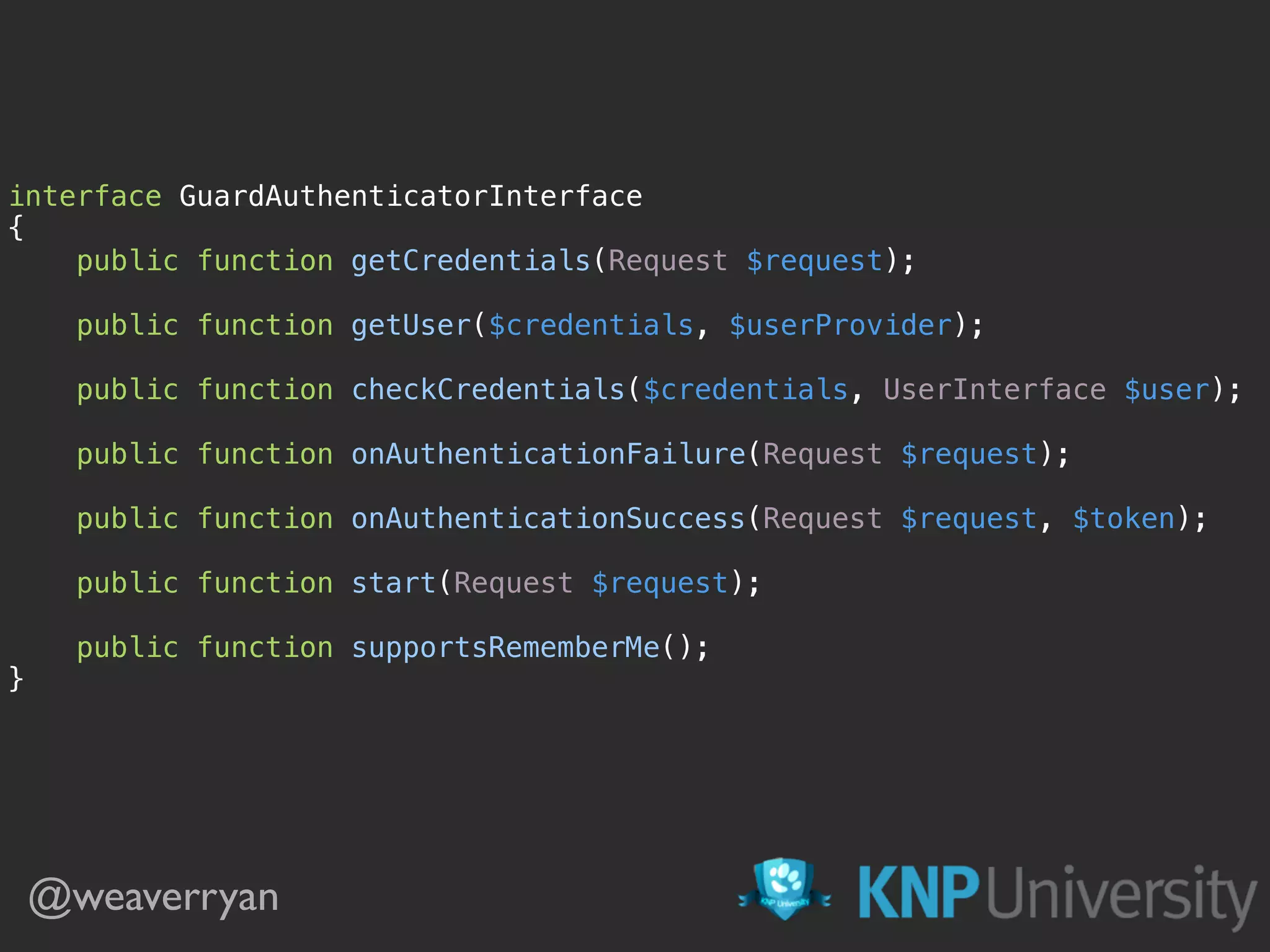
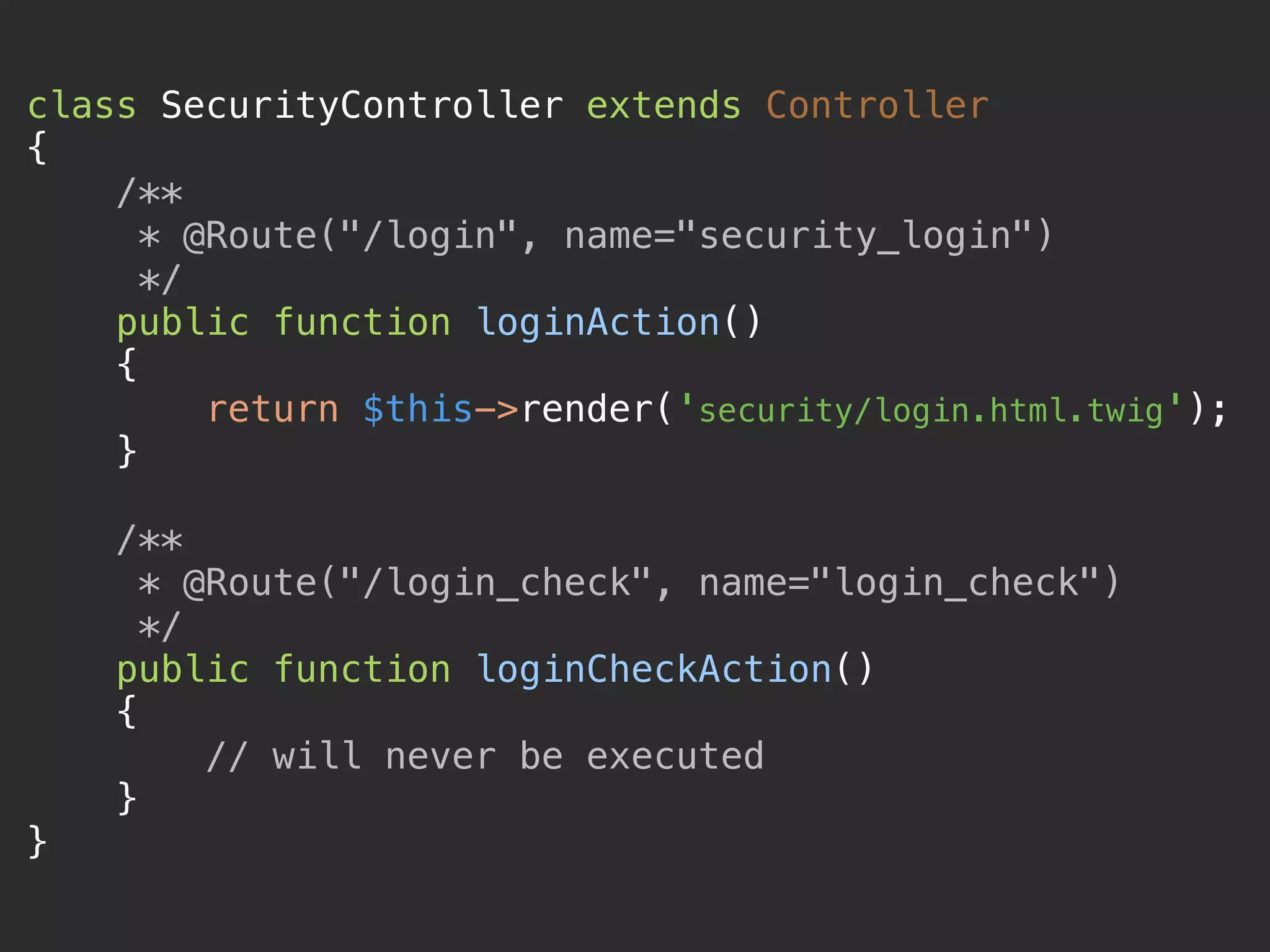
The document provides a comprehensive overview of implementing authentication in Symfony using Guard, including steps for user credential validation, form login setup, and JWT authentication. It discusses various classes involved, the user provider interface, and how to handle authentication success and failure. Additionally, it touches on integrating social login via Facebook and outlines the necessary configurations and code snippets for implementing these features.




















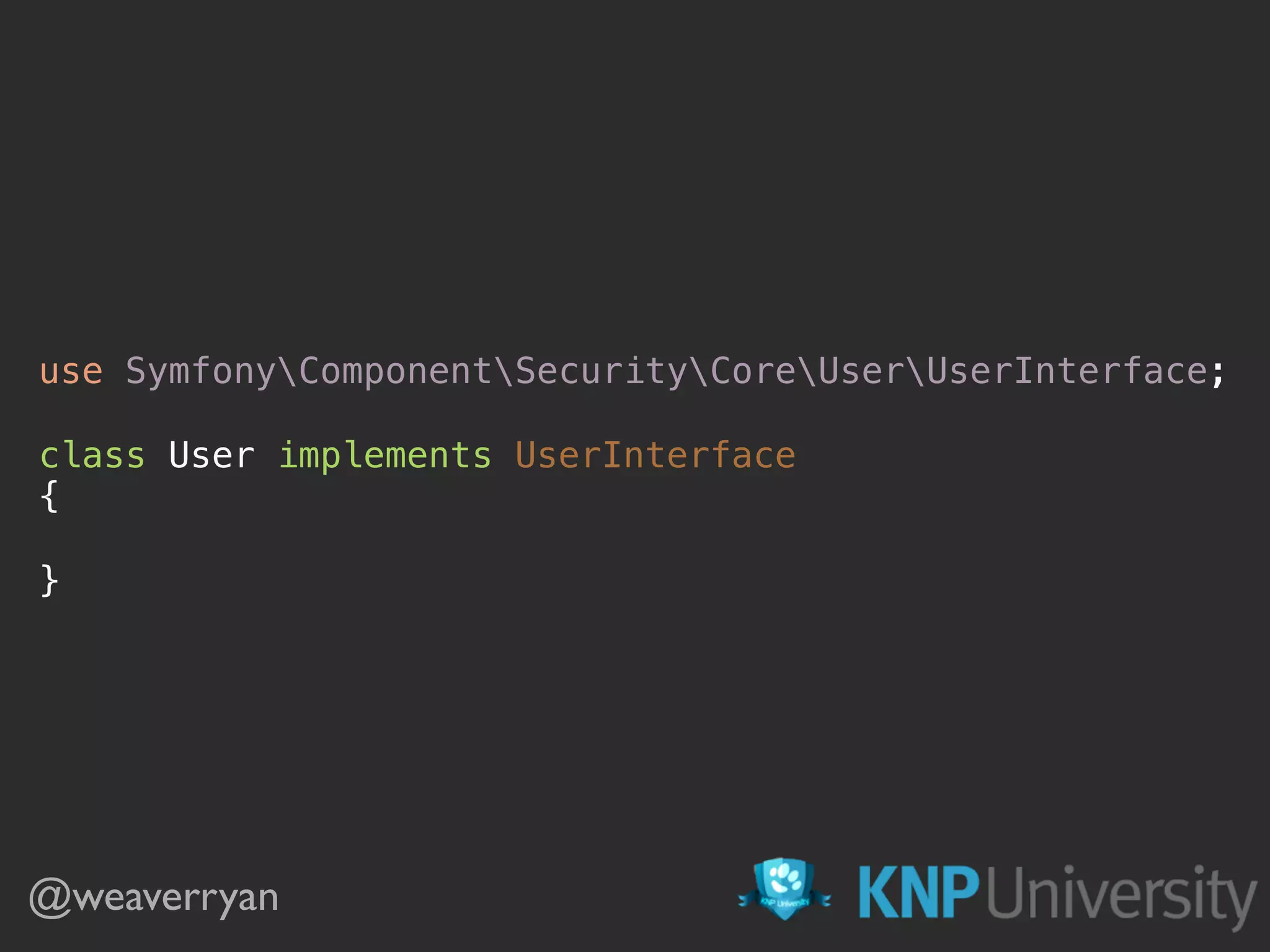
![class User implements UserInterface
{
private $username;
public function __construct($username)
{
$this->username = $username;
}
public function getUsername()
{
return $this->username;
}
public function getRoles()
{
return ['ROLE_USER'];
}
// …
} a unique identifier (not really used anywhere)](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-27-2048.jpg)




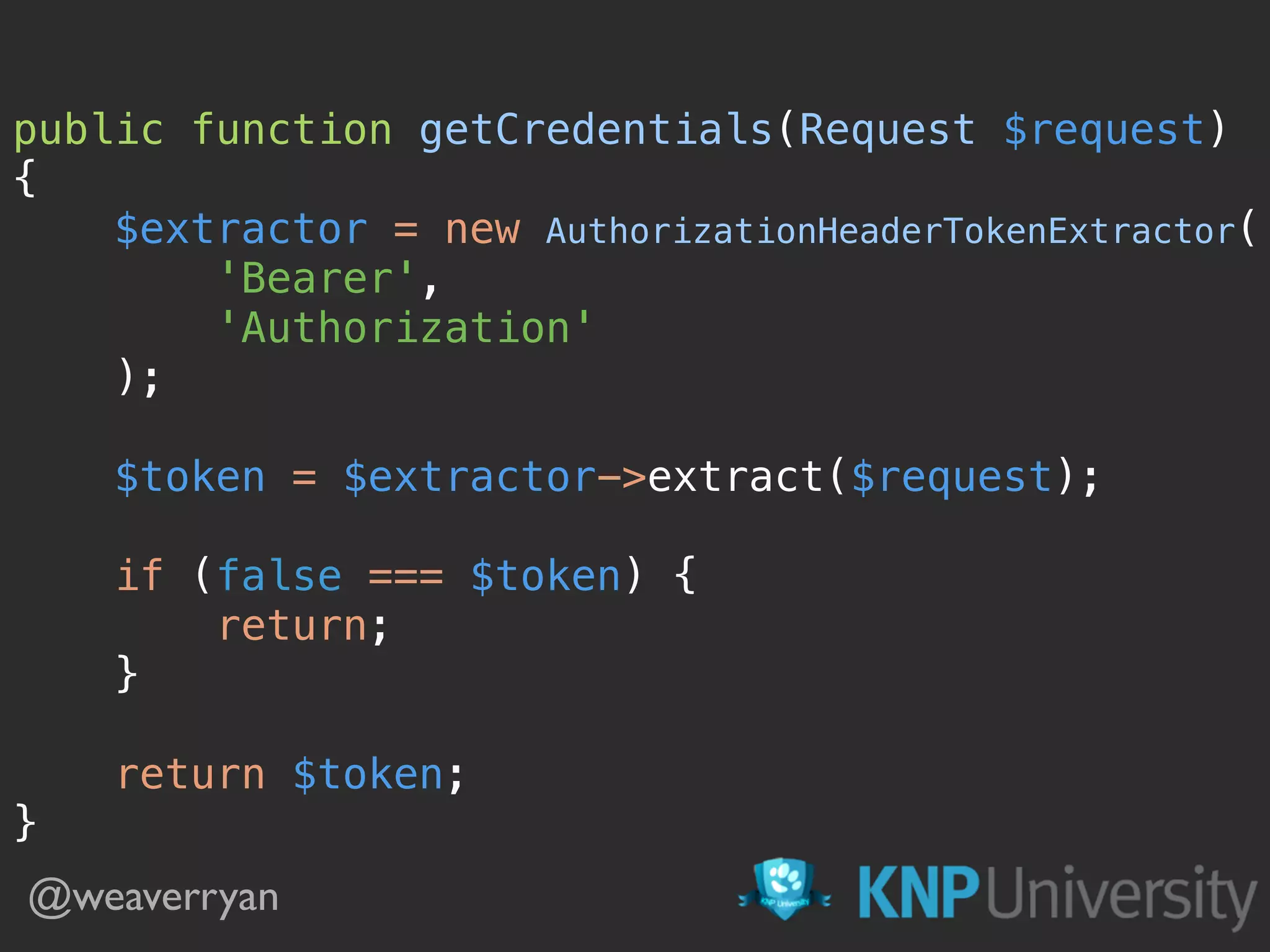
