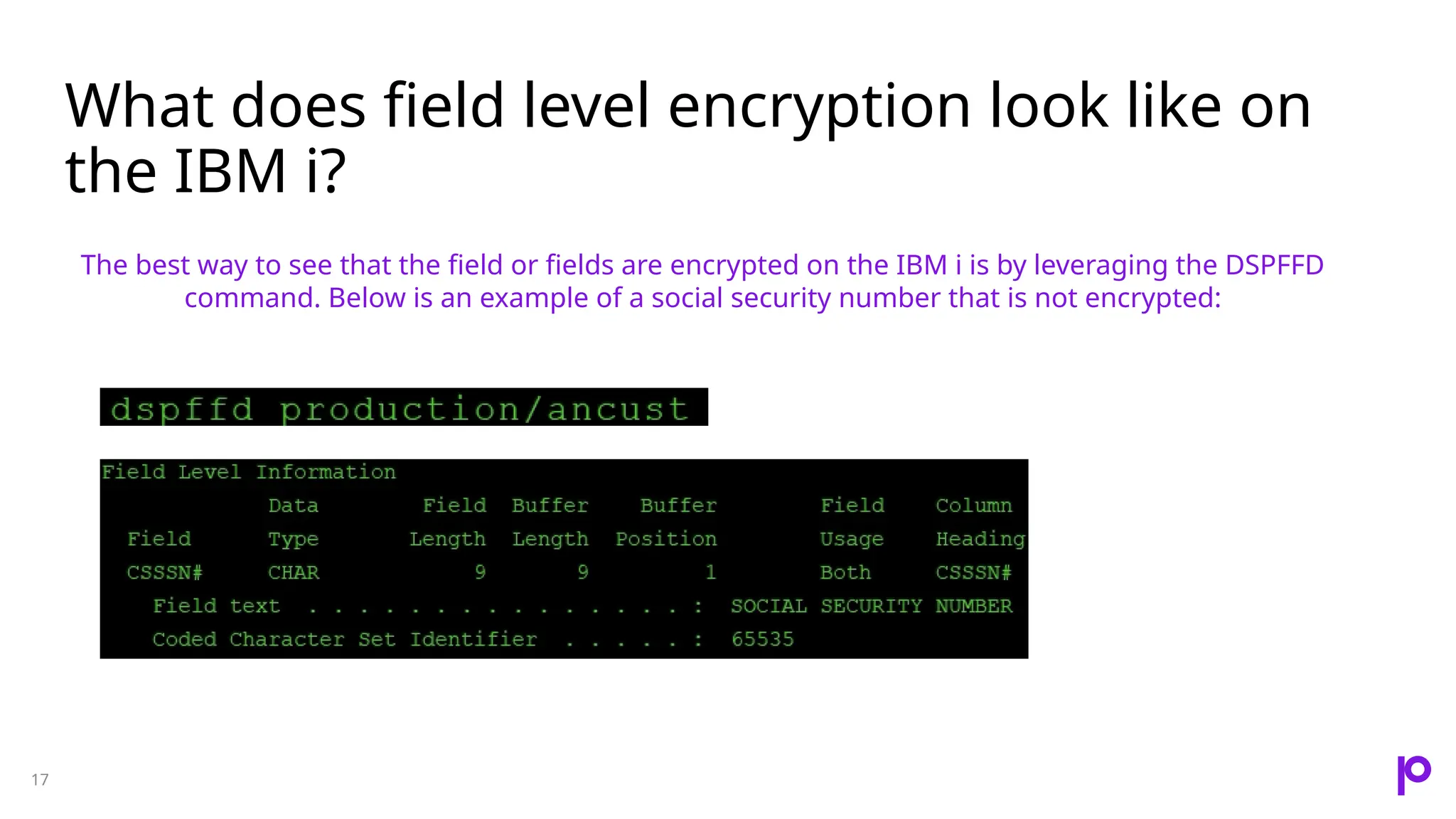
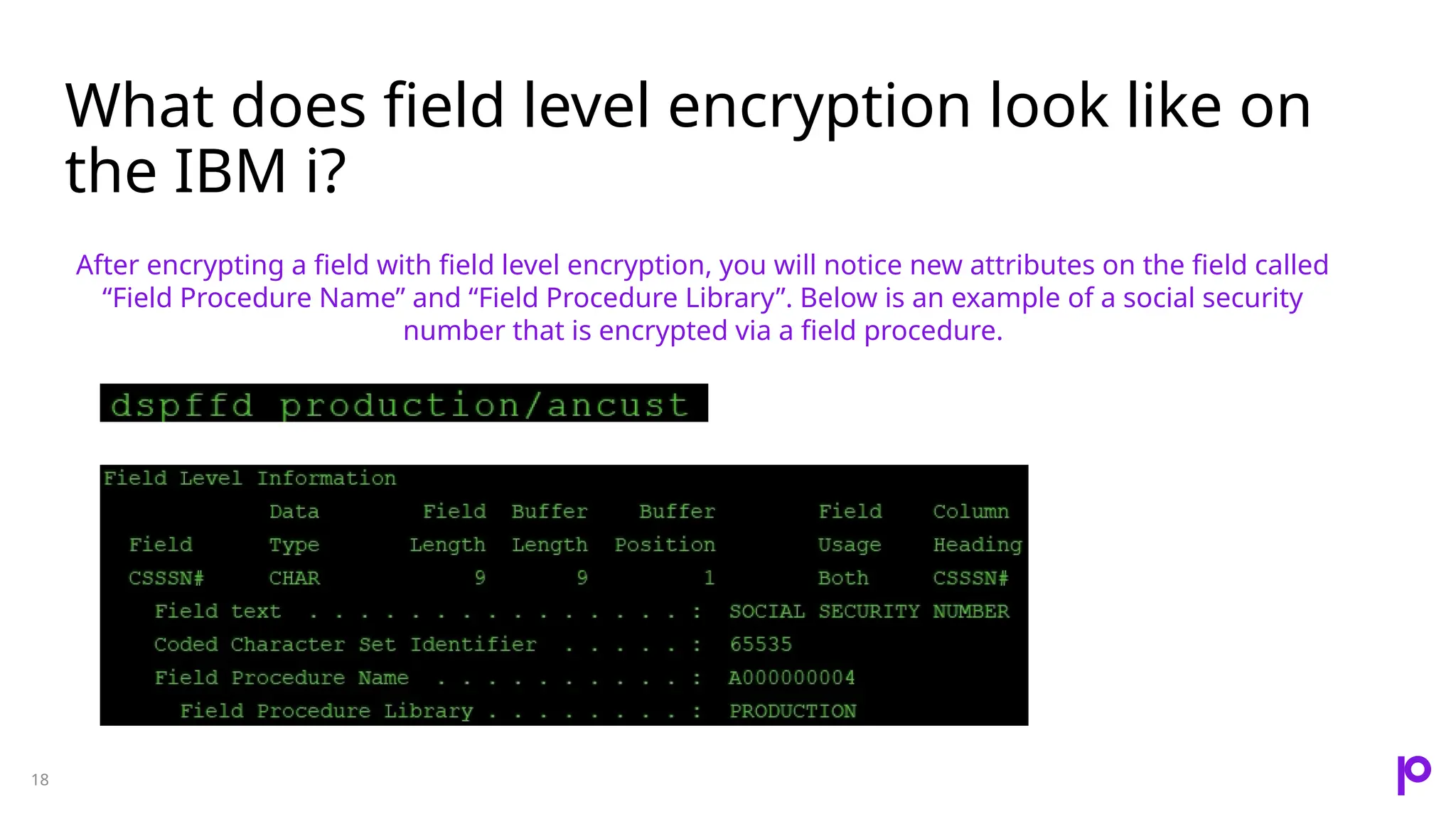
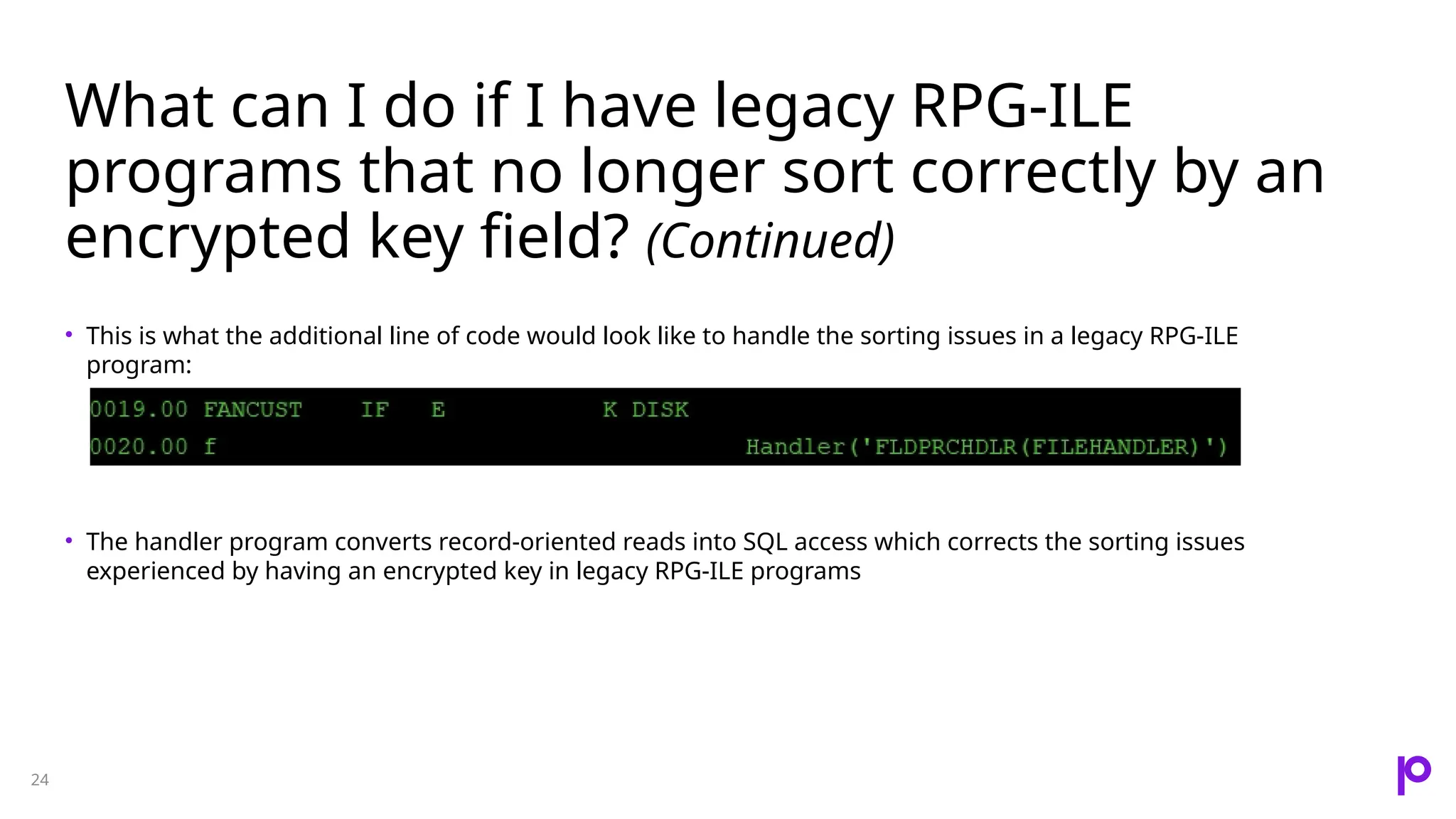
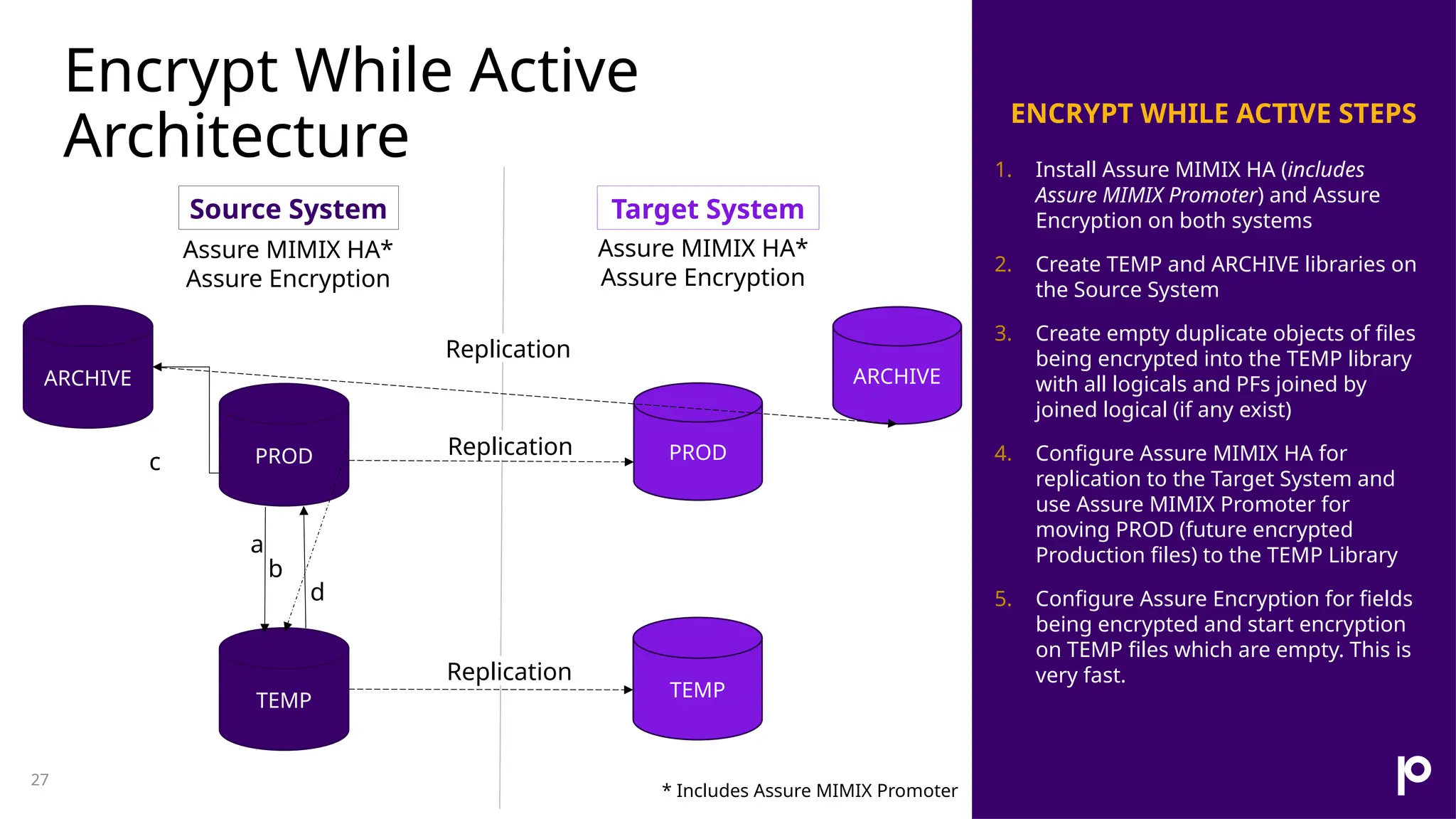
