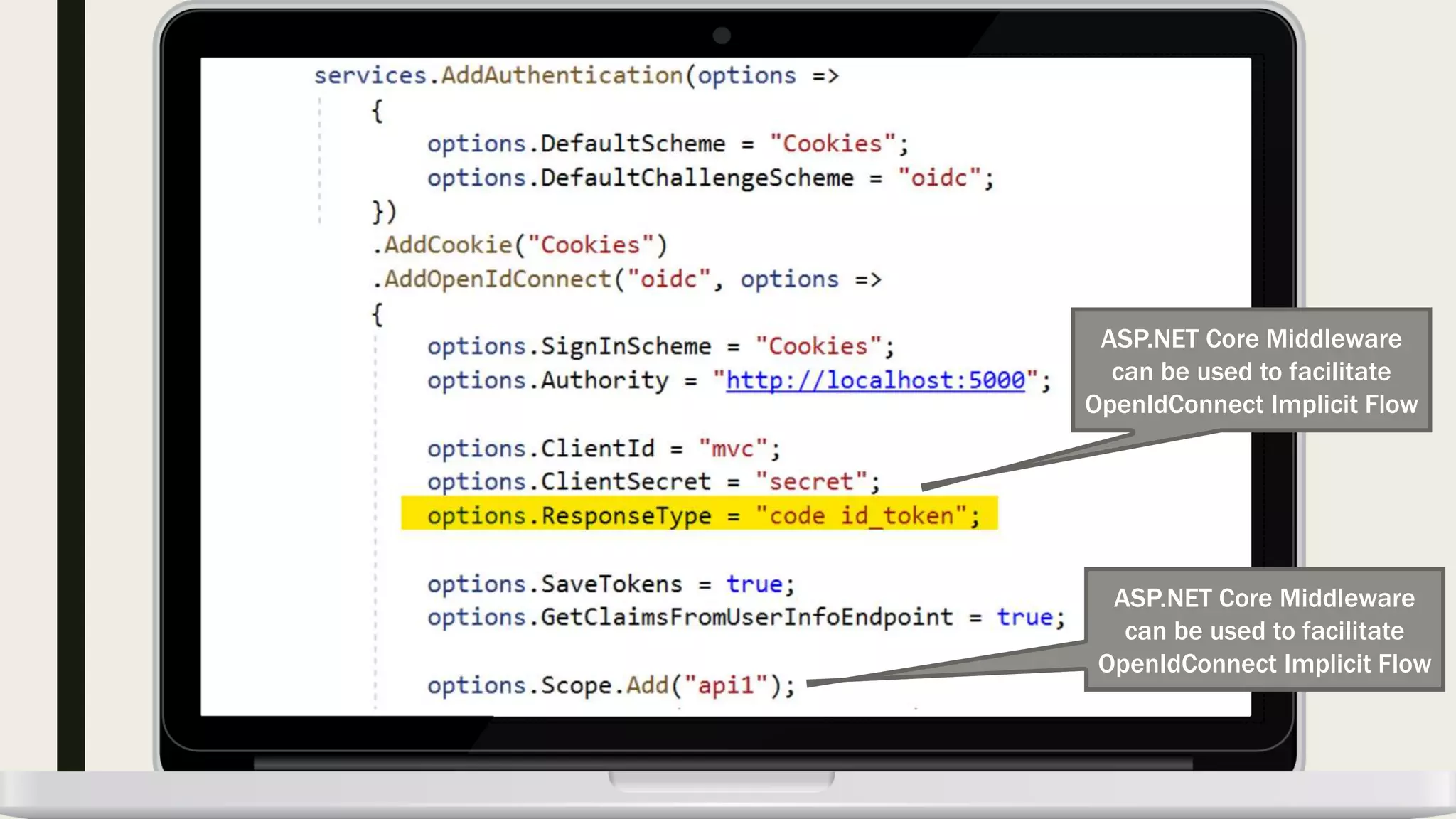
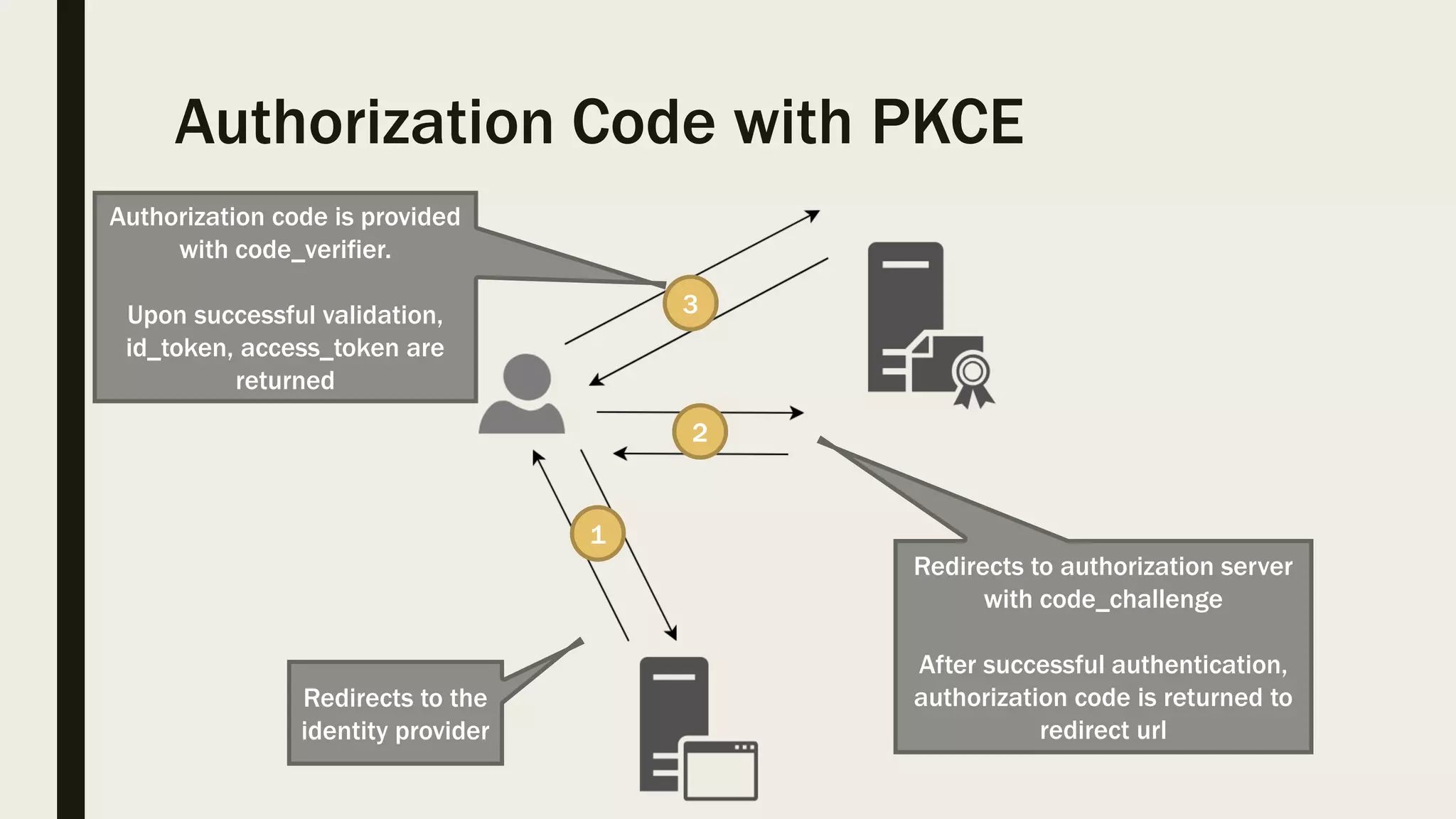
The document discusses user management and authentication methods for web applications, highlighting the evolution from traditional identity management to utilizing OAuth 2.0 and OpenID Connect with JSON Web Tokens (JWTs). It covers various authentication flows, including client credentials, password, and implicit flows, emphasizing the importance of choosing the right identity provider based on the application's infrastructure. The document concludes with recommendations for modern authentication practices, particularly for single-page applications (SPAs), advocating for the use of authorization code with Proof Key for Code Exchange (PKCE).