![public function getCredentials(Request $request)
{
if ($request->getPathInfo() != '/login_check') {
return;
}
return [
'username' => $request->request->get('_username'),
'password' => $request->request->get('_password'),
];
} Grab the “login” credentials! @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-35-2048.jpg)
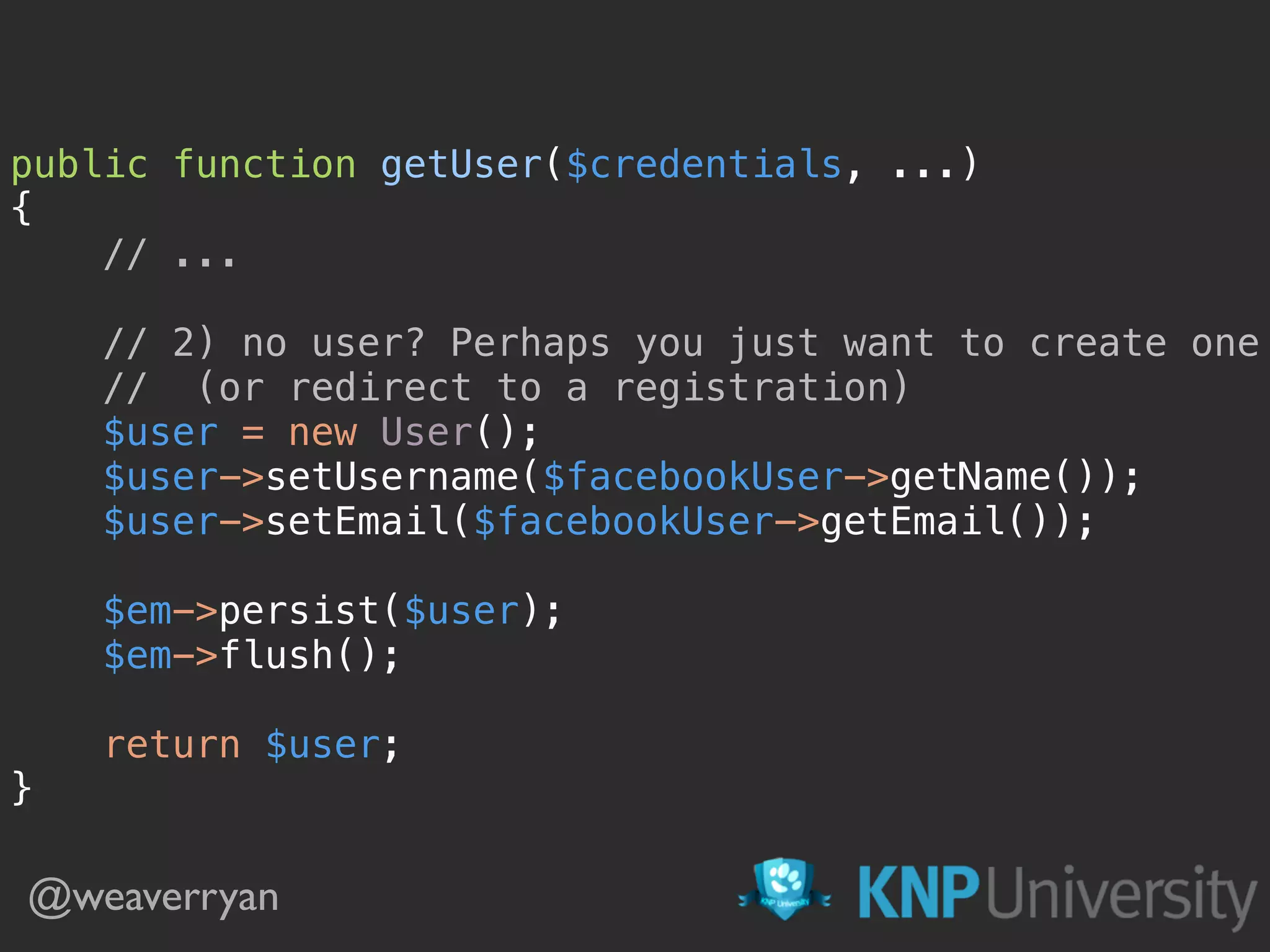
![public function getUser($credentials, UserProviderInterface $userProvider)
{
$username = $credentials['username'];
$user = new User();
$user->setUsername($username);
return $user;
} Create/Load that User! @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-36-2048.jpg)
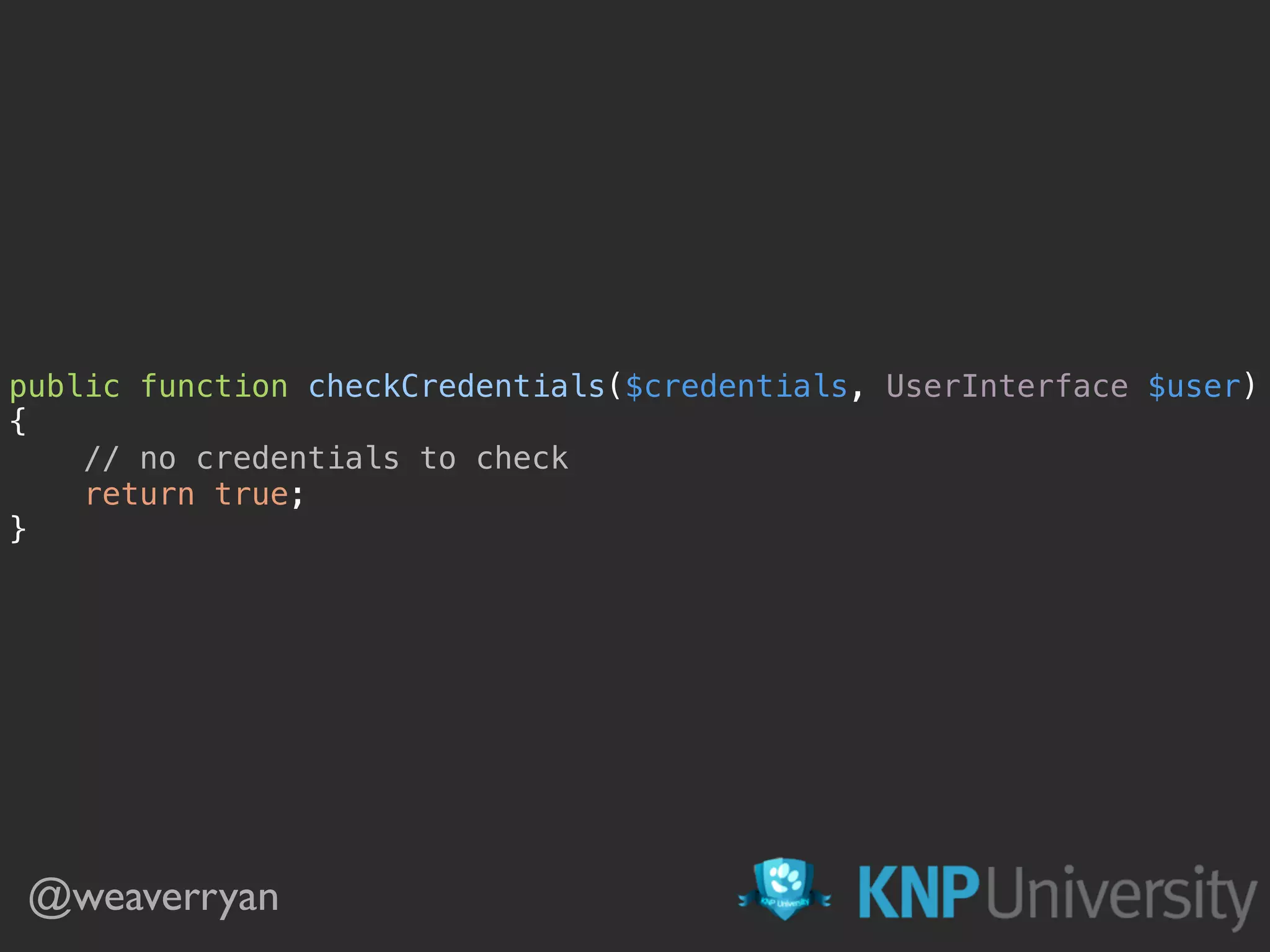
![public function checkCredentials($credentials, UserInterface $user)
{
$password = $credentials['password'];
if ($password == 'santa' || $password == 'elves') {
return;
}
return true;
} Are the credentials correct? @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-37-2048.jpg)
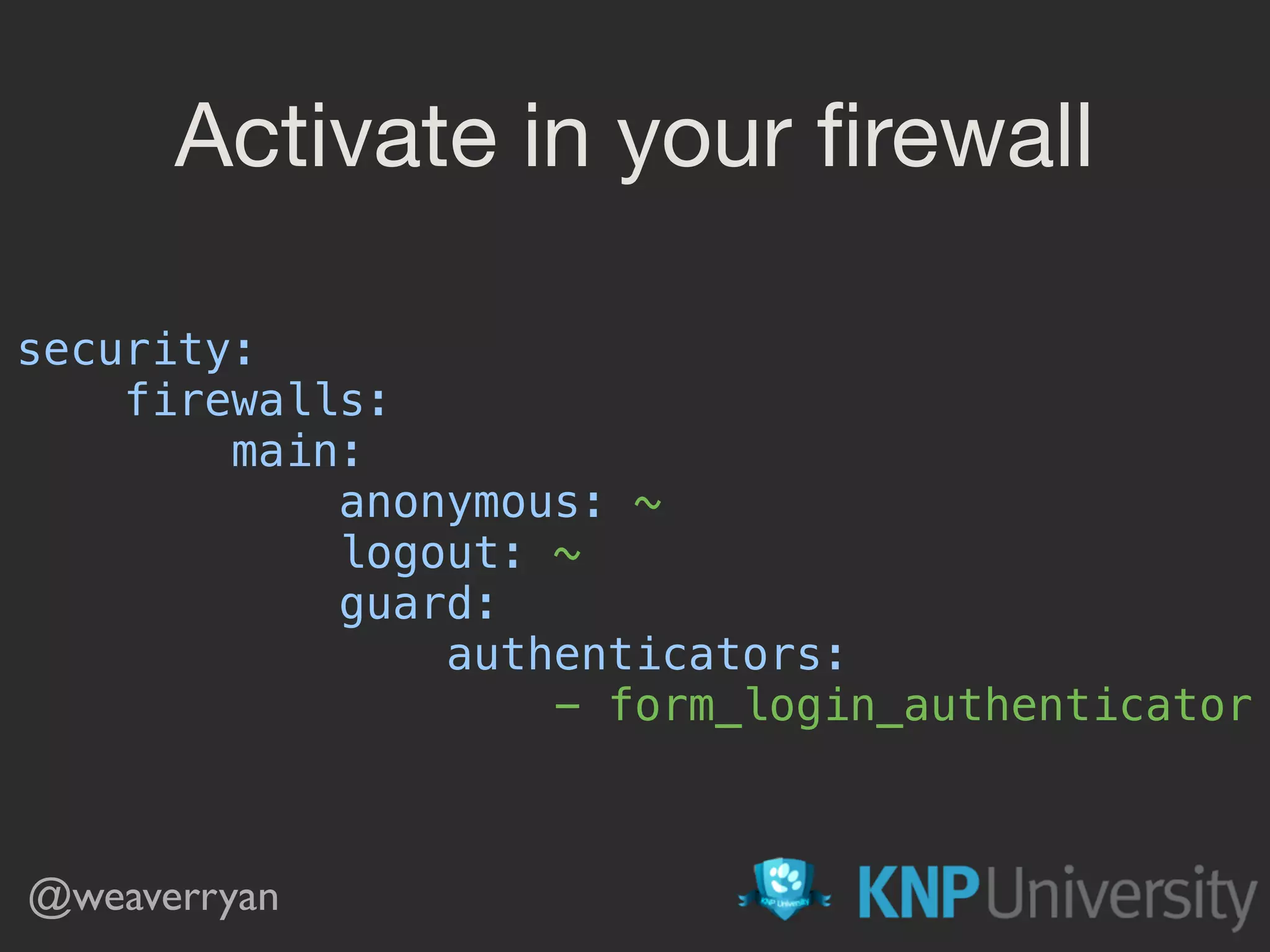

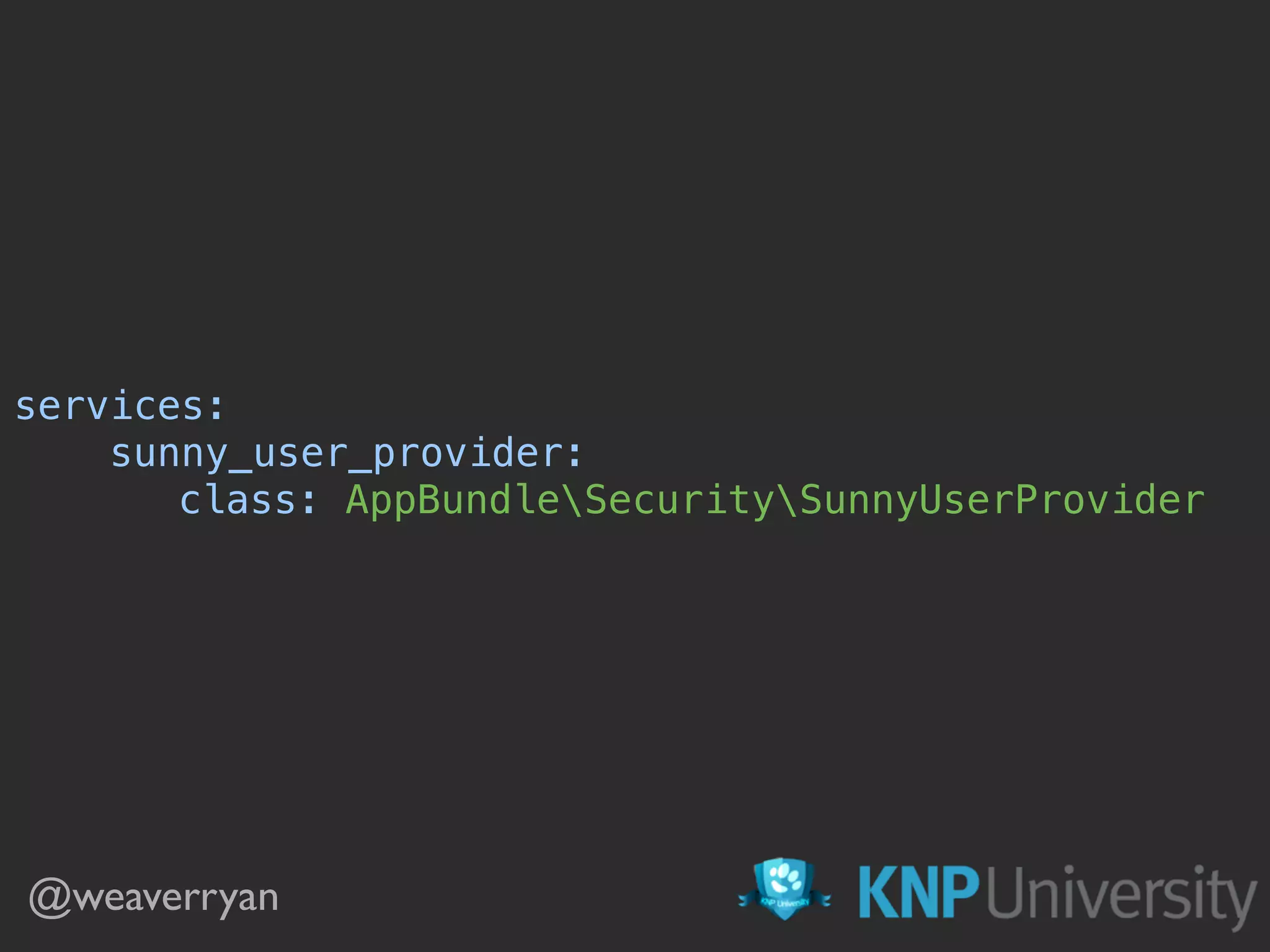
