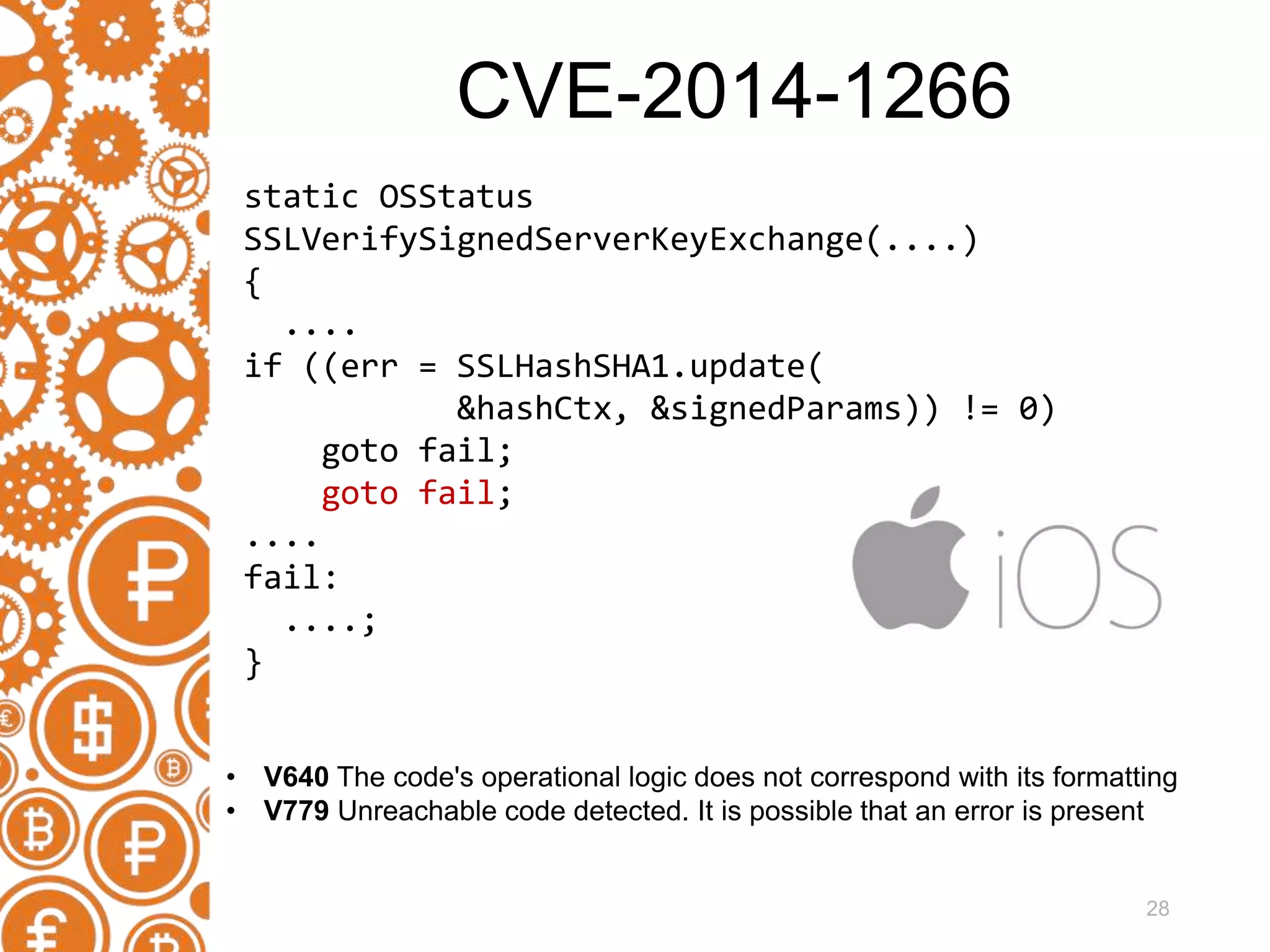
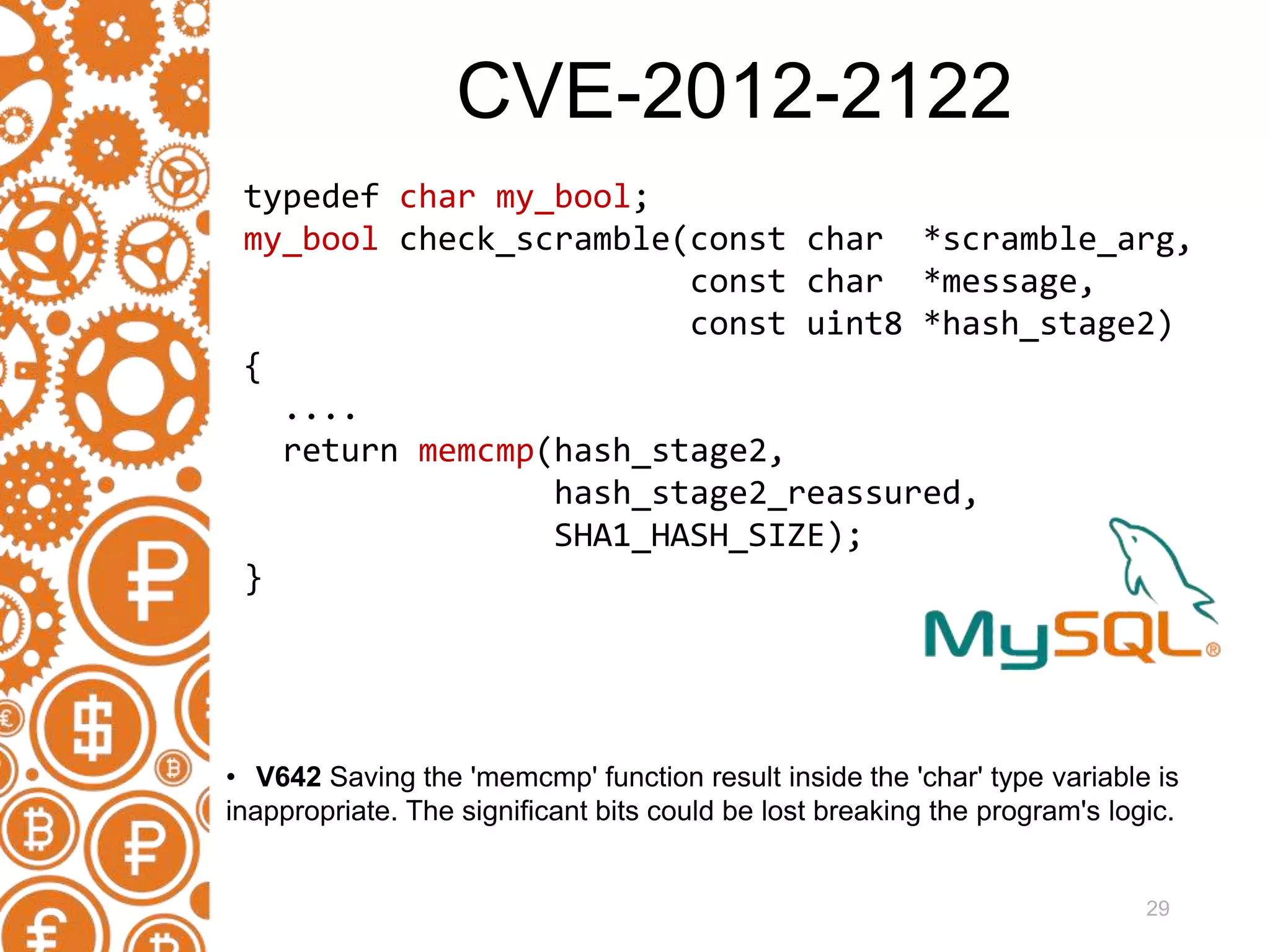
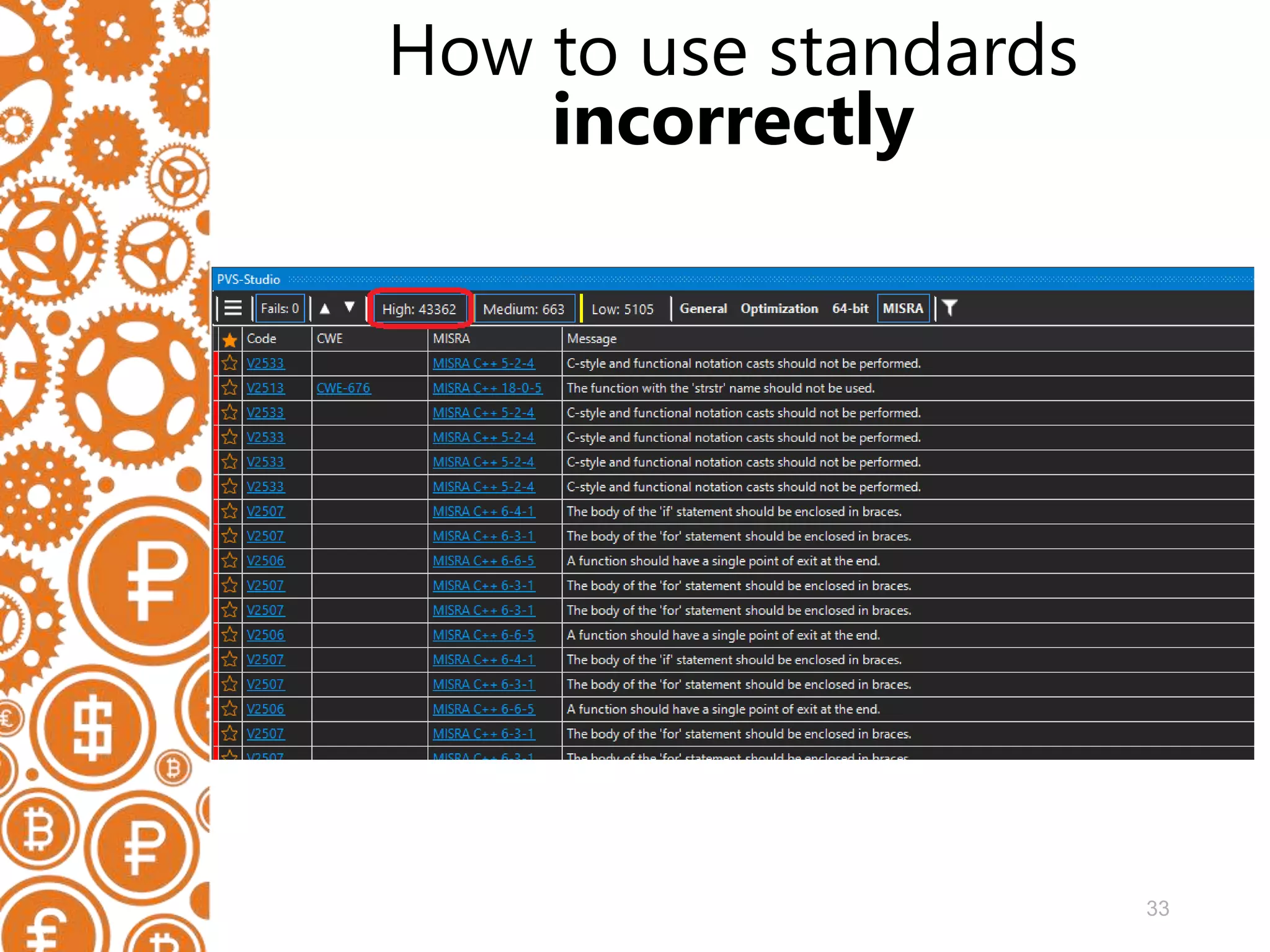
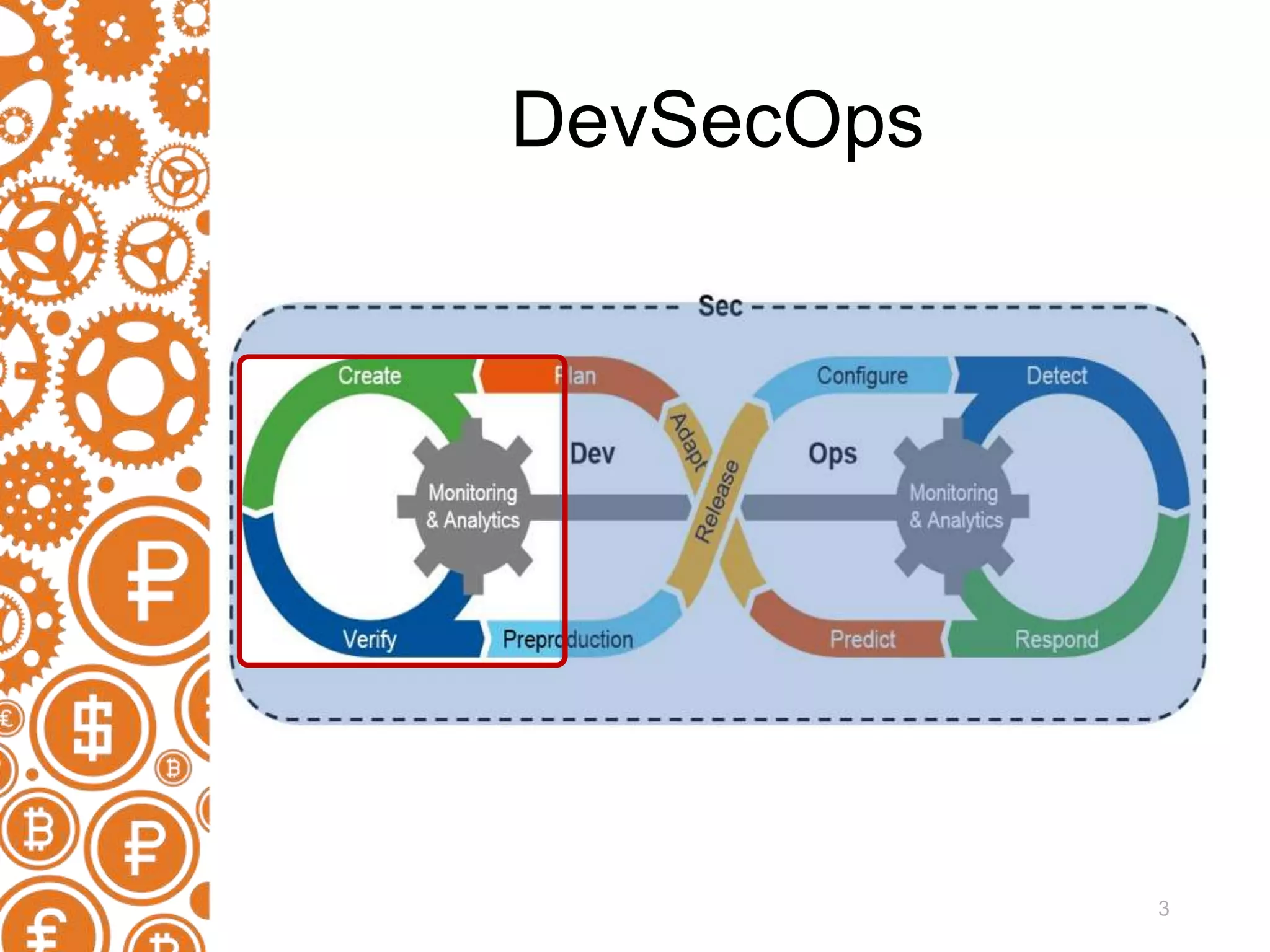