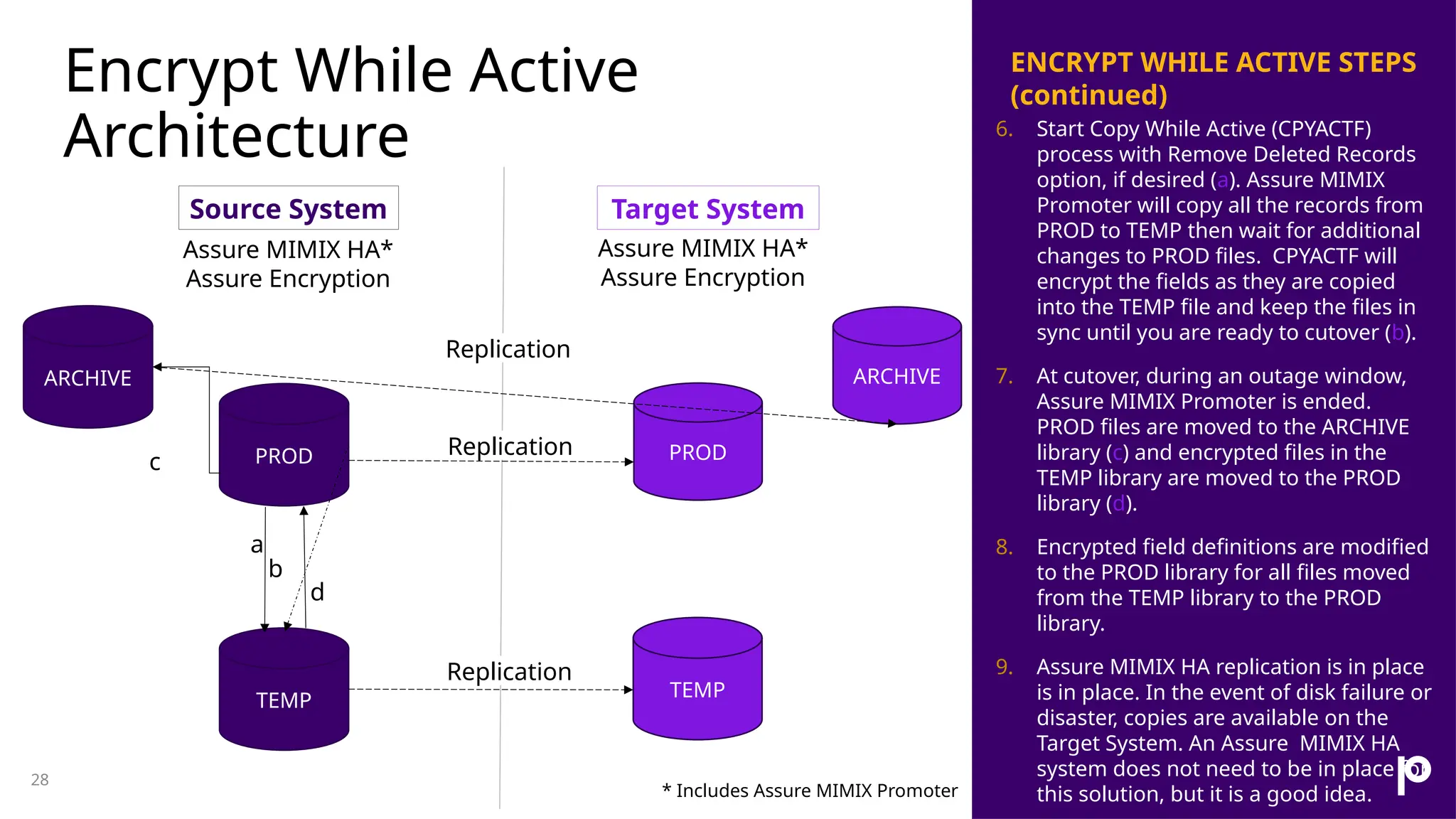
The document discusses the importance of data encryption for protecting sensitive information on IBM i systems, highlighting benefits such as data protection, compliance, and maintaining brand reputation. It compares different encryption strategies, including disk-level and field-level encryption, and introduces the 'encrypt while active' feature that minimizes downtime during encryption processes. Additionally, it addresses challenges such as key management and application risks associated with encryption implementation.