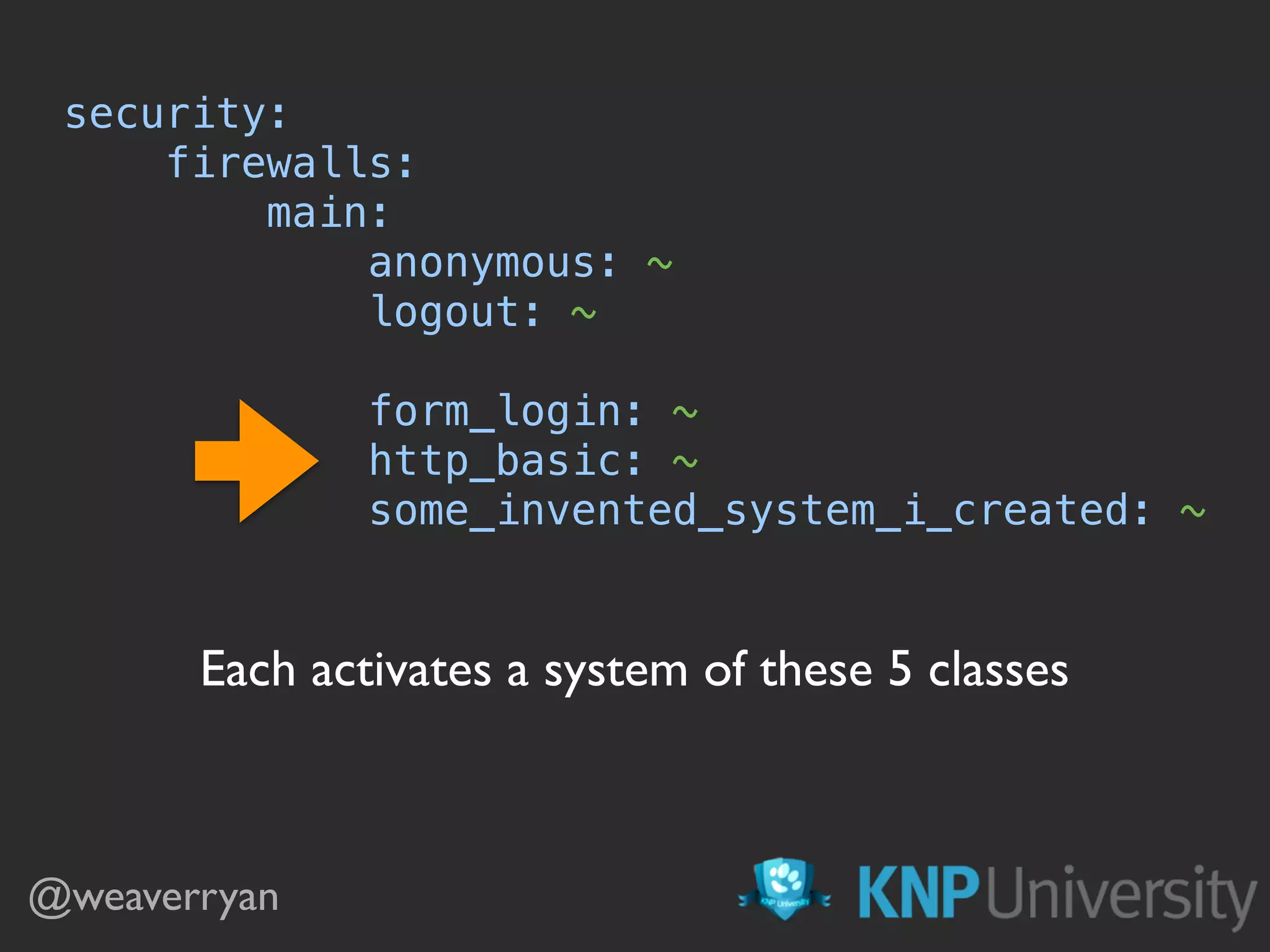
![security:
providers:
sunnny_users:
id: sunny_user_provider
firewalls:
main:
anonymous: ~
logout: ~
# this is optional as there is only 1 provider
provider: sunny_users
guard:
authenticators: [form_login_authenticator]
Boom! Optional Boom!](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-48-2048.jpg)

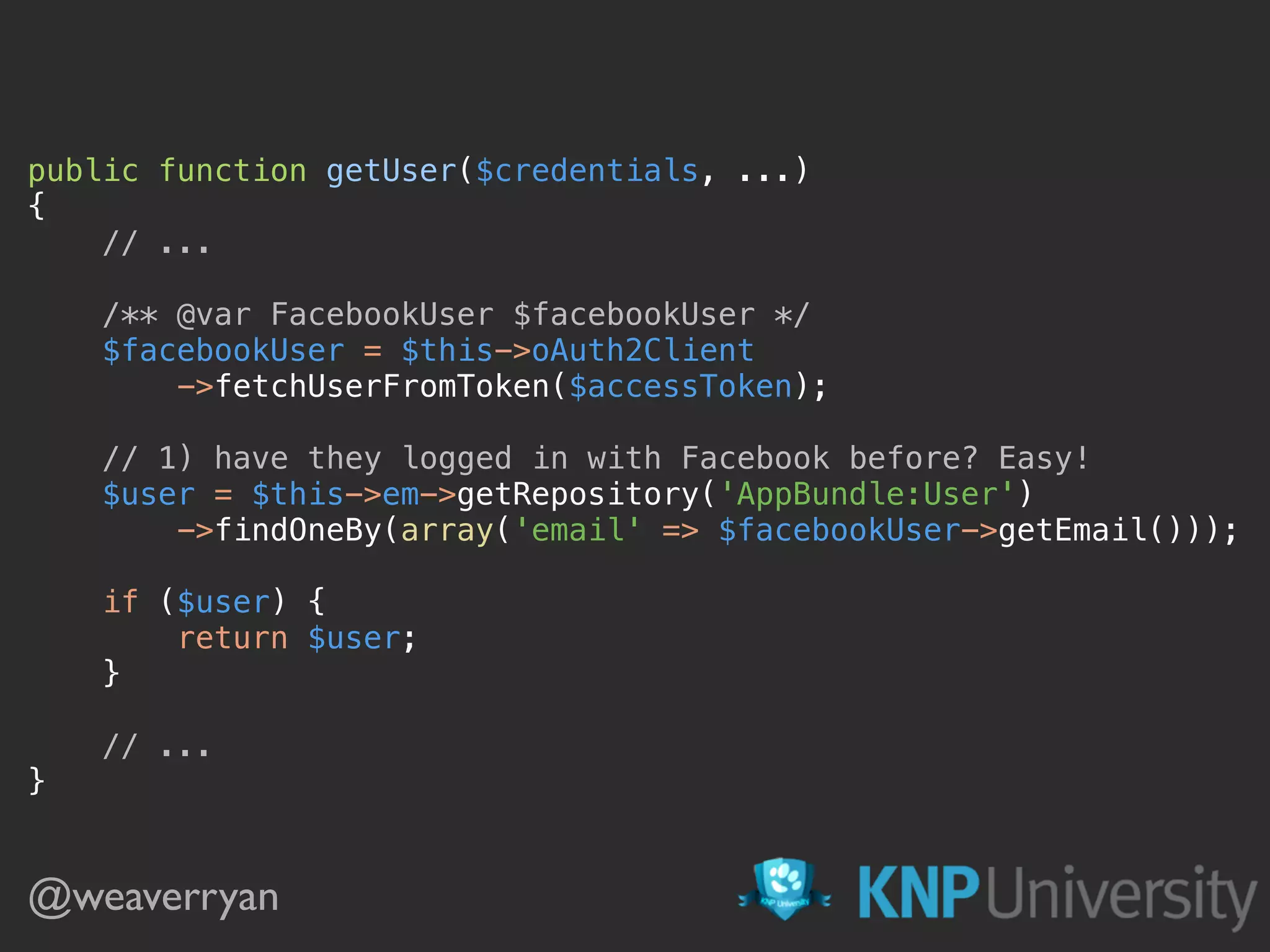
![public function getUser($credentials, UserProviderInterface $userProvider)
{
$username = $credentials['username'];
//return $userProvider->loadUserByUsername($username);
return $this->em
->getRepository('AppBundle:User')
->findOneBy(['username' => $username]);
} FormLoginAuthenticator you can use this if you want to … or don’t!](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-53-2048.jpg)
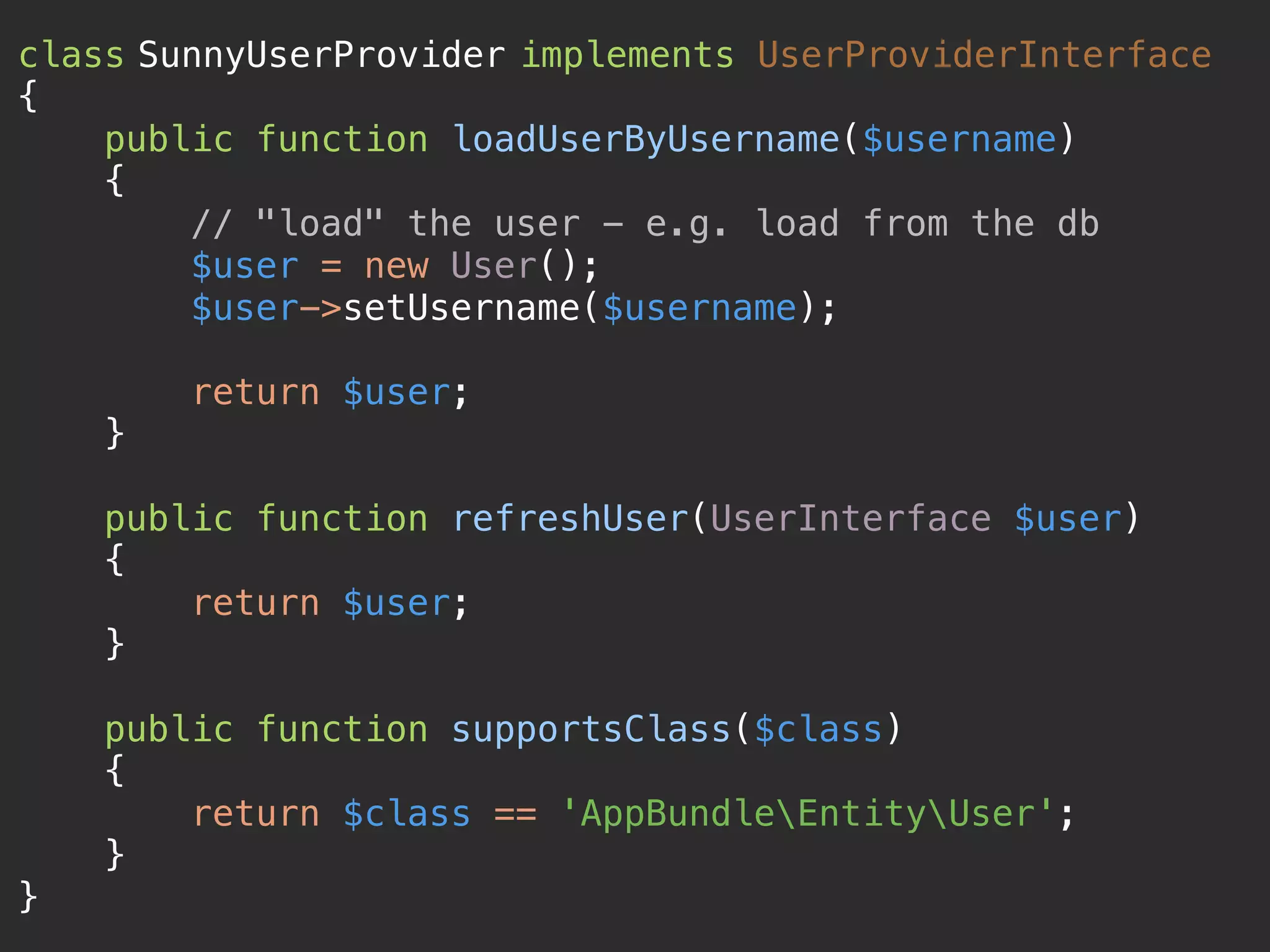
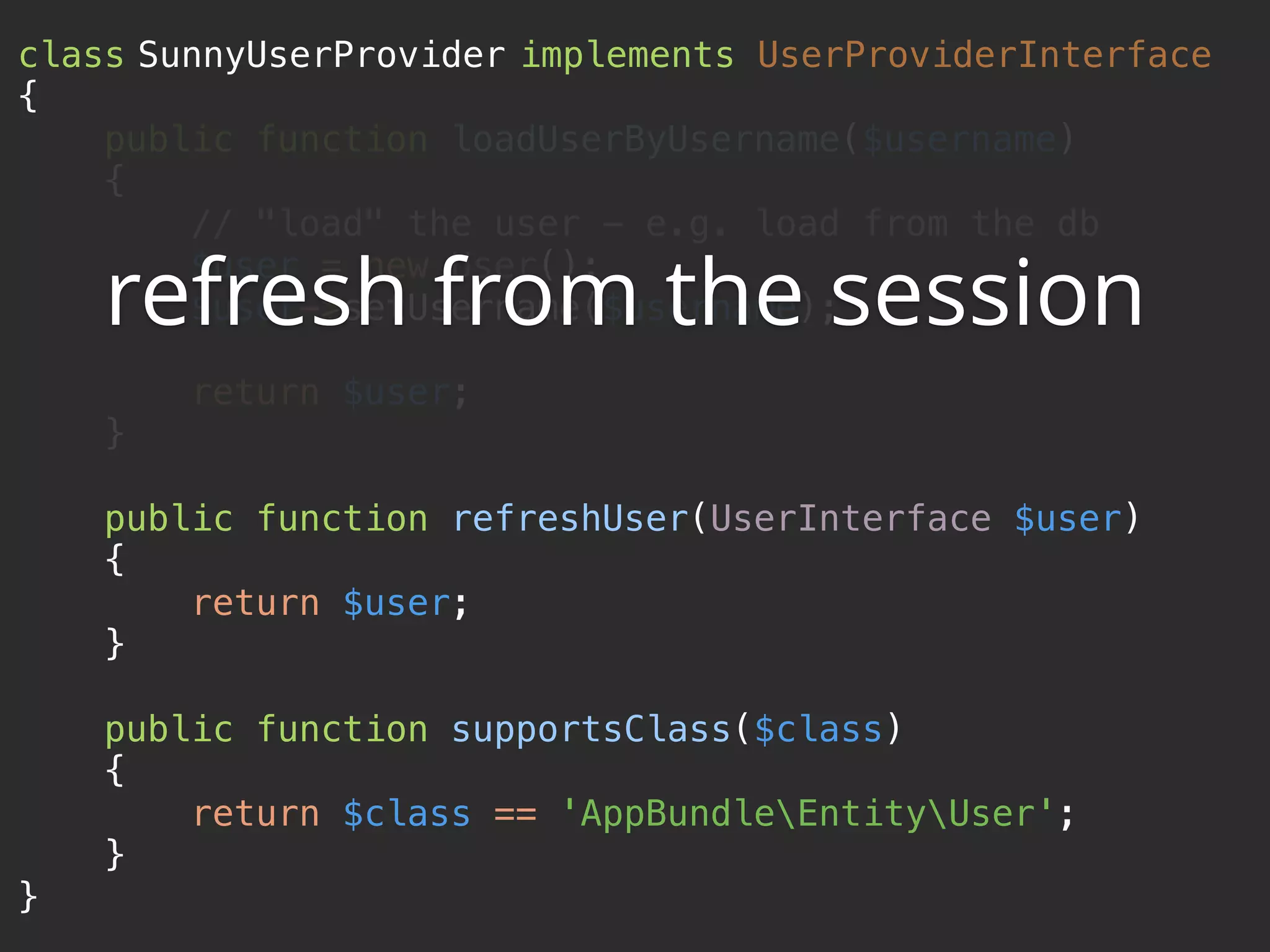
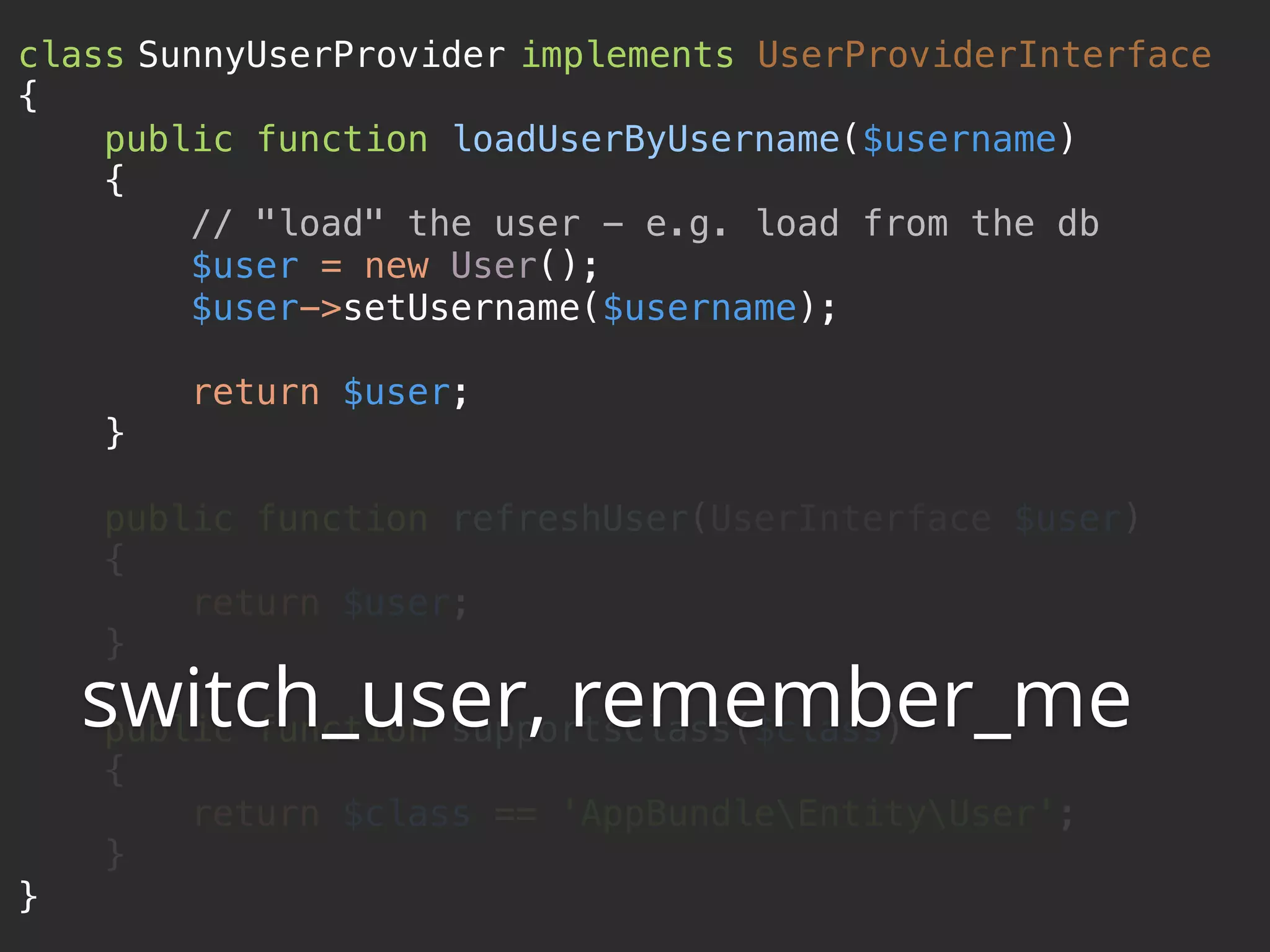
![class SunnyUserProvider implements UserProviderInterface
{
public function loadUserByUsername($username)
{