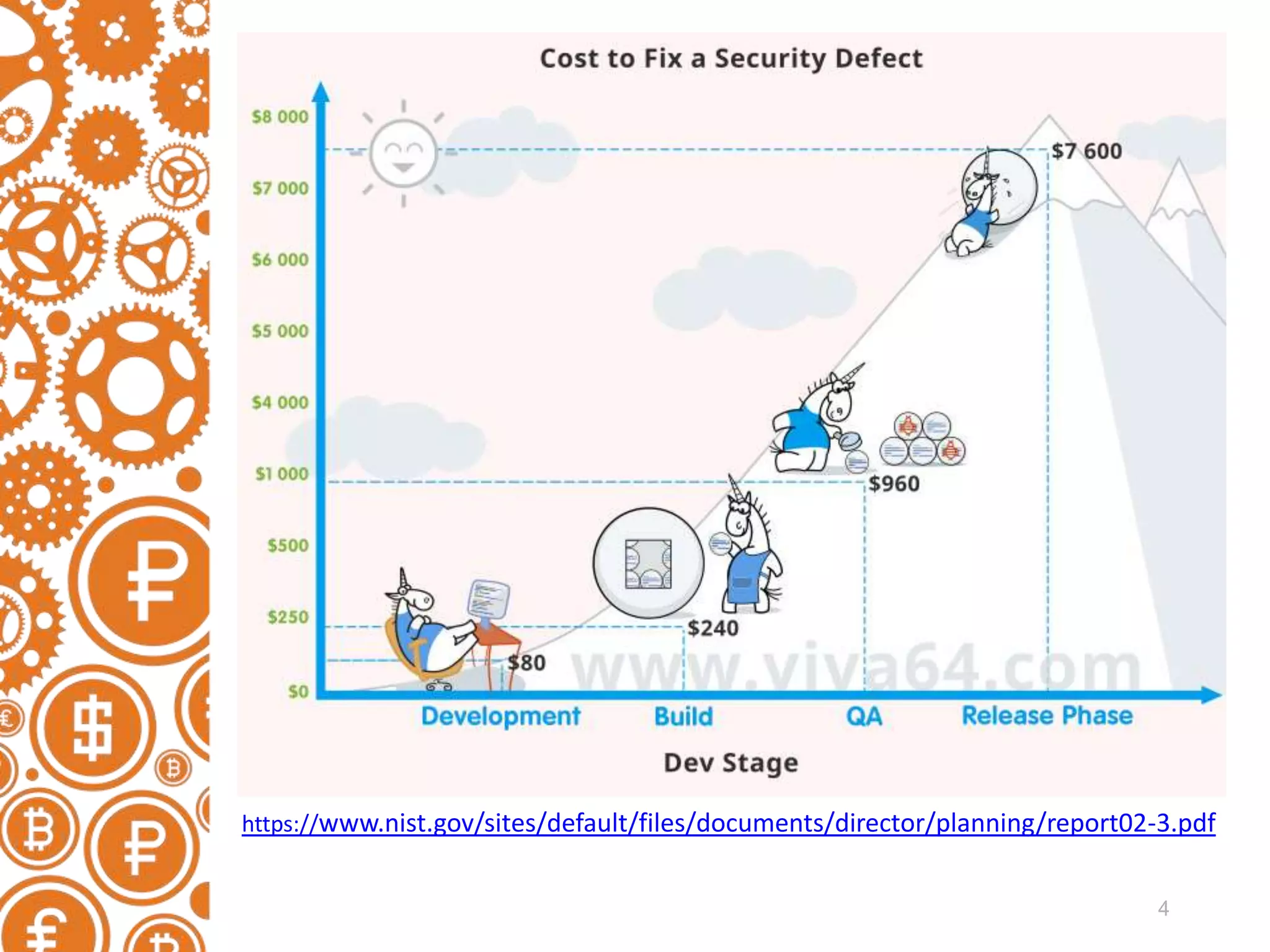
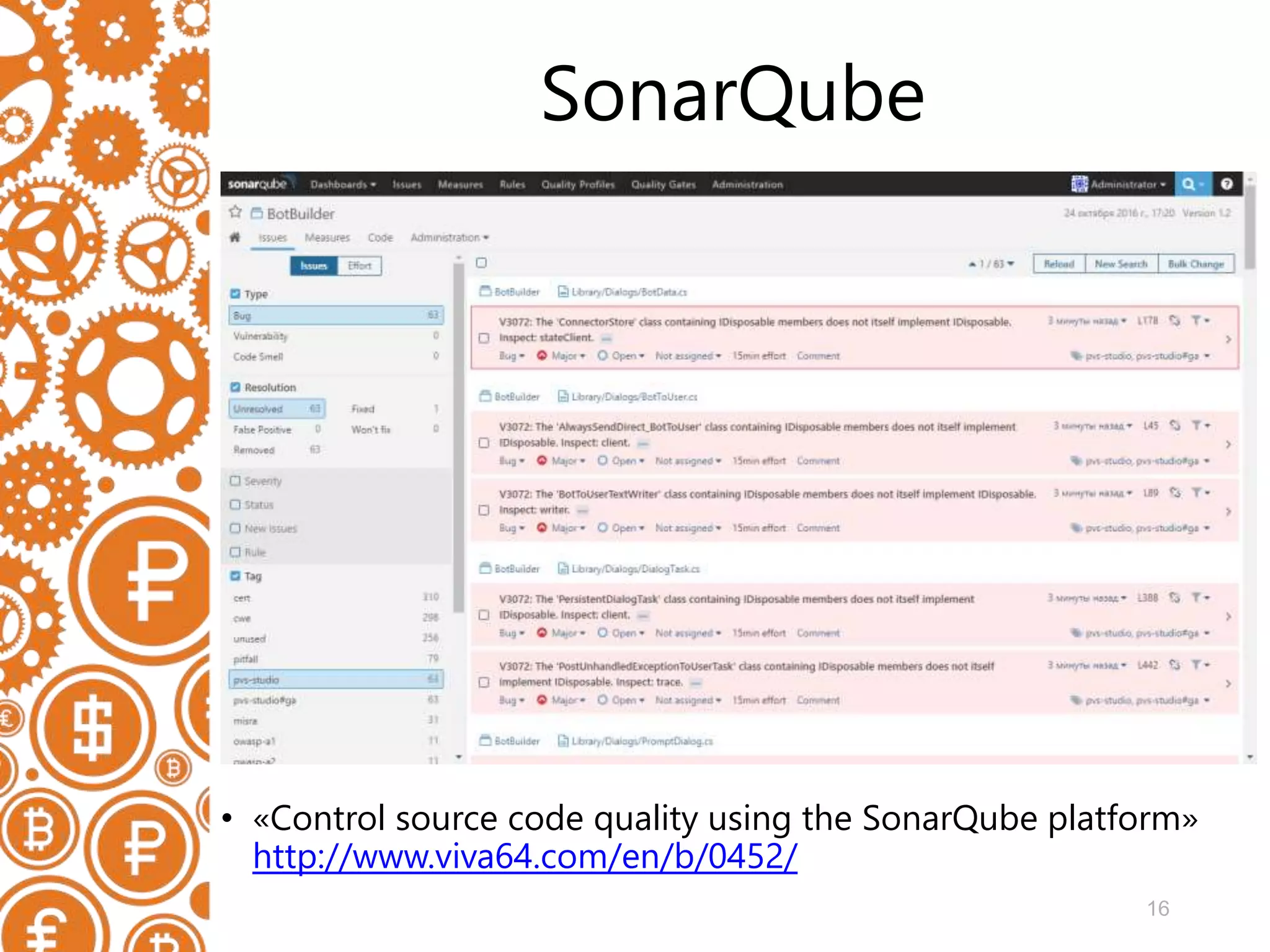
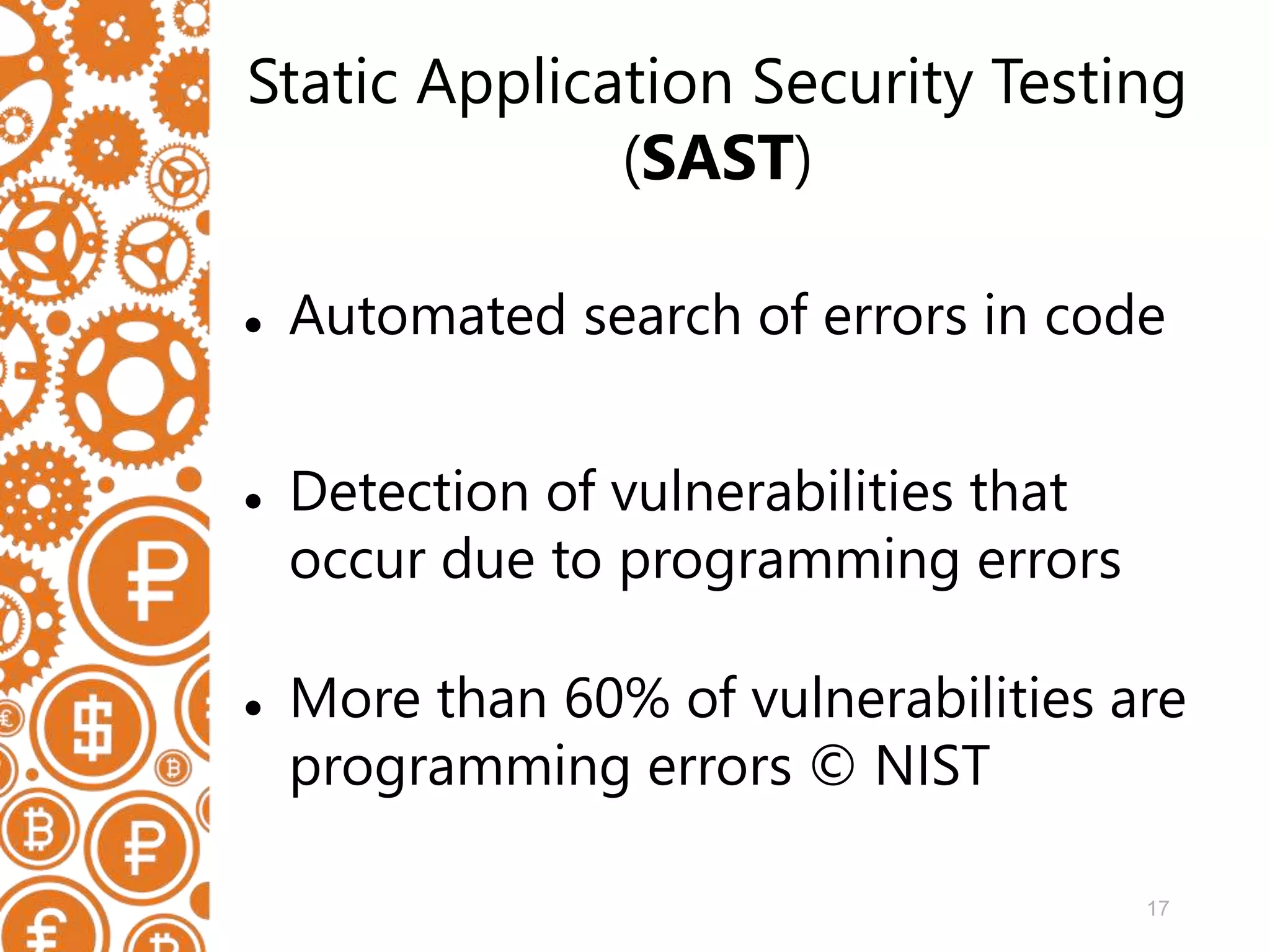
