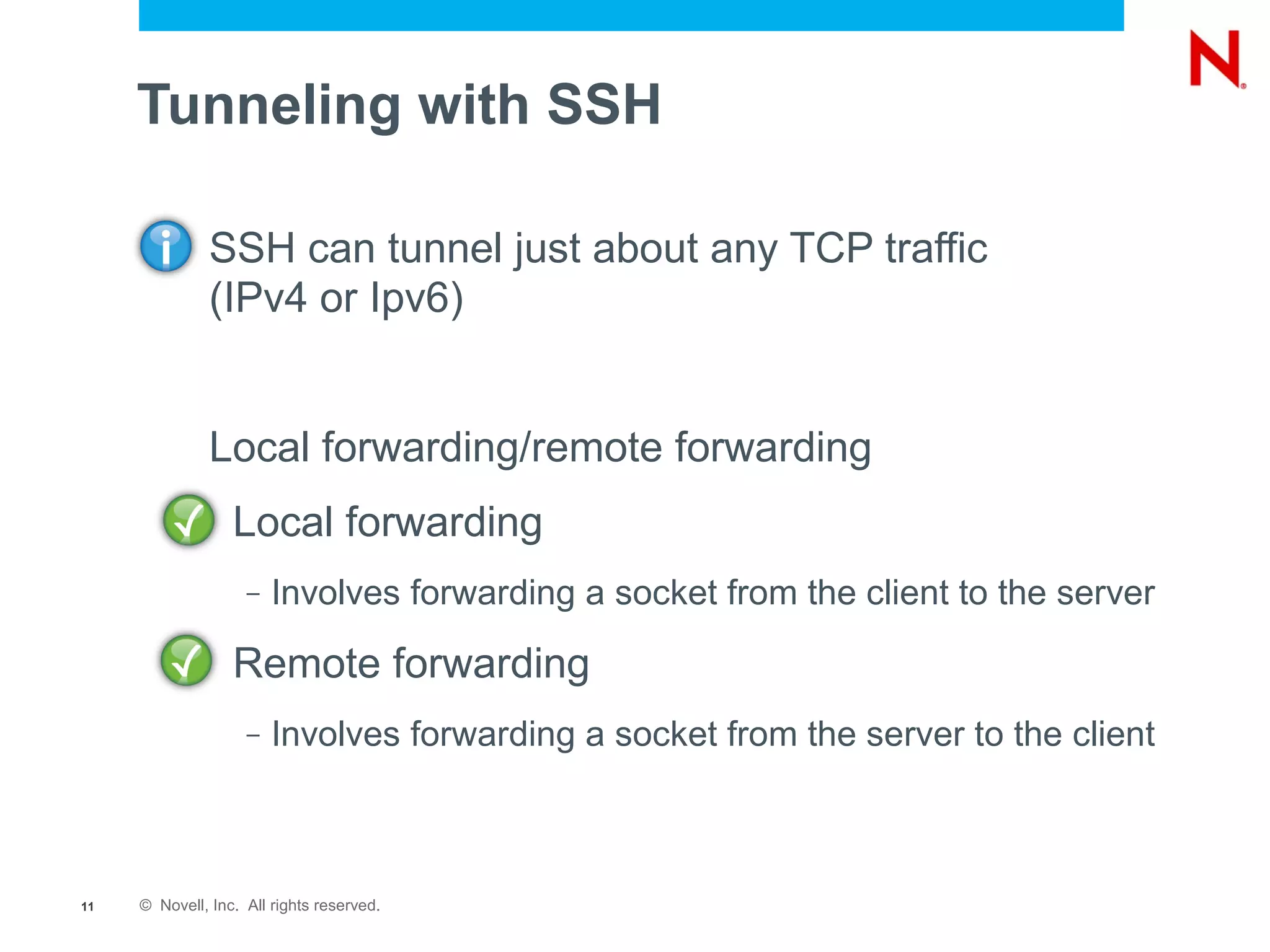
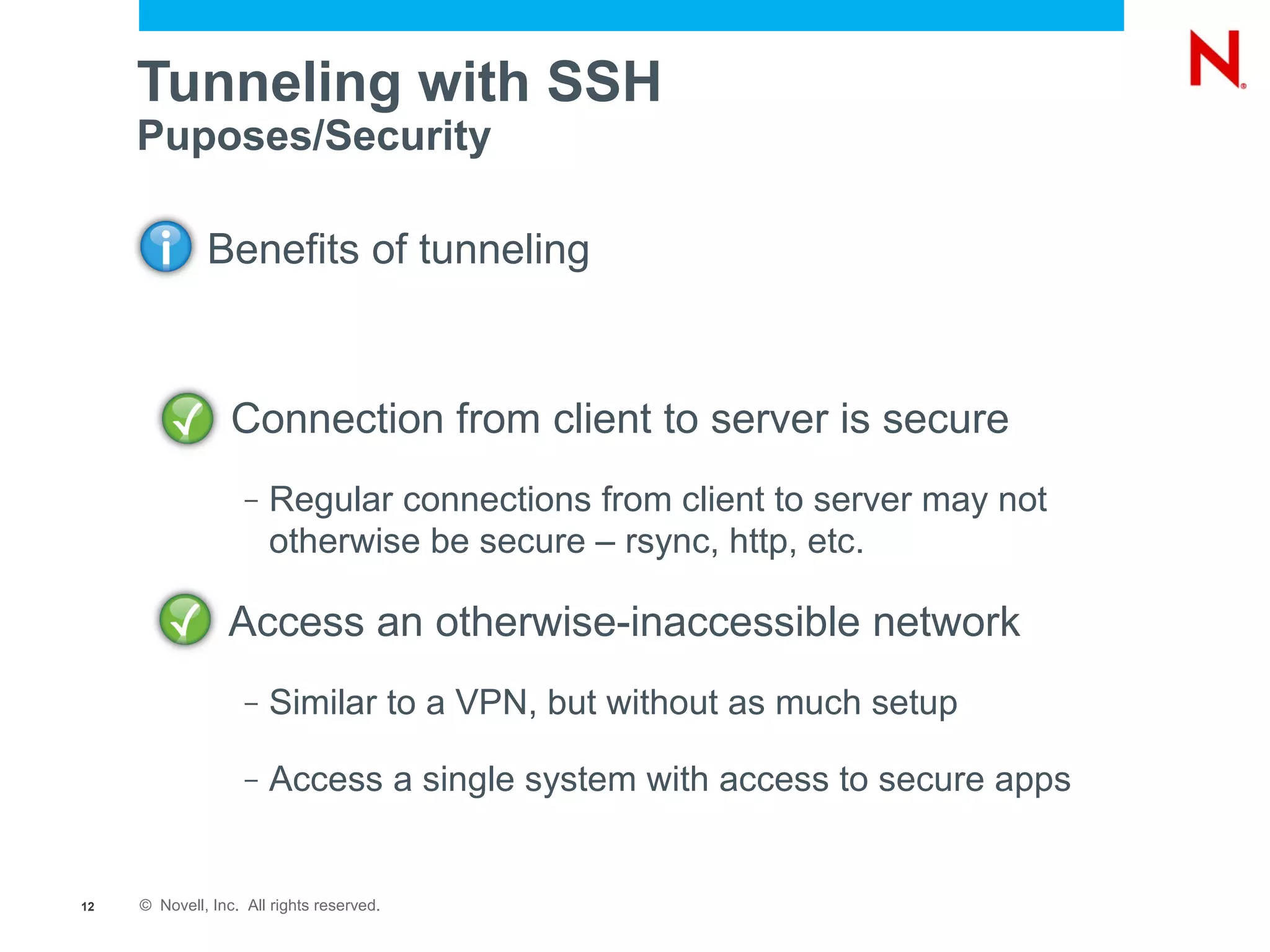
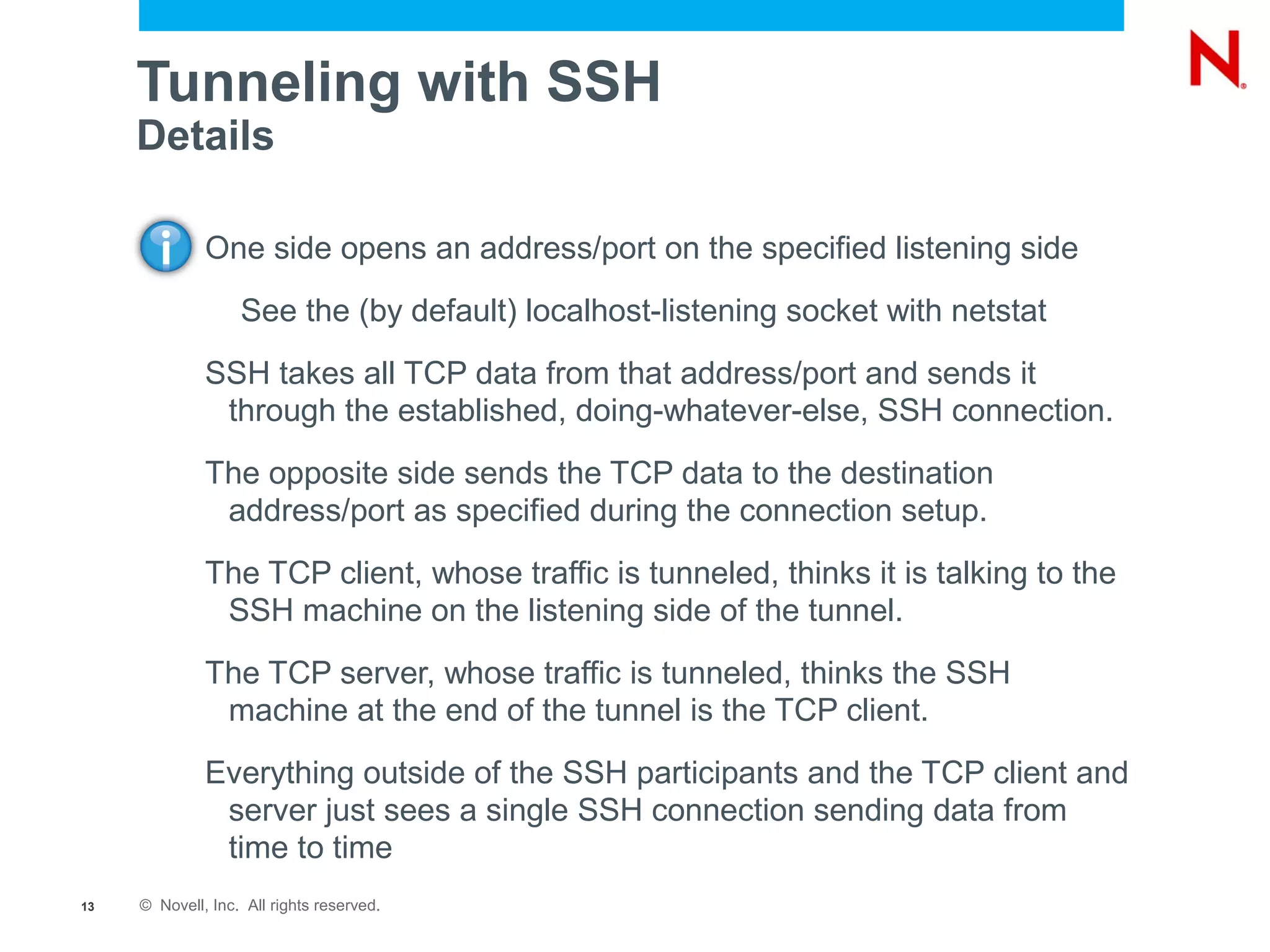
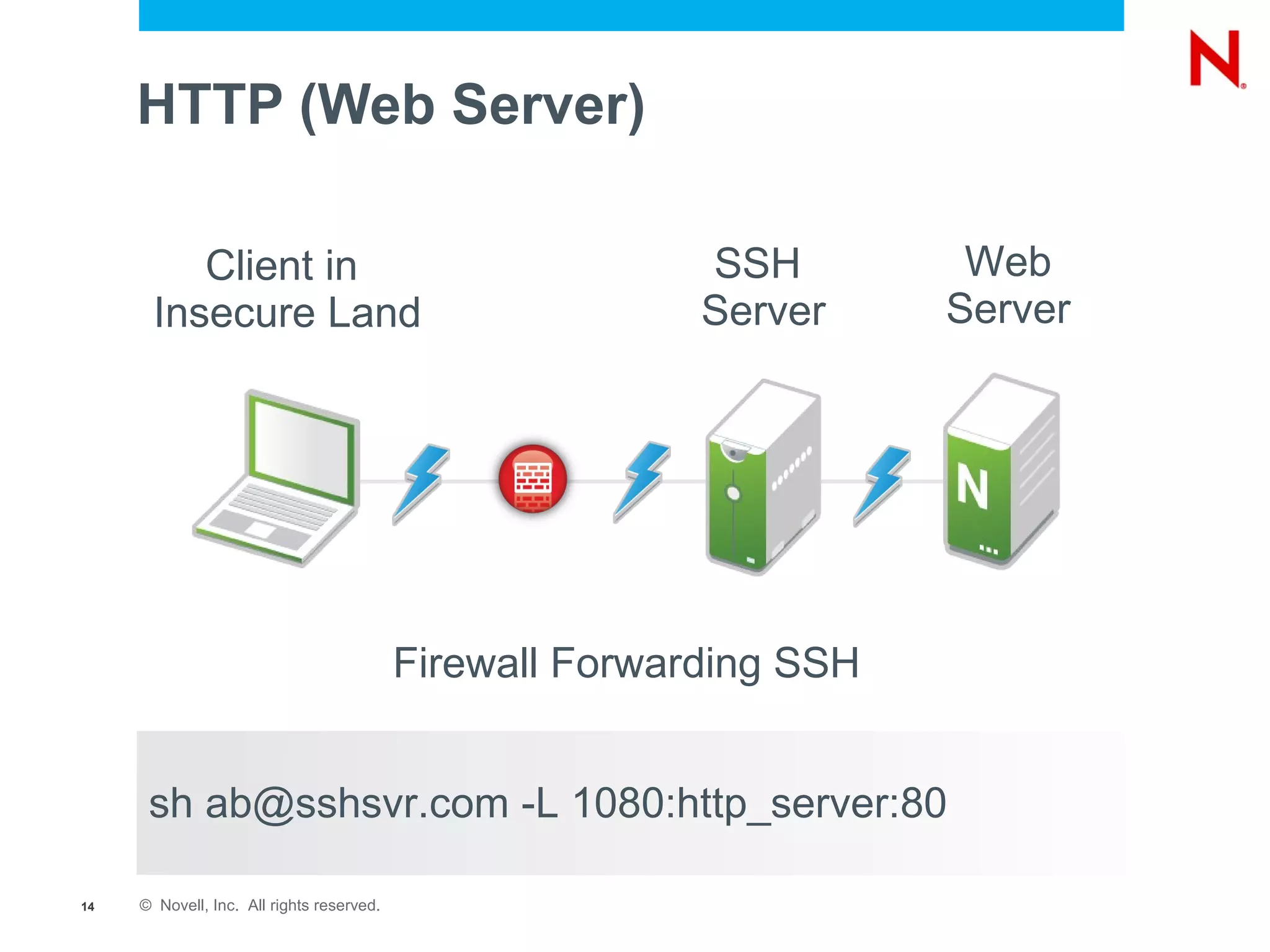
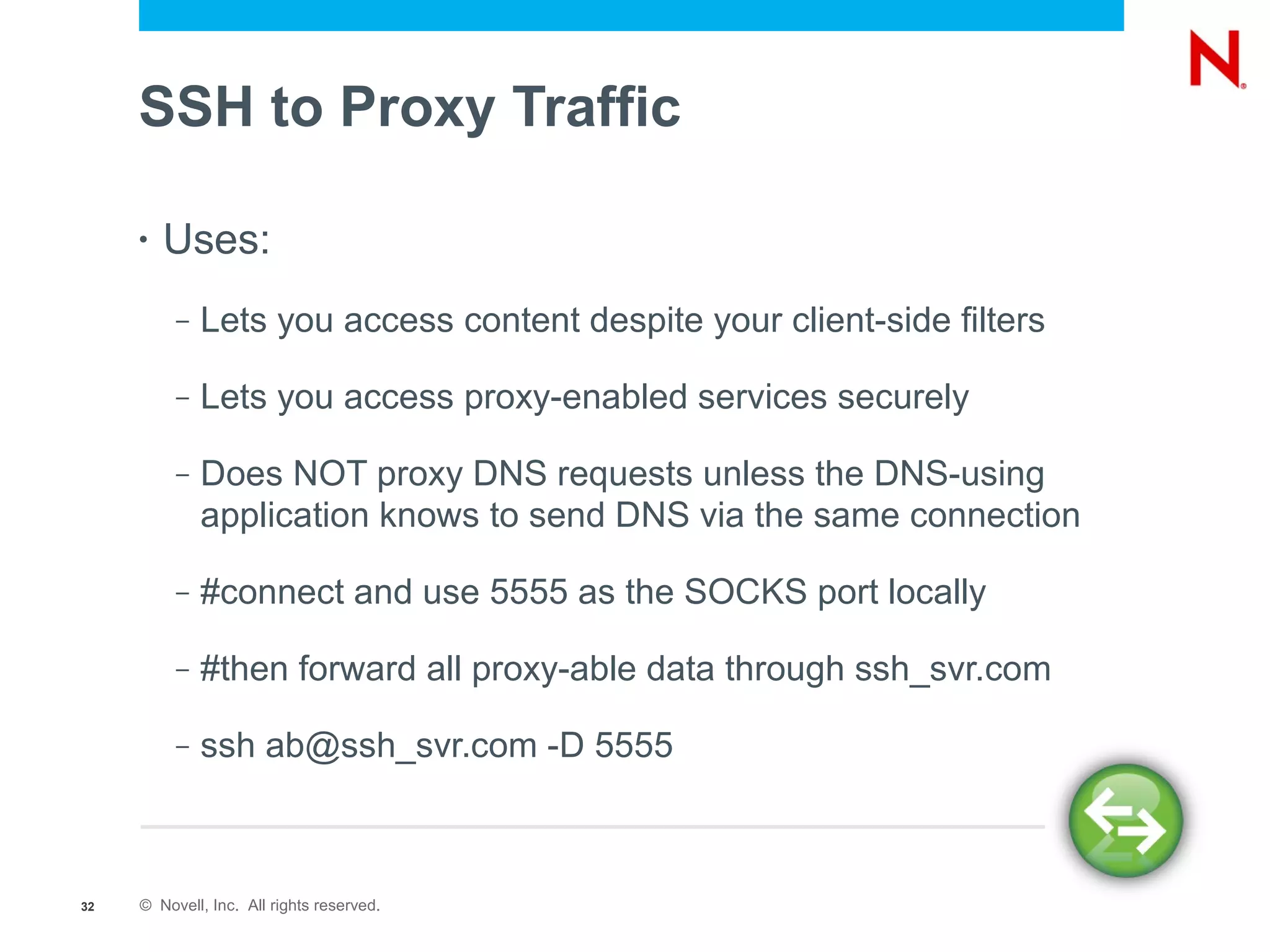
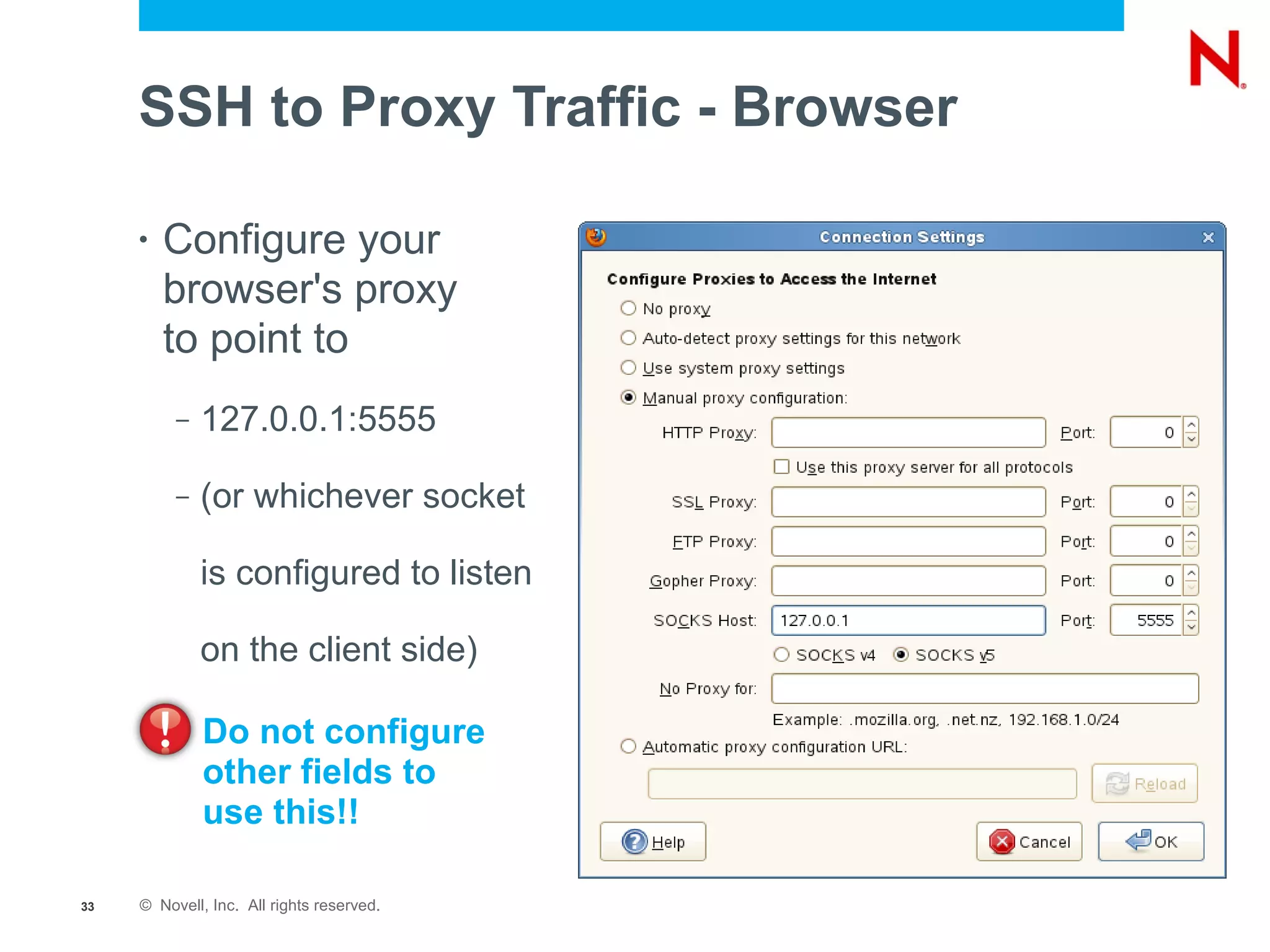
The document provides a comprehensive overview of SSH, a secure network protocol, detailing its accessibility, usage, and tools available on various operating systems. It explains how SSH can be utilized for various tasks such as tunneling, remote command execution, file transfers, and secure connections to networks and services. Additionally, it emphasizes the importance of key management for authentication and outlines troubleshooting steps for common SSH issues.










![SSH Troubleshooting • Understand the technology and feature – TCP-based – Tunneling/proxying opens sockets – X-forwarding requires X libraries on the forwarding side, X- server on the forwarded side – Authentication can happen in multiple ways • Test another system – Maybe client or server is a lemon, e.g. running Windows :-) • Use the -v[v[v]] options from the command line – More 'v' mean more-verbose... lots of good data in here – Get a baseline BEFORE it breaks 35 © Novell, Inc. All rights reserved.](https://image.slidesharecdn.com/els201-100324143423-phpapp01/75/Using-Secure-Shell-on-Linux-What-Everyone-Should-Know-35-2048.jpg)