$user = $this->em->getRepository('AppBundle:User')
->findOneBy(['username' => $username]);
if (!$user) {
throw new UsernameNotFoundException();
}
return $user;
}
} @weaverryan (of course, the “entity” user provider does this automatically)](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-54-2048.jpg)

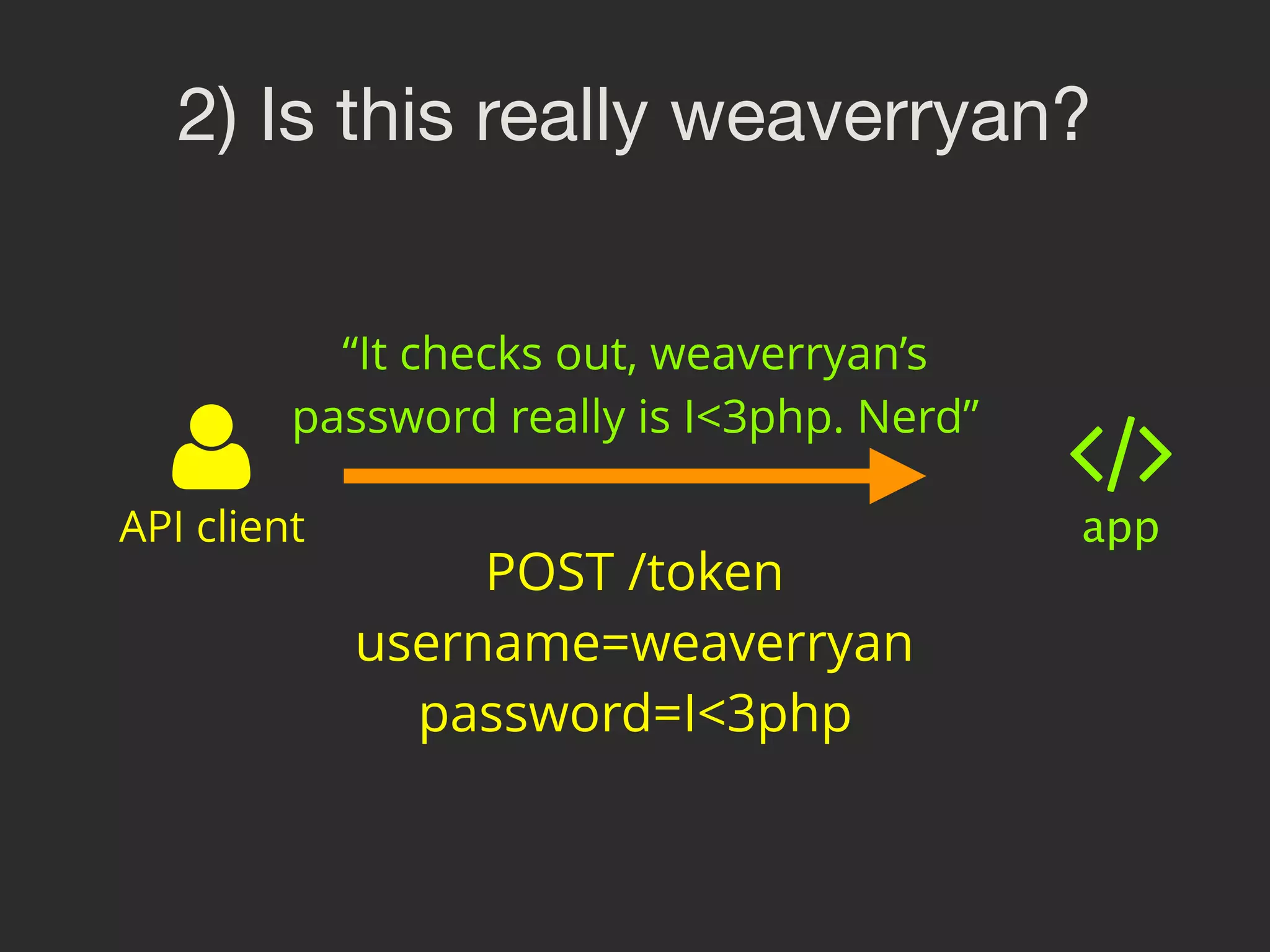
![3) Create a package of data API client app $data = [
'username' => 'weaverryan'
];](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-59-2048.jpg)
![4) Sign the data! $data = [
'username' => 'weaverryan'
];
// package: namshi/jose
$jws = new SimpleJWS(['alg' => 'RS256']);
$jws->setPayload($data);
$privateKey = openssl_pkey_get_private(
'file://path/to/private.key'
);
$jws->sign($privateKey);
$token = $jws->getTokenString()](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-60-2048.jpg)
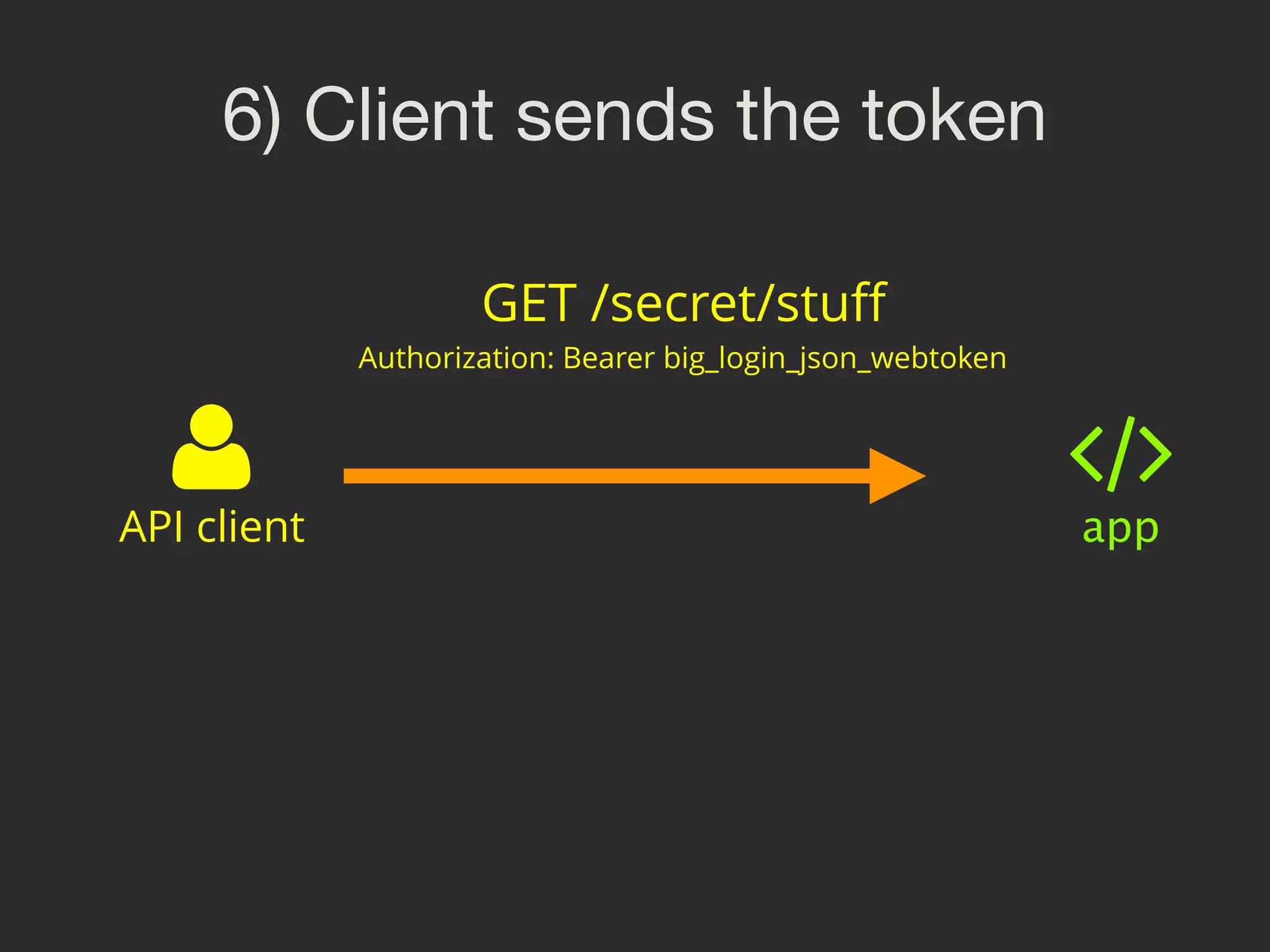
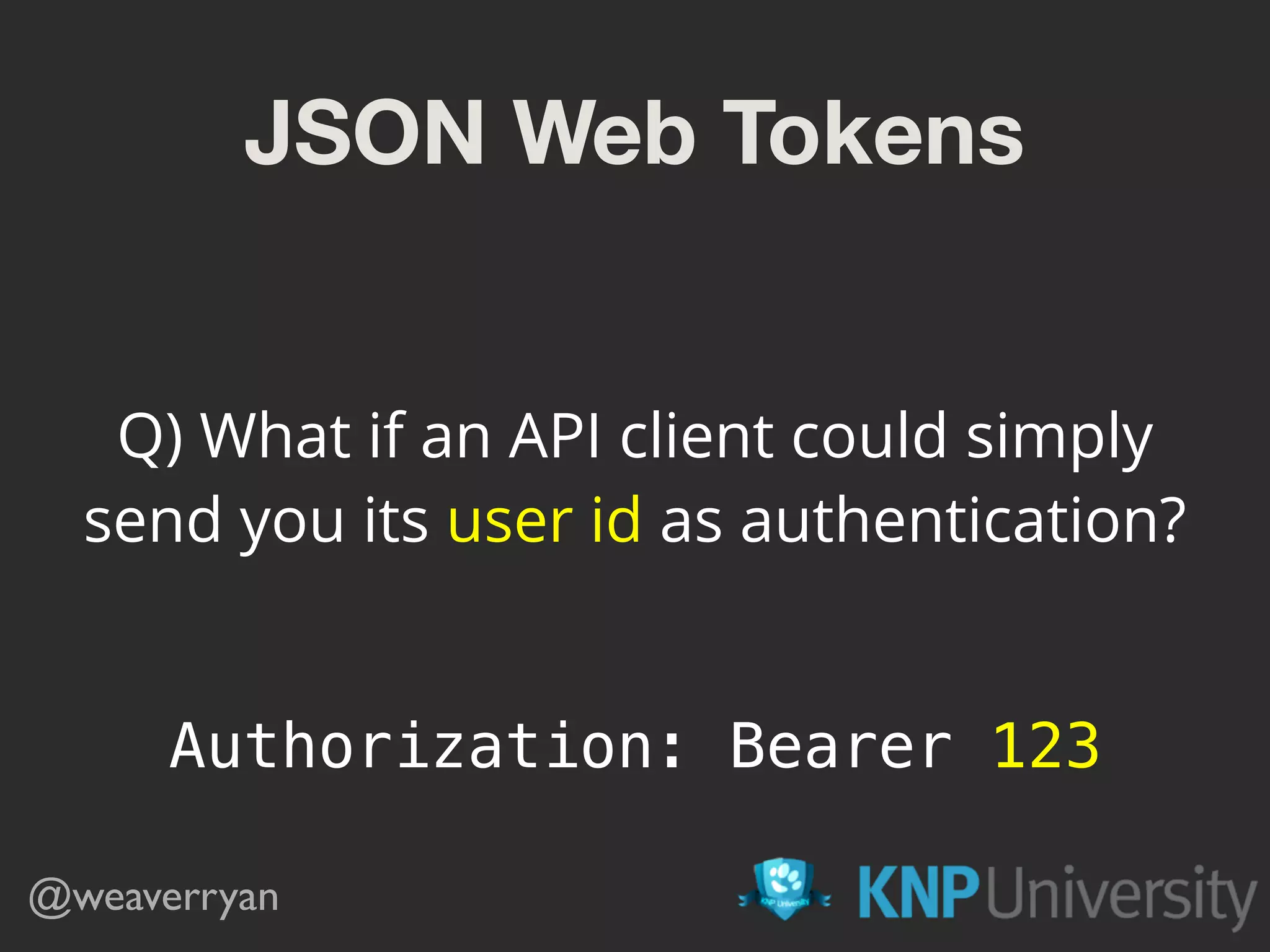
![7) Verify the signature // "Authorization: Bearer 123" -> "123"
$authHeader = $request->headers->get('Authorization'); $headerParts = explode(' ', $authHeader);