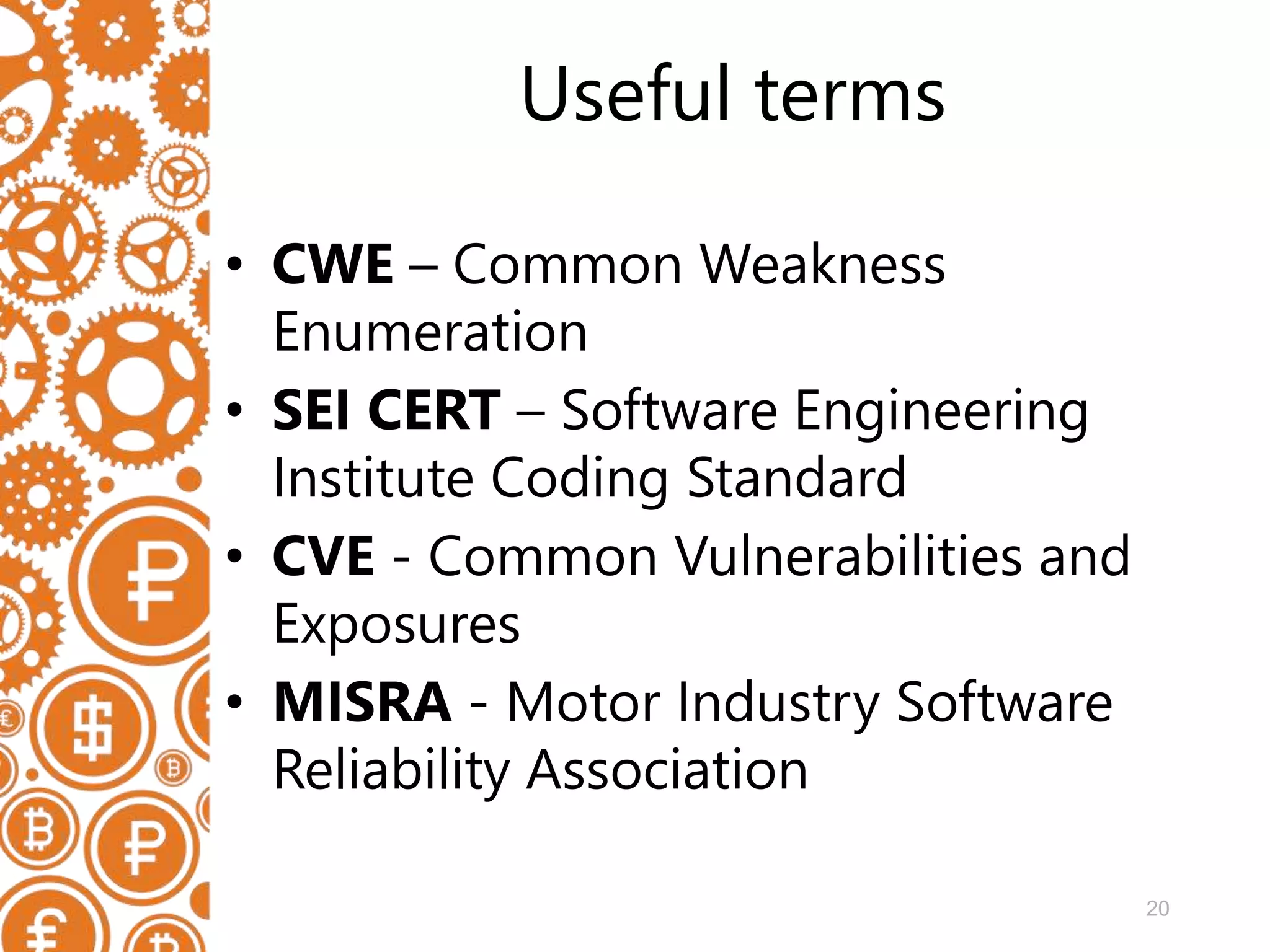
The document discusses the role of static code analyzers in a DevSecOps environment, highlighting their automation benefits for vulnerability detection compared to traditional code reviews and dynamic analysis. It emphasizes the importance of integrating these tools into development processes for ongoing error detection and prevention, using standards and frameworks such as CWE, CVE, and MISRA. The conclusion stresses the high cost of security issues in final products and advocates for regular static analysis to uncover potential vulnerabilities early in the development cycle.











