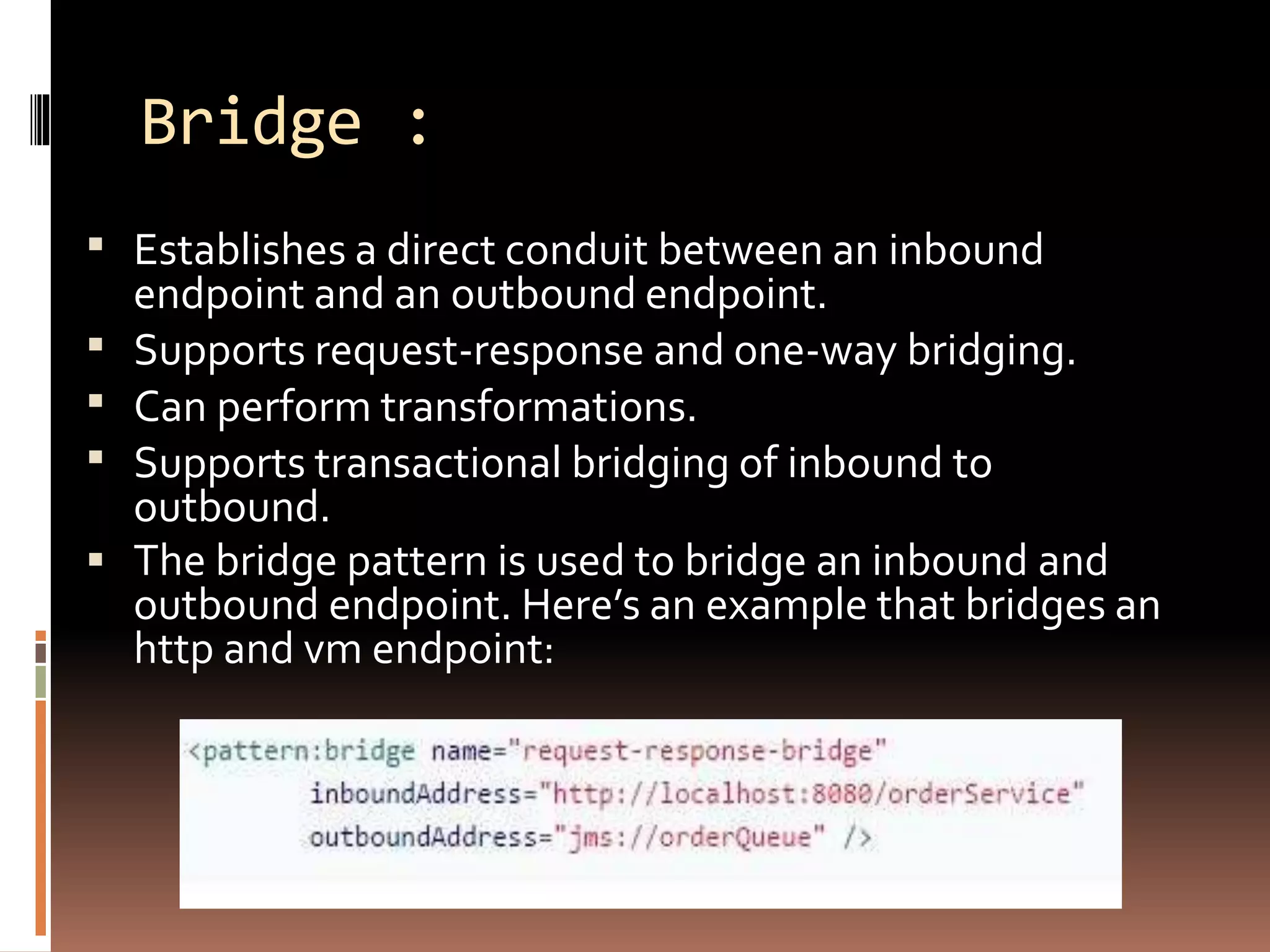
This document discusses Mule configuration patterns, including simple service, web service proxy, bridge, validator, and HTTP proxy patterns. It provides descriptions of each pattern type and examples of how they can be used. The key points are that configuration patterns make common tasks simpler and more understandable by acting like predefined templates, avoiding complex XML configuration when possible. Developers are encouraged to use a configuration pattern if it matches their needs rather than building custom flows from scratch.