$token = $headerParts[1];
$jws = SimpleJWS::load($token);
$public_key = openssl_pkey_get_public(
'/path/to/public.key'
);
if (!$jws->isValid($public_key, 'RS256')) {
die('go away >:(')
}](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-63-2048.jpg)
![8) Decode the token
$payload = $jws->getPayload();
$username = $payload['username'];](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-64-2048.jpg)


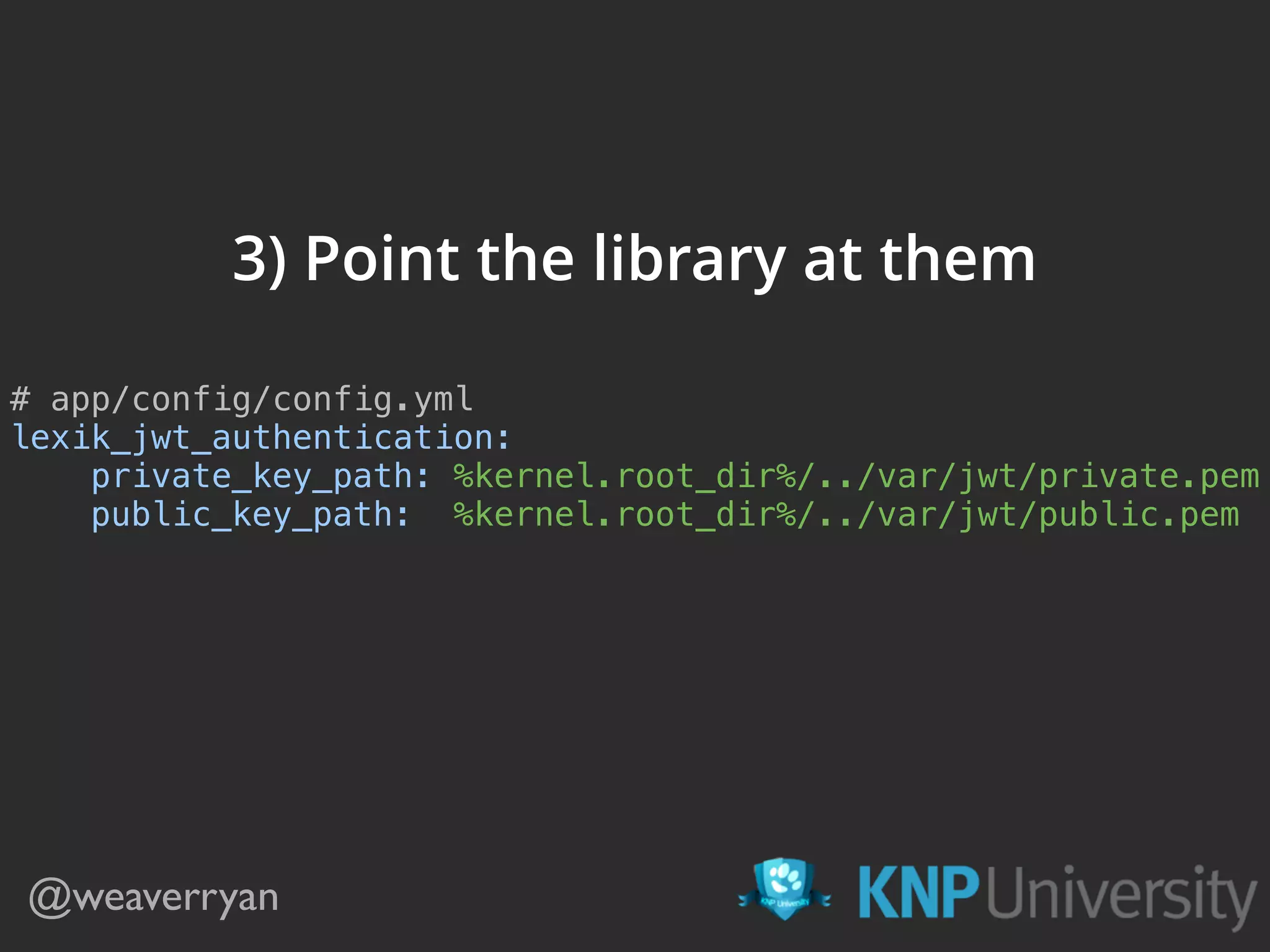
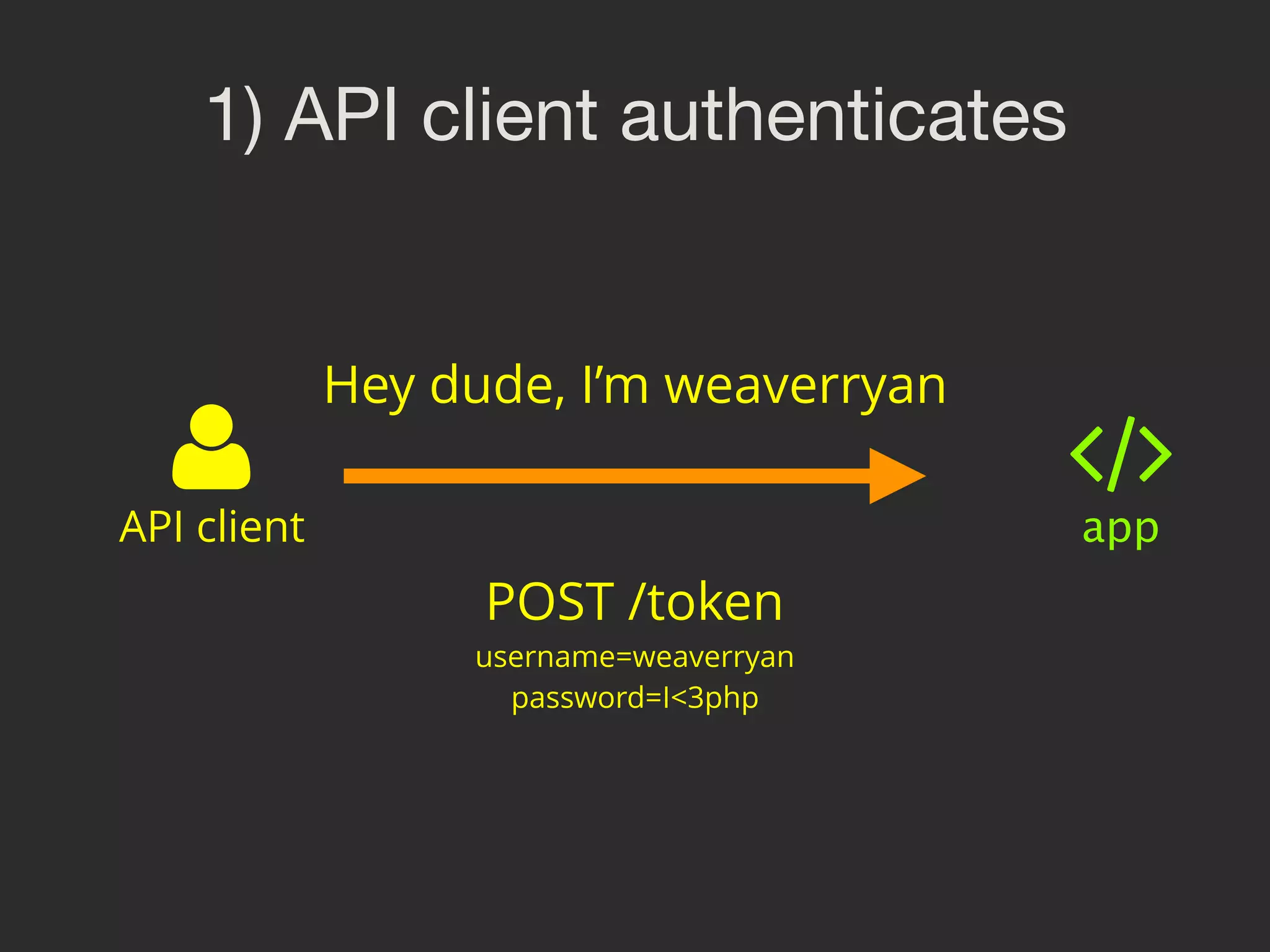
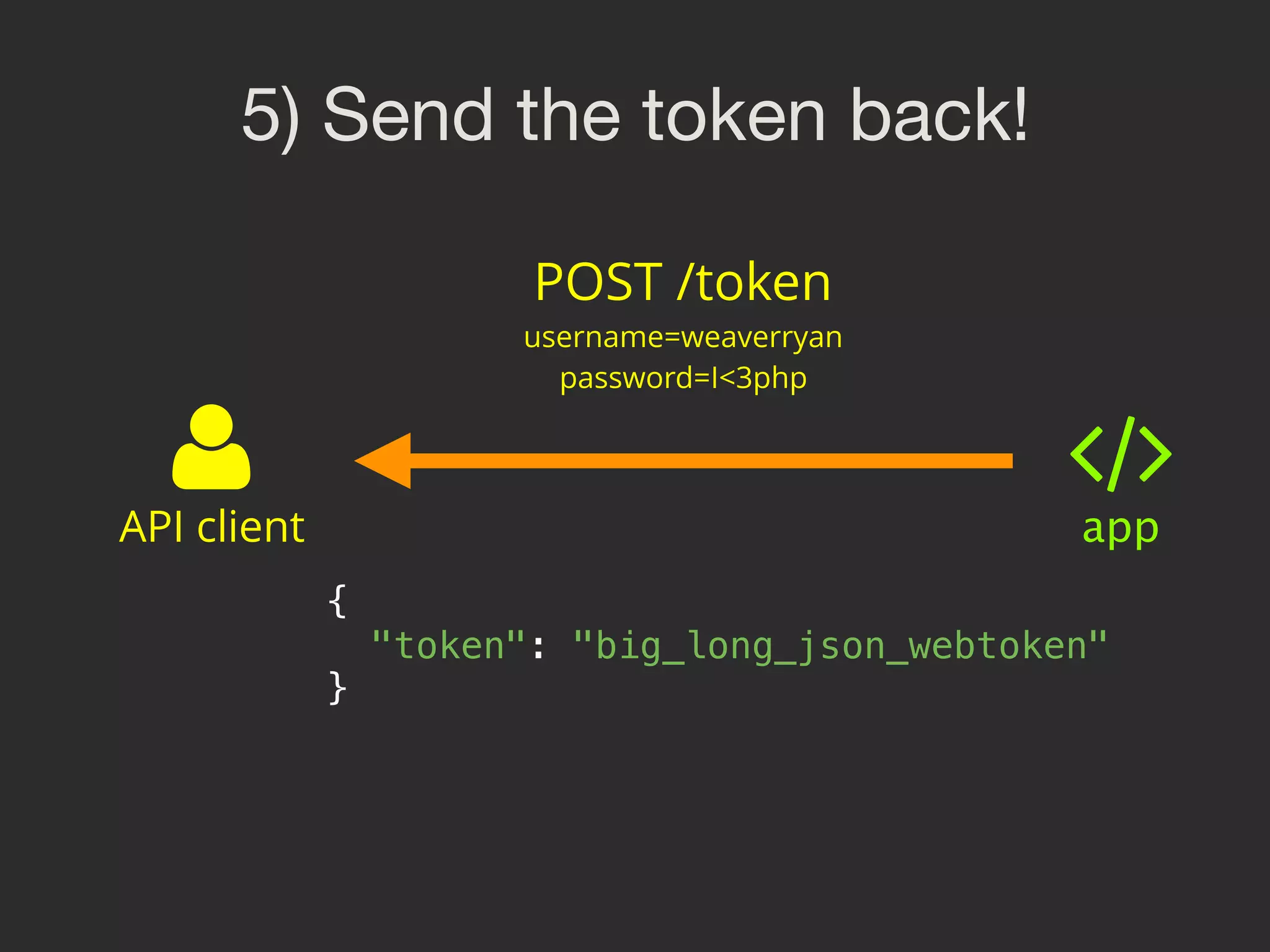
![4) Endpoint to return tokens /**
* @Route("/token")
*/
public function fetchToken(Request $request)
{
$username = $request->request->get('username');
$password = $request->request->get('password');
$user = $this->getDoctrine()
->getRepository('AppBundle:User')
->findOneBy(['username' => $username]);
if (!$user) {
throw $this->createNotFoundException();
}
// check password
$token = $this->get('lexik_jwt_authentication.encoder')
->encode(['username' => $user->getUsername()]);