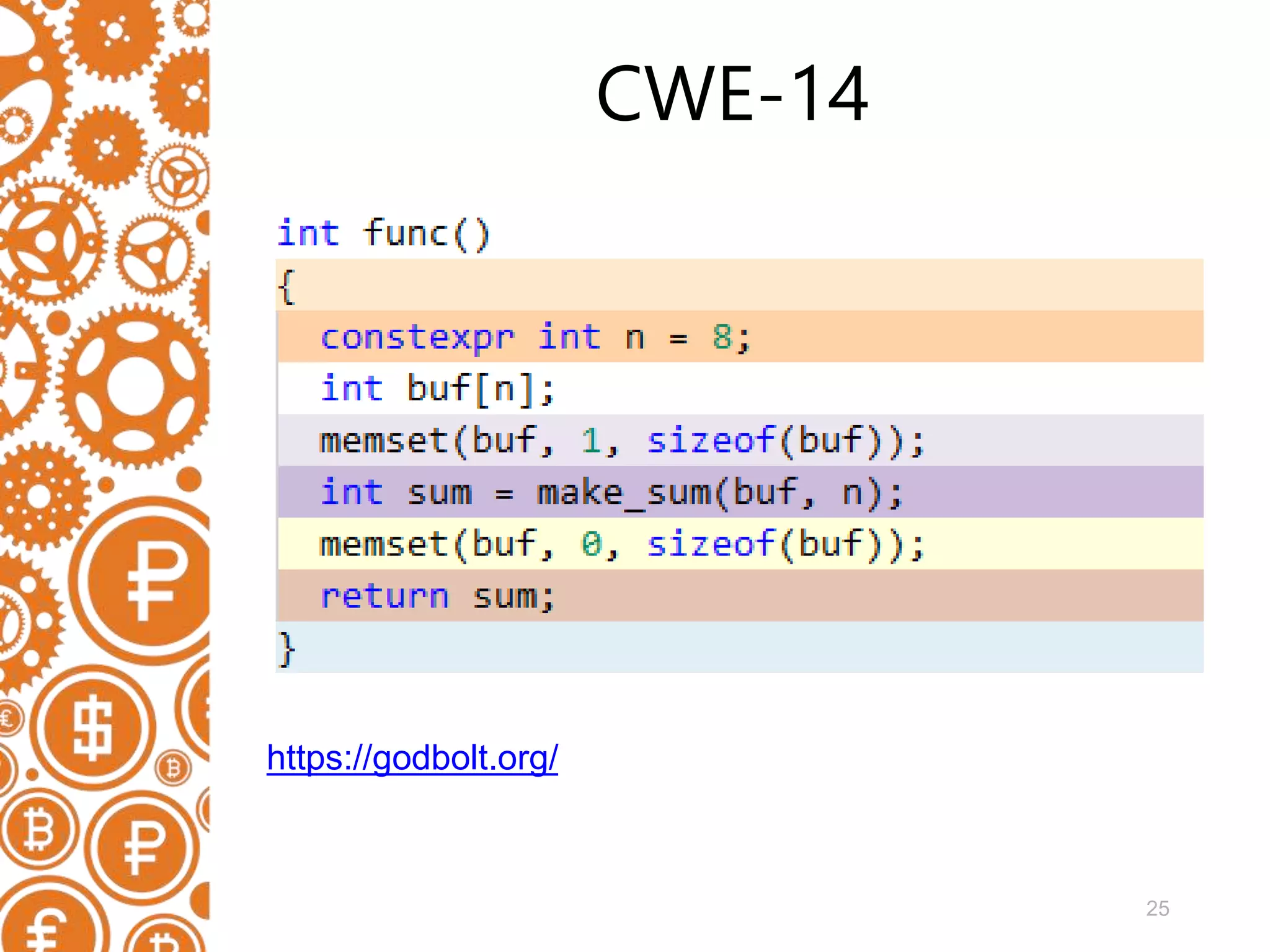
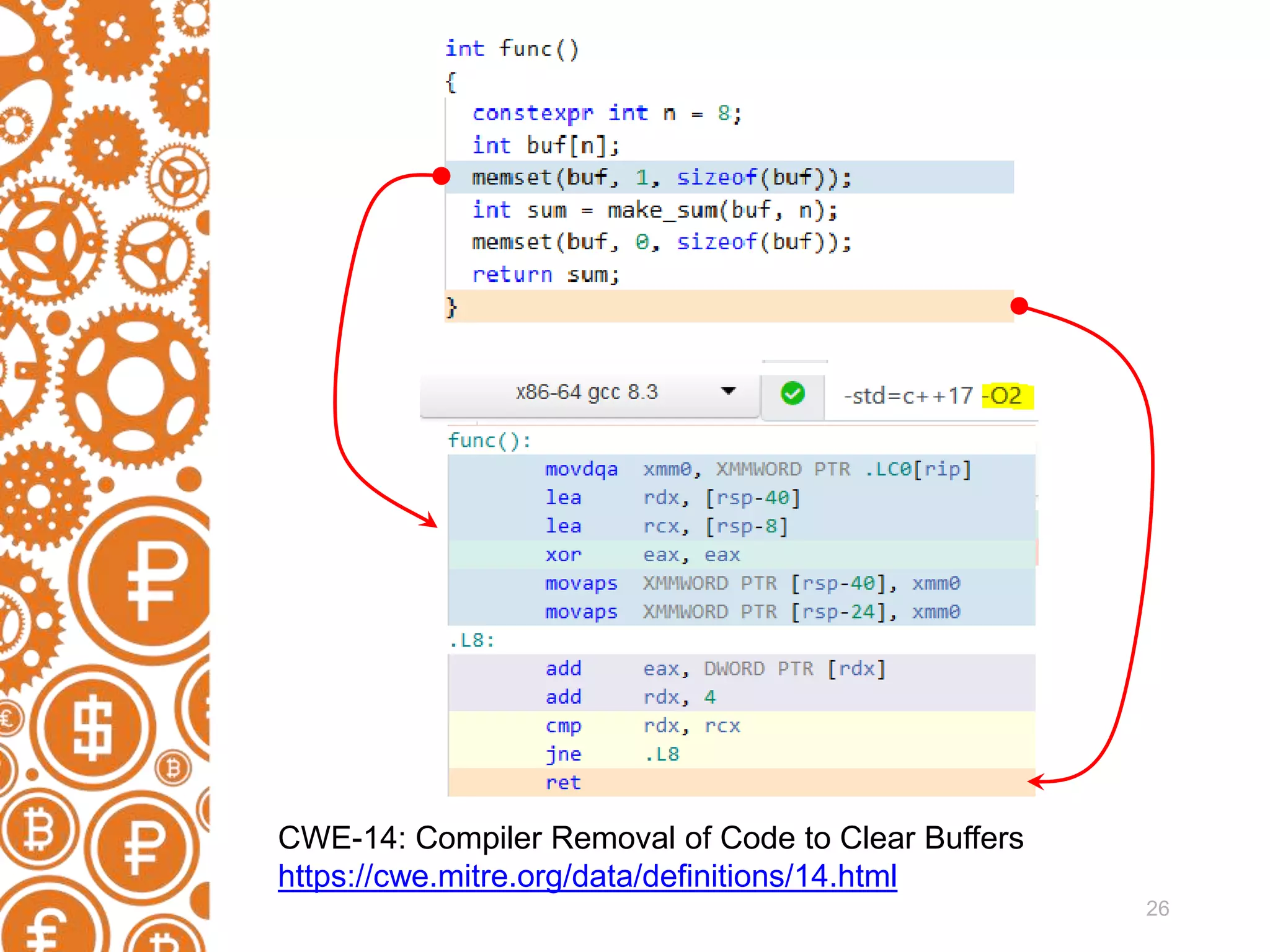
![23 Example of CWE static void SHA1Final(unsigned char digest[20], SHA1_CTX *context) { u32 i; unsigned char finalcount[8]; .... memset(context->count, 0, 8); memset(finalcount, 0, 8); }](https://image.slidesharecdn.com/men-190508205905/75/Static-code-analyzers-as-a-DevSecOps-solution-23-2048.jpg)
![24 Example of CWE static void SHA1Final(unsigned char digest[20], SHA1_CTX *context) { .... memset(finalcount, 0, 8); } CWE-14 V597 The compiler could delete the 'memset' function call, which is used to flush 'finalcount' buffer. The memset_s() function should be used to erase the private data.](https://image.slidesharecdn.com/men-190508205905/75/Static-code-analyzers-as-a-DevSecOps-solution-24-2048.jpg)