return new JsonResponse(['token' => $token]);
}](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-69-2048.jpg)

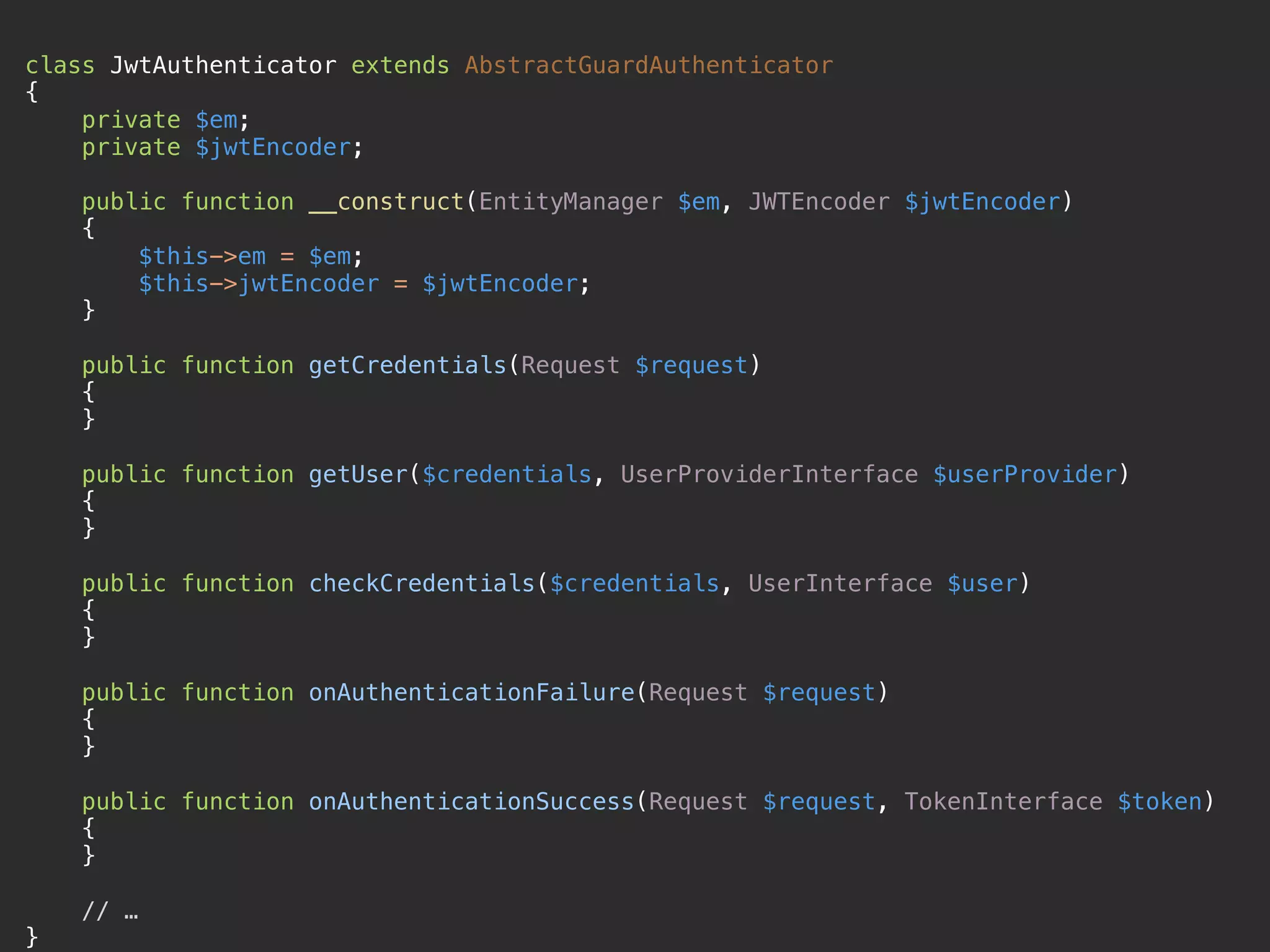
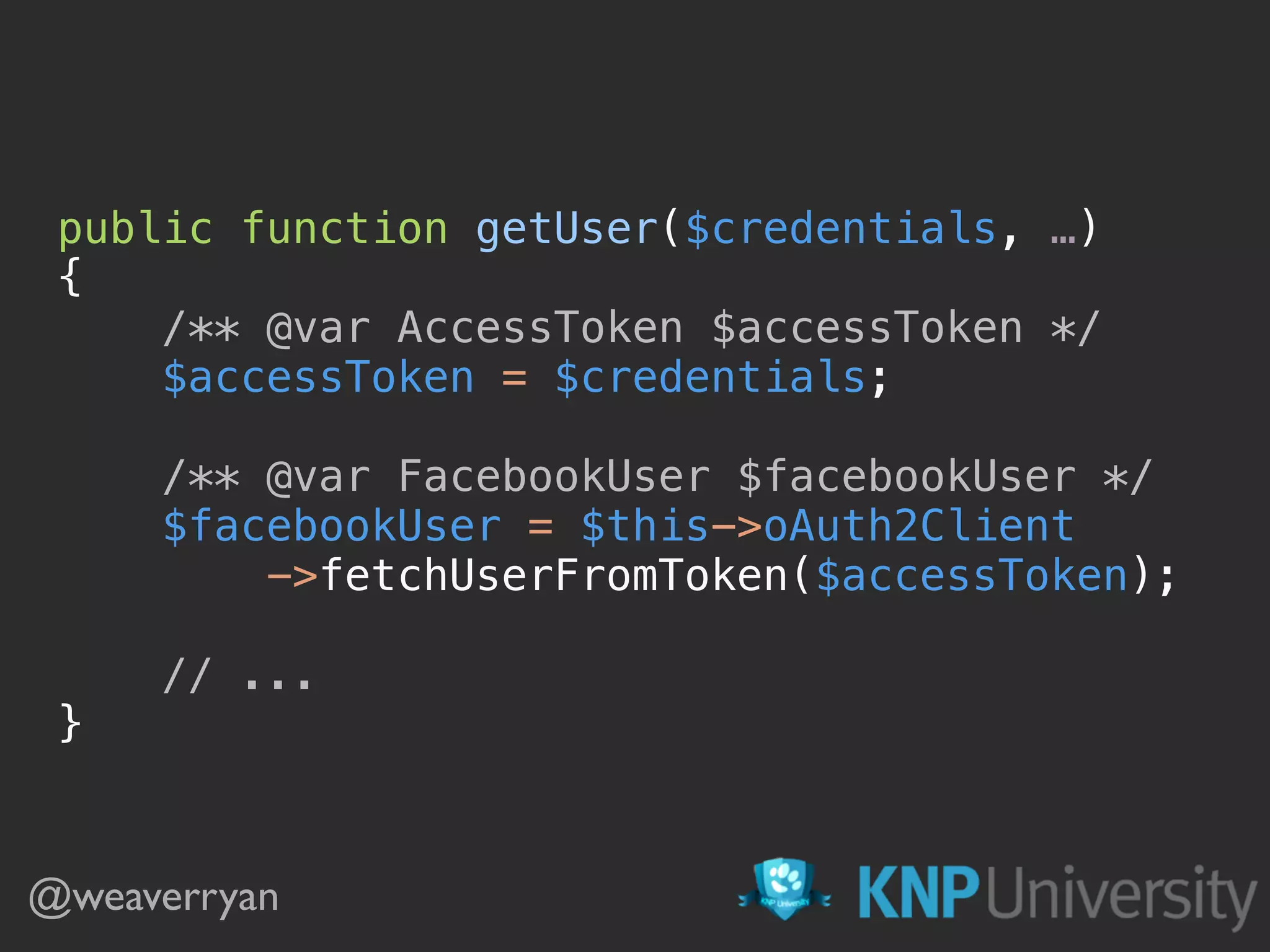
![public function getUser($credentials, UserProviderInterface $userProvider)
{
$data = $this->jwtEncoder->decode($credentials);
if (!$data) {
return;
}
$username = $data['username'];
return $this->em
->getRepository('AppBundle:User')
->findOneBy(['username' => $username]);
} @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-73-2048.jpg)
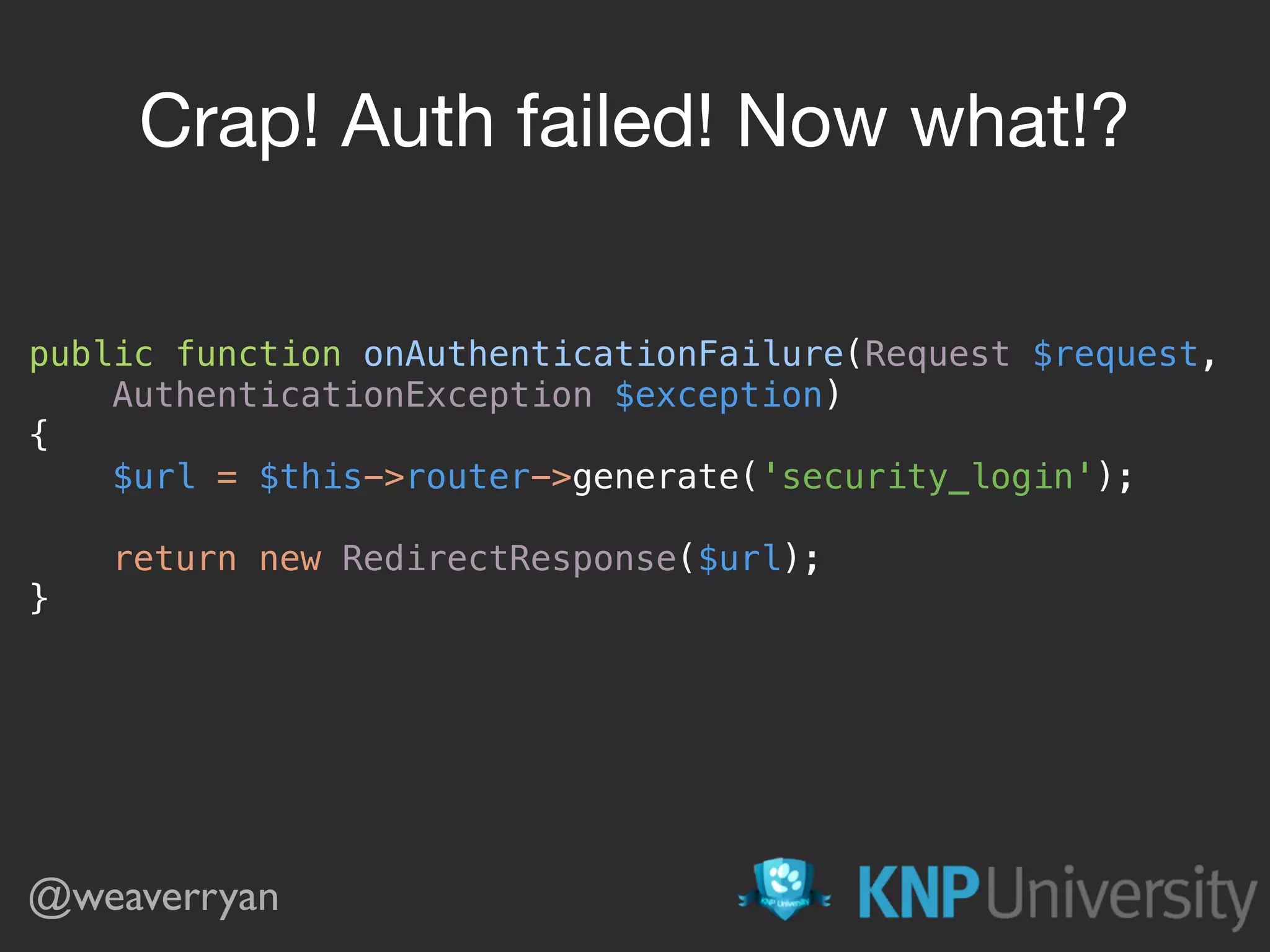
![public function onAuthenticationFailure(Request $request, AuthenticationException $exception)
{
return new JsonResponse([
'message' => $exception->getMessageKey()
], 401);
} @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-75-2048.jpg)
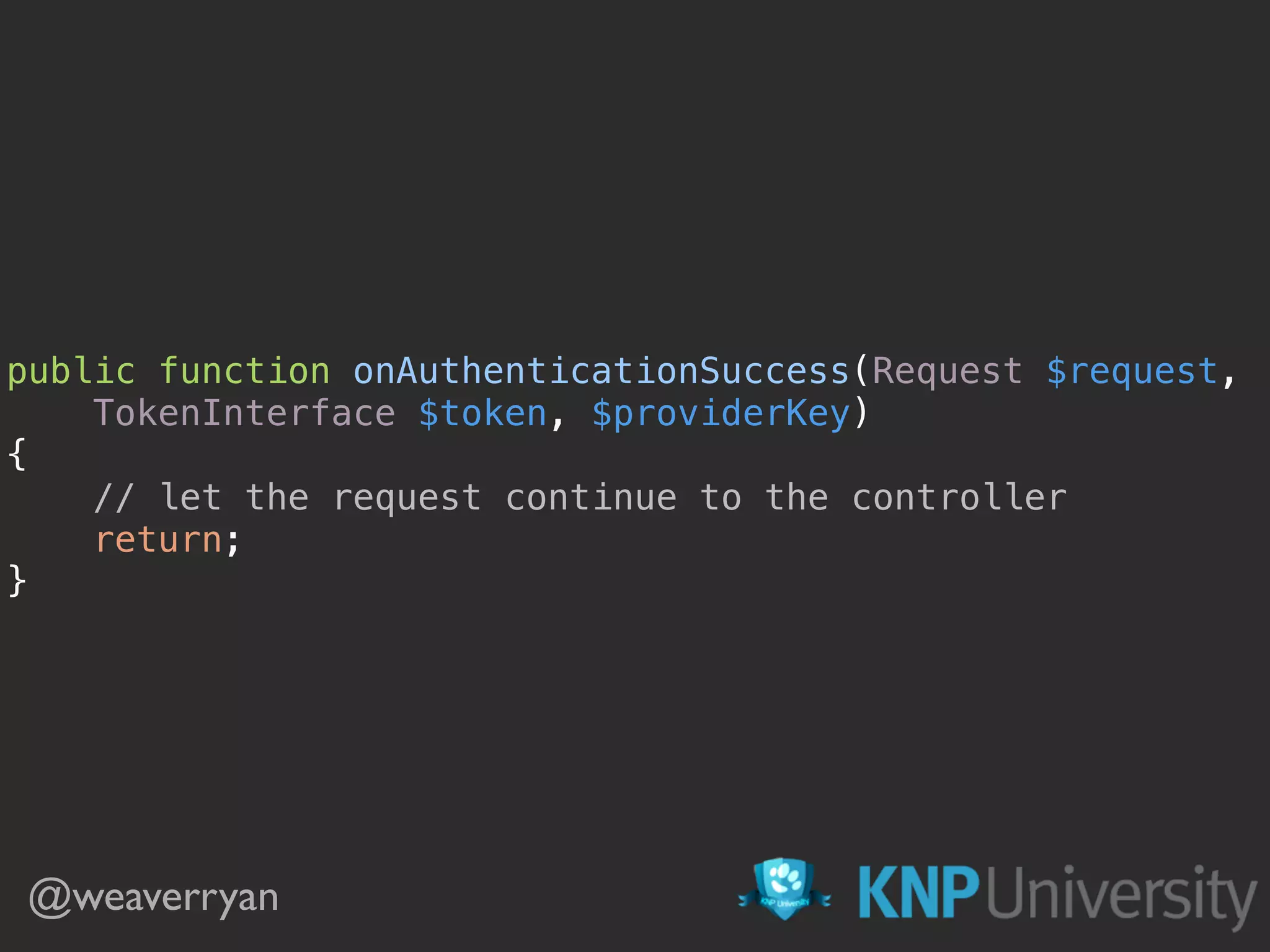
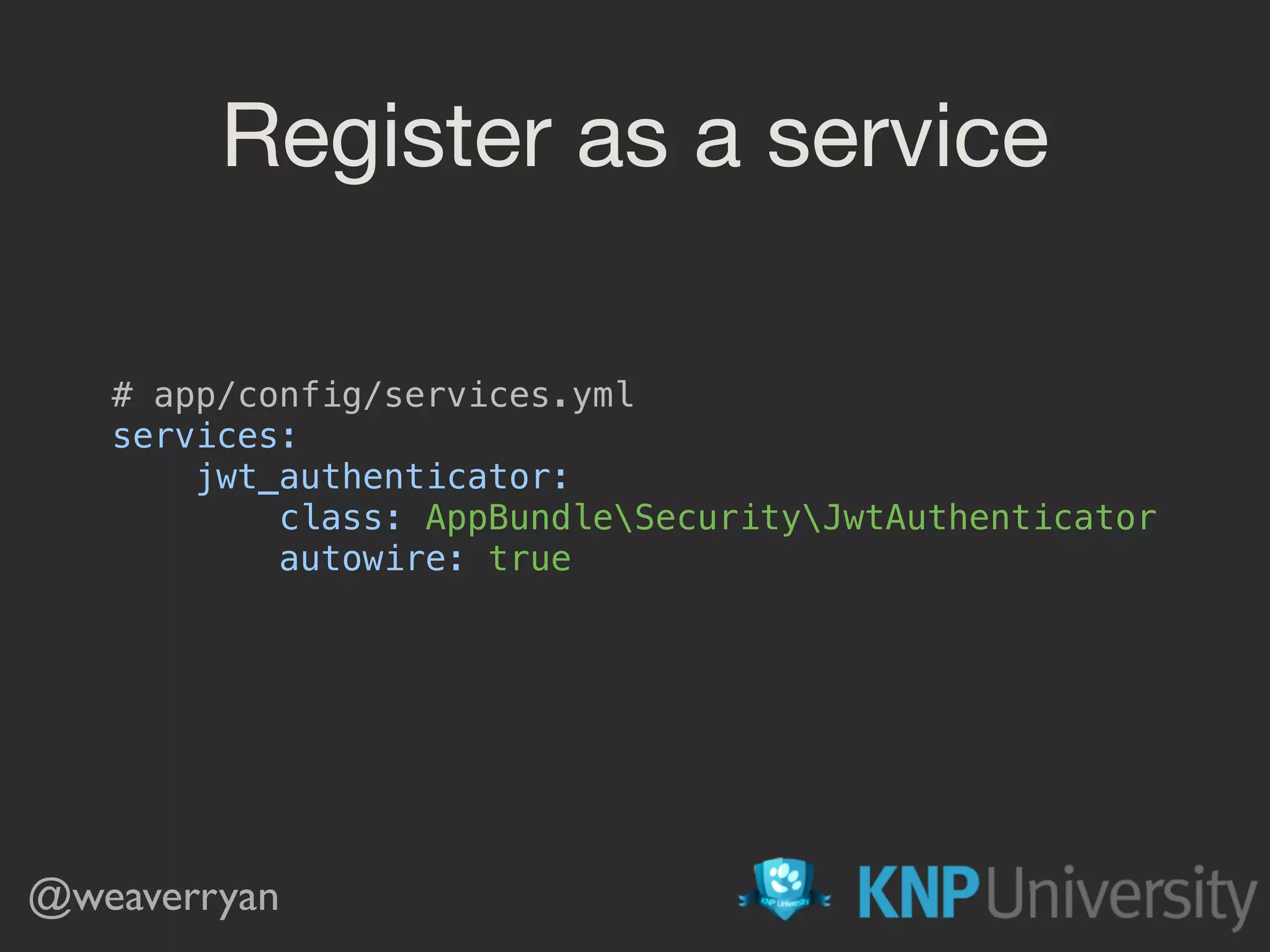
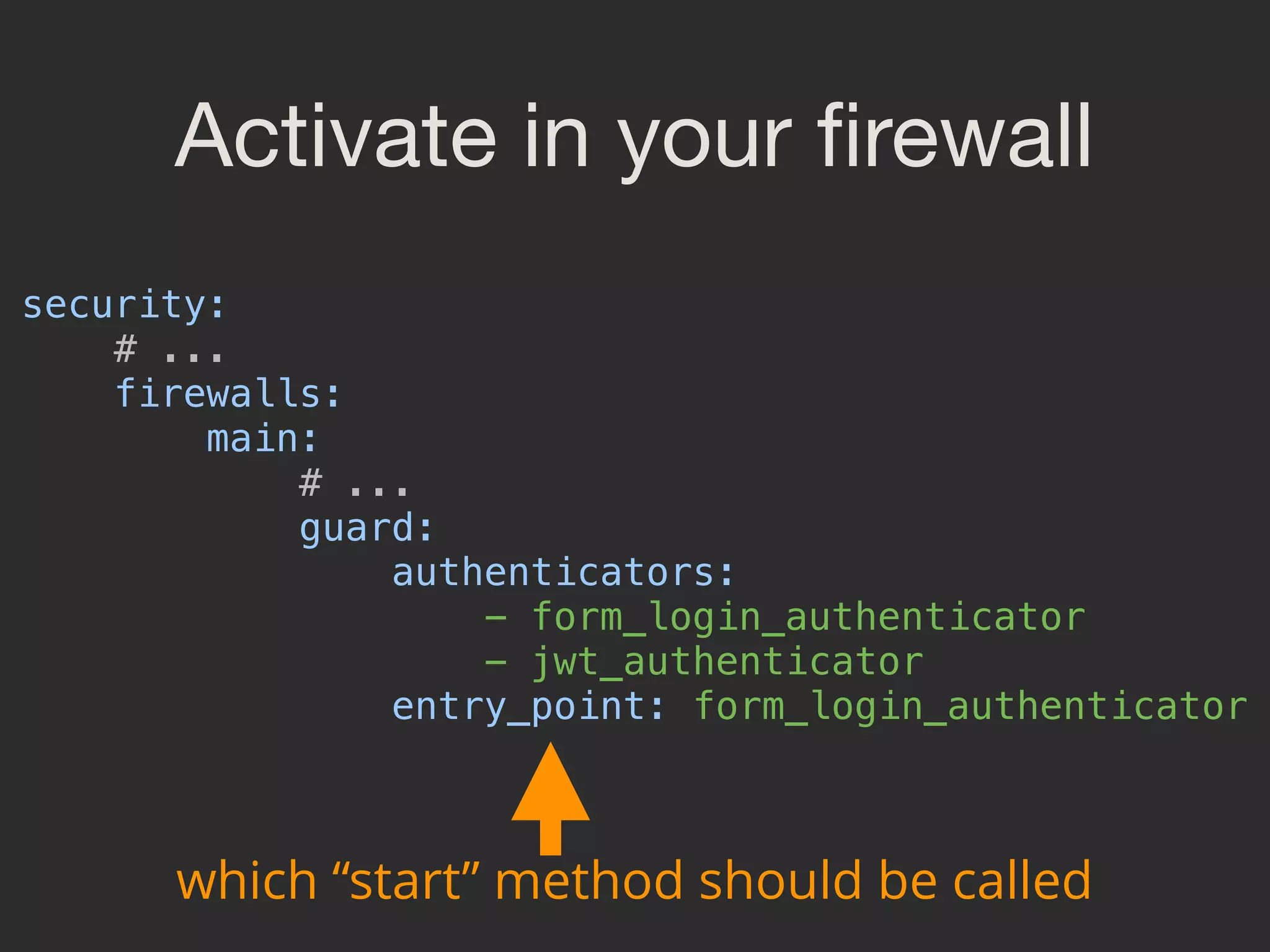
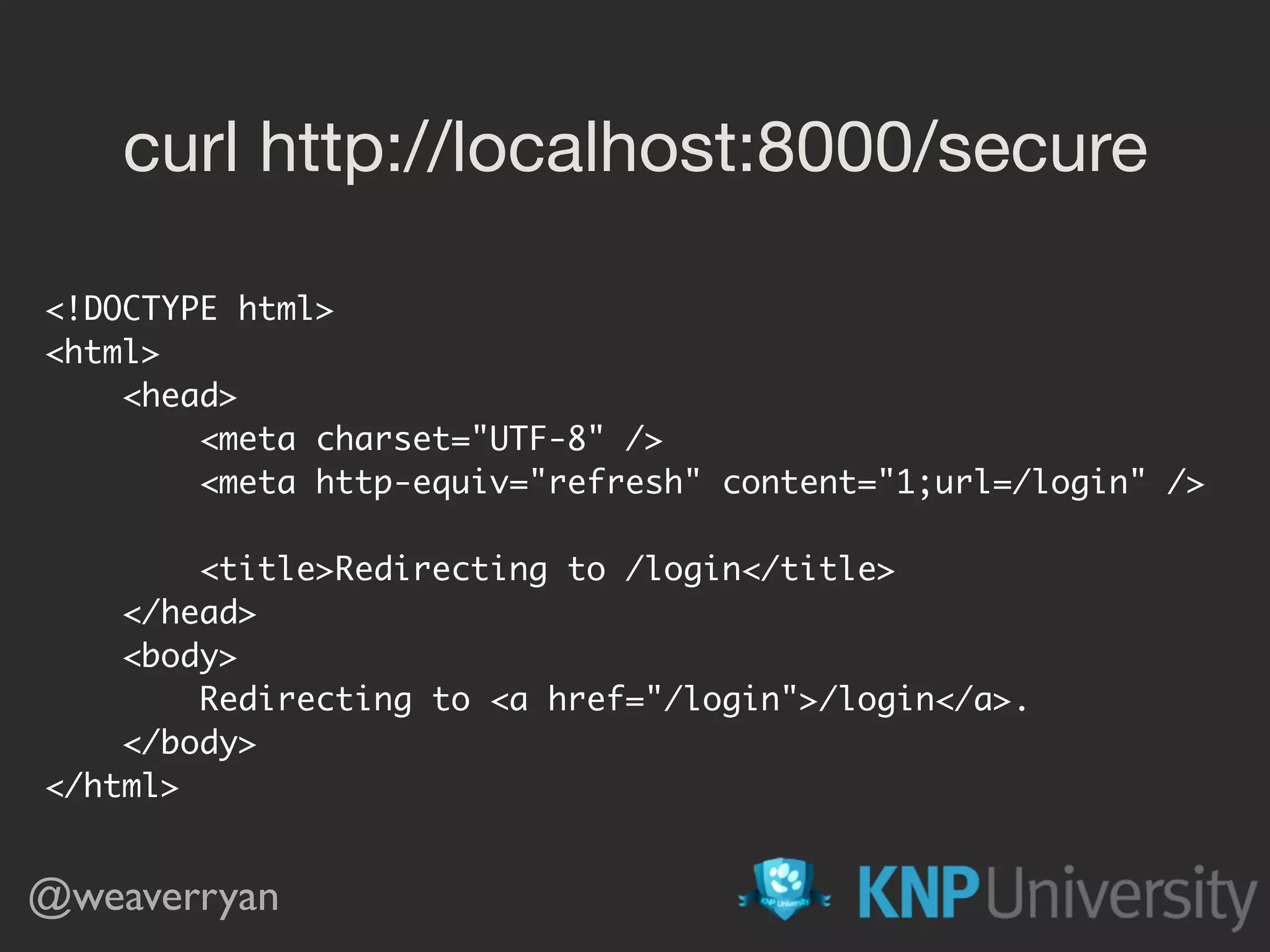


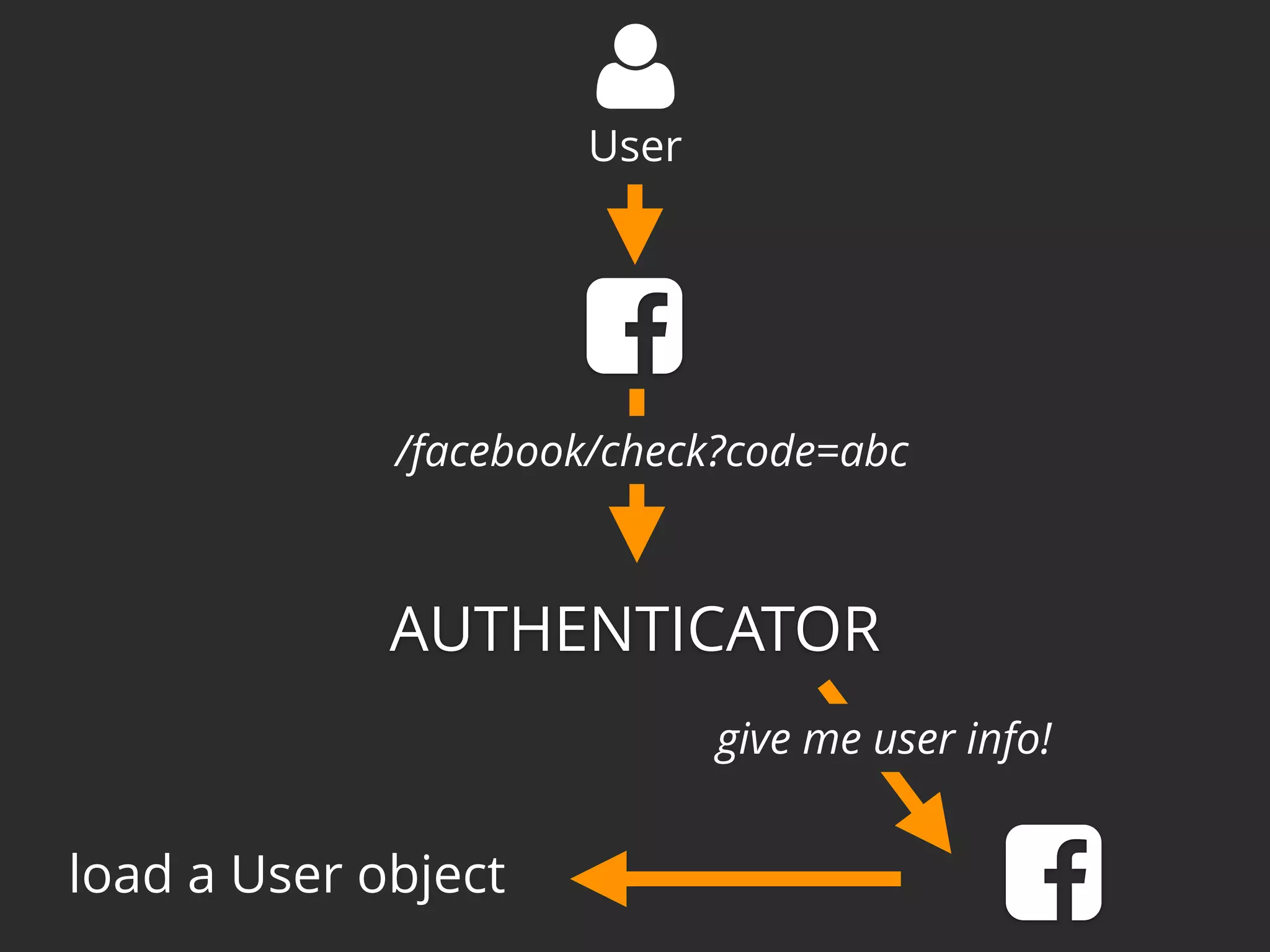

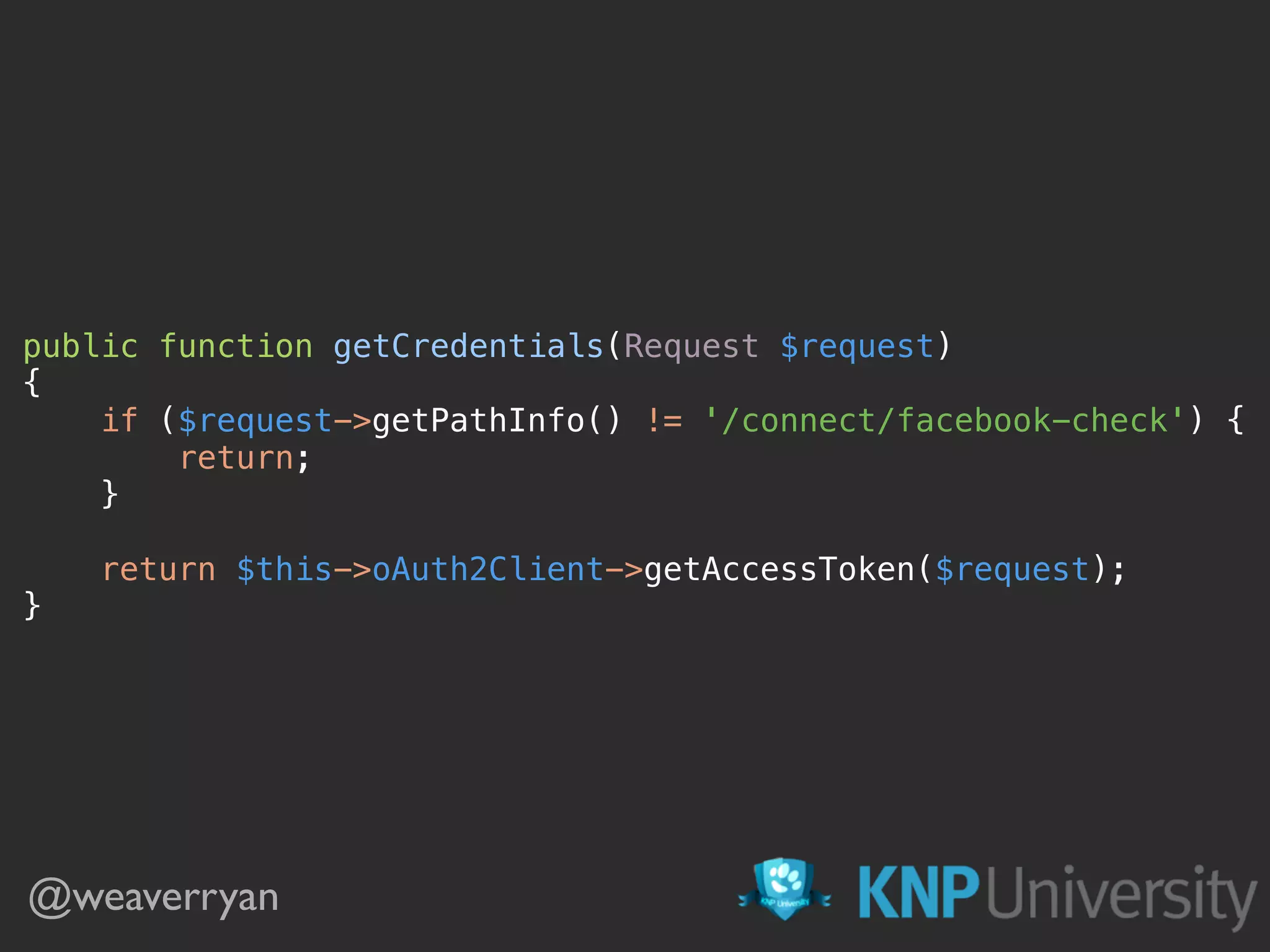
![@weaverryan /**
* @Route("/connect/facebook", name="connect_facebook")
*/
public function connectFacebookAction()
{
return $this->get('knpu.oauth2.client.facebook')
->redirect(['public_profile', 'email']);
}
/**
* @Route("/connect/facebook-check", name="connect_facebook_check")
*/
public function connectFacebookActionCheck()
{
// will not be reached!
}](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-86-2048.jpg)





![public function onAuthenticationFailure(Request $request, AuthenticationException $exception)
{
return new JsonResponse([
'message' => $exception->getMessageKey()
], 401);
} @weaverryan Beach Vacation Bonus! The exception is passed when authentication fails AuthenticationException has a hardcoded getMessageKey() “safe” string Invalid credentials.](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-98-2048.jpg)
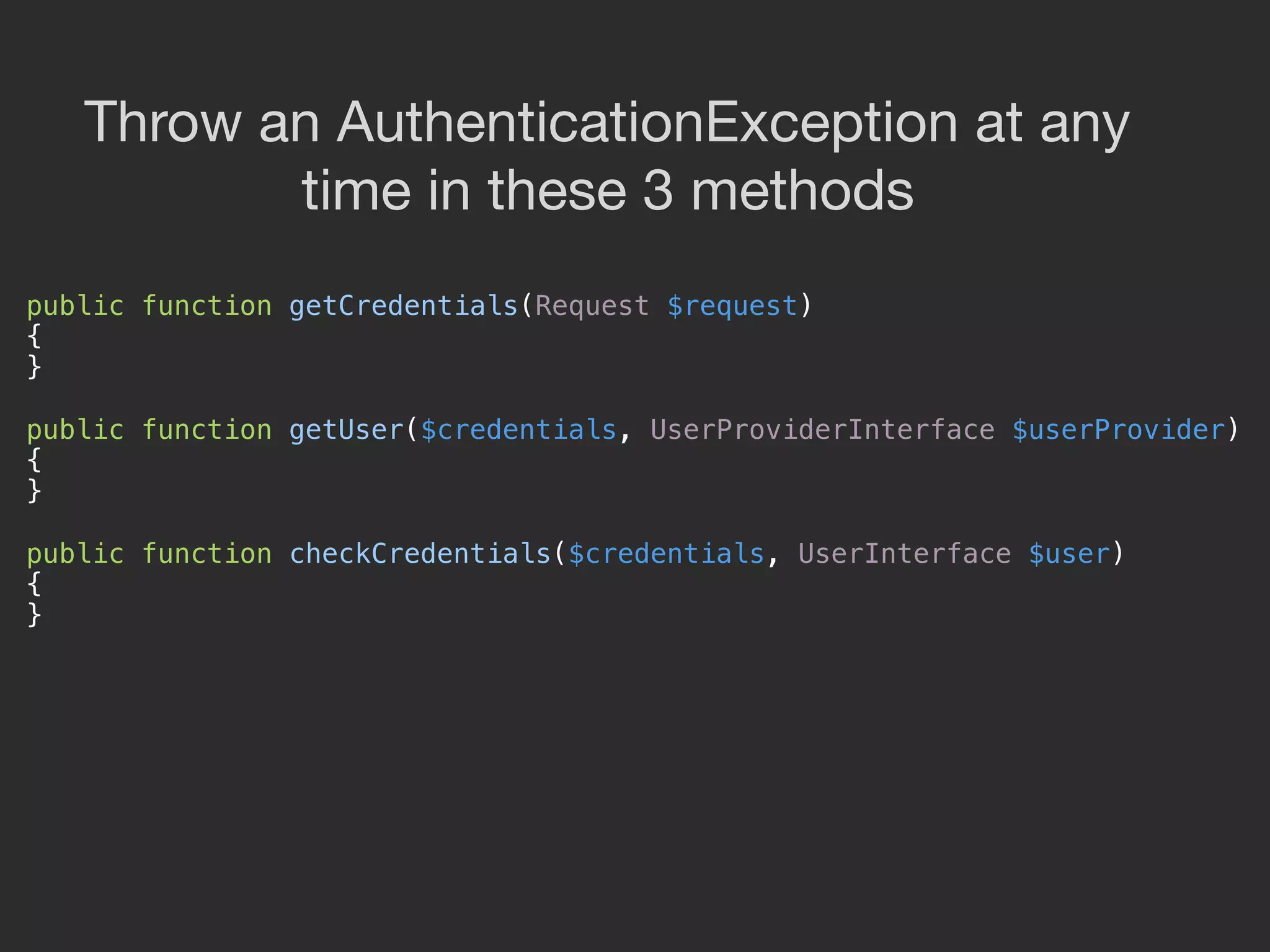
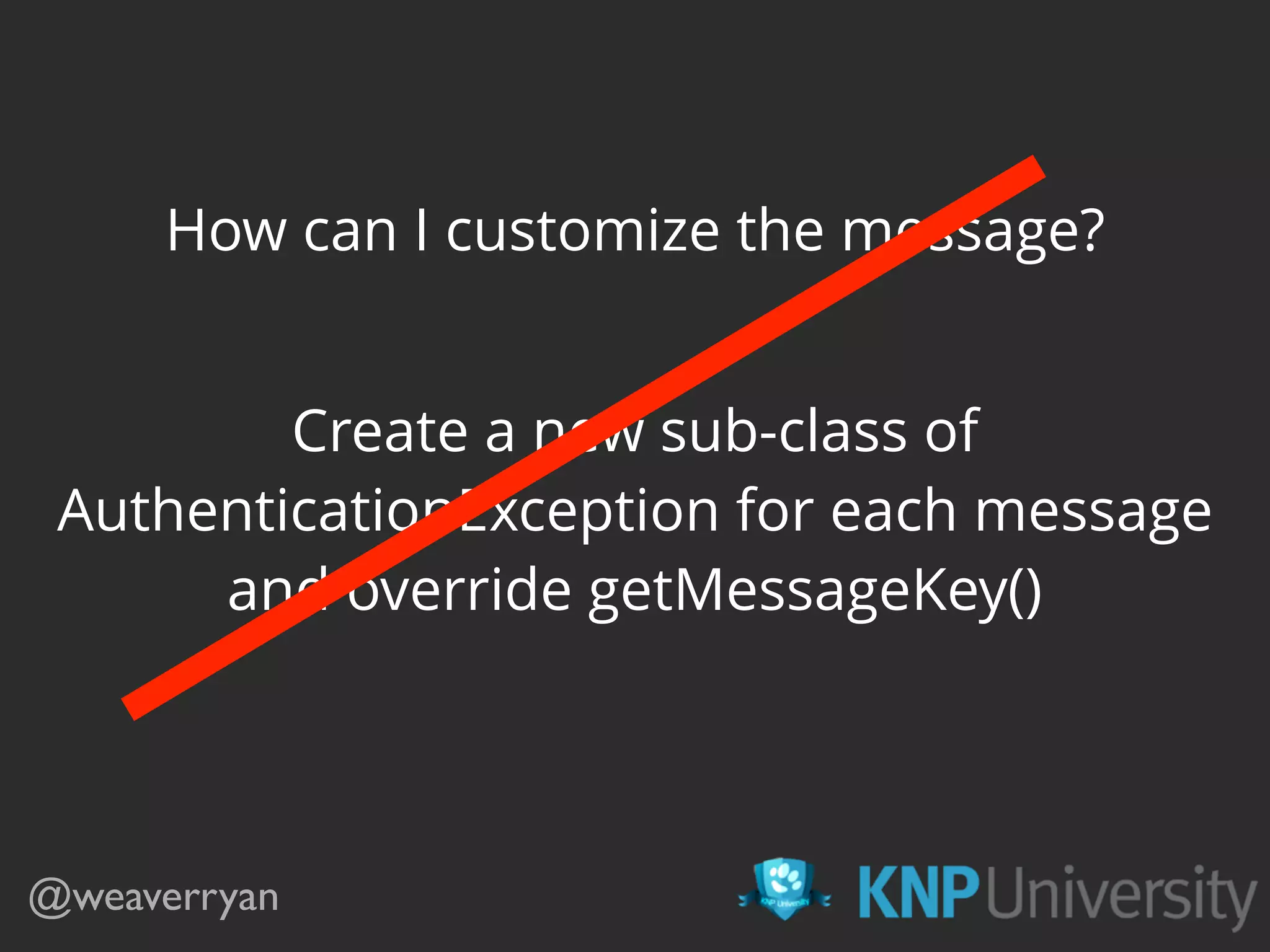
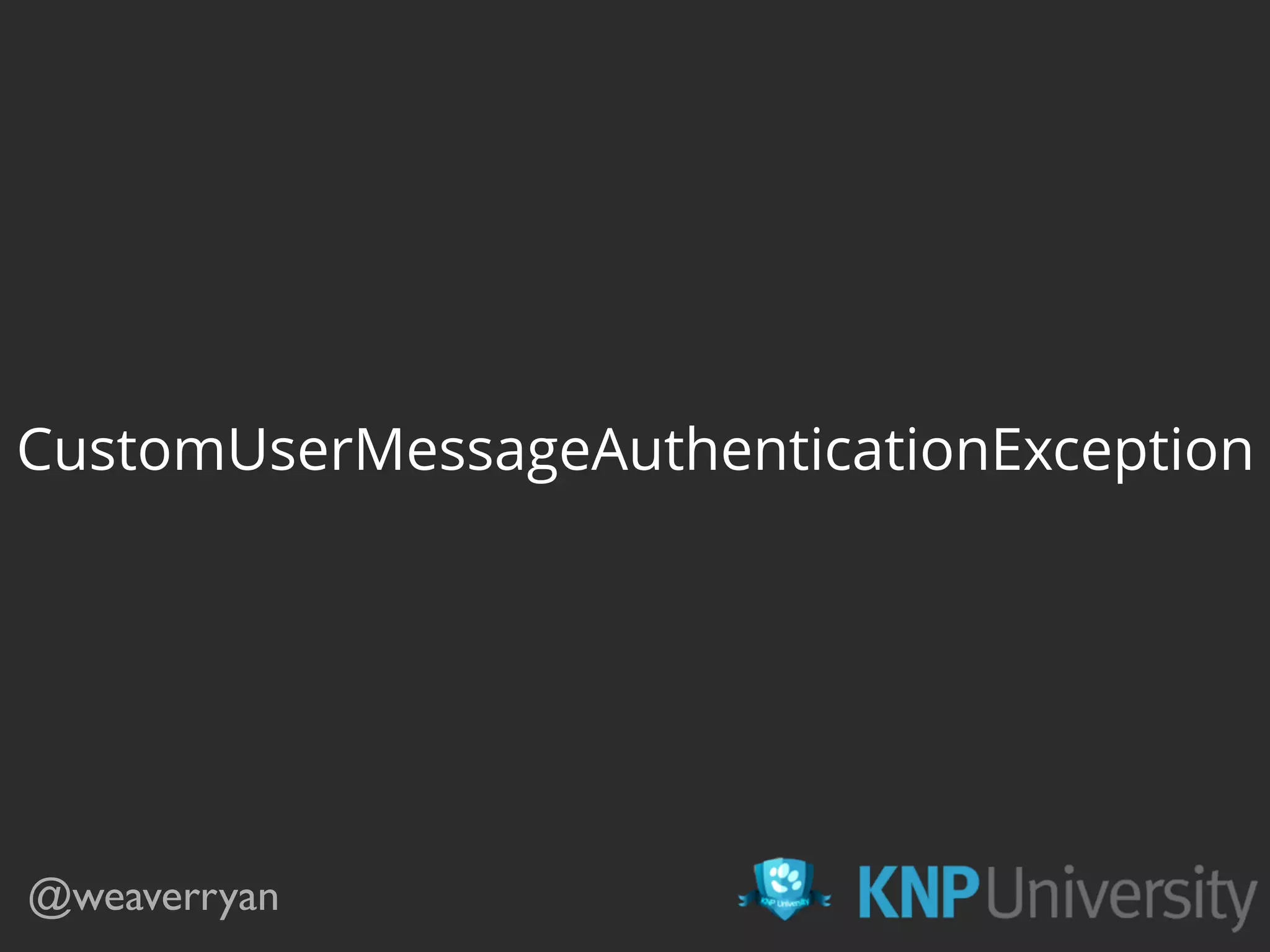
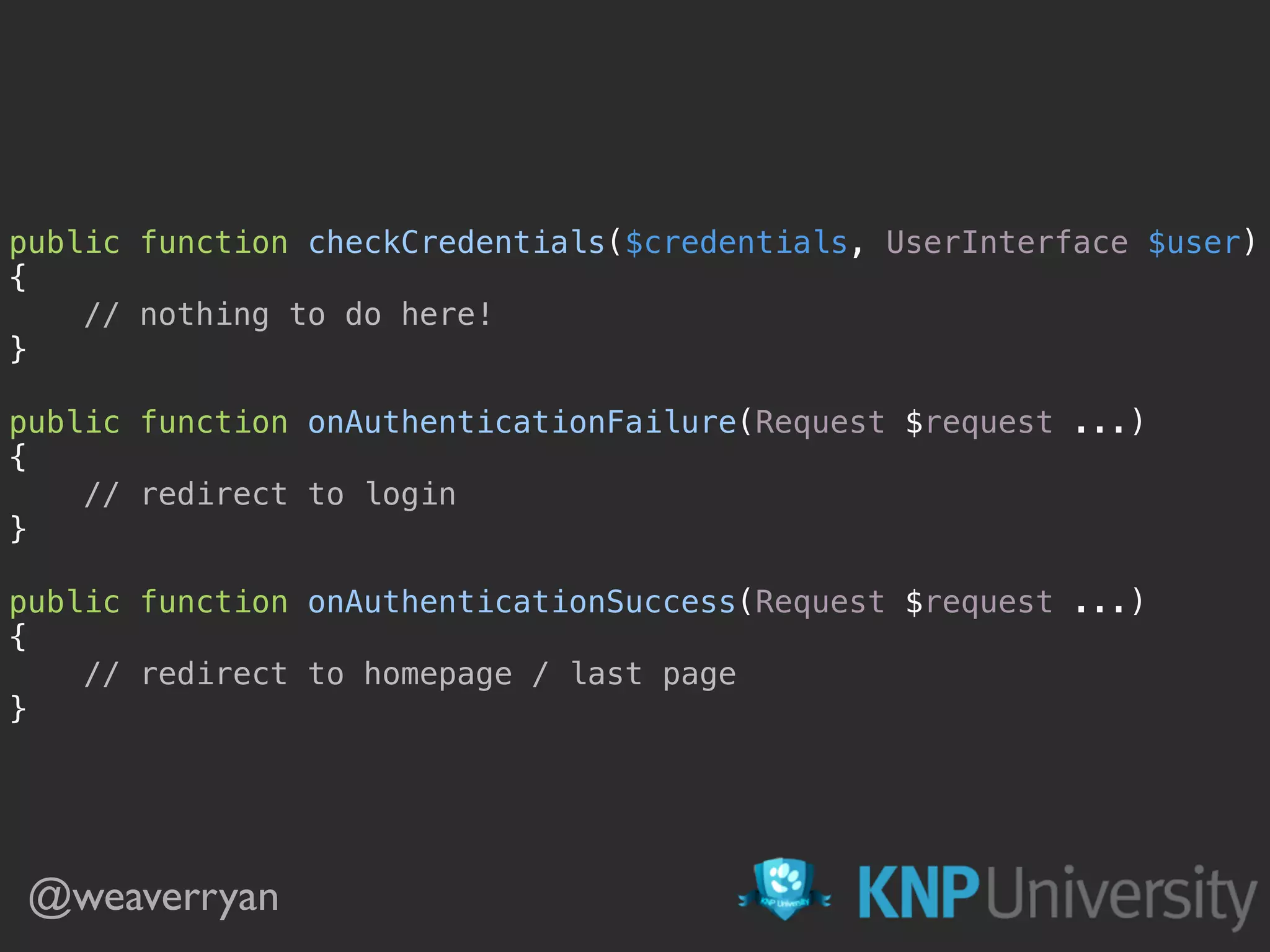
![public function getUser($credentials, ...)
{
$apiToken = $credentials;
$user = $this->em
->getRepository('AppBundle:User')
->findOneBy(['apiToken' => $apiToken]);
if (!$user) {
throw new CustomUserMessageAuthenticationException(
'That API token is stormy'
);
}
return $user;
} @weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-102-2048.jpg)

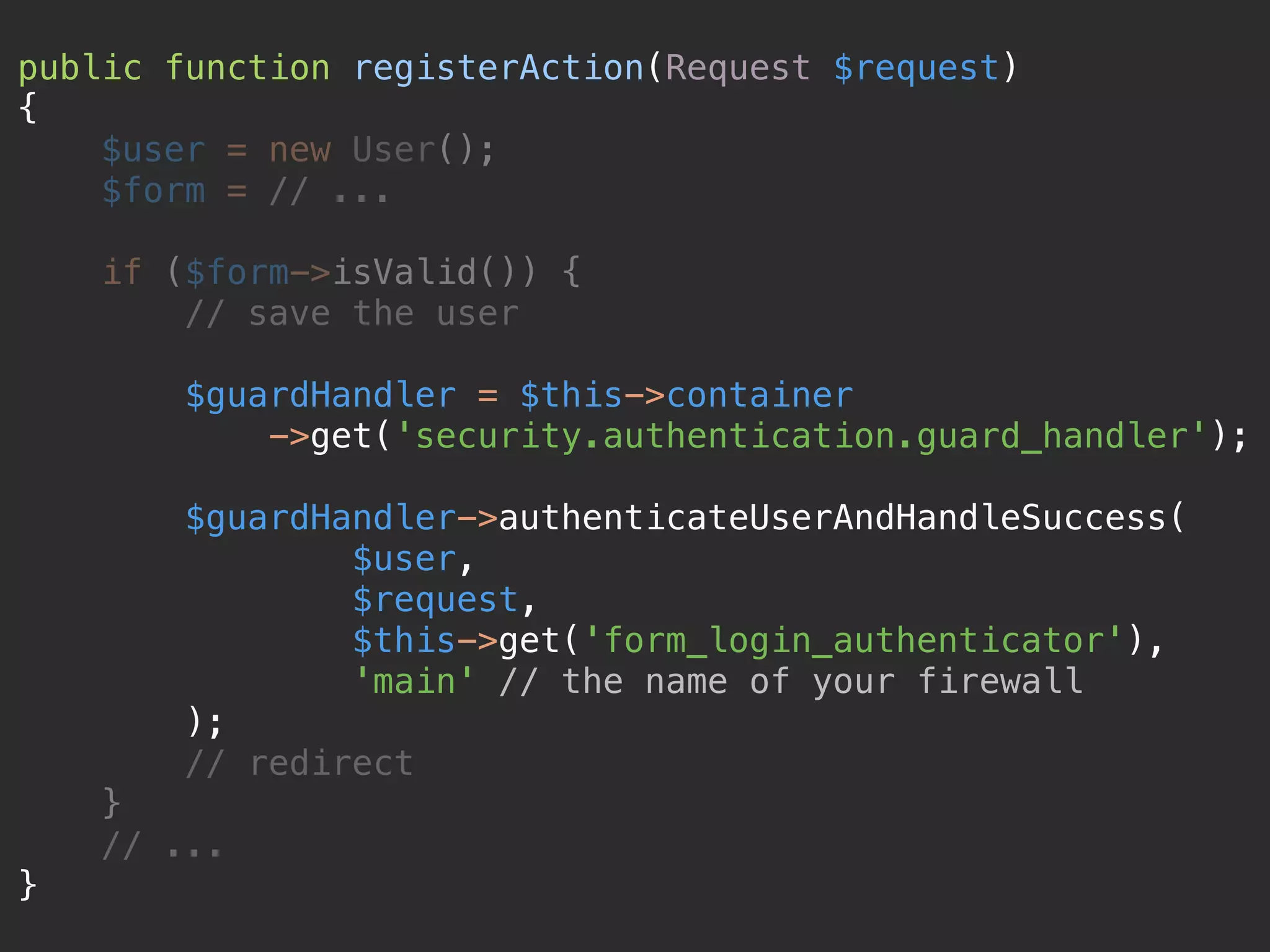
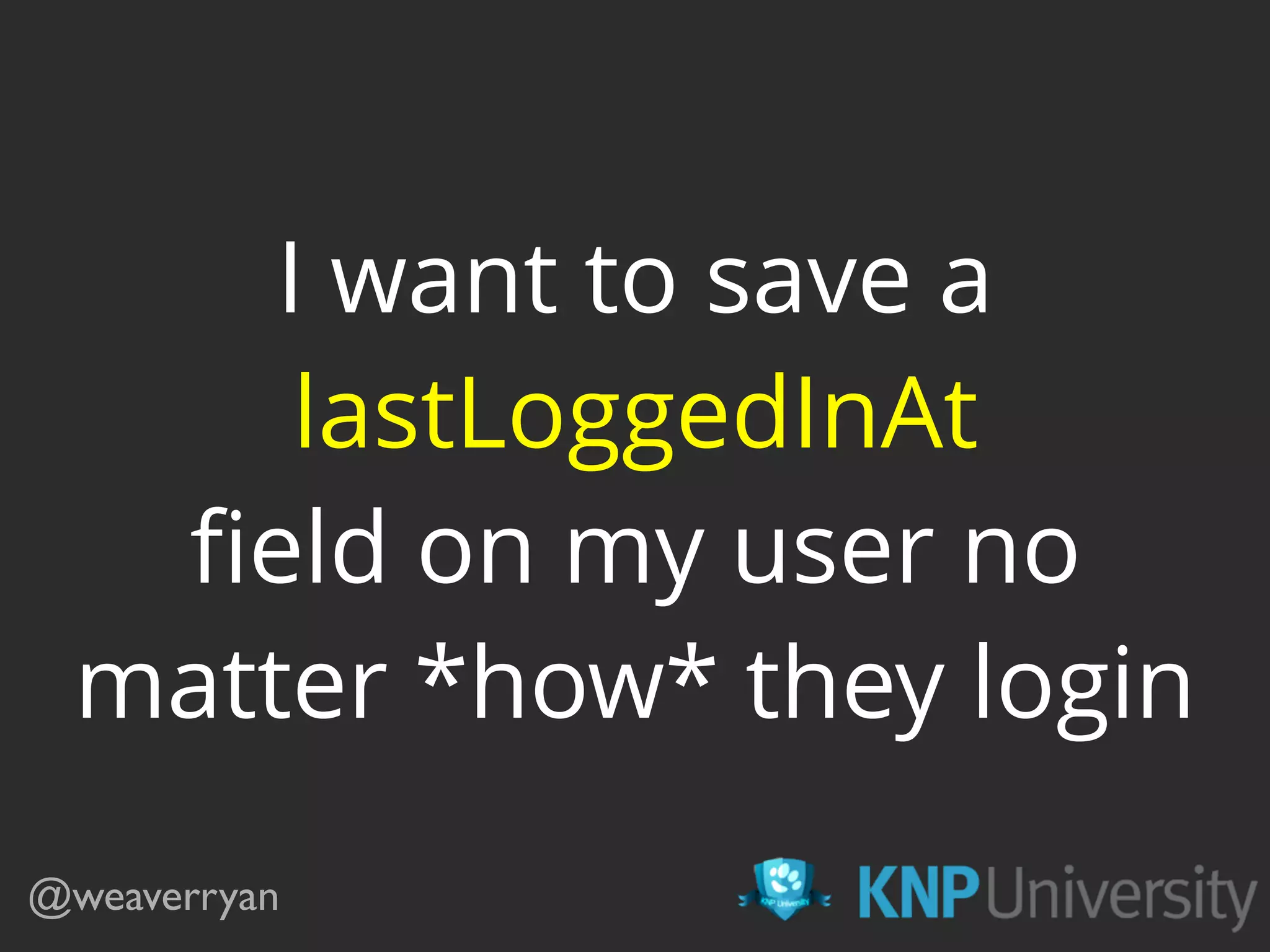

![class LastLoginSubscriber implements EventSubscriberInterface
{
public function onInteractiveLogin(InteractiveLoginEvent $event)
{
/** @var User $user */
$user = $event->getAuthenticationToken()->getUser();
$user->setLastLoginTime(new DateTime());
$this->em->persist($user);
$this->em->flush($user);
}
public static function getSubscribedEvents()
{
return [
SecurityEvents::INTERACTIVE_LOGIN => 'onInteractiveLogin'
];
}
}
@weaverryan](https://image.slidesharecdn.com/sunshinephp2016-guard-160206111232/75/Symfony-Guard-Authentication-Fun-with-API-Token-Social-Login-JWT-and-more-107-2048.jpg)